Microsoft just released another patch for Win10 Creators Update. KB 4016240 brings the 1703 build number up to 15063.250. That’s quite normal for a ne
[See the full post at: Just when you thought it couldn’t get any more complicated, Creators Update gets a new kind of patch, KB 4016240]

|
Patch reliability is unclear, but widespread attacks make patching prudent. Go ahead and patch, but watch out for potential problems. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
Just when you thought it couldn’t get any more complicated, Creators Update gets a new kind of patch, KB 4016240
Home » Forums » Newsletter and Homepage topics » Just when you thought it couldn’t get any more complicated, Creators Update gets a new kind of patch, KB 4016240
- This topic has 26 replies, 11 voices, and was last updated 7 years, 12 months ago.
Tags: 15063.250 KB 4016240
AuthorTopicwoody
ManagerApril 25, 2017 at 2:09 pm #110871Viewing 5 reply threadsAuthorReplies-
NetDef
AskWoody_MVPApril 25, 2017 at 2:48 pm #110889It’s geared towards larger organizations that use WSUS or WUFB, not to the clients that take updates directly from Microsoft Updates.
This gives system admins a bit more granularity on which classification of updates to accept for their networks month to month. (I was one of the admins that requested this feature for business networks.)
So: Now we can choose only security updates, only critical updates, or feature updates separately and on separate schedules. For example with this separation — I can allow criticals the day they are released, feature updates a month later, and security updates the week (say – Friday evening) they are released.
~ Group "Weekend" ~
4 users thanked author for this post.
-
thymej
AskWoody Lounger -
Kirsty
ManagerApril 26, 2017 at 1:49 am #111061
1 user thanked author for this post.
-
thymej
AskWoody LoungerApril 26, 2017 at 4:07 pm #111281 -
woody
ManagerApril 26, 2017 at 5:06 pm #111300I’m still trying to figure out how this works but based on what I’ve seen, the intent is to have two types of updates:
Non-security patches (described as “cumulative” but I don’t believe it)
Monthly cumulative updates
If that’s the case, some of what’s being said makes sense. But some doesn’t. 🙂
Far as I can tell, that’s the way Win10 has always been patched. There may be changes in the “Optional” flag for update servers, but for regular people, I don’t see how anything has changed. (And even if the “Optional” flag is set, I don’t understand how that will benefit admins. But maybe I’m just not looking at it the right way.)
1 user thanked author for this post.
-
-
-
-
-
woody
ManagerApril 26, 2017 at 12:13 pm #111200This gives system admins a bit more granularity on which classification of updates to accept for their networks month to month.
More details, please! I see where the Win7 patching method of separating Security-only and Monthly Rollup patches help with WSUS. But I don’t understand how this combination of Non-Security-Only and Monthly Rollup helps.
Are the Non-Security-Only patches really cumulative? Or is that a typo?
Thanks!
1 user thanked author for this post.
-
NetDef
AskWoody_MVPApril 27, 2017 at 11:36 pm #111580This gives system admins a bit more granularity on which classification of updates to accept for their networks month to month.
More details, please! I see where the Win7 patching method of separating Security-only and Monthly Rollup patches help with WSUS. But I don’t understand how this combination of Non-Security-Only and Monthly Rollup helps. Are the Non-Security-Only patches really cumulative? Or is that a typo? Thanks!
My understanding is they are cumulative, and are likely analogous to the Preview early patches for the current release builds. (My understanding may not be 100% how MS would like to present them.)
The major value is we can test on a subset of our domain workstations before they are released, again much like preview, but for WSUS management.
I am not at all certain you would see these patches outside a managed update environment.
It’s worth noting that the Preview ring is not an option for machines joined to a WSUS managed network, which means for us to test that ring we have to have stand-alone workstations – which invalidates (IMO) the testing.
So in short, I <span style=”text-decoration: underline;”>think </span>what we are seeing is a WSUS friendly workaround for the Preview Ring.
