
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Microsoft touts Universal apps, once again
In this issue
- WACKY WEB WEEK: Brisbane musician is a one-man cover band
- TOP STORY: Microsoft touts Universal apps, once again
- LANGALIST PLUS: How to customize file and folder views
- ON SECURITY: The many ways PCs have become vulnerable
- LOUNGE LIFE: Updates can cause as well as fix trouble
- BEST UTILITIES: A tour through the powerful Autoruns utility
Brisbane musician is a one-man cover band
 |
Sometimes imitation becomes a new form of art. Such might be the case with Australian performer Tom Thum — a beat-boxer of extraordinary talent. Tom makes music (often percussive) and other noises with just his mouth and a microphone. He persuasively mimics musical stylists as diverse as a didgeridoo instrumentalist and Michael Jackson. In this video, he also conjures up an entire jazz band — singers and master of ceremony included. For his most complex creations, Tom gets some help from technology. But his vocal skills alone could make a myna bird weep. Click below or go to the original YouTube video. |
| Post your thoughts about this story in the WS Columns forum. |
Microsoft touts Universal apps, once again
Microsoft has spent a great deal of time and money trying to convince developers and customers that “Universal” (formerly “Modern,” formerly “Metro”) apps will drive the future of Windows.
This is the third time we’ve heard variants of the same spiel, but it (finally!) just might work.
What exactly is a Windows Universal app?
The software we interact with — whether you call it a program, an application, or simply an “app” for short — nearly always runs on top of an operating system. And most of these applications communicate with the OS through a set of routines collectively called the application programming interface or, simply, “API.” With Windows, the API is colloquially known as Win32, and — with rare exceptions — all the desktop apps you and I have ever run have relied on this set of API routines.
But in early June 2011, Microsoft revealed a new set of APIs called Windows Runtime — or, more commonly, WinRT. Speaking at the All Things D D9 conference, then–MS Windows president Steve Sinofsky and then–VP Julie Larson-Green debuted Windows 8 (video). As part of the show-and-tell, they demonstrated new “Metro” apps, which would interact with Windows in a very different way: the apps would use the newly minted — and still evolving — WinRT API set.
Microsoft used labels such as “immersive” and “full-screen” for these apps, but almost everyone else settled on Microsoft’s internal code name: Metro — a name I and a zillion other techies still prefer for clarity. (Microsoft had to give up the use of “Metro” to avoid a lawsuit — more info.)
It seemed as if Redmond would never settle on a final name for WinRT-based applications; it’s used “Modern UI,” “Windows 8 apps,” “Windows Store apps,” “New User Interface,” “Microsoft Design Language,” “Microsoft style design,” and simply “Modern.” With Windows 10, these “Windows-native” apps are now called “Universal.” (A recently posted MS support page still refers to them as “Windows Store apps.”)
Whatever you call them — Metro, Windows Store apps, or Universal — they all refer to the same type of software; they’re all applications that use the WinRT API.
Universal apps have other characteristics that set them apart from classic Windows programs. For example, they’re sandboxed, which makes it harder to spread infections through them. They’re also easily interrupted, which helps minimize their power consumption. And if a Universal app hangs, it’s unlikely it will freeze the entire machine.
WinRT API support started with Windows 8/8.1 and Server 2012. And, as you undoubtedly know by now, Universal apps run only on the “Metro” side of Windows — not on the desktop. ARM-based processors, used in many phones and tablets (such as the MS Surface RT) also run the WinRT API.
But just to add a bit of confusion, current Windows phones run Windows Phone RT API, which is vaguely similar to the WinRT API.
If you’re curious about the history of WinRT, Ars Technica’s Peter Bright wrote a comprehensive account that’s well worth reading.
The ongoing checkered history of WinRT apps
If you’ve followed Microsoft’s recent spate of Windows Store announcements, you might think that Universal apps are a new concept — a programmatic Holy Grail that will kick-start the development of fabulous apps for Windows Phone and all other future versions of Windows.
It’s not new; we’ve seen this all before.
Microsoft first started its pan-version vision at the September 2011 Build conference. Martyn Lovell’s presentation, “Lap around the Windows Runtime,” gave the first in-depth look at how WinRT would work. It touted a completely new and different way to construct Windows-native applications.
At the time, I detected a healthy amount of skepticism among developers. Some analysts, on the other hand, clearly bought what Microsoft was selling. A June 2012 Gartner article stated that WinRT “provides a common interface and programming API set from phones to servers.”
Gag!
Nothing of the sort happened. Microsoft created the WinRT-based Metro side of Windows 8 almost independently of Windows Phone RT, though both were building something called “Windows 8” with a “Windows RT” runtime. The development teams were completely separate; Steve Sinofsky had the Win8 side and Terry Myerson ran the Phone side — and rarely the twain did mix.
Depending on how you count, we’re now on the third version of Windows RT. The initial 1.0 pan-version efforts soon evolved into Windows 8’s ugly, bifurcated deception. Then Sinofsky left and Myerson took over all Windows development.
