
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
How to make lithium-ion batteries last for years
In this issue
- LANGALIST PLUS: What to do when Win8 system images won't restore
- TOP STORY: How to make lithium-ion batteries last for years
- FIELD NOTES: Doing work while doing your civic duty
- LOUNGE LIFE: Great to have backup from good old computer days
- WACKY WEB WEEK: Don't play with puff adders; play with popcorn
- PATCH WATCH: No summer break from Windows/Office patching
What to do when Win8 system images won't restore
It’s painfully frustrating when a backup or system image simply won’t restore properly. But there’s an easy fix for a common problem with Win8.1’s custom images.
Plus: A hard drive is filling with huge and mysterious files, questions about dual-booting Win10 and Linux, and suggestions for removing an active malware infection from a PC.
Unable to recover Win8.1’s recimg backups
Reader Jose Correa made system images using Win8’s built-in recimg tool. But now Windows can’t find or restore his saved images.
- “Mr. Langa, based on your instructions in the Oct. 10, 2013, Top Story, “Creating customized recovery images for Win8,” I’ve used recimg to create several image backups of my Windows 8.1 system. I’m using an external drive to store the backups.
“My problem is that I’ve not been able to recover any of my backups using the System Image Recovery option in Settings.
“After the computer restarts, I can’t find any of my backups because my external drive doesn’t show up at all.
“Can you please tell me what I am doing wrong?”
Sounds like you’ve run afoul of your PC’s UEFI and/or Secure Boot setup.
The technically elegant solution is to adjust the UEFI and boot settings to allow access to your custom .wim image file on the external drive. You’ll find the information you need in “How to solve UEFI boot and startup problems,” the Dec. 11, 2014, Top Story, and in “Emergency access to your PC’s UEFI settings,” in the Jan. 15 LangaList Plus.
The quicker, simpler, brute-force fix is to copy your custom image file from the external drive to your boot drive (usually C:) and then tell the recimg tool to use the file there.
You could, for example, create a new folder called CustomRefreshImage on your root drive (again, typically C:) and then copy your custom .wim image file from the external drive to that folder.
You’d then tell Windows to forget about the previous location of the custom .wim file with this admin-level command:
recimg /deregister
Next, still in an admin-level account, set the new location with this command:
recimg /setcurrent C:\CustomRefreshImage
Because the .wim is now present and registered on the always-available C: drive, your custom restores should now work properly.
Mysterious files consuming his hard drive
Dale is plagued by massive, unwanted, and unidentified files on his hard drive.
- “Hi! Longtime reader here — since the separate LangaList days.
“I’ve had some oddly large files show up lately on my Windows systems, and I was wondering whether you can tell me what’s going on. Googling the problem got me nowhere.
“In the Windows folder of several PCs, I’ve seen many exceptionally large files (most are around 4GB each) with single-letter filenames — such as ‘0,’ ‘a,’ ‘b,’ ‘c,’ and so forth — all with nearly identical timestamps. They also all have system and hidden attributes turned on.
“With Resource Monitor, it appears that the ‘System’ process is the only thing that reads or writes to them.
“Using a boot CD to delete them (they can’t be deleted while the normal install of Windows is running) seems to cause no harm. They’re regenerated when I boot the normal Windows; if any were originally larger than 4GB, they’ll be trimmed to 4GB.
“There seems to be no rhyme or reason to it; they show up on some of my systems, and on some systems they don’t — there’s little in common between the systems.
“Any ideas?”
That’s somewhat puzzling, but let’s look at the clues.
First, most of the files are 4GB, which is the upper file-size limit for 32-bit PCs. Whatever is creating the files is trying to make most of them compatible with any system — 32- or 64-bit.
The timestamps are another clue: All the files were created in rapid succession, at approximately the same time.
The sequential alphanumeric file names are yet another clue: This is a common naming method used by software that’s automatically generating large numbers of similar files.
There are several types of software that create files with those three attributes: mostly fixed size, sequential timestamps, and simple alphanumeric naming.
For example, if you were to create a full-system backup and tell the software to keep the resulting files small enough to work on a 32-bit system, the software might well create a series of roughly 4GB files, with sequential names time-stamped in rapid, serial succession.
File recovery or undelete tools can also create files of that sort. Likewise, .zip-compression tools might split large files into 4GB chunks. Peer-network torrent apps can also create large files of the sort you describe.
I assume you’d know if you were doing any of those or similar actions. So, what’s left?
Malware might be the cause: something might be mining data from your hard drives for eventual transmission to an unknown destination. The malware on one system could be transmitting the accumulated information across your local network, or all your affected systems could have the same infection.
It’s easy to check for malware. Disconnect the affected machines from your local network and then scan them, one by one, with a reputable, self-contained, bootable, anti-malware scanner. (Disconnecting from the network will help to ensure that cleaned machines aren’t reinfected by the as-yet uncleaned ones.)
For some suggestions on good scanning tools, see the April 11, 2013, Top Story, “A dozen tools for removing almost any malware.”
If the PCs are clean, you then can do further sleuthing to learn what legitimate software might be behaving as if it were backing up or copying or recovering or buffering large files.
One method is to actually open the mysterious files to see what’s inside. Of course, you don’t want to open a 4GB file in a typical text editor or word processor. Most of those tools will choke on a file that large — and even if they did load it, they run excruciatingly slow.
Instead, your best bet is to use a special-purpose editor that can examine the raw contents of a file in its native form. These are called binary or hexadecimal editors — hex editors, for short. Here are just a few free tools to choose from:
- Hexplorer – open source; SourceForge
- HxD – mh-nexus
- Frhed – SourceForge
- XVI32 – chmaas.de
Using the hex editor of your choice, examine several of the files by looking at their start, end, and several points in between. You might find information that tells you what created the files. Barring that, you’ll at least see what the files contain — possibly text, file names, or random gibberish — that might help you understand what’s going on.
If the file contents don’t reveal what’s creating the files, you’ll need to babysit one of the misbehaving PCs to catch the file-writing in action. You’re already on the right track with Resource Monitor, although it doesn’t seem to be giving you the level of detail you need.
