
|
There are isolated problems with current patches, but they are well-known and documented on this site. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Control ill-behaved apps with DEP in IE
In this issue
- BONUS: Learn Windows 7 by pictures, not words
- TOP STORY: Control ill-behaved apps with DEP in IE
- KNOWN ISSUES: Some keyloggers can read the Clipboard, too
- WACKY WEB WEEK: Humans will eat almost anything … if it's pizza
- LANGALIST PLUS: Best way to clean a PC with multiple accounts
- BEST SOFTWARE: What to do when a program installation fails
- PERIMETER SCAN: Success in digging malware from my own back yard
Learn Windows 7 by pictures, not words
This month’s bonus is a two-chapter excerpt from Teach Yourself Visually Microsoft Windows 7 by Paul McFedries. The book uses illustrations and screen shots instead of straight text to help make the transition to Windows 7 easier than ever for computer users. The printed volume isn’t yet available in most stores. But all paid subscribers can receive our exclusive download now through Sept. 23.
Free subscribers can get the bonus by upgrading to paid. You’ll see a download link afterwards. Paid subscribers can simply visit their preferences page, save any changes, and see the download link. Thanks for your support! —Brian Livingston, editorial director
Free subscribers: Upgrade to paid and get the bonus
Paid subscribers: Set your preferences and then download
Info on the printed book: United States / Canada / Elsewhere
Control ill-behaved apps with DEP in IE
 By Susan Bradley
By Susan Bradley
Internet Explorer 8 includes a security feature that shuts down misbehaving applications before they can harm your system.
This capability, known as Data Execution Prevention (DEP), runs by default when IE 8 is installed on XP SP3 and Vista SP1 or later, but it may not always be clear to you why DEP has put the brakes on one of your PC’s applications.
DEP is the best reason I know for updating to Internet Explorer 8 and Vista SP1. For many years, Microsoft has included DEP — which is also called No-Execute (NX) — only in parts of Windows. For example, DEP is available in IE 7 but is off by default to avoid conflicts with old, incompatible programs.
DEP is now a key part of Vista and Internet Explorer 8. When I try to install older software on newer machines, I must configure Data Execution Prevention to allow the software installer to run with DEP disabled. (See Figure 1.)

Figure 1. You can configure Data Execution Prevention to create an exception for an application.
To open the Data Execution Prevention dialog in XP, open Control Panel, choose System, and then select the Advanced tab. Click the Settings button in the Performance section and select the Data Execution Prevention tab. In Vista, choose Performance Information and Tools, click Advanced Tools in the left pane, select Adjust the appearance and performance of Windows, and click the Data Execution Prevention tab.
For instance, when I install QuickBooks 2007 on Windows Server 2008, I have to exclude under the DEP tab the QuickBooks updating tool in order to install it on the server.
Keep in mind that the only reason I’m doing so is because I trust Intuit, the publisher of QuickBooks. If I didn’t change the settings, DEP would prevent me from installing an older version of this software on the newer system.
If I didn’t already trust the vendor, I’d look for valid reasons why DEP was blocking the installation before I took the step of changing any DEP settings. In most instances, good, up-to-date software shouldn’t need to be excluded from DEP.
DEP helps block malware in Internet Explorer
Since IE 7, Microsoft has used DEP to help thwart online attacks in the browser itself. What the company didn’t do until IE 8, though, was to enable DEP by default.
Prior to IE 8, DEP was disabled by default for compatibility reasons, as documented on the IE blog. Many older IE add-ons were built using earlier versions of the Active Template Libraries (ATL). They aren’t compatible with DEP, therefore, and crash when IE loads them.
When DEP is enabled and combined with Address Space Layout Randomization (ASLR), IE’s ability to protect against Web-based attacks improves considerably. In a nutshell, ASLR is designed to make it harder for automatic attacks to occur. You can read more about ASLR in the MSDN blog.
Specifically, ASLR helps prevent exploits both in IE and in any add-ons that are loaded. Even with the new security protections in IE 7 and 8, the browser is still targeted more often by malware authors than other browsers. This has caused security pundits to state, as Wired’s Brian X. Chen does on the Gadget Lab blog, that Apple’s new Snow Leopard operating system is “less secure than Windows, but safer.”
(If you use Snow Leopard, I encourage you to update your system to OS X version 10.6.1. This includes a patch for the insecure Adobe Flash Player that Snow Leopard shipped with, as documented in an Apple security update.)
There are many protections built into Internet Explorer 8 that may be considered just another annoying browser crash when seen in action. (See Figure 2.)
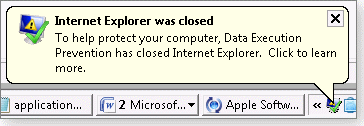
Figure 2. When DEP prevents bad code from executing in IE, it closes the browser and pops up an alert.
Unfortunately, it’s not always obvious that IE is actually protecting you when in fact it is.
