
|
Patch reliability is unclear, but widespread attacks make patching prudent. Go ahead and patch, but watch out for potential problems. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Downgrade Vista to XP in seven easy steps
In this issue
- TOP STORY: Downgrade Vista to XP in seven easy steps
- INSIDER TRICKS: Microsoft flubs a way to disable AutoRun in XP
- KNOWN ISSUES: Readers dubious of suites, want to mix and match
- WACKY WEB WEEK: Hell hath no fury like a lunchbox scorned
- LANGALIST PLUS: Sorting out Windows setup-disc mixups
- WINDOWS SECRETS: New rating service verifies sites in real time
- PATCH WATCH: Service packs undo vital XP, Server 2003 patches
Downgrade Vista to XP in seven easy steps
 By Scott Dunn
By Scott Dunn
Windows 7’s arrival is just a few months away, but many people aren’t waiting and just want to replace Vista’s newness — some say weirdness — for the familiarity of XP.
If you long for the good old days of XP and still have your install CD, this step-by-step guide will help you revert to Vista’s predecessor.
These days, you have to work to find a new computer that comes with XP installed. Many PC users who upgraded their XP systems to Vista are disappointed with the newer OS’s performance and other problems. In either case, as long as you have an XP installation CD, you can kiss Vista good-bye.
“Downgrading” from Vista to XP is not as difficult as you may think, but it does entail some time-consuming operations. Many online sources claim to offer techniques for reinstalling XP without having to reformat your hard disk. Based on my research, however, deleting the Vista partition and installing XP in its place is arguably the easiest approach. Moreover, this method ensures a clean install that is uncontaminated by Vista leftovers.
(Note: In certain cases, you may be able to undo an XP-to-Vista upgrade, even without an XP installation CD, by following the instructions in Microsoft article 933168. The article takes a command-line approach to the XP restoration, and also requires that you have a windows.old folder on your root drive.)
Make a pot of coffee and a new, clean XP machine
With your XP installation CD and your application discs in hand (and maybe a cup o’ Joe), you’re ready to begin:
Step 1. Back up your data. Unfortunately, you can’t restore in XP a backup that you created using Vista’s Backup and Restore Center. That means you have to either back up your data files manually or use a third-party backup tool that works in both XP and Vista. One such program is 2BrightSparks’ SyncBack (more info), which is available in free and paid versions.
Don’t bother backing up your applications; you’ll need to reinstall them from their installation CDs after XP is back in place.
Do back up the folders that your portable apps use to store their data. The portable apps themselves won’t need to be reinstalled, but you’ll have to restore their data files from the backup. Managing portable apps is discussed in the Oct. 18, 2007, Top Story, “Free software on USB enables portable computing.”
Step 2. If necessary, configure your BIOS to boot your computer from a CD, if one is present. Insert your XP installation disk and reboot.
Step 3. When XP setup loads, follow the on-screen prompts to accept the license agreement and continue installing XP. When you get to the screen prompting you for the partition on which to install XP, select the one containing Vista and press D to delete the partition. You’ll need to press Enter and then L to confirm that you want to delete all data and software on the partition.
Step 4. Once you’ve returned to the partitioning screen, select the unpartitioned space that used to be Vista. You may see that this space has been selected for you automatically. Next, press C to create a partition. Specify the desired partition size, or press Enter to accept the default allotment, which is the maximum possible partition. (Simply pressing Enter instead of C also creates a new partition of the default size.)
Step 5. If you’re still seeing the partition screen, make sure the desired partition is selected and press Enter. Choose the option that formats the disk as NTFS and press Enter again.
Step 6. Follow the prompts on-screen to continue the XP installation.
Step 7. Reinstall your applications and restore your data from your backup.
That’s all there is to it. If you ever change your mind, you can always insert your Vista DVD and upgrade from XP to Vista all over again.
Scott Dunn is associate editor of the Windows Secrets Newsletter. He has been a contributing editor of PC World since 1992 and currently writes for the Here’s How section of that magazine.
Microsoft flubs a way to disable AutoRun in XP
 By Susan Bradley
By Susan Bradley
Microsoft’s instructions for disabling AutoRun in Windows XP, which I referred to last week, pointed to an incorrect Registry key.
It’s easy to find the correct key, however, and understanding this Registry tweak can give you fine-grained control over the kinds of external media that AutoRun is allowed to work on.
Last week’s Top Story covered Microsoft’s delay in releasing an AutoRun patch for Windows XP and Server 2003. Many people want to disable AutoRun entirely, because when it runs the autorun.inf file that’s often found on CDs, USB drives, and other removable media, your machine can silently become infected. Prior to the patch, Microsoft’s official method for disabling AutoRun could be circumvented by hackers.
Unfortunately, Microsoft’s Knowledge Base article about disabling AutoRun included some misinformation. The document specified a location in the Registry that can be used to disable AutoRun, but the location exists only in Vista. The key is in a different branch of the Registry in XP.
To clarify the process of configuring XP’s AutoRun settings, I’ve created a Web page with screenshots to help explain the steps once and for all.
