
|
There are isolated problems with current patches, but they are well-known and documented on this site. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Mobile security: Apps to protect Android devices
In this issue
- TOP STORY: Mobile security: Apps to protect Android devices
- LOUNGE LIFE: Word 2003 toolbars lost and recovered
- LANGALIST PLUS: Problems with Win8's custom recovery image
- PATCH WATCH: New attacks on Windows' secondary components
- WACKY WEB WEEK: We can supply you with binder twine
Mobile security: Apps to protect Android devices
There are hundreds of free and paid security apps for Android phones and tablets. But many of those offerings are of uncertain quality.
Here’s a sampling of some of the best software for keeping Android devices free of malware, managing passwords, locking up your data, and more.
Android needs third-party security apps
If you have an Android phone or tablet, there’s good news and bad news.
The good news: You’ve picked the world’s best-selling mobile operating system. Something like 70 percent of all new phones and tablets run Google’s OS. That’s a strong incentive for software developers to build cool applications for the platform.
The bad news: Android’s open architecture and popularity have made it a favorite target for malicious hackers, thieves, and other criminals.
Android’s built-in security features have never been strong, and even the latest version (4.4.4, as I write this) offers only modest safeguards for your personal data and communications. For that reason, all Android devices need third-party security apps in order to be safe. (Virtually no operating system, by itself, is safe from malicious hacking.)
Fortunately, there are plenty of Android security tools to choose from. The Google Play Store has all manner of free and commercial apps. Note, however, that some are junk — amateurish software that could cause crashes, hangs, slowdowns, or other problems.
Other tools seem to work fine — until you look at them more closely. Take, for example, some “free” virtual private networking (VPN) apps, which provide some Web-browsing anonymity (especially on public Wi-Fi) by routing your data through the VPN provider’s servers. If the service is free, how does the provider pay the bills for running the servers and buying Internet bandwidth? How does the provider keep the lights lit? A cautious person might suspect that the company is mining user data.
That said, there are many reputable companies with excellent Android security products. Some are familiar and well-respected names you might recognize from the Windows world, while others are relative newcomers who develop products exclusively for mobile operating systems.
Below, I’ll provide summaries of well-regarded security apps — some paid, others free — in five essential categories:
- Antivirus/anti-malware suites
- Password management and encryption
- Lost or stolen device recovery
- VPNs
- Secure file-wiping (to delete personal data when you’re selling or trading in your device)
(Note: The following information applies equally to all portable Android-based devices, including tablets. But for brevity, I’ll use “phone” throughout the rest of the article.)
Security suites: The absolutely must-have apps
The cornerstone of Android safety is a good security suite from a reputable vendor. Even a single, well-designed security app can provide coverage against a wide range of attacks and dangers.
Lookout Security & Antivirus (Google Play page; publisher’s website) is a typical example of a reputable suite in the security category. It offers a comprehensive selection of tools (see Figure 1) — some free and others paid. (I’ll list other brands in a moment.)
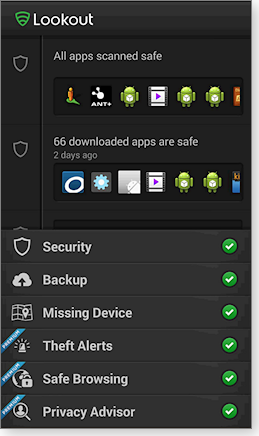
Figure 1. Lookout Security & Antivirus offers basic security features for free; additional features are in its paid version.
Lookout’s free version provides:
- Anti-malware: It gives automatic, always-on protection from viruses, adware, spyware, and other types of malware.
-
Lost/stolen phone recovery tools: A map shows you the phone’s location (see Figure 2), viewable via a free, private account on the Lookout website.
The Scream option sounds a loud alarm, even if the sound was turned off. The alarm might scare a thief into abandoning the phone, but it can also help in more mundane situations such as when you simply misplace the phone at home or the office. The sound will lead you to the phone’s location.

Figure 2. Lookout can help you locate and recover a phone, whether it's been stolen or just lost in the sofa cushions.
- Signal flare: This option saves your phone’s location when the battery is about to run out. It might help you find the phone once it’s gone dead.
- Automatic backups: Your contacts are saved to your private account on the Lookout website. You can download the contacts to your PC or to a new or secondary device.
- Multiple device support: The free account is limited to two devices.
Lookout’s paid version adds:
-
Expanded Theft Alert features: You can have the phone send an email to your PC in the following circumstances:
1. The phone’s unlock passcode is incorrectly entered more than three times in a row.
2. The SIM card is removed.
3. Airplane mode is enabled or the device is turned off (two tricks thieves might try to avoid detection), or a thief tinkers with the phone’s Device Administrator mode.
Lookout’s notification email includes a map of the phone’s location when the Theft Alert was generated plus a theftie — a photo of the person holding the phone at the time the alert was triggered, taken automatically with the phone’s built-in camera. The same Theft Alert information is posted on your private account on the Lookout website.