~ Group "Weekend" ~
2 users thanked author for this post.
-
ch100
AskWoody_MVPApril 28, 2017 at 4:10 am #111596I am not at all certain you would see these patches outside a managed update environment.
I believe that the current non-security CU is released to the common Windows Update, outside of WSUS.
There may be a good reason for this behaviour, which is the classification of the current update as Critical Update instead of the more commonly intended Update.2 users thanked author for this post.
-
-
VulturEMaN
AskWoody LoungerApril 25, 2017 at 5:25 pm #110936Always give Michael Niehaus the benefit of the doubt at MS – he’s one of the few people that gets it and is really trying to refine the way that we do patching and general OS management. He created MDT, was instrumental with nano server, etc etc.
With this change adding all of the granularity for the Enterprise folks, this should resolve a bunch of issues on the enterprise WSUS end of things for patch management.
-
woody
ManagerApril 26, 2017 at 7:06 am #111116Totally agreed. In my book, Neihaus is one of the good guys. But he could benefit from a tough editor – one who questions what’s being communicated. Many of his posts don’t become clear until we’ve had a few months to gauge what they really say.
That isn’t a Neihaus problem. It’s a Microsoft problem.
1 user thanked author for this post.
Noel Carboni
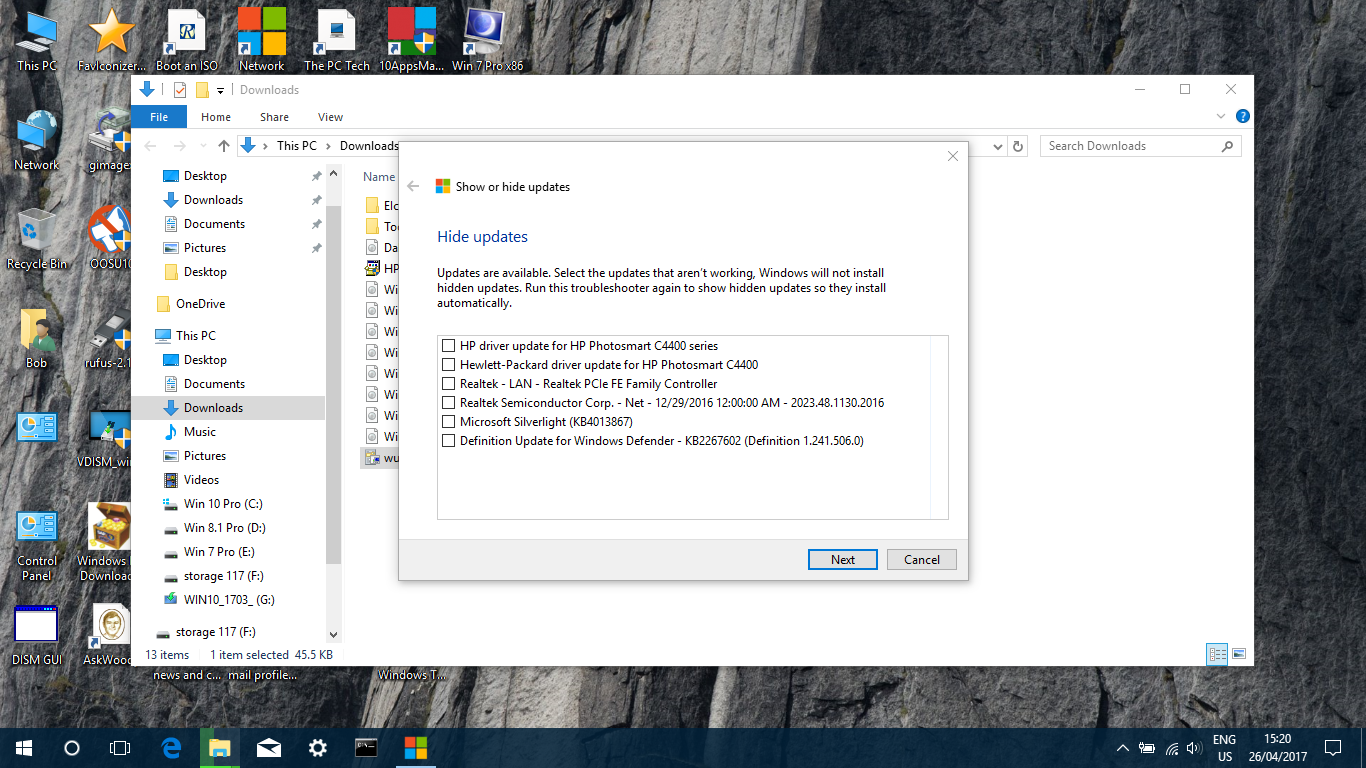
AskWoody_MVPApril 26, 2017 at 6:50 am #111110According to the WUShowHide tool on my Win 10 (15063.138) test system there are no available updates at this time for Win 10 Creators from the online Windows Update servers, so this update truly seems to be not yet available via the normal “public beta tester” means?
