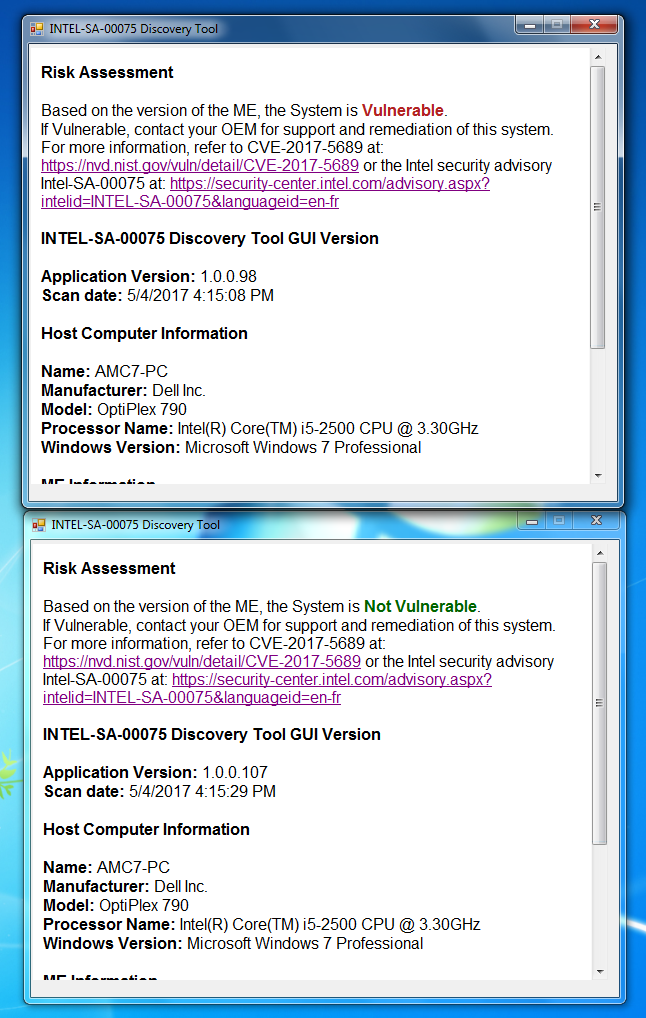
Intel Active Management Technology, Intel Small Business Technology, and Intel Standard Manageability Escalation of Privilege
Intel ID: INTEL-SA-00075
Product family: Intel® Active Management Technology, Intel® Small Business Technology, and Intel® Standard Manageability
Impact of vulnerability: Elevation of Privilege
Severity rating: Critical
Original release: May 01, 2017
Last revised: May 19, 2017
Summary:
There is an escalation of privilege vulnerability in Intel® Active Management Technology (AMT), Intel® Standard Manageability (ISM), and Intel® Small Business Technology versions firmware versions 6.x, 7.x, 8.x 9.x, 10.x, 11.0, 11.5, and 11.6 that can allow an unprivileged attacker to gain control of the manageability features provided by these products. This vulnerability does not exist on Intel-based consumer PCs. This vulnerability does not exist on Intel-based consumer PCs with consumer firmware, Intel servers utilizing Intel® Server Platform Services (Intel® SPS), or Intel® Xeon® Processor E3 and Intel® Xeon® Processor E5 workstations utilizing Intel® SPS firmware.
For general guidance on this issue please see https://newsroom.intel.com/news/important-security-information-intel-manageability-firmware/
As Intel becomes aware of computer maker schedules for updated firmware this list will be updated:
HP Inc. – http://www8.hp.com/us/en/intelmanageabilityissue.html
HP Enterprise – http://h22208.www2.hpe.com/eginfolib/securityalerts/CVE-2017-5689-Intel/CVE-2017-5689.html
Lenovo – https://support.lenovo.com/us/en/product_security/LEN-14963
Fujitsu – http://support.ts.fujitsu.com/content/Intel_Firmware.asp
Dell Client – http://en.community.dell.com/techcenter/extras/m/white_papers/20443914
Dell EMC – http://en.community.dell.com/techcenter/extras/m/white_papers/20443937
Acer – https://us.answers.acer.com/app/answers/detail/a_id/47162
Asus – https://www.asus.com/News/uztEkib4zFMHCn5r
Panasonic – http://pc-dl.panasonic.co.jp/itn/info/osinfo20170512.html
Toshiba – https://support.toshiba.com/sscontent?contentId=4015668
Intel – NUC, Compute Stick and Desktop Boards
Description:
There are two ways this vulnerability may be accessed please note that Intel® Small Business Technology is not vulnerable to the first issue.
An unprivileged network attacker could gain system privileges to provisioned Intel manageability SKUs: Intel® Active Management Technology (AMT) and Intel® Standard Manageability (ISM).
CVSSv3 9.8 Critical /AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
An unprivileged local attacker could provision manageability features gaining unprivileged network or local system privileges on Intel manageability SKUs: Intel® Active Management Technology (AMT), Intel® Standard Manageability (ISM), and Intel® Small Business Technology (SBT).
CVSSv3 8.4 High /AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Affected products:
The issue has been observed in Intel manageability firmware versions 6.x, 7.x, 8.x 9.x, 10.x, 11.0, 11.5, and 11.6 for Intel® Active Management Technology, Intel® Small Business Technology, and Intel® Standard Manageability. Versions before 6 or after 11.6 are not impacted.
Read the full article here