
|
Patch reliability is unclear, but widespread attacks make patching prudent. Go ahead and patch, but watch out for potential problems. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Find safe-browser technologies that really work
In this issue
- TOP STORY: Find safe-browser technologies that really work
- KNOWN ISSUES: Early adopter of Windows 7 shares his secrets
- WACKY WEB WEEK: The greatest Halloween prank ever
- LANGALIST PLUS: Step by step: reload apps after clean install
- BEST SOFTWARE: Two free removal utilities go head to head
- WOODY'S WINDOWS: Add Windows 7 PCs to Vista and XP networks
Find safe-browser technologies that really work
 By Yardena Arar
By Yardena Arar
The major browsers and security programs all tout their ability to warn you about malware sites before you visit them, but do any of these early-warning systems really work?
Experts say they’re all useful, but none provides a silver bullet — and any browser-security product’s claims of superiority are extremely difficult to verify.
One of the ways browsers and their add-ons combat malware is by tracking sites containing infected files and warning you before your browser opens them.
Safe-browsing products and technologies go by different names: Internet Explorer 8 has a SmartScreen Filter, while Firefox and Chrome use the Google Safe Browsing API. Opera’s built-in fraud protection depends on malware data assembled by Netcraft.
If you use Firefox, the free LinkExtend add-on combines alerts from several site-rating services. You’ll find more information about LinkExtend, plus a download link, on the product’s site. WS senior editor Gizmo Richards described the utility in his March 5 Best Software column (paid content).
These products use different techniques to maintain their data on malware-dispensing sites. The analysts I consulted say each technique is effective, although none is perfect. Determining which one works best isn’t easy — or even possible, according to the experts — because their performances in tests will depend heavily on the samples used.
Johannes Ullrich, director of the SANS Institute’s Internet Storm Center, says all safe-browsing features depend to some extent on what he calls a sensor network. For Google’s Safe Browsing API, the sensor network is composed of the search service’s Web crawlers. Other safe-browsing products rely on a large number of volunteers whose systems report rogue URLs to the mother ship as they encounter them.
Of course, the resulting databases of malware-serving sites are only as good as their most-recent scans or user contributions. When a new malware site comes on line — as they do with alarming frequency — it won’t appear in any malware database for some time.
Different browsers use different malware lists
Google’s Safe Browsing API is based almost entirely on what the search engine’s spiders see. The protection depends, therefore, on how frequently the spiders crawl sites and furnish updates to the Safe Browsing blacklist that’s downloaded to Firefox and Chrome. Because of the potential for slowing down the browser, the latest version of the API provides ways to customize the frequency of blocklist downloads.
The bottom line is that there’s inevitably a lag time between the discovery of a new malware site and the addition of that site to a blocklist update.
Safety-conscious users should consult an on-demand database (which, with a broadband connection, shouldn’t impact your overall browser performance). On-demand lists are the default approach in IE 8 and the latest versions of Opera, but you must turn this capability on in Firefox. When you visit a new site, the browser sends the URL to a server that determines whether the site is in the malware database.
However, some observers — such as the Ha.ckers security blog — believe this approach represents a privacy threat. After all, you do reveal to the browser maker which sites you’re visiting. The SANS Institute’s Ullrich says there’s “no blanket answer” to that concern. “That’s something you have to decide for yourself,” he states.
McAfee’s Site Advisor browser add-on and Netcraft’s blocklists are created primarily through feedback from their users. After all, you’re letting the browser maker know what sites you’re visiting. This may or may not produce faster updates than those generated by Web crawlers, depending on the type of site hosting the malware.
Another variable is the type of malware site the safe-browsing product monitors. Netcraft, for example, is heavily oriented toward collecting URLs of phishing sites — hacker dens that imitate legitimate sites. Phishing sites attempt to trick visitors into entering personal information, such as passwords or Social Security numbers.
This is why Opera uses Netcraft data for phishing sites, but information from Haute Secure for sites that attempt to infect your PC with viruses, Trojans, or other malware.
Internet Explorer 8 sniffs out malware sites
Microsoft greatly expanded its SmartScreen Filter protections in the transition from IE 7 to IE 8. The company’s URL Reputation Service, much like other safe-browing systems, collects the names of known phishing and malware sites. However, SmartScreen flags sites based on their heuristics within IE 8 — something not all the other browser watchdogs do.
The heuristics component may explain why Microsoft trounced the competition in an NSS Labs study (PDF) released last August that tested the effectiveness of various browsers in blocking “socially engineered” Web sites. According to NSS Labs, these are sites that trick users into voluntarily downloading malware — for example, a site purporting to offer a video clip sent to you by a friend.
Spokespersons for Google and Opera state that the companies were unable to replicate the results of the NSS Labs study, which was paid for but not designed by Microsoft.