- Privacy Advisor: This lets you manage the permissions and personal data that each app on the phone can access.
- Remote lock and wipe: In the event the phone is stolen and not recoverable, you can remotely lock it and erase your personal data.
- Safe Browsing: This option alerts you when you visit websites known to harbor malware or other security threats.
- Photo and call-history backups: Use this tool to automatically clone photos and call data to your private Lookout account.
- Multiple device support: This lets you manage up to three devices from a single Lookout account.
You can test-drive Lookout’s paid version for up to two weeks at no cost; after that, it’s a modest U.S. $3 per month or $30 per year.
Again, Lookout Security & Antivirus is just one example of a typical, comprehensive, Android security suite. There are other suites with similar features.
For example, Avast Mobile Security & Antivirus (Google Play page; publisher’s site) doesn’t take “thefties” of would-be phone thieves, but its paid version does offer Geo-Fencing — the phone performs a specified action (lock, siren, send location, and so forth) if it passes outside a perimeter you’ve established, such as a set distance from your table in a café. It also offers App Lock, which lets you passcode- or gesture-protect access to specified apps.
Avast Mobile Security & Antivirus is available in both free and paid versions; after a 30-day free trial, the premium edition costs $2 per month or $15 per year.
Bitdefender is another name that might be familiar to Windows users. Its Mobile Security & Antivirus (Google Play page; publisher’s site) is also available in free and paid versions. Its features are similar to Avast’s, but it tries to differentiate itself with aggressive pricing. After a two-week free trial, the paid version costs only $1 per month or $10 per year.
You can download Kaspersky Internet Security (Google Play page; publisher’s site) for free. You must register with Kaspersky for the paid edition’s 30-day free trial; it’s $15 per year to keep. Two advanced features are Call & Text Filter, which helps block unwanted calls and texts, and a theftie option similar to Lookout’s; it can automatically take a photo of a would-be thief.
Again, you can find many more security suites, apps, and options by visiting the Google Play Store and using the search string “security” or “security suite.”
Password management and data encryption
It’s likely you’ve already been affected by one or more of the recent and massive corporate hacking incidents such as the data thefts at Adobe, Target, eBay, and others.
One of the best ways to protect yourself against these increasingly common hacks is to use a unique password for every site. (See the Oct. 17, 2013, Top Story, “Protect yourself from the next big data breach.”)
Remembering potentially dozens of passwords sounds burdensome, especially on a phone or tablet where typing can be difficult. But password-management software makes it vastly easier. The software does the hard lifting for you, remembering all passwords and storing them in a securely encrypted database.
If you’re using password-management software on your PC, there’s a good chance you can find an Android equivalent. That can greatly simplify setup and use because the software will already be familiar. It might even be able to access and use the database of passwords on your PC, saving you from the chore of re-entering everything again.
For example, RoboForm (possibly the world’s most popular password manager) has a free Android version (Google Play page; publisher’s site) that connects with an existing desktop RoboForm Everywhere account ($10 per year). Android’s built-in browser (a version of Chrome) doesn’t work with third-party password apps, so RoboForm comes with its own mini-browser that you can use to sign in to password-protected sites. You can also use the RoboForm app with Android editions for Dolphin or Firefox.
Similarly, there are two free Android versions of the popular, open-source, desktop Keepass Password Safe. One is called Keepass2Android Password Safe (Google Play page; publisher’s site) and is shown in Figure 3.
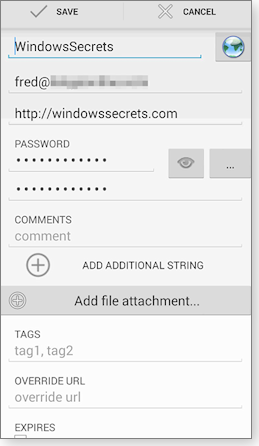
Figure 3. As with other password managers, enter a site's password once and Keepass2Android will then remember it for you.
The other Android version of Keepass is called KeepassDroid (Google Play page; publisher’s site). Both versions operate much like the desktop version of KeePass, and they share the same database format.
If desktop commonality isn’t an issue for you, the free/donationware, open-source Universal Password Manager (Google Play page; publisher’s site) might be of interest.
You can find many similar apps by using the search terms “password manage” and “manage password” (though seemingly similar, the two searches yield slightly different results).
Apps for recovering lost or stolen phones
As already mentioned, many of the best Android security suites (Lookout, Avast, Bitdefender, Kaspersky, and so forth) come with robust tools that can help you find and recover a lost or stolen phone — typically by sending you a map of the phone’s location, letting you wipe or lock the phone, and even snapping a photo of the thief.
But most versions of Android also include basic, built-in features that can reconnect you with your phone — or wipe it clean. For example, Android 4.1 and higher includes the Device Manager app (see Figure 4) that can, when linked to your Google account, locate your phone on a map and let you remotely ring, lock, or erase it. The specific details are explained in the Android Device Manager support page.