Now, with both the mobile and the desktop efforts in the same organization (and the phone guys running the show) we just might see a new WinRT API that really can run on multiple types of devices, with only minor changes for platform/screen size.
Where Microsoft is headed with WinRT
Microsoft desperately needs WinRT to succeed — which means enticing software developers into writing truly great apps that use the WinRT API. The future of Windows might well depend on it.
If you look carefully at the current crop of WinRT apps offered in both the Windows Store and the Windows Phone Store, you can come to only one conclusion: the quantity and quality of apps doesn’t come close to what Apple or Google offers. You get the feeling that there are actually fewer good apps than crappy ones — and I’m not just talking about freeware. It’s embarrassing.
Here are some examples. In the past few weeks, both Bank of America and Chase pulled their apps from the Windows Store and Windows Phone Store. Microsoft makes a YouTube app, but it doesn’t take advantage of many YouTube features (and Google, which owns YouTube, isn’t about to make a WinRT version).
Search for YouTube apps, and you’ll find acres of bogus offerings. There are no decent WinRT-based Kindle apps; few banks or credit cards have Windows Store apps; American Airlines dropped out — and others such as Southwest, Delta, and Virgin Air never posted a Windows Store app. SnapChat’s a no-show.
You can’t use a Starbucks app to pay for coffee, although you can find plenty of apps that claim to provide info about Starbucks. (They even use the Starbucks logo, although they’re offered by people with names like Naif Alkhaldi, Frenchie25, Savviki and Sherif El Mahdi.)
Microsoft does have one huge leg up on the competition: the enormous base of Windows 7 (and even some XP) users. If the company can put one WinRT API on desktops, laptops, tablets, 2-in-1s, Windows Phones, the Xbox (yes, WinRT is promised for the Xbox), the Raspberry Pi 2, HoloLens, Surface Hub, and heaven knows what else, the potential market is staggering.
Microsoft will succeed if it can honestly market Universal apps as being truly “universal” — i.e., “Buy this app and run it on your laptop, your phone, and your vacuum cleaner.”
Most developers want that type of cross-platform capability. Building a WinRT-based Universal app that runs only on the Metro side of Windows 8 is of dubious value. The same is true for Windows Phone apps, given that platform’s tiny sliver of the smartphone pie. But a high-quality app that runs on all Windows platforms will almost assuredly make a developer money.
Microsoft is headed toward a universal, pan-version structure. Whether and when it will get there is still unknown. But with this latest WinRT API, we should see a bit of that vision materialize.
Can Microsoft pull the RT rabbit outta the hat?
To prod developers into making more and better Universal apps, Microsoft must lead the way. Given the horrendous track record of existing native-Win8 applications, building a substantial offering of high-quality Universal apps is likely a mountainous proposition.
Look at the evidence. Microsoft has taken years to build a touch-first version of Office. Missing the Windows 8 deadline, it kludged together a version to run on Windows RT machines — and only RT systems. We now have outstanding touch-centric Office apps, but they first appeared on Apple iOS, then Android, and now in beta for Windows 10.
Given the company’s focus on the WinRT API platform, you really have to wonder why it’s taken Microsoft so long to get “Universal” Office out the door.
Here’s another pain point: Project Spartan. The current Internet Explorer is a hellacious can of worms, demanding massive security fixes every month or so. Microsoft’s been working on a replacement for IE for years.
Project Spartan is a “Universal” browser that, obviously, uses the WinRT API. With Windows 10’s ability to run Universal apps inside windows on the desktop, Microsoft can finally start the migration away from IE — replacing it with a vastly less buggy and infection-prone Spartan. (Win8’s full-screen Metro version of IE has always been a cumbersome and unintuitive joke.)
It’s taking Microsoft a long time to get Spartan out the door. More than two years into the Windows 10 build cycle, we’ve seen only a few leaked screenshots — underwhelming ones at that — although we’ve been promised that Spartan will be better than IE. Live Spartan code will reportedly show up in some future beta drop of Windows 10, but no one I know has seen it yet.
If it takes Microsoft two years or more to build a basic WinRT-based browser, independent software developers — with significantly less capital and fewer insights into Microsoft code — will have to ask themselves whether building to WinRT is worth the effort.
It’s a helluva good question. We’ll have to see where version 3.0 takes us.
How to customize file and folder views
Windows 7 and 8 lost some useful options for organizing files and folders — features fully supported in XP and Vista. Here’s how to regain similar functionality.
Plus: A query about anti-malware recommendations and a discussion about more problems with updater apps.
Why can’t Win7/8 show files the XP/Vista way?
Reader Stanley Lenci wants to position files manually within his folders and have Windows remember and reuse his custom layout. XP and Vista had that handy capability, but Microsoft dropped it in Win7 and Win8.
- “Prior to the release of Win7, users had the ability to disable file ‘auto arrange’ and randomly set the order of files via drag-and-drop within a folder. The user could close the folder, and when that folder was reopened, it would list those files in the same order as when it was closed. Can I get that feature back? Do you know whether Win10 will restore it?”
