
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Rethinking the process of hard drive sanitizing
In this issue
- BONUS DOWNLOAD: A deep and wide reference to Office work
- TOP STORY: Rethinking the process of hard-drive sanitizing
- WACKY WEB WEEK: Shall we dance everywhere with Matt?
- BEST PRACTICES: Hidden tricks to make Gmail work better for you
- LANGALIST PLUS: Forgotten/lost/damaged Content Advisor password
- LOUNGE LIFE: Always good advice: Check your settings!
- PATCH WATCH: A new operating system, a new round of patches
A deep and wide reference to Office work
|
Microsoft Office 2010 is a really big set of tools. Even if you’re intimately familiar with just one, two, or even three of its iconic programs, you can be forgiven for not remembering every nuance of the suite. Microsoft Office 2010 On Demand, by Steve Johnson, can prod your memory for those simple — but infrequently used — Office tasks. But it also has the depth to help prepare you to become a Microsoft Certified Applications Specialist (for which you must pass an exam). This month, all Windows Secrets subscribers can download two excerpts. Chapter 5, “Formatting Office Documents,” explains the sophisticated formatting tools with which you can create a consistent look for all your business documents. Chapter 24, “Expanding Office Functionality,” instructs you in add-ins, macros, and how to work with Microsoft Visual Basic for Applications. It can move you from simply using Office programs to customizing them. If you want to download these free excerpts, simply visit your preferences page and save any changes; a download link will appear. Info on the printed book: |
Rethinking the process of hard-drive sanitizing
Standard drive- and file-wiping tools are no longer adequate for completely removing data — especially when used with the newest hard drives.
But researchers have identified new procedures that reliably make old data virtually unrecoverable on any drive, whether magnetic or solid-state.
Leftover data is an obvious security risk when you sell, give away, or otherwise dispose of any computer storage device. Any data — old documents, files, financial records, passwords, photos, whatever — left behind on a hard drive can come back to haunt you, should they fall into the wrong hands.
Most Windows Secrets readers already know that simply erasing files or reformatting a drive doesn’t mean your data is safely removed. There are plenty of undelete and unformat tools (many free) readily available that require no special skills to use.
That’s why, for years, the common advice has been to sanitize or wipe a hard drive before it leaves your possession. The process most often used is overwriting, which typically replaces all existing data with meaningless patterns of ones and zeros.
That’s the theory, at least.
Erasing everything is actually not all that easy
It’s been known for some time that even a multi-pass (so-called “government”) wipe of traditional magnetic drives leaves behind some data — information that might be recoverable by someone with enough access, time, and forensic technology to analyze the drive’s platters.
For example, powerful signal-processing software can unravel many layers of overwrites to reconstruct the original data. And specialized equipment can easily read between the tracks of a magnetic platter’s normal data-recording zones to recover information recorded in nearby magnetic-field spillover areas.
Solid-state drives (SSDs) are even harder to fully erase. To prevent their memory cells from suffering premature wear and failure, most SSDs have hardware-level protections that prevent data from being written to the same area again and again. These internal protections might not allow a standard overwrite. Without special software, overwrite data might actually be written to a new area — which obviously defeats the whole point of overwriting!
For that reason, some SSD vendors provide special sanitizing software for their drives. Recently, however, researchers at the University of California, San Diego, Non-Volatile Systems Laboratory found that those tools (and similar tools for flash-based devices such as thumb-drives) often did not work.
Their report, “Reliably erasing data from flash-based solid state drives” (free PDF download), matches similar studies in Europe and elsewhere which found that some vendor-supplied, secure-erasure tools often leave as much as 10 percent of a hard drive’s data still recoverable!
The ugly truth: software-driven wipes or overwrites simply can’t be counted on to erase 100 percent of your data — no matter what kind of drive you have.
In fact, the National Institute of Standards Technology, in its “Guidelines for Media Sanitization” (free PDF download), recommends overwrite-based data-wiping only for the most basic level of data sanitizing (see Table 2-1, “Clearing”).
If you need to securely erase a drive, an overwrite wipe simply isn’t enough anymore.
Introducing the SAFE drive-sanitizing process
After the UCSD researchers identified the difficulties of sanitizing SSDs, another UCSD group developed a solution to the problem. And it turns out that their method works on all types of drives.
Called Scramble and Finally Erase (SAFE), the process is beautifully simple in its essence. First, encrypt your sensitive data; then, use a proven disk-erasure tool (not necessarily one supplied by the drive vendor). For more on SAFE, see the free PDF download, “SAFE: Fast, verifiable sanitization for SSDs.”
This two-step process is safer and more reliable than either encryption or drive-wiping alone. A good wiping tool will ensure that very little original data is left behind; encryption ensures that anything left behind will be incomprehensible gibberish.
Let’s take a look at the two components of SAFE drive-sanitizing.
SAFE, step one: Encrypting all sensitive data
A quick Web search will turn up dozens of tools that can encrypt your most sensitive files — or an entire hard drive.
Your needs might be different, but file-level encryption is sufficient for me because most of the files on my hard drive don’t contain any particularly sensitive information.
