
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Getting a handle on security certificates
In this issue
- BONUS DOWNLOAD: Bonus helps you get to know Windows 8
- TOP STORY: Getting a handle on security certificates
- LOUNGE LIFE: The fizzy season of festivities and fraud
- WACKY WEB WEEK: Zelda: Not an ordinary New York City matron
- LANGALIST PLUS: Controlling apps that launch unexpectedly
- BEST HARDWARE: Making the hardware switch to Windows 8
Bonus helps you get to know Windows 8
 |
Some Windows 8 differences from its predecessors are more than skin-deep. Among these are security enhancements that bolster your computing safety — especially when you’re behaving prudently. This month, we’re especially pleased to bring you a bonus download from Windows 8 All-in-One for Dummies, written by our very own Woody Leonhard. As a treat to all Windows Secrets subscribers, Woody and Wiley Publishing are offering free excerpts of Chapter 1: “Spies, Spams, Scams” and Chapter 2: “Fighting Viri and Scum.” You’ll learn which hazards to look out for, how to know whether your computer is infected with malware, how to protect yourself with the aid of Windows 8, and more. To download this free excerpt, simply visit your preferences page and save any changes; a download link will appear. Info on the printed book: United States |
Getting a handle on security certificates
We rely on SSL certificates for safe Web surfing and secure online transactions; but how many of us understand the issues surrounding security certs — or those related error messages?
Here’s what you need to know about SSL certificates — and how update KB 2661254 helps solve certificate problems.
Updating the strength of certificates
Windows update KB 2661254 ensures that our operating systems no longer trust any security certificate of fewer than 1024 bits. I’ve had this update in the Patch Watch chart “Wait” category for several months. It’s now time to install it, and I’ll explain why.
But before I discuss certificates, let’s be clear about a closely related topic that’s easily confused with certificate security — browser encryption strength. When you click Internet Explorer’s Tools icon and then About Internet Explorer, you’ll see that the browser has a cipher strength of 256 bits — significantly fewer than the 1024 bits we now require for SSL certificates. The primary reason browsers use only 256-bit encryption is speed. A 2007 TechNet blog states that 128-bit encryption was sufficient for the data we send and receive over the Net. So 256 bits should be a good balance between speed and security.
An MSDN blog describes how a browser securely communicates with a website. Here’s the simple version: The browser starts by sending a handshake offer to the targeted website. The website sends a handshake back. You can see part of this process in the Figure 1 screen capture of a Wireshark report generated as I signed in to windowssecrets.com and entered my username and password. (Wireshark [download site] is an app that lets you see networking transmissions at a deep level.)
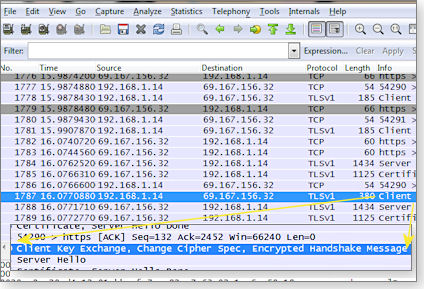
Figure 1. Wireshark shows the step-by-step process of establishing a secure Web connection.
The sign-in process might appear to users as a nearly immediate, one-step process, but Wireshark shows the multiple steps needed to complete the transaction. The details of how it works are too long for this story, but a Wikipedia article does a relatively good job of explaining it. Briefly put: Within moments, your computer and a remote webserver agree to use a secure connection, via a handshake.
When a browser makes a secure connection to a webserver, another critical part of the process ensures that the server is authentic. This is accomplished by means of Secure Socket Layer (SSL) certificates (SSL is the component that encrypts transmitted data). But although 256-bit encryption might be fine for passing our credentials (username and password) and our data over the Net, it’s inadequate to protect certificates.
As mentioned above, KB 2661254 establishes a minimum certificate-encryption strength of 1024 bits. Some security researchers argue that even this level isn’t good enough — especially for online commerce. As far back as 2007, Ecole Polytechnique Fédérale de Lausanne cryptology professor Arjen Lenstra stated, according to a Network World story, that it was merely a matter of time before we saw the end of 1024-bit encryption. As computers get faster, it’s easier to crack encryption.