Find the source of DEP-related browser crashes
Some PC support sites, such as the Tech Support Forum, recommend that you disable DEP to prevent it from closing IE whenever an unauthorized memory access is detected. However, once you understand why the browser is shutting down, it becomes clear why disabling DEP is a bad idea.
Generally, DEP errors in IE are due to an add-on, a hardware conflict, or a corrupted IE installation. If DEP continually shuts down IE on your system, find the cause of the failures instead of disabling DEP. For example, there are reports that stealthy toolbars from the Chinese search engine Baidu are the source of many DEP closures.
If DEP is closing IE 8 on a regular basis, first try opening the browser with all add-ons disabled. To do so, click Start, All Programs, Accessories, System Tools, Internet Explorer (No Add-ons).
If the DEP closures stop, this indicates that an add-on is causing the problem. Disable each add-on and then enable them one by one until the crashes return. At that time, you’ve found the culprit.
To review the processes DEP has enabled by default, press Ctrl+Alt+Del and click Start Task Manager. Click the Processes tab, select View, and choose Select Columns. Scroll to the bottom of the resulting dialog box, check the Data Execution Prevention option, and click OK.
| UPDATE 2009-09-22: The instructions for viewing the Data Execution Prevention column under Task Manager’s Processes tab apply only to Vista, not to XP. |
A new column appears in the Processes window that shows which processes on your PC are natively protected by DEP. The more processes for which DEP is enabled, the better your system is protected from buffer overflows and the other memory-related vulnerabilities DEP shields you from.
If you decide that you must disable DEP, you can easily do so in the 32-bit versions of IE 7 and IE 8.
To find this setting in IE 7, click Tools, Internet Options, Advanced, and scroll to the Security section, as shown in Figure 3. (Press the Alt key if IE’s standard menu isn’t visible.)
In IE 8, first right-click the IE shortcut, select Run as administrator, and then enter the browser’s Advanced options.
In both IE 7 and IE 8, uncheck Enable memory protection to help mitigate online attacks to disable DEP.
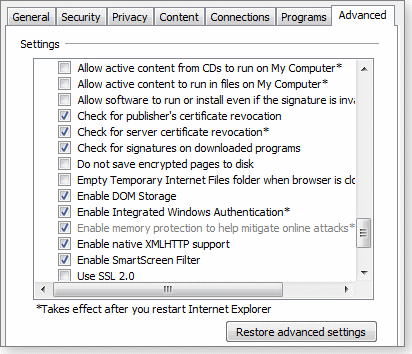
Figure 3. On 32-bit systems, DEP is enabled by the “Enable memory protection” option, which is fourth from the bottom in this screen shot.
The 64-bit version of IE 8 lacks a DEP option on the Advanced tab. The reason it’s not visible in the 64-bit version of IE is that DEP is enabled automatically and can’t be disabled. If you’re running a 64-bit operating system, you probably want the protections that DEP gives you.
Susan Bradley recently received an MVP (Most Valuable Professional) award from Microsoft for her knowledge in the areas of Small Business Server and network security. She’s also a partner in a California CPA firm.
Some keyloggers can read the Clipboard, too
 By Dennis O’Reilly
By Dennis O’Reilly
Several dozen readers responded to WS contributing editor Scott Dunn’s Sept. 10 Top Story on keeping your passwords out of the hands of sneaky keyloggers on untrusted PCs you may be forced to use while traveling.
The most frequent suggestion was to copy passwords from a text file and paste them into password boxes, but many keyloggers — unfortunately — capture any text you paste from the Clipboard.
Crooks with computers are experts at raiding online bank accounts and making a profit from personal information. Every time you think you’ve outsmarted them with a new defense, hackers find a way around or through it.
Scott described the “revised Vesik method,” which involves typing nonsense characters and mousing them into place to form a real password. It’s admittedly a convoluted way to hide data from keyloggers when you need to sign in to a Web site using a PC that might be infected. Scott acknowledged that the trick is time-consuming and prone to error.
Many readers recommended other programs and techniques to thwart either hardware or software keyloggers. Chris Miller points out the advantages of authentication techniques used by banks in Europe:
- “I don’t know the position in the U.S., but here in Europe, sensitive Web sites such as [those for] Internet banking are usually configured to defeat keyloggers.
“The best way is for the bank to supply a token — similar in concept to the SecurID or Vasco two-factor authentication systems that readers working in IT departments may be familiar with — that requires you to insert a bankcard and enter your usual PIN number before it generates a unique key that will allow logon.
“Even if this is read by a keylogger, it won’t work for any subsequent logon attempts. The drawback is obviously that you need to carry it with you and be able to attach it (via USB) to any public computer you want to use.
“Alternatively, banks require you to select a long password — say, 12 characters — and then ask at logon for a random subset: e.g., ‘Please enter the 8th, 3rd, and 10th character of your password.’
