
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Get your system ready for a Windows 7 upgrade
In this issue
- TOP STORY: Get your system ready for a Windows 7 upgrade
- KNOWN ISSUES: Netbook news on Windows 7 is hype, Woody finds
- WACKY WEB WEEK: Google's invisible city is an identity saver
- LANGALIST PLUS: Restore a hard drive's lost boot sector
- BEST SOFTWARE: Manually remove programs that lack uninstallers
- WOODY'S WINDOWS: Sharing is easy with Windows 7's homegroups
Get your system ready for a Windows 7 upgrade
 By Scott Spanbauer
By Scott Spanbauer
Removing unneeded applications and making sure your hardware devices will work with Windows 7 are good things to do before you purchase and install the new operating system.
A merciless approach — ruthlessly excising software clutter prior to the OS upgrade — will help ensure that the process goes smoothly.
With Windows 7’s official release to consumers just weeks away, you may be champing at the bit to upgrade your existing system. If you choose to install Win7 on an old Vista machine, however, a wise precaution is to clear out some of the clutter the machine has collected over the years.
First, determine which version of Windows 7 is best for your needs. In his July 16 Top Story, WS contributing editor Woody Leonhard examines the various Win7 editions. He concludes that, for most people, the less-expensive Home Premium version is a better choice than either Windows 7 Professional or Ultimate.
(Note that Windows 7 Starter Edition is available only preinstalled on netbooks. Woody’s June 4 Top Story discusses the design limitations Microsoft is placing on netbooks running Windows 7 Starter.)
Once you’ve selected a Windows 7 version, download and run the beta of Microsoft’s Windows 7 Upgrade Advisor, which you’ll find on the company’s Get Windows 7 page. The utility will indicate whether there are known Windows 7 compatibility problems with any devices on your PC. If so, the advisor may even suggest how to resolve the problem.
Microsoft’s page states that systems running Vista will usually have no problem moving to Windows 7. Conversely, if you’re currently using XP or any other operating system, the company says you should “experience Windows 7 on a new PC.” That may be good advice, but I’m the kind of guy who likes to find out for myself rather than take Microsoft’s word for it.
To be sure, many (most?) Windows 7 hardware and software incompatibilities won’t become known until after the OS ships on Oct. 22. This means you should take the advisor’s results at this point with a grain of salt.
The current beta version of the advisor is available only in English. Also, using the page requires that you share information about your system with Microsoft, though the company promises that “no information will be used to identify or contact you.”
Dump the applications you no longer use
Uninstalling unused applications not only frees disk space, it also returns precious system memory to Windows and applications, shortening their start-up times. If you’re planning an upgrade to Windows 7, moreover, removing nonessential programs reduces the odds that you’ll encounter incompatibilities during the upgrade process.
We’re often our own worst enemies when it comes to unnecessary software installations. A program catches our eye, we give it a spin or two, and then we promptly forget all about it. In addition to wasting disk space and cluttering the Start menu, the software can become a security threat as it ages and goes unpatched.
If you plan to use a program infrequently in the future, it may be best to install it only long enough to use it and then uninstall it until the next time you need it. A side benefit of this approach is that you may be more likely to try alternative applications — possibly smaller and faster ones — instead of sticking with whatever program’s already on the system.
Another option is to exile some programs from your computer’s hard drive to removable media. Firefox, OpenOffice.org, 7-Zip, Java, and other popular Windows apps and utilities are now available in portable versions you can install on a USB drive. This keeps them handy without adding them to the Registry or Start menu.
WS senior editor Gizmo Richards reported on how to choose and use portable applications in his June 18 and July 2 Best Software columns (paid content).
Free utilities make system cleanup a breeze
The problem with the uninstall utilities that ship with most apps is that they tend to leave behind files, folders, shortcuts, and Registry entries.
Gizmo’s Sept. 17 Best Software column (paid content) describes two free uninstall utilities that do a more-thorough job of excising applications from your system: ZSoft Uninstaller and Revo Uninstaller. You’ll find links to download the former on the ZSoft Software site and the latter on the VS Revo Group site.
Also, in today’s Best Software column, Gizmo covers the manual approach to removing programs when an uninstall routine is unavailable.
After dumping all but the essential programs on your system, take a moment to jettison other superfluous files. Right-click the Recycle Bin icon on the desktop and choose Empty Recycle Bin to really delete those deleted files. Next, right-click your hard drive’s icon in Windows Explorer or any folder window and choose Properties, Disk Cleanup.
Finally, defragment your hard disk. You can start Windows’ built-in disk defragmenter from the drive’s Properties dialog box by choosing the Tools tab and clicking Defragment Now. However, a third-party tool such as J.C. Kessels’ free MyDefrag (formerly JKDefrag) is faster and more thorough. You’ll find a download link for the program on the MyDefrag site.