Although Windows offers built-in encryption services (I’ll come back to this in a moment), my tool of choice for file-level encryption is the free, open-source 7-Zip (site). It not only compresses files and folders to a fraction of their original size, it can also apply strong AES-256 encryption (Wikipedia explanation) to those files or folders. 7-Zip is free, fast, and easy to use. I routinely employ it to compress and encrypt financial, tax, and other sensitive files.
If you need or prefer whole-disk encryption, the free, open-source TrueCrypt (site) is an excellent choice. It runs on all versions of Windows (plus Mac and Linux, too). Once set up, it offers automatic, transparent, real-time (on-the-fly) encryption of everything on your hard drive.
Of course, any encryption scheme needs a strong password, or there’s no point to it. I use RoboForm (free and paid; site), which stores all my passwords in its own, separate, AES-256 encrypted database. I need only generate and remember one password — my master password to RoboForm itself — and the app remembers all the rest. This lets me use long and complex (thus, extremely safe) passwords that I don’t have to memorize.
RoboForm can keep one copy of your encrypted passwords on whatever device you’re using (PC, phone, tablet, etc.) and another encrypted copy in the company’s online database. (RoboForm never stores or transmits passwords in plaintext.) The centralized database synchronizes passwords across all your devices; it also ensures that, even if you lose access to your local copy — say, through a hard-drive crash — your encrypted passwords still are safely backed up and recoverable.
The free version of RoboForm is trialware, allowing you to store only a handful of passwords. The paid RoboForm Everywhere version that I use is currently offered at only U.S. $9.95 per year. But there are other, well-regarded password managers that are completely free, such as the open-source KeePass Password Safe (site) and LastPass (site; paid version adds smartphone support and removes ads).
And again, you can find plenty of other encryption tools with a Web search.
Windows’ built-in encryption-tool limitations
Since Windows 2000, Microsoft has offered the Encrypting File Service (EFS) as an option with the NTFS file system. Although EFS works, it has some serious drawbacks.
For example, it’s fully supported only in the business-oriented editions of Windows — it’s not available in the Starter, Home Basic, and Home Premium editions of Windows 7 and Vista. (The third-party encryption tools mentioned earlier can work on all versions of Windows.)
Another drawback: EFS depends on the presence of a kind of key file — an encryption certificate — that must be available on your hard drive in order to decrypt EFS-scrambled files. If the encryption certificate is damaged, corrupted, or lost and you don’t have a backup (more on that below), you won’t be able to decrypt your files.
If that’s not a problem for you (and you have a business edition of Windows), it’s easy to encrypt any file or folder. Simply right-click it, select Properties, click the Advanced button near the bottom of the General tab, and then select Encrypt contents to secure data, as highlighted in Figure 1. Click OK to finish.
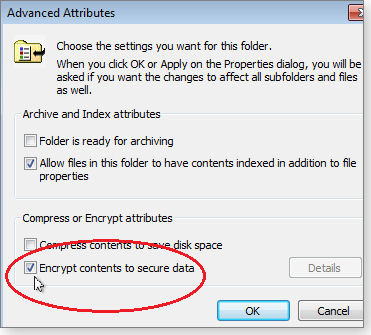
Figure 1. In business-oriented editions of Windows, encrypt files and folders via their Properties menus.
The first time you use this encryption method, Windows reminds you to back up the encryption certificate, as shown in Figure 2.
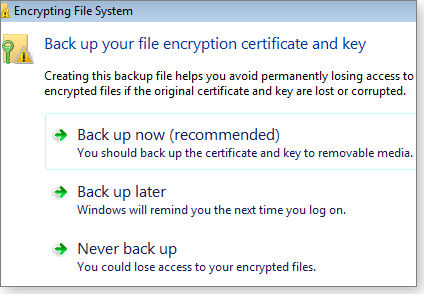
Figure 2. Follow the on-screen instructions to create a password-protected backup copy of the Windows encryption certificate.
Making a complete backup of the certificate is a two-step process. Once you’ve created a local backup file (by default, it’s placed in your Documents folder), put a copy of that file in a safe, off-system location such as an external hard drive or a CD — anywhere but the drive where the encrypted files are stored.
Remember: You must always have a working copy of the certificate available, or your files will be forever encrypted and unrecoverable.
Yes, this is kind of a pain— and it’s one of the reasons I find EFS to be overkill for my modest encryption needs. If you want to delve further into EFS, there’s plenty of additional information online from Microsoft. For example, see the TechNet article, “The Encrypting File System.”
Windows’ BitLocker offers whole-disk encryption
The Enterprise and Ultimate versions of Vista and Win7 also offer an enhancement to EFS — BitLocker Drive Encryption — which encrypts entire drives.
It works fine and has its place, but it has even more drawbacks than does EFS. In addition to BitLocker’s limited availability and encryption-certificate maintenance requirements, your PC must have special Trusted Platform Module (TPM) circuitry. Check that your system supports TPM before considering BitLocker.
I think these drawbacks make BitLocker unsuitable for general use, but if you want more information, see the Microsoft article, “Hardware requirements for BitLocker Drive Encryption,” and the BitLocker FAQs for Windows 7 or Vista.
The MS article, “What’s the difference between BitLocker Drive Encryption and Encrypting File System?,” is also useful.
