
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Microsoft DHCP bugs make Windows lose networking
In this issue
- BONUS: Get some great tricks for a healthy space
- TOP STORY: Microsoft DHCP bugs make Windows lose networking
- KNOWN ISSUES: A manual approach to reinstalling .NET Framework
- KNOWN ISSUES: Does the glitch in .NET patching put you at risk?
- WACKY WEB WEEK: Hang on, I've got the perfect song for this!
- LANGALIST PLUS: Boost performance by killing unneeded processes
- BEST SOFTWARE: Connect safely over open Wi-Fi networks
- WINDOWS SECRETS: Freeware helps to boot the bots off your network
- PATCH WATCH: Internet Explorer is target of zero-day attack
Get some great tricks for a healthy space
The new year is a perfect time to throw out old things and start anew. We’ve licensed a copy of the best techniques from Alison Haynes’s new book, Clean Sweep, to help you rid your home and workplace of unseen pollutants and toxins, especially those that can cause allergies. The printed book won’t be available in stores until January 2009, but all Windows Secrets subscribers can get our exclusive excerpt now through Jan. 7, free of charge. Just visit your preferences page and update your data, and a download link will appear. Have a great holiday season! —Brian Livingston, editorial director
All subscribers: Visit your preferences page and download your bonus
Info on the printed book: United States / Canada / Elsewhere
Microsoft DHCP bugs make Windows lose networking
 By Scott Spanbauer
By Scott Spanbauer
Numerous perplexed Windows users have discovered that attempting to connect their PCs (especially Vista) to their existing networks or Wi-Fi hotspots results in flaky or nonexistent connections.
One reason: a change by Microsoft in Vista’s Dynamic Host Control Protocol (DHCP) is causing conflicts with some networking hardware, which can require a Registry edit to fix.
The many reports of Vista networking snafus range from the gravest of symptoms — no Internet connectivity at all — to occasional connection drops:
- No-Fi when in power-saving mode. Microsoft acknowledged last year that wireless connections on portable computers running Windows Vista would slow down or disconnect completely when battery management kicks in.
The culprit is that, unlike Windows XP, Vista assumes that all wireless routers correctly implement Wi-Fi’s power-save protocol. Unfortunately, many access points don’t support this spec. The solution? Plug your laptop into an AC outlet or modify the notebook’s power-saving plan, as described in Knowledge Base article 928152.
- Vista insists on the “broadcast flag.” The same skewed reasoning led the wizards of Redmond to another infuriating decision, which Microsoft only belatedly explained. You bring home your new Vista computer, or you upgrade your XP system to Vista, only to discover that the machine won’t connect to your local network or the Internet.
You try everything to fix the problem. You waste hours — days, even — tweaking settings, plugging and unplugging, resetting, rebooting, and rehashing, but to no avail.
The problem? Windows Vista assumes that your router’s DHCP server — the one that hands out dynamic IP addresses to computers and other devices on the network — supports the DHCP broadcast flag. Again, many routers don’t support this flag.
The solution requires a Registry edit to toggle off Vista’s broadcast-flag expectations. Refer to the Resolution section of KB article 928233 for step-by-step instructions.
- Two network adapters spell trouble. Yet another kind of network malfunction afflicts PCs running Vista or Windows Server 2008 that have more than one network adapter installed. The multiple adapters befuddle the Network Location Awareness service in those OSes. This causes the service to disable Internet access to both adapters and label them as Local only.
KB article 947041 explains the problem but provides no solution. The only cure at this time may be to disable one of the network adapters. Thanks, Microsoft.
How to troubleshoot XP and Vista network woes
Network-connection problems are infuriating. Finding their source requires a step-by-step approach. Before editing your Registry for the umpteenth time or tossing your router into the trash, run through this network-troubleshooting checklist:
- Temporarily disable your software firewall. It sounds dumb, but often it’s your firewall that’s blocking your network connection. Even if the firewall has worked flawlessly for months, a small configuration change or automatic update could have caused a problem.
At least twice this year, Windows XP users of Check Point Software’s ZoneAlarm personal firewall have lost their ability to connect to the Internet due to a Windows update. Windows Secrets contribtuing editor Susan Bradley described this problem in her Oct. 16 Patch Watch column (paid content).
This alone is not a good reason to stop updating, though. It’s true that patches can introduce problems with firewalls, but subsequent fixes that remedy the issue will often appear within 24 hours.
- Check the physical connection. Make sure the router, modem, and other network devices are plugged in and powered on. Are the network cables between PC and router still connected firmly? With a device’s power switch off, it doesn’t hurt to unplug the component and then plug it back in again to make sure the contact is solid. If weak power-cable connections are ruled out, simply powering the devices off and back on can sometimes be all the resetting your network link needs.
- Renew your connection. Changes elsewhere on the network can sometimes knock out your connection. To reconnect quickly, click Start, Run in XP (or press the Windows key in Vista), type ipconfig /renew, and press Enter.
- Update your firmware and drivers. Makers of routers and network adapters may be caught unawares by patches to operating systems (such as the ones in Vista noted above). But the vendors often issue firmware or driver updates that fix the problems. Check the support pages of your router and adapter manufacturers’ sites for downloadable updates.
- Return to default settings. Often, we are our own worst enemies as we poke around the configuration settings of our routers and network connections. You may not remember that you turned on your router’s MAC filtering, but doing so could have blocked all of your devices from connecting, just the same.
In general, it’s best to change settings one at a time and observe the results of the change before making any other alterations to your system. If you don’t see an obvious way to return your hardware and software to their default settings, you may have to uninstall and reinstall the device or program to regain its original settings.
In all fairness, Vista isn’t the only version of Windows that experiences network glitches. XP has its own series of connectivity aggravations, as you can see by a search-engine query of Microsoft’s support center.
If your connectivity problems aren’t resolved by using the points discussed above, you may be suffering from an even more obscure issue. If so, ruling out the tricky configuration problems I describe here may at least help you isolate the real problem and restore your network link.
Scott Spanbauer writes frequently for PC World, Business 2.0, CIO, Forbes ASAP, and Fortune Small Business. He has contributed to several books and was technical reviewer of Jim Aspinwall’s PC Hacks.
A manual approach to reinstalling .NET Framework
 By Dennis O’Reilly
By Dennis O’Reilly
The Dec. 4 Top Story in Windows Secrets described how to make sure your system has the Microsoft .NET that’s needed by various applications, but doing so sometimes requires a brute-force approach.
When it’s time to reinstall vital Windows components — or the entire operating system — you’d best have a plan in mind.