“For further protection, these characters may be selected by using drop-down menus, which should defeat most keyloggers.
“The drawback is a slight weakening against brute-force guessing — you have a chance of guessing correctly if you can make many tens of thousands of attempts — but there are strong limitations on the number of incorrect logon attempts that are allowed before the account is locked (typically three), requiring a phone call to reset the procedure.
“Simpler still is for the bank to issue a ‘one-time pad’ of randomly generated passwords that you use once and then discard. Obviously, a written pad can be lost, but as long as you don’t keep it with other identifying information — e.g., your account number — this should not be a problem.
“I think one of the reasons for the different systems in Europe is that here the onus is on the banks to provide security. If your bank account or credit card is ‘hacked,’ any resultant loss is the responsibility of the bank, unless they can demonstrate collusion on the account holder’s part. I understand this doesn’t apply in the U.S.”
Some keylogger software can, in fact, record the choices in drop-down menus. And there are reports of man-in-the-middle attacks that exploit one-time passwords only momentarily, as explained in a blog item by the Washington Post’s Brian Krebs.
But it’s clear that European banks, due to tighter regulation, are ahead of American financial institutions in security practices that defeat run-of-the-mill keyloggers. In the U.S., the Electronic Funds Transfer Act limits consumer liability when someone is the victim of an online theft. There remains little uniformity, however, in online banking.
Scott will discuss additional password-management utilities and techniques in a follow-up article about keyloggers on Sept. 24. Stay tuned!
| Chris will receive a gift certificate for a book, CD, or DVD of his choice for sending a comment we printed. Send us your tips via the Windows Secrets contact page. |
The Known Issues column brings you readers’ comments on our recent articles. Dennis O’Reilly is technical editor of WindowsSecrets.com.
Humans will eat almost anything … if it's pizza
 |
By Stephanie Small
Everyone — well, practically everyone — enjoys a slice of pizza now and then. Be it cheese, meat, veggies, or some weird combination of them all, pizza is the perfect all-inclusive and delicious meal! Domino’s, however, kicks that claim up a notch with its latest offerings. People consuming things like “cheese burst pizza” and “crispy nacho platter pizza” may make you think there’s a genetic predisposition to eat unhealthy foods. Now pizza is even being offered as a dessert, with a strawberry-like substance on one and a cookie look-alike on the other. Are you brave enough to give these a try? Play the video |
Best way to clean a PC with multiple accounts
 |
By Fred Langa
Yes, one tool can optimize a Windows setup comprising many different user accounts. PC cleanup tools take various approaches to removing junk from every account — from standard to administrator — without damaging or deleting files a user may require. |
System-wide cleanup help for multiuser PCs
A reader calling himself “Net Star” asks a savvy question about PCs with several user accounts:
- “What’s the best way to clean a computer with multiple accounts? Should you install and run [the cleanup] software on each account? If you install the software on one account, will it clean the entire computer, including each account?
“For example, programs like CCleaner will install on only one account and don’t offer the option for all users. Does this mean the program will clean the entire computer, including other accounts, or do I have to install CCleaner on each account to clean up each user’s account?”
Most reputable cleanup software does clean system-wide but may not do so in an obvious way. Remember, tools such as Piriform’s free CCleaner are not only junk-file deleters but also potentially dangerous Registry cleaners and editors. (CCleaner is available on the vendor’s site.)
Although it’s handy for all users on a PC — including non-administrators — to have easy access to junk-file removers, it might not be safe or wise to allow users with standard accounts to modify the system’s Registry.
Different tools address this safety issue in different ways. For example, CCleaner automatically installs to all accounts, but the program does so in a nonstandard way that might lead you to think it’s not present. Instead of listing itself normally in each user’s All Programs menu, CCleaner inserts itself into the context menu that appears when each user right-clicks the Recycle Bin.
From there, each user can access CCleaner’s relatively safe junk-removal features. But the program’s more-dangerous Registry cleanup features are available only to the administrator who originally installed it and who has the access rights and (presumably) the knowledge required to use CCleaner properly. This is a safe approach, but it doesn’t make it obvious that CCleaner is installed on all accounts!
Another popular free system cleaner, Macecraft’s jv16 PowerTools, handles installation differently. The program installs to all user accounts, including non-admin ones, and appears in the All Programs menus of all users. The utility’s junk-removal tools work for everyone, but if a non-administrator tries to run its Registry cleaners, the software stops with a politely worded error message stating that the Registry cleaning functions don’t work from a non-admin account.
This approach is different from CCleaner’s but has the same effect in that it blocks unskilled users from potentially mucking up the system. Visit jv16 PowerTools’ download page to get your copy (scroll to the bottom of the page to find the download link).
| UPDATE 2009-10-01: In his Oct. 1, 2009, column, Fred clarifies that jv16 PowerTools is free for only 30 days, but the PowerTools Lite version of its program is completely free. Info about PowerTools Lite is available on the Macecraft Software site. |
As for cleaning all accounts at once, I know of no cleanup tool that’s designed to work quite that way by default. In fact, for the safety and security reasons I mentioned above, you wouldn’t want a cleanup utility to give non-admins access to such features. But if you do want to clean all accounts at once, you can make it happen from an administrator account.