Figure 4. Android's built-in Device Manager lets you locate, ring, lock, or erase a lost phone remotely from your Google account running on another device (shown above).
Older versions of Android — 2.2 and higher — allow for basic remote wiping, as explained on the Remote Wipe a Mobile Device support page.
Those tools are better than nothing, but third-party apps such as the following can do more — for example, take photos of a would-be thief. Visit the associated websites for full details.
- Where’s My Droid (Google Play page; publisher’s site) offers basic capabilities for free (see Figure 5) plus extended features — such as remote lock — for $4.

Figure 5. Where's My Droid offers good lost device–recovery features, including a GPS-based locator.
- AndroidLost (Google Play page; publisher’s site) is completely free, though the program’s author accepts voluntary donations.
- Locate My Droid (Google Play page; publisher’s site) also is free, with voluntary donations accepted.
Virtual private network apps for Android
A virtual private network (VPN) connection can let your phone operate securely, privately, and anonymously from any site — even from public hotspots in coffee shops, airports, restaurants, hotels, and so on.
A VPN uses encryption to establish a secure, private channel between your PC and the VPN provider’s server. That server, in turn, then connects to whatever website or other server you want to reach (see Wikipedia’s VPN article).
But you really want to trust the VPN provider, because it’ll potentially have access to your unencrypted data. Most legitimate VPN services recover their costs by charging a modest fee based on your data usage — or by displaying ads as you use their service. I think this is an important consideration, because a provider with a viable revenue stream should never feel tempted to mine your data stream for usernames, passwords, credit-card numbers, and so on.
Here are some of the better-regarded Android VPN services and their associated client software:
- VyprVPN for Android (Google Play page; publisher’s site) — three-day free trial; $7–$20 per month thereafter, depending on plan details
- ExpressVPN (Google Play page; publisher’s site) — one-day free trial; $8–$13 per month thereafter
- IPVanish (Google Play page; publisher’s site) — one-week, money-back guarantee; $5–$8 per month thereafter
- Hotspot Shield: VPN Proxy WiFi (Google Play page; publisher’s site) — free, ad-supported version; ad-free Elite version, $30 per year.
Apps for thoroughly sanitizing Android devices
No, this is not dipping your phone into a glass of Lysol. When it’s time to sell or trade in your phone, all recent-vintage Android-based models let you easily restore the original factory configuration. That makes it harder — but not impossible — for the next user to recover traces of your data left behind in the phone’s flash memory.
In fact, completely erasing flash memory is technically difficult and could require special tools and extra steps. (For more info, see the Sept. 13, 2012, Top Story, “Rethinking the process of hard-drive sanitizing.”)
If your phone uses a removable SD memory card, scrubbing it is relatively easy. The best bet is to remove the card, connect it to your PC, and use the tools described in the aforementioned Top Story. (Or, if you can, simply keep the SD card, possibly reusing it in some other device you own.)
But when the flash memory is built into the phone, it’s harder to get at — and harder to erase. These apps can help:
- SaniDroid (Google Play page; publisher’s site) — $1

Figure 6. Special-purpose apps such as Sanidroid can help remove lingering traces of personal data from a phone you're selling or trading in.
- iShredder 3 (Google Play page; publisher’s site) — free and Pro versions ($3.50); see site for details
- Secure Wipe (Google Play page; publisher’s site) — free
- SHREDroid (Google Play page; publisher’s site) — free (doesn’t work on Motorola devices)
- File Shredder (Google Play page; publisher’s site) — free (works only on a file-and-folder basis; reportedly, whole-phone erasure in a future paid-for version)
Security tools can help keep you safe
Mobile devices such as phones and tablets are wonderfully convenient, but they also pose huge security risks. Not only are these devices subject to the same kind of malware and hacking that your Windows PC must cope with, they’re also far more likely to be lost or stolen than your desktop or laptop system.
But with one good tool from each of the categories above, your portable Android device can be as safe and secure as current technology allows. None of these products will dent your pocketbook, so protect yourself!
Word 2003 toolbars lost and recovered
Lounge member Adela lost some Word functions and didn’t know how to restore them.
Luckily, other Lounge members in the Word Processing forum set her on the path to discovery — advising her not just how to repair those problems but also other potential troubles she hadn’t yet recognized. And the bonus gift? A list of keyboard shortcuts.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right into today’s discussions in the Lounge.
Problems with Win8's custom recovery image
Win8 lets you place custom recovery images in locations that won’t allow for proper restoration. Here are the right locations and methods.
Plus: UEFI-related Windows updates on non-UEFI PCs, more questions about Macecraft’s jv16 PowerTools, and fixing a flash drive stuck in read-only mode.
A Windows 8 custom recovery image fails
Win8’s custom recovery image option lets you roll back your system files and your add-on software to a previous, known-good state. Used in conjunction with Win8’s File History, a custom recovery image lets you quickly recover from even serious system trouble. You won’t need to reinstall Windows or applications from scratch, and your personal data remains untouched.