However, as reported by Erik Larkin in PC World’s security blog — and confirmed to Larkin by NSS Labs — the study didn’t test browser effectiveness in keeping people away from exploit sites. These are sites that take advantage of browser vulnerabilities to install malware without your having to download anything, also known as “drive-by downloads.”
“It’s like rating a car for seatbelts and not worrying about airbags,” said Jordy Berson, group product manager for Check Point’s ZoneAlarm division. Berson adds that drive-by downloads may account for up to 70% of all malware delivery. Check Point’s ZoneAlarm ForceField beta program maintains a database of malware URLs based on the company’s own research, along with malware-site data obtained from Netcraft and RSA.
Of the major browsers, Benson says Chrome offers the best protection against exploits because it uses virtualization technology. Thus, malware loaded through exploits “doesn’t hit the actual machine,” according to Berson. The Chromium blog provides more information on Chrome’s built-in “sandbox” feature.
Is definitive safe-browser testing possible?
Various studies of browser safety produce conflicting results. In a separate study (PDF) released last July, NSS Labs focused exclusively on phishing sites and found IE 8 tied statistically with Firefox 3. Symantec points to a Carnegie-Mellon study (PDF) conducted earlier this year that gives the company’s Norton 360 security suite high marks for quick detection of phishing sites obtained through spam e-mail campaigns. Symantec says its software uses blacklists based on its own Web crawlers, plus user feedback and heuristics.
“It’s always hard to do these studies right,” says the SANS Institute’s Ullrich. So much depends on the test sample, especially on whether the sample uses real sites or a controlled set. Heuristics analysis has a huge edge in the latter case. Safe-browsing studies similar to the double-blind studies medical researchers conduct have never been conducted. Such studies would last a year, and the testers wouldn’t know which technology — if any — they were using.
The lack of a clear winner, Ullrich emphasizes, shouldn’t prelude the use of safe-browsing technologies. He estimates that most of these products will catch about 80% of malware sites. “I don’t think there’s anything that’s better. You do get rid of a lot of the bad stuff, and the performance impact is fairly small.”
Jeremiah Grossman, chief technology officer at WhiteHat Security, is more skeptical. “Personally, I don’t think it [safe-browsing technology] matters that much.” He adds that the modern browsers capable of warning you not to visit malware sites tend to have other malware protections as well. Differences between them, he adds, are likely “slight and meaningless.”
“Where it would have made a difference is with IE 6,” Grossman says.”We have new security features to protect the browser that’s not vulnerable.”
Grossman’s recommendation for safe browsing is to use the popular browser of your choice for routine browsing and a different — and preferably less-targeted — browser for serious transactions. He adds that you should always shut the browser down once the transaction is complete.
Grossman’s suggestion sounds like a good strategy to me, but I’ll continue to use all my browser’s security features as well.
WS contributing editor Yardena Arar has written about technology for the New York Times, the Canadian Press, the Associated Press, and the Los Angeles Daily News. She was an editor of PC World magazine from 1996 to 2009.
Early adopter of Windows 7 shares his secrets
 By Dennis O’Reilly
By Dennis O’Reilly
For most Windows users, the transition to Windows 7 will be bump-free.
But even if the initial installation goes smoothly, you know there’ll be glitches — some big and some small.
There’s no teacher like experience. Fortunately, however, there’s also no reason we have to learn everything the hard way. You can avoid a few potholes by listening to one early Win7 adopter, Ed Kirkpatrick:
- “We have been using the released-to-manufacturing version of Windows 7 Professional since it became available through our Microsoft TechNet account. You may have already learned these facts about Windows 7, but I haven’t seen them written up in any reviews yet.
- 1. There’s no ‘Classic View’ of anything (no workaround available without third-party software).
- 2. There’s no Quick Launch toolbar available (see below for a workaround we like even better).
- 3. The WPA2-Personal wireless security key can be seen in clear text by anyone after it has been typed in (see below for Microsoft’s suggested workaround).
- 4. There’s no way to copy User Profiles (except the Default User profile — see below for more info).
“If anyone has found a resolution to any of these ‘problems/features,’ we are interested to hear about them.
“We opened up a security issue case (ID 109083169417505) for #3 above, and a technician was very helpful with the other issues as well.
“A workaround for #2 is to create a folder in the root of C: (we called it QuickLaunch) and put links there to all the programs you would normally put in the Quick Launch. Then right-click the taskbar, choose Toolbars, New Toolbar and direct it to the folder in the root of C:. We then move this toolbar over against the Start Menu so it’s in the same position as the Quick Launch.
UPDATE 2009-11-12: In the Nov. 12 Known Issues column, reader David Shirly describes how to restore the Quick Launch toolbar in Windows 7. “For #3 above, the Microsoft tech-support engineer stated that Microsoft’s stance is that WPA2-Personal (or lower) is only for ‘home use’ security, and the owner/user should be able to see the security key at any time. If enterprise security is required, he said, WPA2-Enterprise with a Radius server should be implemented. I asked him about an in-between scenario — i.e., a public implementation where a Radius server is not feasible — and his answer was to use WPA2-Personal along with MAC address listing.
