
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Certificate cleanup for most personal computers
In this issue
- TOP STORY: Certificate cleanup for most personal computers
- LOUNGE LIFE: When it's more efficient to start over
- WACKY WEB WEEK: Where the fish are jumping — by the hundreds
- LANGALIST PLUS: Windows-like security for Android devices
- BEST SOFTWARE: Windows 8 preview: Easier file management
- BEST PRACTICES: Revising printing habits saves money and trees
Certificate cleanup for most personal computers
 By Susan Bradley
By Susan Bradley
A little Dutch company potentially lets a flood of problems into our Windows machines.
The company manages digital certificates; after its recent break-in by hackers, security certificates for Mozilla, Yahoo, WordPress, and other sites are now suspect.
On a daily basis, no matter what our level of paranoia, we trust the companies we work with. … Well, at least our browsers and computers do. Inside all computers, both Windows and Mac, is a collection of digital certificates that everyone on the Net has agreed to trust. On Vista and Windows 7 systems, these root certificates (definition) are updated by the issuer automatically. But on Windows XP machines, they’re updated manually.
Companies doing business on the Internet buy certificates linked to a root certificate and automatically become part of the chain of trust. Because your computer trusts the vendor who provided the root certificate, it automatically trusts all online businesses with associated certificates.
This process is the foundation for secure Web transactions such as shopping on Amazon, online-banking, and e-mail.
Many updates after breaks in the chain of trust
Typically, this system works well. But on the rare occasions it fails — when the chain of trust is broken — it can instantly affect thousands of PCs.
Such is the case with that small company in the Netherlands, DigiNotar. Reports from various sites indicate that hackers compromised the firm’s servers and generated rogue certificates. In a Kaspersky Lab Securelist blog, lab expert Roel speculates that as many as 200 rogue certificates were generated before the hack was discovered.
With a rogue certificate in place, a hacker can make your system think it’s using a legitimate, trusted certificate from well-known companies such as Google and Yahoo. The hacker can then intercept your Internet connection with the site you intended to use and redirect you to a fake site, where you are tricked into entering personal information such as your user name and password. Your computer still thinks it’s connected to a trusted site.
Fortunately for most of us, this particular attack appears to have targeted Internet users in Iran — it’s the only country where these rogue certificates were spotted.
Soon after the breach, browser vendors offered updates that removed the Dutch root-certificate holder from their browsers’ list of trusted certificate issuers. An August 29 Chrome Online Security blog reported that Google had disabled the DigiNotar certificate authority in Chrome 13.0.782.218.
The next day, Firefox followed suit in a Mozilla Security blog, announcing the release of numerous updates for Firefox (versions 3.6.21, 6.0.1, 7, 8, and 9), Thunderbird (3.1.13 and 6.0.1), and SeaMonkey (2.3.2) that revoked the DigiNotar root certificate.
On September 6, Microsoft released an out-of-cycle update — KB 2607712 — for Windows 2003, XP, Vista, Windows 7, and Server 2008 that not only removed all DigiNotar root certificates from the trusted list but also moved them to the untrusted-certificate store. If you find any DigiNotar certificates in the Trusted Root Certification Authorities list, I recommend you install KB 2607712.
If you do not see these certificates in your trusted-root store, you probably ignored all previous root-certificate updates. You can safely wait until the next Patch Tuesday to install the patch.
Manually removing the certificates from XP systems
Windows XP users have the option of deleting the certificates manually or merely looking over the list of certificates installed to see whether the DigiNotar cert. is there. Here’s how:
- Start out by clicking on the start button and typing mmc.exe. into the Run box, as shown in Figure 1. You’ll see a window pop up typically labeled Console1.
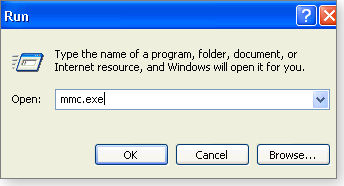
Figure 1. Opening up the mmc snapin - Click File, then Add/Remove Snap-in. In the Add/Remove Snap-in box, click the Add button, select Certificates (see Figure 2), and then click Add again.
