
|
There are isolated problems with current patches, but they are well-known and documented on this site. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Emergency repair disks for Windows: Part 2
In this issue
- LOUNGE LIFE: Times-have-changed department: Marital chat
- TOP STORY: Emergency repair disks for Windows: Part 2
- WACKY WEB WEEK: Playing with winter snow — in August
- LANGALIST PLUS: Is it worthwhile to upgrade an XP-era PC?
- BEST SOFTWARE: Taking Microsoft's Office for iPad for a spin
- ON SECURITY: Shedding some light on security-cert warnings
Times-have-changed department: Marital chat
Lounge member donny wants to talk to his wife. He wants to talk to his wife while he’s downstairs and she’s upstairs.
He wants instant messaging to work between two computers in the same house, using the same router. Looking for a simple solution, he consults fellow Loungers in the Social Media forum. You have choices these days, he’s happy to learn. Here’s a posted observation you’d not have heard 10 years ago: “Most people I know just use their Facebook accounts to IM … in the same household.”
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right into today’s discussions in the Lounge.
Emergency repair disks for Windows: Part 2
Part 1 of this two-part series told how to create a Windows repair disk that boots a failing PC and provides tools that might fix what’s ailing Windows.
Part 2 tells how to use a repair disk on all PCs — including those locked down with Win8’s Secure Boot — and also gives some advanced tips and tricks.
Creating a repair disk is the first step
A good repair disk or drive (collectively, disk) is a fundamental tool for troubleshooting an ailing Windows. Every PC owner/manager should have one for each system — and know where it resides. There are multiple repair-disk options for all versions of Windows, from XP on. Part 1 of this series lists nine, most of them free.
XP requires third-party tools for creating repair disks, and enabling Vista’s built-in app takes some efforts. But both Windows 7 and 8 make the process easy and include numerous troubleshooting tools.
Creating a repair disk is a necessary first step; the next is ensuring the disk correctly boots the PC. Some systems — especially Win8 systems with Secure Boot enabled — take a little prep work.
That’s the starting point for the exercises in this article. You’ll see how to use emergency boot/repair disks to start just about any PC, then use those repair tools included on the disk.
Make an initial test of your emergency disk
If you haven’t yet created an emergency boot/repair disk or drive for your version of Windows, please do so now. See the April 10 Top Story, “Emergency repair disks for Windows: Part 1.”
Depending on how your system is set up, booting a PC from its rescue disk might not require anything unusual — or you might have to change one or two settings.
The best way to find out is also the simplest:
- Shut down all software, exit Windows, and turn your PC completely off (i.e., a full power-off shutdown).
- Place your boot/repair CD/DVD into your PC’s optical drive or plug the rescue drive into a USB socket.
- Turn your PC on.
If your PC boots from the rescue disk, you’re done! Simply label it and store it in a safe place. If you’re using Win8, skip to the end of this article for those aforementioned advanced tips and tricks.
On the other hand, if your PC fails to boot from the rescue disk, use the following steps to make the necessary adjustments to your system.
Controlling your PC’s startup
With all PCs, initial startup is controlled by low-level software that wakes up the system’s components in the correct order and then hands off control to Windows.
In older systems, that software is the Basic Input/Output System — commonly referred to as BIOS.
Most newer systems use the far more powerful and flexible Unified Extensible Firmware Interface — or UEFI. (See Woody Leonhard’s Jan. 19, 2012, Top Story, “Say goodbye to BIOS — and hello to UEFI!”)
UEFI has been around for years, but early versions (mostly in Vista- and Win7-era PCs) usually simply mimicked classic BIOS, perhaps with a few extra features thrown in.
Version 8 was the first Windows to fully exploit UEFI. The OS’s Secure Boot feature uses UEFI to make the boot process resistant to unauthorized changes by malware and other factors. (See the Microsoft article, “Securing the Windows 8 boot process.”)
(I’ll discuss UEFI in a bit more detail later. But for now, as shorthand, I’ll use “BIOS” to refer to both the classic BIOS and UEFI.)
Virtually all PCs have a boot-order setting in BIOS that lets you define the sequence of devices a PC should access at startup. The PC checks each listed device, one after another, looking for an operating system to boot from. Typical boot devices include a hard drive, optical drive, USB drive, and the network.
Obviously, if the standard, hard drive–installed version of Windows won’t boot correctly, you want to ensure that the system looks for the rescue disk first. So to boot from a rescue CD or DVD, the PC’s optical drive should be listed first in BIOS’s boot order.
Or, to boot from a rescue drive, the first device in the list should be a USB drive.
Two ways to change a system’s boot order
Virtually all pre-Win8 PCs — and even some Win8 systems — offer two easy ways to change a PC’s boot order.
First method: At the very start of bootup, most PCs display an on-screen message that says something such as Press {some key} to select Boot Device (see Figure 1).

Figure 1. On this system, pressing the F12 key selects the boot device.
On my test system, it’s the F12 key; on other PCs, it could be any other key or key combination. (Note: This is not the key combination that pops up the BIOS settings. You’ll use the BIOS settings for the second method described below.) Press the key or keys for your particular machine. You should then see a boot-order menu — something similar to the example in Figure 2.

Figure 2. A typical boot-order menu. Simply press the designated key to boot from a listed device.
Next, simply select the device you want to boot from. In the example shown (your PC’s options could be different), you’d press the c key to boot from your rescue disk in the optical drive.
The selection you make in this menu is one time only. At the next boot, the system will revert to its normal boot order.