SAFE, step two: Use known-good data-erasure tools
Properly encrypting sensitive files is essential for hard-drive data security throughout a hard drive’s life. But when it’s time to sell, pass on, or scrap the drive, combining encryption with a properly implemented, whole-disk erasure tool will remove all traces of useful data.
Although vendor-supplied tools might not work, there are tools that do an acceptable job of wiping an entire drive.
Secure Erase, developed at UC San Diego’s Center for Magnetic Recording Research, is one example. A free download (site), it’s designed to securely erase magnetic media of all types — and it works with SSDs as well.
Secure Erase is pretty straightforward to use, but if you need more detail, Kingston Technology (a maker of SSDs) offers complete how-to instructions online. The only drawback to Secure Erase: it’s a DOS-level tool, so you have to boot from a floppy, optical disc, external flash drive, etc., to run the software and wipe the target drive.
Another good option is the free (donationware) Parted Magic tool (site). Its Erase Disk menu offers a feature (also called Secure Erase) with two options specifically for flash-based drives. Internal erases internal SSDs; External erases external, USB-based flash drives. (These function much like SSDs, making them almost as hard to sanitize.)
Parted Magic is well documented, but if you need detailed instructions, CNET has a how-to article.
Bottom line: Foolproof hard-drive sanitizing
SAFE really is that simple — just two steps:
- 1. Routinely use encryption to protect at least your most sensitive files (if not the whole drive).
- 2. Wipe the whole disk with a known-good tool when it’s time to sell, scrap, or pass along your device.
With SAFE, you’ll have a high level of confidence (especially if you use whole-disk encryption) that none of your data can be extracted from your retired drives without an extraordinary amount of time, effort, and cost.
And remember: The SAFE approach works for any kind of drive — thumb, SSD, or magnetic!
Shall we dance everywhere with Matt?
 |
For about a decade, video-game developer and world traveler Matt Harding has danced enthusiastically — though not beautifully — in many exotic locations. In this latest of his viral videos, he dances with new friends in 71 places around the world. For most people, Matt’s dancing with anyone and everyone is deeply cheering. See whether you feel like joining him. Play the video |
Hidden tricks to make Gmail work better for you
If you use Gmail’s Web-based user interface, you know its power and versatility. But you might not know some of its less obvious nuances.
Here are eight Gmail tips that could make your e-mail chores easier.
Some new features from Google’s public workshop
Most of these Gmail enhancements come from Google Labs, a place where new, experimental features are poked, prodded, and tweaked for a while. Some of these experiments eventually become official Gmail features; others might simply disappear.
I’ll tag these Labs features so you’ll know where to look for them. Almost all of the tweaks discussed are enabled via Gmail’s Settings menus. So I’ll start by reminding you how to get there:
- Step 1. Click the gear-shaped Tools icon near the upper-right corner of the Gmail window (just below your personal photo) and select Settings from the drop-down list.
- Step 2. For the tricks tagged “Labs,” click Labs in the tabs bar. That page will list experimental features currently available. The Labs page does warn that these features might “change, break, or disappear at any time.” In other words, you use them at your own risk.
If you want to try something in Labs, click the Enable button. The Labs page lists features in alphabetical order and conveniently keeps all enabled features at the top of the list.
- Step 3. After you’ve made your tweaks to Gmail, always scroll down to the bottom of the settings page and select Save Changes.
Read a message before officially opening it
Labs: Working through newly arrived messages, opening and closing each one, can be a nuisance. And marking a message as “unread” after reading it is yet another nuisance. Message Sneak Peek lets you read new messages without formally opening them. If a message was “unread,” it remains officially “unread.”
Once Message Sneak Peek is enabled, you simply right-click any message and it’s immediately displayed in a popup box. (Click the View entire thread link, however, and the message becomes “read.”)
Message Sneak Peek is obviously a work in progress. When you view highly formatted messages (such as the Windows Secrets newsletter), some of the text on the right side is clipped off; there’s no way to expand the width of the window and no horizontal scroll bar to slide the missing text into view.
Control Gmail via keyboard shortcuts
If you prefer keeping your hands on the keyboard to mousing around, try Gmail’s Keyboard Shortcut option. Once it’s enabled on the Settings page, for example, you can simply press c to compose a message (Shift + c pops up a blank message in a new window) or n to read the next message in a thread.
The Google keyboard help page provides the complete list. (You’ll probably want to print it out, at least to start.) To best understand how Gmail’s keyboard shortcuts work, you’ll have to experiment on your own — the instructions are thin at best.
Labs: Using a Labs feature, you can take keyboard shortcuts a step further with custom key combinations. Click the Labs tab and enable Custom keyboard shortcuts; when you save the change, a new “Keyboard Shortcuts” tab appears in the Settings page tabs bar. Clicking the new tab displays a box with the default shortcut key and an empty field for your new, custom key command. (See Figure 1.)