Once in a while, you’ll run into a program that just can’t be pried loose from your Windows installation by using Windows’ own tools. WS editor-at-large Fred Langa presents his favorite uninstall tools, including Microsoft’s free Windows Installer CleanUp Utility and jv16 PowerTools, in his March 26 LangaList Plus column, “Clean up the mess left by incomplete uninstalls” (paid content).
Prepare your PC for the big Win7 migration
There are three more steps to take prior to beginning the upgrade.
First, use Windows’ free, built-in Backup utility or another backup program to copy your data files to a removable medium. You’ll find instructions for using Windows Backup in Microsoft Knowledge Base article 308422. Gizmo reviewed third-party backup programs on Sept. 4 and Sept. 18, 2008 (paid content).
Second, gather the installation discs and serial numbers for your applications. If you do a clean install of Windows 7, you’ll need the discs and software license numbers to reinstall the programs once the upgrade is finished. Also, be prepared to download and install any patches and security updates for the programs from the vendors’ sites.
Third, be prepared for any unexpected hardware glitches. Visit the download section of your PC vendor’s site to find the Windows 7 drivers for your specific video and network adapters. Save the Win7 version of the drivers for your system’s adapters on a USB drive or other removable medium. If something goes wrong with your upgrade, installing the new drivers you’ve saved in this way may solve the problem.
There’s no reason to start your Windows 7 sojourn with a poky PC. By banishing the bloat beforehand, you’ll spend more time working (or playing) and much less time watching the Windows hourglass.
| UPDATE 2009-10-08: In the Oct. 8, 2009, Known Issues column, readers describe how to prevent a reinstalled application from activating. They also suggest additional areas of Windows to clean out prior to upgrading from Vista to Windows 7. |
Scott Spanbauer writes frequently for PC World, Business 2.0, CIO, Forbes ASAP, and Fortune Small Business. He has contributed to several books and was technical reviewer of Jim Aspinwall’s PC Hacks.
Netbook news on Windows 7 is hype, Woody finds
 By Dennis O’Reilly
By Dennis O’Reilly
This week, several tech news sources reported that Microsoft had lifted restrictions on which versions of Windows 7 could be installed on netbooks.
In fact, WS contributing editor Woody Leonhard reported months ago that no such restrictions were in place and that netbook makers could install any version of Win7.
On Sept. 25, TG Daily blogged that Microsoft would no longer restrict netbook OEMs to Win7’s weak “Starter Edition.”
That sounds like quite a scoop. But in his June 4 Top Story, Woody reported that MS would allow any version of Win7 to be installed (although OEMs would of course be charged more for higher versions).
Our esteemed contributing editor would like to set the blogosphere straight on the matter:
- “Recent reports ping-ponging around the Web breathlessly claim that ‘Microsoft confirms no Windows 7 restrictions for netbooks.’ The gist of the claim is that netbook manufacturers will now be allowed to sell their wares with any version of Windows 7 preinstalled. Supposedly, big bad Microsoft has relented and won’t force Windows 7 Starter Edition on the netbook masses.
“Pardon me, but that’s horse pucky. Microsoft has never had any such restriction. This news ain’t news at all.
“As I wrote on June 4, Microsoft did set restrictions on the maximum hardware that Windows 7 Starter Edition can be installed on. The ‘Softies insist that netbook manufacturers can offer Starter Edition only on netbooks that are suitably stunted. The implication is that you’ll have to pay significantly more for Windows 7 if you want to move up to a more-powerful netbook.
“But there’s never been a restriction saying that netbook manufacturers had to sell Starter Edition. Restricting the super-discounted Starter Edition to skimpy hardware is just a Microsoft marketing move. It’s designed to provide a cheap, weak version of Win7 for entry-level netbooks rather than abandoning the low end to penguin-based Linux alternatives.
“There are some implications to the hardware restrictions that are more sinister, as I described in my June 4 story. But Microsoft has never said it would force netbook manufacturers to sell only Starter Edition.
“Starter Edition is a crock, anyway. Any netbook worth its salt works just fine with Win7 Home Premium. All through the beta and release candidate stages, I ran Windows 7 Ultimate on a rather sedate ASUS 1000H netbook with nary a hiccup. It’s penny-wise and pound-foolish for anyone to buy a netbook with Starter Edition preinstalled.
“And for the Chicken Littles on the Web: cut the fearmongering and get the details right, OK?”
You’ll find more on preparing your PC for a Windows 7 upgrade in today’s Top Story by Scott Spanbauer.
The Feds go to lengths to protect online access
In the Sept. 10 and Sept. 24 Top Stories, WS contributing editor Scott Dunn described ways you can try to outwit keyloggers if you have no choice but to sign in to a Web site from a public PC. If you really need to protect your password, however, take a tip from the U.S. Department of the Treasury, as Jerry Smith describes:
- “The U.S. Treasury has a very robust system for maintaining the security of Internet-accessed accounts under its Treasury Direct program. Treasury Direct is used for buying and holding savings bonds and other Treasury investments.