That’s what reader Alan Crawford found out after stumbling through a reinstallation of Windows XP on one of his PCs:
- “I recently had to reinstall a PC that uses a handful of .NET apps. After installing Windows [XP] from an SP2 image, I used Microsoft Update to reinstall all necessary patches and updates, including the three .NET versions and their various service packs and other patches. Having already encountered problems with .NET patches on other machines, I wasn’t surprised when .NET 1.1 SP1 wouldn’t install.
“In the past, I was able to uninstall all .NET versions and then proceed, one at a time, to get them all reinstalled. No such luck this time. After several rounds and many visits to the Microsoft Knowledge Base — even using the .NET cleanup tool — I still could not get this package to install.
“My last-gasp effort was to try the whole exercise ‘manually,’ and it worked! Despite the extra time involved — and having to validate the PC on each download — had I started on this tack to begin with, I would have saved hours of frustration (seemed like hours, anyway, even if it wasn’t).
“Here’s the procedure I used:
• Step 1: I had previously downloaded the .NET cleanup tool.
• Step 2: I removed all traces of existing .NET installations and then ran the .NET cleanup tool.
• Step 3: I rebooted.
• Step 4: I manually downloaded .NET 1.1, 1.1 SP1, 1.1 SP1 Hotfix, and 2.0 installers — individually — from the Microsoft download site.
• Step 5: I installed them in the order downloaded, with reboots as required.
I picked up at this point with downloads from Microsoft Update — installing the 2.0 Hotfix, then 3.0, then the 3.0 Hotfix in separate runs — and all now seems to be just fine.
“Thanks, as always, for the best newsletter out there.”
Free option for controlling kids’ Net access
Becky Waring’s Dec. 4 parental-control software review (paid content) led reader Rob de Santos to tell us about a new way to use an old, reliable — and free — Internet security service:
- “I highly recommend an option usually overlooked by most parents (and unknown to them): control access via your router. If you utilize Open DNS and follow their instructions to change your router’s DNS settings, you can then use the easy-to-configure OpenDNS settings pages to block any category of sites you choose, be it … porn, chat, or advertising.
“This is an excellent supplement to any PC-based software and much harder for any child to override or avoid. It can also be remotely changed if necessary. Best of all, it’s free!”
Free is good. Difficult for a clever child to overcome is even better. And I know a lot of Internet users who’d be interested in a free, effective way to block Web ads.
Note that in her July 24, 2008, Patch Watch column (paid content), Susan Bradley described how to use the OpenDNS forwarding service to improve the security of routers and Web servers.
Speaking of Susan, since her lead story about problems patching Microsoft’s .NET Framework appeared on Dec. 4, she’s dug up additional information. Although she usually writes for Windows Secrets’ paid content, her follow-up on .NET appears today as a free column.
| Readers Alan and Rob will each receive a gift certificate for a book, CD, or DVD of their choice for sending tips we printed. Send us your tips via the Windows Secrets contact page. |
The Known Issues column brings you readers’ comments on our recent articles. Dennis O’Reilly is technical editor of WindowsSecrets.com.
Does the glitch in .NET patching put you at risk?
 By Susan Bradley
By Susan Bradley
People using Windows XP Service Pack 3 may not be offered all the .NET security patches their applications require.
However, if none of your PC’s programs requires a version of .NET Framework, this problem will have no impact on your system.
My Dec. 4 Top Story stated that, due to a bug, Windows XP SP3 users aren’t being offered security patches for Microsoft’s .NET Framework 3.0. I’m publishing this special column today because several of you asked whether your XP SP3 systems are at risk as a result of this glitch.
First I’ll give you some background on .NET Framework, and then I’ll describe how to tell whether you need to be concerned about the matter.
Microsoft created .NET Framework to provide building blocks for applications. .NET is not a component of Windows itself. I strongly recommend that you avoid downloading .NET until you install an application that requires one, at which time the program will likely install the necessary version for you.
To determine whether you have any versions of .NET Framework installed on an XP PC, open the Add or Remove Programs applet in Control Panel and look for entries reading Microsoft .NET Framework. If you don’t see any such entries, you needn’t worry about the update failure.
If you do see .NET Framework in the list of currently installed programs, you need to make sure you’re receiving all the updates your system requires.
When you open the Microsoft Update service on Windows XP, you’ll see buttons labeled Express and Custom on the Welcome screen. Click Custom to see three patching categories under Select by Type in the left pane: High Priority; Software, Optional; and Hardware, Optional.

Figure 1. Clicking the Custom button on Microsoft Update’s Welcome screen shows a list of high-priority and optional updates for your PC.
While all three categories can be considered security-related, in reality only the top section lists critical patches. The second section shows optional patches for Windows and your apps; the third lists driver updates.
Always install patches listed in the upper section. You can selectively install patches from the Software, Optional section, but I recommend that you never install driver updates directly from the bottom section. In the past, drivers I’ve downloaded from Microsoft’s update service have caused problems. Instead, go to the vendor’s own site and download driver updates from there. And remember: if the device isn’t causing any problems, refreshing its driver software may be more trouble than it’s worth.
When I tested several XP SP3 systems, the upper section of the update window — which lists critical security patches — looked much the same as it did on XP SP2 machines. However, SP2 and SP3 showed many differences in the middle section listing optional software updates, including those for .NET Framework.
There’s a very good reason the updates in the middle section are listed as “optional.” Until an application on your system requires .NET Framework to function, don’t install any .NET Framework patches.
Microsoft’s update service will offer systems running XP SP2 an update to .NET Framework 3.0, but machines using XP SP3 won’t see it listed among the optional patches.
Because of this difference — and the fact that .NET installs can fail, as I discussed last week — I urge you to regularly use a third-party software-update service such as Secunia’s free online Software Inspector or the company’s standalone program, Personal Software Inspector (obtain PSI from its download page), to check the vulnerability of your PC’s software.
PSI scans for outdated and vulnerable versions of Sun’s Java, Apple’s QuickTime, Adobe’s Flash and Acrobat, and other common programs that put your system and data at risk if they’re not patched. After scanning 20,000 machines in a recent seven-day period, Secunia reported on Dec. 2 that fewer than 2% of the computers were fully patched.
By the way, several readers notified me that they had problems with the Secunia software scanner. I’ll investigate these issues and report what I find in a future Patch Watch column.
Here’s the bottom line: don’t install any .NET Framework patches listed in Microsoft Update’s “Software, Optional” section unless you’re sure you have the corresponding .NET Framework installed on your system. Any application requiring a specific .NET Framework, such as Intuit’s Quickbooks accounting program, will install the necessary version automatically.
Once the Framework is on your machine, install any offered security patches for it, but be prepared for potential installation glitches. Aaron Stebner’s .NET Framework cleanup tool (download page) can help you out if a .NET update gets stuck. You may have to uninstall that version of .NET and reinstall it, as described by Alan Crawford in this week’s Known Issues column.