CCleaner, jv16 PowerTools, and other cleanup utilities support the use of command-line arguments. This means you can create scripts or shortcuts to scrub whatever target folders you wish, either automatically — such as at startup or shutdown — or via some manual trigger.
For example, CCleaner’s /auto command automatically cleans whatever locations you’ve previously selected from within the main program. So if you create a shortcut with this as the target:
“C:Program FilesCCleanerccleaner.exe” /auto
and then put it into this folder:
C:Documents and SettingsAll UsersStart MenuProgramsStartup
CCleaner will run in /auto mode each time any user signs in.
You can do the same thing with jv16 PowerTools, whose command-line options actually provide greater power and flexibility than those in CCleaner. Jv16 PowerTools even has a built-in script editor to assist in performing arbitrarily complex, highly automated system-maintenance operations.
Another way to track down unknown devices
Mark Henwood expands on identifying mystery devices, a topic I covered in a recent column:
- “In the Aug. 20 issue’s ‘Fix unknown-device errors in Device Manager,’ Fred discussed how to locate drivers for devices that Windows doesn’t recognize. But one very useful method was left out. When looking at the driver information for the unknown device, you can frequently discern the PCI Vendor and Device IDs. These in turn can be looked up to identify the errant device.
“I usually go to the PCI Database and can usually find something helpful there. Also, if you find yourself working with a range of computers, a tool like AIDA32 is invaluable. The program is discontinued but still available at various sites on the Web.”
Thanks, Mark. Ultimately, all these tools and approaches rely on Windows’ own ability to sniff out and report on the hardware it finds. But it still can be good to have multiple options available, because one technique may get you further along than the others.
In that regard, AIDA32 is indeed a good tool and is still available on the Major Geeks site, for instance. A similar program, Lavalys’ Everest Free Edition, is also offered on a Major Geeks page. However, both programs are showing their age and may not recognize newer hardware and software.
Lavalys offers up-to-date Corporate and Ultimate versions of Everest that you can download from the company’s site. But Everest is now a purely commercial offering that can be test-driven only as feature-limited trialware. The Ultimate version costs U.S. $39.95 for a one-year license.
The most-complete and up-to-date free hardware-diagnostic app I know of is SIW (System Information for Windows), available on the publisher’s site. A $69 “technician’s version” of the utility is also available.
PC locks user out of his own music files
Don O’Neill lost access to some multimedia that he thought was his for good:
- “I have tried everything I can think of, that my friends can think of, and that tech-savvy friends of friends can think of. Here’s the problem:
“I have an external hard drive formatted in NTFS. It connects only to a Sony Vaio running XP Pro Media Center Edition SP3. I use the drive to store music files. Recently, I discovered that some of these files are encrypted (why, I don’t know). When I try to decrypt these files, I get ‘access denied.’
“I might add that I have never had a third-party encryption program installed. But I have had to do an OS factory restore in the recent past, using Sony’s Media Recovery Kit. I have tried decrypting the files via Properties, Advanced, and also by using cmd.exe and then cipher /D K:, but to no avail. I can delete these files and restore them to their original place on drive K:, but I can’t decrypt, copy, or move them.
“Do you know a way through or around this very perplexing problem?”
That’s very weird, Don. But there may be reason to suspect Sony software as the culprit. Sony uses “OpenMG” digital rights management (DRM) software and includes it in products such as Sony SonicStage.
Sad to say, Sony has a spotty record — pardon the expression — when it comes to music “protection.” A few years ago, Sony released XCP, an “Extended Copy Protection” scheme that caused an uproar because it quietly installed itself as a rootkit on users’ PCs. XCP was withdrawn only under threat of punitive legal action. More info about the fiasco is available on the Electronic Frontier Foundation site.
XCP may be gone, but today you can find online reports of OpenMG’s conflicting with a Windows update and — just as you encountered — locking users out of their own music files. Once the files are scrambled, there’s no getting them back.
There’s no good way around it except to avoid Sony’s DRM schemes, which have a proven history of being unusually user-hostile.
Save power by playing movies from hard drive
Albert Pomey is looking for maximum battery life while watching movies:
- “I have a Dell Inspiron laptop with a 300GB hard drive and internal DVD player. In order to maximize battery life, should I watch movies copied to the hard drive or directly from the DVD player?”
Strictly speaking, you’ll save a little battery life by copying the movies to your hard drive while the laptop’s plugged in, and then viewing the movies from the hard drive when you’re on battery power.