“For #4 above, the Microsoft tech-support engineer told us Microsoft’s stance is that user profiles shouldn’t be copied all the way down through Windows 2000. So with Windows 7 you just can’t. One workaround could be to use Microsoft’s USMT (User State Migration Tool). [See Microsoft’s User’s Guide to USMT.] But this is primarily to move user data from one computer to another, not to copy user profiles from one profile to another on the same computer.
“A more-reasonable method seemed to be to ‘build up’ the default user profile, which can be copied. [See ‘How to customize default user profiles in Windows 7,’ MS Knowledge Base article 973289.] We haven’t had time to try this yet, but hopefully it will do what we need.”
This is just the first of a torrent of Windows 7 tips and tweaks you’ll be reading about from Windows Secrets in the months to come. I hope you’ll take us along on your personal Windows 7 adventure. Enjoy the ride!
| Reader Ed Kirkpatrick will receive a gift certificate for a book, CD, or DVD of his choice for sending a comment we published. Send us your tips via the Windows Secrets contact page. |
The Known Issues column brings you readers’ comments on our recent articles. Dennis O’Reilly is technical editor of WindowsSecrets.com.
The greatest Halloween prank ever
 |
By Stephanie Small
Halloween trick-or-treaters in creative costumes were everywhere last weekend. Pranks and scares also belong to this holiday, and the one in this video could very well be the topper! Instead of being scary, though, it’s simply a humorous — and harmless — thing to do if you’re too old to go trick-or-treating and still want some free candy. Who knows, with a year to think it over, you may come up with something even more clever for Halloween 2010! Play the video |
Step by step: reload apps after clean install
 |
By Fred Langa
When you do a clean install of Windows — whether the new version 7 or one of its predecessors — make sure you reload your software in the correct order. Here’s my tried-and-true method for building a stable, secure installation of any version of Windows. |
Is there a ‘correct’ reinstallation sequence?
A reader with the nom de Web of “PTL” is rebuilding his OS and wants to know the best way to proceed:
- “Is there a proper sequence for installing applications in a clean install? Obviously, the OS needs to be installed first, but what about after that? I asked several techie friends this question, and every one has a different answer. Any suggestions?”
There’s no one, true way to set things up. But I do believe there’s solid justification for the following common-sense, bottom-up approach:
- Back up your old setup’s data and collect your software serial numbers. It almost goes without saying — almost: Move your personal files and folders to a removable medium or online backup service from which you can restore them on your new setup. Also, gather the serial numbers for all your applications so that you can reauthorize them as part of the reinstallation.
- Yes, the OS must go first. With your data backup in place and your serial numbers at the ready, install Windows with its firewall and other built-in security functions enabled. Don’t surf to any site — none at all — until you’ve gone to the Windows Update site to download and install all patches for your Windows version. This brings your fresh OS fully up to date.
UPDATE 2009-12-10: In the Dec. 10 LangaList Plus column, Fred responds to a reader’s question about whether OEM drivers are more reliable than the generic drivers built into Windows. I’m a belt-and-suspenders type of guy, so I make a full backup of the newly installed, fully updated OS and store the backup in a safe place. This initial backup lets me roll back to a pristine OS setup very quickly if the need ever arises (and it does).
- Get your defenses in place. Once the OS is set up, install your antivirus, third-party firewall, anti-malware, and other security programs. These tools are the foundation of safe computing and should be the very first apps you add to a clean Windows setup.
- Load your browser and e-mail client. If you use Firefox or another third-party browser and/or an e-mail program such as Thunderbird, install and update them next.
At this point, you have the core OS and your security and communications programs in place. Although no major applications are installed on it yet, the machine’s a complete, functioning system that’s secure and ready for use. At this point, I suggest you make another backup and tuck it away as well.
- Add your “productivity” apps. Next, install your most-essential, major productivity apps, such as Office. Basically, anything that qualifies as a primary function of your PC gets installed and updated here. And yes — I make a backup at this point, too.
- Now load the extras. You’re in the home stretch. Install nonessential items and “frills”: third-party maintenance tools, games, and browser add-ons all qualify. This is also the time to load your dangerous stuff: IM apps, file-sharing utilities, beta versions, etc. Make another backup after these programs are installed.
- Don’t forget your data! Finally, reinstall the user data you backed up from your previous installation and — you guessed it — back up the whole shebang one more time, with feeling.
By installing your software in this sequence — from most important to least important — you’re helping to ensure that your PC’s core setup is rock-solid. This means your system is less likely to be affected adversely by later software additions.
Also, by making a complete backup at each major step, you can roll your PC back to whatever depth you need to, without having to go through the entire ground-up process again.
