
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
CryptoLocker: A particularly pernicious virus
In this issue
- TOP STORY: CryptoLocker: A particularly pernicious virus
- WACKY WEB WEEK: Uneasy lives of dogs in cats' houses
- LOUNGE LIFE: Parsing Office 365 requirements: Always online?
- BEST SOFTWARE: Three good Windows 8 apps — and two lousy ones
- LANGALIST PLUS: Different approaches to solving driver problems
- PATCH WATCH: A rocky start for the Windows 8.1 launch
CryptoLocker: A particularly pernicious virus
Online attackers are using encryption to lock up our files and demand a ransom — and AV software probably won’t protect you.
Here are ways to defend yourself from CryptoLocker — pass this information along to friends, family, and business associates.Forgive me if I sound a bit like those bogus virus warnings proclaiming, “You have the worst virus ever!!” But there’s a new threat to our data that we need to take seriously. It’s already hit many consumers and small businesses. Called CryptoLocker, this infection shows up in two ways.
First, you see a red banner (see Figure 1) on your computer system, warning that your files are now encrypted — and if you send money to a given email address, access to your files will be restored to you.
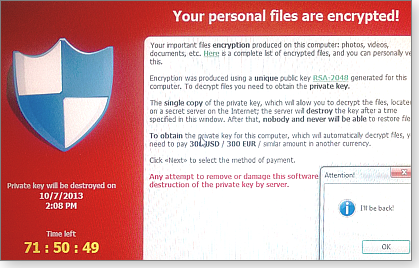
Figure 1. CryptoLocker is not making idle threats.
The other sign you’ve been hit: you can no longer open Office files, database files, and most other common documents on your system. When you try to do so, you get another warning, such as “Excel cannot open the file [filename] because the file format or file extension is not valid,” as stated on a TechNet MS Excel Support Team blog.
As noted in a Reddit comment, CryptoLocker goes after dozens of file types such as .doc, .xls, .ppt, .pst, .dwg, .rtf, .dbf, .psd, .raw, and .pdf.
CryptoLocker attacks typically come in three ways:
1) Via an email attachment. For example, you receive an email from a shipping company you do business with. Attached to the email is a .zip file. Opening the attachment launches a virus that finds and encrypts all files you have access to — including those located on any attached drives or mapped network drives.
2) You browse a malicious website that exploits vulnerabilities in an out-of-date version of Java.
3) Most recently, you’re tricked into downloading a malicious video driver or codec file.
There are no patches to undo CryptoLocker and, as yet, there’s no clean-up tool — the only sure way to get your files back is to restore them from a backup.
Some users have paid the ransom and, surprisingly, were given the keys to their data. (Not completely surprising; returning encrypted files to their owners might encourage others to pay the ransom.) This is, obviously, a risky option. But if it’s the only way you might get your data restored, use a prepaid debit card — not your personal credit card. You don’t want to add the insult of identity theft to the injury of data loss.
In this case, your best defense is prevention
Keep in mind that antivirus software probably won’t prevent a CryptoLocker infection. In every case I’m aware of, the PC owner had an up-to-date AV application installed. Moreover, running Windows without admin rights does not stop or limit this virus. It uses social engineering techniques — and a good bit of fear, uncertainty, and doubt — to trick users into clicking a malicious download or opening a bogus attachment.
Your best prevention is two-fold:
1) Basic method: Ensure you keep complete and recent backups of your system. Making an image backup once or twice a year isn’t much protection. Given the size of today’s hard drives on standalone PCs, an external USB hard drive is still your best backup option. A 1TB drive is relatively cheap; you can get 3TB drives for under U.S. $200. For multiple PCs on a single local-area network, consider Michael Lasky’s recommendations in the Oct. 10 Best Hardware article, “External hard drives take on cloud storage.”
Small businesses with networked PCs should have automated workstation backups enabled, in addition to server backups. At my office, I use Backup Box by Gramps’ Windows Storage Server 2008 R2 Essentials (site). It lets me join the backup server to my office domain and back up all workstations. I run the backups during the day, while others in the office are using their machines — and I’ve had no complaints of noticeable drops in workstation performance.
The upcoming release of Windows Server 2012 R2 Essentials (site) will also include easy-to-use, workstation-backup capabilities. Recently announced Western Digital drives will also act as both file-storage servers and workstation-backup devices.
2) The advanced method: If you have Windows Professional or higher, you can tweak your systems to protect them against CryptoLocker. You’ll want to thoroughly test the impact of the settings changes detailed below — and be prepared to roll back to your original settings if needed. (After making some of these changes, you might not be able to install or update some applications.)
All business and Pro versions of Windows include the ability to prevent certain types of software from launching from specific locations. CryptoLocker launches from a specific location and in a specific way (well, for now). By implementing Windows’ Software Restriction Policies rules, we can block CryptoLocker from launching its payload in your computer.
Software Restriction Policies (more info) were first introduced in Windows XP and Server 2003. In a domain setting, you can use Group Policy to set up these restrictions or rules; on standalone machines, you can use Local Security Policy. (Windows Home Premium doesn’t support Group or Local policies, so none of the following settings changes is supported.)
Again, be sure you test these settings changes on a single workstation first before rolling them out to other systems. Also, take the extra step of undoing the changes and checking whether the test system still runs as expected. Most important: Back up all systems before making the changes.
To make the changes, click Start/Control Panel/Administrative Tools. Click Local Security Policy and locate Software Restriction Policies under the Security Settings heading. Right-click it and select New Software Restriction Policies. Right-click Additional Rules and select New Path Rule to open the new-rule dialog box shown in Figure 2.