Still, copying/ripping movies is a bit of a hassle, don’t you think? A more practical solution is to play the movies from the DVD drive and take other steps to reduce overall battery-power consumption.
Use your system’s built-in power-management tools and options to turn off your Wi-Fi or other networking connections while the movie’s playing. Also, run the CPU at the slowest speed that retains acceptable video performance.
You’ll also save power by exiting or suspending all nonessential software, turning the screen’s backlight down as low as circumstances allow, and setting the hard drive timeout to a short interval— just a minute or two. Also, use headphones instead of the built-in speakers, because headphones are usually more electrically efficient.
Oh, one final thing: Don’t get popcorn butter on your keyboard. (Don’t ask me how I know!)
Fred Langa is editor-at-large of the Windows Secrets Newsletter. He was formerly editor of Byte Magazine (1987–91), editorial director of CMP Media (1991–97), and editor of the LangaList e-mail newsletter from its origin in 1997 until its merger with Windows Secrets in November 2006.
What to do when a program installation fails
 |
By Ian “Gizmo” Richards
One of the most frustrating experiences for a Windows user is when an installation fails — you often can’t delete the fragments or restart the install process, leaving you with nowhere to go. Don’t give up hope; I’ll show you how to overcome this sticky stalled-installation situation. |
The causes of software-installation quagmires
There are many reasons why a program installation may fail. It could be due to a fault in the installation program itself, or perhaps the user didn’t properly read the installation instructions.
A common cause of a balky install is that some required component, such as a Windows DLL file, is missing on the user’s PC. Another likely source of the installation glitch is that a security app is preventing the installation of one or more of the program’s components.
When a software installation fails to complete, there’s usually a residue of information written by the installation program to the Windows Registry and other parts of the computer before the install failed. This leftover detritus can prevent the user from installing the program a second time. In the worst case, this orphan data may leave the user’s PC unstable or even unusable.
When an install fails, most people go to the Windows uninstall applet in Control Panel. (Windows XP’s uninstall applet can be found in Add or Remove Programs, while in Vista it’s located in Programs and Features.) Unfortunately, the program you were attempting to install probably won’t be listed — or it is listed but with the uninstallation option inoperable.
One way to get out of this mess is to manually remove the information left over by the failed install. This isn’t as easy as it sounds:
- First, you need to identify what information was written to your PC and which locations it was written to.
- Second, you’ll generally need to remove the data using specialized tools such as a Registry editor.
- Third, the volume of this data can be huge — it’s not uncommon for a program to write thousands of values into the Windows Registry when it installs.
So although it is possible to manually remove this data, doing so can be a challenge.
Easier to prevent install errors than cure them
The simplest way to clean up after a failed install is to use an uninstall program to manage the install process in the first place. These uninstallers actively monitor an installation and record all changes made to your PC by the routines. If an installation fails, the uninstall utility can easily undo all the changes the installer made and delete all the files it placed on your system.
This sounds like an attractive option, but there’s a catch. Most uninstallers require you to run the program’s installation routine from within the uninstaller itself, so you must start the uninstaller before you begin the app’s own installation routine. This is necessary so the uninstaller can monitor the progress of the installation.
That may sound easy enough, but it requires extra time and some extra effort by the user. Many people are unwilling to exercise this level of discipline. More commonly, they simply forget to start the uninstaller before they install a new program.
However, if you’re prepared to take the trouble of launching an uninstall program before you install any software, you can very effectively prevent problems due to failed installs.
There’s another advantage in using an uninstaller program: If you install an app and don’t like it, the uninstaller will successfully remove all traces of the program from your PC. In fact, uninstallers do a better job of this than the uninstallation routines that are usually provided as part of the program you’re installing.
If you want to use an uninstaller utility, there are several excellent freeware options. My top pick is ZSoft Uninstaller. It works with XP and Vista, is relatively small, and is very effective and easy to use. Download your copy from the ZSoft site.
ZSoft works by taking before-installation and after-installation snapshots of your computer and then comparing the results. (See Figure 1.) If necessary, the uninstaller can undo all changes so your computer is returned to the exact state it was in before the installation began.

Figure 1. ZSoft Uninstaller creates before-and-after snapshots so you can easily roll your PC back to the preinstall state.
You can use ZSoft as a replacement for Windows’ built-in uninstallation applet. In fact, ZSoft runs much faster than the Windows uninstall routine and is more thorough in its removal capabilities.
A good way to remove unmonitored installs
Most failed software installations occur because the installer isn’t being monitored by a separate program such as the ZSoft Uninstaller. In this case, users don’t have the simple option of reversing all changes. Fortunately, there are several options available that may help resolve the problem:
- Some software developers provide on their Web sites standalone programs that will remove all traces of their products from your computer. Two such vendors are security-software publisher Symantec and Nuance, developer of the NaturallySpeaking voice-recognition app.