“In the first stage of login, the user enters a 10-digit account number using the computer keyboard. Then a password of at least 8 characters is entered using a virtual keyboard displayed on the login screen. The virtual keyboard has a random arrangement of keys that changes each time you log in.
“Once this step is completed, a new screen is displayed, requiring information from an access card that has been provided to the account holder. The first step on this screen is to select the correct access-card number from a choice of three different numbers that are shown.
“Then, three grid coordinates are provided that correspond to letters or numbers on a 5-by-10 grid on the access card. The corresponding values must be entered using a randomized virtual keyboard also.
“The first time or two that you log in, this process seems a little tedious. However, after a few logins, you become comfortable with it and can log in quickly. I worry about the security of my bank accounts because of the relative ease with which they can be broken into, but I don’t worry at all about my Treasury Direct account.”
The access card provided to users by the Treasury contains numbers that a hacker wouldn’t know how to display on the screen. Several online banking sites use similar techniques, which are known as two-factor authentication. The two factors include something you know (such as your password) and something physical — such as an ID card, token, fingerprint, retinal scan, and so on.
Two-factor authentication isn’t perfect. A sophisticated “man in the middle” attack can exploit a user’s credentials, as reported by Dancho Danchev on his Zero Day blog at PCMag.com.
But a combination of factors is better than a simple password that could easily be copied by a keylogger when you’re using an untrusted PC.
| Reader Jerry Smith will receive a gift certificate for a book, CD, or DVD of his choice for sending a tip we printed. Send us your tips via the Windows Secrets contact page. |
The Known Issues column brings you readers’ comments on our recent articles. Dennis O’Reilly is technical editor of WindowsSecrets.com.
Google's invisible city is an identity saver
 |
By Stephanie Small
Identity theft is something everyone fears these days. With the invention of the Internet, people can simply search for your personal information and even find out where you live. That’s why, as this hilarious video explains, Google invented its new “opt out” feature. It allows people to move to a remote village, where they’re unable to contact anyone from the outside world. It’s even invisible to Google Maps, because the city is contained in a metallic box. Finally, the answer has arrived for the utmost in identity protection! Play the video |
Restore a hard drive's lost boot sector
 |
By Fred Langa
A hard drive without a boot sector means big trouble — but the situation is not necessarily fatal. Without your hard drive’s boot sector, your PC can’t boot or access any software on the hard drive; but thankfully, Windows’ built-in repair tools can put things right. |
Singing the ‘can’t boot my drive’ blues
Karl Barton encountered one of the worst problems that can happen to a hard drive, perhaps second in severity only to a mechanical head crash:
- “My mother’s Dell Inspiron 8100 died the other day. Through the process of trying to find out what went wrong with it, we lost the boot sector of her hard drive. What can I do to recover it without losing the information on it?
“I purchased a USB-to-SATA/IDE adapter that recognizes it there, but nothing shows in Windows Explorer. I tried another drive and it shows up. Is there a safe-and-easy way to repair the boot sector without losing the information on it?”
Probably, yes. If it’s an XP system, you can use the XP Recovery Console’s fixMBR and fixBoot commands to rebuild the Master Boot Record (MBR) and repair the damaged Windows boot sector.
The information you’ll need for XP is in Microsoft Knowledge Base article 314058, “Description of the Windows XP Recovery Console for advanced users.”
Vista’s version of the Recovery Console is called the Windows Recovery Environment (RE) and operates quite differently. The Bootrec.exe tool in Windows RE serves a function similar to XP’s fixMBR and fixBoot commands. Bootrec.exe lets you troubleshoot and repair various boot and startup issues. (BTW: Windows 7 uses the same Windows RE as Vista.)
For more information, see MS KB article 927392, “How to use the Bootrec.exe tool in the Windows Recovery Environment to troubleshoot and repair startup issues in Windows Vista.”
If Windows’ own tools don’t restore the drive’s boot sector, commercial programs such as Active Data Recovery Software’s Active@ Partition Recovery (U.S. $40) may help. Read more about the utility on the vendor’s site.
If you’re seriously old-school, you can manually edit the boot sector, as described in an article on the NTFS.com site. Just make sure you speak hexadecimal!
Reviving an ancient DOS app in Vista
R. Neil Capper has a mission-critical DOS program (yes, they still exist). Trouble is, it stopped working after a crash:
- “I have an old DOS medical-office program with an essential patient database that dates back to Windows 3.1 and Windows 98. I’m able to run the DOS program in Windows XP and was also able to do so in Vista, until a recent crash.
“Since the crash, any attempt to load the program in Vista fails. A popup dialog box states simply ‘[program].exe is not a valid Win32 application.’
“I’ve tried unsuccessfully to load the .exe program by left-clicking, by using the Run box, and by using the command line. Can you help?”
The sequence of events — the program worked fine, there was a crash, the program is broken — strongly suggests that the .exe file was corrupted by the crash. The simplest fix would be to reinstall a copy of the old software from the original disc or backups. (You do have backups, don’t you?)