Hey, hear that sound? It’s a can of worms being opened! Folder customization is a big topic.
You’re right: Vista is the only current Windows version that offers Auto Arrange and Align to Grid options in Windows Explorer (see Figure 1). To manually arrange Vista folder contents the way you want, all you have to do is deselect both options.
(Vista users can access these settings by right-clicking on an empty spot inside a folder and selecting View.)

Figure 1. Vista's Windows Explorer offers Auto Arrange and Align to Grid options that are missing in Win7/8.
From Windows 7 on, the only Auto Arrange and Align to Grid commands you’ll see are for desktop icons. (Right-click on an empty spot on the desktop and select View.) For files within folders, the two options Auto Arrange and Align to Grid are enabled and active, with no way to turn them off.
But both Windows 7 and 8 have other ways to manage and display folder contents. One of these just might give you the kind of organization you seek.
And if not, there’s an unofficial Registry hack you can use to restore the Auto Arrange and Align to Grid options in Win7’s Explorer.
Let’s start with short summaries of the four file-display options built into Win7 and 8. (I’ll provide links for more information in a moment.) Note: Arrange applies to Library folders; the other three apply more or less everywhere.
- Arrange creates arbitrary visual groupings of files according to criteria you set.
- Sort sequences files according to user-selectable attributes.
- Group creates visual breaks and headings in file listings based on those same attributes.
- View changes the appearance of the files and folders (e.g., file names, icons, thumbnails, and so forth).
These functions are controlled by the attributes and tags (a kind of extended attribute) associated with each file. By mixing and matching various tags, you get extraordinary control over file information and sorting in Windows Explorer/File Explorer (Explorer) — and in some dialog boxes.
I’m sure you’re familiar with Windows’ default tags such as name, date modified, type, and size. But Windows’ Choose Details dialog box lets you select over 300 other tags. And if none of those fits your needs, you can easily create one or more custom tags.
For example, by using built-in and custom tags, you can tell Explorer to sort and display office files according to department or author — or to group your files according to date assigned or date due. You could also have files arranged by management review/approval status.
Most of us have hundreds of digital photos on our personal PCs. Using file tags, you can tell Explorer to sort and/or group those images by camera brand, model, lens type, focal length, shutter speed, and more — basically any information in a file’s metadata.
To see the range of attributes built into Windows, select a folder — Documents or Pictures are good examples — and click View/Sort by in the folder’s toolbar (or right-click on an empty spot and select Sort by). Next, click More; the Choose Details dialog box will appear (see Figure 2). Scroll through the long list of tags and select those you’d like to show up in Explorer.

Figure 2: Win7/8's Choose Details box lets you pick from over 300 tags that help determine how files are sorted, arranged, grouped, and displayed.
Typically, only a few of the 300+ attributes are applicable to a given file or file type. For example, “focal length” and similar image-related attributes don’t make sense for a typical Word document. Those attributes simply don’t exist in the document’s metadata. (You can view a file’s metadata fields by right-clicking the file and selecting Properties/Details.)
Selecting an unused or empty attribute is harmless. Feel free to experiment; if there’s no data for a particular attribute, you’ll get just an empty column in Explorer — or similarly benign effects in sort, group, and arrange operations. Just deselect the empty attribute to remove it from the display.
If you don’t see a usable attribute, you can add a custom tag in the file’s Tag attribute. (This is similar to adding tags to images in a photo editor.)
Figure 3 is a simple demonstration of grouping images with custom tags. I used four custom tags: “Demonstration tag 1,” “Demonstration tag 2,” and so on. I added one of these tags (in no particular order) to eight separate photos scattered across several different folders.
Next, I had Explorer arrange the files based on my custom tags. As Figure 3 shows, it neatly grouped and sequenced them all in one window, disregarding file name, type, or location.

Figure 3. Selecting Arrange by: Tag (highlighted) lets you display files in an order of your choosing.
This is worth restating: Figure 3 shows a purely visual arrangement of the files — no files have been moved from their original folders, renamed, or changed in any other way. Explorer is simply arranging the display to give me easy access to the files that carry my custom tags.
For specifics on using Windows’ built-in file and folder customizations, see the Microsoft page, “Arrange, sort, or group your files.” (That page specifically discusses Windows 7, but the process in Win8 is very similar.)
For information on setting up custom tags for the file types that allow it, see the Microsoft page, “Add tags or other properties to a file.” (The page references Vista, but the process is similar in Win7 and 8.) Another page, “Tag pictures so they’re easier to find,” gives details specifically for photos. But the same concepts can be applied to other taggable file types.
Again, the Arrange by Tag option is limited to Win7/8 libraries. For more information on using libraries, see the March 10, 2011, Top Story, “Make the most of Windows 7’s Libraries,” and the March 25, 2010, LangaList Plus column, “Tips on working within Windows 7’s Libraries.” That information also applies to Windows 8.