Whenever an installation fails, go first to the developer’s site to see whether the company provides a removal program. Unfortunately, most vendors don’t offer such uninstallers, but don’t let that fact deter you from checking.
- A second option is to restore your computer to its preinstall state by using Windows’ System Restore to revert to the checkpoint created before the installation was attempted. This will normally reverse all changes made to the Registry. However, it will not necessarily remove all files that were written to your computer during the install.
For example, reverting to a previous system checkpoint will not remove entries in the Program Files folder, although these files can be deleted manually quite easily. In addition, such leftover files do little harm other than to take up disk space unnecessarily.
Unfortunately, many users won’t have a recent Windows checkpoint available for them to revert to. In this case, you’ll need to use another uninstall approach.
- A third option is to use a Registry cleaner to remove leftover entries in the Registry. RegClean is one of several free Registry cleaners that you could use for this purpose. The program is available for download from the RegClean site.
Keep in mind that a Registry cleaner will fix only the Registry problems created by the failed install. It won’t remove data written to the Program Files folder or other areas of your hard drive. These files will need to be deleted manually.
- Microsoft offers the free Windows Installer CleanUp Utility — but before you get your hopes up, I should tell you that this rather limited tool is useful only for programs that were installed using Windows’ built-in installer. (Many programs don’t use the Windows installer but rather a custom-built installation routine or a commercial third-party installer. Programs that do use the Microsoft installer usually have an installation file name that ends with .msi.)
There are other problems with this utility. First, it fixes only a limited range of installation problems and certainly won’t remove all the files the failed installation placed on your hard drive. The CleanUp Utility also has a well-deserved reputation for messing up installations of other programs on your PC that were working perfectly well beforehand.
And, last but not least, Microsoft’s uninstaller won’t work with Office 2007 and a number of other products. Still, it’s worth trying with failed .msi installs. I would, however, use System Restore to create a system checkpoint before using the Windows Installer CleanUp Utility, just in case you encounter problems. You can read more about the program and find a download link on the Microsoft Help and Support site.
- I’ve left one of the best options for last. The freeware utility called Revo Uninstaller provides the same monitored installs as ZSoft and also has the capability to clean up installs that the program didn’t monitor. And it does a pretty good job of it, too.
For monitored installs, I prefer ZSoft. But for failed installs, Revo is my freeware tool of choice. You could certainly get away with using just Revo, but as the two programs are both free, the best solution is to use each for the task it does best. Get your copy of Revo Uninstaller from the vendor’s site.
Using Revo is very simple: When you start the program, it displays a list of installed programs. Right-click the program you want to uninstall and choose Uninstall. (See Figure 2.) That’s it — you’re finished.

Figure 2. To remove a program using the Revo Uninstaller utility, simply right-click its entry in the Uninstaller window and choose Uninstall.
Revo also has a Hunter Mode that lets you uninstall a program by dropping its desktop or toolbar icon onto a special target icon.
However, even Revo can’t uninstall programs that it can’t find. So if you open Revo and the program you want to uninstall isn’t listed in the program’s main window, open the Options dialog and check the Advanced mode box. You should now see more programs listed in Revo’s main window. Hopefully, this includes the program you want to get rid of.
Sometimes, the program you’ve targeted for removal won’t be listed by either Revo or ZSoft. If you find yourself in this situation and you’ve exhausted the other options above, you’ll need to uninstall the program manually. In my next column on Oct. 1, I’ll describe the manual uninstallation process.
In the meantime, do check out ZSoft and Revo and start getting into the habit of monitoring all your installs. Your grandmother was right: An ounce of prevention is worth a pound of cure.
| UPDATE 2009-10-01: In his Oct. 1, 2009, column, Gizmo provides more tips for removing programs that lack their own uninstaller. |
| UPDATE 2009-11-05: In his Nov. 5, 2009, column, Gizmo takes a closer look at the Revo Uninstaller and ZSoft Uninstaller utilities. |
Ian “Gizmo” Richards is senior editor of the Windows Secrets Newsletter. He was formerly editor of the Support Alert Newsletter, which merged with Windows Secrets in July 2008.
Success in digging malware from my own back yard
 |
By Ryan Russell
It took more than one security tool for me to rid a Vista installation of a nasty virus infection. And once the malware was jettisoned, another several hours were required to ensure that Vista was up-to-date. |
Using multiple tools to clean infections
In my May 28 column, I wrote about the free anti-malware tool SUPERAntiSpyware, which you can download from the vendor’s site. Well, there’s nothing like a real-world problem to test out a tool.
A short while ago, a family friend brought by a laptop and claimed it was infected with “viruses.” It was a Dell machine running an OEM version of Vista Home Premium.
Without bothering to see what the actual symptoms were, I downloaded a copy of SUPERAntiSpyware onto a USB drive and got to work. The program wasn’t able to update itself once I had installed it on the laptop, so I downloaded the utility’s signature updates manually.