But reader Gerald Greenberg had trouble getting Win8 to recognize and use a custom recovery image he’d created.
- “Fred, I’m trying to use Win8’s recimg command to restore a prior version of my setup.
“From time to time, I create customrefresh.wim files and store them on a backup drive.
“But when I tried to use a .wim file to restore my system to an earlier setup, the Change Settings screen gave me three options: Refresh, Reset, or Advanced Startup.
“If I use Refresh, the system displays a screen telling me what will happen; another screen then tells me what apps I will lose and need to replace.
“I see no mention of using the customrefresh.wim file and no place to select the file! It seems to be saying that it’s not going to use the file.
“Under Advanced Startup, there is mention of using the recimg-created file, but the only option is Restart now, which does just that — it restarts my computer!
“I would appreciate any info you can supply.”
I noted that you store the image files on a backup drive. Be aware that any recovery image must be immediately accessible at boot time. That means the files should not be on an extended (nonprimary) partition. Nor should they be on a virtualized drive or in a location accessed via a symlink (symbolic link; more info). There’s also the problem of when USB drives become accessible during your PC’s boot sequence.
If Windows isn’t automatically finding and using your custom recovery image, open an administrator-level command window and type the following:
recimg /setcurrent {folder}
where {folder} is the path to and name of the customrefresh.wim file you wish to register as the current Refresh source file.
When that command completes, enter the command
recimg /showcurrent
to verify that the correct recovery image is in fact the one that’s currently active.
But again, if the file is in a location that’s not immediately accessible at boot time, you’ll run into trouble — even if the file’s location is properly registered with recimg.
That’s likely your problem. I suggest moving your custom recovery image to a location you know will be accessible at boot —such as C:. Then use the recimg /setcurrent {folder} command to make that image and location active.
Once you make those changes, I bet that your custom restores will work properly!
For more information, see the Oct. 10, 2013, Top Story, “Creating customized recovery images for Win8.”
A question about UEFI updates on non-UEFI PCs
Most newer PCs use the Unified Extensible Firmware Interface (UEFI) in place of a classic BIOS. (See the Jan. 19, 2012, Top Story, “Say goodbye to BIOS — and hello to UEFI!”)
But some PCs use only a partial implementation of UEFI, while others — especially older systems — still use a classic BIOS.
Reader John Heathe wonders about the security implications of classic BIOS-based systems, especially when Microsoft rolls out security patches for UEFI-equipped hardware.
- “Dear Fred: Recently I noticed that there were several updates available for my Win 8.1 setup. However, because my mainboard is somewhat old, a lot of the new updates are UEFI-related and will not install on my system.
“Does the lack of new security features put me at risk? Do you advise updating my system? Or will Microsoft offer workarounds for older systems like mine?
“I don’t really feel I should have to change my mainboard and drives because of [the move to UEFI-based security]. I’d really appreciate some options that will protect those of us with older systems.”
I wouldn’t worry about it, John. UEFI is hardware-based, and its updates are much like the updates offered for other hardware that’s not present in your PC.
For example, an older PC’s hard drives might use parallel ATA connections (PATA; Wikipedia info). So Windows updates related to the newer serial ATA (SATA, Wikipedia info) simply wouldn’t apply.
Similarly, an older PC might use SVGA output (Wikipedia info) to connect to a monitor. Windows updates for HDMI classes of hardware (Wikipedia info) are irrelevant.
That said, SATA is better than PATA — it’s faster, more extensible, and less complex mechanically. HDMI is better than SVGA — it’s digital, not analog, and has much higher bandwidth and resolution. And so too, UEFI is better than a classic BIOS because it’s more flexible and offers better security options.
There’s no way that software updates and patches can add the benefits of newer hardware technologies such as these. The only way to gain the benefits is to upgrade the hardware.
When you eventually do upgrade, your new PC will likely have the newer technologies and will be able to provide capabilities your present system simply cannot support. Then, the updates relating to those technologies will apply.
Until you get a new PC, keeping your current system as secure as possible comes down to installing all applicable security updates that Windows, your installed applications, and your current hardware can support.
More concerns about Macecraft’s jv16 PowerTools
Jv16 PowerTools — a popular registry cleaner and system optimizer for advanced Windows users — is apparently undergoing major changes, prompting numerous reader emails over the past several months.
For example, see the previous LangaList Plus items, “Security concerns with jv16 PowerTools” (Jan. 23), and “More questions about jv16 PowerTools” (Feb. 13).
David Tooley has another question about the tools.
- “Some weeks ago, you mentioned you were no longer recommending jv16 as a primary cleanup tool. I’m curious as to why. You did mention that it was dangerously powerful.
“But if you use only the Fix button (and not Delete) after getting the scan results, where’s the harm? I’m also careful to back away if there’s a warning popup.
“For me, jv16 has proved to be a perfect adjunct to using CCleaner, Malwarebytes, Microsoft Security Essentials, and Spybot – Search & Destroy.”