Second method: As noted above, this option uses the BIOS settings menus. It’ll let you make boot-order changes semipermanent.
Again, at the start of the boot process, look for the on-screen message that states something along the lines of Press {some other key} to enter BIOS setup. Press whatever key or key combination opens your BIOS settings editor.
Boot-order settings are usually on a page or screen labeled Boot (or something similar); you then change the boot order by rearranging the listed devices. (See Figure 3.)
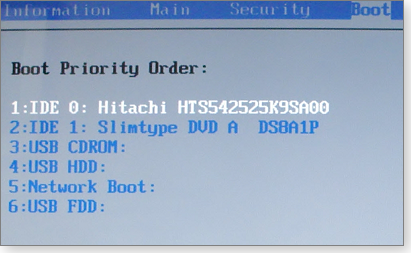
Figure 3. Virtually all PCs let you set the default boot order in BIOS.
Following the on-screen directions, place the device you plan to use for the rescue disk at the top of the list. When you’re done, save your changes and exit the BIOS settings, typically by pressing the F10 key.
Your system should now restart and boot from the rescue disk. Keep in mind that the new boot-device order will stay in effect until you alter it again.
If neither of those methods works on your pre-Win8 PC and it doesn’t show any obvious way to change boot order, visit the vendor’s online support site and search for instructions specific to your brand and model of PC. Good search terms to use include access BIOS, enter BIOS, and edit BIOS.
Working around Windows 8’s Secure Boot
As mentioned above, most UEFI-based Win8 systems enable a special, tamper-resistant startup that locks down the boot process and is designed to prevent unauthorized modifications. This Secure Boot feature makes the use of a rescue/repair disk a bit more complicated.
For example, to change boot order, it usually takes a few extra steps simply to get into the UEFI settings. Then, you must disable Secure Boot entirely if you want to ensure that a PC can boot from a non-Microsoft repair disk or drive.
Here’s one easy way to accomplish both tasks in Win8.1. (Win8.0 is very similar; for specifics, see the Oct. 3, 2013, LangaList Plus.)
- Save and back up all your work; close all running apps.
- Open the Charms bar, click the gear icon (Settings) and then click Change PC settings at the bottom of the bar.
- On the PC settings page, select Update and recovery.
- Click Recovery and then, under Advanced startup, click Restart now. (Despite the terminology, your PC will not immediately restart — that’s normal.)
- On the Choose an option screen, click Troubleshoot and then click Advanced options.
- If a UEFI Firmware Settings option appears, select it. (It might also be under a somewhat different label, such as Change UEFI Settings.) If no such option exists, skip the rest of these steps.
- On the UEFI Firmware Settings screen, select Restart.
- Your PC will restart and run the built-in UEFI setup utility.
- UEFI settings often look much like classic BIOS setup pages — and typically work in much the same way. Follow the on-screen directions for navigating to and selecting the settings you’re going to change.
- The UEFI boot-order settings are usually under the Boot section (or something similar). As above, change the PC’s boot order so that the optical drive or a USB drive is at the top of the list. Your options will likely look something like those shown above in Figure 3.
- Next, if you’re going to use a non-Microsoft rescue boot disk, disable Secure Boot. The Secure Boot settings are often found under Security (see Figure 4), Boot, Authentication, or something similar.

Figure 4. Secure Boot is typically enabled by default. Select Disabled to use a non-Microsoft rescue/repair disk.
- When you’re done, save your settings and exit (typically by pressing the F10 key).
- Your system should now restart and boot from the rescue disk. If you disabled Secure Boot, the system will also bypass Win8’s normal boot restrictions.
- When you’re done testing your rescue disk — or when you’ve finished using it in a real emergency — re-enable Secure Boot via the steps above.
If there’s no UEFI Firmware Settings option in Windows 8’s Advanced options screen, your particular system might use a different method for accessing UEFI settings — such as the old-school trick of pressing a specific function key during initial boot.
Some PC brands use a special OEM tool or dashboard, often accessed from the Windows Start menu, that lets you access the UEFI boot settings, either immediately or after a reboot.
If none of those options is offered, visit the PC vendor’s online support site and search for instructions specific to your brand and model of PC.
For more information on managing Win8’s Secure Boot, see:
- “Secure Boot overview” – MS TechNet article
- “Windows startup settings” – MS Windows 8 article
- “Boot a PC in UEFI mode or legacy BIOS-compatibility mode” – TechNet article
Two advanced tips for Windows 8 users
I wish I could give advanced tips for all Windows versions, but most emergency rescue/repair disks are take-it-or-leave-it propositions. You get whatever comes on the disk, and that’s that. There’s usually no way to alter the disk’s contents.
However, Win8’s Recovery Media Creator is different. As noted in Part 1 of this series, it lets you add your own custom recovery image to the recovery drive.
This lets you do more than just boot and repair your PC; you can also use the recovery disk for a custom Refresh (a nondestructive reinstall) or custom Reset (full reinstall) of Win8. For more on Refresh and Reset, see these two related Top Stories: Aug. 15, 2013, “A ‘no-reformat reinstall’ for Windows 8,” and Sept. 12, 2013, “A clean-slate reinstall for Windows 8.”
Tip 1: How to create a custom recovery disk:
- If you haven’t already done so, create a custom recovery image by following the steps in the Oct. 10, 2013, Top Story, “Creating customized recovery images for Win8.”
- Next, create a new, empty folder inside the root folder of your C: drive; name it Win8-Recovery (in other words, create C:\Win8-Recovery).