Fast-forward to 2012, and we’re just installing an update that prevents Windows from accepting security certificates of fewer than 1024 bits.
Ultimately, all websites will have to move to 2048-bit encryption. In its Special Publication 800-57 (PDF), Recommendation for Key Management, the U.S. National Institute of Standards and Technology (NIST) advised that 1024-bit encryption keys could keep us secure for only so long. An Entrust document cites that report as the reason Microsoft will remove 1024-bit certificates from its Root Certificate Program by Dec. 31, 2013 — a little over a year hence.
Again, this is all due to better encryption-cracking tools: faster computers and cloud computing that lets groups of computers crunch away at possible encryption keys — the code that actually unlocks encrypted files. For example, cloudcracker.com is a security site that lets professionals test “WPA-protected wireless networks, crack password hashes, or break document encryption.” Its Chapcrack tool (site) captures network transmissions, uploading a file to a website powered by cloud computing. Pay your fee, wait a few hours, and, voilà, you get a cracked WEP or VPN password. Until recently, that level of computational work took days, weeks, or months.
But why stop at 2048-bit encryption? Why not double that? Or triple it? Again, it comes down to processing speed; having more bits of encryption taxes servers and slows down the initial connection process, as noted in a 2010 semicomplete.com study of SSL latency. It’s that delicate balance between security and our expectation of Internet speed.
Bottom line: it’s time to ensure your systems no longer trust any SSL certificate presented that has less than 1024-bit encryption. Install KB 2661254 soon. I’ve had no problems with the update on my systems.
Getting to the bottom of SSL-cert errors
If you’ve spent any time on the Web, you’ve run across a large and often confusing certificate-error message. Often, these warnings state that the site has a problem with its security certificate but never tell you what exactly the problem is.
Take, for example, the “There is a problem with this website’s security certificate” error shown in Figure 2. It recommends only that you close the suspect webpage. Even if you’re sure the website is safe, the warning will cause some level of worry. Has the site been hacked, or is there merely a technical error? Reluctantly, you click the Continue link, as shown in Figure 2.
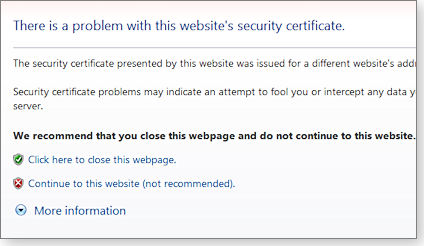
Figure 2. Certificate-error messages often provide little information, leaving you with an uncomfortable decision.
Often, these error messages come from small-business sites using self-signed certificates (Wikipedia info), for which the site owner signs the issued certificate. (More specifically, a service on their server — the certificate authority — issues these SSL certificates.) Self-signed certificates simply ensure that the browser/webserver connection uses SSL encryption.
For many years, Small Business Server 2003 included self-signed certificates as part of its remote-access technology. However, it has increasingly fallen out of favor for two reasons, one of which is those confusing cert-error messages.
It also became harder and harder to get self-signed certificates installed on computers and phones that needed to connect back to the server. For example, securing e-mail between a phone and server typically requires manually installing the certificate on the phone — or instructing the phone to ignore the self-signed cert error. That’s not an easy task on a Windows-based phone.
Typically, when visiting a self-signed certificate site, you have to click Continue to get to the site. From there, you can click the red Certificate Error box, as shown in Figure 3, to find out why the browser doesn’t like the certificate.
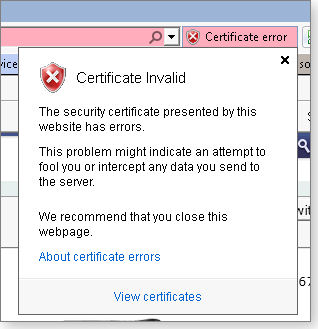
Figure 3. Click the red Certificate Error box to the right of the browser URL bar (IE shown) for more info on the error.