Macecraft’s jv16 PowerTools (site) was once a top-rated cleanup utility. But yes; I’ve stopped recommending it.
The original jv16 PowerTools debuted in 2001, when most of us were still using Win98 and Windows ME. Those Windows versions needed a lot of help to keep running smoothly. Jv16 PowerTools’ ability to sort out problems by digging deep into the Registry was a welcome addition to any serious Windows user’s toolkit.
But today’s Windows is hugely more stable and less trouble-prone than those earlier versions. There’s simply not much need anymore for that kind of potentially destabilizing deep cleaning.
Eventually, Macecraft streamlined PowerTools’ interface — and even offered a safer Lite version for everyday use. But by then, many users had moved on to simpler, safer tools such as CCleaner.
With sales falling off, Macecraft decided to make jv16 PowerTools an open-source project, funded by voluntary donations. But the open-source conversion didn’t seem to go anywhere. According to the company’s homepage, its crowd-funding campaign reached just 41 percent of its U.S. $100,000 goal.
The software is once again fee-based for business use or personal use that includes technical support.
So, jv16 PowerTools still has an uncertain future. And in the hands of inexperienced or non-expert users, it can still be dangerous to use. (Even for advanced users, I strongly suggest making full system images before doing any deep cleaning with the utility.)
That said, I’m sure jv16 can be used safely, especially if one follows the instructions and uses only the automated fix options. But why bother? Tools such as CCleaner (free and paid; site) offer reliable cleaning — without the added risks of deep-cleaning options that are almost never needed on current versions of Windows.
Unlike jv16, CCleaner’s ongoing development seems stable and reliable. According to its publisher, it’s been downloaded over a billion times and is installed on about 25 percent of the world’s PCs. So the odds are excellent that CCleaner will still be around and fully supported in six months or a year. Jv16 PowerTools? Who can say?
Bottom line: If jv16 PowerTools works for you, great! There’s no reason for you to stop using it. But I believe its uncertain future, plus the fact that it’s overkill for routine cleanups, make it unsuitable for most users — especially when safer alternatives exist.
You are, of course, free to disagree!
USB flash drive stuck in read-only mode
Paul Audcent encountered the frustration of having a USB flash drive rendered useless by being locked into read-only mode.
- “Can anyone advise me how to unlock a plug-in flash drive that’s now locked? I tried to reformat it via Windows and Partition Magic, but they both tell me it’s locked! No; I don’t know how it became locked, but it might have been when I removed it before using Windows’ eject button.”
Indeed, a flash drive’s software structures can be damaged if you unplug it before all files on the device are closed and all pending writes are completed. Windows’ hotplug applet — also known as Safely Remove Hardware and Eject Media — is designed to prevent exactly this kind of trouble. (For more info, see the MS Support page, “Safely remove devices from your computer.”)
But there are several ways to recover access to a locked drive. In most cases, you need nothing more than utilities and functions that are built into Windows.
In fact, I devoted most of a previous column to exactly that issue! Check out the May 9, 2013, article, “Unlocking a read-only USB flash drive.”
Most likely, one of the simple fixes detailed in that column will get your flash drive going again!
New attacks on Windows' secondary components
July’s security updates target vulnerabilities in Windows Journal, DirectShow, On-Screen Keyboard and other supporting components.
But the bulk of July updates, once again, consists of nonsecurity fixes for all current versions of Office and their associated applications.
MS14-037 (2962872)
The ongoing battle to protect our browsers
July’s Internet Explorer patch fixes 24 newly disclosed vulnerabilities in Microsoft’s browser. Given the large number of new IE security flaws discovered each month, one has to wonder whether IE was really poorly written or there are more really talented hackers poking at the code. KB 2962872 is rated critical for all current workstation installations of IE (Version 6 and up).
All but one of the newly revealed vulnerabilities were privately reported, meaning they were most likely found by security researchers and reported to Microsoft — i.e., not already “in the wild.” The majority of the flaws could result in exploits using IE memory corruption, but one vulnerability might allow attackers to bypass IE’s Extended Validation Certificate security feature. As usual, the most severe exploits could allow attackers to take remote control of your PC.
Note: XP users won’t receive this update — once again illustrating that using IE with Windows XP is increasingly dangerous.
Another Patch Tuesday chore is adding the latest Adobe Flash Player update. For July, Adobe has released Flash 14.0.0.145 for Windows and Mac, and Version 11.2.202.394 for Linux, as noted in Adobe’s July 8 security bulletin. Flash Player is updated automatically in Chrome, IE 10, and IE 11.
As an aside to the regular update process, Google announced that unauthorized digital certificates for several Google domains had been issued by the National Informatics Centre of India, which is trusted by India CCA. As noted in the announcement, India CCA certificates are “included in the Microsoft Root Store [more info] and thus are trusted by the vast majority of programs running on Windows, including Internet Explorer and Chrome. Firefox is not affected because it uses its own root store that doesn’t include these certificates.”