The inability of security programs to update is not uncommon on infected machines. Often, the malware will hijack Internet connections, which prevents access to tools and updates.
I also noted that Windows Defender was already installed on the machine but wasn’t working, nor would Windows updates download and install. It looked to me as if the system hadn’t been updated since early 2008.
After a couple of rounds with SUPERAntiSpyware — including a few requisite reboots — the machine finally scanned clean, though it continued to behave suspiciously. I was able to update Windows Defender manually and scanned the laptop using the free Windows Live OneCare scan.
Each scan with SUPERAntiSpyware and Live OneCare found additional malware items. After several rounds of scanning with these multiple tools, the machine finally came up clean again.
Based on the locations of some of the malicious files, I determined that the most-likely malware entry point was a LimeWire install used by the family teenager to obtain the latest music.
Surprisingly, the malware cleanup turned out to be the easiest step in the process.
Struggling to get Windows Update back online
After satisfying myself that the infection was dealt with for now, I turned my attention to getting the pending Windows updates installed. Whenever I lay hands on someone’s home machine, I follow the same procedure:
- First, take care of the malware;
- Next, get the machine’s applications patched and up-to-date and — usually — install scanning tools and updating software;
- Finally, make sure Windows Update/Microsoft Update is working and all required Windows patches are installed.
Unfortunately, I couldn’t get Windows Update to work on my friend’s laptop. It would report that updates were needed, try to download them, and then report error 0x800700C1, which means something along the lines of “bad executable” or “signature check failed.”
This also isn’t unusual during or following an infection. As I mentioned above, malware will often take steps to survive by disabling access to updates and tools. In my July 17, 2008, column, I described a DNS hijacking Trojan that would serve up bogus IP addresses for the Windows Update servers.
I suspected something similar here. But Wireshark (a network-security utility I covered in my April 3, 2008, column) and NSlookup (a free network-management utility described in MS Help and Support article 200525) verified that I was talking to the legitimate IPs.
So I decided to break out the big hammer and try to manually upgrade the Windows Update software and/or the Vista Service Pack. Frustratingly, these installs failed in a similar way.
Checking the following two locations:
C:WindowsWindowsUpdate.log
C:WindowsLogsCBSCBS.log
I found that the base problem boiled down to a similar set of errors around bad executables.
If the machine had a bad updater or installer file, I suspected the Windows updates would replace it and fix the problem. But that was only if I could get the updates to run.
After conducting a few Web searches, I found a number of references to a tool named System File Checker. In particular, it supports an sfc command, which you run from a command prompt.
To do so, you right-click Command Prompt under Accessories on the Start menu, select Run as administrator, type sfc /scannow, and press Enter. The utility will report whether it found errors, tell you to look in the cbs.log file, and give you the file location.
Have I mentioned yet that I haven’t worked with Vista much? All the while I’m doing these commands and trying to run updates, UAC is popping up for verification. This happens a lot when you’re trying to use system utilities.
But the sfc command turned out to provide a key piece of information. In particular, it told me that a file named smipi.dll was bad and couldn’t be repaired. This information was in the copious cbs.log file, which I read with Notepad.
The trick to manually updating system files
I set about trying to replace the smipi.dll file. Back at the command prompt, I changed the directory to C:Windows and typed dir /s smipi.dll. This returned three locations for the file in different subdirectories. Two of the locations were:
C:WindowsSystem32
C:WindowsWinSXSx86_microsoft [100 or so hex characters] smipi.dll
Obviously, the “live” copy of the file is the one in System32, right? Not at all, no matter how many versions I tried. Finally, I observed that dropping the file into the System32 folder was useless, so I turned my attention to the other location, which I then saw was full of zeros instead of being a valid executable. Ah, so that’s the bad executable.
Now I need to drop a good copy of that file into the correct folder. I got a good copy of the file via the Windows Update installer. I used the expand command to unpack the .msu file and then opened Explorer to look inside the .cab file.
When I tried to drop the file in the appropriate directory, I got a permission error. Oh, administrators don’t have access to those folders by default. I opened the containing directory in Explorer, right-clicked the file, and chose Properties, Security, Advanced, Owner, Edit.
I assigned Administrators as the owner, closed the dialog, right-clicked the file again, and chose Properties, Security, Edit, Give Administrators Full Control. Now I could finally overwrite the file.
Bingo! Windows Update worked again. Happy ending? Not yet.
After installing all required updates, then Vista SP1, then more updates, then SP2, I found that many critical system services wouldn’t start. This included the Event Log Service and the DHCP Service, thus preventing the machine from getting on the Internet.
Attempting to restart the Event Log Service, for example, produced error 1079. This indicates that some items in the group are running as a different user. Uninstalling Service Pack 2 fixed the glitch. The services problems were the result of how Windows runs multiple services under one Service Host process. In this case, all of the services having trouble were part of the “LocalServiceNetworkRestricted” group. I found this by running the msinfo32 program and selecting Software Environment, Services.
