|
In this issue MICROSOFT 365: Removing MFA Additional articles in the PLUS issue SILICON: Apple’s M1 processors are shaking up how you compute MICROSOFT 365: Get more OneDrive with these tips ON SECURITY: Gearing up for cyberwar
MICROSOFT 365 Removing MFA
By Will Fastie How many times have articles in this newsletter told you that multifactor authentication (MFA) was a good idea and suggested that you turn it on? A lot. It’s good advice. Just the other day, I turned on Microsoft 365 MFA for one of my clients. It’s too embarrassing for me to describe the mistake I made. Suffice it to say that it was an accident, because I didn’t intend to turn it on. Before I get into how I fixed it, let me assure you that I do think multifactor authentication is a good idea and that it is mandatory for any kind of financial account. On the other hand, it can be extremely annoying for frequently used systems and services, such as email. I would not want to respond to an authentication challenge every time I launched Outlook, especially because I’m connecting not to one, but to four, different email accounts. In this case, I wasn’t dealing with my own accounts. The service belongs to one of my Web clients. All that means is that it isn’t up to me to decide how to configure security — it’s my client’s call. I can only recommend. When the client was challenged for authentication, he gave me a very clear message that it was not desired. Why didn’t I warn him in advance? Because I didn’t realize what I’d done until he alerted me. So, MFA needed to be turned off. It proved more challenging than expected. Finding the switch
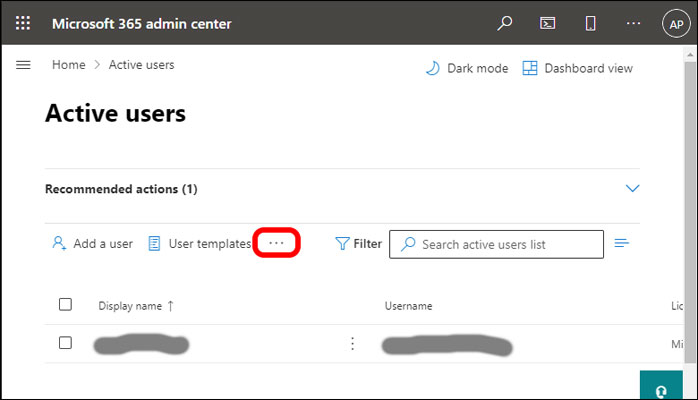
I’m not a stranger to the 365 control panel, aka the “Microsoft 365 admin center.” I’ve configured 365 for many clients over the past decade and generally know what I’m looking for. What I’m not is an expert on the Microsoft Exchange server or Azure AD. Originally, the 365 control panel was a mess. It was extremely complicated, with a dizzying array of switches, gauges, and levers. A lot of deeper Exchange settings, things most consumers and small-business owners would never need to see, were exposed at a high level, seeding further confusion. Finding things was very difficult, but to offset this (and to Microsoft’s credit), tech support was top-notch (which continues with business plans to this day). So when I got lost, I could pick up the phone. Good thing, too, because the early support ticket system was weak. Over the years, Microsoft made the control panel much more approachable for average users. Only the most common things are visible at the uppermost level of the user interface today, and in most cases it’s fairly obvious how to drill down. And deep access to settings for Exchange remains available if needed. How did I get lost? By looking for the obvious. And getting confused. After logging in to my client’s account and reaching the admin center, I navigated to the Active users section (Figure 1).
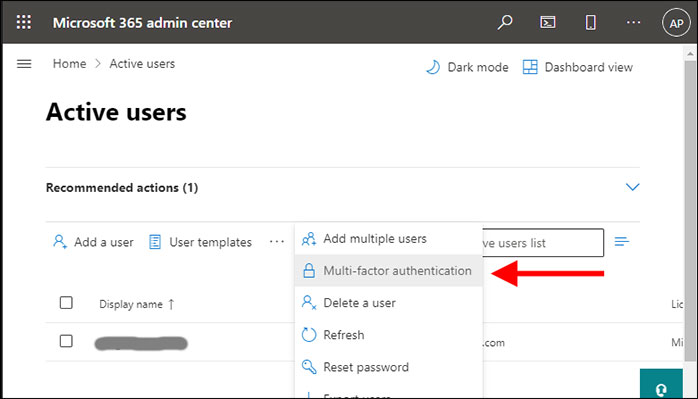
Here, I encountered a minor UI problem in that I was not able to see the MFA option I was looking for. That’s because any menu item that won’t fit on the line is in a dropdown menu, activated by clicking the ellipsis (three dots). Then MFA appeared in the dropdown (Figure 2).