In this case, the error was self-inflicted: I have a printer that has a Web-based console. I use a self-signed certificate provided by the printer manufacturer to protect the site when I sign in with my username and a password. In reality, the site didn’t have an error; when I clicked the view certificates link, the next popup dialog box (see Figure 4) showed that I needed to manually install the self-signed certificate into my browser.
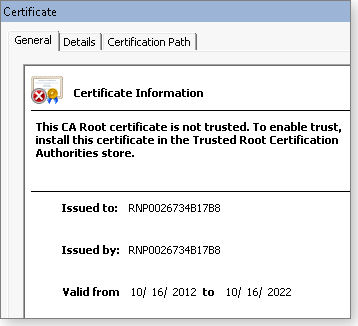
Figure 4. The Certificate Information box shows that the certificate is not flawed; it needs to be installed.
Pages with secured and unsecured content
There’s another common certification-error message. Go to a website that includes SSL security (as noted by the https:// in the URL). While on the site, you get this message: “Do you want to view only the webpage content that was delivered securely?” In this case, the site is providing both https (secure) and http (unsecure) information on the same webpage.

Figure 5. Some sites will deliver secure and unsecure content on the same page.
Typically this occurs when a site uses banner ads or external images on an otherwise secured e-commerce page. (It would be best if websites never included unsecured information on a page containing SSL transactions.) Practically speaking, I recommend clicking the No button. The page will probably have a broken image box or two and blank banner ads, but it should otherwise work.
The root-cert conundrum
Root certificates (Wikipedia definition) are key tools for Web security in Windows. Vista or newer versions of Windows get root certificates automatically; Windows XP systems still need manual updates. KB 931125, a package of root certificates for XP systems, adds new certificates and removes outdated ones.
Typically, I’ve recommended not installing the update if your system was running fine. But every now and then, I get it wrong. So please ignore my previous advice and install KB 931125 from its MS Download Center. According to an MS TechNet document, Microsoft’s Root Certificate Program lets trusted Certificate Authorities (CAs) add or remove their certificates as needed.
There have been cases where a member CA has been tricked, scammed, or hacked and has therefore released a fraudulent certificate. So being on Microsoft’s trusted-root listing comes with a high level of responsibility — and we have to trust this security foundation. (The potential flaw in the system is that if you trust the root certificate, you automatically have to trust all certificates covered by the root.)
To see this certificate/root certificate relationship for yourself, go to the DigiCert help page and enter a website address, such as that of Windows Secrets. As shown in Figure 6, because your system trusts the GeoTrust DV SSL CA certificate, it also trusts the SSL provided by windowssecrets.com’s sign-in page. (GeoTrust is a member of the MS Root Certificate Program.) You never needed to install a windowssecrets.com certificate.
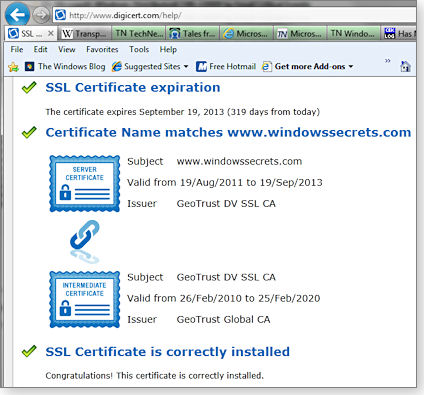
Figure 6. Windows Secrets' site certificate is held within the GeoTrust DV SSL CA certificate.
As mentioned earlier, Vista, Win7, and Win8 get certificate updates automatically, but XP and Windows Server 2003 do not. Consequently, there are instances where an important e-commerce site fails on an XP system, even though the site had a proper SSL certificate — simply because the user had not installed KB 931125.
So once again, install KB 931125 — especially if you stumble on a website that displays errors.
Have you come across SSL certificate errors that leave you scratching your head? Post the error in the Windows Secrets Lounge thread for this article, and we’ll do our best to decipher them.