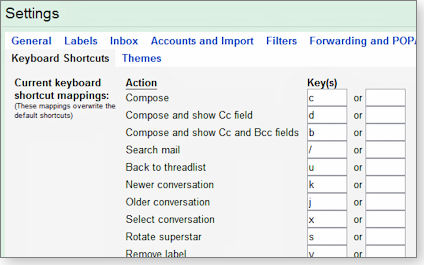
Figure 1. Customizing Gmail keyboard shortcuts
Type it once; reuse it again and again
Labs: You probably have chunks of text that you use over and over again: signatures, your snail-mail address, or statements such as “No thank you — I’m already working on a similar deal with another Nigerian prince.” Enable Canned Responses in Labs, and you can quickly grab those frequently used sentences and phrases.
Canned responses appears as a pull-down menu under the Subject box when you’re composing a message. To create a new response, type the desired text into an otherwise empty message. Pull down the Canned responses menu, select New canned response from the menu (shown in Figure 2), and give your new response a name.

Figure 2. The Canned responses menu lets you select, add, or delete often-used chunks of text.
To insert the text, just select it from the menu’s Insert section. The other two sections let you overwrite a previously saved response or delete a response.
I’m really surprised this feature hasn’t moved out of the Labs — I’ve depended on it for years.
Use the e-mail font of your choice — by default
Labs: When you compose a message, Gmail uses Sans Serif by default — and there’s no easy way to change it. (You have to manually select another font.) Fortunately, the Labs feature Default text styling gives you more control.
When enabled, the feature adds a new category — Default text style — under Settings/General. There you can select your preferred font type, size, color, and so on. It’s another option that should be in Gmail by default.
Text from Gmail without special codes
Labs: It’s possible to send a text message from almost any e-mail client. All you need to know is the recipient’s phone number, the recipient’s mobile carrier, and that carrier’s mail-to-text domain name (more info).
Hey, I didn’t say you could do it easily!
But with help from Labs’ SMS (text messaging) in Chat tool, you can do it easily within Gmail. Once it’s set up, all you need is the number for a phone capable of receiving text messages.
First, though, you have to tweak a couple of Gmail settings. Open Settings and click the Chat tab. Check that Chat on is selected and save any changes. Return to Settings, click the Labs tab, and enable SMS (text messaging) in Chat. Click Save Changes at the bottom of the page.
You should now see a small Chat icon (gadget) at the bottom of Gmail’s left pane. Click the icon and enter the phone number in the “Search, chat, or SMS” text box. Select Send SMS, and a separate window pops up a message-entry box (shown in Figure 3).

Figure 3. Labs lets you add SMS texting to Gmail Chat.
Organize your message labels sensibly
Managing e-mails in Gmail can be confusing. It doesn’t use folders for organizing messages — it uses labels (Google explanation), which work like folders but have added capabilities. For example, you can assign a descriptive label to all messages pertaining to a particular subject. But you can also move a message to a particular label. You can also assign multiple labels to messages that cover more than one subject.
But it’s easy to overdo it. Too many labels will simply organize your mailbox into a state of confusion.
A large number of labels is easier to work with if you can nest them inside each other — as you do folders on your hard drive. For instance, you can have a Money folder containing subfolders for this year’s taxes, last year’s taxes, and money owed to you.
This tree structure for labels is built into Gmail by default — you don’t even have to go the Settings screen to enable it. To create a sublabel inside an existing label, highlight the top-level folder’s name in the Gmail’s left column and click the little down-arrow that appears. In the arrow’s drop-down list, select Add sublabel (shown in Figure 4).

Figure 4. Add sublabel lets you organize messages in a familiar tree structure.
The Gmail Settings/Labels tab gives you a one-stop place to manage labels. Also, whenever a dialog box for creating or editing a label pops up, there’s a Nest label under option. Messages are reorganized as soon as you click Save Changes.
Let your labels organize themselves
Labs: A lot of your mail falls into easily defined categories — and I’m not talking just about spam. Turn on the SmartLabels feature within Labs, and Gmail automatically identifies and labels bulk mail, notifications, and forum messages. Once enabled, SmartLabels adds a Bulk label to your Gmail page. By default, bulk mail (or, more specifically, bulk mail that doesn’t qualify as spam) skips the inbox and is sequestered in Bulk. Notifications and forum messages get labeled but remain in the regular inbox.
You can change that default filtering, of course. Go to the Settings/Filters tab. You’ll find four filters with titles such as Matches: label:^smartlabel_group. (Two of them, _newsletter and _promo, get channeled to the Bulk category.) From there, you can click the edit link to alter what happens to messages identified in any of these categories.
Show other categories of e-mail with the inbox
Labs: In Gmail, clicking the Inbox label displays only messages in the inbox — unless you’ve turned on Multiple Inboxes. This feature won’t help you manage multiple e-mail accounts, but it will show you both your regular inbox and other lists of mail, such as those you’ve starred or assigned a particular label.
To try it, enable Multiple Inboxes in Labs. Once you’ve saved the change, a new tab — Multiple inboxes — will appear in Settings, where you can change the new look.
Note: In the newly configured inbox, the Settings icon will move from its familiar place. It stays with the standard Inbox panel. By default, Multiple inboxes places the Inbox pane below the extra panels (such as your starred messages). To change this, go to the Multiple inboxes tab and scroll down to the Extra panels positioning section.
The Multiple inboxes tab is also where you select the panes (up to five) displayed with the inbox.
Now if only Google could separate the messages with jokes from messages with jokes that are actually funny.