Instead of Resource Monitor, I suggest you try tools that can provide more detail, such as Microsoft’s Process Explorer (free; site) and/or Process Monitor (free; site). For more information about these two tools, see “Solving complex OS issues with Process Monitor” (June 3, Best Utilities ), “A tour through Windows Process Explorer: Part 1” (Feb. 5, Best Utilities, and Part 2 (Feb. 12, Best Utilities).
Ideally, run two tools — or two instances of the same tool — side by side. When one tool shows a spike in disk-writing activity (because the mysterious files are being created), see what programs, processes, or services have bubbled to the top of the activity list in the other tool — that software is the likely culprit.
By drilling down to see exactly which software components are in play when the large files are being written, you should — at last! — be able to discover the source of this problem.
Dual-booting with Windows 10 and Linux
In “Prepping a Win7 PC for the Win10 upgrade” (July 2 LangaList Plus), I offered advice to a reader about getting his Win7/XP dual-boot system ready for an upgrade.
After reading the column, Stan Bucci wrote in, wondering whether the same advice applies to a Windows/Linux dual-boot setup.
- “Dear Mr. Langa, I currently dual-boot Linux Mint 17.1 along with Windows 7. I now intend to give Windows 10 a go.
“In your article, you suggest that you would ‘leave the system as a pure Win10 single-boot.’ Is this suggestion meant to apply solely to Peter, whose issues you explore in the beginning of your article, or are you not in favor of dual-booting in general?
“Moreover, if I install Windows 10 on top of Windows 7 in a dual-boot configuration, will Windows 10 install in the pre-existing Windows 7 partition and respect the dual-boot configuration, or will it attempt to remove the dual-boot configuration and thereby delete Linux? Also, does Win10 introduce another feature which might prevent my dual-booting Linux? An example might be ‘secure boot,’ which I understand is a feature of UEFI systems.
“Could you explore this issue?”
Generally speaking, I’m not in favor of dual-booting, period.
Dual-booting is a very old technique that adds needless complications to newer systems — especially PCs (such as those running Win8 and Win10) that use Secure Boot, Trusted Boot, Fast Boot, and related technologies. (See the section labeled “UEFI components that might cause boot trouble” in the Dec. 11, 2014, Top Story, “How to solve UEFI boot and startup problems.”)
In most cases, it’s much safer and simpler — and more certain — to run whatever alternate operating systems you need inside the confines of a virtual PC. Not only is it safer, it lets you switch between OSes on the fly.
Yes, there are exceptions where an alternate OS might need direct access to the system hardware. But those cases are rare. In my opinion, it’s almost always better to have one OS in total control of the hardware — and to safely sandbox any other OSes in virtual PCs.
For your Win10/Linux setup, I suggest you follow the same advice I gave Peter: simplify your setup — let Win10 manage the hardware and install the alternate OS (in your case, Linux) in its own VPC.
Best tool to remove an active malware infection?
Pat Ferguson is looking for the best way to clean infected PCs.
- “My husband and I are in the computer sales and service business, and people bring us lots of computers for virus repairs.
“What is an excellent and reasonable antivirus program for businesses to use when repairing customers’ computers?”
When a PC is actively infected — or even if you merely suspect the presence of an active infection — your best bet is to use heavy-duty, self-booting, external malware-cleaning tools — preferably more than one for each suspected infection.
Download the self-contained, anti-malware tools of your choice to a known-clean PC. Next, burn each of the tools to a bootable medium, such as an optical disk or flash drive. Boot the infected PC from the disc/flash drive and use the anti-malware app to scan and clean the system.
Self-contained AV tools work best because they scan while both the installed Windows and the malware are inert and inactive, letting the tool bypass any defenses the malware might use. That greatly increases the odds of a successful disinfection.
There are many self-booting anti-malware apps offered, both free and paid. See, for example, the April 11, 2013, Top Story), “A dozen tools for removing almost any malware” — skip down to the section, “Heavy-duty, self-booting, malware-cleaning tools.”
Once the infected PC is clean, remove whatever anti-malware app was on the system at the time of infection; clearly, it failed and should not be relied on again. Install a different anti-malware app, from a different vendor.
Experienced, careful users — those who know not to click on bogus links, who can recognize phishing scams, and so forth — can get by with modest anti-malware apps. For example, I use the lightweight Microsoft Security Essentials as my primary anti-malware tool, and it’s perfectly adequate for my needs.
But inexperienced and/or inattentive users, or those whose PCs have succumbed to a major malware infection, need an advanced level of protection — they need an app that can work even in the face of major mistakes on the part of users. For some excellent recommendations, see Lincoln Spector’s July 23 Top Story, “AV testing: Is your antivirus app doing its job?”
How to make lithium-ion batteries last for years
The lithium-ion (Li-ion) batteries used in most of today’s tablets, smartphones, and portable PCs require very different care and feeding than with the nickel-cadmium (Ni-Cd) and nickel-metal-hydride (Ni-MH) batteries used in earlier devices.
In fact, proper care of a Li-ion battery can result in as much as 15 times longer service life than with an improperly cared-for battery. Here’s how to make sure that your expensive Li-ion batteries last as long as possible in all your portable devices.
I recently had to replace a damaged smartphone — and it was all my fault.
The symptom was ominous: my phone’s case became distorted — the body of the phone actually started to bend.
On inspection, it turned out, the phone’s Li-ion battery had actually swollen.
At first, I hadn’t noticed the change; the battery looked more or less normal when viewed face on (see Figure 1). But when I removed the battery and placed it onto a flat surface, it became obvious that the battery’s front and back were no longer flat and parallel; one side of the battery had developed a substantial bulge, as shown in Figure 2. This bulge is what had caused the body of the phone to bend.

Figure 1. The damaged battery looked more or less normal when viewed face-on.

Figure 2. But an end-on view of the battery showed a noticeable distortion. Instead of lying flat, one side bulged out — enough to deform the body of the phone.
The bulge indicated something severe: a high-pressure buildup of toxic gases inside the battery.