- Copy your new custom recovery image from wherever you placed it (typically in a RefreshImage folder) and paste it into the C:\Win8-Recovery folder. Then rename the pasted file as INSTALL.WIM (i.e., C:\Win8-Recovery\INSTALL.WIM).
- Open an admin-level command prompt — e.g., press Win + X and select Command Prompt (Admin.
- Enter the following command to register the copied/renamed INSTALL.WIM file as the recovery image on your PC:
REAGENTC /SetOSImage /Path C:\Win8-Recovery\INSTALL.WIM /Index 1
- Use the Win8 Recovery Media Creator to create a new recovery drive, following the steps in “Emergency repair disks for Windows: Part 1.” When prompted, enable the Copy the recovery partition from the PC to the recovery drive option; your custom recovery image will then be added to the new recovery drive.
(For more detail, see the Microsoft Answers thread, “Windows 8.1 and making a USB Recovery Drive.”)
Tip 2: This second tip lets you get around a limitation in Win8.1’s Recovery Media Creator.
As mentioned in Part 1 of this series, Win8.1’s Recovery Media Creator can make only a recovery flash drive; whereas the 8.0 version of the tool is able to create bootable CDs or DVDs — as well as a recovery flash drive.
But Win8.1 users can get what amounts to a free rescue/repair DVD directly from Microsoft! Simply download a free, 90-day evaluation copy of Win8.1.
Prior to the download, you have to provide an email address and answer a few basic questions, but there’s no cost whatsoever.
The evaluation copy is an .iso file, which you can burn to a DVD. The resulting disk is bootable and fully functional. It also includes a Repair your computer option (see Figure 5) that’s equivalent to the standard repair tools created by Win8’s built-in Recovery Media Creator.

Figure 5. The Win8.1 evaluation edition is bootable and fully functional. As highlighted above, it contains the standard complement of Win8 repair/restoration tools!
The free evaluation copy of Win8.1 is available to anyone. Download your copy via a Microsoft TechNet page. (Note: The download is for the Enterprise version, but the boot and repair tools work on any Win 8 version. You can boot from the Enterprise disks and use the basic repair tools as they are. You also can use the Enterprise boot disks to refresh or reset your system from your own system’s images.)
A rescue disk for all reasons — and all Windows. This two-part series should help all users of Windows — from XP on — recover from problems such as malware attacks to complete hard-drive failures — and everything in between. Make sure you have an emergency rescue disk or drive ready and waiting.
Playing with winter snow — in August
 |
A good many people in the northern hemisphere are happy about cherry trees, tulips, daffodils, magnolias, fritillarias — you name it — in bloom. Lengthening April days and more sun switch on giddy moods for northerners. A few people haven’t had their fill of winter adventures in snow. If you’re one of them, here’s a video to give you someplace to aim for in coming months: Arthur’s Pass in New Zealand, where the snow might be deep enough to give you joy in June, July, August, September — sometime in the southern winter. Click below or go to the original YouTube video. |
| Post your thoughts about this story in the WS Columns forum. |
Is it worthwhile to upgrade an XP-era PC?
How practical is it to upgrade XP-era hardware with more modern components capable of running Windows 7 or 8?
Plus: Preserving an XP setup as an .iso file, self-destructing cookies for Firefox and IE, and running Android as a native Windows app — no virtual PC required!
The pitfalls of upgrading XP-era hardware
Richard Grimme wants a discussion on refurbishing older PCs.
- “How about a series of articles on upgrading a typical XP computer to something that could run Windows 7? The typical XP machine probably has something like a 1GHz P4 processor and a 40GB drive.
“Sure, it’s nice to have the most powerful PC available, but who really needs it? The typical user probably runs a word processor, spread sheet, and maybe some basic games.”
Richard, I’m all for keeping old gear going — when it’s practical to do so. And I’ve never recommended buying new gear just because it’s new.
In fact, I have some Vista-era systems that are still in daily service running Win7. They’re slow but are perfectly acceptable as backup systems. I’ll continue to use them until they die — or until Win7’s end of life. (See Microsoft official Windows life cycle info.)
But refurbishing or upgrading very old, XP-era PCs is probably not cost-effective. Almost everything in such systems should be replaced.
Cooling fans and hard drives that have spun millions of times are likely near the end of their service life. Aging power supplies succumb to the myriad small surges and sags they suffer. With thousands of heating and cooling cycles, the insulation inside components becomes brittle; it cracks and leads to short circuits. Chips eventually malfunction because of the cumulative effects of overheating. The list goes on and on.
If you haven’t replaced peripherals along the way, they’ll also eventually fail and add to the cost of refurbishing an old system. But more problematic might be the drives for new printers and other devices — they might not be compatible with older hardware.
Practically speaking, the only part of an old PC that doesn’t eventually wear out is the metal case!
Ultimately, the total cost of repeatedly repairing/upgrading an XP-era PC will probably be more than the cost of a new machine — especially if you add your labor to the equation.
Think of your PC the way you think of your car. If you need a new engine, transmission, and so on, keeping it alive is a marginal proposition. Your XP system is equivalent to a ’57 Chevy. Yes, you can keep it running indefinitely, but only with extraordinary effort and expense.
If your XP-era hardware is still working, a better option is to use it as a spare or backup. An alternative solution is to sell it or give it away so it can still find productive use until it inevitably dies. Purchase a new, fully up-to-date replacement PC for your “daily-driver” use. There’s no reason it has to be a high-octane muscle machine — a modestly priced system should be more than sufficient for the average PC user.