Most security patches take effect as soon as you install them. The patches for AutoRun, by contrast, merely enable you to disable AutoRun in a way that hackers can’t get around. After installing the AutoRun update, you need to reset a Registry key to actually disable AutoRun. The setting you choose will be based on how much you trust the USB flash drives and other removable media you might use.
First off, unless you use Microsoft’s free TweakUI or a similar third-party utility, the Registry key that controls AutoRun in Vista is under HKEY_LOCAL_MACHINE; in XP it’s under HKEY_CURRENT_USER. In other words, the key in XP that you need to navigate to in the Registry Editor is as follows:
HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Policies Explorer
The instructions to disable AutoRun in last week’s article worked fine in Vista Home and Vista Business, where the Registry key is where Microsoft said. The instructions also worked in XP Professional, which includes the Group Policy Editor and automatically operates on the correct branch of the Registry.
The errant key location in the steps affected only users of XP Home, which doesn’t come with the Group Policy Editor. XP Home requires manual editing of the Registry key via the Regedit utility.
Disabling AutoRun, of course, means you won’t get automatic loading of content, such as camera-conversion software. You’ll need to remember (and teach others who use your PC) to use Windows Explorer or your favorite file manager to start any software that may exist on removable media. If every USB flash drives you touch is guaranteed to be free from viruses, you may decide not to disable AutoRun. But you probably can’t guarantee such a thing.
It’s likely that you’ll want to change this setting on the computers of friends and relatives. On these systems, the preferred AutoRun setting depends on which types of external media you want to block. You can block or allow some or all types of AutoRun functions. Instructions for doing so at the Annoyances.org site describe (in technical language) how you can configure AutoRun by adding up decimal values.
For example, let’s say you want to disable AutoRun for everything but CD-ROMs. To block the other media types, according to Microsoft’s cryptic documentation, you’d add 1 for unknown media, 4 for removable drives (such as USB drives), 8 for fixed drives, 16 for network drives, 64 for RAM drives, and 128 for other drives of unknown types. Add all of those decimal values together and enter the result — 221 — in the Decimal box of the NoDriveTypeAutorun Registry key.
To install the AutoRun patch, which is described in Microsoft Knowledge Base article 967715, without having to validate your computer via Windows Genuine Advantage, you can use the update described in KB article 953252 instead. This patch is exactly the same, except that you can install it without the WGA checkup.
Windows 7 won’t let you postpone updates
In a column on Feb. 5, WS contributing editor Woody Leonhard explained a crucial flaw in the forthcoming Windows 7’s User Account Control (UAC) function. Hacker code could defeat UAC in the beta of Win7, a fact amply demonstrated by blogger Long Zheng and many others besides Woody.
Microsoft initially refused to change the settings, forcing Long to make his concerns public. A few days later, Redmond changed course, announcing it would fix the problem, as Woody reported in a special news update on Feb. 11.
The situation with the weird shutdown logic of Windows 7 isn’t security-related, but is just an important to many of us. When an issue like this comes up, I wish every bug tester had the ability to muster public support the way Long did. I recall many times when Microsoft has shut down any discussion of bugs by simply labeling them “by design.”
Microsoft has already closed at least one bug ticket on the shutdown behavior in exactly this way: calling it “by design.” I disagree with Microsoft’s decision, and I think you will, too.
Here’s the problem: when you set Windows 7’s update settings to Download but do not install, the new OS behaves much differently than the same settings in XP and Vista. If I happen to be in a situation where I don’t have time to install patches, the shutdown buttons in XP and Vista currently let me turn the machine off without installing patches. (See Figure 1.)

Figure 1. Windows XP lets you shut down without installing updates.
Even Windows Server 2008 allows you to shut down the computer and choose to patch at a later time. (See Figure 2.)
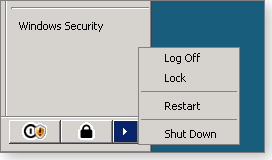
Figure 2. Windows Server 2008 gives you the same selective shutdown.
In build 7000 of the Windows 7 beta, however, there’s no option on the shutdown button to quit without installing the updates. You see only a button for the normal shutdown process, which applies the patches before the machine powers off. (See Figure 3.)

Figure 3. Windows 7’s shutdown options don’t include the no-update alternative.
I was caught off guard and found that patches were being installed as the system shut down. I had to turn the system back on to confirm that this is what had happened; it was caused by the lack of an “install patches later” choice.
Workaround for a no-update Windows 7 shutdown
Here’s the secret: the only way to shut down Win7 without installing patches is to press Ctrl+Alt+Del and then click the up-arrow by the red shutdown button. This allows the system to shut down without installing patches. (See Figure 4.)

Figure 4. The only way to shut down Windows 7 without applying patches is via Ctrl+Alt+Delete.
I’m aware that build 7000 is only a beta of Win7 and not a release candidate. I honestly don’t know whether this behavior will be included in the final version. If it is, though, I consider it to be a bad design decision that will give many Windows 7 users an unsatisfactory patching experience.
I’m not the only Win7 beta tester with concerns about the way Microsoft is passing over bugs in its zeal to get the product out the door. Don’t get me wrong: I like Windows 7 and think you’ll like it as well, once you see it in action. However, I’m concerned that a squeaky wheel is what it takes these days to goad Microsoft into making some required alterations. I hope I’m wrong and that Win7’s lack of this important shutdown option will get fixed.