It’s also possible that the program’s compatibility settings got scrambled. You can make sure they’re OK by running Vista’s built-in Compatibility Wizard, which is specifically designed to help you run old-style programs in a carefully constrained environment within Windows. See MS KB article 555917, “How to start the Program Compatibility Wizard in Windows Vista.”
Likewise, it’s possible that the crash resulted in the program being erroneously flagged as being a Web download, and thus may be “blocked” by Windows’ security. Right-click the program, select Properties, choose “unblock,” and see if that helps.
One of these approaches — reinstalling a fresh, known-good copy of the original program and/or correcting Vista’s settings for the program — should get your prehistoric app going again!
Lost my Outlook Express contacts — again!
A reader named Vicki wants to stop losing her contact list:
- “I’ve lost my Outlook Express contacts three times over the years when I’ve had to have a new PC. Is there a way of saving the contacts onto a USB [drive], for instance?”
Sure, Vicki! While many third-party tools automate the contact-backup process, you can also back up your contacts entirely from within Outlook Express itself. Microsoft KB article 270670, “How to back up and to restore Outlook Express data,” walks you through the process.
If the official Microsoft verbiage is too geeky — it can be, at times — the folks at Free Email Tutorials have a nicely illustrated explanation of the same information. See the site’s article titled “Backup Outlook Express address book contacts” for the inside scoop.
Oops! Trialware/freeware confusion strikes
Long-time reader Henry S. Winokur properly takes me to the woodshed for an error in my Sept. 17 column:
- “I’m flabbergasted that Fred says that jv16 PowerTools is free, since he’s been using it for a very long time. I use it on his recommendation, but it most certainly is not free. It’s free for 30 days, but if you intend to use it longer than that, you’re supposed to pay for it.
“Considering what a good job it does, even at $30, it’s cheap.”
Thank you, Henry. Yes, jv16 PowerTools is free to try and is fully functional as trialware — no feature lockouts or other restrictions — but the program will time out after 30 days unless you purchase a license.
I apologize for my confusion and will now go eat some ginkgo biloba.
Where did all the nasty photos come from?
H. Berrien Zettle has a very prickly problem:
- “I hope you might have some explanation for a very peculiar happening that my daughter experienced recently. She had taken some photos with her digital camera (Samsung), downloaded them to her laptop (running XP), and e-mailed them to a family friend in Colombia, South America.
“The eight-year-old son of one of her friends opened the e-mail to view the pictures and found that several pornographic photos had somehow become attached to the file, along with the photos my daughter had attached to her e-mail. Can you suggest any reason for this aberration? It’s the first time I’ve ever heard of this happening.”
Oh, dear.
The cause of the uninvited images could be innocuous. It’s possible that separate e-mails got concatenated into one. I’ve had this happen — very rarely — on my systems. It’s as if an e-mail loses its end-of-file marker and gets seamlessly connected to the following message.
Upon reading the conjoined e-mails, you see the first one normally, but within the same e-mail, the headers and text of the next message appear. The result is messy, hard to read, and clearly caused by a software error.
As I mentioned, such concatenated e-mails are very rare and usually happen only after your e-mail program crashes. In my experience, only the body of the messages is involved, never e-mail attachments.
For this to happen, the e-mail immediately after your daughter’s would have to be the one with the objectionable photos, and the header information — showing who sent the X-rated photos — would still be visible. Thus it would be obvious what was going on.
I suppose there could be other equally rare scenarios involving errors by the e-mail server or ISP, but to be honest, I can’t think of a way that the naughty photos would just arrive from nowhere, seamlessly attached to your daughter’s e-mail.
It’s much more likely that the images really did come from your daughter’s camera or her system. Perhaps she loaned the camera or PC to someone else who took or saved the photos.
There are obvious issues of privacy and trust wrapped up in this. A lot will depend on how old your daughter is and what kind of relationship you have with her. But if you want to find out where the pictures came from — maybe you don’t — you could start your forensics by checking your daughter’s “sent” folder to see if the questionable photos are in the original copy of the e-mail. If they’re there, then the photos were attached inside your daughter’s e-mail client, not in Colombia or en route.
You might also ask your Colombian friends to send the bad photos back; you or your daughter could use the photos’ names, dates, and sizes to search for similar items on your daughter’s PC and perhaps track them down that way.
Most digital cameras also encode EXIF (Exchangeable Image File Format) data along with the photos. EXIF data can tell you what camera took the photos, the date the photos were taken, and more. Some image-processing software can show you the EXIF data directly, and numerous standalone tools do the same thing. See “How to read EXIF data from your image files” on CelluTips’ EXIF page for more on the technology.
