
|
There are isolated problems with current patches, but they are well-known and documented on this site. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Exploring Windows’ Administrative Tools: Part 4
In this issue
- TOP STORY: Exploring Windows' Administrative Tools: Part 4
- LANGALIST PLUS: How to recover from an accidental reformat
- LOUNGE LIFE: FTC takes on telephone scareware scammers
- BEST HARDWARE: For your health: Finding an ergonomic keyboard
- WACKY WEB WEEK: Not your ordinary road hazards in Scandanavia
- PATCH WATCH: Clerical error causes huge Patch Tuesday ripple
Exploring Windows' Administrative Tools: Part 4
The Windows Task Scheduler can run almost any program automatically — at a time and in a way you set.
Task Scheduler is part of Windows’ Administrative Tools, a suite of professional-quality, system-management utilities used to adjust and control many of the operating system’s essential functions and features.
Starting with XP, these tools are either built into Windows or are offered as free add-ons. This guide to using Task Scheduler is the fourth installment in our Windows Administrative Tools series.
Part One of the series explains what the tools are and how to make them easily available from the Windows Start menu.
Part Two discusses Windows’ Performance Monitor, which reports in real time what’s happening within the OS as programs run — or fail to run!
Part Three describes how to use Windows’ Memory Diagnostic tool to thoroughly test your system’s random-access memory.
I’ll focus on the Windows 7 version of Task Scheduler because that’s the OS most Windows Secrets readers are currently running. Windows XP’s and Vista’s Task Schedulers are similar, so many of the instructions given below also apply to those operating systems. I’ll also include links for Vista- and XP-specific information.
The basics of how Task Scheduler works
To understand how Task Scheduler automatically runs defined tasks, you have to understand triggers. In many cases, a trigger is simply a specific time when Task Scheduler should run a task. You set both the time and the task. Time-based triggers can be once-only (such as “at 8 p.m.”) or repeating (“every Tuesday at 8 p.m. for the next 52 weeks”).
There are, however, other kinds of triggers — for example, system events (such as startup, sign-on, sign-off, or shutdown) or just about any kind of error condition.
You can define any number of tasks. For example, you might have Task Scheduler run a cleanup tool at every system shutdown, automatically launch Windows Network Diagnostics when a connection fails, or start a malware scan late at night when your PC is otherwise idle.
Task Scheduler can do much more than merely launch a program. Obviously, once a program is launched, you want it to actually do something — not just idly sit there.
To specify what the program should do once it’s running, you use special commands — technically called command line inputs or arguments — which are really nothing more than plain-text equivalents of the mouse clicks normally used to control a program.
In short, any program that accepts command-line inputs can be controlled via Task Scheduler.
An app’s online support pages will tell you what command-line inputs are allowed — if any — and how to use them. Here are two examples:
Piriform’s CCleaner clean-up tool accepts a few command-line inputs; they’re listed and explained on the app’s advanced usage page. You can, for instance, use Task Scheduler to automatically run CCleaner and then shut down Windows when CCleaner is done.
Searching the Microsoft site, you’ll find that Windows’ Remote Desktop Connection (RDC) accepts command-line inputs. An MS Help & How-to page lists supported command-line options.
Searching a publisher’s support pages will sometimes reveal that there are two versions of an app — one with a normal graphical user interface and another, nongraphical version specifically intended for command-line use. That stripped-down version will work nicely in Task Scheduler. (I’ll give an example below.)
Other ways to discover command-line inputs
Although querying a software publisher’s site is the best and surest way to discover which command-line inputs are allowed, some programs will list the inputs they’ll accept — if you ask them the right way. Here’s how:
From an administrator-level account, open a command window. (Need help? Check out Microsoft’s online Command Prompt FAQ.)
Next, inside quotation marks, type the full path and name of the program you wish to control. After the trailing quotation mark, add a space, forward slash, and question mark.
For example, to see what command line inputs are accepted by Windows’ built-in defragmentation tool, defrag.exe, type:
“c:\windows\system32\defrag.exe” /?
Press Enter, and defrag will then list all the command-line inputs it can accept.
If the /? option doesn’t work with a given program, try -h (which stands for -help) as an alternative.
For example, to see what command line inputs you can use with the 7-Zip file compression and encryption utility, you type:
“c:\program files\7-zip\7z.exe” -h
Press Enter. 7-Zip will then list all the command-line inputs it can accept.
If a program fails to respond to either the /? or -h options, it’s likely the program does not accept command-line inputs — and thus cannot be controlled via Task Scheduler.
Real-life example: custom antivirus scanning
In the Sept. 20 LangaList Plus item, “A fine-tooth comb process for malware removal,” I mentioned using Task Scheduler “to set up a full, weekly MSE [Microsoft Security Essentials] scan in the middle of the night so … there’s absolutely no impact on my productive use of the PC.”
Many readers wrote, asking for instructions for how to do just that. So I’ll use scheduling automated MSE scans as a simple Task Scheduler example.
If you search the Microsoft site for command-line options for MSE (for example, a Microsoft Community page), you’ll see that MSE is one of those tools that exist in two versions — and both automatically install on your system when you download MSE. The first, msseces.exe, is the version typically seen with the full graphical interface; MpCmdRun.exe is a stripped-down version specifically intended for use with command-line inputs.
The aforementioned Microsoft Community page lists the command-line inputs that MpCmdRun.exe supports, but you also can find them by using the direct-query technique described earlier. In fact, seeing the direct-query syntax can make it easier to set up MSE in Task Scheduler, so let’s take a look.
Assuming you have MSE installed on your system, open an admin-level command window and type:
“C:\Program Files\Microsoft Security Client\MpCmdRun.exe” /?
You’ll see a list of all the command-line inputs that MpCmdRun accepts. Those of immediate interest include the -scan command, which tells MSE to perform a scan; the -scantype option, which defines the type of scan; and the 2 option, which initiates a full scan.
So here’s the complete, plain-text command to tell MSE to launch and perform a full scan:
“C:\Program Files\Microsoft Security Client\MpCmdRun.exe” -scan -scantype 2
With that information in hand, the hard part’s done. Now, all that’s left is to feed that command into Task Scheduler.