Susan Bradley recently received an MVP (Most Valuable Professional) award from Microsoft for her knowledge in the areas of Small Business Server and network security. She’s also a partner in a California CPA firm.
Readers dubious of suites, want to mix and match
 By Dennis O’Reilly
By Dennis O’Reilly
The tremendous response to our request for your opinion on the best approach to securing your PC gives us much to ponder as we prepare the next Security Baseline update.
Many readers feel that security suites stink, and best-of-breed is the only way to go — but, unfortunately, what’s “best” for one PC can be disastrous for another.
Last week’s Known Issues column presented responses to Ryan Russell’s Feb. 26 Top Story on the WS Security Baseline. We asked you to chime in on your security-software preferences. Your opinions on the subject could easily fill an entire newsletter — in fact, multiple newsletters.
The responses were many and varied, but most people agreed on two points:
The first is that individual antivirus, anti-spyware, firewall, and other specialty apps are preferable to such all-in-one security suites as Symantec’s Norton Internet Security 2009. (Ryan’s article had pointed out that NIS 2009 is the top choice of PC World, PCMag.com, Maximum Software, and other reviewers. But not everyone concurs.)
The second is that a security solution that works great on one PC or network may flop miserably on another.
Reader Mary Smith-Markell puts it this way:
- “OK, I’m going to take you up on your offer to share my thoughts. I’m tired of people giving their opinions about which security product, operating system, word processing software, hamburger, pizza, automobile, etc., is ‘the best.’ Opinions are like assholes … we all have one.
“NIS 2009 might work just great on my computer because of the way my machine is configured and the specific software I have installed. NIS 2009 might totally suck on my neighbor’s machine because it’s not set up the same as mine. Does that mean NIS 2009 is a defective product, or is it an unreasonable expectation that Norton (or McAfee, AVG, Avast, Trend Micro, et al.) be all things to all people? With so many user variables — not to mention machine variables — it’s a wonder that most software actually works most of the time.
“A few months ago, a friend bought a 2009 Cadillac Escalade — a fairly pricey and supposedly well-built vehicle. It’s been in the shop more than it’s been on the road, and the dealership is taking action under the Lemon Law to replace it. Stuff happens.
“To all the readers who have a favorite security product they swear by, I’m happy for you. Really, I am. But to those who tried a product and found it didn’t work, quitcherbitchin’ and use a different product. Having some kind of security product is better than no security product at all.”
If experience counts for anything, you’d be nuts to buy any security suite, regardless of how highly the professional software reviewers rate it. Tim Marsh echoes Dennis Edelbrock’s sentiments regarding best-of-breed vs. all-in-one security programs:
- “Like Dennis Edelbrock, I too have been building/repairing computers for 20 years. I must agree that Peter Norton was a genius and had the best products, bar none. It’s not surprising that his products were wanted by a larger company. Unfortunately, it didn’t take long before Symantec completely ruined Peter’s great name. It’s a shame, really.
“If you ask any repair technician who’s been doing this for years, they’ll all tell you that standalone products far outperform their suite counterparts. There is simply no debate on this matter. I agree that for a large number of people, suites are easier to install/maintain and are therefore a good choice, as compared to not running anything or not enough.
“You must also realize that magazines/Web sites are in business to make money. It makes me wonder how any reputable company could ever say that the Symantec suite is best of class. I guess if by ‘class’ you mean ‘suites,’ then it’s possible to make this claim. However, if the intent is to configure one’s computers to ensure maximum protection, then standalone products simply can’t be beat. And the funny thing is, in my opinion, many free products outperform most commercial products.
“I urge your readers to keep reading this newsletter, as it always shows both sides to every story. Also, keep in mind that any commercial-based company may not have the end user’s best interest in mind when they’re advertising-based. I would rather take the advice of someone like Dennis Edelbrock any day before a magazine or commercial Web site.”
In defense of computer magazines, I know that the one I worked for until late 2007, PC World, went to great lengths to ensure the impartiality of its hardware and software reviews. I truly believe that most professional tech journalists are not influenced by the vendors. Their bosses, on the other hand, may be a different matter.
| Readers Mary and Tim will each receive a gift certificate for a book, CD, or DVD of their choice for sending tips we printed. Send us your tips via the Windows Secrets contact page. |
The Known Issues column brings you readers’ comments on our recent articles. Dennis O’Reilly is technical editor of WindowsSecrets.com.
Hell hath no fury like a lunchbox scorned
 |
By Katy Abby
Celebrity chef Gordon Ramsay (of the popular televised competition “Hell’s Kitchen”) is notorious for his foul mouth and short fuse. Few and far between are the episodes that don’t culminate in crying contestants, as Gordon summarily rips apart their culinary slogs with a fiery enthusiasm. But where did he acquire such a dramatic and pigheaded disposition? Take a gander at this hilarious supposition about where the devilish cook got his start, and maybe things will make a little more sense. I pity the next person who serves the tiny tyrant overcooked chicken fingers or generic mac ‘n’ cheese! Play the video |
Sorting out Windows setup-disc mixups
 |
By Fred Langa
If you’re one of the many Windows Secrets readers who’s charged with managing multiple PCs — and I bet you are — you may be juggling a half dozen or more Windows installation CDs and DVDs. Here’s how to stay sane while making sense of the different setup discs that shipped with the systems. |
Which setup CD goes with which PC?
