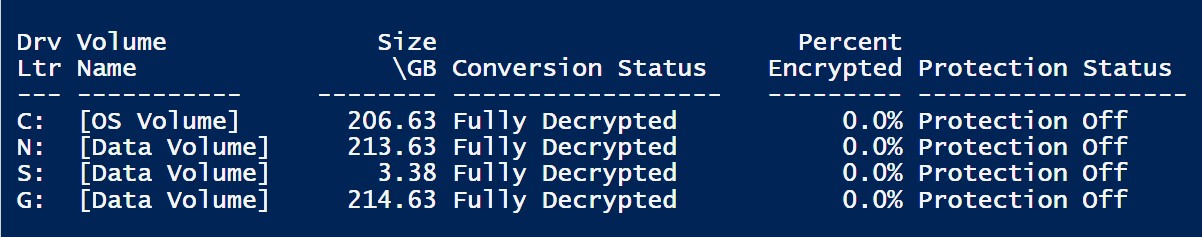
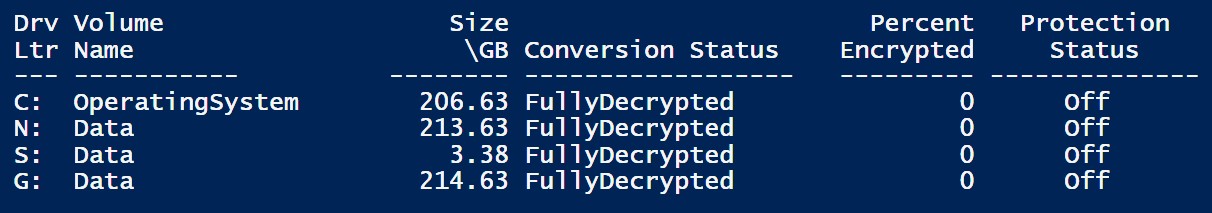
Bit-locker isn’t activated on my Win 11 machine, but after an update this week it is asking for the key and wont let me past it. Then today I get a call from someone else who had the same issue. One is a Dell desktop and one a Lenovo laptop. Something isn’t right here. I have never seen this and to have it twice in one week? I called Dell and they said just to wipe clean and start over. This needs to be investigated.
Brad


 )
)