The battery’s case had done its job — it had contained the gases — but the battery was now potentially a tiny, pressure-cooker bomb — just waiting for something to set it off.
Both the battery and the phone were now irretrievably damaged; it was time for a new phone.
Adding insult to injury, not only was the damage my fault, it could easily have been prevented. (At the end of this article, I’ll tell you what I did wrong.)
To avoid repeating my past mistakes with a new phone — or with other Li-ion-powered devices such as tablets and portable PCs — I spent some time researching the care and feeding of Li-ion batteries.
I wasn’t looking so much for ways to get more run time between recharges; those techniques are already well known. Most portable devices offer ample manual and automatic power-saving modes and methods such as adjusting screen brightness, slowing CPU speed, and reducing the number of apps running.
Rather, I focused on ways to extend the battery’s overall service life — i.e., ways to keep it safe and healthy and able to function as it should for potentially years to come.
In a list at the end of this text, I’ve included the best references I found; there’s a ton of good information there.
But to save you time, I’ve also distilled some of the best and most interesting takeaways below. Follow these five important tips, and you’ll help ensure that your Li-ion batteries will deliver long, full, safe service lives in all your portable devices.
Tip 1: Keep your lithium batteries cool
I was surprised to learn that heat is the number-one enemy of Li-ion batteries. Heat issues can be caused by usage factors such as the speed and duration of battery charging and discharging. (I’ll come back to this in a moment.)
The external, physical environment also matters. Simply leaving your Li-ion-powered device in the sun or in an enclosed car — even if the device isn’t being used at the time — can significantly reduce the battery’s ability to take and hold a charge.
Li-ion batteries perform best at about normal room temperature (68F/20C). If the device warms to 86F/30C, its ability to hold a charge drops by about 20 percent. If the battery is used at 113F/45C — a temperature easily reached by devices that are working hard or that are in the sun (say, on a car dashboard), battery capacity can be reduced by half.
So if your device or battery becomes noticeably warm while you’re using it, consider moving to a cooler location. If that’s not possible, try reducing the amount of power the device is using by turning off unneeded apps, features, or functions; by reducing screen brightness; or by activating the device’s power-saving mode.
If that still doesn’t help, turn the device fully off until its temperature returns to normal. For fastest cooling, remove the battery (if the device allows that) — the battery and the device will cool off faster if they’re physically separated.
Incidentally, although high temperatures are a major issue with Li-ion batteries, low temperatures aren’t as much of a worry. Low temps usually won’t cause any long-term damage, although a cold battery won’t produce as much power as it otherwise would. The power drop becomes very noticeable at temperatures lower than about 40F/4C. Most consumer-grade Li-ion batteries are essentially useless at temperatures around or below freezing.
If your Li-ion powered device becomes excessively chilled for any reason, don’t try to use it. Leave it powered off and move it to a warm place (a pocket or a warm room) until the device is at normal temperature. As with overheating, physically removing the battery (if your device allows this) and warming it separately from the device will speed the warm-up process. Once the battery warms to a normal temperature, so will its electrical performance.
Tip 2: Unplug the charger to save the battery
Overcharging — leaving a battery connected to a too-high voltage source for too long — can reduce a Li-ion battery’s ability to hold a charge, shorten its life, or kill it outright.
Most consumer-grade Li-ion batteries are designed to operate at around 3.6 volts per cell but will accept a temporary overvoltage of around 4.2 volts while charging. If a charger outputs the higher voltage for too long, internal battery damage can occur.
In severe cases, overcharging can lead to what battery engineers delicately refer to as “catastrophic failure.” Even in moderate instances, the excess heat produced by overcharging will negatively affect battery life, as you saw in Tip #1.
High-quality chargers can work in concert with circuitry inside well-designed Li-ion-powered devices and their batteries, reducing the danger of overcharging by properly tapering off the charging current. (I’ll cover charging devices in a moment.)
But the simplest, can’t-fail method is not to leave your Li-ion devices connected to any charger longer than is needed.
These properties are quite different from those of older Ni-Cd and Ni-MH battery technologies, which did best when left on their chargers for as long as possible. That’s because those older battery types have a high rate of self-discharge; that is, they start losing a significant amount of stored energy the moment you take them off the charger, even if the device they power is turned off.
In fact, a Ni-Cd battery can self-discharge at a rate of 10 percent in the first 24 hours. The self-discharge curve flattens after that, but a Ni-Cd battery will still lose an additional 10–20 percent charge per month.
Ni-MH batteries are even worse. Their self-discharge rate is about 30 percent higher than that of Ni-Cd.
But Li-ion batteries have a very low rate of self-discharge. A healthy, full, lithium battery will self-discharge at about only 5 percent in the first 24 hours off the charger — with only an additional 2 percent or so per month after that.
Thus, it’s simply not necessary to leave a Li-ion device on the charger until the last possible moment. For best results and the longest battery life, unplug the charger when it or the lithium-powered device shows a full charge.
It’s also not necessary to give new Li-ion devices an extended charge before first use. (Ni-Cd or Ni-MH devices used to come with warnings to provide an initial charge of anywhere from 8 to 24 hours.) Li-ion batteries are fully ready for use when the charger or the device reads 100 percent charge. No extended charging is needed.
Tip 3: Don’t deep-discharge your battery
Not all discharge cycles exact the same toll on a battery. Long and heavy usage generates more heat, putting more stress on the battery; smaller, more frequent discharges extend the overall life of lithium batteries.
You might think that a higher number of small discharge/recharge cycles would eat into the battery’s overall lifespan. That was true with older technologies, but it’s not the case with Li-ion.
Battery specs can be confusing because most manufacturers count a full Li-ion charge cycle as whatever it takes to add up to a 100 percent charge. For example, two 50 percent discharge/recharge events equal one full-charge cycle. Likewise, three 33 percent discharge/recharge cycles equal one full-charge cycle, five 20 percent cycles equal a full charge, and so on.
In short, a higher number of small discharge/recharge cycles doesn’t reduce a lithium battery’s total available full-charge cycles.