It’s easy; here’s how:
- Step 1: Open Task Scheduler. Click Start/Control Panel/System and Security. Under Administrative Tools, click the Schedule tasks link. (Or select it from the Start menu’s Administrative Tools, if you’ve set it up.)
- Step 2: When Task Scheduler opens, click the Create Basic Task option in the right-hand pane, highlighted in Figure 1. (You’ll probably see tasks for other apps in the center Task Scheduler pane, automatically created when the apps were installed.)

Figure 1. Task Scheduler's Create Basic Task can handle the vast majority of task-scheduling needs.
- Step 3: In the Create a Basic Task dialog box, give your new task an obvious name and enter an optional, fuller description, as shown in Figure 2. Click Next when you’re done.
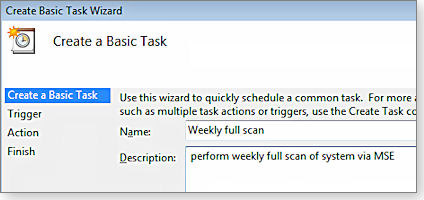
Figure 2. Give your tasks meaningful names and descriptions to avoid confusion with tasks you might create later.
- Step 4: In the Task Trigger window, select the instance or frequency with which you want to run the task. In this case, you’re setting up a weekly scan, so you should choose the Weekly trigger, as you’ll see in Figure 3. Click Next when you’re ready to move on.

Figure 3. Choose when or how often the task is triggered.
- Step 5: If you selected a frequency, the next windows lets you further refine the task’s schedule (see Figure 4). Here, I’ve set the scan to run every Sunday at 3 a.m. Click Next when you’re done.

Figure 4. With a weekly trigger, you can choose specific days and times.
- Step 6: Now select what should happen when the task is triggered. For our example, you want Task Scheduler to Start a Program — that is, to launch MSE. (Figure 5.) Click the “Start a program” button and then click Next.

Figure 5. The Action dialog box gives you three task choices.
- Step 7: Fill in the Start a Program specifics window. Use the command-line information you obtained earlier, as shown in Figure 6. Click Next when you’re done.

Figure 6. This example shows the command-line options (in Add arguments) required to run a full MSE scan.
- Step 8: Double-check the information in the Summary display, as shown in Figure 7, and click Finish to finalize your new task. Checking Open the Properties dialog for this task when I click Finish (before clicking Finish) will let you make additional tweaks to your task.

Figure 7. The Open the Properties … check box gives more task options.
- Step 9: The new task’s Properties window includes security options, as shown in Figure 8. For an unattended MSE scan, select Run whether user is logged on or not and Run with highest privileges. Click OK when you’re done. (Because you specified Run with highest privileges, you’ll be asked for your admin password when you click OK.)

Figure 8. Use the task's Properties dialog to refine how you want the task to run.
- Step 10: You’re almost done! But first, take a moment to check your work. In the center pane of Task Scheduler’s main window, scroll through the Active Tasks list (shown in Figure 9) and find the task you just created. Double-click the new task and double-check its settings.

Figure 9. In the Active Tasks pane, you can review the settings of all tasks.
- Step 11: Controls in the Selected Item pane (lower-right of Task Scheduler windows) let you run, end, disable, and delete the task. In this case, click Run (highlighted in Figure 10) to test the new task. If you need to make changes, use the tabbed area of the central pane to edit the task’s triggers, actions, conditions, and settings until things work the way you want them to.

Figure 10. Select your new task and click Run to give it a test drive.
Note: In this example, you’re running the nongraphical, command-line version of MSE, so you won’t see MSE’s usual display window. The only immediate indication that MSE is working will be the heavy disk activity that’s typical of a full scan.
- Step 12: Once your test scan appears finished, launch MSE’s normal graphical interface and check the Last scan text at the bottom of the main dialog window (see Figure 11). It should show that a full scan was just completed.
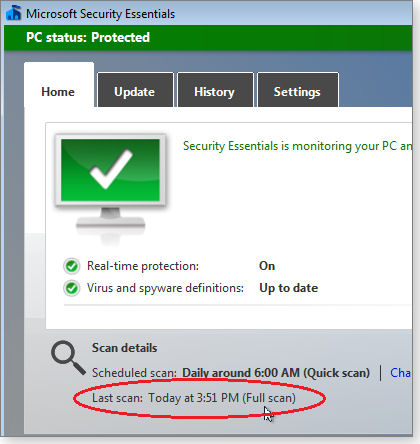
Figure 11. The Last scan notification in the standard (graphical) version of MSE confirms that Task Scheduler launched a full AV scan.
Advanced: Use system events as triggers
You may have noticed in Figure 3 that you can use specific system events as task triggers. System events include the starting and stopping of all programs and drivers, all errors, most user-initiated actions, and more. Windows assigns each system event an event ID. If you know an event ID, you can specify it as a task trigger.
There are literally thousands — perhaps tens of thousands — of event IDs, and (alas) there’s no single, central database containing them all.
But here are the best sources for event-ID information that I’ve found:
- MS TechNet’s Events and Errors listing
- MS Support’s “Look up an error message” page.
- MS TechNet blog, “How to find all possible event ID’s for a given event source”
- UltimateWindowsSecurity.com’s listing of Windows Security Log Events
- And this simple, but very complete, event ID lookup page from EventID.net
Digging deeper for Win7, Vista, and XP
There’s plenty more information available online for users of all skill levels and for all current versions of Windows.
Here are some great resources:
- MS support article 308569, “How to schedule tasks in Windows XP”
- MS TechNet article, “Windows Vista Task Scheduler”
- MS Help & How-to article, “Schedule a task” (Vista)
- MS Help & How-to article, “Schedule a task” (Windows 7)
- MSDN Task Scheduler page
- MSDN Task Scheduler 2.0 page
Once you get the hang of it, you can use Task Scheduler to have Windows automatically do just about everything — except make the coffee!
How to recover from an accidental reformat
Deleting a file you need is bad enough, but accidentally deleting your entire hard drive is truly awful.
Fortunately, there are many unformat tools that can restore some, most, or even all of the erased data.
An accidental reformat wipes out drive
Reader George Blalack had a very bad day:
- “Fred, I accidentally did a quick format of my Windows 7 drive.