-Noel
2 users thanked author for this post.
-
BobbyB
AskWoody LoungerApril 26, 2017 at 7:02 am #111113didnt show on my WSUS show & Hide yesterday (only Dvrs) but it was there at approx 1400MST and as soon as you “Zero” the defer updates option and hit “check” it gets installed, You might want to hold off that one though my Win10Pro V1703 VHD has gone in to a real slow down since that update. Edge has stopped working like it should (no great loss there) not seen many other complaints on the web though it could be a one off on my VHD.
PS WSUS show & Hide didnt show a slew of office2016 updates that came with kb4016240 either “curious and curiouser”
1 user thanked author for this post.
-
woody
ManagerApril 26, 2017 at 7:19 am #111117According to the WUShowHide tool on my Win 10 (15063.138) test system there are no available updates at this time for Win 10 Creators from the online Windows Update servers
didnt show on my WSUS show & Hide yesterday (only Dvrs) but it was there at approx 1400MST and as soon as you “Zero” the defer updates option and hit “check” it gets installed,
I’ve got it on my test machine. Noel, any chance you have the update blocked?
2 users thanked author for this post.
-
Noel Carboni
AskWoody_MVPApril 26, 2017 at 10:15 am #111161Thanks.
There is a chance I’ve riled up the update gods somehow. I did make a small router change last night having to do with multicast that could be affecting Windows networking.
It looks like the update servers are being contacted successfully, but something under the covers seems to be failing with an 0x80070426 error.
More investigation is in order.
-Noel
1 user thanked author for this post.
-
-
-
BobbyB
AskWoody LoungerApril 26, 2017 at 4:48 pm #111293Well further to the “Major slowdown” post kb4016240 install & using WSUS show & Hide. It would appear that if you have both updates deferred settings set in in Settings->updates ETC->Advanced panel then if you run WSUS show & Hide it wont show the update in waiting i.e. kb4016240.
Basically never got to the bottom of the “major slowdown” (press. of work & all that) running post uninstall DISM clean up, restore health returns an error outlined here
http://borncity.com/win/2017/04/26/windows-10-v1703-fix-for-dism-error-0x800f081f/
I reapplied 15063 to the same VHD and sure as anything WSUS Show & Hide didnt pick up kb4016240 (see below) So it would appear that WSUS S&H cant be relied on if you have updates deferred. As for the slowdown never got to the bottom of it as removing the errant update didnt help at all. Probably to use WSUS S&H its better to use the GPedit setting to change the freq. of checking for windows updates, disable the defer setting temporarily then check.
May be they should change TGIF to TGIV (Thx Gdnss Its a Vhd 😉 )1 user thanked author for this post.