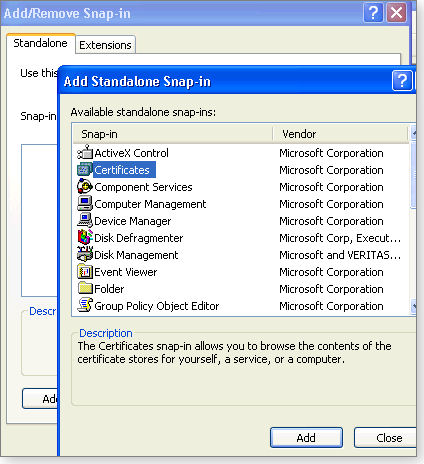
Figure 2. Adding the certificate snap in - Yet another dialog box will open, with three choices. Select Computer account and click Next. Select Local computer (the computer this console is running on) and click Finish. Now close the Add Standalone Snap-in box. In the Add/Remove Snap-in box, click Okay. That returns you to the certificate-management console.
- In the left-hand pane of the console, you should now see Certificates (Local Computer) with a small + next to it. Click on the + to expand your selection. You’ll now see numerous folders, starting with Personal and including Third-Party Root Certification Authorities, as shown in Figure 3.
For more information on what folders you might typically see, check out the superuser post, “What are the Windows system certificate stores?” (In my example, the Windows XP system is a client of Windows Home Server and thus has a WHS certificate folder you probably will not see on your XP machine.)

Figure 3. Reviewing the list of certificate types - Now expand the Trusted Root Certificate Authorities folder and click on the certificates folder underneath. You should now see a list of certificates in alphabetical order (see Figure 4). Find any DigiNotar Root CA certificates and remove them from your computer.
An alternative way to remove certificates is through Internet Explorer. In IE, click Tools/Internet Options/Content and then Certificates. Click Trusted Root Certificates. Find the listings for DigiNotar Root CA (there are two in Figure 4) and remove them by clicking the Remove button. Click Yes to the warning that removing these certificates may prevent Windows from working properly. Then click Close and Okay.

Figure 4. Removing the DigiNotar certificate.
If you don’t see these two certificates in your trusted-certificate store, it’s because you’ve probably used the “if it ain’t broke, don’t fix it” rule of updating and thus ignored previous root-certificate updates. (I found one system without the DigiNotar certificate, and when I installed the latest root certificate — KB 931125 — the rogue certificate appeared.)
Think you’re safer running the Apple platform? Guess again! Apple also included DigiNotar in its trusted root certificate program. In Apple it’s a little more complicated to remove this rogue cert — a FairerPlatform blog has the details. Apple will most likely release a patch for its platform soon.
This issue exposes the vulnerable underbelly of trust of certificates, a process we may really need to start questioning. The listing of certificate authorities includes companies from countries that aren’t always friendly to one another — and companies that have already been in the news for security breaches. If one small certificate authority in the Netherlands can be used in this type of potential spoofing attack, I hate to imagine what mischief can be done with a larger organization.
Needless to say, I may recommend holding off on future root-certificate updates until they have been examined more closely. In some cases you might be better off editing your existing root certificates rather than blindly adding updates.
Bottom line. If you have the DigiNotar certificate in your trusted-root certificate store, I recommend installing KB 2607712. On XP and Server 2003 systems, this will force a reboot — so plan accordingly. If you do not have the DigiNotar certificate in your trusted-root certificate store, simply wait for the next Patch Tuesday and apply it then.
| Feedback welcome: Have a question or comment about this story? Post your thoughts, praise, or constructive criticisms in the WS Columns forum. |
Susan Bradley has been named an MVP (Most Valuable Professional) by Microsoft for her knowledge in the areas of Small Business Server and network security. She’s also a partner in a California CPA firm.
When it's more efficient to start over
By Kathleen Atkins
Installing Malwarebytes on a machine that’s already infected is like trying to install a deadbolt on a door thieves have already crashed through.
Or maybe the exercise works as a form of diagnostic testing — if you can’t run the antivirus software, you’ve got a virus.
You can ponder ideas such as these in Lounge member squire’s post, where helpful Lounge members discuss ways to get Malwarebytes to run on his machine. Find out what he’s tried on his way to reinstalling his operating system. More»
The following links are this week’s most interesting Lounge threads, including several new questions to which you might be able to provide responses:
☼ starred posts — particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right into today’s discussions in the Lounge.
The Lounge Life column is a digest of the best of the WS Lounge discussion board. Kathleen Atkins is associate editor of Windows Secrets.