“I know there is software out there that can restore the files (some even restore the file folder directory structure), but I thought the best start was to clone the drive using imaging software. That way, I could try to restore my files using the clone. If the results [of one application] don’t give me a rebooting drive, I could try other software to restore the files and structure.
“I tried the paid version of Acronis on my XP machine, but it said it would not work. I’m also concerned that it will move data around and make the drive not 100 percent recoverable. Do you know of any imaging software that will work?”
I know of no imaging software that copies the residual data left over from files that have been deleted through reformatting. Although imaging software makes an exact replica of the contents of the current disk structure, it treats empty space (such as space where files used to be) as, well, empty.
In other words, if you make an image of your reformatted disk, that image will be an exact duplicate of the reformatted disk, period. It won’t contain any data from the previous format.
I think your best bet is to obtain and use a partition-recovery tool (sometimes called unformat software) right away. If all you did is a quick format, a partition-recovery tool has a good chance of recovering all or most of your previous format and data. With a little luck, your disk will be exactly as it was before the reformat.
Partition recovery can be easy if the reformatted partition isn’t the one you boot from. (The boot partition is usually C:). If, say, you reformatted your D: partition, simply boot your PC normally and then download and run a reputable partition-recovery tool from your regular C: partition.
But you say you reformatted your “Windows 7 drive,” and I take that to mean you formatted your boot partition (probably your C: drive). That’s a little harder to fix because you need a working operating system to run the recovery software. Your reformatted drive doesn’t have an OS installed, and you don’t want to reinstall an OS because you’d be overwriting the data that you hope to recover.
If this is your situation, you have two options. The harder one is to physically remove the drive and install it as the secondary drive in a different, working PC. Then run partition-recovery software on that PC. The much easier approach is to run partition-recovery software from a bootable CD/DVD or flash drive on your reformatted PC.
You can choose from many recovery tools, but one is especially noteworthy: EaseUS Partition Recovery (site) is free and has an excellent reputation — its partition-recovery wizard makes it point-and-click simple to use. EaseUS also offers a good, free Partition Recovery Tutorial section (follow the links on the same page) to walk you through the recovery process.
Because you need to recover your boot partition, note EaseUS’s Partition Recovery WinPE Bootable Disk how-to. It shows how to set up a bootable copy of Windows — along with a copy of the EaseUS partition-recovery tool — on a CD or DVD. Of course, you’ll need to use a second computer to download the software and set up the CD/DVD. But once that’s done, you can boot your damaged system from the CD/DVD and then run the recovery tool to restore your C: partition.
If you don’t like the EaseUS tool, you have many other choices. For example, WinSite (info page) offers several free partition-recovery tools. Or you can try TestDisk (site), a free open-source tool for recovering lost partitions and/or making nonbooting disks bootable again.
All these alternative tools come with their own instructions, and you also can use the EaseUS how-to procedures as general templates for partition recovery with other tools.
Your favorite Web search engine can also link you to many other recovery tools. Start with search terms such as partition recovery and unformat.
Certain partition-recovery tools require a second data-recovery tool to complete the restoration of the files and folders within the recovered partition. Just follow the instructions that accompany the tool of your choice, and — with just a little bit of luck — you’ll soon have your deleted partition, files, and folders back!
The time to make a complete image backup is after everything’s restored. Should this sort of thing ever happen again, you can restore the image and get your PC working in almost no time.
For more help, see the May 12, 2011, Top Story, “Build a complete Windows 7 safety net.” That article includes links for XP and Vista-based backup and imaging as well as for Win7.
Alternate fix for Chrome/Flash crashes
After reading the Sept. 26 item, “Fixing Chrome when Flash repeatedly crashes,” Alan Atwood sent in this tip, which suggests a completely different way to correct the problem:
- “I can’t take credit for this tip. But from personal experience, I know it works — and I think it might be an alternative to fixing crash issues with Flash under Chrome worth considering.
“See the article, ‘How To Fix Shockwave Flash Crashes in Google Chrome,’ at HowToGeek.com.
“I won’t cut and paste the entire tip here, but it boils down to opening up the about:plugins settings page in Chrome and disabling the internal version while leaving the standalone version enabled. The method cuts down a lot of steps and doesn’t require the uninstall and reinstall of either the Chrome browser or the standalone Flash plugin.”
Thanks, Alan. Looks like this would be the thing to try first when Flash crashes in Chrome. If it works, great! If not, then the longer, more-certain method I described should do the trick.
Do-it-yourself easy passwords
Valerie Simons sends in her technique for creating easy-to-remember but hard-to-guess passwords.
- “I took the advice in an old Windows Secrets article and devised a strong password of the following elements:
“[my initials][old house number][initials of personal nickname][non-alpha character][three-letter acronym of the site].
The first elements are constant; the last varies by site.
“For example, let’s say John Doe used to live at 456 Main Street, and his friends call him Stretch. His password might be JD456S*mic on the Microsoft site, and JD456S*eba on the eBay site. Very strong, consistent, and easy to maintain.”
That’s good, Valerie. Your method puts you light-years ahead of most users: unbelievably, the world’s most common password is still 123456. (See Imperva.com’s analysis of 32 million hacked passwords.)
The principal danger in your method is that it follows a predictable pattern. That makes it easier for you to remember, but it also makes it easier for someone to crack — either from knowing you (e.g., social engineering) or from stealing your passwords from two sites at which you’re registered and then finding the common elements in your passwords.
That’s not an extremely high risk, and so this easy-to-use method of password generation is probably fine in most cases — especially on nonbanking, noncommerce, and otherwise low-risk sites (sites where you’re not performing monetary transactions, entering financial data, and so on).
For high-risk sites, I still prefer a totally random password. My preferred tool is RoboForm (site), but the next letter (below) shows a popular alternative.
It’s a matter of degree and how secure you want to be. But as I said, you’re already doing far, far better than most people!
Free password-keeper and -checkers
Gary Zellerbach writes:
- “I use a different password for almost all websites and keep track of them using Password Safe, a free, open-source program that is easy to use, offers very strong encryption, and can even fill in user names and passwords with a single click when you return to websites. Even better, there’s an Android app (built by a third party) for it, so I can securely access my passwords on the go.