You can also check the camera’s own memory to see what’s there. Any capable “undelete” or file-recovery software will see and recover any recently erased photos in the camera’s memory. The excellent Major Geeks download site has a long list of such tools.
| UPDATE 2009-10-15: In his Oct. 15 column, Fred presents two other possible explanations from readers for the appearance of the unwanted photographs. |
Good luck with this. Technology can help you find out where the photos came from, but your heart will have to guide you from there.
Fred Langa is editor-at-large of the Windows Secrets Newsletter. He was formerly editor of Byte Magazine (1987–91), editorial director of CMP Media (1991–97), and editor of the LangaList e-mail newsletter from its origin in 1997 until its merger with Windows Secrets in November 2006.
Manually remove programs that lack uninstallers
 |
By Ian “Gizmo” Richards
It will happen to you one day: You’ll try to uninstall a software program and then discover that no uninstaller is provided. Thankfully, it’s usually possible to manually remove programs lacking their own uninstall option. |
Failed installations can leave your PC hanging
There are two ways you can end up without an uninstall option. The first is when the program installation itself fails and as a result the uninstall option provided by the developer is not available. That’s the situation I discussed in my Sept. 17 column, which is the first part of this two-part series.
The second case is when the developer does not provide an uninstall option. This is not all that common with commercial software, but you do strike it with freeware.
In this situation, you’ll need to uninstall the program manually. This is what we’ll be looking at today.
The procedure for uninstalling a program manually can actually be applied to both cases. However, before we start, I should make perfectly clear that manually uninstalling a program is an imperfect procedure. You can never be exactly certain what changes a program makes when it’s installed to your computer. You can take a good guess, but that’s all.
Because there’s some guesswork involved, there’s always a small chance that manually uninstalling the program may cause problems with your computer. For that reason, it’s essential that you back up the Registry beforehand by creating a restore point. To do so, click Start, All Programs, Accessories, System Tools, System Restore. Choose Create a restore point, click Next, and step through the wizard.
A review of the normal installation process
Uninstallation consists of identifying what data has been written to your computer during installation and then deleting it.
That sounds simple enough, but unfortunately, there’s no universal standard for what a program does during installation. It’s up to the program developer to determine exactly what takes place.
That said, most installers do the following:
- Write the program itself to the Program Files folder on your hard drive.
- Create data and user-specific files in the configuration and settings folders on your hard drive.
- Add entries to the Registry.
- Put shortcuts in the Windows Start folder or other locations so that the program and/or its services start with Windows.
Although this is only a rough guide, it helps to identify the location of the program’s various components.
Step 1: Remove the program’s autostart entries
Most programs make changes to your PC when they’re installed, ensuring that they or their services will start every time Windows does. There are many ways of doing this. Manually chasing down the exact method used by the program you want to uninstall can be tedious.
The most efficient way of removing autostart entries is to use a startup utility that monitors all startup locations. My favorite such utility is the free Autoruns from SysInternals (now owned by Microsoft). The program lists absolutely everything that autostarts on your computer. As a bonus, Autoruns itself doesn’t require installation. Visit the Microsoft TechNet site to grab your copy.
Fire up Autoruns and click the Everything tab. Next, click the Publisher tab to sort the listing by publisher. Look for the product or developer name. If the information relates to the program you want to remove, uncheck the box on the left side of its listing. (See Figure 1.)

Figure 1. Uncheck a program’s entry in Autoruns’ Everything tab to prevent the program from starting with Windows.
Be careful to ensure that the program you uncheck is specifically related to the program you want to uninstall. The name of the publisher is a helpful guide but can be misleading if you have more than one program on your PC from that vendor. If in doubt, enter the file name in a search engine and look for clues that it’s associated with the program in question.
The startup program you want to halt may have no publisher name listed. In this case, you’ll have to rely on the file name itself to guide you. Again — if in doubt, search the Internet for the file name.
Don’t worry too much about stopping the wrong program, because unchecking an Autoruns entry merely disables it. You can recheck the box if you run into problems.
After completing this step, reboot your computer to remove any running programs or processes associated with the program you’re uninstalling. You must reboot before proceeding to the next step.
Step 2: Delete all the program’s files
Open the C:Program Files folder and look for a subfolder with the same name as the product you want to uninstall. Once you’ve located the program’s folder, select and delete it and all its contents.
There’s a trap here you need to be aware of. Sometimes, products aren’t installed in the folder of the same name as the product but rather in a subfolder within a folder with the developer’s name. For example, PerfectDisk isn’t installed in the C:Program FilesPerfectDisk folder, as you’d expect, but in the following location:
C:Program FilesRaxcoPerfectDisk
“Raxco” is the name of the developer of PerfectDisk.
The folder you want to delete is the folder named after the product itself, not the folder named after the developer. If you delete the developer’s folder, you may also remove other programs from the same developer that are stored in the same folder.
Step 3: Delete the app’s user and data files
This step’s a little tricky, because user and data files can be located in several different areas on your PC. Worse still, the locations vary in different versions of Windows.