-
Noel Carboni
AskWoody_MVPApril 26, 2017 at 7:45 pm #111325I’ve just gotten my test system updated to 15063.250 via running KB4016240 from the catalog…
Can you describe the slowdown you saw in a bit more detail? So far I’m not seeing what appears to be a slowdown, but chances are I don’t do the same things you do with it.
I *DID* see the return of a lot of Apps that I had previously uninstalled. Good thing I have a re-tweaker script to undo that.
I need to poke around more in this version to see what else may have been reverted. Why does Microsoft make keeping up to date in Win 10 so difficult?
-Noel
1 user thanked author for this post.
-
BobbyB
AskWoody LoungerApril 26, 2017 at 8:20 pm #111332@Noel settings unesponsive 1-2 mins to open, windows explorer opening files in general same as, close button works a treat (which I ended up using quite a bit) The whole demeanur of the system as a whole seemed noticably slower.
Threw it in a VHD this time as opposed to VHDX of same size 45gb probably give that a try with kb4016420 later on. Stangely it fixed the remove lock screen which never worked from a “cold boot” i.e. displayed the login background whereas before from a “cold boot” you used to get the plain Blue screen.1 user thanked author for this post.
-
Noel Carboni
AskWoody_MVPApril 26, 2017 at 9:10 pm #111335Hm, Settings comes right up here.
I was able to figure out why the Apps came back and kept coming back after a reboot… The system was running the App Readiness service as though I was a new user all giggling and ready for all the great new Apps.
Thank Goodness THAT’s Disabled now.
-Noel
1 user thanked author for this post.
-
-
-
BobbyB
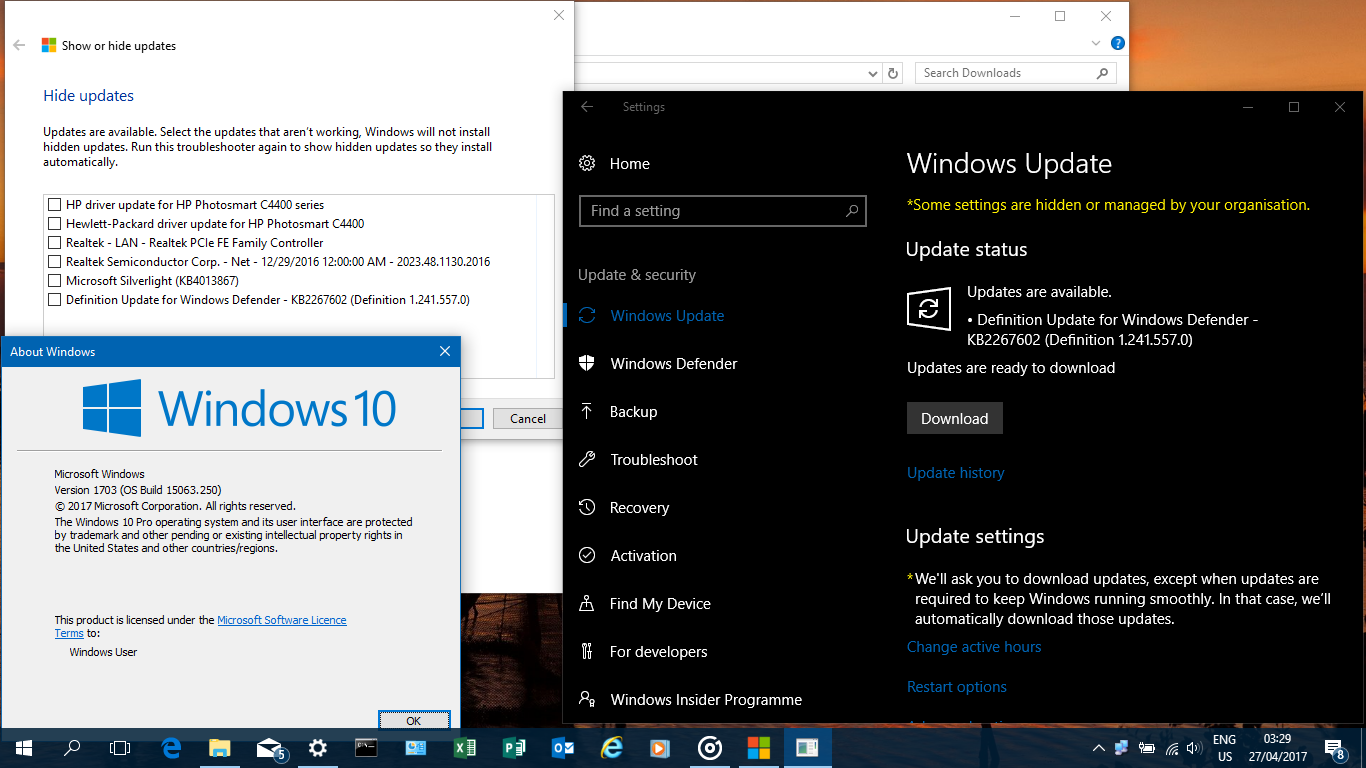
AskWoody LoungerApril 27, 2017 at 4:49 am #111392@Noel further to you comment above well threw it in a VHD and then installed kb4016240 from the desktop and “et voila” no problems. whether its a problem with the VHDX format or VHD who can tell? as I know there’s a couple more updates apparently lurking out there (KB402001/2) I tossed a screenshot in (yeah I have been known to sleep on occasion lol 😛 )
the office got updated or started updating while I was away from my desk as normally WSUS S&H will show them. theres a couple of links youve probably seen them but for anyone else following this it may be handy
