
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Get help from the Windows Reliability Monitor
In this issue
- TOP STORY: Get help from the Windows Reliability Monitor
- LOUNGE LIFE: Windows 7 generates many and varied questions
- WACKY WEB WEEK: How to make eating truly mindless
- LANGALIST PLUS: More on where Windows 7 puts important files
- BEST SOFTWARE: What — or who — is using your connection?
- INSIDER TRICKS: Tailor Windows to work the way you do
Get help from the Windows Reliability Monitor
 By Woody Leonhard
By Woody Leonhard
Windows abounds with special-purpose tools that can help in the care and feeding of the beast — if you can just figure out where to find them.
Today, I’d like to introduce you to the Reliability Monitor, one of my favorite ways to identify and exorcise the demons that lurk within.
The Windows 7 Reliability Monitor, as well as the version in Vista, slices and dices event logs (as explained later). The logs record information related to your PC’s stability. The Reliability Monitor doesn’t catch everything — more about that in a moment — but what it does find can give you instant insight into what’s ailing your machine.
The easist way to launch the Reliability Monitor is to enter reli in the Start menu’s search box and press Enter. (In Vista, you can enter perfmon /rel in the Start, Run dialog box or at a command prompt.) To get the most out of the monitor, sign in as an administrator.

Figure 1. The Reliability Monitor in its Windows 7 version.
The top line in the display (see Figure 1) supposedly rates your system’s stability on a scale of 1 to 10. In reality, it doesn’t do anything of the sort. But if you see that line drop like a barrel over Niagara Falls, there’s likely some problem in your system worth investigating.
Your rating more or less reflects the number and severity of problems recorded by the event logs in the following categories: Application, Windows, Miscellaneous, and Warnings.
The information icons (circled i’s) generally represent updates to programs and drivers. If you have Microsoft Security Essentials installed, for example, there should be a circled-i icon almost every day, because MSE frequently updates its signature files.
A Microsoft TechNet document contains more details about the types of data reported in Reliability Monitor.
You can arrange the stability graph by day or by week — click on either, and a box at the bottom of the monitor shows entries from the corresponding event log. Many of these event entries have a more detailed explanation, which you can see by clicking the View Technical Details link.
Using Reliability Monitor to solve real problems
The Reliability Monitor does not provide a comprehensive list of all the bad things that have happened to your PC — and it isn’t much of a stability tracker, either. The 1-to-10 rating uses a trailing average of daily scores, where recent scores are weighted more heavily than old ones.
In my experience, the stability graph doesn’t track reality: my system’s performance can bounce like a Willys Jeep in the Nevada desert, and it doesn’t affect the rating. Conversely, my system can hum along like a well-tuned machine while its stability rating tanks.
The Reliability Monitor’s true value lies in showing you a time line of key events — connecting the temporal dots so you may be able to discern a cause and effect.
For example, if you suddenly start repeatedly seeing the dreaded message “Windows Explorer has encountered a problem and needs to close,” check the Reliability Monitor to see what changed in your system recently.
Installing a new driver, for instance, can make your system unstable. If you see your rating tumble on the same day as the driver update, it’s a good bet the new driver is the culprit.
I dug into the Reliability Monitor recently, after I noticed unusual conflicts between Outlook 2007 and Excel 2007. When I tried to preview a spreadsheet in Outlook, I suddenly couldn’t start Excel, open a new sheet, or even switch to Excel. The problem cropped up when I started looking at e-mailed spreadsheets.
I didn’t remember seeing that kind of weird behavior before, so I immediately ran to the Reliability Monitor … and didn’t find a thing. The Reliability Monitor told me that Excel had crashed once, months before, but that didn’t seem to be associated with my current problem. The Reliability Monitor didn’t even show the conflicts that kept Excel from working correctly. Bummer.
But I noticed that my Reliability Monitor rating had taken a big hit several weeks earlier and had not improved. It took a bit of clicking and some head-scratching on my part, but I finally figured out that Adobe Flash was crashing when I went to a specific site. I hadn’t noticed the crashes previously because the browser hadn’t done anything unusual — although it did seem to slow down. I installed a new copy of the Flash Player and, lo and behold, the crashes and slowdowns stopped.