There are many ways to handle a reinstall, but I’ve found that this order produces the best, most-stable results while also ensuring that any future disaster-recovery efforts go much, much faster!
‘Server error’ more common with NOD32?
Hugo Galindo reveals something interesting about the IRPStackSize error I wrote about in my Oct. 22 column:
- “In your article, ‘What’s with the no-room-on-the-server error?’, you say that the IRPStackSize error is uncommon and very rare, but I disagree.
“I work with many machines, and this problem is currently very common because all machines that I have seen with the popular NOD32 Antivirus v4.x have had it. I fix it with a value of 18, sometimes 20, in the IRPStackSize [parameter].”
Thank you, Hugo. It’s interesting that the error crops up with NOD32. I’ve seen it only on systems with Symantec’s Norton antivirus suite.
Still, the “Not enough server storage” error is uncommon in the sense that it affects only a small percentage of the overall Windows population.
NOD32 has only about a 9% share of the overall AV market. Even if you see lots of IRPStackSize problems within that slice of the pie, it’s a very small slice overall. Clearly, IRPStackSize trouble happens, but it’s far from common.
Most Windows users will never encounter this particular problem, although users of some antivirus suites run a higher risk of seeing it. In any case, the solution I presented in my previous article is simply to bump up the IRPStackSize parameter, though you might also consider switching to a less-problematic antivirus package.
Thanks for writing!
Are external drives OK for primary backups?
A reader known as Schuhj would like to turn off his backup server and rely on inexpensive external drives instead:
- “With the advent of terabyte-sized external hard drives, is it still advisable to use a server (generic computer with multiple HDs) for backup if you’re protecting only a couple of TB of data? A server requires floor space, an OS with the hassle of updating, and a monitor/keyboard/mouse. And it uses constant energy if kept on all the time.
“USB external HDs use the existing system and seem to be able to power down to be energy-efficient; they can be rotated and stored in a fireproof safe.”
External drives are very easy to set up, and their prices can be astonishingly low. As I write this, multiple online vendors are selling 1- and 2TB external drives for under $100 per terabyte. You gotta love pricing like that!
But ironically, just last week my 1TB Maxtor/Seagate OneTouch external drive died — for reasons unknown — after less than a year of service. Various repair tools all failed to correct the problem, and my subsequent attempts to reformat the drive came up empty. I had to send the unit back to the factory.
The drive contained mostly tertiary data — a backup of a backup — so my original, main backup was intact. Fortunately, I didn’t lose anything except time and effort. The unit was under warranty and Seagate was good about promptly sending back a new (refurbished) replacement, which I’m now using.
But the process took over a week, cost me $20 in shipping, and left me without one of my safety nets. I’m glad it was only a tertiary backup and not used to store any critical, irreplaceable data.
I didn’t keep any banking records or other sensitive data on that drive, which is good — because I was unable to data-wipe the drive before sending it back. Anyone recovering the data would now have copies of my MP3s and Langa family photos and videos, among other miscellaneous files.
If the drive had contained sensitive data, I would’ve destroyed it to make the data unrecoverable and then eaten the full cost of a replacement. Never would I have sent it back to the manufacturer — or to anyone else.
What went wrong with the drive? Well, external drives are usually ordinary desktop drives mounted in standalone enclosures. Unlike the drives engineered for use in portable devices, most desktop drives have little or no protection against physical shock.
Also, external drives are usually USB-based, which makes them both slower and less reliable than devices using the dedicated, high-speed data connections (IDE, ATA, SATA, etc.) inside your PC.
As a quick way of moving huge amounts of data from machine to machine — or for noncritical backups — external storage is hard to beat. But you’re asking for trouble if you expect an external drive to be as reliable or long-lasting as a classic internal drive.
More ways to capture ‘uncopyable’ text
Expanding on the item in my Oct. 22 column, “Capture text in dialog boxes and folder windows,” several readers wrote in with additional ways to capture file paths and print directory (folder) window contents:
- “I select a file in Explorer, press F2, then Ctrl+C; I have the file name in the Clipboard. I also have in my context menu the free ClipboardPath utility, which copies the Drive:pathfilename.ext to the Clipboard.” —Dan Bale
[ClipboardPath adds an option called Copy Path to Clipboard to the right-click menu of Windows Explorer. The utility is available from Stefan Bertels’ site.]
- “Microsoft describes a method to add this capability to the right-click context menu in Windows XP and Vista [in Knowledge Base article 321379]. In addition, Karen Kenworthy has long offered a free Directory Printer program [on her Power Tools site]. Perhaps one of these offerings will be useful to Roy and others who would like to do this very thing.” — Joe K.