The fizzy season of festivities and fraud
Before commencing your holiday online gift-buying binge, you might want to fortify yourself with a few cautionary tales.
Lounge member bobprimak tells one this week in the Security & Scams forum and is swiftly joined by others with experiences and advice of their own. We advise you to read all posts before embarking on the holiday charge.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right in to today’s discussions in the Lounge.
Zelda: Not an ordinary New York City matron
 |
By Kathleen Atkins Most people acknowledge the mental toughness required for life in Manhattan, one of the most densely populated peninsulas on the planet. Zelda, who has lived in Battery Park since mid-2003, must be exceptionally resolute — and cannier than many of her kind. She’s a wild turkey. She has been profiled in the New York Times and has an entry in Wikipedia. To widespread rejoicing, Zelda is reported to have survived the recent Superstorm Sandy, which otherwise visited misery on her neighborhood and beyond. She might be, by now, one of the more respected old ladies in New York City. It’s considered bad form to chase her. Play the video And in case you have some extra time on your hands this week, here are some other Thanksgiving links for your entertainment. |
Controlling apps that launch unexpectedly
There can be all sorts of legitimate reasons for software to launch, seemingly on its own.
But when an app frequently and repeatedly launches itself against your wishes, mangled file associations and flawed startup settings could be the cause.
Windows Media Center continually boots
Rune Stenvik’s wrestling with a Windows Media Center installation that keeps launching itself, unbidden.
- “My brother has (probably by mistake) installed Windows Media Center (WMC) on his Vista Home Premium PC.
“WMC opens on startup, even though I’ve unchecked all the appropriate boxes in the Startup and Windows Behavior settings. What’s more, WMC pops up every three or four seconds, and always on top. I can’t stop this program, and it’s d*#@#d annoying.
“After Googling for a solution, I did the following:
- Disabled Windows Media Center Services (via services.msc)
- Removed ehtray.exe from Startup Programs (via WinPatrol)
- Tried killing ehshell.exe, ehmsas.exe, and ehtray.exe in Active Tasks (via WinPatrol)
- In the Registry, under HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft: entered a new key — WindowsMediaCenter — then entered a DWORD Value — MediaCenter — and set its value to 1.
“Result: WMC still pops up as before.
“What more is there to do? Reinstall Vista? Or do you have another solution?”
Excellent troubleshooting! The steps you’ve already taken pretty much prove that Windows Media Center isn’t being launched directly.
If the problem isn’t with Windows Media Center or its settings, then something else — something that might seem unrelated — is causing WMC to run when it shouldn’t.
For example, Vista is especially prone to getting its file associations cross-wired, triggering programs (such as WMC) to launch when they shouldn’t.
Although this kind of problem can happen in any Windows version, it’s so common in Vista that Microsoft offers a free, Vista-only, automated fixit (50194) repair tool in MS Support article 950505. Some manual fixes are also detailed in that article.
In a similar vein, a Vista-specific Microsoft article has additional links for checking and changing Vista’s file associations, controlling autoplay behavior, and setting the default programs for different file types.
If the above doesn’t help, try a third-party freeware tool — File Association Fixer 1.0 (download page) on the MajorGeeks.com site. I can’t personally vouch for the tool (my Vista system has no broken file associations to fix), but it has a good reputation online.
If it’s not a file-association issue, I suggest seeing what’s going on at startup; something there might be indirectly calling on WMC.
The Sept. 6 Top Story, “Near-certain ways to improve PC startup times,” lists methods and free tools to help identify and control exactly what’s going on during system startup.
And if even that doesn’t work (whew!), you can use the information in the June 13 Top Story, “Exploring Windows’ Administrative Tools: Part 2,” to see what else is running when WMC launches. One of those other programs is probably triggering WMC.
Is there an XP Mode in Windows 8?
David Fadness is exploring Windows 8 and — like many of us — has questions.
- “I haven’t heard anyone talk about whether Windows 8 has the ability to run an XP window, as Windows 7 does.”