Reliability Monitor has a link at the bottom called Check for solutions to all problems. Clicking the link almost always brings up a box stating No solutions are found (this is very common for Microsoft products) or a link to a manufacturer’s Web site, along with the general admonition to install the latest version of the offending program. Not exactly rocket science.
Proverbial bottom line: the thing doesn’t keep track of everything, and some of it’s a bit deceptive, but the Reliability Monitor can provide some worthwhile information when Windows starts hiccupping. Well worth adding to your diagnostic bag of tricks. For detailed information on the app, see Microsoft’s TechNet documentation.
Mining your system’s info with the Event Viewer
Every Windows routine leaves traces of itself in various event logs. Start a program, and the event gets logged; stop it, and the log gets updated. Install a program or a patch — and a log knows all, sees all. Every security-related event goes into a log. Things that should’ve happened, but didn’t, get logged — as well as things that shouldn’t have happened but did.
Most of what ends up in event logs is understandable only to programmers and computer techs. But there is information that the average computer user can understand — and use. The window to all of these logs is the Event Viewer app. (Note: you need administrator rights to view all logs.)
To launch the Event Viewer in Win7, enter event in the Start menu’s search box and press Enter. To open the program in other versions of Windows, see Knowledge Base article 308427, the app’s Vista directions, and its Win7 directions.
Event Viewer’s left column contains a list of logs and also offers predefined filters. The right column displays log details, as illustrated in Figure 2.
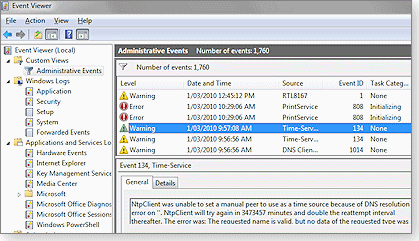
Figure 2. Windows 7’s Event Viewer offers a wealth of information about your PC’s health.
Don’t expect any divine revelations from the Event Viewer. A casual glance at Windows’ event logs can be overwhelming, and nailing down a specific problem is like looking for a needle in a field of haystacks. But the info is there if you want it.
| Have more info on this subject? Post your tip in the WS Columns forum. |
Woody Leonhard‘s latest books — Windows 7 All-In-One For Dummies and Green Home Computing For Dummies deliver the straight story in a way that won’t put you to sleep.
Windows 7 generates many and varied questions
By Tracey Capen
Upgrading to any new operating system is a time of uncertainty for most PC users, and the rollout of Windows 7 is no exception.
For those burning questions regarding Win7, tap into the collective expertise of the Windows Secrets Lounge for answers.
And if you haven’t done so already, on your next visit to the Lounge, read WS editorial director Brian Livingston’s post describing the Lounge’s new search engine.
- Windows 7 RAM usage compared to XP Home
John Sweden wonders about rumors that Windows 7 is a memory hog. This always seems to crop up with each new version of Windows. Over a dozen Loungers replied to this one — with the unanimous response that this rumor is bunk. More»
- Denial of service attack?
Watching your e-mail inbox load up with hundreds of junk e-mails can ruin your day. In this case, Lounge member Nano Geek received over 3000 suspect messages in Outlook via a Hotmail account. Is it a massive attack or just bad communication between Hotmail and Outlook? More»
- Just fun: can you get out of this room?
Yes, there is a lighter side to the Windows Secrets Lounge. Alrock43 posted a link to a seemingly simple online game — figuring out how to open a door. Based on the number of responses, this one looks like a winner. More»
The most-interesting questions raised this week
Sometimes there are no easy answers. Here are a few of the recently posted questions you might be able to answer:
- Tables around forwarded Thunderbird 3.0 msgs
- Vista patch stalls on reboot
- Publisher 2003 forgets style
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right in to today’s discussions in the Lounge.