“It’s on the Sourceforge Password Safe site.
“Now all I have to remember is one (very long but very safe) password to access all other my passwords. I ran my master password through one of those password-strength evaluators online, and the test said it would take several billion years to crack my password — so I think I picked a good one!”
Thanks, Gary!
Many sites online can check your password strength. Naturally, for maximum safety, you should use only password-checker sites that you trust — otherwise, you’re giving away your password to strangers. It also makes sense to submit for testing a variation on your real password rather than the actual one itself.
Microsoft offers a free password-checker webpage, and I believe it to be safe to use.
Other popular, free password-testing sites include testyourpassword.com, GRC.com, passwordmeter.com, and Rumkin.com).
We all need passwords — make sure yours are good ones!
|
Readers Alan Atwood, Valerie Simons, and Gary Zellerbach will each receive a gift certificate for a book, CD, or DVD of his or her choice for sending the tips we printed above. Send us your tips via the Windows Secrets contact page. |
FTC takes on telephone scareware scammers
Perhaps you’ve been cold-called by a “representative” of Microsoft, Dell, McAfee, or some other large, reputable computer software or hardware manufacturer. The caller tells you something is wrong with your computer.
Thanks to six lawsuits filed last week by the FTC, you might get fewer of those calls for a while. In the Security & Scams forum, Lounge member BruceR posted a link to an Ars Technica article reporting the FTC complaints against tech-support scammers. See the link and follow the discussion in the forum.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right in to today’s discussions in the Lounge.
For your health: Finding an ergonomic keyboard
If you spend a lot of time working at your PC, you’re very likely to suffer a computer-related physical ailment eventually — if you haven’t already.
There are ways to prevent these workstation-induced injuries, and they start with the keyboard.
Good habits for comfortable computing
Keeping to a minimum the wear and tear of working hours at a PC requires a comprehensive approach. You need regular stretch breaks to keep the muscles moving in new directions and the blood flowing. You need the right equipment — chair, monitor, mouse, and keyboard. And you need to arrange them correctly to reduce stress on your hands, arms, back, neck, and eyes.
Your chair should be comfortable, with strong back support and armrests, The seat should be low enough so that your feet rest on the floor but high enough so your knees are level with your hips. The center of your monitor should be just below the height of your eyes. And the keyboard should be at a comfortable level for your hands when your arms are on the chair’s armrests. For more advice, see the Office Ergonomics pages on the WebMD website (info) and the Mayo Clinic website (info).
But a conventional keyboard, even if properly positioned, can still do you harm. Unless you have extremely narrow shoulders, you have to turn your arms inward to reach the home keys, putting your fingers at an angle. Plus, because the keyboard itself is not angled, you have to turn your wrists outward. If the keyboard isn’t slanted correctly, you have to turn your wrists up or down as well.
Fortunately, not all keyboards are conventional. You can buy an ergonomic keyboard to help protect yourself from the ravages of typing. Some are shaped to be more comfortable for the average human. Others are adjustable, so you can make them comfortable for you.
In researching this article, I tried five ergonomic keyboards, using each one for two full weeks of regular work. Each had a unique design and a consequently unique learning curve for the user. Although they all used the standard QWERTY layout, each keyboard put auxiliary keys such as Delete, Backspace, and Home in different locations.
Here are the three keyboards that I can recommend:
Natural Ergonomic Desktop keeps hands down
Most keyboards slant upward, so that the function keys are higher than the spacebar. But if you hold your hands out naturally, you’ll notice that your fingers face down.
Someone at Microsoft also noticed that and designed a keyboard that slopes downward as it goes back so that the spacebar is higher than the function keys. Microsoft also gave its Natural Ergonomic Desktop (NED) keyboard a gentle crest between the G and H keys, which gently rotates your hands into a more comfortable position. Unlike some split keyboards, such as the Goldtouch V2 discussed below, the shape of the NED isn’t adjustable (though it does have extendable rear feet to raise the back of the keyboard). But overall, the NED does a good job of placing keys where your fingers naturally rest.
Microsoft offers two models of the NED with identical layouts. The 4000 (info) costs U.S. $50 and connects via a USB cable; the 7000 ($120 info) is wireless and comes with a wireless, ergonomic mouse. I tried the 7000.

Figure 1. The Natural Ergonomic Desktop 7000 is nicely curved to fit your hands. —Source: Microsoft
The 4000/7000 may be the largest keyboard I’ve ever used. Although average in width, the keyboard measures more than 10 inches from back to front and rises more than three inches from the surface of the desk. It barely fit on my keyboard tray, crowded as it was by the tray’s built-in wrist support.
You could do just fine without the tray’s wrist support because this keyboard comes with an extremely comfortable, padded wrist support of its own. With your wrists on it, your fingers naturally point downward on the keys.
The 4000/7000 has the most conventional layout of any ergonomic keyboard I’ve tried. All the standard keys to the right of the QWERTY layout — arrows, Insert, Home, and the number pad — are right where you’d expect them. This is good for the learning curve but not for ergonomics. Average keyboards — and the 4000/7000 — put too much space between the QWERTY keys and your mouse (assuming you’re a right-handed mouser). This distance forces you to either bend your right arm too far out for mousing or too far in for typing.
But this keyboard still comes with a learning curve. I found that it took a while to get used to an N key that’s larger than the Enter key.
The NED comes with some nice, extra buttons, including a zoom control and five numbered buttons that bring up the first five applications on the task bar. But it lacks buttons to skip to the next song on your playlist or back to the last one. Worse, the keyboard lacks indicator lights. When you press CapsLock or NumLock, an onscreen message flashes only briefly to tell you of your new status.
The Natural Ergonomic Keyboard 4000 is considerably cheaper than the other keyboards I looked at, and many people will find it extremely comfortable. But it lacks the versatility of the adjustable keyboards I’ll talk about next.
The Goldtouch V2: Twist and type
At first glance, the Goldtouch V2 Adjustable Comfort Keyboard looks like a normal keyboard with unusually rounded edges and no number pad. Then you adjust the keyboard to your comfort and discover just how exceptional it is.
This keyboard comes in two versions. The PC-only version (info) lists at $109. The PC and Mac version (info), which is what I tried, costs $119.