Again, heat and stress from heavy discharges reduce battery life. So try to keep your deep-discharge events to a minimum. Don’t let your device routinely run down to zero charge (where the device turns itself off). Instead, think of the bottom 15–20 percent of battery capacity as a reserve — for emergency use only. Get into the habit of swapping in a fresh battery (if possible) or plugging the device into external power well before the battery is empty.
Tip 4: Slow and steady charge/discharge is best
As you now know, both fast discharging and fast recharging generate excess heat and exact a toll on battery life.
If you’ve run a device long and hard, let the battery cool to room temperature before recharging it. Batteries won’t accept a full charge when hot.
And when recharging, make sure your charger doesn’t make the battery become hot to the touch — a hot battery is a sign the charger is pumping too much current, too fast, through the battery.
Overcharging is more likely with chargers that are cheap, off-brand models; that use fast-charge circuitry; or that are wireless (inductive).
A cheap, generic charger could be little more than a transformer in a case with some connecting wires. These “dumb” chargers simply pump out current, accepting little or no feedback from the device being charged. Overheating and overvoltages can easily occur, damaging or even destroying the battery.
Fast chargers are designed to provide a useful charge to a drained battery in minutes rather than hours. There are various approaches to fast-charging technology, and not all of them are compatible with all lithium batteries. Unless the charger and the lithium battery are specifically designed to work together, fast charging could cause overheating and overvoltages. Generally, it’s best not to use one brand of fast charger on a different brand’s device.
Wireless (inductive) chargers use a special charging mat or surface to restore a battery’s power. It sounds wonderfully convenient, but inductive charging always generates excess heat, even when it’s working normally. (Some hi-tech kitchen stove tops actually use induction to heat pots and pans.)
Not only is the excessive heat produced by a wireless charger not good for lithium batteries, it also wastes energy. By its nature, inductive charging’s efficiency is always going to be significantly lower than a standard charger’s. To me, higher heat and less efficiency easily outweigh convenience. You might feel differently.
In any case, the safest approach is to use only chargers sold by the OEM of your lithium-powered device. It’s the only way to be sure that the charger will keep temperatures and voltages within specs.
If an OEM charger isn’t available, use a low-output charger that’s unlikely to pump damaging amounts of power into the device you’re charging.
One source of low-output, non-OEM charging that’s often available is the USB port on a standard PC. A typical USB 2.0 port provides 500mA (.5 amps) per port; USB 3.0 provides up to 900mA (.9 amps) per port. In contrast, some dedicated chargers will output 3,000-4,000mA (3-4 amps). The low amperages offered by USB ports will usually provide cool, safe charging of almost any Li-ion device.
Tip 5: Whenever possible, carry a spare battery
If your device allows for easy battery replacement, carrying a spare battery is cheap insurance. It not only gives you twice the run time but also helps you avoid the need to fully discharge a battery or use a quick charge. When the in-use battery approaches 15–20 percent charge, simply swap out the drained battery for a fresh, cool one — you get instant full power, with no heat worries.
A spare battery also allows for other benefits. For example, if you find yourself in a situation where the installed battery is running hot (say, because your device was working extra hard at some long task or because the ambient temperature is exceptionally high), you can swap out the hot battery to let it cool.
Having two batteries should also eliminate any need to use fast chargers — you can charge the spare at a safe, slow rate while the other is in use.
Post mortem: My battery-killing mistakes
Looking back, I believe I damaged my smartphone battery on a long road trip. I was using the smartphone’s GPS to navigate on a beautiful, sunny day. The smartphone was sitting in the sun, in a dashboard-mounted cradle, and I had the screen brightness turned all the way up so I could see the moving maps in the bright sunlight.
Moreover, all my normal background apps — email, etc. — were running. And I was also streaming music via 4G and piping the audio into the car’s sound system via Bluetooth. That phone was working hard.
To keep the phone powered, I’d plugged it into a generic 12V adapter I’d bought because it had the right plug — and was inexpensive.
The combination of solar heating, high CPU use, full-on screen, and poorly regulated electrical power made the phone get exceedingly hot. I remember being surprised at how toasty it was when I removed it from its cradle. This severe overheating undoubtedly started the battery’s death spiral.
I apparently compounded the problem at home by routinely leaving the phone plugged in overnight, letting it needlessly sit on a generic charger for hours after reaching full charge.
With my new phone, I’m now using only OEM chargers and carrying a spare battery. I expect to get long — and safe — service from both the batteries and the phone by following the tips and steps mentioned above.
But those are the basics; there are more ways to extend battery life. I suggest checking out the extensive resources listed below — the best sites I found in my research — and you’ll have all the information you need to get the most battery power and life from all your lithium-powered devices.
Much more information on modern batteries
If you want to know everything about caring for Li-ion batteries, see the following:
- “Lithium-ion battery” – Wikipedia entry
- “Batteries in a portable world” – buchmann.ca website
- “Battery University” – Cadex Electronics website
- “HP Notebook PCs — Understanding lithium-ion and smart battery technology” – HP Customer Support website
- “Tips for extending the life of your smartphone battery” – Samsung website
- “Maximizing battery life and lifespan” – Apple website
- “ASUS battery information center” – ASUS website
- “Charging Li-ion batteries for maximum run times” – Power Electronics Technology PDF
- “Capacity fade study of lithium-ion batteries cycled at high discharge rates” – Journal of Power Sources PDF
- “Battery performance characteristics” – Electropaedia article
- “Basic understanding of LiPo, Li-ion and LiFePo4 battery, its use and care” – COBOX article
- “Lithium-ion battery and lithium iron phosphate battery charging basics” – PowerStream website
- “Proper lithium-ion battery charging and safety” – EDN Network article
- “3 easy ways to extend your lithium-ion battery life” –RELiON Batteries article
- “Ask Ars: What is the best way to use a Li-ion battery?” – Ars Technica article
Doing work while doing your civic duty
It’s an abbreviated version of Field Notes this week, thanks to a jury-duty call for yours truly.
Here are a few lessons learned while trying to work on Windows Secrets on government time.
The first lesson: Don’t take vacation days right before jury duty if you can avoid it. However, in this case, I plead not guilty by dint of family obligations.