Figure 2. Creating a new path rule to block CryptoLocker
The following rules block applications such as CryptoLocker from running in the defined locations. For example, the first set of rules applies to the specific user folder %Appdata%, which equates to user\{yourusername}\appdata\roaming.
Enter the following sets of Path, Security Level, and Description information as separate rules:
For Windows XP, enter the following:
- Path: %AppData%\*.exe
- Security Level: Disallowed
- Description: Don’t allow executables from AppData
and
- Path: %AppData%\*\*.exe
- Security Level: Disallowed
- Description: Don’t allow executables from AppData
For Windows Vista and higher, use the above settings plus the following:
- Path: %localAppData%\*.exe
- Security Level: Disallowed
- Description: Don’t allow executables from AppData
and
- Path: %localAppData%\*\*.exe
- Security Level: Disallowed
- Description: Don’t allow executables from AppData
Additional paths for blocking ZIP-file locations are described in the bleepingcomputer.com CryptoLocker Ransomware Information Guide and FAQ. The following will ensure the virus can’t launch from embedded or attached .zip files.
- Path: %Temp%\Rar*\*.exe
- Security Level: Disallowed
- Description: Block executables run from archive attachments opened with WinRAR.
From archive attachments opened with 7zip:
- Path: %Temp%\7z*\*.exe
- Security Level: Disallowed
- Description: Block executables run from archive attachments opened with 7-Zip.
From archive attachments opened with WinZip:
- Path: %Temp%\wz*\*.exe
- Security Level: Disallowed
- Description: Block executables run from archive attachments opened with WinZip.
From archive attachments opened using Windows’ built-in .zip support:
- Path: %Temp%\*.zip\*.exe
- Security Level: Disallowed
- Description: Block executables run from archive attachments opened using Windows’ built-in ZIP support.
Figure 3 shows the Software Restrictions Policies section with newly entered rules.
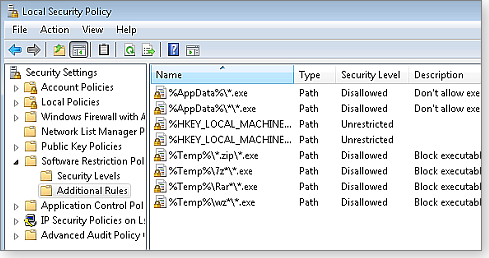
Figure 3. A completed set of software restriction policies
When you’re done entering new rules, reboot your system so that the changes take effect. Again, if you discover you can no longer update some applications or install software, you might need to undo some of these changes. Look in your application event log — or in the admin section — for the specific rule that’s misbehaving. (To open the log, click Control Panel/Administrative Tools/Event Viewer; then, in the navigation pane, click Windows Logs/Application. For more on the Event Viewer, see the Oct. 27, 2011, Top Story, “What you should know about Windows’ Event Viewer.”)
As the malware authors change their tactics, you might need to revisit the rules settings; I’ll try to post updates into the Windows Secrets Lounge whenever needed.
For even stronger CryptoLocker protection, those folks with solid IT savvy might want to consider application whitelisting — i.e., setting up a list of applications approved to run on their workstations. All other software installations are blocked. See the National Security Agency (yes, that NSA) document (downloaded PDF), “Application whitelisting using Software Restriction Policies.”
Be aware that application whitelisting is a highly advanced tactic. Take some time to determine all allowed applications in order to properly set up application whitelisting.
Once again, keeping your AV software up to date is not the panacea for CryptoLocker. The hackers using this exploit are adapting the virus so quickly that AV vendors can’t keep up with the many CryptoLocker variations in play. It’s up to individual users to stay vigilant about what they click. The bad guys just keep getting badder.
Uneasy lives of dogs in cats' houses
 |
In the shared lives of domestic dogs and cats, it’s fair to say that cats often exert more power than their relatively smaller sizes might indicate. Safe in its home environment, a cat can be just as inclined to be “top dog” as any dog is. This video is a tribute to mannerly dogs flummoxed — and even intimidated — by feline occupation of a dog’s special place. Watch how various dogs take matters into their own paws and teeth. Play the video |
Parsing Office 365 requirements: Always online?
Lounge member CWBillow has been offered a deal: Office 365 for U.S. $20 a year through his university.
But he worries about what will happen to his productivity in the Office suite if he loses his Internet connection. Is all work toast? Word Processing forum members help him figure out the fine print.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right in to today’s discussions in the Lounge.
Three good Windows 8 apps — and two lousy ones
Most Windows 8 users probably stick with tried-and-true classic Windows desktop applications and avoid the Metro alternatives.
That’s generally a wise choice, but if you stick only to the desktop environment, you’ll miss some useful and entirely free little programs. On the other hand, you’ll miss a lot of junk, too.
Working within Windows 8’s tiled user interface
I suspect that most of today’s Win8 users spend much of their time getting lots of work done in the old-fashioned Desktop environment, running classic Windows applications. But if you spend all your time there, you’re not benefiting from some fun and useful freebies.
You’ll find this especially true if you’re using a tablet or convertible laptop, or if you’re one of the few with a touchscreen display attached to a desktop PC. Despite being (in the opinion of many) flat, ugly, and unintuitive, the new UI really is more tap-and-swipe friendly than is the classic Desktop — once you learn a few crucial tricks. Of course, if you’ve got a Windows RT tablet, you have no choice in the matter; you’re stuck with the Metro UI and can use only Win8 applications. You have my condolences.
But ultimately, the success of the Metro environment will depend more on its applications than on its usability. And that’s where Microsoft seems to be still struggling. There’s no shortage of Metro apps offered at the Windows Store, but there is a shortage of quality software — programs that are excellent replacements for the classic Windows apps we’ve happily used for years.