The V2 is actually two half-keyboards connected by a ball socket in the top center (between F6 and F7). When you open the lever on the top left, you can adjust the halves, separating them into an inverted V, raising the center of the keyboard (called tenting), or both. When you have it the way you like it, you close the lever and lock the keyboard in place.

Figure 2. The Goldtouch V2 Adjustable Comfort Keyboard lets you set the two halves to your most comfortable position. —Source: Goldtouch
You can also adjust six flip-open feet on the bottom of the keyboard, two of them below the spacebar. You can orient the V2 to slope downward from
front to back, like the Microsoft 4000 and 7000.
The result is a highly adjustable keyboard. It takes a little experimentation to get exactly what you want; when you get it, closing the lever without changing the relative distance and tilt of the two halves of the keyboard can be tricky. But once you’ve got everything the way you want, the keyboard feels great.
Let me put it another way: After I finished researching this article, I returned to the V2. I’m typing on it right now.
Goldtouch designed the V2 to be as small as possible without sacrificing key size or spacing. To do that, they had to eliminate the number pad and move the non-QWERTY keys to new locations. Print Screen, NumLock, and others are on the left; navigation keys (arrows, Home, End, and so on) on the right. You’ll find Delete and Backspace keys on both sides.
The V2 behaves somewhat like a laptop keyboard. NumLock converts several keys on the right side of the keyboard to numbers so that you can type KL and get 23, which is startling the first time you do it by accident. You can hold down the Fn key and press a function key for a feature otherwise not available. For example, the key combination Fn+F3 plays or pauses your music. Blue icons on the keys tell you what they do when you press them in combination with Fn.
Similar, gold icons may confuse you. They’re for using the keyboard with a Mac.
The learning curve for this keyboard isn’t formidable. It took me a while to adjust to the Delete key’s location, which is much higher than on a standard keyboard. And every so often, I still hit the down arrow unintentionally.
But this is an extremely comfortable keyboard.
Kinesis Freestyle2: Complete separation
The Kinesis Freestyle2 (info, $99) takes keyboard-splitting to a whole new level. Once you remove a simple plastic joint (and yes, it’s intended to be removed), the two pieces are connected only by a nine-inch cord. You can extend your arms straight out and still reach the keys.
This gives you even more versatility than with the Goldtouch V2 — at least on a horizontal plane. You can also set the two halves at any angle to one another and keep your mouse between the two halves, if you want.

Figure 3. The Kinesis Freestyle2 takes the split keyboard to a new level. —Source: Kinesis
However, that much separation can really affect your typing habits. For the first couple of hours on the Freestyle2, I averaged about three typos a word. That didn’t last, although — as with the V2 — learning the locations of the non-QWERTY keys took longer.
Like the V2, this keyboard comes with a laptop-like Fn key as well as a NumLock key that turns letters on the right side of the keyboard into numbers. Two columns of extra keys on the left provide some handy features. With one key press, you can copy, paste, or go back and forth between sites on the Web.
But there are other typical keyboard features that I missed. For example, although you can mute sound and control volume with Fn and some function keys, the Freestyle2 offers no easy way to pause or play your music.
Here’s an ergonomic problem: the Freestyle2 lies flat. You can’t tent it or even fold out legs to give it a slight slant. Kinesis sells three different tenting accessories for the Freestyle2, ranging in price from $25 to $199. (To find them, go to the info page and scroll down). But I figured out a cheaper solution. I put a stack of magazines in the middle of my keyboard shelf, and they provided the tenting for me. That worked fine.
If you’re particularly broad-shouldered, the Freestyle2 makes a very good choice. But have some magazines handy!
An ergonomic keyboard can go a long way toward keeping you comfortable. But it’s only one piece of a healthy computing lifestyle. And now, if you’ll excuse me, it’s time for my exercises.
Not your ordinary road hazards in Scandanavia
 |
By Kathleen Atkins If you sometimes find yourself irked by your commute to work, microblogger Stevan Svartling has chronicled a mythic Monday morning ride of his own to help you keep yours in perspective. He forgot his sunglasses, of course. And there were goats and sheep on the bridge. But how many times have you encountered trolls, as Stevan did, on your way to the office? Play the video |
Clerical error causes huge Patch Tuesday ripple
We have our work cut out for us this Patch Tuesday. A missing piece of information in code-signing certificates means that many of the updates we’ve already installed will be reoffered.
What started out as a relatively mild Patch Tuesday has suddenly turned severe — and Microsoft indicates this might not be the last of it.
2749655
Security certificates will expire prematurely
As reported in a Microsoft Security Research & Defense blog, numerous MS digital certificates released in the past few months have faulty timestamp attributes. The error code will cause the certificates to expire too soon. The good news is that this debacle is not a security threat. Without an update, however, you might run into problems with future MS software patches. According to the blog, the correctly re-signed updates are MS12-053 through MS12-058 (more on these updates below).
Here’s a bit of history on this problem. Between June 12 and Aug. 14, a subset of binaries (translation: the files in some of the updates we received between June and August) had faulty digital signatures. A core component of the Windows security system, these signatures ensure that malware can’t enter your system via Microsoft Update or Windows Update.
The process resembles the words of that old children’s song: “The toe bone’s connected to the foot bone.” A code-signing server issues digital signatures to new software. With a valid code-signing key and timestamp, Windows knows that the software can be trusted and will install and/or run it. The software remains trusted until its timestamp expires. Unfortunately, in this case, the affected files will expire prematurely — within a few months.
As the SRD blog puts it, the “signing error involved the timestamp placed on each file as it was being signed. The certificate used for timestamping was missing a critical attribute that will cause the digital signature to become invalid at the point in the future when the package’s signing key has expired. Normally, the signing key is valid for a reasonably short amount of time, while the timestamp allows the binary to be trusted as ‘valid’ for a much longer period of time.”
What does that mean for us? Beginning this month and possibly well into the future, Microsoft will reissue updates released between June and August. In the meantime, installing update 2749655 will make Windows trust the flawed-timestamp updates until we’re able to add the fixes.
To repeat: The flaw does not create any new vulnerabilities or problems for our systems. The timestamp fix prevents problems with future updates and with software compatibility.