Forgotten/lost/damaged Content Advisor password
When Internet Explorer’s Content Advisor misbehaves, your browser acts as if it were no longer your own.
But here’s how you can reset the password and regain control of IE.
Locked out of IE by a bogus password
Something bad happened to reader Brmacg’s copy of Internet Explorer.
-
“As the administrator of a small home network still operating XP Pro, I have recently been frustrated by Content Advisor’s (IE 8) constant demand for an unknown, forgotten, or lost password needed to access the Web.
“I’ve tried everything. I searched the Windows Secrets archives and found a LangaList post from 2001! However, most of the links are no longer valid.”
Content Advisor is a lightweight, Web-filtering technology. It includes some parental controls that let you limit IE to specific websites (see Microsoft’s Content Advisor FAQ).
As you’d expect, Content Advisor’s settings, once implemented, are locked behind a password.
In XP, the password is encrypted and stored in the Registry. You can regain control of Content Advisor by deleting the password key. You need to be signed in to an admin-level account, but it’s otherwise quite easy.
Vista and Windows 7 users have a much harder path: I couldn’t find a Content Advisor repair process anywhere online, and the official word from Microsoft is to contact MS Support and have a tech perform the repair. (See MS support article 155609.)
Here are the specific steps for Windows XP:
- In an admin-level account, type regedit into the Start menu’s Run box and press Enter.
- When the Registry Editor opens, navigate down the left-hand pane as follows:
- HKEY LOCAL MACHINE\
Software\
Microsoft\
Windows\
Current Version
Policies\
Ratings
- HKEY LOCAL MACHINE\
- Next, in the right-hand pane, select the Key entry and delete it, as shown in Figure 1. (Note: If you haven’t enabled Content Advisor on your XP system, the key doesn’t appear.)
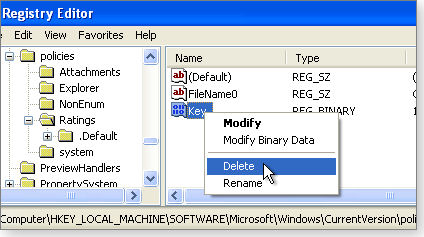
Figure 1. In XP, deleting the Ratings Key wipes out the Content Advisor password.
- Exit Regedit and reboot the system. The Content Advisor password should now be gone — as simple as that! You can now adjust Content Advisor’s actions (or disable them entirely) as you wish.
If you’d prefer a more automated method for XP, see the scripts and small programs offered on a Kelly’s Korner page; look under the C index heading for the Content Advisor section.
Compacting Thunderbird folders loses e-mail
Pat Rourk encountered a nasty malfunction in his copy of Thunderbird, the popular e-mail client from Mozilla.
- “I’ve used Thunderbird for six years and numerous versions. My system is still running XP. (I’m just now migrating to a new Win7 box.)
“Yesterday, [Thunderbird’s] automatic Compact Folders window popped up.
“I selected ‘Yes,’ and, for the very first time, I lost all my inbox e-mails. (Luckily I had read them.) Moreover, a folder that I had just moved 38 pictures to (most of them 250K, none over a megabyte) just flat disappeared.
“This concerns me greatly. I’m just about ready to start using a new PC, and I’m apprehensive about loading Thunderbird after this fiasco. Any suggestions to help me here?”
I hope you had a recent backup available. If so, you can, of course, simply restore the lost messages.
Even if you don’t have a backup, the messages might not be truly gone. Thunderbird stores your messages in a database; the messages are indexed, and the index is also stored in a database. A problem with the index might make your e-mails seem lost — they could still be on your hard drive, but Thunderbird doesn’t know where they are.
Open Thunderbird, click Tools/Account Settings/Local Folders, and note the location of the Local directory. That’s where all your local Thunderbird mail (and the associated databases) is stored.
Close Thunderbird and, using Windows Explorer, navigate to the Local directory’s folder. Have a look; you should see files and folders there that match the folders you’re used to seeing in Thunderbird.
The files with no file extension (e.g., the inbox file) are the actual Thunderbird message stores. Any similarly named folders with the .mozmsgs extension (e.g., inbox.mozmsgs) contain duplicate copies of the messages. These copies are used for full-text indexing.
Search those files and folders for your missing messages. Thunderbird stores e-mail as plain text, so you can drag any file to Notepad to view its contents. (If the message is formatted, you’ll also see the plain-text HTML formatting commands.)
It’s neither fun nor fast to recover lost messages this way, but if the lost messages still exist, that’s where and how you can find them.
And by the way, Thunderbird development is winding down. Version 15 was just released, and there are additional upgrades in the pipeline that will bring Thunderbird to Version 17. But that’s the end of the line for this classic mail client.
As stated in MozillaWiki:
- “Mozilla is focusing a lot of its efforts towards important web and mobile projects, while Thunderbird remains a pure desktop only e-mail client. We have come to the conclusion that continued innovation on Thunderbird is not a priority for Mozilla ….”
Thunderbird is still current and good (I use it!), but its days are numbered. It’s time for Thunderbird users to start thinking about an alternative.
A Windows update locks up laptop during install
John Willoughby’s PC is stuck in a Windows Update Twilight Zone.