Clicking the MFA option displays a new list of users, this time with the MFA status clearly showing on the right (Figure 3).
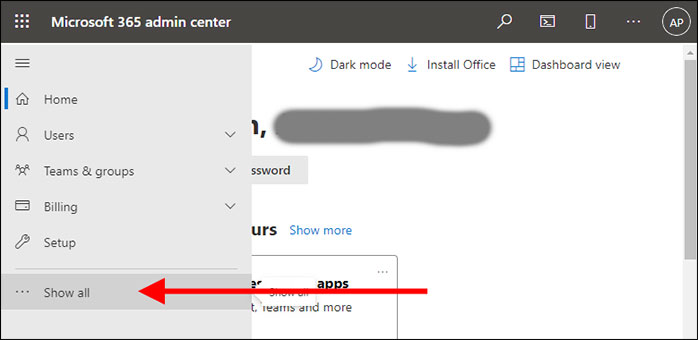
I was stumped. I knew that MFA was turned on, not only because my client had reported it but also because I myself had experimented to confirm it. But the list clearly showed that it was disabled. After poking around the admin center UI for a bit, I turned to the Internet to see whether I could find answers. Surprisingly, the top results from my search resulted in instructions to do exactly what I had done already. So I submitted a support ticket on behalf of my client and asked him to forward the response from the support agent. Here’s what I learned. As I mentioned earlier, Microsoft simplified and streamlined the UI for 365. That’s why the basic menu has just a few items showing (Figure 4). But it also presents a last option, Show all.
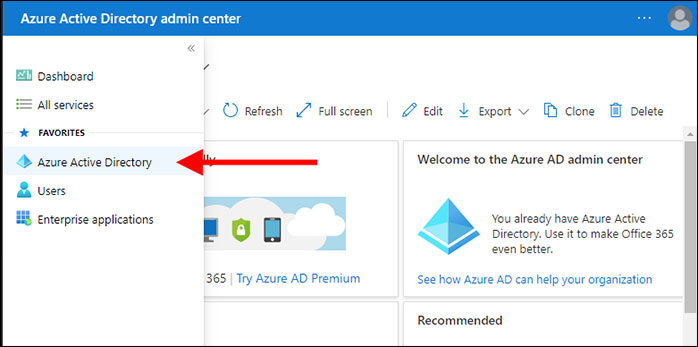
Clicking Show all expands the admin center’s menu dramatically. In Figure 5, you can see I found what I was looking for. And, if you look closely, you’ll notice that Azure Active Directory is very low on the menu (the thumb on the scrollbar is at the very bottom). This is where the support agent instructed me to go, so I clicked through.
The first thing one notices about the next dialog (Figure 6) is that we have departed the Microsoft 365 admin center and arrived at the Azure Active Directory admin center. This is most evident by the change in color of the title bar.