Susan Bradley recently received an MVP (Most Valuable Professional) award from Microsoft for her knowledge in the areas of Small Business Server and network security. She’s also a partner in a California CPA firm.
Hang on, I've got the perfect song for this!
 |
By Katy Abby
It’s no wonder that portable music players have become so popular. With the right song playing in the background, ordinary actions can be transformed into extraordinary experiences. Everyday activities beg for personalized playlists: get in the groove of your daily workout, rock out while cleaning the house … the possibilities are endless, even if we’re not! Take a look at this video of a guy who’s ready for anything … or his iPod is, anyway. I wonder what he listens to while reading Windows Secrets? Play the video |
Boost performance by killing unneeded processes
 |
By Fred Langa
Some of the software running in the background on your PC does nothing but unnecessarily bog down your system. There’s a right way and a wrong way to prevent needless processes from tying up your machine’s resources, so let me show you a method that won’t bring you grief. |
A process of elimination for Windows processes
Glenn Haring voiced a problem almost every Windows user faces at one time or another:
- “Where can I learn about processes that are running on my XP system and know which ones I can turn off to save system resources? Can you help me understand how to control what starts up every time I boot up? I know I always have ‘junk’ running that I almost never use.”
I know just what you mean, Glenn. I just encountered the same thing with a new computer that arrived loaded with branded add-ins and so-called “extras” that I didn’t want and had no use for.
The clutter and wasted disk space were bad enough, but as you suggest, some of these items were running at every startup. They consumed memory and CPU cycles as they sat there in the background, waiting for me to call on them, even though I never would. I stripped them out. But I didn’t do it by killing their “processes,” and I suggest you avoid axing processes as well.
Here’s why: you can think of a process as a low-level mini-program that’s launched by other software to handle a specific task or tasks. A single mainstream application or utility may launch many separate processes. The operating system launches many others.
Because the processes running on your PC are the result of other software running, the best way to eliminate unnecessary processes is to eliminate the unnecessary software. This way, the needless processes won’t start in the first place, and that’s much better than trying to kill processes after they’re running.
I’ll get to identifying individual processes later. Let’s start by removing unnecessary software and preventing other apps from starting until you need them.
As always, before you make significant system alterations, create a complete backup. This way, you can experiment more freely: if you don’t like the way things turn out, simply restore the backup to revert your system to its pre-altered state. Windows Secrets senior editor Gizmo Richards offers a great backup primer in his Sept. 18 Best Software column.
With your backup in place, open Control Panel’s Add or Remove Programs applet. (In Vista’s Control Panel, the applet is called Programs and Features.) Review the list of installed programs and select and uninstall any software that you don’t want or don’t use. Depending on what you choose, one or more reboots may be required to complete the uninstallations.
Next, click Start, All Programs, Startup to open your Startup folder. The shortcuts in this folder represent the programs that auto-run when your system starts. If there are shortcuts in your Startup folder to software that you don’t want to run at startup, right-click the unwanted item and select Delete from the context menu. (Note that this doesn’t remove or uninstall the software; it simply removes the program from your PC’s roster of auto-start apps.)
Your system also has a separate and more extensive “startup list” of programs and system services that automatically run when the system boots. This startup list operates at a lower level than the Startup folder mentioned above.
There are many ways to manage this startup list. Several excellent ones were referred to in Dennis O’Reilly’s Known Issues column in the Nov. 20 newsletter.
XP and Vista users have a very good, free startup manager at their disposal; believe it or not, it’s Microsoft’s Windows Defender, which is built into Vista and available as a free add-on for XP (download page). Windows Defender is thought of primarily as an anti-malware tool, but the program also greatly simplifies management of your startup apps.
In XP, install Windows Defender and click Start, All Programs, Windows Defender. When the main Windows Defender window opens, click Tools, Software Explorer.
In Vista, open Windows Defender by clicking Start, Control Panel, Control Panel Home (if you’re in Classic View). Under Programs, choose Change startup programs to open Windows Defender’s Software Explorer tool with Startup Programs selected in the Categories drop-down menu. Alternatively, you can press the Windows key, type windows defender, press Enter, click Tools, and choose Software Explorer.
From there, the process is the same in both XP and Vista: choose Startup Programs in the Categories drop-down menu (it’s probably selected already). You’ll see a list of your startup items along with a ton of additional information about each entry, including who published the software, where the program lives on your hard drive, and whether it’s digitally signed for security purposes. This saves you the manual digging that other startup editors require to find this information.
If you have more than one user account on your system, click the Show for all users button at the bottom of the window. Note that some firewall programs will immediately report activity by the “COM surrogate,” but that’s normal and should be allowed.
Select a program that you want to prevent from running and click Disable and then Yes to confirm. Repeat this step for every program you want to stop from running at startup. That’s all there is to it!
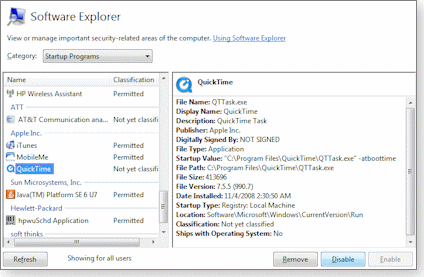
Figure 1. Find out about your startup apps before you disable or remove them via Vista’s Software Explorer tool.
Note that disabling startup applications is mainly a temporary fix designed to let you troubleshoot startup problems; the apps you disable are still fully installed. Although you can leave startup apps disabled forever, Windows will nag you about disabled startup items by popping a warning out of the system tray each time you boot up.
Once you’ve identified the program or programs that are the bogging down your system, the permanent solution is to uninstall the offending apps and replace them with better-behaved ones.
OK, now you’ve uninstalled the software you never use and have disabled the automatic startup of software that doesn’t need to be running all the time. There’s an excellent chance your PC will run better than before, especially if you take a little extra time to do some disk cleanup, such as emptying your Recycle Bin. Even better, run a defrag to clean up after your changes.
If your startups are still too slow, press Ctrl-Alt-Delete to open Task Manager (in Vista, you must also click Start Task Manager). Select the Applications tab to see what’s running on your system. If there’s unnecessary software active, use the techniques described above to uninstall the programs or prevent them from starting until you specifically invoke them.
If things still aren’t the way you want, then — and only then — should you look at the individual items in Task Manager’s Processes tab.
Processes don’t exist independently: they’re launched by programs. Therefore, the best way to control what processes run on your system is by managing the software you run, not by tinkering with the actual processes they launch.
If you don’t recognize a specific process on this list — the names are often cryptic or uninformative — you can use sites such as ProcessLibrary.com or WhatProcess.com to help identify the purpose of each process. Advanced users may wish to ID obscure processes by downloading and using the free Process Explorer utility (download page), which was developed by Sysinternals and is now owned by Microsoft.