What’s important in a new PC is that it use current technology, be compatible with current software, and come with a solid warranty.
Here are some places that will accept working PCs that are too old for practical upgrading:
- Dell Reconnect (Goodwill)
- Best Buy recycling
- Staples recycling
- Electronics donation and recycling guide (EPA)
- How to donate your computer to charity (HowStuffWorks)
Preserving an XP setup as an .iso file
Maurice Carson wonders about turning his XP setup into an .iso file on CDs or DVDs — for safekeeping and easy restoration.
- “I have just reinstalled windows XP and have gone through all the updates. I now have a clean, fully updated system that I would like to back up. Do I make an .iso, and if so, how do I go about that process?”
You can make an .iso copy of your hard drive, but that’s not usually the best option.
A better solution is to use a system imaging tool, designed specifically for backing up and restoring complete PC operating systems. For the most part, .iso files are a type of CD-based image that’s not really optimized for any one purpose.
There are plenty of free system-imaging tools that will run on an XP PC. Here are a few options:
- Macrium Reflect (site)
- Paragon Backup & Recovery 2014 (site)
- Clonezilla (site)
- DriveImage XML (site)
If you still want to create an .iso file, a free tool such as ImgBurn (site) will run on your XP system. The ImgBurn Guides pages can assist you with the process.
Self-destructing cookies for Firefox and IE
Joe O’Loughlin likes an add-on for the Firefox browser — and he’s seeking something similar for Internet Explorer.
- “The Firefox add-on, ‘Self-destructing cookies,’ (site) automatically removes no-longer-needed and unwanted cookies. It works well.
“I’m looking for a similar add-on that works with Internet Explorer, but I can’t seem to find one. There are plenty of do-it-yourself suggestions, but that’s the rub — I need one for IE that works automatically.
“Am I beating a dead horse, or is there something that does the job?”
Like you, John, I’d rather not beat a dead horse. But a tool I’ve mentioned dozens of times — CCleaner (free/paid; site) — can automatically eliminate cookies in all the major browsers — not just Firefox. It can also clean up myriad other temp files, useless Registry entries, and so on.
In the free and paid versions of CCleaner, the Options/Settings dialog box lets you set the tool to automatically remove cookies and other junk files on a user-definable schedule — and/or every time Windows starts.
CCleaner’s paid version also offers an additional Options/Monitoring dialog box that lets you schedule automatic cookie-deletion for every time you close a browser or every time a browser’s junk files grow past a user-definable point.
It’s up to you: using a single-purpose/single-browser cookie cleaner is fine. But I prefer a general cleanup tool that does much more than clean just one type of junk file for one brand of browser.
Running Android as a native Windows app
In the March 13 Top Story, “How to run Google’s Android OS on a Windows PC,” I described running Android inside a VirtualBox virtual PC.
Sophie Hamilton wrote to tell us of an entirely different method: one that lets Android run as a native Windows application — no virtual machine software required!
- “I wanted to point out that there’s an even better way to run Android on Windows, using a program called Windroy (site).
It runs the Android kernel directly, which makes it really, really, fast. And you don’t need to mess with VirtualBox to get it working. The Android file system is also directly accessible in Windows.
“It runs in full-screen mode by default. You can, however, change it to run windowed — though to do so you need to set the environment variable: WINDROY_RESOLUTION. I currently have it set to 480-by-800. I also edited my /system/build.prop file to set the DPI to be similar to that of a phone. (You need to add a line such as ro.sf.lcd_density=210.)
“If you want the Back/Home/Apps keys to show up, you’ll also need to add the line — qemu.hw.mainkeys=0′ line — to the /system/build.prop file
“That said, Windroy might not be the best way to run Android, because it doesn’t have Google Play. So adding new apps ranges from hard to impossible. It’s a shame!”
Thanks, Sophie. Windroy is a very clever bit of programming. And, as you say, it’s very fast!
But, significantly, because Windroy runs directly in Windows, with access to the Windows system’s drives and other devices, it could be dangerous. Any problems or malfeasance that happens in Windroy — or in the apps Windroy runs — could affect the host Windows PC.
In contrast, the Android-x86 version that I described in the Top Story runs safely inside a virtual PC, where it’s well isolated from Windows. Problems that arise inside the virtual PC are unlikely to have any effect whatsoever on the Windows host.
And, of course, Android-x86 is a complete implementation with full access to Google Play and the one million-plus apps available there. As you state, Windroy lacks the features of a full-blown Android implementation.
Windroy is worth discussing for experimenters and readers who like to live dangerously. Again, it is a clever bit of coding! But I think Android-x86 is a much better choice for most users wishing to run Android on a Windows PC.
Thanks for the tip!
Taking Microsoft's Office for iPad for a spin
![]()
![]()
By Michael Lasky and Lincoln Spector
Over 150 million is not a market size that anyone can ignore — not even Microsoft. That’s the number of iPads in use, many of them at work.
Bowing to the obvious, Microsoft released Office for iPad on March 27 via the Apple App Store. It’s a good start, but there are, of course, some serious limitations.
The three faces of Office for iPad
Although Microsoft is promoting “Office for iPad,” there’s actually no single app with that name. Office for iPad is offered as three separate apps: Word, Excel, and PowerPoint. You can download and install whichever of the three you want. Many iPad/Windows users will recall that Microsoft tested the waters with OneNote for iPad about a year ago.