Microsoft Support article 812003, “How to modify your folder view settings or to customize a folder,” is an older article, but it discusses still-used techniques for creating custom icons and folder pictures or thumbnails. It also covers ways to alter the templates that Windows uses to display information about a folder’s contents.
As you can see, this topic is complex; there’s a lot to digest.
If you’d like a simpler approach, or if you can’t find any way to make the many arrange/sort/group/view options work to your satisfaction, there’s the Win7-specific Registry hack. It might restore Auto Arrange and Align to Grid to Windows Explorer.
The hack worked in my tests, but I must offer some warnings. The hack is unofficial and unsupported; it also runs counter to the direction Microsoft is taking Windows (i.e., the four built-in folder customizations). In my experience, it’s generally not good practice to use hacks to restore deprecated or phased-out Windows functions. There’s no way to know what the unintended consequences might be, further down the road. You could be setting yourself up for trouble.
But if you’re feeling adventurous and want to try, make a complete system image or full backup and then try the hacks listed in the WinHelpOnline article, “How to disable Auto Arrange in folders in Windows 7,” or the Windows SevenForums article, “Windows Explorer Auto Arrange — Disable.”
Why don’t you recommend [X] anti-malware tool?
John Osborne’s note specifically asks about the SpyHunter software, but it’s representative of many letters Windows Secrets receives about anti-malware recommendations.
- “I am using and have used several different antivirus/malware programs, but none of them stopped and removed the malware caught by SpyHunter. However, I don’t see SpyHunter reviewed or mentioned in magazines, newsletters, and so forth. I assume it’s a legitimate program to use; just wondering why it doesn’t get more attention.”
There are several reasons why any given security tool might not be mentioned frequently — or at all.
To start, there are hundreds of anti-malware tools offered — far too many to test and rate.
Also, not all tools are created equal. SpyHunter, for example, currently garners an extremely unimpressive one-star (out of five) user rating at Download.com and a tepid 2.4 out of 5.0 at Softpedia. Other popular download sites such as MajorGeeks used to carry SpyHunter but seem to have dropped it. With so many highly rated tools available, there’s no particular reason to focus on those with low user-satisfaction ratings.
Here’s another problem. You can’t truly test-drive SpyHunter. Although you can scan your PC at no charge, you have to pay to actually remove any malware. I’m all in favor of paying for the tools you use — I upgrade to the Pro/paid version of any tool I keep on my PC. But some AV tools that require payment before they’ll remove malware have a vested interest in finding infections. They might claim to find trouble that doesn’t really exist, in order to scare you into purchasing the product (or making you feel good about your purchase).
Never having used SpyHunter, I can’t say whether it fits into that group. But I have seen a number of other AV apps that use scare tactics. I discussed this issue in the two-part Top Story, “The Windows Maintenance Challenge” (Aug. 14 and Aug. 28, 2014).
I could go on, but I assume you get the idea. Again, with so many good tools out there, there’s no particular reason to settle on tools with low user ratings or that raise questions about their operation or motives.
That said, if SpyHunter is working for you, great! That’s all that really matters.
By the way, for a discussion of free and paid anti-malware tools, and for a three-part anti-malware strategy that should keep just about any PC malware-free, see the March 12 LangaList Plus item, “Preventing anti-malware software conflicts.”
Another problem with software updater apps
After reading the March 5 LangaList Plus item, “A free, reader-recommended application updater,” Brian Nicol wrote this:
- “It’s worth pointing out another pitfall of these updaters.
“It occurs where some software vendors issue their older products on a free-to-use basis, while the newest version of the product is available only on payment of an upgrade or new-license fee.
“It also occurs with software bundled with hardware products such as scanners and optical drives. If you allow an update, you could find yourself being asked to pay for a new/upgrade license.
“You then have the trouble of uninstalling the update and finding the media/download to reinstall the free older version — which you were perfectly happy with.
“This is primarily why I never use those updater applications anymore.”
I agree, Brian: Newer versions aren’t always better than older ones, and some new versions actually can make things worse.
When it comes to upgrades and updates, my mantra remains: “If it ain’t broke, don’t fix it.”
The many ways PCs have become vulnerable
From nation states pursuing cyber warfare, to the growth of the “Internet of Things,” to smarter mobile devices, to ever-more-sophisticated malware, the breadth and number of malicious intrusions seems to know no bounds.
That’s what you can conclude from recent incidents such as Superfish and from the findings of several new security reports.
Recently, the Royal Bank of Canada (RBC) issued a report to its clients (of which I am one) who are considering investments in security firms. The report, “A deeper look at key cyber-security trends,” is a summary of studies published by various security firms. It shows the extent to which we underestimate cyber crimes against consumers, businesses, and government agencies. Despite the efforts of a growing cadre of vigilant security watchdogs — and our use of ever-improving anti-malware software — malicious intrusions are still increasing. The report’s conclusion: There’s no single silver bullet to protect against all cyber threats.
(Because the RBC report was produced exclusively for customers, its investment recommendations are proprietary information and are not included in this article. But the bank’s reasons for considering these investments were insightful and became the genesis of the article.)