Where the fish are jumping — by the hundreds
 |
By Tracey Capen
The fisherman’s lament: Spent all day casting my line and have nothing to show for it but an empty pouch, lost hooks, and a sunburn. Like all outdoor endeavors, fishing can be a frustrating sport. Now consider a place where the fish are not only plentiful but leap out of the water straight into your boat — by the hundreds. Is it a fisherman’s dream or nightmare? Play the video |
Windows-like security for Android devices
 |
By Fred Langa
Long-time Windows users will see something very familiar in Android phones and tablets. Android feels a lot like early versions of Windows. So, applying your hard-won Windows know-how will smooth your way when working on Android devices. |
Three key elements help secure Android devices
Reader Jen Conolly wonders how to get good security on her brand-new smartphone.
- “Hi team! I recently purchased an Android phone. I have a question about a very important security issue.
“Some simple, straight talk on the subject of security/personal protection when using the plethora of phone apps available out there would be fantastic. It would give me (along with countless others, I suspect) some clarity on the subject.”
Not to worry, Jen. The same basic security techniques you use with Windows will also serve you well on your Android device. Even some of the same security-tool vendors you’re familiar with in the Windows world — Norton, AVG, and others — now offer security products for mobile computing, too.
If you’re just getting started with Android, focus on three things:
First, just as on your Windows PC, the very best thing you can do to protect yourself on Android is simply to pay close attention to what your software is doing. For example, when you’re installing an app — especially freeware — make note of what the app wants in return. (Most newer Android phones will tell you exactly what permissions an app is requesting.) If the app is asking for stuff it shouldn’t, don’t install it.
One example: I recently tried an ad-supported chess app that wanted access to both my smartphone’s network connection and my phone’s contact list. The network access made sense — the app needs to download banner ads from time to time. But why on earth did it need to rummage through my contacts? Common sense says the app is asking for way too much for what it delivers.
Second, just as you already do on Windows, use good passwords for your phone, its apps, and the sites you visit. Typing a long password can be a hassle with the tiny keyboards common on phones, but mobile password managers can make things easier. In some cases, you can even run essentially the same app on Windows and on your phone.
For example, the commercial password tool, RoboForm (site), offers interoperable mobile and desktop versions that can keep all your passwords on both platforms encrypted, in sync, and up-to-date.
Other password tools, many free or low-cost, abound on the Android Market site. Two of the best in user rankings are LastPass Password Manager (Android Market info page) and mSecure Password Manager (page).
Third, just as you do on Windows, use an antivirus/anti-malware app on Android.
My current favorite is AVG Anti-Virus Free (page). It not only does all the normal antivirus and anti-malware tasks, but also can find and disable your stolen phone or tablet, add a customized logon screen (e.g., “If found, please return to …”), and lots more. It’s an amazingly comprehensive security app — and it’s free!
Other notable security offerings include Lookout Security & Antivirus (free and paid; page) and Norton Mobile Security Lite (free, with paid upgrade option; page).
You can find many more high-quality phone utilities and tools by using the qualifier “best” in your searches, such as best android {string} apps in your browser. Replace the {string} with the category you seek — for example security, password, anti-theft, and so on.
And I gotta say: I’m excited by Android. To me, it feels a lot like early Windows — maybe Windows 3.0 — in terms of its overall operability, UI (in)consistency, and fit and finish. PC historians will recall that the subsequent Windows 3.1 was the one that really kicked Microsoft’s desktop OS into high gear. My guess is that Android is similarly poised, and its next major release may be just the ticket for truly explosive growth.
It’s really amazing how similar the two worlds are!
Restoring backups on different hardware
Arlester Christian was one of several readers asking the same question after reading “Build a complete Windows 7 safety net” (May 12 Top Story).
- “Can a Windows 7 backup be restored to different hardware?”
Yes, but it’s not ideal. When Windows wakes up on the new system, it’ll be expecting its previous hardware. But it will find something completely different. At best, it’ll churn for a long time to find and load all the new drivers it needs (expect a ton of “New Hardware Found …” messages). At worst, some of the new hardware will work poorly or not at all. And when it’s all done, you’ll have a messy setup that commingles old and new system information.
There may also be licensing issues if your copy of Windows was licensed to a specific PC.