The Lounge Life column is a digest of the best of the WS Lounge discussion board. Tracey Capen is technical editor of WindowsSecrets.com.
How to make eating truly mindless
 |
By Stephanie Small
Let’s face it: there are times when eating is just a drudge. Who cares about flavor — just get it down as quickly as possible. Don’t you wish there were a gadget to speed up the task? Well, now there is! Watch this hilarious “commercial” advertising a portable conveyer belt that delivers food directly to your mouth. No hands, no exertion required. You’ll either want to order it immediately or give up eating altogether! Play the video |
More on where Windows 7 puts important files
 |
By Fred Langa
PC users who have made the jump from Windows XP to Windows 7 are in for a surprise when they go looking for temporary files. In the Feb. 25 Windows Secrets newsletter, I answered the question, “Where did ‘Documents and Settings’ go in Win7?” This week, a subscriber wants to know where Win7 puts temporary Internet files. |
Scattering temp files improves Win7 security
Reader R. Jones wants access to his Win7 temporary Internet files, but he can’t find them where they used to be in XP.
- “In Win7, how do I see temporary files while I’m on the Internet? With XP, the temporary files were available under ‘local settings.’ Now, when I search for ‘temporary files’ I see several choices for dealing with such files but I don’t see a path to a temporary folder.”
The simplest way to view most temporary Internet files is to do so from right inside your browser. In IE 7 and 8, for example, click Tools, Internet Options. On the General tab, under Browsing history, click Settings, View files. That’s all it takes!
If you prefer navigating to those files more directly, Win7 caches temporary Internet files in the following folder:
C: Users username AppData Local Microsoft Windows Temporary Internet Files
Another location holds many subfolders containing more temporary files used by the browser, add-ons, and other utilities and applications. That folder’s path is:
C: Users username AppData Local Temp
A third folder is specifically reserved for downloaded software:
C: Users username Downloads
Why multiple folders? Unlike XP, which tosses almost all system- and application-generated temp Internet files into the same basket, Vista’s and Win7’s file segregation makes it harder for temp file–-based malware attacks to succeed.
For a good overview and explanation of this change, see the WinVistaClub.com page on managing Vista’s and Win7’s temporary Internet files folder.
Problems installing Office 2007 on Win7 PCs
Rick Kirchoff can load Office 2003 onto his new Windows 7 systems, but Office 2007 stalls.
- “I’ve tried several times to install Microsoft Office Enterprise Edition 2007 onto several computers that were originally shipped with Windows 7. The install seems to go slower than normal; then it just stalls out, stops, and sometimes locks up.
“The same Office 2007 software installs without issues into Vista and XP.
I’ve also been able to install other programs from the same drives onto the Win7 systems, so that rules out the possibility of DVD/CD issues. I’ve found this problem on three different computers that came with Win7 factory installed.
“Odd thing is that Microsoft Office Professional 2003 installs very quickly on my Win7 machines, and without issues.”
Hmmm. I’m writing this column with Office 2007 installed on a Windows 7 system, so it certainly can be done. I encountered no problems in my setup, and a quick search online didn’t reveal any widespread or obvious problem with that application and OS combination. But something’s clearly gone wrong with your specific setup.
One of the most common reasons for problems with an Office 2007 installation is the presence of a trial version of Office, which is often part of a “preinstalled bundle” on new PCs. If a trial version exists, it’s best to uninstall it before installing a full retail version.
If a trial version of Office isn’t the issue, Microsoft Knowledge Base article 971179 offers several options (including an automated “Fix it” button) to help resolve installation problems with Office 2007.
Be aware that Office 2007 won’t let you use some of the same repair tools that worked on earlier versions of Office. For example, Microsoft specifically warns against using the venerable “Windows Installer CleanUp Utility” on Office 2007 — see Microsoft support page 290301 for more on that topic.
Instead, try the official, Redmond-blessed fix described in the above-mentioned article (971179) first; if that doesn’t work, a third-party cleanup tool might do the trick. Revo Uninstaller, for example, specializes in solving uninstall problems that stymie standard uninstall/cleanup tools. Pick up a free 30-day trial version on its download page — it’s $39.25 thereafter.
