In recent years, companies have been implementing various levels of encryption within their apps and services. ProtonMail offers encryption between its mail users, WhatsApp has encryption turned on by default, and Facebook Messenger lets you flip to more secure chats if you would like. While not the most straightforward to set up, Mozilla has tightly integrated PGP into its e-mail client Thunderbird, so you can encrypt e-mails, no matter your provider.
In this guide, I’ll go over:
How to set up your encryption keys
How to add your contact’s keys
How to share your own keys
How to upload your keys to a keyserver, so they can be found easily
How to backup your keys..

|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
How to set up end-to-end encryption for your e-mails in Mozilla’s Thunderbird
Home » Forums » Cyber Security Information and Advisories » Code Red – Security/Privacy advisories » How to set up end-to-end encryption for your e-mails in Mozilla’s Thunderbird
- This topic has 7 replies, 3 voices, and was last updated 2 years, 9 months ago.
AuthorTopicAlex5723
AskWoody PlusAugust 18, 2022 at 1:22 pm #2471127Viewing 5 reply threadsAuthorReplies-
OscarCP
MemberAugust 18, 2022 at 3:30 pm #2471144A problem, I find, with encrypting one’s emails, is that it works only if sent to people who can decrypt them. And not everybody even knows about encrypted emails.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV1 user thanked author for this post.
-
Alex5723
AskWoody PlusAugust 19, 2022 at 5:12 am #2471240A problem, I find, with encrypting one’s emails, is that it works only if sent to people who can decrypt them. And not everybody even knows about encrypted emails.
You don’t encrypt every mail sent. You should encrypt only important/confidential mail like : to your bank, workplace, lawyer, doctor.. to them you should send a ‘public key’.
..How to share your own keys
To send your public key to a contact, head back into the OpenPGP Key Manager and right-click your key. You should then see an option to send your public key by e-mail, pressing this will open up a new compose window with your key attached. To import this, your recipient just needs to open their key manager, press File and import the public key from the file…
1 user thanked author for this post.
-
Fred
AskWoody LoungerAugust 19, 2022 at 2:18 pm #2471347—–BEGIN PGP SIGNED MESSAGE—–
Hash: SHA512~~~~~~
You can verify this text for authenticity by original signer.
Encryption techniques are nice, but not easy.
Microsoft also makes many mistakes in the digital signing of their
messages;Who oh who cares?
I do.~~~~~~
—–BEGIN PGP SIGNATURE—–
Version: Encryption Desktop 10.5.0 (Build 1520)
Comment: PGP_10.5.0 MP1 [Build 1520],Secured
Charset: utf-8wsFVAwUBYv/gYrY5OeMN8SSAAQqLohAAvqKDV2lNr7Ss8i6RrUGERLbDmXIzjjP8
Lre8SOhyBMIsoqKuGvo0NdZltywW5q4G5MSpG/87aSmw3ZZtFAfjP10jP9gzTGdk
jhp+nlKh/F5GTZt18hxGfA2TAaVd9RyRh16aAJfUyLpPX/AMI2o74mySuxNFhSlF
oZoRcHjCSVR9RU1UGsQQvdKTdD6314Trz/T9wfEyoZKYqg8V6TJ3wcJ9ngHfyYJl
Nh4PhkDN1P0YA+3jjTVaOqoVB8BqhoEHwSjDAmFEU4SmOfN3Zn/WfdqOLo9wNwYa
W8pzLfoC2tZBaPrzJFdL/f7YDHc9s61UPy0mO+CmpEguFEl95sCj2zJXpD8CP+oq
AYKRkhy+FRpt5Z6M7Dj81CjggUYjB6QzTjE9YmmKsgf7iGUdFFrT9RCBQG7RTbAv
WgkD3TmFhz3Gak2zDYLaj51jze2p2VeeoUzPnTYwthF2ypERmXVwmYkVem7IjJ/7
QEDcCXj0Ar72TLsKqVaEKen9HbnQ+WMSoWpFl7eD+IXrw6pmiOsikRTAon3mdKPE
BZLhQ8da2QlUqp/Qz9K3NvTk/QaXN7FSx3TMRBsZqSnVans9HO/+ZhsxggcbDulu
gtkw5vH6/i7/CGqito+rVTB9M+TRMGxl524yLp7luEnZhlMMw+VFnvvpoxLtDkrf
YsrnE6HSozE=
=H9pm
—–END PGP SIGNATURE—–* _ ... _ * -
OscarCP
MemberAugust 19, 2022 at 5:46 pm #2471395Fred, Thanks.