For those who, by choice or by necessity, work at least part-time within the Metro environment, here are five free apps you should know about. The first three are less known but worthy offerings that provide simple but usable functionality when you don’t need a powerhouse application or need to depend on touch. The other two are clumsy, Metro-style adaptations of two nearly indispensable services — Dropbox and Gmail.
A touch-friendly but limited file manager
Windows 8’s built-in File Explorer is a truly awesome file manager — easily the best Microsoft has ever produced. I reviewed it in the Nov. 1, 2012, article, “Getting to know Windows 8’s File Explorer.” But its roots are obviously classic Windows — it’s definitely not touch-friendly. Just try managing files and folders with a finger, and you’ll quickly learn its limitations.
Compal’s File Brick (site) doesn’t come close to replacing all File Explorer’s features, but it does offer the basics: you can open, move, copy, rename, and delete files with easily touchable tiles.
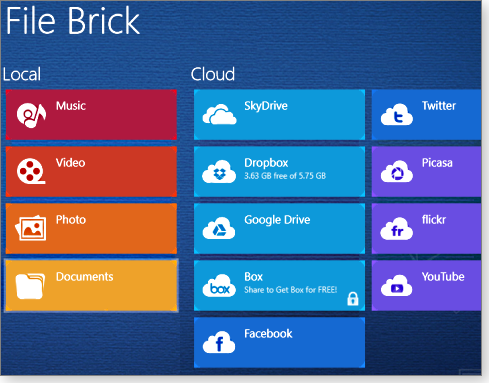
Figure 1. File Brick provides basic file management within the tiled, Metro interface.
On the other hand, the app doesn’t support simple drag-and-drop, nor does it let you copy a file’s or folder’s path to the clipboard.
The home screen provides an equivalent to File Explorer’s Favorites and Libraries panes. With shortcuts displayed as colorful tiles, you can open libraries, cloud services, and other computers on your local network. (Some of the cloud services require the full version of File Brick, which will set you back all of U.S. $2.49.)
Oddly, the default home screen offers no way to get to your documents or drives. But that’s easily fixed by creating shortcuts to them.
Tapping a file will open it. Stroking down on the file icon (touch) or right-clicking it (mouse) will bring up a menu of other options.
I wouldn’t want to depend entirely on File Brick, but when you don’t have a mouse handy, it’s a big help.
A KeePass-compatible password manager
Most of us need a password manager. Without one, we can’t possibly manage the many difficult-to-crack passwords we need for websites and applications. (For more on this topic, see the Oct. 17 Top Story, “Protect yourself from the next big data breach.”)
But moving all your passwords from one manager to another is usually a major hassle. Fortunately, there’s a Metro-based password manager that might be compatible with the password utility you’re already using.
The classic Windows password manager, KeePass Password Safe (website), is free, easy-to-use, and immensely popular. If you’re not yet using a password manager, this is an excellent choice. If you’re already using it, you probably don’t want to move to anything else.
But as I write this, KeePass doesn’t support Windows 8’s Modern Interface. That’s okay, because the Metro-based PassKeep (site; see Figure 2) reads KeePass password files. You can now access the same password database from either program — depending on the environment you’re working in at the moment.
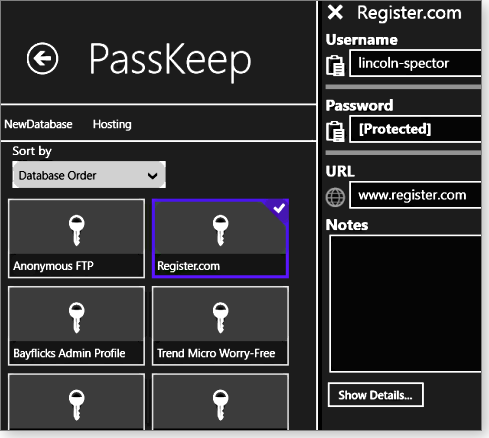
Figure 2. PassKeep is a Metro-based app that supports password files created by the popular KeePass password manager.
PassKeep isn’t a pretty program, but it’s simple and intuitive. Once you’ve loaded your database and entered your master password, each password category is displayed as a simple, small tile. Click or tap one, and the accounts within the category pop up — all equally tappable.
Click/tap an account, and a pane on the right side displays the account’s information (except, of course, the password itself). Tap the Password field, and its contents appear. Or, better yet, tap the clipboard icon next to the password field to copy and paste it into the appropriate sign-in boxes for a site or application.
For other options, such as editing account information, right-click anywhere on the screen or swipe up from the screen’s bottom.
Photo Editor: Beautifying your memories
But enough of practical ways to work in Metro. Let’s have some fun.
Aviary’s Photo Editor (site) offers basic tools for fixing and enhancing digital images. It’s not going to replace the powerful tools discussed in the March 21 (article), “Free photo editors vs. Photoshop Elements.” You can’t, for example, replace one color with another or use layers to combine two photos. And though Photo Editor has brightness and contrast controls, it doesn’t let you fiddle with highlights and shadows.
But this image editor has tools for removing red-eye, finding a better color balance, and adding color casts. There’s even a blemish remover that works reasonably well, though it probably won’t pass close inspection. You can even turn night into a day (only in your images, of course).
Photo Editor isn’t always intuitive. For example, the cropping tool will initially insist on creating a perfect square — very annoying. The solution is to open the cropping options and either pick a preset dimension or use Custom (see Figure 3).