- After [my attempt to install the July] Windows updates on my Vista laptop, a loop started that has made the machine unusable. It stops at the point: ‘Configuring Updates, stage 1 of 3, 0% complete, do not turn off your computer.’
“It has continued to show that message ever since, never going further. I’ve tried System Repair using my installation CD and many other ways. Nothing works; it continues in this loop. I would appreciate any advice I can get about how to break the loop.”
The first question I have to ask: Did you try rolling the system back to a restore point created before the appearance of the trouble? That, or restoring a backup or system image from a pre-trouble date, is the best way to go.
If that’s not possible, there are several other options available.
For example, a Microsoft Answers item, “Stuck on ‘configuring updates stage 3 of 3, 0% complete,'” describes a scenario that’s almost identical to your situation. Microsoft gives three approaches to solving the problem.
More generically, MS Support article 971058, “How do I reset Windows Update components?,” might also help you get out of the loop.
Some users report successfully beating a malfunctioning Windows Update back into submission by using the “System Update Readiness Tool.” See Support article 947821.
Surely one of these five approaches — or simply restoring an image or backup or system restore point that predates the trouble — will help get you going again!
OK to put rapidly changing data on an SSD?
David Horwood wonders about the life expectancy of his SSD.
- “I’m about to put Win7 on a new SSD installed in an older PC. I have not bought an SSD yet so don’t know what instructions they come with.
“What do you recommend for Eudora’s mailboxes and other frequently changing application data? Under Win7, Eudora’s Roaming data sub-folder is on the C: drive [by default.] But is that a wise choice with an SSD?”
The admonitions you’ve read about SSD lifespan apply mainly to totally unnecessary (essentially abusive) operations such as defragging. (There’s no point in defragging an SSD — it has no mechanical moving parts.) Win7 knows about SSDs and automatically avoids this kind of needless wear and tear. You won’t have to do any special configuration changes to get a full, normal lifespan from your new drive.
Besides, hardware is meant to be used! The whole point of having an SSD is to take advantage of its inherent speed, which is most apparent in applications with a lot of rapidly changing data. In my case, I omitted nothing from my SSD. Everything I used to have on my magnetic C: drive is now on my SSD C: drive — no changes at all.
So I suggest you set up your SSD in a completely normal way, with your files and folders in their default locations. No special tweaks or adjustments are needed with Win7.
And trust me: you’re gonna love the speed!
Always good advice: Check your settings!
A Lounge member voices a frequent complaint about e-mail messages: incoming e-mail fonts are too small!
Not Brightest Bulb (self-styled) is stymied by his investigation of Thunderbird settings. He simply wants Thunderbird to use a normal font size for incoming mail. Fortunately, other Lounge members have been researching the problem, too. See their helpful suggestions.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right in to today’s discussions in the Lounge.
A new operating system, a new round of patches
On an unusually light Patch Tuesday, Windows 7 gets three nonsecurity updates and Windows 8 gets its first patch.
But Microsoft is scrambling to add Flash updating to Windows 8 in order to protect the newly released platform.
2751352
Problems with tiles, and a Flash update to come
Windows 8 is barely out of RTM and already has an update for its user interface. KB 2751352 fixes an issue with Win8 tiles when using the “All Apps View.” Microsoft states that All Apps View is not updating a cache correctly when you change a tile’s file-type association.
That’s a minor problem, compared to updating Adobe Flash in Windows 8. Although Windows 7 users can download the latest Adobe Flash update (site) on their own, Win8’s Internet Explorer 10 has Flash embedded. That means Microsoft must provide any Flash updates for IE 10. Until that happens, the browser is vulnerable.
As noted in a ZDNet blog, Microsoft plans to release the needed update “shortly.” If you’ve already taken the Windows 8 plunge, it might be good to download another browser.
 What to do: Windows 8 users should install KB 2751352 and be on the lookout for the upcoming Flash update. I’ll discuss Windows 8 patching in an upcoming article.
What to do: Windows 8 users should install KB 2751352 and be on the lookout for the upcoming Flash update. I’ll discuss Windows 8 patching in an upcoming article.
2719857, 2735855, 2741355
Three nonsecurity updates for Windows 7
As is its unfortunate habit of late, Microsoft has released a few nonsecurity updates on Patch Tuesday. As regular Patch Watch readers know, I don’t approve of mixing together nonsecurity and security updates — it just makes the process of installing and testing critical security patches more difficult. However, September’s Patch Tuesday has so few security patches, I’m okay with tackling the following nonsecurity updates now rather than at the end of the month.
KB 2719857 fixes a conflict between Windows 7 and USB-based, 3G/4G wireless networking devices using Remote Network Driver Interface Specification (RNDIS). The problem is obvious: you can’t connect to a 3G or 4G network. I have one of these devices, and it’s never had a problem connecting to the Internet. I installed the patch anyway, and I didn’t run into any problems with it.
KB 2735855 is a hotfix for Windows Filtering Platform (WFP) applications. Microsoft’s description for this update is cryptic, but apparently you can apply the hotfix if your network connection is slow when running a WFP-based app with Windows 7.