Am I guessing right that the long and seemingly random sequence of characters is the encrypted PGP public key?
https://www.varonis.com/blog/pgp-encryption
Quote: “ProtonMail – like most email clients that offer PGP – hides all of the complexity of the encryption and decryption of the message. If you are communicating to users outside of ProtonMail, you need to send them your public key first. “
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV
-
Fred
AskWoody LoungerAugust 19, 2022 at 10:57 pm #2471456OscarCP y’re welcome:
In the message is everything beginning from —–BEGIN PGP to —–END PGP SIGNATURE—– is the with PGP signed message. The actual message is in the middle between the tilde-lines that I started and ended the message with, just to make it a bit more readable:~~~~~~
…..
…..
~~~~~~So and thus, if there is a single letter and/or space within the mesage altered than this message does not check out to be with a good signature and thus not to be original, like the picture of the pgp-check shows that this case is original.
My original text was signed with my PGPkey. This key consists of two parts: a private part and a public part. The private part of the this key is very secret and only in my possession, and the public part can be sent to somebody else, or to a (public-key) server on the internet, this usually is called a PGP-publickey-server.
Everybody who has anough of my cridentials can collect/download this publickey. Knowing the PGP-ID of somebody is anough to collect this publickey, in this case my “PGP-ID=(0x0DF12480)”.
((to make it a bit more complicated: anybody having the fingerprint of my PGPkey can collect this publickey too; in this case this accompanying fingerprint is “970A 5D81 27BD 73F9 5EB4 4139 B639 39E3 0DF1 2480”. So when I hand over to somebody this PGP-ID or this PGPkey-fingerprint he can collect my publicPGPkey and can check this text to be original or not.But never ever forget:
This whole system of encryption is based on a single trust of WHO keeps the PrivateKey , that is very easyly forgotten.This message was only encrypted to my PGPkey, so the result is clearly visible.
When I encrypt this message to an other publickey from somebody else, than this message can only be decrypted by the owner of the other privatekey(s), and now the result is very scrambled with various signs.herewith the example of the oversight of my PGPkeypair:
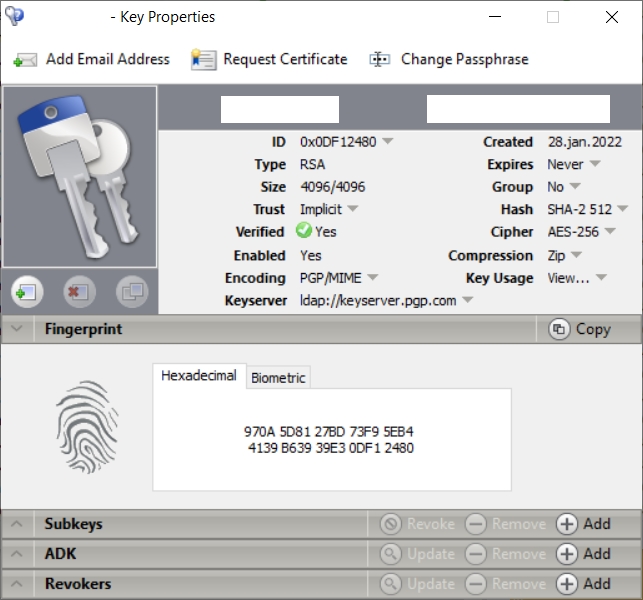
((for obvious reasons I blancked-out a few parts))
Using Protonmail or anything like it is based on this “simple principle”, and is a bit more user-friendly 😀
.
* _ ... _ *Fred
AskWoody LoungerAugust 19, 2022 at 11:22 pm #2471462Quote: “ProtonMail – like most email clients that offer PGP – hides all of the complexity of the encryption and decryption of the message. If you are communicating to users outside of ProtonMail, you need to send them your public key first. “
Using Protonmail in a good and smooth way, it’s always best that the receiving party is using Protonmail too, and than all the encryption behind the surface is done automaticly correct.