Once you’ve tracked a specific process back to the software that launched it, you can decide whether you need it. If you feel the process isn’t required to run, uninstall or disable the software that spawned it, using the techniques I described above.
Note that simply killing an individual process is a last resort. If you don’t disable or stop the software that launched the process, the process will simply return at the next boot. In some cases, killing a process without dealing with the software that generated it may hang the program or make your system unstable.
Bewildering motherboard battery woes
Ron Troy describes the issue with his aging PC as “weird XP/Dell problems”:
- “The PC is an old Dell. On boot or reboot, sometimes the Dell logo comes up, and nothing else. Try again: Dell logo and normal boot sequence. No rhyme or reason why and when.
“Also, out of the blue the PC will sometimes run its Power-On Self Test (POST) and do the usual one beep, but the boot menu never comes up. When I put in a boot CD, I get the message to hit any key to boot off the CD/DVD. But I can’t make the hard drive bootable.
“Finally, after all obvious attempts to fix things, I do a from-scratch reinstall of XP, the updates, etc. The PC runs wonderfully for months, then I’m back to ‘out of the blue.’
“This isn’t my main PC, but the problems are weird and interesting to me, and I’d love to be able to get a solution for them.”
With an old system like yours, Ron, several things may be going wrong. My first guess is that the small battery on the PC’s motherboard is near death. That battery is used to retain some system settings when your PC is totally powered off. These settings include the hardware previously detected as well as the type and geometry of the hard drive.
A weak or dead battery can cause problems ranging from system clocks that can’t keep time to PCs that “forget” what kind of hard drives and other hardware they use.
If a battery is at the very end of its useful life, there may be some days — such as when the room temperature is high or the PC is already warmed up — when it still can produce just enough juice to keep things going. On other days — such as when the room or the PC itself is cool — the battery can’t fire up.
Doesn’t this sound a lot like what’s going on in your system, Ron?
Most PC motherboards use standard coin-size batteries that cost just a buck or two at the local electronics or drug store, and they’re easy to replace. For instructions, read this how-to article from the LangaList archives.
Give the new battery a shot, and I’ll bet your mysterious boot problems will disappear!
Is it OK to delete old install files?
Peter Sands is running out of disk space and wants to know whether some mystery files are safe to delete:
- “I have a laptop running XP Home that’s struggling for space on the C: drive. There are over 100 $NtUninstallKB… folders in C:Windows that range in size from 2MB to 8MB — it all adds up! I believe these are MS updates, but are they needed?
“Also, there is a folder called C:WindowsInstaller that has hundreds of files totaling around 3GB. What are these? Are they really needed? And if not, what’s the best way to kill them?”
Yes, you can delete the $NtUninstallKB… files and any related $NtServicePackUninstall$ folders and files, if you wish. Those are mostly uninstall files from Windows Update and — as you might guess — service packs. You need these files only if you might ever want to roll back or uninstall a Service Pack or update.
If you’re going to keep a given patch or update, the uninstall files serve no further purpose. Just delete them as you would any other file or folder. (Note: Windows will correctly prevent the deletion of any of those files that are still needed for one reason or another. Don’t be alarmed if a few files or folders remain behind after your cleanup.)
The fixes will still be listed in XP’s Add or Remove Programs Control Panel applet. To remove their entries, open the program, check Show updates at the top of the window, scroll to Windows XP – Software Updates, select each one at a time, and click Remove.
You’ll get an error message telling you the file has already been deleted. Click Yes and move on to the next one. Just be sure not to accidentally uninstall an update that you haven’t already deleted. If the Software Update Removal Wizard opens rather than the “already deleted” error message, click Cancel.
The files in C:WindowsInstaller are different. Those files are usually generated by the Windows Installer (a.k.a. “Microsoft Installer,” the source of the .msi file extensions so often used by installer packages). Those files are needed when you change, modify, or repair the software placed on your hard drive by the Windows Installer.
Plus, as you upgrade and patch that software, additional files may be added to the Installer folder. Proper operation of your software may very well depend on having all these files — original and patches — available. I suggest that you leave the Installer files in place.
But you’re not out of options. Windows’ built-in file/folder/disk compression tool can reduce the size of the files in that folder — or even the entire contents of your hard drive — by roughly half. This can effectively double the drive’s capacity.
The main disadvantage of compression is that it makes disk writes and reads fractionally slower, but in most cases, the delay isn’t noticeable without a stopwatch. Microsoft’s instructions for using compression in XP are in KB article 306531 and for Vista in this article on the Windows Help and How To page.
If you’re truly out of disk space and a higher-capacity drive isn’t a good option, then disk compression might be just the ticket!
Another great source for help with driver woes
In my Nov. 20 column, reader Keith Hoffman reported being able to record but not hear what he was recording. I suspected bad drivers were the problem and steered Keith to a couple of well-known sources of drivers.
But Sande Nissen found a great source that I’d never heard of before for Vista-compatible drivers:
- “I had similar problems finding 32-bit Vista drivers for an ADI 198x sound card (a.k.a. SoundMAX). After trying every piece of advice I could find on the Web, I found the solution in an unexpected place.
“If you’re willing to allow an ActiveX control to be installed on your PC to detect your hardware, you can get free drivers from Ma-Config.com. But first, a warning: the Web site comes up in French. To change it to English, look for the small round icon in the upper-right corner that looks like a Union Jack (the British flag) and click that.
“Thus far, Ma-Config.com has found every Vista driver I was missing on every PC, 32- and 64-bit.”
Thanks, Sande! It should be noted that ma in French means “my” in English, and the site sometimes refers to itself as My-Config.com (a domain that redirects to Ma-Config.com). There are several similar tools available at other sites that use English as their mother tongue, including DiagnoseDrivers.com.
Using an ActiveX component from a third party is always a little unnerving for the security-conscious. However, doing so might be acceptable as a last resort in tracking down obscure drivers, especially on a fresh Windows installation that contains little if any personal information for a bad guy to steal by exploiting some ActiveX vulnerability.
I suggest that, after using the driver-sniffing tool, you uninstall the software and then make sure the ActiveX component is gone. In Internet Explorer, click Tools, Internet Options, Programs, Manage Add-ons. Select Downloaded ActiveX Controls in the Show drop-down menu. If the uninstall routine left the control behind, you can manually flag and delete it there to make sure it’s well and truly gone.
The simplest way to measure bandwidth use
In my Dec. 4 column, reader Peter Sutherland asked how to log his network-bandwidth use to ensure that he didn’t exceed his ISP’s monthly limit. I suggested he use the network monitor built into Windows, but that utility doesn’t track bandwidth use over time.