Two popular Registry cleanup tools, Ccleaner and PowerTools, can also help remove left-behind junk files and Registry entries. Download a free version of Ccleaner at its product page. Pick up the free PowerTools Lite at its download site, or get the more powerful version at its product page — free for 30 days, $29.95 thereafter.
Once the mangled installation is fully removed, you should be able to install Office 2007 normally.
Working with FLAC audio is not that difficult
Rick Kierman is having trouble learning how to run the popular open-source Free Lossless Audio Codec (FLAC) format on his PC.
- “I just bought a PC with Windows 7 and want to record and burn live concerts streamed in FLAC format, but nobody can tell me how. Some even tell me Windows and Macs can’t accept or play FLAC format streams! Is this true?”
A codec is a piece of software that handles the coding and decoding of digital information. You’re correct — neither Microsoft nor Apple includes the FLAC codec with its respective operating system.
For Windows PCs, Sourceforge’s FLAC FAQ shows how you can get FLAC working with Windows Media Player. Or, if you prefer, that same Sourceforge page offers links to about a dozen third-party Windows audio tools that can handle FLAC-format downloads and streams.
The audio tool of your choice (not any codec in itself) handles the saving/ripping/burning of tracks or songs. So, once you have FLAC working in whatever audio tool you select, use that tool’s normal functions to save/rip/burn as you wish.
When to upgrade a BIOS, and why you’d do it
Joe Degwara simply wants to know:
- “Can you explain how and why to flash a BIOS?”
“BIOS” stands for Basic Input/Output System. A PC’s BIOS controls its basic power-up operations until the operating system (e.g., Windows) takes over.
Loading a new program into the BIOS’s RAM to expand, improve, or repair the original programming is called “flashing the BIOS.”
The term “flashing” is a holdover from computing’s Paleolithic era, when some chips had a little clear window on top and could be erased with a strong flash of ultraviolet light.
BIOS updates fall into the “if it ain’t broke, don’t fix it” category. In fact, BIOS updates are rare with modern PCs. You should do it only if your PC vendor or the motherboard manufacturer directs you to, via the information on its customer-support pages.
Most BIOS updates are handled in one of two ways. Most often, you download and run a BIOS update application, carefully following the manufacturer’s instructions.
However, a few systems use an older, less-automated method — you save the update file to a floppy or thumb drive; then boot your PC with the floppy or thumb drive. The updater takes over, completing the update process.
It’s critically important once the update process begins, to leave it alone until it runs to completion. Interrupting a BIOS update (either intentionally or by accident, as might happen with a power failure) can leave the BIOS half-flashed and unbootable.
If you find the system vendor’s or motherboard manufacturer’s instructions confusing or too cryptic (sadly, that’s often the case), the following references will give you a good feel for the details of the overall process:
- PCStat.com’s story, “Beginners guides: flashing a motherboard BIOS”
- Motherboard.org’s article, “How to flash a BIOS without giving yourself a headache”
- DevHardware.com’s hardware guide, “Why and how to flash your BIOS
After reading the above, the system-specific instructions from your system- or motherboard-maker’s site should make more sense and you’ll be well-prepared if the time comes to actually do the deed.
| Have more info on this subject? Post your tip in the WS Columns forum. |
Fred Langa is senior of the Windows Secrets Newsletter. He was formerly editor of Byte Magazine (1987–91), editorial director of CMP Media (1991–97), and editor of the LangaList e-mail newsletter from its origin in 1997 until its merger with Windows Secrets in November 2006.