Chrome browsers have been protected since July 3, and I anticipate that Microsoft will take similar action with their root certificates. Starting with Vista, the Windows root certification updating process is automatic; Redmond will most likely release an out-of-cycle fix, with no actions needed from users.
 What to do: Install KB 2962872 (MS14-037) as soon as offered. And if you’re manually updating Flash Player, watch out for those potentially unwanted software offers included with the Flash installer.
What to do: Install KB 2962872 (MS14-037) as soon as offered. And if you’re manually updating Flash Player, watch out for those potentially unwanted software offers included with the Flash installer.
Closing yet another door on Windows XP
Oracle announced that users installing Java 7 updates on XP do so at their own risk. There will be official Java 7 support for versions of Windows from Vista on. The cryptic announcement also notes that XP users will not be able to install Java 8.
This is just another nail in XP’s coffin. The list of software you can use safely on XP systems seems to be getting shorter by the day.
 What to do: Once again, I strongly recommend that you not go online with any XP system that’s connected to a local network, contains files with personal information, or is used for email.
What to do: Once again, I strongly recommend that you not go online with any XP system that’s connected to a local network, contains files with personal information, or is used for email.
MS14-038 (2971850)
Windows Journal brings noteworthy attacks
Most Office users are probably familiar with OneNote, Microsoft’s excellent note-taking application. But how many of us have run across Windows Journal — the basic note-taking app included in nearly all current versions of Windows? (To open the app, enter “Journal” into the Start menu search box.)
KB 2971850 fixes a privately reported flaw in Windows Journal that could allow remote-control attacks using malicious .jnt files. The update is rated critical because a successful exploit could let an attacker gain full access to a computer.
Note that on some servers, the update applies only if Ink and Handwriting Services is enabled. Given that Windows Server 2003 is not vulnerable, it’s likely that Windows XP isn’t threatened, either.
 What to do: Install KB 2971850 (MS14-038) when offered.
What to do: Install KB 2971850 (MS14-038) when offered.
MS14-040 (2961072)
Kernel-driver flaw leads to elevated privileges
By itself, the vulnerability patched by KB 2961072 is not a significant threat. Although a successful exploit could let an attacker gain admin-level access to a system, the patch is rated merely important because the attacker must have valid sign-in credentials. However, this vulnerability can become more of a threat when combined with other exploits. Using phishing, drive-by browsing attacks, and other techniques, it’s not all that hard for hackers to gain a toehold on your system.
The patched flaw is in the Windows Ancillary Function Driver, a kernel-mode driver that supports Windows sockets applications and is part of the TCP/IP stack. Typically, I recommend holding off on kernel patches, but it’s possible this vulnerability will be exploited relatively soon.
 What to do: Install KB 2961072 (MS14-040) when offered.
What to do: Install KB 2961072 (MS14-040) when offered.
MS14-041 (2972280)
Elevation-of-privilege attacks with DirectShow
DirectShow and DirectX are used to display media on your computer. DirectShow in particular provides support for audio/video sourcing, manipulation, and rendering. A privately reported flaw in the way DirectShow handles memory could let an attacker gain elevated privileges on a PC. With many exploits, an attacker has the same privileges as the current user. That’s why I often recommend not running in administrator mode. But this type of vulnerability would allow the attacker to take full control with admin rights.
KB 2972280 is rated important for most versions of Windows and Windows Server. (Windows RT isn’t affected.) Because Windows Server 2003 isn’t vulnerable, there should be no impact on Windows XP.
 What to do: Install KB 2972280 (MS14-041).
What to do: Install KB 2972280 (MS14-041).
MS14-039 (2973201)
On-screen keyboard another avenue of attack
Windows has so many components, it’s small wonder there are many ways to attack the OS. For example, Windows includes an on-screen keyboard, even on desktop systems that don’t have a touchscreen. KB 2973201 patches a flaw somewhat related to the DirectShow vulnerability — one that would allow an attacker to launch the on-screen keyboard and load malicious code. The flaw would give the hacker elevated privileges on the system.
The update is rated important for all versions of Windows except Windows Server 2003 — and by extension, XP is probably also unaffected. As with the two updates mentioned immediately above, this exploit will probably be used in conjunction with others.
 What to do: Install KB 2973201 (MS14-039).
What to do: Install KB 2973201 (MS14-039).
MS14-042 (2972621)
MS Service Bus flaw could allow DoS attacks
The final July security update — a patch for Microsoft Service Bus for Windows Server — impacts only Windows Server 2008 R2, 2012, and 2012 R2. Service Bus adds messaging features to Microsoft’s cloud platform, Azure (more info). The vulnerability is a bit unusual; it doesn’t affect Azure systems directly, but it will impact them if a system administrator has downloaded and installed Service Bus.
The update signals that with more hybrid deployments, there will be a growing number of threats to cloud services. The update is rated moderate and is available only from the Microsoft download site.
 What to do: Test KB 2972621 (MS14-042) thoroughly before deploying it on production services.