https://www.ghacks.net/2017/04/25/microsoft-to-offer-more-updates-for-windows-10/
https://www.ghacks.net/2017/04/26/kb4020001-and-kb4020002-for-windows-10-1703-released/
I am getting the impression WSUS S&H may not be the solution to all but still a mega handy tool to be sure. Probably going to go back to using block driver updates using GPOL, thats if I decide to go “live” yet with 1703 after all its still early days and theres a lot of stuff, Data & settings to be redone. 🙁1 user thanked author for this post.
_Reassigned Account
AskWoody LoungerApril 26, 2017 at 7:04 am #111114I just succumb to the fact my PC is not my PC anymore. First Microsoft made the choice to roll everything into one update path and not allow anyone but enterprise to have control. Now Microsoft decides that separating non security updates from security updates is a good thing? Isn’t that pretty much what we had before? Does it really matter to the average home user who has updates forced on their systems anyway? At least its nicer to have stuff spread out than a big update once a month. I just will never accept the fact I have to endure whatever Microsoft dishes out if I want to run Windows.
1 user thanked author for this post.
-
woody
ManagerApril 26, 2017 at 7:30 am #111118As I understand it, this really doesn’t separate out security from non-security updates. It’s kind of like a mirror image of the current situation with Win7/8.1 updates. But then there’s the Preview ring (as opposed to Rollup Previews), and my brain does another roller coaster loop.
I’ll read up on it and see if I can pull something coherent out of it.
1 user thanked author for this post.
-
Noel Carboni
AskWoody_MVP
AJNorth
AskWoody PlusApril 26, 2017 at 11:37 am #111187To add to the Windows 10 mix, Ian Paul over at PC World has an article, published this morning, that is sure to stir things up, “Don’t install the Windows 10 Creators Update on your own, Microsoft advises (Wait for Windows Update to ensure your hardware works properly, Microsoft says)” – http://www.itnews.com/article/3192588/windows/dont-install-the-windows-10-creators-update-on-your-own-microsoft-advises.html .