Have you ever ended up with a fistful of setup CDs without a clue as to which discs came with which PC? I sure have, and so has Geoff Nicholls:
- “Your [Feb. 12] column, “Retrieve a lost product key for Windows XP,” was very useful and partly solves my problem, having found the key for each PC.
“But, like many of your subscribers, I look after multiple PCs and have stored all of the discs in the same place over different generations. Is there a way to find which disc relates to which PC? XP Pro vs. Home is easily sorted, but does a key apply to a certain service-pack level as well?”
Here’s some good news: product keys aren’t that restrictive, and sorting out your setup discs may be easier than you think. In fact, you may not even need most of them!
First — just to be clear — a Windows product key is generally supposed to stay with the PC it was originally installed on. The key doesn’t change with normal updates and service packs. It remains in force for the life of the OS on a given machine.
Now consider that all PCs running the same version of XP — or any version of Windows, for that matter — draw from the same pool of original code and updates. With one exception that I’ll mention in a moment, your installations of XP Pro, for example, are essentially the same as mine and all others everywhere in the world. We have different licenses and keys, but the core OS code is more or less interchangeable.
Because all systems running the same version of Windows use essentially the same code, it doesn’t matter where that code comes from. That, in turn, means the setup CDs for a given version of Windows will work on any PC. Indeed, Microsoft’s standard end-user policy is “one PC per license,” not “one PC per setup CD.” The license and product key go with the PC, not with the setup disc.
It’s even 100% legitimate to create your own custom, fully up-to-date XP setup CD for each version of Windows and use that disc for reinstalls on any PC that has its own separate and legitimate product key for that Windows version.
That’s what I recommend you do. Create one fully up-to-date “master” setup CD for each version of XP and use those masters for all your OS reinstalls. (See my Dec. 18, 2008, column, “Slipstreaming simplifies Windows reinstalls,” for information on creating master setup CDs.) When asked for the product key during a reinstall for a given version of XP, just enter the original key for the version of Windows that came with that specific PC. It works and it’s 100% legit.
There’s one caveat: the OEM setup disks that ship with new PCs (which often carry vendor-specific branding) may contain drivers unique to the machine the CD shipped with. This usually isn’t a huge deal, because Windows will use generic drivers if brand-specific drivers aren’t available. After a generic reinstall, simply browse to the vendor’s site and download whatever custom drivers the PC may need. You can avoid this minor hassle by keeping these branded OEM setup CDs with the PCs they came with.
Remember, for normal end-user versions of Windows, it’s “one PC per license,” not “one PC per setup CD.” A setup CD for a given version of Windows can be used on pretty much any PC that has its own separate, legitimate Windows product key. You can use my setup CDs and I can use your setup CDs. As long as we keep our product keys separate and use them only on the PCs they’re associated with, we’re golden.
Resuscitating a dead System Restore applet
Danny Cope’s PC has lost its ability to use System Restore to create restore points.
- “Could you give me ‘Dummies’-type help to fix my XP System Restore? It no longer works. It seems the ‘restore points’ are still being created, but [the system] will not actually restore.”
You haven’t given me a lot of information to work with, Danny, but here are some of your options:
First, try disabling and then re-enabling System Restore. To do so, click Start, Control Panel, Performance and Maintenance (in Category view), System. In the System Properties dialog box, click the System Restore tab and check the Turn off System Restore option.
Reboot and go through the same steps again, but this time, uncheck the Turn off System Restore option. This process should clear out your old restore points and give System Restore a fresh start.
If that doesn’t work, try running the Restore/Enable System Restore script from the Kellys-Korner site. (Look for item 278.) In addition to the Restore/Enable System Restore script, the item includes an Undo script. Obviously, you want the former.
If you’re still System Restore-less, the System File Checker, sfc.exe, may help by ensuring that all your system files are up-to-date. (See MS Knowledge Base article 310747 for more info).
Finally, Microsoft’s optimistically named article, “Windows XP System Restore Is Easy to Use,” may help you track down any glitches that the above operations fail to resolve.
A ‘fix’ causes more problems than it solves
Mary Smith-Markell offers this comment on the tip “A fix for Windows’ broken installer utility” in my Feb. 26 column:
- “If you do a repair install of Windows XP, you might find out that Automatic Updates stop working, as explained in this Knowledge Base article.
“It’s also possible that the resolution in the above KB article may not fix things. The first time I did a repair install with my XP Pro w/SP2 CD, I had to manually re-register my regsvr32 files (wuapi.dll, wuaueng.dll, wuaueng1.dll, wucltui.dll, wuweb.dll, wups.dll and wups2.dll.)”
Good tip, Mary. Thanks!
Yes, several of Window’s own repair/maintenance tools sometimes cause new problems. For example, running the Disk Cleanup tool in Vista can break the Hybrid Sleep and Hibernation feature. If you need help re-registering your regsvr32 files, you can read about and download the patch in KB article 929846. That fix pertains to all Vista versions, not just Vista Enterprise — despite what the page says.