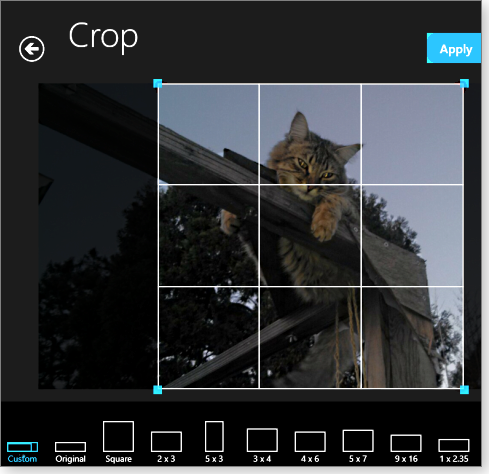
Figure 3. Photo Editor provides a solid selection of basic photo-fixing and enhancement tools.
You can use Photo Editor to add drawings and text to photos. Its Stickers feature lets you paste in circles and arrows or add whimsical touches such as funny hats and bow ties — or as Figure 4 shows, stick Groucho glasses and a nose onto your cat.

Figure 4. Photo Editor's Stickers tool adds a bit of fun to photos.
One Photo Editor oddity: Reopen an edited image and it’ll appear that you’ve lost all your changes. Don’t worry; Photo Editor automatically saves altered photos into a folder called Aviary inside the Pictures library.
Where desktop and mobile get really confused
Dropbox is one of those services that many of us truly depend on for sharing, synching, and archiving. And most dedicated Dropbox users know that its desktop and mobile versions behave quite differently. Unfortunately, the Metro edition of Dropbox treats the desktop like a phone.
In classic Windows, Dropbox is almost entirely transparent; you just install it, enter sign-in information, and forget about it. The files in your designated Dropbox folder automatically sync with Dropbox servers and any devices signed in to your Dropbox account.
Mobile versions of Dropbox, on the other hand, are anything but transparent. Files are typically viewed and managed within a separate Dropbox application. Or you must open the file in an associated app that also supports Dropbox.
Unfortunately, Dropbox (the company) decided that a Windows 8 PC is a mobile device and designed its Metro-based app (site; see Figure 5) around that concept. To open a file, you have to launch the Dropbox app, navigate to the file, and then load it into the appropriate application. Some Metro apps, including the aforementioned File Brick, make that process easier by supporting Dropbox directly. Of course, you’ll need to give all these apps your Dropbox password.
But here’s the worst scenario: If you need to work with a file when the Internet isn’t available, you must download it to a local folder when you do have Internet — and then remember to upload it again later.

Figure 5. Designed for mobile devices, Dropbox's Metro-style app is cumbersome to use.
For now, you’re far better off sticking to the classic Windows Dropbox (site) if you can. (Windows RT users are stuck with the Metro version — an all-too-familiar problem.)
When you’re better off with the website
With all its faults, I love Gmail. It’s powerful and flexible, and it allows me to organize my mail the way I want. Yes, I know it spies on me, but I know how to protect myself from prying eyes (see the Aug. 8 article, “Send email that only the recipient can read”).
As of this writing, Google doesn’t offer a Metro-based Gmail app. And considering the quality of Google’s iOS and Android apps, that wouldn’t be too big a loss.
But if Google did offer a native-Win8 app, it couldn’t be worse than PaolosApps’ Gmail Touch. There’s so much to dislike about this program.
The flaws start with the big advertisement in the lower-right corner of the app (see Figure 6). Yes, I know that Gmail has always had advertising, but the big, changing, brightly colored ads in Gmail Touch are particularly distracting and annoying. Turning the ads off will cost you $3 (a one-time charge).

Figure 6. The Metro-based Gmail Touch includes large, annoying ads — unless you pay to turn them off.
The program is also clumsy to use — just opening a message can be challenging. Click or tap a message and nothing happens. Double-click, and you select a word. Double-click really, really fast and you open the message.
It’s also painfully slow. I often found myself watching the screen and wondering whether my selection would ever come up.
In addition to its own problems, Gmail Touch also shares the shortcomings of Google’s own iOS and Android mail apps. For example, all three apps lack such advanced features as Superstars and Canned Responses. (Admittedly, Canned Responses is still in Google’s Lab, though I’ve depended on it for years.) Nor is there any rich-text formatting.
Gmail Touch does have one helpful feature: an icon near the top-right corner that opens up the real Gmail in a browser pane. Wow! What an improvement. On the other hand, you could get the same effect, full screen, by simply skipping this app altogether and using your browser.
The Modern UI/Metro side of Windows is, and probably will be for some time, a work in progress — a grand experiment for Microsoft and Windows users, to put it charitably. The right Metro apps will make Metro bearable and possibly even interesting; bad Metro apps will make the UI a nightmare.
Different approaches to solving driver problems
Some Windows problems can be truly baffling; but there’s almost always a path — or even several paths — to the solution.
Plus: Questions about accessing compressed disks, ongoing Win7 coverage, and that Win + X shortcut.
Resolving strange hardware problems
With some deep digging, reader Christopher Harris cured a strange problem afflicting 15 PCs he maintains for his school. In every PC, three different subsystems — the USB ports, My Network Places, and Device Manager — were malfunctioning simultaneously!
Although the exact steps he followed are specific to his situation, the thorough diagnostic work he describes might suggest similar problem-solving approaches for others also facing difficult problems. And my follow-up suggestions below might provide a faster approach.
- “Fred, after many years of benefiting from Windows Secrets, I’d like to give back some insight.
“Last year, I had to change the IP [address] of a teacher’s XP Pro machine from dynamic (DHCP) to fixed in order to bypass filtering.
“I went into My Network Places properties — and it was empty! Device Manager was also empty!
“After a long time on the Web trying various solutions — such as making sure the Plug and Play service was running, checking permissions on the CurrentControlSet\ENUM Registry key, installing Microsoft hotfix KB 953979, running command-line options, and anything else I could come up with — I gave up and reimaged the PC.