What — or who — is using your connection?
 |
By Ian “Gizmo” Richards
Unexpected disk and processor activity on your PC is worrisome, but unexplained Internet activity is more troubling. When a PC suddenly starts uploading or downloading data from the Internet, a bit of paranoia is perfectly reasonable — possibly your system is infected with a virus or other malware. In this report, I’ll give you some tips and tools for diagnosing unexplained Internet traffic. |
Monitoring tools for watching Internet traffic
You can’t identify mysterious Internet activity if you don’t know there is activity. In the days of dial-up modems, flashing lights on the modem let you know when real information was flowing back and forth. However, the lights on today’s ADSL and cable modems can flash almost continuously, making them a poor guide to intensive Internet activity.
The Windows network icon (showing two linked computers) in the system tray will also flash when Internet transfers take place. But its flash likewise represents local network activity — making it, too, an unreliable guide. It’s also been dropped from Windows 7.
The best way to monitor the volume of Internet traffic through your PC is to install a download/upload metering utility. Most of these simple applications display on your desktop or system tray a small graph of current Internet traffic. The better apps trigger alarms when traffic reaches specified levels.
My favorite is NetMeter, available as a tiny 575KB download directly from the publisher’s site. It looks deceptively bare-bones when first installed, but it’s a powerful utility and easy to customize.
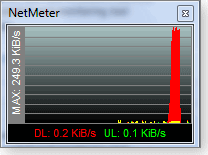
Figure 1. NetMeter offers many ways to measure network activity.
Upload/download meters are invaluable for alerting you to unexpected internet activity, but they won’t help you identify what’s causing the activity. For that you need a monitoring tool that identifies individual internet connections.
In my previous column, I discussed Process Hacker, a free utility for diagnosing system processes running in PCs. But this app is also an excellent download/upload meter. The network tab in Process Hacker identifies programs that create open network connections and also indicates current uploading and downloading activity with red and green graph bars.
The most useful task Process Hacker performs is identifying the Internet Protocol addresses of computers at the far end of the connection. If you know the remote IP address, you can use a free Web-based IP location service — such as www.iplocation.net’s site — to find the remote computer’s geographic location and possibly its owner. If it’s in North Korea or some other location that’s known to harbor hackers, you might have a serious problem.

Figure 2. Process Hacker’s list of remote IP addresses can help determine whether Internet data is coming from a suspect location.
Windows tools and firewalls meter traffic
Many firewalls, including the popular free Comodo firewall and Online Armor, have the capacity to show your active Internet connections. Some even display the total bytes uploaded and downloaded by each program using the Internet. Figure 3, for example, shows Comodo’s outbound connections chart.

Figure 3. The free Comodo firewall displays a detailed summary of Internet activity.
Vista’s and Windows 7’s built-in Windows Performance Monitor is another excellent tool for chasing down mysterious Internet activity. To open the performance monitor, open Windows Task Manager, click the Performance tab, then click the Resource monitor button. Next, click the Network tab to see a list of programs currently sending or receiving data over the Internet.
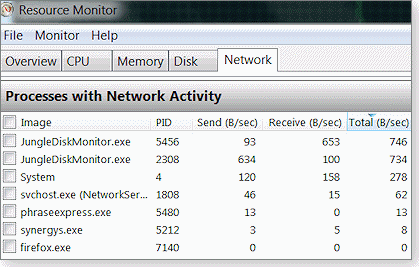
Figure 4. The Network Activity tool in Vista and Win7 provides a wealth of Internet traffic information.
Clicking on the Network Activity, TCP Connections, and Listening Ports headings reveals more details about the remote computers’ IP addresses.

Figure 5. Remote IP addresses displayed in the Resource Monitor’s Network Activity window.
Information in all three panels can be tied together using the process name (Image) and process identification number (PID). That means you can easily identify the program causing the activity, the nature of the activity, and the URL of the remote computer at the other end of the connection. A quick lookup of the remote computer URL at IPLocation.net can complete the picture.
Firewalls help, but still have security holes
Why do you need to worry about network traffic if you have a firewall to keep threats at bay?
If you are using a top firewall such as Comodo or Online Armor, you have a substantial level of protection. Even these firewalls, however, are not perfect — and less-robust firewalls may have substantial security holes. Windows’ built-in firewalls have virtually no outbound protection, so you are not protected when a hacker tries to pull private information off your PC.