If you mean the specific application, XP Mode, then no — that software installs and runs only on Win7 Pro, Enterprise, and Ultimate systems. (See the MS Windows XP Mode features page for more info.)
Some Win8 versions contain a limited alternative: the 64-bit versions of Windows 8 Pro and Enterprise ship with Microsoft’s Hyper-V virtualization software (detailed in a TechNet Hyper-V article).
Note that Hyper-V works only on 64-bit PCs equipped with Second Level Address Translation (SLAT) technology — a form of hardware virtualization — and an absolute minimum of 4GB of RAM (more info.)
Fortunately, third-party virtualization tools are far less demanding and work fine for running XP. For example, you can run VMware (site) or VirtualBox (site) — my favorite — on any edition of Win8, including the 32-bit variants.
However, unlike XP Mode, neither Hyper-V nor the third-party virtualization apps come with an operating system already set up. Instead, you’ll have to use a regular installation CD, DVD, or .iso file for XP (or whatever OS you’re setting up). You’ll also need a legitimate license key to activate the virtualized copy of Windows, once it’s running.
Looking for an antivirus for a virtual machine
Robert Glas is running Windows virtualized on a Mac (yes, it happens), but his question applies to any form of virtualized Windows.
-
“I run programs and servers under Windows, using versions from XP to Win7. But several months ago, I ventured into the Apple realm, running a MacBook Pro with an Intel Core i7 processor. I now run Win7 Pro simultaneously on the machine, using Parallels Desktop 7 for Mac. So far, no hiccups.
“My question is about antivirus protection. Currently I’m running two versions of Kaspersky, one for the Mac OS and one for Windows. Is there a reliable product or a licensing arrangement that will let me avoid paying for two subscriptions on one laptop? Or is the virtual environment considered a second machine?”
In most cases, software installed on a host machine and on a virtual machine counts as two separate installations. Most software licenses, in fact, don’t care whether a system is real or virtualized. An installation is an installation, period.
That said, good, free antivirus software is available. For example, I suggest you try Microsoft Security Essentials (site) on your virtualized Windows installation.
Microsoft Security Essentials (MSE) isn’t perfect (nothing is), but it’s worked well for me on all my systems — real and virtualized. What’s more, MSE is self-maintaining; once installed and set up, you can pretty much forget about it.
One more point: With any virtual PC setup, it’s a good idea to run virtual machine(s) for at least a few hours once a month, shortly after the second Tuesday (“Patch Tuesday”), when Microsoft releases new Windows Updates. That way, your virtualized Windows installation can install any/all Windows updates it needs — and also run other routine maintenance tasks, such as MSE’s automatic malware scans.
An easy way to capture fleeting error codes
Out of necessity, Sue Andersen had a brainstorm:
- “I recently had a BSoD problem. But on restart, the error code flashed by so quickly that I couldn’t read it. There might be a better way to capture it, but I videoed the restart with my phone. I then paused the video to read the error code. With that, I fixed the BSoD.”
Nice, Sue!
You can also use your camera to record BIOS settings. Just open the BIOS editor and grab a shot of each page of settings. That way, you’ll have a permanent record of how things are set up.
Sometimes, it pays to “think outside the (PC) box!”
New “House Call” volunteers needed
House Calls is a project (on no fixed schedule) where I visit a reader’s home or business and attempt to diagnose and cure real-life PC problems.
It works like this. From time to time, I issue a call for volunteers for a personal, onsite, PC troubleshooting session. I select one of the more interesting problems plaguing a reader — a problem that might help a wider audience of Windows users. I then pay that reader a personal visit, at no cost to the reader. I do whatever I can in one day to solve the problem (or problems) and make the system run as well as it can.
The results of House Call visits appear in Windows Secrets. For examples, see the April 12 Top Story, “House Call 2012: Fixing a sluggish PC,” or the July 12 Top Story, “House Call 2012: One family, four PCs.”
It’s been almost a year since I last asked for volunteers, so it’s time to refresh the list. But this time, I’d like to target a specific geographic area.