For this task, you need a program such as Hoo Technologies’ $20 Net Meter. (There’s a free 30-day trial version available from the company’s download page). Net Meter graphs your Internet usage in real time and reports on your daily, weekly, and monthly traffic, among other types of reports. My thanks to long-time reader Guy Jacques for his research help on this topic.
| Guy will receive a gift certificate for a book, CD, or DVD of his choice for sending a tip we printed. Send us your tips via the Windows Secrets contact page. |
Fred Langa is editor-at-large of the Windows Secrets Newsletter. He was formerly editor of Byte Magazine (1987–91), editorial director of CMP Media (1991–97), and editor of the LangaList e-mail newsletter from its origin in 1997 until its merger with Windows Secrets in November 2006.
Connect safely over open Wi-Fi networks
 |
By Ian “Gizmo” Richards
Using a Wi-Fi network in a coffee shop, airport, or hotel is such a serious security risk that I simply never do it without taking additional measures to protect my data and my PC. These three techniques will keep you safe while using a public network, often without costing you anything but a small bit of time. |
Public wireless networks attract data thieves
Wi-Fi may not in itself be insecure, but various implementations of the wireless technology are.
The most vulnerable of these are “open” networks, which don’t even require a password or network key to use. Unfortunately, open networks are common; indeed, most of the free networks you encounter in coffee shops, hotel lobbies, and other public spaces fall into this category.
Whenever you use an open network, the information you send and receive is exposed for all to see. And there are plenty of nasty types lurking around who want to see it. They are looking for confidential information in your e-mails, SMS messages, and other Web communications that would enable them to steal your passwords, personal identity, and money.
Stealing information from traffic on an open Wi-Fi network is relatively easy. You don’t have to be a technical expert or hacker because there is a wide range of tools available for download that allow just about anyone to tune into and record other people’s communications.
One such program is the free Wireshark utility, which Ryan Russell described in his Mar. 20 Perimeter Scan column. Hey, there’s even a YouTube video showing how to do it.
So the next time you’re considering using an open network, remember that the person at the next table or in the next room may be listening in. If that thought makes you uncomfortable, here are some things you can do to prevent being a wireless victim.
Option 1: Always connect via a secure network
Accessing many hotel and airport Wi-Fi networks requires a network key that you typically have to purchase. Such networks are much more secure than open networks, but there are two serious caveats that you need to be aware of.
First, don’t purchase access to the network by entering your credit card details over the same network. When you buy access online, you’re doing so over an open network. It has to be open to allow you to buy the access key.
Admittedly, most such credit card purchases make use of an encrypted https: connection, but this encryption is not a total safeguard. Quite often, these transactions use both secure and insecure pages, so some of your personal details can still be stolen.
A much better solution is to bypass the problem entirely by buying a network access card or coupon from a clerk or vending machine. It’s simply a much better practice. None of your credit card details can be stolen because you enter only the access code over the open network — never any personal data.
If you regularly use open networks, a more convenient solution is to purchase the services of a Wi-Fi access provider such as MobilityPass, Boingo, or iPass. Most such services offer secure connections and let you buy access before you travel. Some also offer VPN access and other additional security measures. On the downside, these services don’t offer universal coverage and are not cheap.
A second caveat is that not all networks using access keys are secure. Some such networks still use the first-generation Wired Equivalent Privacy (WEP) security protocol rather than the more recent and more secure Wi-Fi Protected Access (WPA) and WPA2. WEP security can be broken with relative ease using off-the-shelf tools such as WEPAttack and WEPCrack, so WEP can no longer be considered secure.
Both Windows XP and Vista display the security protocol used whenever you connect to a wireless network. If you see that you’re connected to a WEP network, you’re not secure, even though you used a network password to access the network.
For more on WEP and WPA security, see Mark Edwards’ Nov. 13 PC Tune-Up column.
Option 2: Use a virtual private network
One of the best ways to protect your Wi-Fi sessions is to use a VPN connection. A VPN functions as a fully encrypted private network operating within — or “tunneling through” — the public Internet. In the context of Wi-Fi, a VPN works like this:
A special VPN program runs on your PC and uses a Wi-Fi connection to create a link with a remotely located VPN server. Afterward, all your Internet activities are conducted with the VPN server acting as an intermediary between your computer and the Internet.
In other words, the VPN server sits between you and the Internet. The connection between you and the remote VPN server is fully encrypted, so no one can spy on your traffic over the Wi-Fi link. Furthermore, VPN encryption is virtually unbreakable: you have effectively turned a highly insecure Wi-Fi connection into a highly secure one.
VPNs do more than simply provide a secure link, however. They also give you Web anonymity and privacy — even your ISP won’t be able to determine where you have surfed over the encrypted link. VPNs also let you bypass corporate and national firewalls, which explains the popularity of VPNs in countries with restrictive or totalitarian governments.
The IT departments of most corporations and government agencies provide their employees with VPN connections so the workers can get secure remote access to the organization’s resources. However, home users can also set up a VPN by using one of several different methods.
If you use an always-on Internet connection and your ISP has allocated you a dedicated (or “static”) IP address, then in principle, you can set up your home PC as a VPN server.
Whenever you’re using a laptop or other computer away from home, you can connect to the VPN server software on your home PC to create a secure VPN. Then you can surf securely via your home network, even over an insecure, open Wi-Fi connection.
Challenges to creating a home VPN server
Creating a VPN server on your home PC is technically challenging. Furthermore, doing so creates the risk of enabling a hacker to break into your home PC via the VPN server.
If you’re the adventursome type and tempted to try the home-PC server approach, I suggest you use LogMeIn’s Hamachi program (free for home use) to set up the VPN (download page).
Then follow the instructions on LogMeIn’s forum to tunnel your remote Wi-Fi browsing sessions through Hamachi. An alternative to Hamachi is the open-source OpenVPN program (download page).
A far simpler approach is to use a third-party VPN server. There are many companies that provide this service for a fee, including:
• PublicVPN
• Witopia
• GoTrusted
Most of these services provide access to their VPN servers through a small, downloadable program or, alternatively, via the Web. Access is available on a spot-usage basis or via monthly or quarterly subscriptions.
When choosing a VPN service, make sure the company provides VPN access for e-mail as well as for Web browsing. If you use IM and FTP, make sure these messaging and file-transfer networks are covered by the service as well.
There are several VPN protocols in use, each of which is capable of doing the job. The protocols include PPTP, L2TP, IPSec, and SSL. Indeed, the clients for most VPN services will offer a choice of VPN protocols, because some ISPs don’t support all the protocols.
There have been some security concerns about PPTP, which is the most-widely deployed VPN protocol. However, if you use a long password or passphrase, you’ll be completely safe using PPTP.