Scratching your head over what, exactly, Windows Filtering Platform is? Apps that use WFP have a much more familiar name — firewalls! As defined in an MSDN article, WFP is an API (Wikipedia definition) used by Microsoft and third-party firewall developers. It’s prudent to be extra cautious with code that interacts with third-party firewalls, so I’m putting this update on hold for now. Any reports of problems with the patch should show up in the next couple of weeks.
KB 2741355 repairs a startup problem with Windows Live Movie Maker 2012. The flaw is limited to PCs running Windows 7 (or Windows Server 2008 R2) and graphic cards that support DirectX 9 only. If you don’t use Movie Maker, you can skip this update.
 What to do: Windows 7 users will probably see both KB 2719857 and KB 2741355 offered. It probably can’t hurt to install them, whether they’re needed immediately or not. Hold on KB 2735855 until I report back.
What to do: Windows 7 users will probably see both KB 2719857 and KB 2741355 offered. It probably can’t hurt to install them, whether they’re needed immediately or not. Hold on KB 2735855 until I report back.
MS12-061 (2719584), MS12-062 (2721642, 2733631)
Two updates most WS readers will never see
The only true security updates this month are for two applications I’ll bet few Windows Secrets readers have.
MS12-061 contains a patch for Team Foundation Server 2010 Service Pack 1, a Microsoft product used to build software. The vulnerability itself is the relatively pedantic “elevation of privileges” that can occur only if a user running Team Foundation Server 2010 SP1 clicks an unfamiliar website or instant-message link.
The patch in MS12-062 fixes a vulnerability in System Center Configuration Manager, a Web portal used to manage multiple servers. The method of attack is essentially the same as with the Team Foundation exploit — which is why both updates are rated important.
 What to do: If you’re offered KB 2719584 (MS12-061) or KBs 2721642, 2733631 (MS12-062), by all means install them.
What to do: If you’re offered KB 2719584 (MS12-061) or KBs 2721642, 2733631 (MS12-062), by all means install them.
2736233
Killing off a few more ActiveX controls
Periodically, Microsoft sends out an update with ActiveX kill bits. As defined in a Wikipedia page, a kill bit “instructs an ActiveX control container never to use a specific piece of ActiveX software, whether third-party or Microsoft ….” ActiveX controls are flagged with kill bits when they’re found to have security vulnerabilities.
The kill bits in this update disable three Cisco apps: Secure Desktop, Host Scan, and AnyConnect Secure Mobility Client.
 What to do: If you use any of these programs, install KB 2736233 and look for updates from Cisco. I recommend installing the update even if you don’t need it because you might have the controls on your system and not know it.
What to do: If you use any of these programs, install KB 2736233 and look for updates from Cisco. I recommend installing the update even if you don’t need it because you might have the controls on your system and not know it.
2743314
New exploit targets wireless/VPN connections
When on the road or working from home, many of you probably connect to your offices using Virtual Private Networking (VPN). If those connections frequently originate from public wireless hotspots, I recommend printing out MS Security Advisory 2743314 and handing it to the IT person who manages your VPN configuration. Ask him or her whether you’re using Microsoft Challenge Handshake Authentication Protocol Version 2 (MS-CHAP v2) with Point-to-Point Tunneling Protocol (PPTP). That particular configuration is vulnerable to exploitation by malicious hackers.
According to the advisory, Microsoft doesn’t know of any actual attacks, and there’s no patch yet. But the advisory does provide a couple of workarounds. (Apparently, it’s unlikely there will be a patch, due to the age of the MS-CHAP v2 protocol and because there are newer alternatives.)
One clue to tell whether you’re using MS-CHAP v2 and PPTP: Your VPN connection is using port 1723. The vulnerability in MS-CHAP v2 leaves users open to a man-in-the-middle attack, giving potential attackers access to your VPN credentials.
There’s probably no immediate threat from this exploit. In fact, it’s much easier for cyber criminals to simply call someone in your office and trick them into handing over passwords (or trick you into downloading a malicious e-mail).
To ensure its upcoming Windows Server 2012 Essentials (WSE) isn’t affected by the vulnerability, Microsoft published instructions for setting up DirectAccess — a replacement for VPN. A related article by Robert Pearman discusses how to set up VPN in WSE without using port 1723 but instead using Secure Socket Tunneling Protocol.
 What to do: A small threat is still a threat. Determine whether your VPN connection is using MS-CHAP v2. And if it is, have your IT department make the changes needed to fully secure your remote access.
What to do: A small threat is still a threat. Determine whether your VPN connection is using MS-CHAP v2. And if it is, have your IT department make the changes needed to fully secure your remote access.