The last two house calls were in the U.S.’s Pacific Northwest and Northeast. Continuing clockwise around the country, I’m asking volunteers from the southeastern U.S. and territories — say, anything east of Texas and south of the Mason-Dixon Line.
If you live in that area, are interested in participating, and will be available sometime within the next month or so, please drop a note to this special mailbox: housecall@langaonline.com.
In the subject line of your e-mail, please place your state. For example:
Subject: FLORIDA
Subject: LOUISIANA
Subject: ALABAMA
In the body of your e-mail, please include your physical address (street and town) and a brief note stating what kind of PC you have, what Windows OS you’re using, how you connect (DSL, cable, etc.), and what problems you’re having with the PC.
If I select you as a potential House Call participant, I’ll contact you to make sure we can make things work logistically and editorially. If it looks to me that things won’t work out for any reason, I’ll pick another name.
I’ll be asking for volunteers from other areas in future issues. So stay tuned!
Thanks!
Making the hardware switch to Windows 8
Planning to buy a new Windows 8 system or upgrade your not-so-old Windows 7 system to the new OS?
You can choose from a bevy of new notebooks and peripheral devices to make the transition to Windows 8’s touchscreen paradigm easier than you might think.
Microsoft hasn’t been cagey about its ambition to catch up with Apple’s iPad success — hence Windows 8’s touch-sensitive, finger-swiping transformation from traditional mouse- and keyboard-oriented computing.
For Microsoft, Windows 8 represents significant progress toward the new computing paradigm. To millions of existing Windows users, Win8 might feel like they’re between a rock and a hard place — they must either purchase a new touchscreen-enabled PC or tough it out with their existing mouse-and-keyboard systems.
Fortunately, there are other alternatives for getting the most out of Windows 8. Here are a few of the most recent options.
A notebook/tablet with a yogi’s flexibility
Trying to get the best of both worlds, Lenovo tried to make a tablet out of a laptop, with its U.S. $999 (and up) IdeaPad Yoga 13 (info site). The result is Frankensteinian, but you have to give Lenovo credit for its effort. With a 180-degree turn of its 13.3-inch display, this otherwise traditional laptop converts into a tablet — even if, at 3.4 pounds, it’s too heavy to serve that purpose well.
For the past week, I’ve been putting the Yoga 13 through its paces. Although I find the iPad-like touch screen easy on the eyes and fingers, the hybrid laptop/tablet format’s success ultimately hangs — so to speak — on its versatile hinge.

Figure 1. The Lenovo IdeaPad Yoga 13's highly flexible screen lets it work as a tablet or a traditional laptop.
The Yoga 13’s 1600-by-900 HD display can be rotated 360 degrees for various configurations. It can be raised like a conventional notebook’s screen for traditional laptop computing, using Lenovo’s typically excellent keyboard. Or swing the screen completely around to put it into the usual, keyboardless, tablet configuration.
Or go for something in between: For example, when on a plane, place the keyboard facing down on the tray table and rotate the screen to a comfortable viewing angle. Or swing the screen around and stand the Yoga in an inverted-V tent position — ideal for tapping, swiping, and scrolling. (When you have it in laptop mode, using touch-screen gestures tends to push the screen farther and farther back. Fortunately, the built-in touchpad is refreshingly responsive.)
Though brilliant in concept, the laptop-to-tablet design has a few drawbacks. First, the machine is an un-tablet-like 3.4 pounds. Next, in tablet mode, the keyboard is resting on whatever surface you’ve placed the Yoga upon. That can’t be good for the keyboard in the long term.
The $1,000 unit I tested (specifically for Best Buy) came loaded with 4GB of RAM, Bluetooth 4.0, 802.11n Wi-Fi, a fixed battery, one USB 2.0 and one USB 3.0 port, an SD memory card slot, and HDMI-video output. The Intel Core i5 processor has integrated graphics, which is not ideal for gaming, but plenty powerful for regular programs, such as Microsoft Office and native Win8 apps.
One assumption with Windows 8 is that many computing activities will be conducted in the cloud. So it’s odd that the Yoga does not include an Ethernet port but is Wi-Fi only, just like tablets.