Data-breach headlines becoming all too common
A report of a massive corporate data breach was once a rarity; now they seem to come in multiples and with the regularity of the tides — each apparently more massive than the last. When Adobe and Target got hit in 2013, we thought the two break-ins were as large as they could get. But then came intrusions at Adobe, Home Depot, JPMorgan Chase, Sony, the U.S. Postal Service, and — the biggest known attack to date — Anthem Blue Cross.
Those are the breaches we know about — well after the damage was done to our personal information, financial and health records, and other sensitive data. But according to the Price Waterhouse Coopers (PWC) report, “The global state of information security survey: 2015 results by industry,” nearly 75 percent of survey respondents experienced some form of security breach within the past year, based on data provided by over 9,700 IT and security professionals. The report went on to state that the number of detected intrusions in 2014 increased nearly 50 percent from the previous year — about 42.8 million incidents detected just by those who contributed to the survey. We never heard about these breaches, ostensibly because they were contained before significant damage was done.
As hackers increasingly targeted corporations, the U.S. Congress responded with what it does best: it held hearings. Late last year, at a hearing before the House Permanent Select Committee on Intelligence, National Security Agency Director Admiral Michael Rogers stated that a major cyber attack was on the horizon. “It’s only a matter of when — not if,” he testified (C-SPAN video).
Cyber attacks can and do come from all sides
Long gone are the days when most network intrusions were the relatively benign hobbies of teenagers, messing around in their parents’ basement. Most of the large-scale breaches are now perpetrated by cyber gangs and nation states — possibly working together in some cases. But according to the PWC survey contributors, most of the detected incidents were insider crimes initiated by employees.
Nevertheless, the survey also showed an 86 percent increase in attempted or successful attacks that apparently came from nation states. More alarming, however, was the finding by security firm Solutionary: in a single quarter of 2014, 56 percent of the malware it routinely captured via sensors and other means was hosted in the U.S. — and half of that appeared to originate at 10 Internet service and hosting providers, including Google, Akamai, Amazon Web Services, and GoDaddy, among others.
For PC users who run up-to-date anti-malware software, the greatest threat remains so-called zero-day exploits — newly revealed vulnerabilities in Windows, browsers, and applications that might be rapidly adopted by malicious hackers. Security-software vendors might have just hours to respond to active attacks. (Hackers can also be extremely clever at adapting and/or disguising older exploits.)
Many malware attacks — both personal and corporate — involve social engineering, a clever term for tricking browsers or email users into clicking malicious links or attachments. Other forms of attack simply take advantage of security loopholes that come with new PCs. Just ask Lenovo.
Even personal-computer vendors can be duped
Like other PC companies, Lenovo (currently the top manufacturer) preloads an ample supply of revenue-producing crapware on its personal systems. Last year it loaded Superfish — a better name might have been Superphish — on selected models (more info).
Ostensibly an adware “shopping” app, the preinstalled version of Superfish had some serious security issues — primarily a self-assigning security certificate that intercepted all encrypted Internet traffic and used the same decryption key for all systems (more info). The flaw could be easily exploited by cyber criminals to harvest Internet user names and passwords.
Reportedly, the source of the suspect certificates was Komodia, an Israeli company that specializes in software that lets users control TCP/IP sessions (site). According to an eWeek article, the issues with Komodia’s tools go well beyond Superfish.
Lenovo obviously didn’t carefully vet Superfish before installing it on its new systems. Reportedly, the company was just as surprised by the Superfish vulnerability as everyone else. But that’s really no excuse for exposing thousands of customers to cyber attacks. (Lenovo has posted instructions and a tool for removing the app.)
Mostly, the Superfish incident serves as yet another unnerving example of the many ways malware can infest a computer.
More Net connections, more hacking opportunities
One of the popular themes today is the “Internet of Things.” It suggests a world in which nearly all digital devices are connected to the Net. And as the number of networked devices grows, it follows that so, too, will the opportunities for malware attacks.
One category getting more attention — both from hackers and security experts — is dedicated devices, including home thermostats, baby monitors, smart light bulbs, HDTVs, cars, and more. That smartphone app that lets you remotely control your home heating might also give a cyber thief access to all devices on your home network. A recent 60 Minutes report demonstrated how easy it was to hack a car’s Internet-connected computer, giving the hacker remote control over brakes and accelerator. A Daily Mail story relates how new TVs might be spying on you for advertisers.
In fact, a recent HP study (PDF download) of 10 Internet-connected devices found that seven contained security holes, eight didn’t require strong passwords, and nine collected at least one piece of personal information.
Cisco Systems, apparently another strong proponent of ubiquitous Internet connections, predicted that wireless sensors will soon be found on things such as pacemakers, shoes, clothing, cattle, and nearly all home appliances.
Clearly, tight security must be built into all these products. Ensuring that sufficient security happens will probably come down to us, the consumers. When considering a new Net-connected product, we must research the information it gathers, what it’s used for, and which security features are included.