Storing complete CDs/DVDs on a hard drive
Weldon Schultz’s interest was piqued by a recent item:
- “In ‘What do external drives do best?’ [from the Feb. 19 column], you said: ‘The drive is so big that I’ve even copied many of my installation CDs and DVDs to it.’
“Can you explain how to copy an installation CD over to an external HD?”
Sure, Weldon! There are two basic ways to do this.
The first is to copy the entire contents of the CD or DVD. Say you have a CD with your favorite software on it — let’s call it “Weldonware2009.” Create a new folder somewhere on your giant hard drive named Weldonware2009. Pop your CD into the drive and choose ‘explore’ (don’t select ‘open’ or ‘auto-run’).
Next, highlight the files in the root directory and the top-level folder(s) on the CD and drag them to the Weldonware2009 folder you just created on your hard drive. That’s it. You’re done! In most cases, you can now install the software from the external hard drive just as if it were on the CD; there’s usually a setup.exe program or equivalent in the top-level folder.
Sometimes, installation software is configured to run only from a CD or DVD, either for technical reasons or for copy-protection purposes. In such cases, you have to use the second approach: make an ISO copy of the disk and store that copy on the hard drive. (“ISO” is short for “ISO 9660,” a nearly universal CD format defined by the International Standards Organization.)
Every CD/DVD–burning suite I know of — including those from vendors Roxio, Nero, and Ashampoo — have utilities to create an ISO copy of a CD or DVD. For example, Ashampoo offers the excellent Burning Studio Free (more info). Just search the help files of your CD-burning program for information relating to ISO copying.

Figure 1. All good CD/DVD-burning tools — including Ashampoo Burning Studio Free — let you create ISO image files of your application discs.
When you burn the ISO copy to a blank CD or DVD, the resulting disk will be functionally identical to the original. Even better, “mount” the ISO image directly using special software to create a virtual CD drive. Virtual CD software makes your system think it’s seeing a real drive and lets you use the ISO file exactly as if it were a real, physical CD.
Microsoft offers a small, free, unsupported program called Virtual CD ROM (see Softpedia for info and a download). The program is designed for XP, but with a little fancy footwork, it’ll run in Vista as well. Because it’s an unsupported tool, you’ll need to go to third-party sites for instructions. Two good resources are MakeUseOf and Charles Sterling’s MSDN blog.
Fred Langa is editor-at-large of the Windows Secrets Newsletter. He was formerly editor of Byte Magazine (1987–91), editorial director of CMP Media (1991–97), and editor of the LangaList e-mail newsletter from its origin in 1997 until its merger with Windows Secrets in November 2006.
New rating service verifies sites in real time
 |
By Mark Joseph Edwards
Version 3 of Symantec’s Norton 360 security software includes a new “Safe Web” feature that competes directly with McAfee’s SiteAdvisor. But are Safe Web’s real-time checks of the sites you’re visiting any more effective than SiteAdvisor’s database approach? |
Security application improves its usability
In the Feb. 26 Top Story, Ryan Russell wrote about Symantec’s Norton Internet Security 2009, which several leading tech publications currently rate as the best overall security suite. At the same time, Ryan noted the pain that a lot of users have experienced when installing, using, and uninstalling Symantec’s security software.
I’ve also heard many complaints about the product. Most relate to its software bloat, resource hogging, and disk-space requirements. Apparently, Symantec has been listening. Last week, the company released Norton 360 version 3, which brings several improvements, according to a tour at Symantec’s site.
When I spoke recently with Symantec representatives about the product, I learned that version 3 can be installed in less than one minute and uses less than 10MB of RAM when the software is idle. The new release also requires only about 110MB of hard-disk space. These are all improvements over the previous release.
Among the program’s new features are the ability to block botnets and a tool that helps you disable startup programs. Norton 360 v3 boots and runs faster, updates signatures more frequently (every 5 to 15 minutes), and uses fewer CPU cycles when idle.
But perhaps the most interesting new feature in the program is its Safe Web component. This is a direct competitor to McAfee’s SiteAdvisor, a site-rating service I wrote about in the Feb. 12 Top Story. WS editorial director Brian Livingston subsequently reported in a Feb. 19 follow-up on several details McAfee subsequently revealed on SiteAdvisor’s update and dispute-resolution policies.
Like SiteAdvisor, Safe Web aims to indicate the safety of a given site using a familiar green-yellow-red rating system. But there’s a fundamental difference in the ways that Safe Web and SiteAdvisor establish their ratings.
First of all, you must be a user of Norton 360 to gain access to the Safe Web browser toolbar; there’s no equivalent to SiteAdvisor’s free browser add-on. Secondly, Safe Web scans every Web site that you visit in real time by passing a site’s content into the security tools contained within Norton 360.
Furthermore, every time you visit a Web page, the URL is passed back to Symantec, which schedules its own scan using the company’s proprietary tools. Even though sending Symantec the URLs of all the sites you visit raises significant privacy concerns, scanning pages in real time is theoretically more reliable than the techniques used by LinkScanner, LinkExtend, Web of Trust, and other such services that monitor site safety. (WS senior editor Gizmo Richards reported on LinkExtend in his Mar. 5 column.)