Interestingly, the timestamp flaw doesn’t impact Windows XP as much as it impacts newer versions of Windows. There are timestamp flaws in Windows XP patches, but only in the update installers. If you’ve successfully added the updates, you don’t need to reinstall anything. Windows Vista, Win7, Server 2008, Server 2008 R2, and various versions of Exchange are not so lucky.
 What to do: Install 2749655 to proactively prevent problems with expiring security signatures.
What to do: Install 2749655 to proactively prevent problems with expiring security signatures.
MS12-058 (2756485, 2756496, 2756497)
MS Exchange Server gets an update re-release
The biggest headache the timestamp flaw has caused for me is repatching my on-premises Exchange (e-mail) server. According to an Exchange Team blog, that means reinstalling critical Update Rollups 4-v2, 7-v2, and 8-v2 (plus an additional fix tossed in).
 What to do: Plan on reinstalling KBs 2756485, 2756496, and/or 2756497 (MS12-058) when you have the time. The original versions of these patches installed slowly — so slowly, some admins tried to cancel the installation in process, with disastrous results. When you’re ready to reinstall them, you’ll find some tips on my blog to make the process go a bit more quickly.
What to do: Plan on reinstalling KBs 2756485, 2756496, and/or 2756497 (MS12-058) when you have the time. The original versions of these patches installed slowly — so slowly, some admins tried to cancel the installation in process, with disastrous results. When you’re ready to reinstall them, you’ll find some tips on my blog to make the process go a bit more quickly.
MS12-053 (2723135)
Few will see the timestamp update for Windows XP
In a confusing bit of events, a Windows XP timestamp-related update fixes a vulnerability in Remote Desktop Services (RDS). But in a plot twist only a mystery author could dream up and only a geek could understand, most XP users won’t see it reoffered.
As noted above, it’s only the installer component of the patch that’s flawed. Assuming you’ve already installed the original patch (rated critical), there is no need to install it again.
 What to do: Install KB 2723135 (MS12-053) only if it wasn’t installed the first time around.
What to do: Install KB 2723135 (MS12-053) only if it wasn’t installed the first time around.
MS12-055 (2731847)
A Windows kernel-mode driver patch do-over
The original update (rated important), reissued in MS12-055, fixed an elevation-of-privileges vulnerability in the Windows kernel. As with the RDS fix above, XP users should see this update only if the patch was never installed. If it was installed, no action is needed. Vista and Windows 7 users will need the revised patch.
 What to do: Install KB 2731847 (MS12-055) if and when it’s reoffered.
What to do: Install KB 2731847 (MS12-055) if and when it’s reoffered.
MS12-054 (2733594)
Networking-components patch impacted
The last security update impacted by the timestamp flaw fixed four vulnerabilities in Windows. An attack using a print-spooler request could allow a hacker to run code remotely and gain access to a system. Again, most Windows XP won’t have to worry about this update.
 What to do: The original patch was rated critical, so install 2733594 (MS12-054) when offered.
What to do: The original patch was rated critical, so install 2733594 (MS12-054) when offered.
Other updates affected by the timestamp flaw
I’m sure that right about now you’re asking, “Why don’t you just give me a list of the impacted updates?” I’d love to, but I can’t find an authoritative list of affected patches. Although Microsoft has clearly identified security updates that need to be reinstalled, there are many other nonsecurity updates — many of which I told you to skip — impacted as well.
Here’s a short list of nonsecurity updates I’ve identified so far. It’s probably not all-inclusive; if you see an MS update dated Oct. 10, chances are good it’s timestamp related. I recommend writing down their KB numbers and then using Windows’ Program and Feature tool (or Windows Update’s View update history) to check whether you’ve already installed any of these optional updates. If you did, reinstall them. If you didn’t, your computer has probably been working fine without them — and will continue to do so.
Optional updates identified so far (the first four are Win7 updates):
- KB 2647753
- KB 2729094
- KB 2732487
- KB 2732500
- WCF Data Services 5.0 or 5.0.1 advisory
 What to do: Investigate whether you’ve already installed any of these nonsecurity updates offered this week. For example, I recommended installing KB 2732500 (a Win7 System Restore problem); if you took my advice, reinstall it.
What to do: Investigate whether you’ve already installed any of these nonsecurity updates offered this week. For example, I recommended installing KB 2732500 (a Win7 System Restore problem); if you took my advice, reinstall it.
Take a pass on all new optional updates for now
Patch Watch readers know my primary Patch Tuesday rule: security updates get installed on the second week of the month, and all other nonsecurity updates are pushed to the end of the month.
Especially because of this timestamp mess, I recommend delaying installation of the following nonsecurity updates unaffected by the timestamp flaw:
- KB 2731771; fixes time issues in websites
- KB 2739159; Windows 7 file-encryption corruption problem
- KB 2756822; a time-zone update for Windows
 What to do: Pass on all new nonsecurity updates for now — except, of course, KB 2749655 (the top item in this Patch Watch), which is technically a nonsecurity update.
What to do: Pass on all new nonsecurity updates for now — except, of course, KB 2749655 (the top item in this Patch Watch), which is technically a nonsecurity update.
MS12-064 (2553488, 2687314, 2687315, 2687483, 2687485)
Critical update for Microsoft Word
There are, of course, new security updates released this Patch Tuesday that are not part of the timestamp mishap. We start with a Word fix that impacts all Windows versions of Office, starting with 2003. The patch in MS12-064 prevents attackers from using malicious rich–text format (RTF) files to gain full access to systems — for example, if you open an RTF file in Outlook’s preview pane and Word is set as default viewer.
Office for Mac and MS Works 9 users are spared this update, but SharePoint 2010, the Microsoft server product that allows for document sharing, will need it. Word 2007 users will receive an additional patch, KB 2687314, for the Office Compatibility pack.
Microsoft Works 9 is also left out of the attacks; Microsoft thus recommends installing it as soon as possible.
 What to do: Microsoft anticipates attacks within 30 days, so install the appropriate patch in MS12-064 as soon as possible. If you can’t apply the patch immediately, adjust Outlook so it does not preview files in RTF format; an MS support article explains how to set it to plain-text previews.