My test unit included a 128GB, solid-state-drive, which produced whiz-bang, six-second boot times and speedy page refreshes. If 128GB seems a bit tight (nearly half the space on my Yoga was taken up by system files), Lenovo also offers a 256GB drive.
I found huge productivity benefits to using touchscreen gestures. Tasks are faster and easier to accomplish than with multi-step keyboard and mouse commands. Anyone who has grown fond of his or her iPad or other tablet will naturally gravitate to this new-to-Windows paradigm. On the other hand, those who’ve lived in the Windows XP/Vista/Win7 world will face a bit of a learning curve.
And that’s where the benefits of the IdeaPad Yoga 13 lie. It gives the best of both worlds — an OS détente, you might say, easing us into the future of computing. Is it worth the high price? That, of course, is up to you.
Logitech devices make Win8 transition cheaper
For those of us who prefer to upgrade our existing PCs to Windows 8, the defining touchscreen feature is still missing. What’s the point of upgrading, if we’re stuck with the mouse instead of far faster and more efficient onscreen swipes?
Logitech offers a pair of devices that might make the Windows 8 upgrade worthwhile. Its $80 rechargeable Touchpad T650 and $70 Touch Mouse T620 work with Windows 7 and Windows 8, allowing you to use all the finger gestures built in to the new OS.

Figure 2. Logitech's Touch Mouse T620 and Touchpad T650 offer a relatively inexpensive way to add Win8 touch gestures to an upgraded PC.
The Touch Mouse (info site) has the conventional shape you’ve used for years — except there’s no right or left button. The entire surface is touch–sensitive, and the two sides respond to gentle taps, just like the traditional buttons of yore. The smooth top lets you glide your fingers about and make Windows 8 gestures — such as right and left swipes — needed to navigate the desktop, duplicating the motions you’d make on a touchscreen. (With Windows 7, it works like a standard mouse, with left/right buttons and scrolling.)
Logitech has been in the pointing-device business for years, and it shows with the Touch Mouse’s comfortable, round shape and its accurate optical sensor, which allows for precise tracking on nearly any surface.
The Touch Mouse comes with Logitech’s tiny, 2.4 GHz receiver, which works with up to six compatible devices — such as Logitech’s Touchpad T650.
The sturdy, 5.25-inch-square Touchpad T650 (info site) offers the closest approximation of touchscreen navigation on a legacy PC. In other words, you don’t need to buy a new Windows 8 touchscreen laptop if you equip your current Windows 7 system with the T650. My finger movements zoomed across the screen without actually touching the screen.
Pointing, clicking, scrolling, and swiping are fluid and are accomplished with a surprisingly short learning curve. Also, the entire touchpad acts as a large button, so clicking can be performed wherever your finger hovers at the moment. That’s a great improvement from past touchpads that enforced clicks at fixed locations.
Logitech’s SetPoint software is automatically downloaded and installed when you first power up the Touchpad or the Touch Mouse. If you are not sure which gestures are available, the software’s clearly designed, animated help is displayed on each device’s context-sensitive, configuration menus. (See Figure 3.)
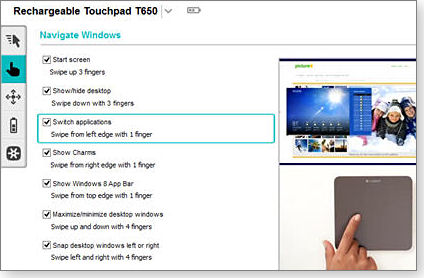
Figure 3. Logitech's SetPoint software displays available touch gestures.
As with the Touch Mouse, the Touchpad works with Windows 7, though without the full set of gestures built into the Win8. Touchpad is also rechargeable and reportedly lasts up to a month on a charge. (The Touch Mouse uses AA batteries.)
Seagate Backup Plus for local, cloud, and social media
Variations of the common external hard drive seem to be multiplying like rabbits. All drive brands are rapidly adding more storage capacity at ever-cheaper prices. Where they differ is read/write speed and included software. The distinguishing feature in Seagate’s new Backup Plus drive (info site) is its proprietary Dashboard backup software.