What to do: Test KB 2972621 (MS14-042) thoroughly before deploying it on production services.
2975061
The issues with Win8.1 Update are far from over
Ever since Windows 8.1 Update was unleashed on Win8.1 users, Microsoft has released a series of updates to Update. KB 2975061 is a fix for Win8.1 Update users who run into “Error 0x80070005” when attempting to install KB 2919355 (Win8.1 Update) or other security updates such as KB 2920189 — a Unified Extensible Firmware Interface (UEFI) patch.
In the case of KB 2919355, a part of the installation process keeps a component-store file open so that it can’t be deleted or overwritten. For UEFI, the optional BitLocker component isn’t installed.
 What to do: Whether or not you’ve run into either of the Win8.1 Update–related issues, install KB 2975061.
What to do: Whether or not you’ve run into either of the Win8.1 Update–related issues, install KB 2975061.
July’s heavy load of nonsecurity updates
The nonsecurity fixes dumped into Windows Update along with security updates is spread across all supported versions of Windows, Office, and other productivity products. Unless noted, the fixes are described by Microsoft simply as “stability and performance improvements.”
For more on July’s Office updates, see the Office Sustained Engineering post.
Windows 7
- 2952664 – Compatibility update for upgrading Win7
- 2966583 – System Update Readiness Tool enhancements
- 2973337 – Enable Transport Layer Security hash SHA-512
Windows 8/8.1
- 2967916 – Win8, Windows RT, and Server 2012; rollup update
- 2967917 – Win8.1, Win8.1 RT, Server 2012 R2; rollup update
- 2971203 – Win8.1 and Server 2012 R2; cumulative update for Windows Store
- 2972094 – Win8.1 and Win8.1 RT; string of Family Safety dialog box is not localized
Office 2003
Office 2007
- 2837608 – Excel
- 2837609 – Office
- 2837611 – Office
- 2837614 – Excel Viewer
- 2849965 – Office
- 2849969 – Office
- 2883030 – Outlook junk-mail filter
Office 2010
- 982726 – Outlook junk-mail filter
- 2837581 – Office
- 2837600 – Excel
- 2837606 – Office
- 2878252 – Office
- 2883004 – SharePoint Server
- 2881028 – Office; lexical improvements
Office 2013
- 2760587 – Outlook junk-mail filter
- 2880987 – Office; improve visuals
- 2881028 – Office; lexical improvements
- 2881074 – Office
- 2881075 – PowerPoint; copy/paste problem in empty placeholders
- 2881080 – Word; crashes when inserting indexes and tables
- 2881082 – OneNote; pen-click open issue
- 2881084 – Office; grammar error
- 2881085 – Excel; improve visuals
- 2881086 – Office; stability and performance
Other nonsecurity updates
- 2883018 – Office Online
- 2878285 – Office Online; lexical improvements
- 2863826 – SharePoint Server
- 2863837 – SharePoint Server
- 2849992 – SharePoint Foundation 2010; lexical improvements
- 2878282 – SharePoint Server 2010; lexical improvements
- 2880990 – Office Web Apps Server 2013; co-authoring issue
- 2880999 – Microsoft Publisher 2013; translation error
- 2881003 – SharePoint Server 2013; sort problem with large Excel files
- 2881077 – SharePoint Server 2013; problem editing Project site collection list
- 2881087 – OneDrive for Business; renaming problem when file upload is pending
 What to do: Wait on these nonsecurity updates.
What to do: Wait on these nonsecurity updates.
Regularly updated problem-patch chart
For Microsoft’s list of recently released patches, go to the MS Security TechCenter page. See our “Windows Secrets master Patch Watch chart” post for a more extensive list of recent updates.