If you don’t like the idea of paying for a VPN service, consider going with a free, ad-supported alternative. The most popular of these is HotSpot Shield. I haven’t used this service myself, but with 15 million customers, the company must be doing something right.
Another free VPN service is iPIG. Unlike HotSpot Shield, there are no ads on iPIG, but most users will find the service’s 10MB data-transfer limit a deal-breaker.
Option 3: Use an anonymizing service
You may have heard of the free Tor program (download page) that allows you to surf the Internet anonymously. However, Tor and other anonymizing services can also be used to increase your Internet security.
That’s because Tor encrypts the first link between your PC and the first Tor server. If that link includes a Wi-Fi connection, then the Wi-Fi link is encrypted as well.
That means you can use even an insecure, open Wi-Fi connection with confidence. Furthermore, Tor’s additional security won’t cost you a cent.
It sounds like a great solution, but there are a couple of catches:
First, you’ll find your surfing noticeably slower when using Tor because all traffic is routed through an additional chain of Web servers. At peak periods, this can be a real problem; I’ve seen Tor bring my network to a near-standstill at times.
Second, you’ll find Tor works well enough for Web browsing but not so well for other Internet activities. FTP is a good example: while it’s possible to configure Tor to work with FTP, I’ve found the performance to be unacceptable. (I’ve heard that BitTorrent performance can be poor over Tor as well.)
These limitation aside, Tor is a free and time-proven solution for improving your Wi-Fi security.
The wireless-security plan that works for me
I travel a lot, so I find myself using Wi-Fi networks in airports and hotels all the time. Because so many of these networks are open, Wi-Fi security is a real and practical problem for me.
I’ve tried various solutions, including setting up Hamachi on my home PC. None of the setups has been problem-free, but on balance, the solution that works best for me is a commercial VPN service. Over the years, I’ve used three of these services, which are mentioned above in Option 2, and all three worked just fine. The one I use today is the cheapest service that offers me the features I need.
As a backup, I also carry a copy of Tor around with me. For this purpose, I use OperaTor (download page), which is a portable implementation of the Opera browser with Tor preconfigured.
Whatever you do, please don’t use open Wi-Fi networks without some form of additional protection. If in the past you’ve gotten away with using open wireless networks without encryption or other safeguards, then thank your lucky stars.
If you continue to use open Wi-Fi without protection, I can assure you that one day, you’re going to get caught out big-time. Be smart and fix the problem now.
Ian “Gizmo” Richards is senior editor of the Windows Secrets Newsletter. He was formerly editor of the Support Alert Newsletter, which merged with Windows Secrets in July 2008. Gizmo alternates the Best Software column each week with contributing editor Scott Spanbauer.
Freeware helps to boot the bots off your network
 |
By Mark Joseph Edwards
Bots can wreak havoc on your network and endanger your data, but they’re not difficult to eradicate. A new tool tracks down bots, intercepts their communications, and produces reports that can aid you in removing them from your systems. |
Sniffing your network for bot-like activity
Bots are little programs that sit unobtrusively on your PC or network, just waiting to collect and transmit your personal information or perform some other nefarious act. There are now armies of these rogue applets; there’s a good chance your network has one, even if you have solid security tools and practices in place.
And even if your network is presently clean, a clever bot could slip by your defenses in the future.
One way to track these nuisances is to use BotHunter, a new free tool from SRI International that detects bot-related activity on computers within your network. The program monitors and correlates the bidirectional communication that typically takes place between a bot and the bot-network operators.
When it detects probable bot activity, BotHunter produces a report with information that helps you figure out where the bot is located on your network and what the bot is attempting to do. With that information in hand, you can then remove the bot and bolster the security of the affected systems.
BotHunter is available for Windows XP and Linux; it also comes on a bootable CD. According to the vendor’s site, the program’s auto-update service delivers information about new threats and sources for more help combatting bots and other types of malware. Also, the program’s dialog-analysis rules are updated automatically to ferret out the latest bad actors.
Get your copy of BotHunter from SRI International’s download page.
Open-source app detects network intrusions
Your network probably has antivirus software and firewalls, but does it have a full-fledged IDS/IPS (intrusion detection system/intrusion prevention system)? If not, then you should take a close look at Snort.
Snort may just be the best open-source IDS/IPS available. The program runs on countless networks all over the world and has a huge community of users. It’s a rules-based scanner that detects an incredibly long list of attack types, including SQL injection, cross-site scripting, Trojans, bots, browser-related attacks, and operating system exploits.
Snort detects and blocks any network attack whose traffic can be matched to a pattern. You can also create your own custom rules if the need arises.
The utility sniffs all network traffic and compares the data to its rule sets. When a pattern matches, Snort performs various actions — including logging the traffic, blocking it, and alerting network administrators to the intrusion attempt.
The stock Snort rule sets are extensive and regularly updated. In addition, Snort users around the world regularly contribute their own rules, which are then shared with anyone who needs them.
Snort is not necessarily a desktop application, although you could run it on a desktop system. While network administrators typically run the program on a dedicated machine on their network, a Windows version of Snort is available.
There are two ways to deploy Snort on Windows PCs:
• Option 1: Download the components you want to use, along with any supporting packages you might need, from the Snort download page. Install and configure the components so that they work well together. This is a very tedious approach, recommended only if you’re thoroughly familiar with network-software configuration.
• Option 2: Use the Windows Intrusion Detection System (WinIDS), which is based on Snort (more info). Download the WinIDS All-In-One Software Pack and associated user guides, which contain everything you need to get started (download page).
The WinIDS option is much simpler than the manual approach. Even if you use WinIDS, you need a fair amount of computer knowledge as well as considerable patience to get Snort working properly. Configuring the utility can be tedious, but the effort is well worth the extra protection you’ll realize when you’re done.
Emerging Threats rules make Snort more potent
If you currently use Snort or intend to adopt the program in the future, consider using Snort’s Emerging Threats rules as well. According to the program’s developers, the Emerging Threats rules are “the fastest-moving and most diverse Snort signature set and firewall rules available.”
The rules are produced through the efforts of the Snort user community and are updated very quickly whenever new threats emerge. For example, on Dec. 9, rules to detect four new ActiveX exploits were added to the app, along with protection against five different SQL injection exploits. The update also provided information on various networks known to distribute malware and other types of fraud.
All together, the Emerging Threats rules require only a few megabytes of disk space. The rules protect against a range of attacks, including those targeted at Web applications, VoIP tools, and games. The rules can also block the influx of new malware and thwart access to hostile networks, bot networks, and such unwanted content as porn and gambling.