Thanks, Dan and Joe!
| Readers Dan and Joe will each receive a gift certificate for a book, CD, or DVD of their choice for sending tips we printed. Send us your questions and tips via the Windows Secrets contact page. |
Fred Langa is editor-at-large of the Windows Secrets Newsletter. He was formerly editor of Byte Magazine (1987–91), editorial director of CMP Media (1991–97), and editor of the LangaList e-mail newsletter from its origin in 1997 until its merger with Windows Secrets in November 2006.
Two free removal utilities go head to head
 |
By Ian “Gizmo” Richards
In my Sept. 17 and Oct. 1 series on program uninstallation, I recommended free program uninstallers from Revo and ZSoft. I’ve had a clutch of subscriber e-mails asking me to explain the difference between these two products and to name the one I prefer. |
The uninstaller that cleans up after the fact
Even though both Revo Uninstaller and ZSoft Uninstaller are excellent programs, they work in very different ways. Revo sweeps up leftovers after a program has been uninstalled using the app’s own uninstaller, while ZSoft uninstalls programs by using before-and-after-installation snapshots it creates.
Think of Revo as a replacement for the standard uninstall routine you’ll find in the Windows Control Panel. Both the standard Windows uninstaller and Revo use the uninstaller supplied by the developer of the program you want to remove.
Revo one-ups the Windows applet by thoroughly cleaning up any files and Registry entries left over by the developer-supplied uninstallation routine. To do this, Revo analyzes your system prior to the uninstallation and again after the uninstaller has run.
This information is used to identify the files, folders, and Registry entries created when the program was installed. Revo then looks at what’s still on your computer after the uninstallation and offers to remove these hangers-on.
At first glance, this doesn’t seem to make sense. Why would you want to analyze the system prior to the uninstallation? Surely, you’d want to do so prior to the original installation? That’s a fair question, but the answer lies in understanding the way Revo works.
Revo needs to look at the system state before and during the uninstallation in order to determine the names of the installation folders, files, and Registry keys used by the product. The uninstaller uses this information to look more deeply for items associated with the app and left behind after uninstallation.
Let’s say you’re using Revo to uninstall the CCleaner system-maintenance utility — which includes a program uninstaller of its own, by the way (visit the vendor’s site for more information). By analyzing the PC’s configuration before and during CCleaner’s uninstallation, Revo determines that the program was installed in the CCleaner folder and identifies the names given to various Registry keys used by CCleaner.
With this information, Revo can check the contents of the CCleaner folder after the program’s removal — if the folder itself wasn’t removed — to look for leftover files. Revo also searches the Registry for any keys with names similar to those that have been removed during the uninstallation procedure.
There’s a degree of guesswork in this procedure, and thus a small risk that Revo may attempt to delete the wrong information. That’s why Revo offers you four different uninstallation options, each of which provides a different balance of thoroughness and risk.
The safest option is to remove only the files deleted by the program’s own uninstaller. This may well be a dependable way to go, but then you’re getting no benefit from using Revo. You might as well have uninstalled the program using the uninstaller in Windows’ Control Panel.
The other three options offer various trade-offs between thoroughness and safety. The option labeled “Moderate” is the default setting and the best choice for most users.
Whichever of the three true cleanup options you choose, Revo will always give you the opportunity to review prior to deletion the items it identifies as extraneous. (See Figure 1.)

Figure 1. Revo Uninstaller lets you choose which leftover Registry entries to delete post-uninstallation.
Of course, if the program uninstaller is particularly thorough and removes all traces of the product, it really doesn’t matter which of Revo’s removal options you choose because there will be no leftover files and Registry entries to clean up. CCleaner is a good example of this. The product’s own uninstaller removes all traces of the utility from your computer, so there’s nothing left for Revo to delete.
Unfortunately, this is relatively uncommon. Most programs leave behind some traces after uninstallation. This is often intentional; for example, your registration data and personalized setup files may be retained deliberately in case you ever reinstall the product.
The decision to remove the files and Registry entries Revo marks as deletable is really up to you. Revo certainly gives you that choice; the regular Windows uninstaller doesn’t.
Revo may not do a perfect job, but in most cases, it comes close. Revo enjoys a great advantage over most other uninstallers, including ZSoft, because it can manage the removal of programs that were originally installed without monitoring by Revo.
Revo Uninstaller is available from the vendor’s site. It works on the 32-bit versions of Windows 2000, XP, and Vista.
Remove apps without using Windows’ uninstaller
ZSoft Uninstaller doesn’t need the uninstallation program provided by the developer to get rid of the unwanted app. Instead, ZSoft takes a snapshot of your system prior to installing a program and another after the installation is finished.
By highlighting the differences between the two system snapshots, ZSoft is able to list all files and Registry entries created during the program’s installation. ZSoft stores the list on your hard drive; should you ever wish to uninstall the program, ZSoft refers to the list and deletes all files and Registry entries associated with the product.