U.S. government takes protective action — slowly
In 2013, the Federal Bureau of Investigation notified 3,000 companies that they’d been victims of cyber attacks. Surprisingly, the companies didn’t know they’d been breached until the FBI told them. Following this disclosure, President Obama issued an executive order to improve cyber security. Then the Senate Intelligence Committee approved a bill increasing the amount of information shared between the public and private sectors on cyber-security risks. As of now, that’s as far as improved cyber security has proceeded.
The president took his own initiative. Back in 2009, he accepted the recommendations of his Cyberspace Policy Review committee. As noted in the published introduction to the Comprehensive National Cybersecurity Initiative, the goal was “to ensure an organized and unified response to future cyber incidents; strengthen public/private partnerships to find technology solutions that ensure U.S. security and prosperity; invest in the cutting-edge research and development necessary for the innovation and discovery to meet the digital challenges of our time; and begin a campaign to promote cybersecurity awareness and digital literacy from our boardrooms to our classrooms and begin to build the digital workforce of the 21st century.”
The president has also included some U.S. $14 billion to boost U.S. cyber-security defenses, and he also called for a new national standard: companies must publicly disclose data breaches within 30 days of discovery. That would allow individuals, government agencies, and companies to respond more quickly to threats and intrusions.
At this point, it’s difficult to know whether those efforts have truly enhanced our cyber security.
Stopping infections requires a combined approach
Hackers are constantly finding new and clever ways to deliver malware. Security companies are developing equally clever ways of keeping infections at bay. They call their defense system the “kill chain,” as shown in a Palo Alto Networks chart. Typically, attackers must complete nine steps for a successful exploit, and each of those steps is an opportunity for stopping an attack.
We all know that crime happens everywhere — even in the safest neighborhoods — and we take precautions. And most of us who use computers are well aware of the dangers of going online. Just as we lock doors and windows, we must secure our access to the Web.
As has been discussed many times in Windows Secrets, anti-malware software and strong passwords are the first line of defense. But when offered, two-step verification is a solid way to thwart all but the most determined hackers.
As noted in the RBC report, our mobile devices are the next frontier for malicious hacking — soon to follow will be TVs, home-control devices, and more. We now need to take the time to ensure that all our Internet-connected devices are secure.
Updates can cause as well as fix trouble
When Lounge member IreneLinda posted in the Graphics/Multimedia forum about Windows Live Movie Maker’s frequent crashes, she was frustrated.
She had already toiled through several efforts on her own to find and fix the cause of the problem.
Thanks to help in the forum plus her own arsenal of expertise, she finally solved her broken-app problem. But it was not before remembering that patches are software downloads that can sometimes mess up, rather than improve, a system’s environment.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right into today’s discussions in the Lounge.
A tour through the powerful Autoruns utility
Among the advanced tools offered on Microsoft’s Windows Sysinternals site is Autoruns, an app that reveals extensive information about programs that start automatically.
An enhanced version of Windows’ System Configuration (msconfig) applet, Autoruns can help you find malware, improve system performance, and remove obsolete bits of leftover code.
As with Process Explorer, which I reviewed in the Feb. 5 and Feb. 12 Best Utilities columns, Autoruns is a deep and complex tool. It’s most suitable for advanced Windows users. If you’ve used Process Explorer, Autoruns will look somewhat familiar. But it has an important difference: instead of showing running processes, it provides detailed information on all programs and drivers that run automatically — and perhaps invisibly — on system boot or when launched by an application.
A word of warning. As always when making significant changes to your system — especially with tools that go deep into Windows — start by making a complete backup of your system. Should you make a bad decision and delete or change something vital, you can then make a full recovery.
(As with the Process Explorer story, my thanks to Tektegrity’s [site] Joshua Erdman for help with understanding Autoruns.)
Downloading and getting started with Autoruns
Start by opening the Sysinternals Autoruns page in your browser and clicking the download link. The tool is small and should download in a few seconds as a ZIP file. Next, click the downloaded file to unpack it. Note that the site has links to two helpful videos for using the utility.
In the unpacked Autoruns folder (typically in your Downloads folder), click the autoruns.exe file to start the app. Note: The second EXE file in the folder, Autorunsc, is a command-line version that includes an extensive set of switches listed on the Sysinternals page (more on this below). And, like other Sysinternals tools, Autoruns can also be launched directly from its online page.
When Autoruns opens, the first thing you’ll notice is its many tabs (see Figure 1). Autoruns typically starts on the Everything tab, which shows all executables. The tool gives you a quick way to control automatic-application startups. If you don’t want an entry to start when you boot, simply uncheck its entry to disable it. If you don’t want the item to execute at all, a better choice is to delete it (more on that below).

Figure 1. Autoruns is an advanced diagnostics tool, as its many tabs indicate.
Note that Autoruns might not load with full administrator privileges, which limits what you can do with it. To solve this problem, select File in the toolbar and then click Run as Administrator — or launch the command-line version of the utility with the -e option.