I think it makes sense to move a system image to completely different hardware only in an emergency, such as when you’re trying to recover the backup files of a totally dead system.
If you’re getting new hardware, you’ll get better and more reliable results by starting fresh with a clean install of Windows.
Another reader misses XP’s Outlook Express
Like many Windows Secrets readers moving from XP to Windows 7, Tom wonders about his favorite e-mail client.
- “I am about to get a computer that has Windows 7 on it. I heard rumors that Outlook Express is not supported very well with Windows 7.
“I have Outlook Express with my present Windows XP computer, and I would like to continue to use it on the Windows 7 computer. How would I be able to do that, and what can I expect from Outlook Express on the Windows 7 platform?”
It’s not a rumor — Outlook Express (OE) won’t run at all on Vista and Win7. It’s been replaced by Windows Live Mail, which operates in a similar way. You can import your old OE mail and settings into Live Mail by following the instructions in the Microsoft Help & How-to article, “Trying to download Outlook Express in Windows Vista or Windows 7?”
Or, if you’re adamant about sticking with OE, you can download and run the free XP Mode for Windows 7 (info), a virtual PC that MS provides just for cases like this — where you want to run old software that can’t or won’t run on Windows 7.
(And BTW: Windows Secrets has a complete, illustrated how-to on XP Mode coming soon. Stay tuned!)
Needed: App-by-app network monitoring
Gert van den Berg wants to know exactly which applications are using his network connection.
- “Please assist! Does anyone know of a utility that can monitor and report on all network traffic in and out of my laptop, by application? I frequently see download/upload traffic, and nothing tells me what is using the connection!
“I have strict security settings, but something is getting by.
“I use Microsoft Security Essentials and Windows’ firewall for safety. The only other application which I have set to auto-update is Firefox — but it reports its own activity.”
Gert, you’ll be glad to hear that Microsoft Sysinternals’ free TCPView (info/download) does exactly what you ask. It can show you where each network connection starts and ends and which program or process owns each connection. It’s a tiny download (285KB!) and runs standalone, without requiring installation or a formal setup.
If you’d prefer not to add new software to your system, Windows’ built-in netstat command also can show you exactly what applications are communicating at any given time. Open an admin-level command window and enter the command:
netstat -b
You’ll see the list generated in real time and presented in a simple text format.
For a full list of the netstat parameters, either go to the MS TechNet Netstat page, or in the command window enter:
netstat /?
There are many third-party tools, too, such as Wireshark (free; info/download) and NetLimiter (free and paid versions; info/download). But they’re probably far more than what you need — sort of like using a sledgehammer to swat a gnat.
Either of these simpler tools, TCPView or netstat, will put the information you need right at your fingertips with minimal hassle — and zero cost!
| Feedback welcome: Have a question or comment about this story? Post your thoughts, praise, or constructive criticisms in the WS Columns forum. |
Fred Langa is a senior editor of the Windows Secrets Newsletter. He was formerly editor of Byte Magazine (1987–91), editorial director of CMP Media (1991–97), and editor of the LangaList e-mail newsletter from its origin in 1997 until its merger with Windows Secrets in November 2006.
Windows 8 preview: Easier file management
 |
By Katherine Murray
Are you happy with the way your current version of Windows — whether Windows XP, Windows Vista, or Windows 7 — behaves when you’re copying, moving, renaming, or deleting files? Windows is notorious for showing inaccurate percentage complete, time remaining, and other information during file operations. Windows 8 is on track to do better. |
Last week, Alex Simons, director of program management on the Windows engineering team, shared a few new Windows 8 features that may make some basic file operations easier and more intuitive. Keep in mind that what’s described below is based on an early preview of Windows 8. These features might — and probably will — change.
When you’re doing a large copy or move operation and have to wait for it to complete, Windows 8 will keep you better informed about the progress than previous Windows versions have. With that information, you’ll have more control over the process. Windows 8 will also handle naming conflicts in a friendlier way so that you can choose the files you want to keep with a minimum of dialog boxes and clicks required.
More and better information as you wait
When you’re performing multiple copy or move tasks at the same time, Windows 8 will show you the status of each operation and enables you to pause files so that others can be copied or moved more quickly. This means you can decide which folders or files you want to work with first, so the most important operations get done the soonest. Figure 1 shows you the more informative copy progress bars.