So there you have it. Locating the source of unexpected Internet activity is fairly easy, once you know which tools to use. The key is knowing when unexpectedly high Internet activity is taking place.
| Have more info on this subject? Post your tip in the WS Columns forum. |
Ian “Gizmo” Richards is senior editor of the Windows Secrets Newsletter. He was formerly editor of the Support Alert Newsletter, which merged with Windows Secrets in July 2008.
Tailor Windows to work the way you do
 |
By Scott Dunn
One of my favorite things about Windows is the many ways you can reconfigure it to suit your own style of work. From startup to shutdown, the following tips can give you a Windows makeover you can live with. |
Customizing Windows 7’s new Aero Peek control
When you need to clear a cluttered Windows screen instantly, the Show Desktop Taskbar button is a handy — and often overlooked — tool. With Windows 7, Microsoft moved Show Desktop to the far-right side of the screen (by the clock), where it’s easier to find, and added Aero Peek: hover the mouse pointer over the Show Desktop button (without clicking it), and all open windows turn transparent, showing only their outline on the desktop.
You may like this feature but want the effect to kick in more slowly. You can do that by editing the Windows Registry. Click Start, Run; type regedit; and click OK. Click Yes if prompted by User Account Control.
Using the navigation tree on the left, make your way to:
HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Explorer Advanced
Click the Advanced icon on the left and right-click the right pane. Click New, DWORD (32-bit) Value. Type DesktopLivePreviewHoverTime and press Enter to name your new setting. Close Regedit.
To see transparency instantly while hovering over the Show Desktop button, leave the new setting at the default, 0. If you want to build in a delay, double-click the Show Desktop icon and enter a number in milliseconds into the Value Data box. For example, for a three-second delay, type 3000 and click OK. The change will not take effect until you Log off Windows and sign back on.
You don’t need Regedit to turn the feature off altogether — just right-click an empty spot on the taskbar and choose Properties. In the Taskbar tab, uncheck Use Aero Peek to preview the desktop. Click OK.
Ease of Access Center turns off Aero Snap
Windows 7 users may develop a love-hate relationship with Aero Snap. As I noted in the February 25 newsletter, Aero Snap is a quick way to maximize windows by dragging them to the top of the screen. Snap also allows you to place them to the right and left screen edges using the keyboard arrow keys. Some users will find this a handy tool; others will just find it annoying. If you are among the latter, you can easily turn it off.
Press the Windows key or click Start and type ease of access. In the Ease of Access Center window, click on any of the following:
- Make the mouse easier to use
- Make the keyboard easier to use
- Make it easier to focus on tasks
Find and check the box labeled Prevent windows from being automatically arranged when moved to the edge of the screen. Click OK.
Customize shut-down options in Vista and Win 7
Windows XP users are familiar with its three shut-down options: Standby, Turn Off, and Restart. So some users who jumped to Windows Vista were surprised — and annoyed — that clicking the power icon yielded only one choice: Sleep mode. It took an extra and somewhat hidden step to shut down completely.
In Win 7, the Shut Down button once again gives you choices, but wouldn’t you rather just have Windows default to the option you use most?
It can. Just right-click the Start button and choose Properties. In the Start Menu tab, choose an option from the Power button action menu and click OK. (See Figure 1.)

Figure 1. Taskbar and Start Menu Properties let you change Windows 7’s default shutdown option.
Despite mention of the “power button,” this option affects only the Start menu, not the actual power button on the PC. To change that, do the following:
Press the Windows key or click Start; type power options. Click Change plan settings for whichever power-saving plan you wish to change, then click Change advanced power settings.
To customize the hardware power button, click the + next to Power button action and choose an option. (In portable PCs, it’s under “Power buttons and lid.”)
In Vista, this window also lets you customize the Start menu’s shutdown option. Click the + by the Start menu power button and choose an option for the default Start menu behavior. Click OK.