According to the information in the App Store, the three new Office for iPad apps are free. But Microsoft isn’t that generous; you need an Office 365 account to use them in any meaningful way. Without an Office 365 account, the three apps are nothing more than document viewers. (Microsoft’s licensing essentially allows Office 365 on one tablet for every licensed PC or Mac. That is, Office 365 Home lets you install the suite on up to five systems — PCs and/or Macs — plus five tablets. You’ll find more about Office 365 on its MS site.)
The iPad, as with all tablets, has always been more about consumption than production. It’s used mostly for reading, watching videos, listening to music, and checking email. It’s not an ideal platform for writing major reports or crunching vast fields of numbers.
But the iPad is well suited to displaying business documents and making minor edits; for these tasks, Office for iPad is a good choice. The look and feel of the programs are true to Office 2013, yet they also adhere nicely to the iPad’s touch interface. The suite offers an acceptable set of editing tools, though nothing close to what you get with the desktop versions.
There’s also a deal-breaker for some iPad users: you must have iOS 7 or higher installed. That leaves a few million first-generation iPads out in the cold. (Oddly, when we tried to install Word for iPad on a first-generation tablet, an error message popped up stating that the iPad needed a front-facing camera. That’s a bit creepy.)
Keep in mind that the Office for iPad apps have the typical Microsoft bulk. Installing all three takes up about 675MB (Word, 246MB; Excel, 223MB; and PowerPoint, 205MB) of your iPad’s precious memory.
If you plan to regularly edit Office documents on an iPad, here’s a recommendation: invest in one of the many Bluetooth keyboards available. Entering small changes via the iPad’s onscreen keyboard is doable but far less efficient than using a physical keyboard. Apple offers a small Bluetooth-enabled keyboard (more info), but there are others such as the ZAGG Universal Keyboard, reviewed in the March 27 Best Hardware article, “Gadgets fill in mobile computing’s missing links.”
The dark cloud: OneDrive to rule them all
(Kudos to Fred Langa for that Tolkienesque line!)
If Office for iPad has a major flaw, it seems to be an intentional one. All three apps are tied tightly to Microsoft’s cloud storage service, OneDrive. If Office for iPad is going to be effective, users need to be able to share documents, spreadsheets, and presentations between the desktop and the tablet — and Microsoft has made sure OneDrive is the only way to do so. You really have no other choice. (Office 2013 at least gives you the option of not saving to OneDrive by default.)
Microsoft can get away with this because Apple’s iOS lacks an open file system. For the most part, data files on iPads are tied to specific applications. You can move a file from app A to app B only if app A allows it. And if app A is Word, Excel, or PowerPoint, it doesn’t allow it.
Using OneDrive on the iPad (Figure 1) is seamless. You can download and open a file with one command. When you save the file, the app updates it in the cloud as you type. (Autosave is set by default. If you switch off Autosave in the File menu, a Save button appears. You must, of course, then remember to manually save your edits.)
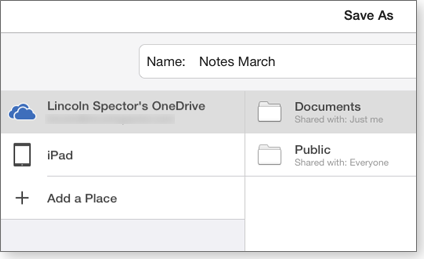
Figure 1. Microsoft's OneDrive for iPad is essentially the only way to manage Office for iPad documents.
On the other hand: if you use, say, Dropbox, you won’t be happy. To edit a spreadsheet, for example, you typically have to find it in the iOS Dropbox app, tap it, and wait until the file downloads and displays. You then tap the Share icon and select Open In/Open in Excel. That opens the file in Excel, but you can’t change it until you’ve saved it in either OneDrive or Excel’s local storage on the iPad.
There are only two ways to get the file back into Dropbox. Either email it back to yourself (or someone else) or upload it to OneDrive. Then, when you’re back at your PC, download the spreadsheet and put it back in Dropbox, where it belongs.
And until you complete that somewhat arduous task, you’ll have two separate versions of the file. You could, if you’re not careful, end up with multiple, diverging versions of the same spreadsheet.
Word for iPad: Powerful — by tablet standards
If you regularly use Microsoft Word on a PC, you’ll find the iPad version comfortably familiar. In many (sometimes subtle) ways, it acts like Word; there’s the desktop version’s ribbon, but whittled down to accommodate the smaller tablet screen.
As soon as you start typing, you feel at home. The first letter in a sentence capitalizes itself automatically; common typos correct themselves; and the ribbon tabs provide formatting and other options.
But Word for iPad has only five tabs instead of nine on the desktop. And there are far fewer options under each tab. For instance, the Home tab lets you select a style but not alter it or create a new one. The View tab (Figure 2) is especially barren, with options only for Spelling, Ruler, and Word Count — there are no zoom, split, or document views such as Draft or Outline.
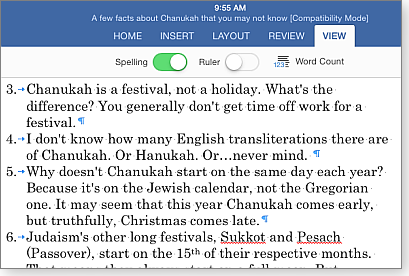
Figure 2. Word for iPad's View tab has far fewer options than what's offered in Word for Windows.
On the other hand, the Review tab (see Figure 3) is clear and simple, and it helps you track changes easily. (The app has an odd and amusing quirk that goes back to much older generations of Microsoft Word. Type =rand(x) [where x is any number], and you’ll get x repetitions of that famous typing exercise, “The quick brown fox jumps over the lazy dog.”)