Figure 1. A first look at a Windows 8 copy procedure (courtesy of the Windows 8 blog)
You’ll also be able to click More Details to see additional information (shown in Figure 2) about the status of the various copy or move procedures. Windows 8 will show you in real time how the copying is progressing. Again, you can pause any process so that others can complete more quickly.

Figure 2. Windows 8 will display the progress, speed, and items remaining in the copy or move operations. (Courtesy of the Windows 8 blog)
Simplifying the resolution of naming conflicts
Another moment of file-management confusion in Windows XP, Windows Vista, and Windows 7 occurs when you encounter a naming conflict between two files. Suppose that you’re copying a set of files from one folder to another, but when you drag and drop the files, Windows lets you know that some of the files you’re copying already exist in the destination folder. You have to click through the prompts, one by one, trying to determine which files you want to keep and which you can overwrite. In Windows XP, you get only a little information to help you make that call, as seen in Figure 3.

Figure 3. Windows XP prompts you to resolve naming conflicts but doesn’t give you much to go on.
Windows 7 gives you thumbnails of the files and includes links so that you can open the files if you choose (see Figure 4). But you still need to proceed one by one, clicking the files you want to keep. If the files are similar or you just don’t remember which is which, you run the risk of overwriting the files and losing information you need.

Figure 4. Windows 7 provides more information than XP does, but you still need to resolve the conflicts one at a time.
Windows 8 promises a more graceful answer to naming conflicts. When Windows 8 prompts you about a conflict, you first choose whether to replace all files, skip the operation, or choose the files you want to copy. If you click the option to choose the files you copy, Windows 8 will display multiple files in a single Choose Files dialog box (seen in Figure 5) so that you can click each one you want to keep. The folders the files are coming from and going to are clearly marked, and check boxes appear to the left of each thumbnail so you can make your choices easily.
Windows 8 will also boldface the information so you can easily see which file is the newest and which is the largest — which can help you determine which file to keep.

Figure 5. Windows 8 should display multiple naming conflicts in a single Choose Files dialog box. (Courtesy of the Windows 8 blog.)
You should also be able to click the thumbnails in the Choose Files dialog box to open the files directly, or right-click them to display a traditional context menu offering other choices that will help you decide which files to keep.
These new operations aren’t flashy new tools that take all the wait time or confusion out of file management, but they should offer more information, better control, and a simplified process. That seems like a good first step in the right direction, and I’m looking forward to hearing what’s next.
| Feedback welcome: Have a question or comment about this story? Post your thoughts, praise, or constructive criticisms in the WS Columns forum. |
Katherine Murray just finished writing Microsoft Office 365 in the Cloud: Connect and Collaborate Anywhere, Anytime (Microsoft Press, 2011). She coauthored Green Home Computing for Dummies (Wiley 2009) with Woody Leonhard. She is also a member of the Society for Environmental Journalists and writes and tweets(@kmurray230) about green tech issues.
Revising printing habits saves money and trees
 By Katherine Murray
By Katherine Murray
Personal or small-office printers have been fundamental components of our computing environment since the earliest PCs. But they can also be expensive and temperamental beasts.
With the growing prevalence of cloud computing, PDFs, and other means of handling digital documents, it’s time to re-evaluate your printing practices.
Save time and money with portable documents
In the 1980s, the printer room in a company was a gathering place; you might catch up on the latest office gossip while you waited for a big machine to collate and print 14 35-page documents for the afternoon meeting. Today, instead of waiting by the printer, you can simply create an e-mail message, enter the recipients, attach a digital PDF of that 35-page document, and click Send. Fast and easy (though gossip will have to wait for lunch). Consider how much time, paper, and energy were saved!
Although the chances are good you create you documents in Word, it’s not the best format for distributing documents to others. Send them as PDFs (Portable Document Format), which are easily read by others — whether they have the program you used to create the document or not. PDF preserves all the elements of a printed document. Recipients of the file do need Adobe Reader (download page) or Foxit Reader (page) to be able to view the file, but that’s available online as a fast and free download.
The process of creating a PDF is significantly easier than it was a few years ago. Many popular business applications today (including Office 2010) include a Save as PDF option. And there are free and low-cost alternatives to Adobe’s PDF creation application — Acrobat. A quick Google search will turn up sites such as PDFCreator, CutePDF, and deskPDF. You can even create PDFs from your Google Docs (select File/Download as/PDF).