Jury duty is not something I try to avoid on the grounds of simple inconvenience. I was once on a jury for a three-week civil trial and found it fascinating. But Patch Tuesday week is truly a bad time to be out of the office. Lesson two concerns the court’s definition of “hardship.” California and Washington set a very high bar with their definitions of business hardships.
Lesson three: If the timing of an invitation to jury duty is bad, be sure to submit your application for a service delay quickly. I neglected that task, mostly because of a busy schedule and a difficult negotiation for the purchase of some property. My bad.
Wi-Fi, yes; an actual connection … maybe. Jury-selection day in Seattle means several hundred people in one large room, with nearly all of them using some variety of notebook, tablet, super-phone, and/or smartphone. Many, if not most, of those devices are sharing a single Wi-Fi network. And the network is, of course, completely open — no password required. The connection problem was compounded by the fact that many notebook users also had their smartphones attached to the local network.
As you might expect in that situation, the local network proved marginal, at best. You might have a suitable Internet connection one minute and then virtually no connection the next. (Getting called twice to a courtroom for final jury selection didn’t help me keep a solid connection.)
Obviously, such a heavily used, unsecure network immediately raises security concerns. I have a VPN app on my laptop, which improves online security. But with the rapidly changing traffic on the local jury-room Wi-Fi network, the VPN proved unreliable; sometimes it connected to the VPN server but more often didn’t. Lesson four: Have a VPN service set up, but don’t depend on it working.
At one point, I needed to upload an edited article ASAP, only to have my Web connections time out. It occurred to me that an alternate solution was to tether my phone to my notebook so that the phone was providing the Internet connection.
The phone offers three types of connections: Wi-Fi, Bluetooth, and USB. The notebook is an older ThinkPad that doesn’t have Bluetooth. Creating a personal Wi-Fi hotspot was easy, but broadcasting my SSID name to a few hundred devices was unappealing. Lesson five: If you have tethering capabilities, bring a USB cable to make a truly secure connection.
Fortunately for my already stretched stress level, I wasn’t selected for a jury — and Windows Secrets went out on time.
Great to have backup from good old computer days
Lounge member LesF’s Task Scheduler in Windows 7 is corrupted, he finds; he wonders what to do about it.
His fellow Loungers in the Windows 7 forum offer suggestions, information, and encouragement.
Happily, they’re able to offer congratulations when he solves his knotty problem completely via a recent backup image. You might want to see why he had to resort to that and how grateful he is that he could.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right into today’s discussions in the Lounge.
Don't play with puff adders; play with popcorn
 |
We’re in favor, completely, of scientific endeavor and excitement. On the other hand, we’re not recommending that you dangle a red water balloon in front of a puff adder so that you can photograph the adder’s response. We offer you the video instead, which ought to supply a thrill or two. If you must try exploding something yourself, try popcorn. Click below or go to the original YouTube video. |
| Post your thoughts about this story in the WS Columns forum. |
No summer break from Windows/Office patching
Although it’s the first Patch Tuesday of the Windows 10 era, little has changed — we’re still getting lots of updates, many of which require reboots.
For Win10, most of the separate updates are for Office; the OS updates now come in one big bundle. Win10 imposes a new limitation: updates can be delayed only if you’re using Windows Server Update Services (more info) on a network.
For Windows 7 and 8 users, it’s patching business as usual. Fortunately, relatively few of the following updates are critical.
MS15-091(3081436)
Windows 10 gets its first Patch Tuesday
Windows 10 has changed the updating rules — not for vulnerabilities but for how you receive updates. For example, KB 3081436 is listed as a critical security update for the new Microsoft Edge browser. But the update’s fine print notes that it’s cumulative — i.e., it also includes all the August security and nonsecurity fixes for Windows 10. (Win7 and Win8 users will see many of these fixes as separate patches.)
Along with the Edge patch, this update also contains the following patches, discussed in more detail further below:
- MS15-079 – Internet Explorer
- MS15-080 – Microsoft Graphics Component
- MS15-085 – Windows Mount Manager
- MS15-088 – Command-line parameter passing
- MS15-092 – .NET
KB 3081436 is, in fact, not Win10’s first cumulative update. Microsoft released KB 3081424 on Aug. 5. Unfortunately, some systems choked on KB 3081424. A WindowsIT Pro article described a workaround, but it required a Registry hack. If you ran into problems with the Aug. 5 update, the better solution now is to block it via the “Show or hide updates” tool offered in KB 3073930.
 What to do: For Windows 10, your only option is to choose when you’ll allow a reboot.
What to do: For Windows 10, your only option is to choose when you’ll allow a reboot.
MS15-079 (3082442)
New month, same browser-updating game
The monthly list of non-Microsoft updates to track along with all browsers, is Adobe Flash Player, Java, and Microsoft Silverlight. Of course, the better solution is to uninstall any of those apps you don’t absolutely need.
For browsers, KB 3082442 is the August cumulative update for Internet Explorer. It’s rated critical for workstations and moderate for servers. Firefox users should now be on Version 40.0, which adds support for Windows 10; Google Chrome should be on Version 44.0.2403.155.
Adobe is still tying its Flash Player updates to Patch Tuesday, for the most part. If you still have Flash installed, check that it’s on Version 18.0.0.232. In the update’s description, Adobe notes that it fixes numerous critical vulnerabilities.
If you must have Java and/or Flash installed, I suggest downloading and using the NoScript browser add-on (site) or a similar app.
Finally, there’s a Microsoft Silverlight update included among the various patches in MS15-080, as described in the next section.
 What to do: Ensure that your browsers and media players are always up to date — they remain a common threat for online attacks.
What to do: Ensure that your browsers and media players are always up to date — they remain a common threat for online attacks.
MS15-080
Squashing a bunch of MS Graphics Component bugs
MS15-080 is a bundle of security fixes for Microsoft graphics subsystems. The patched vulnerabilities cut a broad swath across .NET Framework, Office, Lync, and Silverlight. Mostly rated critical, the patches fix issues with TrueType fonts, OpenType fonts, the Windows kernel, and user validation.