At first, this seems like a much more-sensible and more-comprehensive approach than the method used by Revo Uninstaller. However, it’s not quite that simple.
For the ZSoft approach to work, it’s essential that the uninstaller be started prior to installing any new program so that it can take a snapshot of your system beforehand. (See Figure 2.) This requires a certain degree of discipline by users — but it’s not only a question of discipline. It takes time for ZSoft to create system snapshots, which adds considerably to the overall program-installation time.
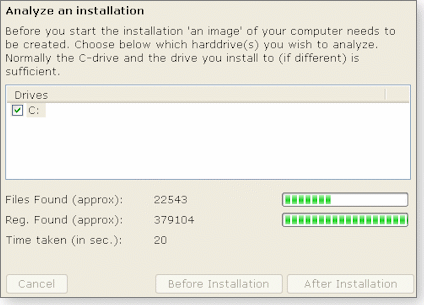
Figure 2. Before you can uninstall a program, ZSoft Uninstaller must take a “snapshot” of the system’s pre-installation state.
There’s a deeper problem with the ZSoft approach: The uninstaller relies on comparing two system snapshots taken before and after a program is installed. Any differences between these snapshots are attributed to the program being installed. However, there are file and Registry changes taking place all the time on a Windows PC. Some of these changes are due to Windows itself, while others are created by your running applications.
These normal, ongoing background changes are picked up by ZSoft and may be incorrectly attributed to the installation process. In fact, they have nothing to do with the program’s installation.
If you subsequently use ZSoft to uninstall a product, the uninstaller reverses the changes made by Windows as well as those actually made by the program’s own installer. Reversing these unrelated changes can have unfortunate consequences for your computer’s well-being.
ZSoft attempts to handle this problem by letting you choose which files and Registry entries to delete. However, very few users have the skill to know which items should be deleted and which should be retained.
In practice, the problem isn’t so bad as it may seem. I’ve used ZSoft to uninstall more than 30 products. Only once did I have to intervene to prevent the accidental deletion of important files having nothing to do with the product I was uninstalling. Nonetheless, the possibility of ZSoft creating a problem during uninstallation is always there.
On the positive side, the ZSoft approach ensures that all traces of the program you no longer want will be thoroughly removed from your PC. That’s something that Revo attempts but may not actually achieve.
This feature makes ZSoft an attractive option when testing out new programs or when you want to install a program for a single occasion rather than leave it on your PC permanently. In both cases, the ability to completely remove all traces of the program is a big plus.
ZSoft Uninstaller is available from the ZSoft site. It works only with the 32-bit versions of Windows 2000 and XP.
Choosing a ‘best’ free uninstaller utility
The uninstallers from Revo and ZSoft use very different approaches to removing programs, and each has strengths and weaknesses. This being the case, I don’t see the need to choose one product over the other. Instead, I treat these programs as complementary products rather than competitors; each is most suitable to particular situations. Given that both products are free, this is an entirely practicable approach.
However, this option is available only to Windows 2000 and XP users because ZSoft Uninstaller is not currently offered for Vista or Windows 7.
But there’s another more-important factor at work here that changes the focus of this discussion. My use of both uninstallers has declined dramatically in recent months. That’s because I’m increasingly replacing the programs installed on my PC’s hard drive with their portable counterparts.
I have reduced to a handful the number of “installed” programs I use, whereas my portable-applications folder is bulging with dozens of utilities. In this context, any discussion of the best uninstaller is cut short. (I discussed the many benefits of using portable apps in my June 18 and July 2 Best Software columns.)
If you take my advice and use portable applications wherever possible, you won’t need an uninstaller at all.
Ian “Gizmo” Richards is senior editor of the Windows Secrets Newsletter. He was formerly editor of the Support Alert Newsletter, which merged with Windows Secrets in July 2008.
Add Windows 7 PCs to Vista and XP networks
 |
By Woody Leonhard
Now that Windows 7 has arrived, many people will be mixing and matching systems running Win7, Vista, and XP on their home and small-office networks. Setting up such heterogeneous networks isn’t as hard as you might think … if you follow a few simple rules. |
The crux of the mixed-network problem
Anybody who has set up a Windows network — any Windows network — will tell you that the process is easy … until something goes wrong. Usually, adding a Windows 7 machine to an existing network of Win7 PCs is as simple as connecting the system to the network, telling Windows you’re on a Home network, clicking a few times, and entering the password for your homegroup. You’re sharing files and printers in a trice.
My Oct. 1 column offers loads of down-and-dirty advice about setting up Win7’s homegroups.
However, adding a Windows 7 machine to an existing Vista or XP network isn’t nearly so simple. Upgrading systems on a mixed network can lead to some inscrutable behavior. I predict more than half the emergency calls I’ll get from new Windows 7 users will be from folks who can’t get their networks going.