“Then yesterday, a teacher reported that four thumbdrives weren’t recognized by her PC. My thumbdrive was recognized, but the safe-to-remove icon didn’t appear.
“On a guess, I cleared two Registry entries: HKLM\System\CurrentControlSet\ENUM USB and USBSTOR. It worked! Windows was able to see all the thumbdrives, and the safe-to-remove icon returned.
“The big surprise was that My Network Places and Device Manager were now fixed. Digging a bit deeper, I selectively deleted entries in the USB key. The magic bullet was to remove all entries that had a class value of HIDClass and a Service value of HidUSB and then reboot.
“Because all 15 PCs had the same empty-Device Manager/My Network Places syndrome — and I wanted to be thorough — I backed up both the USB and USBSTOR Registry keys and then deleted them.
“It takes Windows a bit of time to recognize the keyboard and mouse after reboot; that can be shortened a bit by swapping the USB ports used by the mouse and keyboard.
“I tried a quick USB-key change in Win7 and ran into permissions issues, even when trying to change ownership. That’s a challenge for another day!”
Very nice troubleshooting, Christopher!
What you removed was bogus hardware settings that were written into the Registry. You also discovered that problem settings in one hardware subsystem can spill over into other, seemingly unrelated subsystems. Sometimes the only way to resolve the problem is to identify and alter or remove the bad entries.
Manual Registry editing works, but there’s a simpler, faster method that I’ve used for years to resolve all manner of seemingly intractable hardware-related problems.
You simply refresh the drivers for the malfunctioning hardware, which automatically rewrites all the relevant Registry entries in one, fast operation — no manual sleuthing or editing needed!
There are two ways to refresh drivers, depending on whether Device Manager is working. I’ll start with the most common case: where Device Manager is functioning. (The instructions are specific to XP, but they’re similar in all newer versions of Windows.)
- Save any open files, close all running apps, and back up your system.
- Open Device Manager (in XP: Control Panel/System/Hardware/Device Manager; in Vista: Control Panel/System and Security/System/Device Manager).
- Expand the listing for the device type that’s malfunctioning, right-click the troublesome device, and select Uninstall. If asked, do not choose to delete any associated drivers.
- Press OK, and reboot your system.
- During boot, Windows will discover the “new” hardware and install the drivers. This process creates brand-new Registry entries for the affected device(s), bypassing whatever settings were previously causing trouble.
As in your case, Christopher, with Device Manager out of service, there’s no easy way to uninstall the existing drivers. Perhaps your best bet would have been to visit each PC manufacturer’s site and download/install new drivers for your malfunctioning USB (and maybe networking, too) hardware — even if the “new” drivers were the same version number as those currently installed. After a reboot, I bet things would have returned to normal.
Either approach — refreshing or replacing drivers — causes all the relevant Registry entries to be totally rewritten in one step. And that often clears up whatever was causing the trouble.
Again, nice troubleshooting!
Are compressed disks readable on other PCs?
David Winston wonders about moving compressed disks from PC to PC.
- “After reading Fred’s [Oct. 10] item, “Does disk compression kill performance?” and the Sept. 12 item, “Two ways to solve a space crunch on SSDs,” my friend asked an interesting question:
“Say you have a broken desktop system, and you’ve applied disk compression to its hard drive. If you move that drive to a different PC using either a SATA/IDE-to-USB adapter or an external-drive case, will you be able to recover data files from the compressed drive — assuming both PCs are running the same OS?”
Drives compressed with Windows’ native compression should be transportable from PC to PC. The drive-compression software is baked into the operating system, so it’s always there and automatically available; no extra steps required.
In fact, I have a number of old drives, salvaged from PCs that have left this earthly vale. I still use the drives for archival backup via my USB adapter. I’ve never had any compression-related problem.
Will Microsoft continue to support Windows 7?
Noel Hargood recently moved to Win7, and he’s wondering about his investment.
- “It took me a while to convert from XP to Win7. My quandary is that everything now seems slanted toward Windows 8. Why should I now have to move to Win8? It appears to be designed for tablets and laptops, whereas I am operating a desktop with no touchscreen.
“Please don’t stop supporting Windows 7.”
No worries, Noel; Win7 support isn’t going away anytime soon. According to Microsoft’s Windows lifecycle fact sheet, the company will provide extended support for Win7 through Jan. 14, 2020.
Extended support means that even though Microsoft might not release significant future enhancements to Win7, the OS will get over six more years of monthly security updates — plus ongoing support via Microsoft’s Knowledge Base and related websites. For a full definition of Microsoft’s support policies and terminology, see the Microsoft Support Lifecycle Policy FAQ.
Windows Secrets has always covered the full lifecycle of Windows versions from beta to end of life. And I have no plans whatsoever of dropping Win7 coverage in this column. Heck, I’m still covering 13-year-old XP — where and when it’s appropriate!
Keep in mind, however, that Windows 7 was released in 2009. By now, most of its major features have already been well documented, here and elsewhere. (You’ll find almost everything you need to know about Win7 in the Windows Secrets online archives.) There’s simply not that much new to talk about.
Windows 8 merits extra coverage because it’s new and unfamiliar; it poses new and unusual problems that need exploration. (Many, if not most, new PCs have Win8 installed, and their owners are trying to adapt to a system that is, in lots of ways, significantly different from previous Windows versions.)
There’s plenty of life left in Windows 7!
About that Windows 8 Win + X key combination
Sometimes, I forget that Windows Secrets readers come in all experience levels — from seasoned experts to raw novices. But RQ’s letter serves as a good reminder to not leave anyone behind.
- “In the [Oct. 10] article, ‘How to bypass the Windows sign-in password,’ you mentioned pressing Win + X in Windows 8. I’m not sure what you mean. How’s this accomplished?”