In Windows XP, the most common locations for these files are:
• C:Documents and SettingsuserApplication Data
• C:Documents and SettingsAll UsersApplication Data
• C:Documents and SettingsuserLocal SettingsApplication Data
In these examples, user is your Windows user name.
In Vista and Windows 7, the common locations for program files are:
• C:UsersuserAppDataLocal
• C:UsersuserAppDataLocalLow
• C:UsersuserAppDataRoaming
• C:UsersAll Users
Look in these areas for folders with the same name as the product you’re uninstalling. Once you locate them, delete them. Once again, be aware that the folder you want may be a subfolder located within a folder with the developer’s name. Delete only the product’s subfolder, not the vendor’s folder that contains it.
The folders I’ve listed are the most-common locations. To search for other, more-obscure locations, use Windows’ built-in search function or your desktop-search program to locate files or folders with the same name as the product you want to uninstall. Do a separate search for files or folders with the developer’s name.
For these types of searches, I use the free Everything utility I described in my Feb. 19 column. The Everything app is lightning-fast and extremely thorough in its searches.
Step 4: Remove the program’s Registry entries
Technical hotshots who know how to use Windows’ Registry Editor can remove an unwanted program’s entries by hand. But for most users, I recommend using a third-party Registry cleaner to remove this information. These tools aren’t as thorough as manually deleting the data, but they’re generally safer to use.
Most people have a Registry cleaner (such as Piriform’s popular CCleaner freeware) installed on their system. If you don’t, I suggest you try the free program EasyCleaner, which is available from the vendor’s site. EasyCleaner has an excellent record of cleaning without creating problems.
Using EasyCleaner couldn’t be simpler: just install the program, run a scan, and then delete the erroneous entries it finds.
Step 5: Perform one last general cleanup
To finish the job, click Start and look for any entries on the menu that refer to the program you just deleted, whether in the opening menu or under All Programs. If you find any, right-click the entry and select Delete.
Next, look on your desktop for unwanted icons left over from the program and delete any you find.
Finally, check the Add or Remove Programs applet in Control Panel (in Vista, it’s called Programs and Features) to ensure there’s no entry for the deleted program. There really shouldn’t be, but if there is, you can use CCleaner’s Tools option to remove it. Visit the product’s site to download your copy.
No manual software uninstallation is perfect
After completing these five steps, you should have removed most of the information written to your computer by the program you want to uninstall. However, it’s almost certain that you’ll have missed something:
- The program likely installed DLL modules that will still be in your Windows folder.
- Entries may also have been added by the program to the Windows installer folder.
- The installation may have created Registry values that weren’t cleaned by your Registry cleaner.
- There may be data stored in other obscure locations on your computer.
Most of this remaining information does no harm other than to take up some disk space. You could try hunting it down, but in my experience, it’s better to let sleeping dogs lie.
If you don’t like the idea of this unneeded information cluttering up your computer, reinstall the program you just deleted. But this time, make sure the installation is monitored by an uninstaller such as the free ZSoft Uninstaller. Once the installation is complete, use ZSoft’s program to completely uninstall the program.
All of these uninstall problems can be prevented if you make a practice of monitoring your software installations with an uninstaller such as ZSoft’s. Monitored installations can always be uninstalled, regardless of whether the developer provided an uninstaller or whether the installation failed.
| UPDATE 2009-11-05: In his Nov. 5, 2009, column, Gizmo takes a closer look at the Revo Uninstaller and ZSoft Uninstaller utilities. |
As I said in my last column, an ounce of prevention is worth a pound of cure.
Ian “Gizmo” Richards is senior editor of the Windows Secrets Newsletter. He was formerly editor of the Support Alert Newsletter, which merged with Windows Secrets in July 2008.
Sharing is easy with Windows 7's homegroups
 |
By Woody Leonhard
The most misunderstood new feature in Windows 7 may be homegroups, which lets you share files, media, and printers across Win7 PCs quickly and easily — if you know a few tricks. I’ve seen a lot of bad advice online about Windows 7 homegroups, however, so let’s delve into the belly of the beast to learn the facts. |
What you need to run Windows 7’s homegroups
I talked about homegroups in my May 14 Top Story, “Two big reasons why you’ll like Windows 7.” Microsoft’s new OS is set to appear on store shelves later this month. Unfortunately, misinformation about this important subject is all over the Web. Here are the basics:
• To create or join a homegroup, your PC must be running Windows 7
Systems running Vista and XP can’t participate in homegroups, nor can Macs or Linux computers. That isn’t so dire as it sounds, however.
Regardless of whether your Windows 7 PC is a member of a homegroup, it can still communicate with other computers on your network using the old-fashioned Windows sharing methods you’ve come to know and hate over the years.