Finding and removing potential malware
If you’re hunting down a possible virus problem, you’ll want to become familiar with these tabs: Everything, Logon, Explorer, Scheduled Tasks, Services, and Drivers.
When an executable isn’t digitally signed, there typically won’t be a publisher listed. (Digital signing helps ensure that code has not been altered or corrupted — often by malware.) If 64-bit software isn’t signed, the user will get a security warning when launching it.
Obviously, it’s significantly more difficult for a virus to spread if it first has to ask the user’s permission. But in most cases, that doesn’t happen. Successful infections typically occur because a user is tricked into clicking a malicious link or webpage element. (An exploit that compromises a legitimate site is sometimes referred to as a watering-hole attack — the malicious code is planted in a part of the site that will likely get clicks.)
For example, let’s say — purely hypothetically — that the tools section of the Sears site was hacked. When I click a link to get more information about an interesting new wrench, a message pops up, stating: “Sears needs your permission to install an app in order to improve your browsing experience.” When I click OK, the malicious code grants itself a trusted certificate (though typically not correctly signed by a trusted authority) and installs itself on my computer. The code never again has to ask my permission to run.
Autoruns can reveal these improperly signed, auto-running bits of code. In Figure 2, you’ll see an entry highlighted in pink. Note that there’s no publisher and it hasn’t been signed. This could indicate a virus. When examining these entries, you should note the directory path and install date — in this case, 2006. So it’s most likely leftover code and not a recently installed virus. (I assume my anti-malware application would have noted it by this time.)

Figure 2. Unsigned or improperly signed code is highlighted in pink. These marked entries could indicate a virus.
To find out just what an unknown file does, right-click it and select Search Online from the pop-up menu. That option opens a search in your browser. The menu also gives several other options for examining or disabling an auto-run file — including Delete, Copy, Jump to Entry (which will take you to Regedit), Jump to Image, Process Explorer, and Properties.
Another technique for seeing whether the file is legitimate is to visit Jotti.org. Use the site’s File to scan box to point to the suspect file; Jotti.org will then run the file past 22 different virus-scanning programs.
Finding the detritus of old applications
Cleaning up old applications is another use for Autoruns. When you uninstall an app, you have no guarantee that the software has been completely removed. There could be remnant code, DLLs, and other files that still load and run.
If this happens, you’ll see an entry highlighted in yellow (see Figure 3) and possibly a message such as “File not found.” This is a leftover entry in the Windows Registry, and it can be safely deleted.

Figure 3. Leftover Registry entries are highlighted in yellow.
Skype is a great example of an app that might not fully uninstall. Microsoft’s communications app hooks into many things in Windows. For instance, look at a contact’s phone number in Outlook, and you’ll see that it’s underlined. If you click the number, Skype opens and makes a call. That feature is enabled by a Skype/Outlook plugin. Skype also needs to hook into your PC’s sound and — possibly — video systems to handle calls.
Skype’s impact on a computer can be quite deep. For example, take a snapshot of a new computer’s configuration by using Autoruns File/Save and saving the output as a text or Autoruns .arn file. Install Skype and then uninstall it. Take another configuration snapshot and compare them, using Autoruns’ File/Compare option. Chances are good the two configurations will be markedly different, with files, registry entries, and more left behind.
Installing and uninstalling applications and drivers can, over time, leave other leftover bits that might slow down your computer. (Windows tries to load these remnants at startup and then moves on, creating unnecessary system overhead.) The Autoruns Driver tab displays a list of automatically loaded drivers, which you can use to find executables you no longer need.
For example, a while ago I bought a used Lenovo ThinkPad. When I looked under the Autoruns Drivers tab, I found several files for a Brother peripheral (Figure 4), a printer I’ve never used. I removed them by right-clicking the entries and selecting Delete.

Figure 4. You can use Autoruns to remove unneeded drivers that run on system startup.
If you’re unsure whether to remove or disable an auto-running file, another option is to use IObit Uninstaller (site), which does a deep scan for application remnants and gives you the option of removing any it finds.
(While I was discussing Autoruns with Joshua Erdman, he recommended another third-party utility for hard-drive cleanups. WinDirStat [site] inventories your entire storage system and gives you cleanup options.)
Running Autoruns from a command-line prompt
As noted above, the Autoruns.zip file includes two executables: Autoruns.exe and Autorunsc.exe, the command-line version of the tool.
If you simply double-click the Autorunsc.exe file in Explorer, it’ll open a command window, run for a few seconds, and then disappear. Instead, start by copying or moving autorunsc.exe to your root directory (typically C:\). That will make it easy to enter the command to run the tool. For example, enter C:\autorunsc and add any switches you need. If you need a list of switch options, enter c:\ autorunsc /? (see Figure 5) at the command prompt. (Again, that information is also on the Sysinternals Autoruns page). Some of the switches simply duplicate the tabs in the graphical version of Autoruns.