Using Thunderbird and mobilephone-email with Encryption-keys is very well possible, but not always that smoothly. The internet ‘tends to be very flexible’, as Microsoft learns us all day round with their updates.ps: There are much more encrypted-email-services, but remember: WHO keeps the PrivateKeys, and in what jurisdiction?.
pps: Who has nothing to hide, who cares?
.
* _ ... _ *Fred
AskWoody LoungerAugust 19, 2022 at 11:35 pm #2471465The text in this quoted internet link is not quite true, about the part of being unbrakeable encryption. For that there is much more to be done to give the NSA or the x-Eyes-Aliance a hard time to break it.
Ofcourse Quantum-computing is expected to bring this type of encrypting to an end, eventually new techniques must be invented; or is that already there?* _ ... _ *Viewing 5 reply threads -

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
MS Office 365 Home on MAC
by
MickIver
1 hour, 36 minutes ago -
search by picture an not all that’s cracked up to be (Awaiting moderation)
by
Dru Fuksa
6 hours, 34 minutes ago -
Google’s Veo3 video generator. Before you ask: yes, everything is AI here
by
Alex5723
13 hours, 39 minutes ago -
Flash Drive Eject Error for Still In Use
by
J9438
15 hours, 12 minutes ago -
Windows 11 Insider Preview build 27863 released to Canary
by
joep517
1 day, 8 hours ago -
Windows 11 Insider Preview build 26120.4161 (24H2) released to BETA
by
joep517
1 day, 8 hours ago -
AI model turns to blackmail when engineers try to take it offline
by
Cybertooth
12 hours, 11 minutes ago -
Migrate off MS365 to Apple Products
by
dmt_3904
13 hours ago -
Login screen icon
by
CWBillow
3 hours, 22 minutes ago -
AI coming to everything
by
Susan Bradley
10 hours, 58 minutes ago -
Mozilla : Pocket shuts down July 8, 2025, Fakespot shuts down on July 1, 2025
by
Alex5723
2 days ago -
No Screen TurnOff???
by
CWBillow
2 days ago -
Identify a dynamic range to then be used in another formula
by
BigDaddy07
2 days, 1 hour ago -
InfoStealer Malware Data Breach Exposed 184 Million Logins and Passwords
by
Alex5723
2 days, 12 hours ago -
How well does your browser block trackers?
by
n0ads
1 day, 23 hours ago -
You can’t handle me
by
Susan Bradley
22 hours, 58 minutes ago -
Chrome Can Now Change Your Weak Passwords for You
by
Alex5723
1 day, 15 hours ago -
Microsoft: Over 394,000 Windows PCs infected by Lumma malware, affects Chrome..
by
Alex5723
3 days ago -
Signal vs Microsoft’s Recall ; By Default, Signal Doesn’t Recall
by
Alex5723
2 days, 3 hours ago -
Internet Archive : This is where all of The Internet is stored
by
Alex5723
3 days ago -
iPhone 7 Plus and the iPhone 8 on Vantage list
by
Alex5723
3 days ago -
Lumma malware takedown
by
EyesOnWindows
2 days, 12 hours ago -
“kill switches” found in Chinese made power inverters
by
Alex5723
3 days, 9 hours ago -
Windows 11 – InControl vs pausing Windows updates
by
Kathy Stevens
3 days, 9 hours ago -
Meet Gemini in Chrome
by
Alex5723
3 days, 13 hours ago -
DuckDuckGo’s Duck.ai added GPT-4o mini
by
Alex5723
3 days, 13 hours ago -
Trump signs Take It Down Act
by
Alex5723
3 days, 21 hours ago -
Do you have a maintenance window?
by
Susan Bradley
2 days, 2 hours ago -
Freshly discovered bug in OpenPGP.js undermines whole point of encrypted comms
by
Nibbled To Death By Ducks
2 days, 23 hours ago -
Cox Communications and Charter Communications to merge
by
not so anon
4 days ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