Norton 360 includes anti-malware tools that rely in part on data regarding emerging threats. The program is updated with this data several times an hour, whenever your PC is connected to the Internet. This allows Safe Web to detect new malicious sites much sooner than competing services do — at least in theory.
False positives plague all site-rating services
Safe Web’s approach isn’t perfect. In fact, it’s fraught with the same false positives that hamper SiteAdvisor and other reputation-rating services that rely on content scanning.
For example, Safe Web rates the site Milw0rm.com as red, allegedly because it contains a known bit of malware. In reality, Milw0rm.com is a repository for all sorts of exploit code. The site itself doesn’t perpetrate exploits against its visitors — it merely publishes examples of exploit code, so its red rating is undeserved, in my book.
Interestingly, SiteAdvisor gives Milw0rm.com a yellow rating, which is just as bogus. There’s no reason not to rate Milw0rm.com as green.
If you’re a site owner concerned about how Safe Web might rate your site, visit Symantec’s Safe Web sign-up page to claim ownership of your site. After your registration is complete, you can subscribe to an RSS feed that will keep you up-to-date on your site’s status.
The bottom line is that all site-reputation rating services are jockeying to position themselves as gatekeepers of a secure Web, but that claim is outright dangerous. Any service that can’t rate a site with 100% accuracy, 100% of the time, has no business offering an assessment of the site’s safety.
I think all such services should drop the green and yellow ratings and offer only red ratings to flag sites known to be dangerous. Anything beyond that is unfettered hubris.
Unpatched danger in Adobe Reader and Acrobat
As Susan Bradley pointed out in her Feb. 26 Patch Watch column, an extremely dangerous vulnerability exists in Adobe Reader and Acrobat that could let a bad guy completely take over your system. A patch wasn’t released until yesterday (Mar. 11), so until you’ve applied the update, be very leery of opening any PDF files from unknown sources.
Visit Adobe.com for the patch and install it without delay.
Firefox and Opera browsers need updating
If you use the Firefox and Opera browsers, make certain that you’ve updated your software to versions 3.0.7 and 9.64, respectively. These updates fix dangerous vulnerabilities in the programs.
Firefox 3.0.7 contains fixes for four security problems related to Javascript, PNG image files, XML document data, and document object model elements. Opera 9.64 contains three fixes that remedy security issues related to JPEG image files and JavaScript code, along with a fix for an “unspecified” problem for which no details were given.
A word to wise WordPress users: update!
If you’re among the millions of people who use the WordPress blogging platform, make absolutely certain that your sites are running the latest version — 2.7.1 — of the software. In fact, if you’re running any version prior to 2.6.5, your site is a sitting duck that hackers can take over on a whim.
Over the past couple of months, I’ve kicked hackers out of several WordPress sites for my consulting clients. The pattern of intrusion was the same in each case: the bad guys exploited a site running an older version of the software — even though version 2.7.x has been available since December 2008 — to inject a backdoor into the server.
The backdoor gives the invaders complete and unrestricted access to your entire file system and database. With that level of access, the crooks can modify your page templates, plug-in files, the core WordPress code, and your database. This means they can insert hidden spam links and assorted malware to infect the computers belonging to your site’s visitors.
In some cases, simply upgrading your software won’t remove the backdoor. To completely plug the hole, you must either (1) delete your entire site and restore it from an uninfected backup copy and then immediately upgrade to the latest WordPress software, or (2) hire an expert to track down and close the backdoor. Either route is time-consuming and potentially costly. It’s far more effective to simply keep your software up-to-date in the first place.
Just to be entirely clear, the problem isn’t specific to WordPress; this sort of vulnerability can beset any Web application. Keep all of your Web software as current as possible.
Mark Joseph Edwards is a senior contributing editor of Windows IT Pro Magazine and regularly writes for its Security Matters blog. He’s a network engineer, freelance writer, and the author of Internet Security with Windows NT.
Service packs undo vital XP, Server 2003 patches
 |
By Susan Bradley
If you installed XP Service Pack 3 or Windows Server SP2 after September 2008, you need to reapply an important security update. In addition, if Windows Update offers your XP or Server 2003 system Microsoft’s security bulletin MS08-067 patch, you should install it — even if you’ve previously done so. |
MS08-067 (954593)
XP SP3 and Server 2003 SP2 may need repatching
You may be wondering why my lead topic today is MS08-067, a patch from 2008. Well, I’m wondering, too.
You may find this week that your Windows XP SP3 and Windows 2003 SP2 machines are offered MS08-067 (954593). If so, you probably installed SP3 on XP or SP2 on Windows 2003 some time after September 2008.
People who installed MS08-067 when it first came out last summer — and then installed either the XP SP3 or 2003 SP2 service pack — may not know that systems were reverted back to a vulnerable version of gdiplus.dll.
Service packs aren’t supposed to do that. They’re supposed to be smart enough to retain the patched versions of all system files.
Last month, however, I found that some XP machines I’d updated to SP3 post-September had the pre-update version of gdiplus.dll. On three of the systems, my third-party patching tool from Shavlik flagged this file as out-of-date. It offered the patch to me when I performed a manual scan.