Digital signatures can replace a John Hancock
Many of us might still think that a legal signature requires printing documents and conveying them to the recipients whose autographs are required on the dotted line. That simple process often involved mailings, messenger services, or other transfer costs — and certainly time. Electronic signatures are fast, easy, and sometimes free. For example, DocuSign (info page), an online e-signature tool, enables you to create, mark, and send up to five documents per month for digital signatures at no cost. If your signature requirements are higher than the maximum free allotment, or you have multiple users you want to add to the account, you can sign up for a paid version of DocuSign to handle the load.
Back up and share files in the Cloud
Another common use of printers is to print backup copies of information we might need again someday. For example, if you ordered something online, chances are you printed and saved the receipt; if you found an interesting article, you printed it and filed it away for future reference. If you had a letter from a friend, a sign-up sheet for softball, or a household-inventory listing, you probably printed it and stuck it into an accordion folder for safekeeping.
Today, there are many choices for backing up information digitally — typically physical devices such as external hard drives, flash drives, or writeable CDs and DVDs.
None of these, however, will protect your data against fire, flood, theft, or your bored dog. So consider copying those important documents to cloud storage, using any of the reputable online file-storage services such as Barracuda, Carbonite, Dropbox, Symantec, Ubuntu, or Windows Live SkyDrive. As long as you have an Internet connection, you have instant access to your important files.
Why buy new cartridges when you can refill?
What’s the most common complaint about ink-jet printers? That’s a no-brainer; it’s the cost of the cartridges. Instead of throwing those empty cartridges out (or sending them in for recycling), consider having them refilled — some as many as six times. Did you know your local Walgreens drug store is in the ink-jet cartridge–refilling business? It might even refill your ink-jet cartridge while you wait. If you use a Dell, HP, Lexmark, Okidata, Primera, Sharp, or Xerox printer, look for a refilling service in your area. The cost could be less than half that of a new cartridge. (Check that using a refilled cartridge doesn’t void your printer’s warranty.)
For businesses, refilling laser-printer toner cartridges is a well-established service. Cartridge World (page), for example, specializes in selling refilled ink-jet and laser toner cartridges and boasts some 1,700 franchises across the U.S. You can go to its website and enter your ZIP code to find locations in your area. (I was surprised to find three in my town.) I did a quick price check on a Brother toner cartridge: it cost U.S. $105 new from an office-supply chain, but just over $82 from Cartridge World.
Do-it-yourselfers can get an ink-refill kit and inject fresh ink themselves. This process requires a steady hand, some 10cc syringes that come in the kit, and a old towel to mop up spilled ink. You can get between 10 and 12 refills per kit (this varies by printer model), and kits cost between $17 and $22. For example, the black-ink kit for my printer, purchased from the Printer Filling Station (page), cost $17.95 and should give 12 refills (saving about $300). I’ll let you know how it turns out.
Good habits for when you absolutely must print
When you have something that simply must be printed (for example, your son’s Little League team can’t accept your registration form electronically — you have to print it, sign it, and mail it in), here are a few reminders of how to get the most from every printout you create:
- Use recycled paper. All office supply stores now offer a range of recycled paper options, and the paper is available in high-quality, acid-free styles. You should be able to find recycled letterhead, envelopes, and off sizes, too.
- Print only what you need. Instead of printing a 15-page document when what you really need are pages 5 and 6, select only those pages for printing.
- Preview your document before you print. Doing so lets you see whether you can reduce the size of the content selection or use “Shrink to fit” to save a page or two. (It doesn’t hurt to write or edit for brevity, either.)
- Print only in grayscale. This is a drain on your black cartridge, but it’s much cheaper than using color.
- Print in Fast Draft mode by default. Change your printer’s print-quality settings to use Fast Draft mode for most of your printing.
- Print front and back. Cut your paper consumption by up to 50 percent by using duplex printing. Granted, duplex printing is a bit of a pain if your printer doesn’t handle duplex printing automatically. You might have to (as I do) print all the odd pages first and then flip the stack of printouts over and print all the even pages on the other side. It requires a little coordination, but it saves paper.
- Downsize your printer pool. How many printers do you have in your home or office — and how many do you really need? You can reduce the amount of electricity you’re using by spooling print jobs to a less number of devices. At home, you can likely get by with one or two printers (an ink-jet for color printing and a laser for black-and-white) and share them with everyone in the house through your home network.