If you use Snort, consider the Emerging Threats rules a must-have add-on. You can download the rules from EmergingThreat.net’s rule download page.
Unlock the hidden features in the Windows 7 beta
If you’ve installed the Windows 7 beta, you might be interested to learn that there are hidden features in the program that are easy to unlock, thanks to one talented programmer.
These features were discovered by Rafael Rivera, whose careful sleuthing led to the release of Blue Badge, a program that makes unleashing these hidden functions a breeze.
According to Rivera, Microsoft blocked access to certain features by checking to see whether users were members of certain domains and whether they were temporary or contract employees. Those parameter checks were hard-coded into certain system files.
Blue Badge makes backup copies of the affected system files and then patches those files to bypass the checks Microsoft put in place, thereby opening access to the hidden features. Rivera says the cloaked goodies include the new Windows 7 taskbar, the new Desktop Slideshow, and gestures and panning on touchscreen systems.
If you’re using the beta of Windows 7 and are interested in seeing the hidden features, get a copy of Blue Badge and take them out for a test drive (download page).
Keep in mind, however, that Microsoft executives insist Windows 7’s final interface may look nothing like the features unlocked by Blue Badge — for better or worse.
Mark Joseph Edwards is a senior contributing editor of Windows IT Pro Magazine and regularly writes for its Security Matters blog. He’s a network engineer, freelance writer, and the author of Internet Security with Windows NT.
Internet Explorer is target of zero-day attack
 |
By Susan Bradley
There’s no fix yet for Tuesday’s remote-code-execution exploit, which has already been found circulating in the wild. Windows users should switch to a browser other than Internet Explorer until Microsoft releases a patch for this IE security hole. |
XML parser appears to be the IE malware gateway
French security agency Vupen announced this week a new XML-based attack on IE 7. Symantec, however, reports that the threat might be wider, saying: “Internet Explorer 6 could potentially be affected by the same problem.”
No patch is available for this exploit at this writing. Researchers at the Internet Storm Center recommend in a diary post that you use an alternative browser until the exploit is patched.
There is very little information about the security hole, which was first reported by Robert McMillan of IDG News. The problem appears to be related to the browser’s XML parser. The initial report indicated that the breach was verified on Windows XP SP2, but as Dan Goodin states on the Register, McAfee researchers have confirmed that XP SP3 and Vista SP1 are targets as well. Vupen also found that Windows Server 2003 is vulnerable.
I’ll report to you immediately on this matter via Windows Secrets when more information becomes available, particularly on the expected arrival of a patch from Microsoft for this hole.
MS08-070 (932349)
Office add-ons using ActiveX are at risk
If you use any applications that rely on ActiveX controls, you’ll be interested in Microsoft security bulletin MS08-070 (932349), although the patch really affects only application developers. Several ActiveX controls used in Visual Basic for Applications (VBA) are flagged as being insecure.
Developers use these ActiveX controls to build programs that interact with Word and other Office apps, including many custom business applications. Among the more popular ActiveX controls for this purpose are the DataGrid control, FlexGrid control, and Hierarchical FlexGrid control.
Only VBA programs that create an instance of the ActiveX control directly through Office are affected. A different patch will be offered to systems running different applications, as explained in the following MS Knowledge Base articles:
- 926857: Visual Basic 6.0 Runtime
- 958392: Visual Studio .NET 2002 SP1
- 958393: Visual Studio .NET 2003 SP1
- 958369: Visual FoxPro 8 SP1
- 958370: Visual FoxPro 9 SP1
- 958371: Visual FoxPro 9 SP2
- 957797: Office FrontPage 2002 SP3
- 949045: Office Project 2003
- 949046: Office Project 2007
Note that the FrontPage patch applies only to the Chinese Simplified (China), Chinese Pan (Hong Kong), Chinese Traditional (Taiwan), and Korean languages.
Of course, the problem also affects any proprietary apps that use these ActiveX controls. Unfortunately, developers rarely disclose all the ActiveX controls their applications use. Microsoft’s KB article indicates that Web-based solutions aren’t affected, even though the problem involves ActiveX.
The best suggestion I can make is to monitor any third-party software you use that interacts with Word or Excel. You may start seeing the error messages discussed in KB article 932349. These include “Element not found” and “Object library invalid or contains references to object definitions that could not be found,” in which case a macro will fail to run.
When an Office-based template or form doesn’t work as it should, contact the vendor for an updated version of the application. Then uninstall any of the patches in the list above that you may have installed.
Let me know via the Windows Secrets contact page if you see any of these errors or encounter other problems with your applications. I’ll update the situation in a future column.
MS08-071 (956802)
Return of the image files that ate Windows
When I saw this week’s patch for the Graphics Device Interface (GDI), my first thought was, “We’re patching this again?” Malformed and specially crafted media files are being used to attack us once more. Apply the patch described in MS08-071 (956802) to ensure that bad guys don’t nail you with Web pages that host malicious image files.
For those playing Security Trivial Pursuit this holiday season, remember that the same GDI32.dll file is involved in all the threats. These include attacks in January 2006 (MS06-001), August 2007 (MS07-046), and April 2008 (MS08-021).
I don’t think we’ve seen the last of the vulnerable image files. Give this patch a high priority because it is so easy for criminals to host the attack on a Web page.
MS08-076 (959807)
Sights and sounds of Christmas may be dangerous
Windows Media Player versions 6.4, 7.1, 9, 9.5, and 11 are being updated to patch vulnerabilities that may be exploited in attacks coming from malicious Web pages. This time of year, friends and family regularly send humorous links to pages on such video sites as YouTube and Hulu. These media files may also be used by attackers to gain control of your computer.
While it’s enticing to watch the latest funny video link that friends and family send around — as evidenced by our own Katy Abby’s hilarous Wacky Web Week finds — just remember that some of these videos may be used in attacks. That seemingly innocent link to a musical Christmas greeting could be trying to place malware on your system.
Media Player 6.4 will see the update in the form of the patch described in KB article 954600, Media Player 7.1, 9.0, 9.5, and 11 are patched via the update in 952069, and systems running Media Services on Windows Servers will be offered the patch in 952068.
Give these patches a high priority this holiday season.
MS08-073 (958215)
Yet another important Internet Explorer patch
It wouldn’t be a fitting end to the year’s security patches without one last fix for Internet Explorer (not counting the one we anticipate for the zero-day threat described above). Unfortunately, it’s a safe bet that the IE patches will continue in 2009.
The fix described in Microsoft security bulletin MS08-073 (958215) patches several holes that allow bad guys to use specially crafted Web pages to gain entry to our machines merely by opening the pages in IE. The problem affects only users who are logged in an Administrator account, which gives the criminals full rights to the system.