Regularly updated problem-patch chart
This table provides the status of problem patches reported in previous Patch Watch columns. Patches listed below as safe to install will be removed from the next updated table. For Microsoft’s list of recently released patches, go to the MS Safety & Security Center PC Security page.
| Patch | Released | Description | Status |
|---|---|---|---|
| 2686509 | 05-08 | Kernel Mode Driver; install issues on XP (updated status) | Skip |
| 2699779 | 06-12 | Office 15 installation fix (updated status) | Skip |
| 2709630 | 06-12 | Network domain sign-in delays (updated status) | Skip |
| 2719584 | 09-11 | Team Foundation Server 2010 SP1 | Skip |
| 2741528 | 09-11 | System Center Configuration Manager (server app) | Skip |
| 2553272 | 08-14 | Office 2010 stability/performance fixes | Wait |
| 2598289 | 08-14 | Office 2010 stability/performance fixes | Wait |
| 2647753 | 08-14 | Win7 printing-core components rollup | Wait |
| 2661254 | 08-14 | Minimum certificate key length | Wait |
| 2735855 | 09-11 | Windows Filtering Platform: potential third-party firewall impact | Wait |
| 2729094 | 08-14 | Segoe UI symbol font in Win7 | Optional |
| 2732487 | 08-14 | Win7 sleep mode hotfix | Optional |
| 890830 | 08-14 | Monthly update of the MS Windows Malicious Software Removal Tool | Install |
| 2706045 | 08-14 | JScript and VBScript; 64-bit system only | Install |
| 2720573 | 08-14 | MS Office and SQL Server ActiveX controls; see MS12-060 for complete patch list | Install |
| 2722913 | 08-14 | Cumulative IE security update | Install |
| 2723135 | 08-14 | XP SP3 Remote Desktop | Install |
| 2731847 | 08-14 | Windows kernel-mode drivers | Install |
| 2731879 | 08-14 | MS Office CGM graphics files; see MS12-057 for complete patch list | Install |
| 2732500 | 08-14 | Win7 System Restore failures after updates | Install |
| 2733594 | 08-14 | Windows networking components; KB 2705219 and KB 2712808 | Install |
| 2733918 | 08-14 | MS Visio 2010 SP1 (KB 2597171) and Visio Viewer 2010 SP1 (KB 2598287) | Install |
| 2740358 | 08-14 | MS Exchange Server; see MS12-058 for complete patch list | Install |
| 2719857 | 09-11 | Windows 7/USB wireless-connection fix | Install |
| 2741355 | 09-11 | Windows Live Movie Maker 2012; install if offered | Install |
| 2751352 | 09-11 | Windows 8 user interface fix | Install |
Status recommendations: Skip — patch not needed; Hold — do not install until its problems are resolved; Wait — hold off temporarily while the patch is tested; Optional — not critical, use if wanted; Install — OK to apply.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Outdated Laptop
by
jdamkeene
2 hours, 48 minutes ago -
Updating Keepass2Android
by
CBFPD-Chief115
5 hours, 9 minutes ago -
Another big Microsoft layoff
by
Charlie
4 hours, 49 minutes ago -
PowerShell to detect NPU – Testers Needed
by
RetiredGeek
4 hours, 38 minutes ago -
May 2025 updates are out
by
Susan Bradley
5 hours, 14 minutes ago -
Windows 11 Insider Preview build 26200.5600 released to DEV
by
joep517
10 hours, 53 minutes ago -
Windows 11 Insider Preview build 26120.3964 (24H2) released to BETA
by
joep517
10 hours, 55 minutes ago -
Drivers suggested via Windows Update
by
Tex265
10 hours, 46 minutes ago -
Thunderbird release notes for 128 esr have disappeared
by
EricB
8 hours, 30 minutes ago -
CISA mutes own website, shifts routine cyber alerts to X, RSS, email
by
Nibbled To Death By Ducks
17 hours, 46 minutes ago -
Apple releases 18.5
by
Susan Bradley
12 hours, 11 minutes ago -
Fedora Linux 40 will go end of life for updates and support on 2025-05-13.
by
Alex5723
19 hours, 12 minutes ago -
How a new type of AI is helping police skirt facial recognition bans
by
Alex5723
19 hours, 49 minutes ago -
Windows 7 ISO /Windows 10 ISO
by
ECWS
3 hours, 5 minutes ago -
No HP software folders
by
fpefpe
1 day, 3 hours ago -
Which antivirus apps and VPNs are the most secure in 2025?
by
B. Livingston
50 minutes ago -
Stay connected anywhere
by
Peter Deegan
1 day, 8 hours ago -
Copilot, under the table
by
Will Fastie
1 day ago -
The Windows experience
by
Will Fastie
1 day, 15 hours ago -
A tale of two operating systems
by
Susan Bradley
1 day, 6 hours ago -
Microsoft : Resolving Blue Screen errors in Windows
by
Alex5723
1 day, 20 hours ago -
Where’s the cache today?
by
Up2you2
2 days, 11 hours ago -
Ascension says recent data breach affects over 430,000 patients
by
Nibbled To Death By Ducks
2 days, 4 hours ago -
Nintendo Switch 2 has a remote killing switch
by
Alex5723
1 day, 4 hours ago -
Blocking Search (on task bar) from going to web
by
HenryW
7 hours, 7 minutes ago -
Windows 10: Microsoft 365 Apps will be supported up to Oct. 10 2028
by
Alex5723
3 days, 5 hours ago -
Add or Remove “Ask Copilot” Context Menu in Windows 11 and 10
by
Alex5723
3 days, 5 hours ago -
regarding april update and may update
by
heybengbeng
3 days, 6 hours ago -
MS Passkey
by
pmruzicka
2 days, 8 hours ago -
Can’t make Opera my default browser
by
bmeacham
3 days, 14 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.