Figure 3. Word for iPad's somewhat odd mix of commands includes an easy-to-use Track Changes — plus some Word Basic formulas, used in this example to automatically create multiple copies of boilerplate text.
Searching for text is also relatively easy. Tap the magnifying glass icon and type what you want to find. A tool icon offers some simple but important options (see Figure 4).

Figure 4. Word for iPad's easy-to-use Find options
Word for iPad doesn’t handle macros in any way, shape, or form. And though it has an autocorrect feature, you can’t add your own corrections.
Word for iPad supports templates — sort of. When you create a new document, you get a screen full of templates. But they’re all standard Microsoft templates, starting with New Blank Document. You can’t add your own or alter the ones already there.
There is a workaround: upload your template folder to OneDrive. Then, when creating a new file, tap Open rather than New, go to the Templates folder on OneDrive, and select the template of your choice. Word will then create a new document based on that template.
However, you still can’t alter the template; that has to be done on a PC.
One puzzling feature of the app is the Layout tab’s Size function, which adjusts documents to different paper sizes such as letter, legal, and so forth. It’s puzzling because printing is conspicuously missing from all Office for iPad apps. They don’t support the iPad’s Wi-Fi-based AirPrint. Even the OneDrive iPad app does not include a Print option. There are a few workarounds, noted below.
It’s also important to know that Word for iPad converts .doc files to .docx.
If you use voice dictation, Microsoft has attempted to link its Office apps to Apple’s Siri. Press the microphone icon next to the onscreen keyboard’s spacebar, and your spoken words will be transcribed into Word text. It was, at least in our case, surprisingly accurate.
Excel and PowerPoint: More of the same
Excel for iPad: When you load an Excel spreadsheet of any complexity into Excel for iPad, you’re likely to get some sort of message reminding you of the app’s limitations. The message might say, “This document contains unsupported content. To edit a copy without this content, tap Duplicate.”
Or maybe you’ll get this: “Some content will not be available in this version of Excel. Duplicating this file will remove workbook sharing and tracked changes from this document.”

Figure 5. A warning that highlights Excel for iPad's numerous limitations
Perhaps you’ll be told that “This workbook can’t connect to external data or it contains macros that will not run in this version of Excel.”
In other words, Excel for iPad is a far more limited version of the powerful Windows application. You can’t, for example, sort data in the iPad-based Excel.
That said, as with Word, Excel for iPad retains a look and feel similar to the desktop version while adapting to the touch-and-swipe tablet environment. A typical spreadsheet’s many small cells often make editing a dicey proposition. But selecting cells in Excel for iPad with a fingertip was surprisingly accurate.
Spreadsheets are all about numbers. So Microsoft had to make some accommodation for the iPad’s onscreen keyboard. The solution is a keypad toggle that switches the QWERTY keyboard to a number keypad that also has a good selection of symbols and navigation keys.
When using Excel on an iPad, knowing what will still work within your downloaded, originally Windows-based worksheets will take some experimentation. Macros and pivot tablets might be out, but most formulas, math functions, and charts should remain intact.
Adding formulas into an iPad-based Excel spreadsheet is actually easier than on Excel for Windows. The Formula tab offers eight pull-down menus from which you can select functions by type. It’s clear, simple, and easy.
PowerPoint for iPad: Microsoft might have run out of time or energy by the time it got to its presentation app. It’s a ghost of the full desktop version. Displaying presentations and making minor changes is easy enough. But try any serious work, such as adding additional slides, and the app quickly falls short.
The Insert tab, for example, lets you add slides, tables, pictures, shapes, and text boxes — but not charts, equations, or videos (see Figure 6). In fact, in our tests, presentations downloaded from the desktop PowerPoint are stripped of their animations and video content. The style and color options are less extensive as well.

Figure 6. PowerPoint for iPad's limited insert options
On the other hand, PowerPoint for iPad does offer a generous supply of transitions (Figure 7), which might give the illusion of animation within and between slides.

Figure 7. PowerPoint for iPad's diverse selection of transitions
Ultimately, you probably shouldn’t even consider creating a presentation in PowerPoint for iPad. It’s usable for last-minute corrections to presentations when you’re on the road and for giving the actual presentation (if you have the correct, Apple-approved, video connector). Moving from slide to slide is easily handled with simple screen swipes. Miscellaneous other touch gestures let you navigate around the app — most of which you’ll probably find through trial and error.
Tip: Printing workarounds for iPad Office apps
Printing directly from the iPad requires an AirPrint-enabled Wi-Fi printer. Assuming you have one, the next step is to print your documents from an iPad app that supports printing. A number of online storage services such as Dropbox, Box, and Google Drive offer iPad versions that support AirPrint. To find other apps that enable iPad printing, type printing into the search box in the App Store — numerous apps should pop up. Some of these apps are free; most charge a small fee.
One solution is Cloud Browser, which consolidates popular online storage sites — including OneDrive. From this app you can open files stored in OneDrive for iPad, then use its built-in printing capability to do what Office for iPad can’t: Print!
The bottom line: As we stated at the top, Office for iPad is off to a good start — as long as you understand the limitations. Some of those shortcomings are concessions to the iPad platform. Others might simply be Microsoft’s need to keep you connected to the full Office apps — and drive Office users into Office 365 subscriptions.
Whatever the reason, the Office for iPad suite will be handy for business iPad users who want to spruce up their work while on the road.