I know, because I’ve been there. As much as I love Windows 7, a few of my PCs are going to stay with XP. For one thing, older laptops just aren’t up to making the jump. I’ll also keep one XP clunker around in case I need to use some piece of hardware not supported by Windows 7.
I’ve hit a few snags when attempting to network PCs running old and new versions of Windows. I can’t possibly cover all of the Win7 integration problems you may encounter, but I can share with you a few of the networking tricks I’ve learned. They may save your tail when the big, bad Win7 wolf comes knocking on your door.
By the by, I won’t be referring to domains here. They’re the province of centrally controlled corporate networks run by network admins and legions of geeks in white lab coats. If you plug your computer into a domain, the domain controls just about everything. Get over it.
Public, Work, or Home? HomeGroup or workgroup?
Part of the problem in mixing various flavors of Windows is terminology. When you attach your Windows 7 or Vista computer to a network, you have to tell Windows what kind of network you’re connecting to. The choices are Public, Work, and Home. But you can easily designate your office network as Home or a secure connection in your house as Public. The names don’t mean much. (Windows XP didn’t even bother with such artificial naming conventions.)
Adding to the confusion, Windows XP, Vista, and Win7 all assign a “workgroup name” to the network they’re attached to. When you slap together networks with XP and Vista, it’s important to match up the workgroup name on PCs that need to talk to each other. Contrariwise, Windows 7 doesn’t even nudge you about the workgroup name and largely ignores it.
Muddling the situation further, Windows 7 supports a quick method of sharing files and printers via a network technique called HomeGroup. They may sound similar, but workgroups and homegroups have absolutely nothing in common. Nada.
When you get lost in the HomeGroup/workgroup bafflegab, keep the following points in mind:
- Telling Win7 you’re connecting to a Public network turns off network discovery. This means other computers on the network can’t stumble onto your computer — nor can you see other PCs on your network. It also disables file and printer sharing by default, so you can’t share printers or specific files or folders on your computer unless you change that default setting.
Public folder sharing is turned off as well. As a result, only people who enter your computer’s name and a valid username/password can get into its Public folders. Password-protected sharing gets turned on, so all file and printer sharing (whether in the Public folders or elsewhere) also requires a username and password.
- If you tell Win7 you’re connecting to a Work network, Windows turns on network discovery and file and printer sharing. This also enables public folder sharing and password-protected sharing, which means anyone trying to get into the PC’s files or use its printer needs to provide a username and password that are valid on the PC.
- When you instruct Win7 to connect to a Home network, you get precisely the same settings as with the Work network type. However, the OS also looks to see whether there’s a homegroup already set up on your network. If you then attach your PC to the homegroup, sharing suddenly becomes very easy among Win7 PCs in the homegroup.
- Homegroups work only among Windows 7 machines running on networks identified as “Home.” See my Oct. 1 column for details. If you’re counting on homegroups to help you connect a Windows 7 PC to an XP machine, you’re barking up a nonexistent tree. XP and Vista don’t have a clue about homegroups.
- Finally, every XP, Vista, or Win7 PC has a workgroup name. By default, Win7 and Vista machines are assigned the workgroup name WORKGROUP (original, eh?). Windows XP Home PCs get the default name MSHOME, and all other versions of XP get the name WORKGROUP as well.
(I’ll forgive you if you print this list out and tape it to your monitor.)
Step 1: Make your PC known
If Windows XP and Vista PCs on your network can’t “see” your new Windows 7 machine, chances are good you told Win7 to cloak itself.
To remedy this situation, right-click the network icon in the Windows 7 notification area and choose Open Network and Sharing Center. If the current network under “View your active networks” is listed as a Public network, click that link and change to a Work network or — even better — a Home network.
To preserve the security of a Public network while adding the ability to share a printer, click Change advanced sharing settings in the left pane of the main Network and Sharing Center window. Under “File and printer sharing,” select Turn on file and printer sharing. (See Figure 1.)

Figure 1. Enable printer sharing on a Public Win7 network via this setting in the Network and Sharing Center.
Depending on your other network settings, a person attempting to get to your printer via another PC on the network may have to provide a username and password. It gets complicated.
Step 2: Get your workgroups together
As long as a network contains only Windows 7 PCs, the network name doesn’t matter one whit. However, if you’re trying to get XP, Vista, and Win7 PCs to talk to each other, the workgroup name definitely comes into play. In particular, XP won’t play nicely with your Win7 computer unless the workgroup name on the Win7 machine matches the workgroup name on the XP system. (Vista tends to ignore workgroup names.)
To check and — if necessary — change the workgroup name on any XP PC, right-click My Computer, choose Properties, and select the Computer Name tab. If the workgroup name doesn’t match the name used by the other networked PCs, change it.
In Vista and Windows 7, right-click Computer and choose Properties. In the Computer Name area, you’ll see the Workgroup name; change it by selecting the Change settings link, clicking the Change button, and entering the new name. (See Figure 2.)