Sorry for the shorthand, RQ. “Win” refers to the Windows flag/logo key. It’s usually in a lower corner of standard Windows/PC keyboards, often to the left and/or right of the spacebar. It’s not labeled with text; only with the Windows flag/logo. That’s the Windows key, aka Win.
Thus, Win + X means to simultaneously press the Windows logo key and the X key. (The combination is often further shortened to simply WinX — as in “open the WinX menu.”)
But you don’t have to use keyboard shortcuts. As the text noted, there are other ways to access Windows’ many system functions.
For example, to access the Admin command prompt, you can open the Charms bar, select Search, select Apps, and then enter command prompt (or “cmd” or “command”) as the search term. Wait a moment for the search results to appear before pressing Enter. Right-click Command Prompt in the search results and select Run as administrator from the menu bar, as shown in Figure 1.
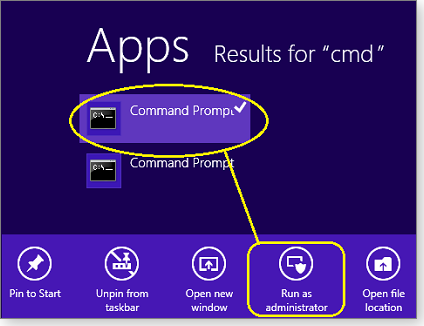
Figure 1. The Win + X key combo gives fast access to many Win8 functions, but they can also be accessed by clicking through the standard menus.
And there are still more ways to open a command-prompt window, as this preset Google search shows.
Hope that Helps, RQ. And don’t worry; you’ll be up to speed in no time!
A rocky start for the Windows 8.1 launch
Current Windows 8 users will get the update to Version 8.1 for free — but be forewarned, Win8.1 is not without issues.
Plus: Ongoing problems with recent Windows kernel updates, .NET patches safe to install, and more on nonsecurity updates.
Windows 8.1 downloads stumble at the gate
It’s difficult to decide whether Windows 8.1 is a patch, an update, or a new version of Windows. Whatever it is, the process of distributing the latest edition of Windows isn’t going well. This upgrade is not a case of “install when offered.”
For example, according to a Microsoft Community post, some Microsoft Surface owners have reported having their tablets bricked (made completely unusable) by installing Win8.1. Microsoft temporarily removed the Win8.1 RT update from the Windows Store but has now restored it. To rebuild their tablets, the reportedly small number of afflicted Surface owners have had to follow step-by-step instructions on an MS webpage and apply a special repair image.
Some PCs using standard Windows 8 are also running into problems downloading and installing the 8.1 update. The best practice is, of course, to ensure you have working recovery media and a recent image backup before migrating to Win8.1. For more on Windows 8’s data-backup tools, see Fred Langa’s recent complete series:
- July 11, “Understanding Windows 8’s File History”
- Aug. 15, “A ‘no-reformat reinstall’ for Windows 8,” which discusses Win8’s Refresh command
- Sept. 12, “A clean-slate reinstall for Windows 8,” a description of Win8’s clean-slate tool, Reset
- Oct. 10, “Creating customized recovery images for Win8,” how to refresh Windows 8 and keep you third-party apps installed
As noted in a Windows 8.1 tutorial, you should, at a minimum, set up File History to archive key files to an external hard drive.
Along with the Win8.1 update issues, related updates might also have unexpected effects on your system. For example, installing update KB 2882342 deactivates AV applications from vendors such as McAfee, Trend Micro, Panda, and others. Described by Microsoft as improving “user experience by not migrating the application to Windows 8.1,” the process requires that you reinstall these essential third-party apps after completing the move to 8.1.
Keep in mind that you might not see Windows 8.1 offered at the Windows Store until you have installed all required preparatory updates, as noted in a Windows 8 FAQ.
 What to do: Stick with your original Windows 8 for a while longer — at least until Microsoft smooths out the upgrade process. (Because you typically must download Win8.1 from the Windows Store, putting off installing the new OS is relatively easy. It’s the pre-install updates you must worry about most for now.)
What to do: Stick with your original Windows 8 for a while longer — at least until Microsoft smooths out the upgrade process. (Because you typically must download Win8.1 from the Windows Store, putting off installing the new OS is relatively easy. It’s the pre-install updates you must worry about most for now.)
MS13-081
Some Windows kernel updates still wreaking havoc
Two weeks after Patch Tuesday, I’d typically be giving the green light to kernel updates. Not this time! Among the glut of kernel fixes are several that continue to cause problems. The complete list of kernel updates from October 8 included:
On Windows XP, expect the following updates:
- 2847311
- 2862335
- 2883150
Windows XP users might also see:
- 2862330
- 2868038
- 2884256
On Vista and Windows 7, expect to see:
- 2847311
- 2855844
- 2862330
- 2862335
- 2864202
- 2868038
- 2876284
- 2883150
- 2884256
Windows 8 systems should see:
- 2847311
- 2862330
- 2862335
- 2863725
- 2864202
- 2868038
- 2883150
- 2884256
On some systems, these updates simply won’t install. Typically, the workaround is to disable any installed antivirus application, add the kernel updates, and then re-enable AV protection. Other systems have fallen to BSoDs, usually because KB 2533552 is missing. Kernel update KB 2862330, in particular, requires that KB 2533552 be installed first. Still other machines have updates offered over and over again.
 What to do: I’m still not comfortable recommending these kernel fixes. I’ll keep on top of these updates in the Windows Secrets Lounge.
What to do: I’m still not comfortable recommending these kernel fixes. I’ll keep on top of these updates in the Windows Secrets Lounge.