According to Seagate, the Backup Plus adds social networking to traditional data protection. For example, its Dashboard software connects to your social-network accounts and automatically saves and shares photos.
Here’s a scenario that might be unique to the Backup Plus: You take a photo from a smartphone and post it to Facebook, Twitter, or other social sites. Dashboard will automatically back up the posted content.

Figure 4. Seagate's Backup Plus adds novel archiving for images posted on social networks.
The Backup Plus can be set to use Windows 8’s new backup feature — File History. And for faster transfer speed, the drive comes with a downward-compatible, USB 3.0 interface, which almost all new Win8 systems include.
When I put the drive through its paces, it worked as advertised. Once connected to my PC, the drive was recognized by Windows immediately. And even the least computer-savvy user should be comfortable with the Dashboard’s intuitive interface.
Slim and highly portable, the drive weighs about six ounces and is powered through the USB connection.
Available in 500GB, 750GB, and 1TB capacities, the Backup Plus drives have a suggested retail price of $110 to $130. I found the 500GB model available online for under $90.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Windows 7 ISO /Windows 10 ISO
by
ECWS
1 hour, 42 minutes ago -
No HP software folders
by
fpefpe
2 hours, 27 minutes ago -
Which antivirus apps and VPNs are the most secure in 2025?
by
B. Livingston
27 minutes ago -
Stay connected anywhere
by
Peter Deegan
7 hours, 50 minutes ago -
Copilot, under the table
by
Will Fastie
5 hours, 4 minutes ago -
The Windows experience
by
Will Fastie
14 hours, 4 minutes ago -
A tale of two operating systems
by
Susan Bradley
5 hours ago -
Microsoft : Resolving Blue Screen errors in Windows
by
Alex5723
19 hours, 24 minutes ago -
Where’s the cache today?
by
Up2you2
1 day, 10 hours ago -
Ascension says recent data breach affects over 430,000 patients
by
Nibbled To Death By Ducks
1 day, 3 hours ago -
Nintendo Switch 2 has a remote killing switch
by
Alex5723
3 hours, 50 minutes ago -
Blocking Search (on task bar) from going to web
by
HenryW
1 day, 11 hours ago -
Windows 10: Microsoft 365 Apps will be supported up to Oct. 10 2028
by
Alex5723
2 days, 3 hours ago -
Add or Remove “Ask Copilot” Context Menu in Windows 11 and 10
by
Alex5723
2 days, 4 hours ago -
regarding april update and may update
by
heybengbeng
2 days, 5 hours ago -
MS Passkey
by
pmruzicka
1 day, 7 hours ago -
Can’t make Opera my default browser
by
bmeacham
2 days, 13 hours ago -
*Some settings are managed by your organization
by
rlowe44
1 day, 23 hours ago -
Formatting of “Forward”ed e-mails
by
Scott Mills
2 days, 12 hours ago -
SmartSwitch PC Updates will only be supported through the MS Store Going Forward
by
PL1
3 days, 7 hours ago -
CISA warns of hackers targeting critical oil infrastructure
by
Nibbled To Death By Ducks
3 days, 16 hours ago -
AI slop
by
Susan Bradley
1 day, 10 hours ago -
Chrome : Using AI with Enhanced Protection mode
by
Alex5723
3 days, 18 hours ago -
Two blank icons
by
CR2
1 day, 2 hours ago -
Documents, Pictures, Desktop on OneDrive in Windows 11
by
ThePhoenix
1 day, 4 hours ago -
End of 10
by
Alex5723
4 days, 5 hours ago -
Single account cannot access printer’s automatic duplex functionality
by
Bruce
3 days, 3 hours ago -
test post
by
gtd12345
4 days, 11 hours ago -
Privacy and the Real ID
by
Susan Bradley
4 days, 1 hour ago -
MS-DEFCON 2: Deferring that upgrade
by
Susan Bradley
2 days, 4 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