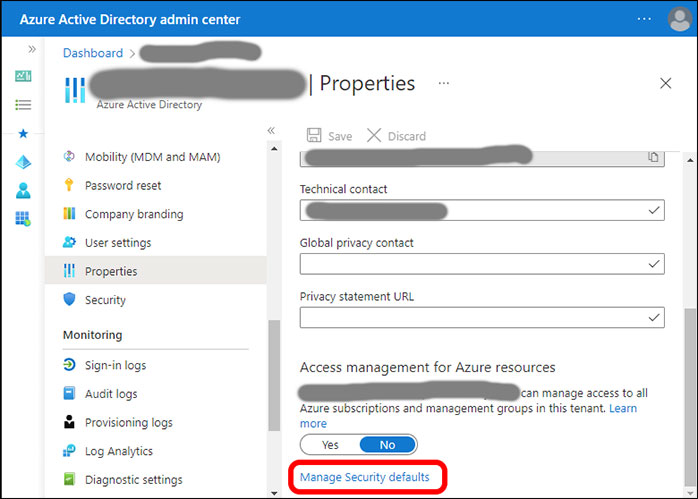
Now we have the first clue about what’s going on. If we’re looking at Azure AD, it means we’re looking at organizational settings, not individual user settings. The agent’s instructions were to proceed to Azure AD, so I clicked through to reveal another menu (Figure 7). The applicable area is Properties. At the very bottom of the panel on the right, almost unnoticeable, is a link to Manage Security Defaults.
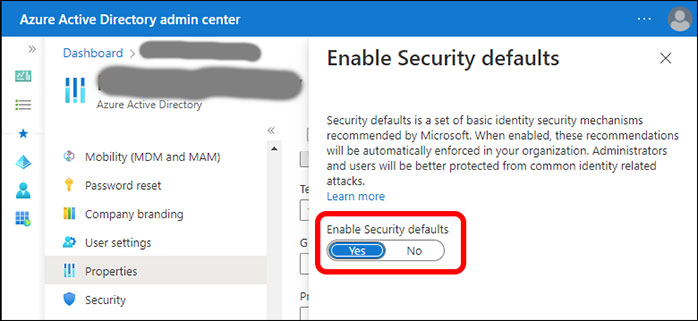
Clicking the link results in a pop-up on the right, Enable Security Defaults (Figure 8). To turn off MFA, it was necessary only to change the setting from Yes to No. Once that was done, MFA challenges ended, and my embarrassing error was corrected.
If you look carefully at Figures 6, 7, and 8, you’ll notice that there is no mention of multifactor authentication at all. Even if I had realized that I needed to get into Azure AD to deal with this matter, I probably still would not have known what to do. Once you go into one of these other “admin centers,” the weeds are much taller and the swamp is hard to navigate. A support ticket would still have been necessary — for me, at least. Did you catch the reference to “centers,” plural? That’s right — there are several admin centers in the UI. These more or less correspond to the control panels you would experience if you were managing an on-premises Active Directory configuration. These centers are slightly simplified, but Microsoft has no choice but to provide the same level of control for what amounts to a cloud-based server as it would for on-premises Windows Servers. Business vs. Personal 365 plans
One thing I didn’t mention is that my client subscribes to the Microsoft 365 Business Standard plan. The operative word here is “Business.” Microsoft rightly assumes that Business plans are going to be multi-user, with accounts for each employee who needs them. That’s why Azure AD is accessible via the 365 admin center — to provide organizational control. My personal 365 plan is, well, 365 Personal. Azure AD is not exposed in my admin center, nor is there any mention of MFA. I’m sure it will turn up sooner or later, but without Azure AD, it will almost certainly be managed at an individual account level. Is this article relevant to you? I think so. Although many in our audience would tend to subscribe to Personal 365 plans, a key reason to choose Business plans instead is that they include email service that can be attached to your own domain name. Personal plans do not, presuming you’re getting email service elsewhere. It’s nice to have your entire productivity environment in one place. But, as you can see, the Business plans have a different level of complexity. I got caught by that complexity, made a stupid error, and needed help to restore my client’s equanimity. One final note. I mentioned that 365 support from Microsoft was good. I submitted the support ticket. I fixed the problem 30 minutes later.
Will Fastie is editor in chief of the AskWoody Plus Newsletter.
The AskWoody Newsletters are published by AskWoody Tech LLC, Fresno, CA USA.
Your subscription:
Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, AskWoody.com, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody Tech LLC. All other marks are the trademarks or service marks of their respective owners. Copyright ©2022 AskWoody Tech LLC. All rights reserved. |
|||||||||||||||||||||||||