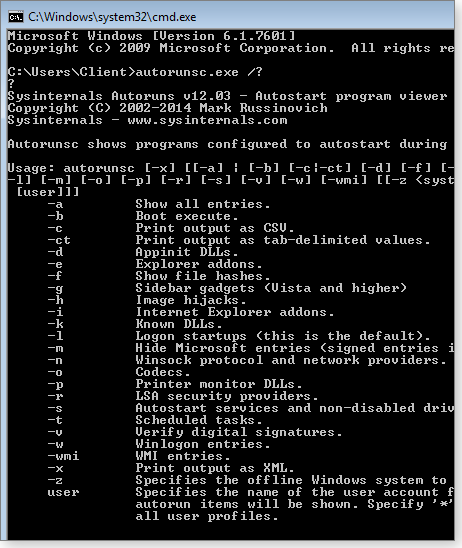
Figure 5. The command-line Autorunsc includes a long list of options.
Another tool for delving deep into Windows
Autoruns and Process Explorer give you two ways to look under the Windows hood. Process Explorer provides a list of running processes. Think of it as a more powerful version of Task Manager. Autoruns looks at Windows from another angle: the auto-loading apps entered into the Windows Registry, Task Scheduler, and elsewhere. Think of Autoruns as a powerful combination of Regedit and System Configuration.
I recommend that anyone who maintains PCs — either just for personal use or for others — take a tour though these tools. If you think you might want to add these utilities to your Windows toolkit, I also recommend taking the time to view the related Sysinternals instruction videos and any other online sources you can find. (There are surprisingly few.) Start with “Malware hunting with Mark Russinovich and the Sysinternals Tools” (TechEd site) and the “Case of the Unexplained: Troubleshooting with Mark Russinovich” (site).
Once you understand how they work, both tools can help track down hidden malware and obsolete files that are dragging down your system.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
A CVE-MITRE-CISA-CNA Extravaganza
by
Nibbled To Death By Ducks
3 hours, 24 minutes ago -
Sometimes I wonder about these bots
by
Susan Bradley
10 hours, 17 minutes ago -
Does windows update component store “self heal”?
by
Mike Cross
16 hours, 21 minutes ago -
Windows 11 Insider Preview build 27858 released to Canary
by
joep517
17 hours, 22 minutes ago -
Pwn2Own Berlin 2025: Day One Results
by
Alex5723
16 hours, 47 minutes ago -
Windows 10 might repeatedly display the BitLocker recovery screen at startup
by
Susan Bradley
13 hours, 17 minutes ago -
Windows 11 Insider Preview Build 22631.5409 (23H2) released to Release Preview
by
joep517
20 hours, 3 minutes ago -
Windows 10 Build 19045.5912 (22H2) to Release Preview Channel
by
joep517
20 hours, 5 minutes ago -
Kevin Beaumont on Microsoft Recall
by
Susan Bradley
8 hours, 39 minutes ago -
The Surface Laptop Studio 2 is no longer being manufactured
by
Alex5723
1 day, 4 hours ago -
0Patch, where to begin
by
cassel23
22 hours, 14 minutes ago -
CFPB Quietly Kills Rule to Shield Americans From Data Brokers
by
Alex5723
1 day, 17 hours ago -
89 million Steam account details just got leaked,
by
Alex5723
1 day, 5 hours ago -
KB5058405: Linux – Windows dual boot SBAT bug, resolved with May 2025 update
by
Alex5723
2 days, 2 hours ago -
A Validation (were one needed) of Prudent Patching
by
Nibbled To Death By Ducks
1 day, 17 hours ago -
Master Patch Listing for May 13, 2025
by
Susan Bradley
1 day, 4 hours ago -
Installer program can’t read my registry
by
Peobody
1 hour, 27 minutes ago -
How to keep Outlook (new) in off position for Windows 11
by
EspressoWillie
1 day, 15 hours ago -
Intel : CVE-2024-45332, CVE-2024-43420, CVE-2025-20623
by
Alex5723
1 day, 22 hours ago -
False error message from eMClient
by
WSSebastian42
2 days, 13 hours ago -
Awoke to a rebooted Mac (crashed?)
by
rebop2020
2 days, 22 hours ago -
Office 2021 Perpetual for Mac
by
rebop2020
2 days, 23 hours ago -
AutoSave is for Microsoft, not for you
by
Will Fastie
2 hours, 23 minutes ago -
Difface : Reconstruction of 3D Human Facial Images from DNA Sequence
by
Alex5723
3 days, 3 hours ago -
Seven things we learned from WhatsApp vs. NSO Group spyware lawsuit
by
Alex5723
10 hours, 45 minutes ago -
Outdated Laptop
by
jdamkeene
3 days, 8 hours ago -
Updating Keepass2Android
by
CBFPD-Chief115
3 days, 14 hours ago -
Another big Microsoft layoff
by
Charlie
3 days, 13 hours ago -
PowerShell to detect NPU – Testers Needed
by
RetiredGeek
15 hours, 58 minutes ago -
May 2025 updates are out
by
Susan Bradley
17 hours, 40 minutes ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