What to do: Microsoft anticipates attacks within 30 days, so install the appropriate patch in MS12-064 as soon as possible. If you can’t apply the patch immediately, adjust Outlook so it does not preview files in RTF format; an MS support article explains how to set it to plain-text previews.
MS12-066 (2687439, 2687440, 2687436, 2687417, 2726382, 2726388 and 2726384)
Patching a bit of Microsoft Office 365
If you are an Office 365 subscriber, you probably have (but might not use) Lync, Microsoft’s instant-messaging and remote-communication server. Lync shares a bit of code, the HTML Sanitization Component, with MS InfoPath, SharePoint 2007/2010, and Office Web Apps. (The component parses HTML to produce content in a browser.) A new vulnerability in HTMLSC could let an attacker gain admin-level privileges in PCs. There are multiple patches in MS12-066, all rated important.
This vulnerability is possibly a preview of more attacks on cloud deployments such as Office 365. An MS SRD blog notes, “We have seen limited, targeted attacks attempting to leverage this vulnerability against Microsoft online services.” (However, there are no reported attacks using the HTMLSC vulnerability — yet.)
 What to do: To be completely protected from this exploit, you need both one or more patches in MS12-066 and one or more of the fixes listed in the previous item (MS12-064).
What to do: To be completely protected from this exploit, you need both one or more patches in MS12-066 and one or more of the fixes listed in the previous item (MS12-064).
MS12-069 (2743555)
Kerberos flaw causes denial of service
Windows’ Kerberos server is used for network authentication. A vulnerability in Windows 7 and Server 2008 could result in a denial-of-service attack. This is not an update I’ll lose any sleep over. To sucessfully use this exploit, an attacker must already be inside your network — which is why this update is rated only important.
 What to do: Install KB 2743555 (MS12-069) when you have time.
What to do: Install KB 2743555 (MS12-069) when you have time.
MS12-065 (2754670)
MS Works threatened by Word documents
Open a Word document with Microsoft Works 9, and you could get an infection that would give a cyber criminal full access to your computer. Rated important, the patch changes the way Works 9 converts Word files.
 What to do: If you use Works 9, install KB 2754670(MS12-065) as soon as possible.
What to do: If you use Works 9, install KB 2754670(MS12-065) as soon as possible.
MS12-068 (2724197)
Another Windows kernel flaw leads to attacks
Affecting current versions of Windows up to (but not including) Win8, this new kernel vulnerability could give a hacker full access to your system. However, the fix is rated only important because the attacker must sign in to a PC and run a malicious bit of code.
By itself, this exploit is unlikely. But it’s one more tool in a long list of Stuxnet-type, blended-attack entry points that might be used to target specialized systems.
 What to do: Install 2724197(MS12-068) when offered.
What to do: Install 2724197(MS12-068) when offered.
MS12-067 (2553402), MS12-070
Two security updates for more-obscure MS products
The patch in MS12-067 impacts SharePoint (an MS product for sharing documents) servers that have FAST Search Server 2010 installed. Workstations probably won’t receive this update.
The 2005 and 2012 versions of SQL Server, Microsoft’s ubiquitous database program, are threatened by a cross-site-scripting exploit in which an attacker tricks the victim into clicking on a malicious link. That action could then send the victim to a website with other malicious components.
There are many applications — large and small — that use SQL Server, so you might see KB 2754849 (MS12-070) in Windows Update — but only if you’re running SQL Server Reporting Services (an app I’ve rarely seen installed on the workstation version of SQL).
 What to do: Because both patches are rated important and they’re rather uncommon, pass on KB 2553402 (MS12-067) and the appropriate update in MS12-070 for now.
What to do: Because both patches are rated important and they’re rather uncommon, pass on KB 2553402 (MS12-067) and the appropriate update in MS12-070 for now.
2661254
Windows security certification enhanced
In another chapter of the ongoing certificate-hardening saga, MS has finally released an update for the minimum certificate key length allowed. With the update installed, Windows will recognize only certificate keys of 1024 bits or more.
It’s unlikely you’ll see cert keys with fewer than 1024 bits; most certificate vendors now require 2048 bits or more.
 What to do:This is an unusual circumstance where I recommend installing the patch — though not immediately. I don’t anticipate any problems with KB 2661254, but it’s prudent to wait a week or so for any reports of problems.
What to do:This is an unusual circumstance where I recommend installing the patch — though not immediately. I don’t anticipate any problems with KB 2661254, but it’s prudent to wait a week or so for any reports of problems.
2756872
Windows 8 already gets a major update
Windows 8 won’t be officially released until the end of October, but it’s getting a hefty update. Weighing in at 170MB, the patch reportedly fixes performance, power-management, battery-efficiency, media-playback, and compatibility issues.
As noted on the Windows 8 blog, Microsoft has been making changes to Windows 8 as it works with OEM vendors. Typically, Win8 upgraders would not see those fixes until the first service pack. This update keeps upgraders current with OEMs. Sadly, the patch doesn’t include a Start Menu option many early users would like to see.
 What to do: If you’re running Windows 8, stay up to date by installing KB 2756872.
What to do: If you’re running Windows 8, stay up to date by installing KB 2756872.
Regularly updated problem-patch chart
This table provides the status of problem patches reported in previous Patch Watch columns. Patches listed below as safe to install will be removed from the next updated table. For Microsoft’s list of recently released patches, go to the MS Safety & Security Center PC Security page.