The various updates include:
- 3054846 – Office 2010 SP2
- 3054890 – Office 2007 SP3
- 3055014 – Skype for Business
- 3072303 – .NET 3.0 SP2
- 3072305 – .NET 3.5.1
- 3072306 – .NET 3.5
- 3072307 – .NET 3.5
- 3072309 – .NET 4
- 3072310 – .NET 4.5/4.5.1/4.5.2
- 3072311 – .NET 4.6
- 3075590 – Lync 2010 Attendee
- 3075591 – Live Meeting 2007 Console
- 3075592 – Live Meeting 2007
- 3075593 – Lync 2010
- 3078601 – Vista and Win7
- 3080333 – Silverlight 5
- 3081436 – .NET 3.5
You’ll see multiple updates for the various installed .NET versions. If you upgraded from Office 2007 to Version 2010, you might still be offered updates for the older Office.
 What to do: Install any of the updates offered in MS15-080.
What to do: Install any of the updates offered in MS15-080.
MS15-081 (3080790)
Patching against malicious Office files
MS15-081 is another big bundle of updates — in this case, for Office apps. Note: Starting Aug. 12, users of Office 2007 will no longer be able to access online templates if they don’t install these updates. Without the patches, you’ll see only a single template thumbnail, along with text that describes how to regain full template access by updating Office (more info).
The severity of these updates is a bit confusing. The title for MS15-081 has “Critical” in it. But only KBs 2553313, 2596650, 3039798, and 3054888 are critical; the rest are rated important or not applicable.
You’ll see some combination of the following updates, depending on the version of Office you have installed. You might see updates for both Office 2007 and 2010.
- 2553313 – Office 2010 SP2
- 2596650 – Office 2007 SP3
- 2687409 – Office 2007 SP3
- 2598244 – Office 2010 SP2
- 2837610 – Office 2007 SP3
- 2965280 – Visio 2007 SP3
- 2965310 – Office 2010 SP2
- 2986254 – Office Compatibility Pack
- 3039734 – Office 2013 SP1
- 3039798 – Office 2013 SP1
- 3054816 – Office 2013 SP1
- 3054876 – Visio 2010 SP2
- 3054888 – Office 2007 SP3
- 3054929 – Visio 2013 SP1
- 3054991 – Excel 2013 SP1
- 3054992 – Excel 2007 SP3
- 3055029 – PowerPoint 2013 SP1
- 3055030 – Word 2013 SP1
- 3055033 – PowerPoint 2010 SP2
- 3055037 – Office 2010 SP2
- 3055039 – Word 2010 SP2
- 3055044 – Office 2010 SP2
- 3055051 – PowerPoint 2007 SP3
- 3055052 – Word 2007 SP3
- 3055053 – Microsoft Word Viewer
- 3055054 – Microsoft Word Viewer
- 3081349 – Microsoft Office for Mac 2011
- 3082420 – Microsoft Office for Mac 2016
 What to do: Install the updates in MS15-081 if offered.
What to do: Install the updates in MS15-081 if offered.
MS15-082 (3075220, 3075221, 3075222, 3075226)
Remote Desktop Protocol used in trick attacks
A vulnerability in Windows could allow an attacker to run malicious code remotely on an infected PC. But to do so, the hacker would first have to install a bogus DLL file on the local system and then either trick the user into opening Remote Desktop Protocol file or run some other app that uses the DLL.
Rated important, the patches apply to all supported versions of Windows except Windows 10. KB 3075222 has an unusual — and relatively minor — side effect. After installing or uninstalling this update, you might have to restart your computer twice.
 What to do: You might not use Remote Desktop, but you could be tricked into launching it. Install KBs 3075220, 3075221, 3075222, or 3075226 (MS15-082) if and when offered.
What to do: You might not use Remote Desktop, but you could be tricked into launching it. Install KBs 3075220, 3075221, 3075222, or 3075226 (MS15-082) if and when offered.
MS15-083 (3073921)
Taking control via Windows Server error logging
KB 3073921 patches a vulnerability in the way Windows handles Server Message Block (SMB) error logging. Rated important, it applies only to Vista and Windows Server 2008 systems.
 What to do: Install KB 3073921 (MS15-083) if offered.
What to do: Install KB 3073921 (MS15-083) if offered.
MS15-084 (2825645, 3076895)
Blocking use of unsecure SSL 2.0 sessions
An attacker who tricks a user into clicking a malicious link or opening a Secure Sockets Layer 2.0 session might be able to see information stored in system memory.
Rated important, the updates in MS15-084 impact both Windows and Office, hardening Microsoft’s XML Core Services (more info). KB 3076895 is for systems running Vista through Win8.1; KB 2825645 is for Office 2007 SP3 and InfoPath 2007 SP3.
 What to do: Install KB 2825645 and/or KB 3076895 (MS15-084) if offered.
What to do: Install KB 2825645 and/or KB 3076895 (MS15-084) if offered.
MS15-085 (3082487)
Taking control of systems with flash drives
There are seemingly thousands of ways our systems can be attacked. For example, a vulnerability in Windows’ Mount Manager could allow an attacker full access to a system as a result of inserting a malicious USB device.
The fix, KB 3082487, is rated important and applies to all current versions of Windows. In the case of Win10, the patch is bundled with the aforementioned cumulative update (KB 3081436).
 What to do: This vulnerability is already being exploited; install KB 3082487 (MS15-085) immediately.
What to do: This vulnerability is already being exploited; install KB 3082487 (MS15-085) immediately.
MS15-088 (3046017, 3079757)
Information disclosure via blended attacks
Some exploits work better when used in conjunction with other exploits. In such cases, an attacker must first use a vulnerability in Internet Explorer to gain access to a system — then run a command-line parameter in an Office app or in Notepad. A successful exploit would let the attacker see information on the local system.
Rated important, this patch changes how IE works with other applications. Most current Windows systems will see KB 3046017; for Win10, the update is included in KB 3081436; and some Windows Server systems will see KB 3079757.
 What to do: Install KB 3046017 and/or KB 3079757 (MS15-088) when offered.