Say your network consists of two Windows 7 PCs and an old XP clunker with an attached shared printer. The Win7 PCs can still use the printer. And the XP machine can retrieve data on the homegrouped Windows 7 PCs via the standard XP/Vista peer-to-peer sharing methods. The main difference is that Win7 PCs in a homegroup get folders and printers served up to them on a silver platter.
| UPDATE 2009-11-05: In his Nov. 5, 2009, column, Woody describes how to set up and maintain networks with a mix of Windows 7, Vista, and XP PCs. |
It’s important to note that any Windows 7 PC can join a homegroup, but the system setting up the homegroup must be running a version of Windows 7 other than Starter or Home Basic.
• To set up or join a homegroup, your PC must be attached to a “Home” network
This sounds mysterious, but creating a Home network is really pretty easy. When you set up a network connection, Windows asks whether the link should be treated as a Public, Work, or Home network. Behind the scenes, choosing a network type is just a handy way of selecting a whole bunch of security settings. In Windows 7, choosing a Home network allows your PC to join or create a homegroup.
You say you don’t know whether your system’s on a Home network? Not to worry. Open the Control Panel. Under the Network and Internet heading, choose View network status and tasks. Below the heading “View your active networks” you’ll see a house icon — how homey can you get, eh? — to indicate that you’re hooked into a Home network. (See Figure 1.)

Figure 1. The house icon indicates that you’re connected to a Home network in Windows 7’s Network and Sharing Center.
If you’re on a Work or Public network and want to change to a Home network, click either of the links labeled Work network or Public network, choose Home network, and click Close. Not quite rocket science.
Many folks who write to me are confused about Home networks. “Home” is just a nom de guerre for a bunch of security settings. You don’t have to be at home to run a Home network, and a Home network can include Macs. The term “Home” refers only to the way your PC treats the network. You wouldn’t normally identify a network connection in a public place such as a coffee shop as a “Home” connection. But in most other cases, a Home network will suffice.
• To join an existing homegroup, you have to know the password
Retrieving a homegroup password is easy. Sign in to a PC attached to the homegroup and click Start, Control Panel. Under the Network and Internet heading, click Choose homegroup and sharing options and then select View or print the homegroup password.
• To use a homegroup, your PC must be running IPv6
I’ve heard several complaints from Win7 users who claim homegroups don’t work. In many cases, the situation can be described by the old Walt Kelly Pogoism, “We have met the enemy and he is us.” If you haven’t messed around with the innards of your Windows 7 machine, IPv6 is running by default. But if you’ve been fooling with Mother Nature, you may have turned off IPv6. Your bad.
Setting up a homegroup requires a wake-up call
Every time you attach a Win7 PC to a network and tell Windows you’re using a Home network, the OS sniffs around the network to see whether there are any Windows 7 PCs attached to it. If there are, Windows then checks to determine whether any of the machines belong to a homegroup.
Several people have contacted me to complain that Win7 PCs that are newly attached to a network don’t discover an existing homegroup. The most common reason for the failure? All the PCs in the homegroup are hibernating. To solve the problem, make sure at least one of the systems in the homegroup wakes up. It only takes one.
If Windows 7 doesn’t detect any kindred spirits on the network that are connected to a homegroup, it offers to set up a homegroup for you.
To set up a new homegroup, you must first select which “libraries” to offer to other PCs. For most people, the big question about homegroups is whether you want to share your Documents library with other PCs attached to the homegroup. By default, Windows doesn’t offer to share your Documents library. (See Figure 2.)

Figure 2. Using Win7’s “Create a homegroup” dialog, select the folders you want to share with other PCs in your homegroup.
The precise sharing details — which folders get shared and who has read and write access — can get a bit complicated, although it’s all quite logical. I cover the details in Chapter 1 of Book 7 of Windows 7 All-In-One For Dummies (Wiley). Info on the book is available from Amazon: United States / Canada / Elsewhere
After you select which libraries you want to share, Windows provides a long password for the homegroup. (See Figure 3.) It’s impossible to memorize this password, which is a pain because you have to enter it on each Windows 7 PC that you want to connect to the homegroup.

Figure 3. The homegroup password generated by Windows 7 is difficult to remember, but you can create a password of your own.
If you wish to change the password to something more reasonable, it’s best to do so before any other computers are connected to the homegroup. If you attempt to change the default password later, you’ll have to change the password manually on each PC on the network — blech!
To set your own password, click Finish in the password box, choose View or change homegroup settings, and select Change the password. Follow the steps listed there to enter your own password.
After the homegroup has been established, adding new Windows 7 PCs to the network is a breeze. Simply attach the Win7 computer to the network and identify the network as the “Home” variety. Windows sniffs and sees a homegroup already established, asks whether you want to share your Documents library, and prompts you to type in the homegroup’s password. Ta-da!
Now it’s time to put your homegroup to use
Homegroups are baked into every nook and cranny of Windows 7. For example, when you click Start, Documents, a homegroup list appears on the left. The same thing happens when you select Pictures, Computer, or Music. If you fire up Word 2007 and click File, Open, the homegroups are right there.