Doing so displays the services as well as the user and program they run under. Sorting by the Path column, I could see all the services that started with the following path:
C:WindowsSystem32svchost.exe -k LocalServiceNetworkRestricted …
Then I compared Start Name (the user it runs as) and saw that the Event Log Service had a different user name from the rest in that group. I couldn’t change it in the Services control panel because the option was grayed out.
I ran the Registry Editor by opening a command prompt, typing regedit, and pressing Enter. I navigated to this key:
HKEY_LOCAL_MACHINE / SYSTEM / CurrentControlSet / Services / Eventlog
I then changed the ObjectName string to match the one that the DHCP Service used. In this case, I changed it to this string:
NT Authority / LocalService
I could then start the Event Log Service. I rebooted to verify that it was still working, installed all Vista updates — including SP2 — and returned the working machine to its owner. Finally!
You may never need to fix a PC that’s as messed up as my friend’s. But I hope this story equips you with some tools to help you persevere, no matter what the problem dumped into your lap may be.
The Perimeter Scan column gives you the facts you need to test your systems to prevent weaknesses. Ryan Russell is quality assurance manager at BigFix Inc., a configuration management company. He moderated the vuln-dev mailing list for three years under the alias “Blue Boar.” He was the lead author of Hack-Proofing Your Network, 2nd Ed., and the technical editor of the Stealing the Network book series.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Who knows what?
by
Will Fastie
43 minutes ago -
My top ten underappreciated features in Office
by
Peter Deegan
53 minutes ago -
WAU Manager — It’s your computer, you are in charge!
by
Deanna McElveen
3 hours, 38 minutes ago -
Misbehaving devices
by
Susan Bradley
3 hours, 40 minutes ago -
.NET 8.0 Desktop Runtime (v8.0.16) – Windows x86 Installer
by
WSmeyerbos
21 hours, 17 minutes ago -
Neowin poll : What do you plan to do on Windows 10 EOS
by
Alex5723
17 hours, 1 minute ago -
May 31, 2025—KB5062170 (OS Builds 22621.5415 and 22631.5415 Out-of-band
by
Alex5723
19 hours, 51 minutes ago -
Discover the Best AI Tools for Everything
by
Alex5723
20 hours ago -
Edge Seems To Be Gaining Weight
by
bbearren
10 hours, 9 minutes ago -
Rufus is available from the MSFT Store
by
PL1
18 hours, 11 minutes ago -
Microsoft : Ending USB-C® Port Confusion
by
Alex5723
1 day, 21 hours ago -
KB5061768 update for Intel vPro processor
by
drmark
1 day, 3 hours ago -
Outlook 365 classic has exhausted all shared resources
by
drmark
41 minutes ago -
My Simple Word 2010 Macro Is Not Working
by
mbennett555
1 day, 16 hours ago -
Office gets current release
by
Susan Bradley
1 day, 19 hours ago -
FBI: Still Using One of These Old Routers? It’s Vulnerable to Hackers
by
Alex5723
3 days, 9 hours ago -
Windows AI Local Only no NPU required!
by
RetiredGeek
2 days, 18 hours ago -
Stop the OneDrive defaults
by
CWBillow
3 days, 10 hours ago -
Windows 11 Insider Preview build 27868 released to Canary
by
joep517
3 days, 20 hours ago -
X Suspends Encrypted DMs
by
Alex5723
3 days, 22 hours ago -
WSJ : My Robot and Me AI generated movie
by
Alex5723
3 days, 22 hours ago -
Botnet hacks 9,000+ ASUS routers to add persistent SSH backdoor
by
Alex5723
3 days, 23 hours ago -
OpenAI model sabotages shutdown code
by
Cybertooth
3 days, 23 hours ago -
Backup and access old e-mails after company e-mail address is terminated
by
M W Leijendekker
3 days, 12 hours ago -
Enabling Secureboot
by
ITguy
3 days, 19 hours ago -
Windows hosting exposes additional bugs
by
Susan Bradley
4 days, 7 hours ago -
No more rounded corners??
by
CWBillow
4 days, 3 hours ago -
Android 15 and IPV6
by
Win7and10
3 days, 17 hours ago -
KB5058405 might fail to install with recovery error 0xc0000098 in ACPI.sys
by
Susan Bradley
4 days, 20 hours ago -
T-Mobile’s T-Life App has a “Screen Recording Tool” Turned on
by
Alex5723
4 days, 22 hours ago
Recent blog posts
Key Links
| S | M | T | W | T | F | S |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | 7 |
| 8 | 9 | 10 | 11 | 12 | 13 | 14 |
| 15 | 16 | 17 | 18 | 19 | 20 | 21 |
| 22 | 23 | 24 | 25 | 26 | 27 | 28 |
| 29 | 30 | |||||
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