Shedding some light on security-cert warnings
On a daily basis, we are bombarded with confusing error messages that can lead to making bad decisions about our online security.
Whether from Java, our browsers, EMET, or some other source, here’s what you should know about the warnings.
Sorting out problems with Java security
I live in California, where the car is king — a MINI Cooper, in my case. At a stop light, I’m fully aware that red means stop, green means go, and yellow means slow down (in theory; this is California, after all). If only warnings on our computers were that clear and simple. All too frequently, our Web browsing is interrupted with confusing security warnings — not just from websites but also from Web-enabled devices and, more recently, Java-enabled platforms.
Many of these warnings lack any real explanation, making it difficult to understand the security consequences of the options we’re offered.
For example, after the recent Java V7 Update 51 has been installed, Java apps need to be signed with a digital security certificate. If they’re not, they’ll be blocked from running. I ran into this problem with my Western Digital My Cloud network-storage device; it would no longer run its Java-based, mapped-drive application. Instead, I received an error message stating: “Java error: Missing required Permissions manifest attribute in main jar.” (Is that obtuse, or what?)
The workaround for the missing certificate was to place an exception in the Java control panel. (I don’t recommend following Western Digital’s instructions to lower the security settings, as noted on its help site.)
Unfortunately, where to put that exemption was at first elusive. According to the Java instructions, it’s located in the Java control panel, under the Security tab (see Figure 1). But it wasn’t there. Eventually, I discovered that I had both 32-bit and 64-bit Java installed. Removing the 64-bit version revealed the previously missing exemptions control.

Figure 1. If the exemptions list doesn't show up under the Security tab, check that you have only one version of Java installed.
Enter application exemptions with the following steps:
- In Windows, click Start/Control Panel/Java and open the Java control panel.
- Click the Security tab, then click Edit Site List in the lower half of the dialog box.
- Enter the problematic site’s or application’s URL. In the case of the balky WD My Cloud app, I entered the drive’s address, as shown in Figure 2. (The URL will, of course, be different for any other device.)

Figure 2. To exempt Java-based sites or apps from being blocked, simply add their URL to the exception site list.
- Click OK to save your changes and exit.
The process can get more complicated for network administrators. For example, to continue using some remote-access tools, they’ll need to enter the URL for remote servers. Tools that use self-signed certificates need to be exempted. Two examples are HP’s iLO server-management app and Dell’s DRAC remote-access card/app.
Interpreting common webpage warnings
Almost everyone who’s gone onto the Web has at one time or another received that annoying — and often confusing — error message: This page contains both secure and nonsecure items. “Fabulous. Now what do I do?” you grumble. “Ignore the warning? What’s really going on?”
A Troy Hunt blog post provides a succinct answer — plus a more informative, longer explanation. He points out that the message is not really about security; it’s more about bad coding.
Webpages often pull content from more than one server. (Ads and content, for example, often come from separate webservers.) The main part of the page is designed to download over a secure https: connection using Secure Sockets Layer encryption. But a component of the page is trying to make an unsecured connection. That could defeat the security of the entire webpage.
A properly coded page uses either http: or the more secure https: throughout. (Troy notes that this is an issue for all browsers.) A fully SSL connection ensures that all content comes from the correct servers and that no content was inserted by an unsecure — and possibly malicious — webserver.
What can you do about these confusing error messages? Not much — the problem can be fixed only by the website’s coders. In most cases, if you skip past the warning, you just won’t see the content downloaded over http:.
EMET 4 puts up warnings about Facebook
If you’ve installed Enhanced Mitigation Experience Toolkit (EMET) Version 4, you might have seen warnings, shown in Figure 3, about an untrusted Facebook certificate — not on Facebook but on sites that have social-networking share buttons or “Like” buttons. (Anyone who has upgraded to EMET 4.1 or to the newly released EMET 5 preview should not see these warnings.)

Figure 3. An error caused by an expired certificate-pinning rule
The source of the warning is an EMET 4 certificate-pinning rule that expired on Dec. 31, 2013. Certificate pinning has been in Google Chrome since 2011 but was only recently added to EMET. As noted in a Random Oracle post, “Pinning addresses [the problem of potentially bogus security certificates] by allowing a website to commit in advance to a set of [certificate authorities] that it will do business with.”
In other words, pinning sets the specific SSL certificates that a site will trust and accept. EMET adds the ability to add expirations to SSL certificate pinning. But it never really explains the related warning. It would be better for all users if EMET noted that its pinning rule needed to be updated — or, in this case, that we need to update to a newer EMET version.
The situation became more complicated after it was revealed that EMET 4.1 can potentially be bypassed by malicious hackers, as reported in a Feb. 25 PCWorld article. You might consider downloading and testing EMET 5.0 (site) — but only if you use Chrome as your default browser and don’t plan on watching YouTube videos.
When I tested EMET 5.0 on IE and attempted to watch various videos on YouTube, the site crashed. I received an error message (see Figure 4) — “EMET detected ASR mitigation in IEXPLORE.EXE Component: Adobe Flash Player 12.0 r0” — that’s discussed in an 0xdabbad00.com post.

Figure 4. An EMET 5.0 error that crashed YouTube
Given that I was trying to watch Pharrell Williams’s Happy (Official Music Video), I was not especially happy that I needed to roll back to EMET 4.1 — at least for the time being.