I thought it odd at the time, but I believed that the problem was with Shavlik’s tool, not Microsoft’s. When I reviewed the patch information on Shavlik’s forum, though, I found a forum post from last November by a commenter named Fordhami indicating that Microsoft knew of this issue back then.
Interestingly, I’d installed XP SP2 on several XP SP3 workstations and then reinstalled XP SP3, only to find that the machines were properly patched. I searched for gdiplus.dll on those systems and found three files in locations similar to the following path:
C:Windows WinSxS x86_Microsoft.Windows.GdiPlus_hashnumber
The version of all three files was 5.1.3102.5581. This indicated that the machine was patched. You may want to search for that file and see what version you have. Don’t worry about any gdiplus.dll files located elsewhere on your system. The important one is found in the WinSxS folder.

Figure 1. This gdiplus.dll version number indicates that the file is up-to-date.
This isn’t the first patch-detection problem for XP SP3. Given the number of months since the update’s initial release, it’s disturbing that the problem is just now coming to light. People still ask me whether it’s OK to install SP3 on XP systems. When it comes to any service pack, I always caution you to be prepared by creating a complete backup before installing it.
I hope, for all our sakes, that this is the last time I’ll be writing about issues with XP SP3 and patches.
MS09-006 (958690)
Plugging yet another image-file hole
The update described in Microsoft security bulletin MS09-006 (958690) patches a possible attack using compromised EMF or WMF image files. The good news is that the likelihood of an attack appears to be slight. I still urge you to apply this patch as soon as you can.
In my tests of the patch, everything went well. But whenever you patch the Windows kernel — as this update does — you should be prepared for potential conflicts with antivirus software, which may need to be updated and/or tweaked.
Firefox users: Got .NET? Get rid of it!
Many users of Mozilla’s Firefox browser got a surprise after they installed .NET Framework 3.5 Service Pack 1: an unexpected .NET add-on for the browser.
to uninstall the add-on, you’ll find instructions in Microsoft KB article 963707. The steps, which are completely manual, are for the brave of heart, to be sure. A note at the top of the article hints that there’ll soon be an update to .NET 3.5 SP1 that automates the uninstall process.
If you’d rather not wait to remove the add-on from your system, take the manual-uninstall route. Personally, I’m just glad that Microsoft has acknowledged the issue. I can wait for the automated uninstallation via the .NET 3.5 SP1 patch, whenever that may arrive.
| UPDATE 2009-10-22: In her Oct. 22, 2009, column, Susan explains why the Mozilla Foundation blocked and subsequently unblocked the .NET Framework Assistant and Windows Presentation Foundation add-ons for the Firefox browser after Microsoft released the patch described in MS09-054 (974455). |
In an unrelated note, all Firefox users should upgrade to version 3.0.7, as Mark Joseph Edwards describes in this week’s PC Tune-Up column.
Adobe and Foxit PDF readers need patching
At first, I thought I’d be discussing today only a brand-new patch for Adobe Reader and Acrobat that fixes a zero-day threat to PDF readers. Not to be left out, Foxit Reader has a fix of its own. However, Foxit beat Adobe to the finish line with its patch release (see the Foxit site for more info). Adobe finally came out with its own PDF updates, although the issue was first reported last month.
If your PDF reader doesn’t prompt you to download and install these updates, you may need to launch the app to make it retrieve the patches. As an alternative, visit Adobe’s bulletin page and download its patch manually, if you use Adobe Reader or Acrobat.
Note that the patch applies only to Adobe Acrobat version 9; the updates for versions 7 and 8 aren’t due until Mar. 18.
The bad news for administrators is that the updated version of Acrobat 9 still doesn’t support roaming profiles in a network setting. In the update’s release notes, the company makes it clear that roaming profiles aren’t supported in version 9, even though they did work in version 8.
For the best security, upgrade to version 9.1 of Adobe Reader and Acrobat, and version 3 of Foxit, whichever version you may currently be using.
Apple’s AirPort gets a much-needed update
While there are no important Macintosh security patches this month, Apple has released a couple of updates that fix a few network problems. The 2009-001 AirPort update described on an Apple support page patches Mac utility software.
Also due this month from Apple are updates for iLife and camera software.
MS09-007 (960225)
Secure Sockets Layer fixes low-risk glitch
You might be wondering why two security patches that Microsoft released on Patch Tuesday this month are so far down in my article today. It’s because the problems they resolve represent little risk for client workstations.
The update described in Microsoft security bulletin MS09-007 (960225) impacts SSL transmissions between a workstation and server.
Why isn’t this a major issue? After all, we use SSL certificates on secure Web sites all the time.
Due to the very limited manner in which the attacker can obtain the access required to launch this attack, it would occur only when a site sends you a secure certificate to install on your machine before you can connect to its servers.
Most of us use a process of public certificates, whereby a third-party organization such as Verisign holds the information to make the certificate valid. Thus for most people, this is a non-issue.
Don’t get me wrong: I’d still like you to patch. But the threat is minor, in my opinion.
MS09-008 (962238)
Domain name services get another patch
At last summer’s BlackHat security research conference, Dan Kaminsky demonstrated the insecurity of the Web’s Domain Name System (DNS). DNS is the master dictionary that computers use to look up Web addresses. At that time, a patch was released that makes it harder for attackers to poison these DNS records.