| Patch | Released | Description | Status |
|---|---|---|---|
| 2651026 | 02-14 | For XP systems only; February .NET updates; see MS12-016 for complete patch list | Skip |
| 931125 | 03-27 | Root-certificate update for XP | Skip |
| 2553248 | 04-10 | Nonsecurity Office update: Recurring meetings (updated status) | Skip |
| 2553267 | 04-10 | Nonsecurity Office update: Social Connector (updated status) | Skip |
| 2553406 | 04-10 | Nonsecurity Office update: Social Connector (updated status) | Skip |
| 2686509 | 05-08 | Kernel Mode Driver; install issues on XP (updated status) | Skip |
| 2699779 | 06-12 | Office 15 installation fix (updated status) | Skip |
| 2709630 | 06-12 | Network domain sign-in delays (updated status) | Skip |
| 2553272 | 08-14 | Office 2010 stability/performance fixes | Wait |
| 2598289 | 08-14 | Office 2010 stability/performance fixes | Wait |
| 2661254 | 08-14 | Minimum certificate key length | Wait |
| 2553402 | 10-09 | MS FAST Search Server 2010 for SharePoint SP1 | Wait |
| 2731771 | 10-09 | Time-zone conversion | Wait |
| 2739159 | 10-09 | Windows 7 encryption | Wait |
| 2754849 | 10-09 | SQL Server; see MS12-070 for complete patch list | Wait |
| 2756822 | 10-09 | Cumulative time-zone update | Wait |
| 2732487 | 08-14 | Win7 sleep-mode hotfix | Optional |
| 2647753 | 10-09 | Printing core components — timestamp reissue | Optional |
| 2732487 | 10-09 | Segoe font — timestamp reissue | Optional |
| 890830 | 08-14 | Monthly update of MS Windows Malicious Software Removal Tool | Install |
| 2706045 | 08-14 | JScript and VBScript; 64-bit system only | Install |
| 2720573 | 08-14 | MS Office and SQL Server ActiveX controls; see MS12-060 for complete patch list | Install |
| 2722913 | 08-14 | Cumulative IE security update | Install |
| 2723135 | 08-14 | XP SP3 Remote Desktop | Install |
| 2731847 | 08-14 | Windows kernel-mode drivers | Install |
| 2731879 | 08-14 | MS Office CGM graphics files; see MS12-057 for complete patch list | Install |
| 2733594 | 08-14 | Windows networking components; KB 2705219 and KB 2712808 | Install |
| 2733918 | 08-14 | MS Visio 2010 SP1 (KB 2597171) and Visio Viewer 2010 SP1 (KB 2598287) | Install |
| 2740358 | 08-14 | MS Exchange Server; see MS12-058 for complete patch list | Install |
| 2687314 | 10-09 | Office Compatibility | Install |
| 2705219 | 10-09 | Networking components — timestamp reissue | Install |
| 2724197 | 10-09 | Windows Kernel | Install |
| 2731847 | 10-09 | Kernel update — timestamp reissue | Install |
| 2732500 | 10-09 | Win7 System Restore failures — timestamp reissue | Install |
| 2741517 | 10-09 | MS Office (HTML Sanitization Component); see MS12-066 for complete patch list | Install |
| 2742319 | 10-09 | MS Word; see MS12-064 for complete patch list | Install |
| 2743555 | 10-09 | Windows Kerberos server | Install |
| 2749655 | 10-09 | Certificate timestamp proactive fix | Install |
| 2754670 | 10-09 | MS Works 9 | Install |
| 2756485 | 10-09 | Exchange 2003 — timestamp reissue | Install |
| 2756496 | 10-09 | Exchange 2007 — timestamp reissue | Install |
| 2756497 | 10-09 | Exchange 2010 — timestamp reissue | Install |
| 2756872 | 10-09 | Windows 8 cumulative update | Install |
Status recommendations: Skip — patch not needed; Hold — do not install until its problems are resolved; Wait — hold off temporarily while the patch is tested; Optional — not critical, use if wanted; Install — OK to apply.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Office gets current release
by
Susan Bradley
4 hours, 47 minutes ago -
FBI: Still Using One of These Old Routers? It’s Vulnerable to Hackers
by
Alex5723
21 hours, 18 minutes ago -
Windows AI Local Only no NPU required!
by
RetiredGeek
5 hours, 50 minutes ago -
Stop the OneDrive defaults
by
CWBillow
22 hours, 7 minutes ago -
Windows 11 Insider Preview build 27868 released to Canary
by
joep517
1 day, 8 hours ago -
X Suspends Encrypted DMs
by
Alex5723
1 day, 10 hours ago -
WSJ : My Robot and Me AI generated movie
by
Alex5723
1 day, 10 hours ago -
Botnet hacks 9,000+ ASUS routers to add persistent SSH backdoor
by
Alex5723
1 day, 11 hours ago -
OpenAI model sabotages shutdown code
by
Cybertooth
1 day, 11 hours ago -
Backup and access old e-mails after company e-mail address is terminated
by
M W Leijendekker
23 hours, 57 minutes ago -
Enabling Secureboot
by
ITguy
1 day, 6 hours ago -
Windows hosting exposes additional bugs
by
Susan Bradley
1 day, 19 hours ago -
No more rounded corners??
by
CWBillow
1 day, 15 hours ago -
Android 15 and IPV6
by
Win7and10
1 day, 5 hours ago -
KB5058405 might fail to install with recovery error 0xc0000098 in ACPI.sys
by
Susan Bradley
2 days, 8 hours ago -
T-Mobile’s T-Life App has a “Screen Recording Tool” Turned on
by
Alex5723
2 days, 10 hours ago -
Windows 11 Insider Preview Build 26100.4202 (24H2) released to Release Preview
by
joep517
2 days, 5 hours ago -
Windows Update orchestration platform to update all software
by
Alex5723
2 days, 18 hours ago -
May preview updates
by
Susan Bradley
2 days, 5 hours ago -
Microsoft releases KB5061977 Windows 11 24H2, Server 2025 emergency out of band
by
Alex5723
1 day, 21 hours ago -
Just got this pop-up page while browsing
by
Alex5723
2 days, 10 hours ago -
KB5058379 / KB 5061768 Failures
by
crown
2 days, 7 hours ago -
Windows 10 23H2 Good to Update to ?
by
jkitc
1 day, 9 hours ago -
At last – installation of 24H2
by
Botswana12
3 days, 9 hours ago -
MS-DEFCON 4: As good as it gets
by
Susan Bradley
7 hours, 19 minutes ago -
RyTuneX optimize Windows 10/11 tool
by
Alex5723
3 days, 21 hours ago -
Can I just update from Win11 22H2 to 23H2?
by
Dave Easley
1 day, 20 hours ago -
Limited account permission error related to Windows Update
by
gtd12345
4 days, 11 hours ago -
Another test post
by
gtd12345
4 days, 11 hours ago -
Connect to someone else computer
by
wadeer
12 hours, 39 minutes ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