1 user thanked author for this post.
anonymous
GuestMay 3, 2017 at 11:12 pm #112623KB4016240 messed with task view (ALT+TAB) previews and thumbnails on taskbar buttons.. https://answers.microsoft.com/en-us/windows/forum/windows_10-start/pixelated-images-in-task-switcher-after-update/0c52b3e9-ac13-433e-b261-468378473720
It’s just ridiculous that the experts at Microsoft break things that worked for ages, and then ship the junk without testing. It was an art of beauty, but the kindergardeners at Microsoft know how to break stuff..
-
Noel Carboni
AskWoody_MVPMay 4, 2017 at 12:54 am #112631Just imagine that they might be breaking “desktop” things on purpose to get users to like the desktop less and less. But slowly, so no one really notices.
I mean, there’s no comparison between a nicely themed desktop and the out-of-box Win 10 desktop. The system can do it – I have a nice theme. It’s pretty clear Microsoft just doesn’t want it to look nice any more.
You’re supposed to just want to sit in your favorite App all day.
-Noel
Viewing 5 reply threads -

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Tracking content block list GONE in Firefox 138
by
Bob99
1 hour, 19 minutes ago -
How do I migrate Password Managers
by
Rush2112
41 minutes ago -
Orb : how fast is my Internet connection
by
Alex5723
5 hours, 40 minutes ago -
Solid color background slows Windows 7 login
by
Alex5723
7 hours ago -
Windows 11, version 24H2 might not download via Windows Server Updates Services
by
Alex5723
5 hours, 31 minutes ago -
Security fixes for Firefox
by
Susan Bradley
5 hours ago -
Notice on termination of services of LG Mobile Phone Software Updates
by
Alex5723
17 hours, 44 minutes ago -
Update your Apple Devices Wormable Zero-Click Remote Code Execution in AirPlay..
by
Alex5723
1 day, 2 hours ago -
Amazon denies it had plans to be clear about consumer tariff costs
by
Alex5723
17 hours, 49 minutes ago -
Return of the brain dead FF sidebar
by
EricB
5 hours ago -
Windows Settings Managed by your Organization
by
WSDavidO61
4 hours, 8 minutes ago -
Securing Laptop for Trustee Administrattor
by
PeachesP
5 hours, 9 minutes ago -
The local account tax
by
Susan Bradley
6 hours, 21 minutes ago -
Recall is back with KB5055627(OS Build 26100.3915) Preview
by
Alex5723
1 day, 15 hours ago -
Digital TV Antenna Recommendation
by
Win7and10
1 day, 8 hours ago -
Server 2019 Domain Controllers broken by updates
by
MP Support
2 days, 3 hours ago -
Google won’t remove 3rd party cookies in Chrome as promised
by
Alex5723
2 days, 5 hours ago -
Microsoft Manager Says macOS Is Better Than Windows 11
by
Alex5723
2 days, 8 hours ago -
Outlook (NEW) Getting really Pushy
by
RetiredGeek
1 day, 11 hours ago -
Steps to take before updating to 24H2
by
Susan Bradley
1 day, 1 hour ago -
Which Web browser is the most secure for 2025?
by
B. Livingston
1 day, 15 hours ago -
Replacing Skype
by
Peter Deegan
1 day, 3 hours ago -
FileOptimizer — Over 90 tools working together to squish your files
by
Deanna McElveen
2 days, 2 hours ago -
Excel Macro — ask for filename to be saved
by
nhsj
23 hours, 56 minutes ago -
Trying to backup Win 10 computer to iCloud
by
SheltieMom
1 day, 3 hours ago -
Windows 11 Insider Preview build 26200.5570 released to DEV
by
joep517
4 days, 8 hours ago -
Windows 11 Insider Preview build 26120.3941 (24H2) released to BETA
by
joep517
4 days, 10 hours ago -
Windows 11 Insider Preview Build 22635.5305 (23H2) released to BETA
by
joep517
4 days, 10 hours ago -
No April cumulative update for Win 11 23H2?
by
Peobody
2 days, 22 hours ago -
AugLoop.All (TEST Augmentation Loop MSIT)
by
LarryK
4 days, 10 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.