The update described in Microsoft security bulletin MS09-008 (962238) improves on the earlier fix, preventing attackers from tricking computers into redirecting users to malware sites. This patch is for servers only, so most people needn’t take any action.
If you run Small Business Server 2003, however, the DNS patch in Microsoft security bulletin MS08-037 caused random selection of ports by the DNS services, interfering with the server rebooting. To prevent this, install the patch described in KB 956263, which should be offered to your server automatically. This update for SBS 2003 is new this week.
Just say no to this Office Live update
Just because Windows Update or Microsoft Update offers you a patch, it doesn’t mean it’s a good idea.
Such is the case for the Office Live add-in for Office 2007. Unless you already use an Office Live product, you don’t need the patch. If you use Vista, you might think the update is a critical patch, because Vista doesn’t separate important updates from optional updates, the way XP does.

Figure 3. Vista lists optional updates, such as the one in the middle for Office Live, along with important patches.
David Barnes indicates in a blog post that this combined listing caused a SharePoint problem in his Small Business Server network. Dave had to remove the optional update from his workstations.
Bottom line: If you don’t really need this patch, don’t install it. If you’ve installed it and don’t need it, uninstall it.
Symantec’s Norton AV oops causes a big headache
For some reason, Symantec sent an unsigned file a few days ago to users of its Norton antivirus product. As a result, many Norton users were alerted to an unknown file that was requesting access to the Internet.
After determining that the “suspicious” file had actually come from Symantec, users went online to the company’s forums and posted questions. The resulting increase of questions and concerns led to Symantec staffers, at one point, deleting valid messages from the forums in an attempt to calm the angry crowd.
As reported in a CNET article, Symantec failed to tell users ahead of time that it was sending out a diagnostic file. Symantec’s failure to digitally sign the file caused it to generate alerts on firewalls. The company did a poor job of handling the resulting firestorm of concern.
Although some unwanted spammers did manage to post junk in the forums to take advantage of the confusion, Symantec should have been up-front about the problem and not deleting entire threads. Let this be a lesson to all vendors: come clean about what you’re doing. Let’s hope they get the hint.
The Patch Watch column reveals problems with patches for Windows and major Windows applications. Susan Bradley recently received an MVP (Most Valuable Professional) award from Microsoft for her knowledge in the areas of Small Business Server and network security. She’s also a partner in a California CPA firm.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
24H2 Installer – don’t see ption for non distructive install
by
JP
3 hours, 57 minutes ago -
Asking Again here (New User and Fast change only backups)
by
thymej
10 hours, 9 minutes ago -
How much I spent on the Mac mini
by
Will Fastie
4 hours, 57 minutes ago -
How to get rid of Copilot in Microsoft 365
by
Lance Whitney
1 hour, 57 minutes ago -
Spring cleanup — 2025
by
Deanna McElveen
16 hours, 1 minute ago -
Setting up Windows 11
by
Susan Bradley
3 hours, 12 minutes ago -
VLC Introduces Cutting-Edge AI Subtitling and Translation Capabilities
by
Alex5723
11 hours, 29 minutes ago -
Powershell version?
by
CWBillow
12 hours, 22 minutes ago -
SendTom Toys
by
CWBillow
7 hours, 1 minute ago -
Add shortcut to taskbar?
by
CWBillow
16 hours, 17 minutes ago -
Sycophancy in GPT-4o: What happened
by
Alex5723
1 day, 8 hours ago -
How can I install Skype on Windows 7?
by
Help
1 day, 7 hours ago -
Logitech MK850 Keyboard issues
by
Rush2112
14 hours, 17 minutes ago -
We live in a simulation
by
Alex5723
1 day, 22 hours ago -
Netplwiz not working
by
RetiredGeek
1 day, 9 hours ago -
Windows 11 24H2 is broadly available
by
Alex5723
2 days, 11 hours ago -
Microsoft is killing Authenticator
by
Alex5723
22 hours, 51 minutes ago -
Downloads folder location
by
CWBillow
2 days, 17 hours ago -
Remove a User from Login screen
by
CWBillow
1 day, 13 hours ago -
TikTok fined €530 million for sending European user data to China
by
Nibbled To Death By Ducks
2 days, 8 hours ago -
Microsoft Speech Recognition Service Error Code 1002
by
stanhutchings
2 days, 8 hours ago -
Is it a bug or is it expected?
by
Susan Bradley
10 hours, 56 minutes ago -
Image for Windows TBwinRE image not enough space on target location
by
bobolink
2 days, 7 hours ago -
Start menu jump lists for some apps might not work as expected on Windows 10
by
Susan Bradley
1 day, 7 hours ago -
Malicious Go Modules disk-wiping malware
by
Alex5723
2 days, 21 hours ago -
Multiple Partitions?
by
CWBillow
2 days, 22 hours ago -
World Passkey Day 2025
by
Alex5723
18 hours, 28 minutes ago -
Add serial device in Windows 11
by
Theodore Dawson
4 days, 6 hours ago -
Windows 11 users reportedly losing data due forced BitLocker encryption
by
Alex5723
2 days, 7 hours ago -
Cached credentials is not a new bug
by
Susan Bradley
4 days, 11 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