Some final facts to consider: According to a Department of Energy report, 10 years ago the average U.S. citizen was using approximately 700 pounds of paper per year, and paper products made up 34 percent of what went into our landfills. By 2009, according to an EPA report, paper represented only 28.2 percent of what we were tossing into landfills, and in 2010, a papercycles.org article states that 63.5 percent of the paper consumed in the U.S. was actually recovered for recycling. So we’re recycling more than we’re throwing away. That’s progress!
| Feedback welcome: Have a question or comment about this story? Post your thoughts, praise, or constructive criticisms in the WS Columns forum. |
Katherine Murray just finished writing Microsoft Office 365 in the Cloud: Connect and Collaborate Anywhere, Anytime (Microsoft Press, 2011). She coauthored Green Home Computing for Dummies (Wiley 2009) with Woody Leonhard. She is also a member of the Society for Environmental Journalists and writes and tweets(@kmurray230) about green tech issues.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Very Quarrelsome Taskbar!
by
CWBillow
4 hours, 45 minutes ago -
Move OneNote Notebook OFF OneDrive and make it local
by
CWBillow
7 hours, 29 minutes ago -
Microsoft 365 to block file access via legacy auth protocols by default
by
Alex5723
8 hours, 47 minutes ago -
Is your battery draining?
by
Susan Bradley
1 hour, 26 minutes ago -
The 16-billion-record data breach that no one’s ever heard of
by
Alex5723
10 hours, 45 minutes ago -
Weasel Words Rule Too Many Data Breach Notifications
by
Nibbled To Death By Ducks
11 hours, 21 minutes ago -
Windows Command Prompt and Powershell will not open as Administrator
by
Gordski
14 hours, 36 minutes ago -
Intel Management Engine (Intel ME) Security Issue
by
PL1
5 hours, 19 minutes ago -
Old Geek Forced to Update. Buy a Win 11 PC? Yikes! How do I cope?
by
RonE22
7 hours, 50 minutes ago -
National scam day
by
Susan Bradley
10 hours, 46 minutes ago -
macOS Tahoe 26 the end of the road for Intel Macs, OCLP, Hackintosh
by
Alex5723
1 hour, 46 minutes ago -
Cyberattack on some Washington Post journalists’ email accounts
by
Bob99
1 day, 12 hours ago -
Tools to support internet discussions
by
Kathy Stevens
1 hour, 6 minutes ago -
How get Group Policy to allow specific Driver to download?
by
Tex265
1 day, 3 hours ago -
AI is good sometimes
by
Susan Bradley
1 day, 19 hours ago -
Mozilla quietly tests Perplexity AI as a New Firefox Search Option
by
Alex5723
1 day, 9 hours ago -
Perplexity Pro free for 12 mos for Samsung Galaxy phones
by
Patricia Grace
2 days, 19 hours ago -
June KB5060842 update broke DHCP server service
by
Alex5723
2 days, 18 hours ago -
AMD Ryzen™ Chipset Driver Release Notes 7.06.02.123
by
Alex5723
2 days, 22 hours ago -
Excessive security alerts
by
WSSebastian42
1 day, 13 hours ago -
* CrystalDiskMark may shorten SSD/USB Memory life
by
Alex5723
3 days, 7 hours ago -
Ben’s excellent adventure with Linux
by
Ben Myers
51 minutes ago -
Seconds are back in Windows 10!
by
Susan Bradley
2 days, 19 hours ago -
WebBrowserPassView — Take inventory of your stored passwords
by
Deanna McElveen
1 day, 12 hours ago -
OS news from WWDC 2025
by
Will Fastie
22 hours, 48 minutes ago -
Need help with graphics…
by
WSBatBytes
2 days, 3 hours ago -
AMD : Out of Bounds (OOB) read vulnerability in TPM 2.0 CVE-2025-2884
by
Alex5723
3 days, 23 hours ago -
Totally remove or disable BitLocker
by
CWBillow
2 days, 22 hours ago -
Windows 10 gets 6 years of ESU?
by
n0ads
3 days, 1 hour ago -
Apple, Google stores still offer China-based VPNs, report says
by
Nibbled To Death By Ducks
4 days, 10 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