I haven’t seen any issues related to this patch, but as with any update affecting Internet Explorer, be prepared to review and adjust third-party firewalls and antivirus settings if you have problems connecting via IE post install.
MS08-075 (959349)
Search vulnerability gets a double-shot fix
It takes two patches to fix the vulnerabilities found in the search function in Vista and Windows Server 2008. Microsoft security bulletin MS08-075 covers the fixes described in KB articles 958623 and 958624.
The search exploit allows Web pages to attack these two operating systems. Fortunately, on any system with Internet Explorer 7 installed, you’ll see a prompt reporting that the Web page is attempting to open content in Windows Explorer. If this occurs when you visit a page, don’t approve the request.
These patches are noteworthy because the exploits they block specifically attack a new feature of Vista and Server 2008. The holes don’t impact Windows XP’s search function.
MS08-072 (957173) and MS08-074 (959070)
Updates arrive for Word, Outlook, and Excel
The last Microsoft patches of 2008 revisit the major attack vectors of the year. The patches for Word and Outlook described in MS08-075 (957173) also affect the Office 2007 Compatibility Pack.
If your system has only Office 2003 installed, don’t be surprised if you’re offered Office 2007 patches as well. These are patching the Office 2007 Compatibility Pack, which an application may have written to your PC without your involvement.
In addition to the Office compatibility patches, you might see a litany of other Office fixes in your update list:
- 956328: Word 2002 SP2
- 956357: Word 2003 SP2
- 956358: Word 2007, Outlook 2007
- 956828: Office 2007 Compatibility Pack
- 959487: Microsoft Works
- 960401: Office for Mac 2008
- 960402: Office for Mac 2004
- 960403: Office XML format for Mac
Not to be outdone by Word and Outlook, Excel closes out 2008 with a multitude of patches of its own. The glitch described in MS08-074 (959070) is similar to the problem in Word that allows an attacker to use a specially crafted file to take full control of your system. Also, like Word’s patch, you may see an Excel 2007 patch due to the presence of the Office 2007 compatibility bundle, even though you only have Excel 2003 installed.
- 958372: Excel 2002 SP2
- 958437: Excel 2007
- 958436: Excel 2003
- 958435: Excel 2000
- 958439: Office 2007 Compatibility Pack
- 958442: Excel Viewer 2007
- 958434: Excel Viewer 2003
- 960401: Office for Mac 2008
- 960402: Office for Mac 2004
- 960403: Office XML format for Mac
You can find out more about Microsoft’s Office Compatibility Pack on the company’s download page for the add-on.
MS08-077 (957175)
SharePoint Server 2007 open to DoS attack
Our final patch for 2008 is for SharePoint Server 2007, a shared-document portal that’s used by many businesses. MS08-077 (957175) describes the fix for a vulnerability that allows an attacker to collect private information or launch a denial-of-service assault on the server.
The only unusual item about the patch is that this security update may place three entries in the server’s Add or Remove Programs list. Normally, you’d receive only one entry; I guess the other two are Microsoft’s version of a holiday bonus.
A WordPad-borne virus? What’s next, Minesweeper?
Microsoft security advisory 960906 reveals that attackers are using WordPad, the word processor built into Windows. You can mitigate the potential for this attack by not opening any suspicious .wri documents. Note that the problem doesn’t affect Windows XP SP3, Vista, or Server 2008. That doesn’t leave many potential victims, fortunately.
Microsoft’s alert indicates that the exploit has been seen only in limited attacks. WordPad is such a core component of Windows that it’s easy to take the program for granted. Perhaps none of our applications are safe. My Dad will have to give up his PC if Solitaire ever becomes a threat vector.
The Patch Watch column reveals problems with patches for Windows and major Windows applications. Susan Bradley recently received an MVP (Most Valuable Professional) award from Microsoft for her knowledge in the areas of Small Business Server and network security. She’s also a partner in a California CPA firm.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Microsoft : Resolving Blue Screen errors in Windows
by
Alex5723
50 minutes ago -
Where’s the cache today?
by
Up2you2
16 hours, 10 minutes ago -
Ascension says recent data breach affects over 430,000 patients
by
Nibbled To Death By Ducks
8 hours, 56 minutes ago -
Nintendo Switch 2 has a remote killing switch
by
Alex5723
10 hours, 41 minutes ago -
Blocking Search (on task bar) from going to web
by
HenryW
16 hours, 51 minutes ago -
Windows 10: Microsoft 365 Apps will be supported up to Oct. 10 2028
by
Alex5723
1 day, 9 hours ago -
Add or Remove “Ask Copilot” Context Menu in Windows 11 and 10
by
Alex5723
1 day, 9 hours ago -
regarding april update and may update
by
heybengbeng
1 day, 11 hours ago -
MS Passkey
by
pmruzicka
12 hours, 56 minutes ago -
Can’t make Opera my default browser
by
bmeacham
1 day, 18 hours ago -
*Some settings are managed by your organization
by
rlowe44
1 day, 5 hours ago -
Formatting of “Forward”ed e-mails
by
Scott Mills
1 day, 17 hours ago -
SmartSwitch PC Updates will only be supported through the MS Store Going Forward
by
PL1
2 days, 13 hours ago -
CISA warns of hackers targeting critical oil infrastructure
by
Nibbled To Death By Ducks
2 days, 22 hours ago -
AI slop
by
Susan Bradley
16 hours, 12 minutes ago -
Chrome : Using AI with Enhanced Protection mode
by
Alex5723
2 days, 23 hours ago -
Two blank icons
by
CR2
7 hours, 44 minutes ago -
Documents, Pictures, Desktop on OneDrive in Windows 11
by
ThePhoenix
9 hours, 42 minutes ago -
End of 10
by
Alex5723
3 days, 11 hours ago -
Single account cannot access printer’s automatic duplex functionality
by
Bruce
2 days, 9 hours ago -
test post
by
gtd12345
3 days, 17 hours ago -
Privacy and the Real ID
by
Susan Bradley
3 days, 7 hours ago -
MS-DEFCON 2: Deferring that upgrade
by
Susan Bradley
1 day, 9 hours ago -
Cant log on to oldergeeks.Com
by
WSJonharnew
3 days, 21 hours ago -
Upgrading from Win 10
by
WSjcgc50
2 days, 9 hours ago -
USB webcam / microphone missing after KB5050009 update
by
WSlloydkuhnle
2 days, 12 hours ago -
TeleMessage, a modified Signal clone used by US government has been hacked
by
Alex5723
4 days, 13 hours ago -
The story of Windows Longhorn
by
Cybertooth
4 days ago -
Red x next to folder on OneDrive iPadOS
by
dmt_3904
4 days, 15 hours ago -
Are manuals extinct?
by
Susan Bradley
1 day, 15 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