Navigating to a homegroup — or a folder in a shared library within a homegroup — is as easy as opening a folder or file on your computer. Media streaming from homegroup computers works in a flash. You can connect to printers on homegroup computers just as easily as setting up a printer on your own computer.
To make a folder available to everyone in your homegroup, simply add the folder to one of your shared libraries. If you share your Documents library, for example, add the folder to your personal Documents folder or to the PC’s Public Documents folder to allow everyone in your homegroup to read, modify, or delete items in the folder.
Sometimes you may want to share a folder with your homegroup without adding it to a shared library. For example, you might want to share your Downloads folder with everyone in the homegroup.
To do so, navigate to the folder, click it once, choose the Share with button at the top of the screen, and select either Homegroup (Read) or Homegroup (Read/Write), depending on how much you trust the other folks in your homegroup. (See Figure 4.)
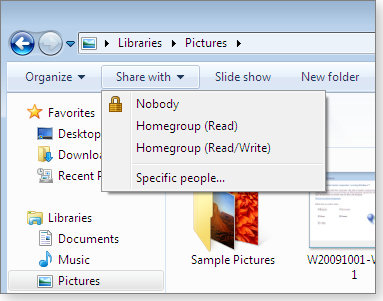
Figure 4. Sharing a folder with other PCs in your homegroup is as easy as selecting it, choosing “Share with,” and clicking one of the four options.
If you want to discontinue sharing a folder with a homegroup, navigate to the folder, click the Share with button, and choose Nobody.
More than one homegroup can exist on a single network, but things quickly get complicated. A particular computer can be part of only one homegroup at a time. You can leave one homegroup and join another, but you can’t be a member of two homegroups at once. (By the by, homegroups work great with Windows Home Server.)
The benefits of homegroups on Win7 far outweigh the quibbles. After the hassles we’ve all experienced when attempting to share files and printers on older versions of Windows, I bet you’ll find homegroups a breath of fresh air.
Woody Leonhard‘s latest books — Windows 7 All-In-One For Dummies and Green Home Computing For Dummies — are currently available in several languages.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Formatting of “Forward”ed e-mails
by
Scott Mills
21 minutes ago -
SmartSwitch PC Updates will only be supported through the MS Store Going Forward
by
PL1
46 minutes ago -
CISA warns of hackers targeting critical oil infrastructure
by
Nibbled To Death By Ducks
9 hours, 46 minutes ago -
AI slop
by
Susan Bradley
8 hours, 57 minutes ago -
Chrome : Using AI with Enhanced Protection mode
by
Alex5723
11 hours, 3 minutes ago -
Two blank icons
by
CR2
17 hours, 32 minutes ago -
Documents, Pictures, Desktop on OneDrive in Windows 11
by
ThePhoenix
19 hours, 57 minutes ago -
End of 10
by
Alex5723
22 hours, 37 minutes ago -
End Of 10 : Move to Linux
by
Alex5723
23 hours, 7 minutes ago -
Single account cannot access printer’s automatic duplex functionality
by
Bruce
19 hours, 35 minutes ago -
test post
by
gtd12345
1 day, 4 hours ago -
Privacy and the Real ID
by
Susan Bradley
18 hours, 46 minutes ago -
MS-DEFCON 2: Deferring that upgrade
by
Susan Bradley
10 hours, 52 minutes ago -
Cant log on to oldergeeks.Com
by
WSJonharnew
1 day, 9 hours ago -
Upgrading from Win 10
by
WSjcgc50
10 hours, 21 minutes ago -
USB webcam / microphone missing after KB5050009 update
by
WSlloydkuhnle
15 minutes ago -
TeleMessage, a modified Signal clone used by US government has been hacked
by
Alex5723
2 days ago -
The story of Windows Longhorn
by
Cybertooth
1 day, 12 hours ago -
Red x next to folder on OneDrive iPadOS
by
dmt_3904
2 days, 2 hours ago -
Are manuals extinct?
by
Susan Bradley
14 hours, 5 minutes ago -
Canonical ditching Sudo for Rust Sudo -rs starting with Ubuntu
by
Alex5723
2 days, 11 hours ago -
Network Issue
by
Casey H
1 day, 22 hours ago -
Fedora Linux is now an official WSL distro
by
Alex5723
2 days, 23 hours ago -
May 2025 Office non-Security updates
by
PKCano
3 days ago -
Windows 10 filehistory including onedrive folder
by
Steve Bondy
3 days, 2 hours ago -
pages print on restart (Win 11 23H2)
by
cyraxote
2 days, 2 hours ago -
Windows 11 Insider Preview build 26200.5581 released to DEV
by
joep517
3 days, 4 hours ago -
Windows 11 Insider Preview build 26120.3950 (24H2) released to BETA
by
joep517
3 days, 4 hours ago -
Proton to drop prices after ruling against “Apple tax”
by
Cybertooth
3 days, 11 hours ago -
24H2 Installer – don’t see Option for non destructive install
by
JP
3 hours, 35 minutes ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