951847
.NET issues with an older .NET
In a somewhat unusual twist, October’s Patch Tuesday’s .NET updates are going relatively well. The one exception is KB 951847, which is being repeatedly offered on some systems — including PCs that have no version of .NET installed. Fellow Windows Secrets contributor Woody Leonhard dubbed this the ‘zombie patch’ in a recent InfoWorld article.
Windows XP systems might see:
- 2858302 and 2861188 for .NET 4.0
- 2861189 for .NET 3.0
- 2861697 for .NET 3.5 SP1
- 2863239 for .NET 2.0
Vista systems might see:
- 2858302 for .NET 4
- 2861190 for .NET 3.5
- 2861188 for .NET 4
- 2861193 and 2861208 for .NET 4.5
- 2861697 for .NET 4
- 2863253 for .NET 2.0
Windows 7 systems might see:
- 2858302 for .NET 4
- 2861191 for .NET 3.5.1
- 2861208 for .NET 4.5
- 2861698 and 2863240 for .NET 3.5.1
 What to do: Install all of the above .NET security updates if offered — except KB 951847.
What to do: Install all of the above .NET security updates if offered — except KB 951847.
First monthly Patch Tuesday now the main event?
Frequent Patch Watch readers know of my rants about nonsecurity updates being released on the first Patch Tuesday (the second Tuesday of each month) and not on the less official, second Patch Tuesday — the fourth Tuesday of the month. That trend makes it increasingly difficult to separate nonsecurity and security updates. October is a prime example.
As noted in the Office Engineering blog, Microsoft released 35 nonsecurity Office updates on Oct. 8. Fortunately, I’ve not come across any reports of problems with these fixes. The blog includes a list of all October Office and SharePoint updates — both security and nonsecurity. Below is a quick summary of nonsecurity Office patches. As you can see, Office 2013 is still a work in progress.
Office 2010
- KB 2826026 for Office
- KB 2827323 for Word
Office 2013
- KBs 2817316, 2827230, 2817314, 2817640, 2827228, 2827235, 2760257, 2760242, 2817490, 2827225, 2817309, 2738038, and 2896300 for Office
- KB 2752018 for Visio
- KB 2752078 InfoPath
- KB 2752097 for Publisher
- KB 2767859 MS Project
- KB 2768008 for Access
- KB 2810016 for OneNote
- KB 2817625 for PowerPoint
- KBs 2817631 and 2827218 for Word
- KB 2825630 for Lync
- KB 2825633 for SkyDrive Pro
Junk email filters
- KB 982726 for Office 2010
- KB 2760587 for Office 2013
- KB 2826021 for Outlook 2003
- KB 2827325 for Outlook 2007
 What to do: Now’s the time to install all nonsecurity Office updates offered in October.
What to do: Now’s the time to install all nonsecurity Office updates offered in October.
Another annoying Microsoft Bing Bar offering
There’s a growing trend among software vendors to use updating mechanisms as a way to push potentially unwanted applications at you. Microsoft is among the offenders with its Bing Bar offering in Windows Update. This month you’ll see Versions 7.2 and 7.3 in the Optional updates category (see Figure 1).

Figure 1. Microsoft pushing Bing Bar in Windows Update
The Bing Bar is an add-on browser toolbar that includes links to news, weather, email, Facebook, and other information, as noted on the Bing Bar site. That’s fine if you like that sort of thing, but I’m not a fan of additional toolbars cluttering up and slowing down my browsers. I prefer the old-school method of bookmarks and shortcuts.
 What to do: I’m especially annoyed when product offerings are included with optional updates. But, if you have the Bing Bar installed, you should update to the latest version. On the other hand, if you don’t want it, feel free to hide the update (using a right-click) — until Microsoft sends it out yet again.
What to do: I’m especially annoyed when product offerings are included with optional updates. But, if you have the Bing Bar installed, you should update to the latest version. On the other hand, if you don’t want it, feel free to hide the update (using a right-click) — until Microsoft sends it out yet again.
(2890882)
Keeping Windows on the right date and time
Making sure your system has the correct time is important — for various reasons. Periodically Microsoft releases updates to Window’s time-zone rules, which might be important to you. But it’s more important that your PC have the correct local time and date.
Typically, each locale decides its time-zone offset and when it will (or won’t) change its clocks to be in sync with the Earth’s rotation. The concept of time zones began with ship navigation and, somewhat later, was applied to the British train system. To make train schedules work, everyone had to agree on a common time. Universal time was established in Greenwich, England, and most nations and/or states set their time zones to some number of hours before or after Greenwich Mean Time (GMT; more info).
GMT is now formally called Coordinated Universal Time (UTC; more info), and it’s what most computer systems use to set their internal time. For example, I’m in UTC -8 — or eight zones away from the 0 UTC zone in Greenwich.
Each government changes its time offset as it sees fit. For example, as the Japan Times reported, Spain is debating whether to change its time zone to better fit current working hours. If it does make a change, every Windows PC might see an update to change the way it handles Spanish time. That update is important if you’re Spanish or you work with someone in Spain, but otherwise you can simply skip the update — it’s your option.
KB 2890882, for example, is an update that changes the time-zone rules for Fiji. According to the update description, “Fiji has announced changes to its daylight saving time (DST) schedule.” That’s important for PCs in Fiji — for everyone else, perhaps not so much.
As I stated at the top, it’s more important that your computer system be set to the correct local time. If it’s not, there can be numerous problems, such as incorrect file synching and an inability to sign in to banking systems. (If your system date is incorrect, SSL certificates might not work.) You also might not be able to install Windows updates, because your computer system’s clock must match the time and date kept by Microsoft’s update servers.
To check your current clock settings, click Control Panel/Date and Time. It will tell you what time zone is set and if/when daylight saving time starts or ends. You might also click the Internet Time tab and check whether your PC is set to automatically synchronize with Internet-time servers.