Hardening up security certificates in Windows
Recently, Microsoft started pushing out updates that remove older encryption protocols. In February, it released KB 2862973 for Windows Vista, Win7, Win8, and Windows RT plus Windows Server 2008, 2008R2, and 2012. The update restricts the use of root certificates with MD5 hashes (more info). You must have KB 2862966 installed before deploying this update.
I recommend installing this update; it’ll increase the security of those SSL certificates that Windows blindly trusts — simply because it trusts the originating root certificate. So far, I’ve seen no side effects from either update.
Initially, I believed KB 2862973 was needed only for managed networks. But after a closer look, I now think it’s best that we all tighten up the screws on SSL certificates — and ensure we remove older encryption standards to protect ourselves from spoofed root certificates.
Hardened enforcement of signed code coming
Although we installed KB 2893294 (MS13-098) this past December, the patch won’t go into effect fully until June 10. On that date, as noted in an MS Security Research and Defense blog post, installers are harden; application code will be considered unsigned if its installer doesn’t conform to the new verification process. After June 10, you might need to disable this enforcement to install older, noncompliant applications.
Noncompliant UEFI Modules
Also this past December, Microsoft released KB 2871690, an update for Windows 8 and Windows Server 2012 that revokes the digital signatures for nine private, third-party UEFI (Unified Extensible Firmware Interface) modules that could be loaded during UEFI Secure Boot. Secure Boot protects your system from rootkits; or, as noted in a TechNet article, it helps ensure that a PC boots using only firmware trusted by the PC manufacturer.
However, some users reported in a Microsoft Answers forum that they couldn’t install KB 2871690 without receiving an error. The patch would install only if they disabled Secure Boot, installed the update, and then turned Secure Boot back on.
It now appears that Microsoft revised the update to fix that issue. The source of the problem seems to be an improperly signed security certificate.
In the end, you have to trust your instincts
I spend a lot of time working with PC and network security. But even I get confused by some of the error messages popped up by various websites. My recommendation: Go with your gut feeling. Exit a site if you don’t feel comfortable with any error messages that might appear. That’s especially the case when new security warnings pop up with sites you’ve previously visited. The safest policy is to leave the site and close down the browser to clear it.
For example, in early January, Yahoo banner ads were infected with code that injected Java-exploiting malware. The malicious ads were served up by Yahoo’s own service: ads.yahoo.com, as reported in a ZDNet blog.
Also consider adding Web-based filtering by using such services as OpenDNS. Changing your router’s DNS entries to point to opendns.com will help block malicious websites.
To quote Michael Conrad’s character in the TV series Hill Street Blues: “Let’s be careful out there!”
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Office gets current release
by
Susan Bradley
6 hours, 40 minutes ago -
FBI: Still Using One of These Old Routers? It’s Vulnerable to Hackers
by
Alex5723
23 hours, 12 minutes ago -
Windows AI Local Only no NPU required!
by
RetiredGeek
7 hours, 43 minutes ago -
Stop the OneDrive defaults
by
CWBillow
1 day ago -
Windows 11 Insider Preview build 27868 released to Canary
by
joep517
1 day, 9 hours ago -
X Suspends Encrypted DMs
by
Alex5723
1 day, 12 hours ago -
WSJ : My Robot and Me AI generated movie
by
Alex5723
1 day, 12 hours ago -
Botnet hacks 9,000+ ASUS routers to add persistent SSH backdoor
by
Alex5723
1 day, 13 hours ago -
OpenAI model sabotages shutdown code
by
Cybertooth
1 day, 13 hours ago -
Backup and access old e-mails after company e-mail address is terminated
by
M W Leijendekker
1 day, 1 hour ago -
Enabling Secureboot
by
ITguy
1 day, 8 hours ago -
Windows hosting exposes additional bugs
by
Susan Bradley
1 day, 21 hours ago -
No more rounded corners??
by
CWBillow
1 day, 17 hours ago -
Android 15 and IPV6
by
Win7and10
1 day, 7 hours ago -
KB5058405 might fail to install with recovery error 0xc0000098 in ACPI.sys
by
Susan Bradley
2 days, 9 hours ago -
T-Mobile’s T-Life App has a “Screen Recording Tool” Turned on
by
Alex5723
2 days, 12 hours ago -
Windows 11 Insider Preview Build 26100.4202 (24H2) released to Release Preview
by
joep517
2 days, 7 hours ago -
Windows Update orchestration platform to update all software
by
Alex5723
2 days, 19 hours ago -
May preview updates
by
Susan Bradley
2 days, 7 hours ago -
Microsoft releases KB5061977 Windows 11 24H2, Server 2025 emergency out of band
by
Alex5723
1 day, 22 hours ago -
Just got this pop-up page while browsing
by
Alex5723
2 days, 12 hours ago -
KB5058379 / KB 5061768 Failures
by
crown
2 days, 9 hours ago -
Windows 10 23H2 Good to Update to ?
by
jkitc
1 day, 11 hours ago -
At last – installation of 24H2
by
Botswana12
3 days, 11 hours ago -
MS-DEFCON 4: As good as it gets
by
Susan Bradley
9 hours, 12 minutes ago -
RyTuneX optimize Windows 10/11 tool
by
Alex5723
3 days, 23 hours ago -
Can I just update from Win11 22H2 to 23H2?
by
Dave Easley
1 day, 22 hours ago -
Limited account permission error related to Windows Update
by
gtd12345
4 days, 13 hours ago -
Another test post
by
gtd12345
4 days, 13 hours ago -
Connect to someone else computer
by
wadeer
14 hours, 32 minutes ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