| Patch | Released | Description | Status |
|---|---|---|---|
| 2871997 | 05-13 | Enhancements to Local Security Authority | Optional |
| 2952664 | 05-13 | Migration compatibility | Optional |
| 2926765 | 05-13 | Windows Shell; also KB 2962123 | Install |
| 2928120 | 05-13 | Group Policies preferences; for admins, also KB 2961899 | Install |
| 2933826 | 05-13 | Windows Server; also KB 2962073 | Install |
| 2952166 | 05-13 | SharePoint (for admins); see MS14-022 for complete list. | Install |
| 2953522 | 05-13 | Internet Explorer; also KB 2961851 | Install |
| 2958732 | 05-13 | .NET; see MS14-026 for complete list. | Install |
| 2961033 | 05-13 | Common controls; basic workstations; see MS14-024 for complete list. | Install |
| 2961037 | 05-13 | MS Office; KBs 2767772, 2878284, 2880463, 2878316; see MS014-023. | Install |
| 2939576 | 06-10 | XML Core Services; also KB 2966631 for Win8.1 (non-Update) | Install |
| 2957189 | 06-10 | TCP Protocol; also KB 2961858 for Win8.1 (non-Update) | Install |
| 2957689 | 06-10 | Internet Explorer; also KB 2963950 for Win8.1 (non-Update) | Install |
| 2965788 | 06-10 | Remote Desktop; also KB 2966034 for Win8.1 (non-Update) | Install |
| 2967487 | 06-10 | MS Graphic Component; see MS014-036 for full list. | Install |
| 2969258 | 06-10 | MS Lync; KBs 2969258, 2963288; see MS014-032. | Install |
| 2969261 | 06-10 | Word; KBs 2880513 and 2880515; see MS014-034. | Install |
| 2961072 | 07-08 | Windows AFD; also KB 2973408 for Win8.1 (non-Update) | Install |
| 2962872 | 07-08 | IE cumulative update; also KB 2963952 for Win8.1 (non-Update) | Install |
| 2971850 | 07-08 | Windows Journal; also KB 2974286 for Win8.1 (non-Update) | install |
| 2972280 | 07-08 | Windows DirectShow; also KB 2973932 for Win8.1 (non-Update) | Install |
| 2972621 | 07-08 | Microsoft Service Bus for Windows Server | Install |
| 2973201 | 07-08 | Windows on-screen keyboard; also KB 2973906 for Win8.1 (non-Update) | Install |
Status recommendations: Skip — patch not needed; Hold — do not install until its problems are resolved; Wait — hold off temporarily while the patch is tested; Optional — not critical, use if wanted; Install — OK to apply.
We can supply you with binder twine
 |
With the Grand Départ, the 2014 Tour de France was launched this past weekend — from Yorkshire England. In anticipation of the event, a Yorkshire man compiled some advice for the cyclists. The video explains to Tour de France riders proper costuming for the Yorkshire stages. Among the many admonitions: No bright colors! (They scare the sheep.) This friendly advisor also offers a preview of Yorkshire hospitality and a view of the county and its people. After viewing this video, we’re sure you’ll feel prepared for a visit — whether you ride your bike fast or slow. Click below or go to the original YouTube video. |
| Post your thoughts about this story in the WS Columns forum. |
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
My Simple Word 2010 Macro Is Not Working
by
mbennett555
9 hours, 37 minutes ago -
Office gets current release
by
Susan Bradley
14 hours, 20 minutes ago -
FBI: Still Using One of These Old Routers? It’s Vulnerable to Hackers
by
Alex5723
1 day, 6 hours ago -
Windows AI Local Only no NPU required!
by
RetiredGeek
15 hours, 23 minutes ago -
Stop the OneDrive defaults
by
CWBillow
1 day, 7 hours ago -
Windows 11 Insider Preview build 27868 released to Canary
by
joep517
1 day, 17 hours ago -
X Suspends Encrypted DMs
by
Alex5723
1 day, 19 hours ago -
WSJ : My Robot and Me AI generated movie
by
Alex5723
1 day, 20 hours ago -
Botnet hacks 9,000+ ASUS routers to add persistent SSH backdoor
by
Alex5723
1 day, 20 hours ago -
OpenAI model sabotages shutdown code
by
Cybertooth
1 day, 21 hours ago -
Backup and access old e-mails after company e-mail address is terminated
by
M W Leijendekker
1 day, 9 hours ago -
Enabling Secureboot
by
ITguy
1 day, 16 hours ago -
Windows hosting exposes additional bugs
by
Susan Bradley
2 days, 5 hours ago -
No more rounded corners??
by
CWBillow
2 days, 1 hour ago -
Android 15 and IPV6
by
Win7and10
1 day, 14 hours ago -
KB5058405 might fail to install with recovery error 0xc0000098 in ACPI.sys
by
Susan Bradley
2 days, 17 hours ago -
T-Mobile’s T-Life App has a “Screen Recording Tool” Turned on
by
Alex5723
2 days, 20 hours ago -
Windows 11 Insider Preview Build 26100.4202 (24H2) released to Release Preview
by
joep517
2 days, 14 hours ago -
Windows Update orchestration platform to update all software
by
Alex5723
3 days, 3 hours ago -
May preview updates
by
Susan Bradley
2 days, 15 hours ago -
Microsoft releases KB5061977 Windows 11 24H2, Server 2025 emergency out of band
by
Alex5723
2 days, 6 hours ago -
Just got this pop-up page while browsing
by
Alex5723
2 days, 19 hours ago -
KB5058379 / KB 5061768 Failures
by
crown
2 days, 16 hours ago -
Windows 10 23H2 Good to Update to ?
by
jkitc
1 day, 19 hours ago -
At last – installation of 24H2
by
Botswana12
3 days, 19 hours ago -
MS-DEFCON 4: As good as it gets
by
Susan Bradley
16 hours, 52 minutes ago -
RyTuneX optimize Windows 10/11 tool
by
Alex5723
4 days, 7 hours ago -
Can I just update from Win11 22H2 to 23H2?
by
Dave Easley
2 days, 5 hours ago -
Limited account permission error related to Windows Update
by
gtd12345
4 days, 20 hours ago -
Another test post
by
gtd12345
4 days, 20 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