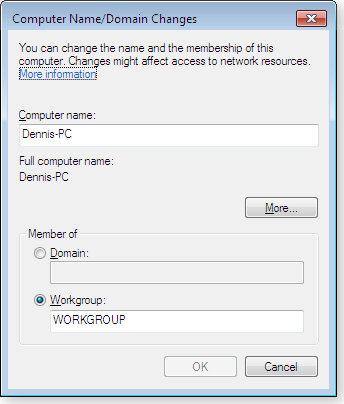
Figure 2. Change the workgroup name on a Win7 PC via the Computer Name/Domain Changes dialog.
To avoid completely inscrutable problems, make sure all the PCs on your network have the same workgroup name, and reboot each one whose name you change.
Step 3: Use the same sign-ins on all PCs
No, it isn’t high security, but using a single sign-in can avoid connection problems.
Different versions of Windows have settings that may or may not require passwords from someone attempting to access data, media, or printers.
You can flip through all the choices — but it’s usually much simpler to enter the same username and password on all of the PCs you need to share. In many cases, using a single sign-in bypasses the extra network-security hurdle and provides a magic, behind-the-scenes “open sesame” when it’s needed the most.
So there you have it. Three easy steps and a mumbo-jumbo decoder that should help solve most of your mixed-network problems. And yes, you’re certain to encounter a few.
| UPDATE 2009-11-12: In the Nov. 12 Known Issues column, reader Stuart Berg describes Microsoft’s free Link-Layer Topology Discovery Responder utility that simplifies networking XP PCs. |
Woody Leonhard‘s latest books — Windows 7 All-In-One For Dummies and Green Home Computing For Dummies — are currently available in several languages.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Tracking content block list GONE in Firefox 138
by
Bob99
3 hours, 5 minutes ago -
How do I migrate Password Managers
by
Rush2112
2 hours, 27 minutes ago -
Orb : how fast is my Internet connection
by
Alex5723
7 hours, 26 minutes ago -
Solid color background slows Windows 7 login
by
Alex5723
8 hours, 46 minutes ago -
Windows 11, version 24H2 might not download via Windows Server Updates Services
by
Alex5723
7 hours, 17 minutes ago -
Security fixes for Firefox
by
Susan Bradley
6 hours, 46 minutes ago -
Notice on termination of services of LG Mobile Phone Software Updates
by
Alex5723
19 hours, 30 minutes ago -
Update your Apple Devices Wormable Zero-Click Remote Code Execution in AirPlay..
by
Alex5723
1 day, 4 hours ago -
Amazon denies it had plans to be clear about consumer tariff costs
by
Alex5723
19 hours, 35 minutes ago -
Return of the brain dead FF sidebar
by
EricB
6 hours, 46 minutes ago -
Windows Settings Managed by your Organization
by
WSDavidO61
5 hours, 54 minutes ago -
Securing Laptop for Trustee Administrattor
by
PeachesP
6 hours, 55 minutes ago -
The local account tax
by
Susan Bradley
8 hours, 7 minutes ago -
Recall is back with KB5055627(OS Build 26100.3915) Preview
by
Alex5723
1 day, 17 hours ago -
Digital TV Antenna Recommendation
by
Win7and10
1 day, 10 hours ago -
Server 2019 Domain Controllers broken by updates
by
MP Support
2 days, 5 hours ago -
Google won’t remove 3rd party cookies in Chrome as promised
by
Alex5723
2 days, 7 hours ago -
Microsoft Manager Says macOS Is Better Than Windows 11
by
Alex5723
2 days, 10 hours ago -
Outlook (NEW) Getting really Pushy
by
RetiredGeek
1 day, 12 hours ago -
Steps to take before updating to 24H2
by
Susan Bradley
1 day, 3 hours ago -
Which Web browser is the most secure for 2025?
by
B. Livingston
1 day, 17 hours ago -
Replacing Skype
by
Peter Deegan
1 day, 5 hours ago -
FileOptimizer — Over 90 tools working together to squish your files
by
Deanna McElveen
2 days, 4 hours ago -
Excel Macro — ask for filename to be saved
by
nhsj
1 day, 1 hour ago -
Trying to backup Win 10 computer to iCloud
by
SheltieMom
1 day, 5 hours ago -
Windows 11 Insider Preview build 26200.5570 released to DEV
by
joep517
4 days, 10 hours ago -
Windows 11 Insider Preview build 26120.3941 (24H2) released to BETA
by
joep517
4 days, 12 hours ago -
Windows 11 Insider Preview Build 22635.5305 (23H2) released to BETA
by
joep517
4 days, 12 hours ago -
No April cumulative update for Win 11 23H2?
by
Peobody
3 days ago -
AugLoop.All (TEST Augmentation Loop MSIT)
by
LarryK
4 days, 12 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