 What to do: When time-zone updates are offered, check whether the update actually impacts you. For most of the world, KB 2890882 is entirely optional.
What to do: When time-zone updates are offered, check whether the update actually impacts you. For most of the world, KB 2890882 is entirely optional.
Regularly updated problem-patch chart
This table provides the status of recent Windows and Microsoft application security updates. Patches listed below as safe to install will typically be removed from the table about a month after they appear. For Microsoft’s list of recently released patches, go to the MS Security TechCenter page.
See our “Windows Secrets master Patch Watch chart” post for a more extensive list of recent updates.
| Patch | Released | Description | Status |
|---|---|---|---|
| 2813430 | 06-11 | SSL-certification hardening; optional for admins | Skip |
| 2817630 | 09-10 | Outlook 2013 update | Skip |
| 951847 | 10-08 | .NET Framework | Wait |
| 2870008 | 10-08 | Windows kernel-mode drivers; see MS13-081 for complete list | Wait |
| 2885089 | 10-08 | MS SharePoint Server; see MS13-084 for complete list | Wait |
| 2687455 | 07-23 | Office 2010 SP2 | Optional |
| 2756473 | 09-10 | Outlook preview-pane issue | Install |
| 2794707 | 09-10 | Outlook 2010 | Install |
| 2825621 | 09-10 | FrontPage 2003 SP3 | Install |
| 2825999 | 09-10 | Outlook 2007 SP3 | Install |
| 2834052 | 09-10 | SharePoint Server; see MS13-067 for complete list | Install |
| 2845537 | 09-10 | MS Word; see MS13-072 for complete list | Install |
| 2848637 | 09-10 | Access; see MS13-074 for complete list | Install |
| 2853587 | 09-10 | Active Directory | Install |
| 2858300 | 09-10 | Excel; see MS13-073 for complete list | Install |
| 2864063 | 09-10 | Windows Theme File | Install |
| 2870699 | 09-10 | Internet Explorer cumulative update | Install |
| 2872339 | 09-10 | Windows Service Control Manager | Install |
| 2876217 | 09-10 | Object Linking and Embedding for Visio files | Install |
| 2876315 | 09-10 | Kernel-mode driver | Install |
| 2864058 | 10-08 | Windows Common Control library | Install |
| 2878890 | 10-08 | .NET; see MS13-082 for complete list | Install |
| 2879017 | 10-08 | Internet Explorer cumulative update | Install |
| 2885080 | 10-08 | MS Excel; see MS13-085 for complete list | Install |
| 2885084 | 10-08 | MS Word; KBs 2826020, 2827329, and 2827330 | Install |
| 2890788 | 10-08 | Silverlight | Install |
Status recommendations: Skip — patch not needed; Hold — do not install until its problems are resolved; Wait — hold off temporarily while the patch is tested; Optional — not critical, use if wanted; Install — OK to apply.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Windows 7 ISO /Windows 10 ISO
by
ECWS
48 minutes ago -
No HP software folders
by
fpefpe
1 hour, 33 minutes ago -
Which antivirus apps and VPNs are the most secure in 2025?
by
B. Livingston
57 minutes ago -
Stay connected anywhere
by
Peter Deegan
6 hours, 56 minutes ago -
Copilot, under the table
by
Will Fastie
4 hours, 10 minutes ago -
The Windows experience
by
Will Fastie
13 hours, 10 minutes ago -
A tale of two operating systems
by
Susan Bradley
4 hours, 6 minutes ago -
Microsoft : Resolving Blue Screen errors in Windows
by
Alex5723
18 hours, 30 minutes ago -
Where’s the cache today?
by
Up2you2
1 day, 9 hours ago -
Ascension says recent data breach affects over 430,000 patients
by
Nibbled To Death By Ducks
1 day, 2 hours ago -
Nintendo Switch 2 has a remote killing switch
by
Alex5723
2 hours, 55 minutes ago -
Blocking Search (on task bar) from going to web
by
HenryW
1 day, 10 hours ago -
Windows 10: Microsoft 365 Apps will be supported up to Oct. 10 2028
by
Alex5723
2 days, 3 hours ago -
Add or Remove “Ask Copilot” Context Menu in Windows 11 and 10
by
Alex5723
2 days, 3 hours ago -
regarding april update and may update
by
heybengbeng
2 days, 4 hours ago -
MS Passkey
by
pmruzicka
1 day, 6 hours ago -
Can’t make Opera my default browser
by
bmeacham
2 days, 12 hours ago -
*Some settings are managed by your organization
by
rlowe44
1 day, 23 hours ago -
Formatting of “Forward”ed e-mails
by
Scott Mills
2 days, 11 hours ago -
SmartSwitch PC Updates will only be supported through the MS Store Going Forward
by
PL1
3 days, 6 hours ago -
CISA warns of hackers targeting critical oil infrastructure
by
Nibbled To Death By Ducks
3 days, 15 hours ago -
AI slop
by
Susan Bradley
1 day, 9 hours ago -
Chrome : Using AI with Enhanced Protection mode
by
Alex5723
3 days, 17 hours ago -
Two blank icons
by
CR2
1 day, 1 hour ago -
Documents, Pictures, Desktop on OneDrive in Windows 11
by
ThePhoenix
1 day, 3 hours ago -
End of 10
by
Alex5723
4 days, 4 hours ago -
Single account cannot access printer’s automatic duplex functionality
by
Bruce
3 days, 2 hours ago -
test post
by
gtd12345
4 days, 10 hours ago -
Privacy and the Real ID
by
Susan Bradley
4 days ago -
MS-DEFCON 2: Deferring that upgrade
by
Susan Bradley
2 days, 3 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