What to do: Install KB 3046017 and/or KB 3079757 (MS15-088) when offered.
MS15-089 (3076949)
Preventing forced use of unsecure SSL 2.0
Microsoft Web Distributed Authoring and Versioning (WebDAV) is a component in Windows systems often used to connect to the cloud or other remote servers. Connection security should be handled via Transport Layer Security (TLS). But many systems still support the unsecure Secure Sockets Layer.
A vulnerability in WebDAV could let an attacker set up an unsecure SSL 2.0 session and then execute a man-in-the-middle attack to decrypt information sent over the Internet. The fix, KB 3076949, impacts all Windows systems except Win10.
 What to do: Install KB 3076949 (MS15-089) if offered.
What to do: Install KB 3076949 (MS15-089) if offered.
MS15-090 (3060716)
Breaking out of the sandbox begets EOP
The Windows Object Manager manages system resources (more info). According to the description for KB 3060716:
“Vulnerabilities could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application or convinces a user to open a specially crafted file that invokes a vulnerable sandboxed application, allowing an attacker to escape the sandbox.”
In other words, this is yet another elevation-of-privileges exploit. The update changes the handling of symbolic links created by sandbox processes. Win10 users are off the hook for this update, rated important.
 What to do: Install KB 3060716 (MS15-090).
What to do: Install KB 3060716 (MS15-090).
MS15-092 (3083184, 3083185, 3083186)
.NET no longer the troublemaker it once was
Since the demise of Windows XP, I no longer fear the release of .NET Framework fixes. Nevertheless, given the number of updates this month, I recommend installing these .NET patches separately from the other updates — just to ensure success.
As an aside, I’ve noted that when there’s a large release of patches, some updates fail to install the first time. But typically, they’ll succeed on the second try.
Rated important, the following patches are only for .NET 4.6. Once again, the update for Win10 is included in KB 3081436.
- 3083184 – Win8
- 3083185 – Win8.1
- 3083186 – Vista and Win7
 What to do: Install any of the above updates (MS15-092) if offered.
What to do: Install any of the above updates (MS15-092) if offered.
3038936
Making Defender updating a bit less intrusive
KB 3038936 is a nonsecurity update for a security application. The patch is designed to reduce Defender’s use of network resources when getting new anti-malware signature files, shared via the Universal Naming Convention system.
The update impacts only Win8 and 8.1.
 What to do: Install KB 3038936 if offered.
What to do: Install KB 3038936 if offered.
MS15-086, MS15-087
Patches of interest to server administrators
Most Windows workstations shouldn’t see KBs 3064919, 3071088, or 3071089 (MS15-086). The patches fix a vulnerability in System Center 2012 Operations Manager, a management tool typically used on large networks. The flaw could let an attacker acquire additional rights if a system user browses a malicious webpage. The update is rated important.
Two other admin-related updates are KB 3073893 and KB 3087119 — the former designed for Windows Server 2008 and the latter for MS BizTalk Server 2010 and 2013.
Rated important, the two updates prevent cross site-scripting attacks via a vulnerability in the Windows UDDI services (more info).
 What to do: Admins should install the updates in MS15-086 and MS15-087 after testing.
What to do: Admins should install the updates in MS15-086 and MS15-087 after testing.
The dog-days list of nonsecurity updates
Microsoft is still releasing nonsecurity updates to Win7, designed to make the transition to Win10 easier. KB 2952664 and KB 2976978 are update-helper apps that check system compatibility. KB 3035583 adds the “Get Windows 10” app in Win7 and Win8.1. You can pass on this update if you plan to stick with Win7 for the near future.
Here’s the August list of nonsecurity updates for workstations. Note: Most of the Windows updates were released in late July. For a complete list of Office updates — including server patches — see the August MS Office Sustained Engineering Team post.
Windows
- 3064209 – Win7/8/8.1; Intel CPU microcode fix for system crashes (now prechecked)
- 3075851 – Win7; enhancements to Windows Update Client
Windows 8/8.1
- 3065988 – Win8.1; Windows Update Client improvements
- 3061493 – Win8.1; magstripe-driver support
- 3065013 – Win8.1; “0x0000007F” and “0x0000009F” stop errors
- 3070071 – Win8/8.1; updated APN entry for SoftBank Mobile Corp
- 3071663 – Win8.1; application crashes
Office 2007/2010
- 3054979 – Outlook 2010 junk-email filter
- 2589318 – Office 2010; Excel key-combo error, Thai characters error
- 3054962 – Office 2010; Formatting errors on file save to earlier verions
- 3055023 – Outlook 2007 junk-email filter
- 3055041 – Outlook 2010; various fixes
Office 2013
- 3055012 – Outlook; various fixes
- 3055013 – Outlook junk-email filter
- 3055016 – Access; excessive CPU use
- 3039718 – Office; PathNotFound error
- 3039792 – Office; PathNotFound error
- 3054807 – Office; broken hyperlinks in workbooks/PDFs, linked via UNC
- 3055000 – Office; integrated Windows authentication with ADFS
- 3055001 – Office; various fixes and improvements
- 3055017 – Office; crashes, PathNotFound error, OneDrive for Business errors
- 3055008 – OneNote; various fixes
- 3055012 – Outlook; various fixes
Other updates
- 3055020 – OneDrive for Business; missing icon in Windows Explorer on Win10
- 3055022 – Project 2013; various fixes
- 3055050 – Project 2010; MPP file not saved properly, template flaws, “completed” errors
 What to do: As usual, put these updates on hold until the end of the month.
What to do: As usual, put these updates on hold until the end of the month.
Look out for Win10-related patches in Win Update
On my Win8.1 test system, I’ve not yet installed Windows 10. But I did leave the “Get Windows 10” icon installed to alert me when Microsoft decides my system is ready for upgrading.
While reviewing the system’s new security-update offerings, I noted that the security updates were unchecked and the “Upgrade to Windows 10 Pro” patch was checked! (See Figure 1.) The lesson: If you’ve not blocked or uninstalled your Win10 reservation, and you don’t want Win10 at this time, pay close attention to which updates are — and are not — checked this month.