Launch documents full-screen automatically
If you live in Photoshop, Excel or similar applications, you may want to launch it automatically in full-screen. Other apps are fine to launch automatically minimized — Windows Media Player, for example, lets you play music from the taskbar.
To force an application, document, or folder to start as minimized, normal, or maximized, create a shortcut to it. (Note that nearly all icons on the Start menu are already shortcuts.) Right-click the shortcut and choose Properties. In the Shortcut tab, choose your preference from the Run drop-down menu. Click OK. The next time you click that shortcut, it will launch as you have set it.
Bonus tip: If you think you’ll want to launch an application in different states on different occasions, make multiple shortcuts for that application. Then give each of them a different Run option.
What are your favorite ways for improving Windows? Let me know and I’ll share more in a future column.
| Have more info on this subject? Post your tip in the WS Columns forum. |
Scott Dunn is a contributing editor of the Windows Secrets Newsletter. He has more than 20 years of experience as a technical writer and editor and has won multiple business-press awards.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Google’s Veo3 video generator. Before you ask: yes, everything is AI here
by
Alex5723
6 hours, 6 minutes ago -
Flash Drive Eject Error for Still In Use
by
J9438
7 hours, 38 minutes ago -
Windows 11 Insider Preview build 27863 released to Canary
by
joep517
1 day ago -
Windows 11 Insider Preview build 26120.4161 (24H2) released to BETA
by
joep517
1 day ago -
AI model turns to blackmail when engineers try to take it offline
by
Cybertooth
4 hours, 38 minutes ago -
Migrate off MS365 to Apple Products
by
dmt_3904
5 hours, 26 minutes ago -
Login screen icon
by
CWBillow
36 minutes ago -
AI coming to everything
by
Susan Bradley
3 hours, 25 minutes ago -
Mozilla : Pocket shuts down July 8, 2025, Fakespot shuts down on July 1, 2025
by
Alex5723
1 day, 16 hours ago -
No Screen TurnOff???
by
CWBillow
1 day, 16 hours ago -
Identify a dynamic range to then be used in another formula
by
BigDaddy07
1 day, 17 hours ago -
InfoStealer Malware Data Breach Exposed 184 Million Logins and Passwords
by
Alex5723
2 days, 5 hours ago -
How well does your browser block trackers?
by
n0ads
1 day, 15 hours ago -
You can’t handle me
by
Susan Bradley
15 hours, 24 minutes ago -
Chrome Can Now Change Your Weak Passwords for You
by
Alex5723
1 day, 8 hours ago -
Microsoft: Over 394,000 Windows PCs infected by Lumma malware, affects Chrome..
by
Alex5723
2 days, 16 hours ago -
Signal vs Microsoft’s Recall ; By Default, Signal Doesn’t Recall
by
Alex5723
1 day, 20 hours ago -
Internet Archive : This is where all of The Internet is stored
by
Alex5723
2 days, 16 hours ago -
iPhone 7 Plus and the iPhone 8 on Vantage list
by
Alex5723
2 days, 17 hours ago -
Lumma malware takedown
by
EyesOnWindows
2 days, 5 hours ago -
“kill switches” found in Chinese made power inverters
by
Alex5723
3 days, 1 hour ago -
Windows 11 – InControl vs pausing Windows updates
by
Kathy Stevens
3 days, 1 hour ago -
Meet Gemini in Chrome
by
Alex5723
3 days, 5 hours ago -
DuckDuckGo’s Duck.ai added GPT-4o mini
by
Alex5723
3 days, 5 hours ago -
Trump signs Take It Down Act
by
Alex5723
3 days, 13 hours ago -
Do you have a maintenance window?
by
Susan Bradley
1 day, 18 hours ago -
Freshly discovered bug in OpenPGP.js undermines whole point of encrypted comms
by
Nibbled To Death By Ducks
2 days, 16 hours ago -
Cox Communications and Charter Communications to merge
by
not so anon
3 days, 17 hours ago -
Help with WD usb driver on Windows 11
by
Tex265
47 minutes ago -
hibernate activation
by
e_belmont
4 days, 2 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