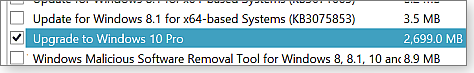
Figure 1. On a Win8.1 system, only the offer to upgrade to Win10 was prechecked.
Regularly updated problem-patch chart
This table provides the status of recent Windows and Microsoft application security updates. Patches listed below as safe to install will typically be removed from the table about a month after they appear. Status changes are highlighted in bold.
For Microsoft’s list of recently released patches, go to the MS Security TechCenter page.
| Patch | Released | Description | Status |
|---|---|---|---|
| 3046339 | 07-14 | Windows Hyper-V; also KB 3046359 | Install |
| 3061512 | 07-14 | DLL threat in Windows; also KBs 3067903 and 3070738 | Install |
| 3065718 | 07-14 | SQL Server; see MS15-058 for completed patch list | Install |
| 3065822 | 07-14 | Internet Explorer | Install |
| 3067505 | 07-14 | Windows Remote Procedure Call | Install |
| 3067904 | 07-14 | Remote Desktop Protocol; also KB 3069762 | Install |
| 3068368 | 07-14 | VBScript scripting engine; also KB 3068404 | Install |
| 3068457 | 07-14 | Netlogon; servers only | Install |
| 3069392 | 07-14 | Windows Graphics Component | Install |
| 3070102 | 07-14 | Windows kernel | Install |
| 3072620 | 07-14 | Office; see MS15-070 for complete patch list | Install |
| 3072630 | 07-14 | Windows Installer Service | Install |
| 3072633 | 07-14 | Windows OLE | Install |
| 3077657 | 07-14 | Windows ATM Font Driver | Install |
| 3046017 | 08-11 | Command-parameter passing; also KB 3079757, 3081436 (Win10) | Install |
| 3060716 | 08-11 | Windows Object Manager | Install |
| 3071756 | 08-11 | Windows Mount Manager; also KB 3081436 (Win10) | Install |
| 3073893 | 08-11 | Windows UDDI Services (Server 2008) | Install |
| 3073921 | 08-11 | Server Message Block (Vista and Win Server 2008) | Install |
| 3075158 | 08-11 | System Center Ops Mgr; KBs 3064919, 3071088, 3071089 | Install |
| 3075220 | 08-11 | Remote Desktop Protocol; also KBs 3075221, 3075222, 3075226 | Install |
| 3076895 | 08-11 | XML Core Services (Windows and Office) | Install |
| 3076949 | 08-11 | Windows/WebDAB servers | Install |
| 3078071 | 08-11 | Internet Explorer cumulative update | Install |
| 3078662 | 08-11 | MS Graphic Component; see MS15-080 for complete patch list | Install |
| 3080790 | 08-11 | MS Office; see MS15-081 for complete patch list | Install |
| 3081436 | 08-11 | Cumulative Windows 10 update | Install |
| 3083184 | 08-11 | .NET Framework; also KBs 3083185 & 3083186 | Install |
Status recommendations: Skip — patch not needed; Hold — do not install until its problems are resolved; Wait — hold off temporarily while the patch is tested; Optional — not critical, use if wanted; Install — OK to apply.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Blocking Search (on task bar) from going to web
by
HenryW
3 hours, 53 minutes ago -
Windows 10: Microsoft 365 Apps will be supported up to Oct. 10 2028
by
Alex5723
9 hours ago -
Add or Remove “Ask Copilot” Context Menu in Windows 11 and 10
by
Alex5723
9 hours, 7 minutes ago -
regarding april update and may update
by
heybengbeng
10 hours, 36 minutes ago -
MS Passkey
by
pmruzicka
6 hours, 40 minutes ago -
Can’t make Opera my default browser
by
bmeacham
18 hours, 16 minutes ago -
*Some settings are managed by your organization
by
rlowe44
5 hours ago -
Formatting of “Forward”ed e-mails
by
Scott Mills
17 hours, 11 minutes ago -
SmartSwitch PC Updates will only be supported through the MS Store Going Forward
by
PL1
1 day, 12 hours ago -
CISA warns of hackers targeting critical oil infrastructure
by
Nibbled To Death By Ducks
1 day, 21 hours ago -
AI slop
by
Susan Bradley
11 hours, 58 minutes ago -
Chrome : Using AI with Enhanced Protection mode
by
Alex5723
1 day, 23 hours ago -
Two blank icons
by
CR2
10 hours, 54 minutes ago -
Documents, Pictures, Desktop on OneDrive in Windows 11
by
ThePhoenix
2 days, 8 hours ago -
End of 10
by
Alex5723
2 days, 10 hours ago -
Single account cannot access printer’s automatic duplex functionality
by
Bruce
1 day, 8 hours ago -
test post
by
gtd12345
2 days, 16 hours ago -
Privacy and the Real ID
by
Susan Bradley
2 days, 6 hours ago -
MS-DEFCON 2: Deferring that upgrade
by
Susan Bradley
9 hours, 13 minutes ago -
Cant log on to oldergeeks.Com
by
WSJonharnew
2 days, 21 hours ago -
Upgrading from Win 10
by
WSjcgc50
1 day, 8 hours ago -
USB webcam / microphone missing after KB5050009 update
by
WSlloydkuhnle
1 day, 12 hours ago -
TeleMessage, a modified Signal clone used by US government has been hacked
by
Alex5723
3 days, 12 hours ago -
The story of Windows Longhorn
by
Cybertooth
3 days ago -
Red x next to folder on OneDrive iPadOS
by
dmt_3904
3 days, 14 hours ago -
Are manuals extinct?
by
Susan Bradley
15 hours, 5 minutes ago -
Canonical ditching Sudo for Rust Sudo -rs starting with Ubuntu
by
Alex5723
3 days, 23 hours ago -
Network Issue
by
Casey H
3 days, 10 hours ago -
Fedora Linux is now an official WSL distro
by
Alex5723
4 days, 11 hours ago -
May 2025 Office non-Security updates
by
PKCano
4 days, 12 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

