
|
There are isolated problems with current patches, but they are well-known and documented on this site. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Pre-encryption makes cloud-based storage safer
In this issue
- LANGALIST PLUS: Making use of unallocated hard-drive space
- TOP STORY: Pre-encryption makes cloud-based storage safer
- LOUNGE LIFE: 'Local' important concept in formatting
- PATCH WATCH: Closing a long year of Windows patching
- BEST HARDWARE: Windows 8 mice: Pointing in the right direction
- WACKY WEB WEEK: A dangerous proximity to curious bears
Making use of unallocated hard-drive space
Some hard-drive setups waste space — even on brand-new systems. Here’s how to make sure every bit of your drive is available for use.
Plus: Getting files off a password-protected PC, running Microsoft Works and Money on Windows 8, and solving email file-attachment woes.
New laptop doesn’t make full use of HDD
Reader Anas Khan has a new PC, but the hard drive isn’t set up well.
- “There’s 42MB of unallocated space on my new Lenovo laptop, as configured by the company. I don’t have any idea why it’s there. I could use some help with this problem.”
Unallocated space is any portion of the drive that’s empty and not assigned to a partition. It’s basically wasted space. (You want to ensure that the “empty” space is truly unallocated — and not a protected or hidden OEM recovery partition.)
On new drives, unallocated space can be due to a manufacturing shortcut. The vendor installs a disk image that’s designed for a smaller drive but then doesn’t extend the new system’s partition to use the entire drive.
You can easily correct this yourself by expanding or extending an existing partition to include the wasted space.
It usually takes only a few clicks, and the process isn’t particularly dangerous. But it makes sense to take precautions any time you’re making fundamental changes to your hard drive.
Start by making an OEM recovery image. Almost all new PCs come with some way of making an externally saved copy of the original factory setup. Lenovo, for example, typically calls it “Rescue and Recovery” (described on a Lenovo support page). Store the OEM recovery files in a safe place, off the drive you’ll be working on.
Next, make a complete, normal Windows backup or image of the system as you currently have it configured. As with the OEM recovery files, store the image or backup files in a safe place, off the drive you’re repartitioning. For information about making backups and images on XP through Win7, see the May 12, 2011, Top Story, “Build a complete Windows 7 safety net.” For Win8, see the Oct. 10 Top Story, “Creating customized recovery images for Win8.”
Now you’re ready to safely change the drive structure.
You can use Windows’ built-in Disk Management tool, as described in the May 19, 2011, Top Story, “Don’t pay for software you don’t need — Part 2.” Skip down to the section titled Win7 does all the disk partitioning you’ll need. (Win8’s tools are almost identical.)
With Disk Management up and running, right-click a partition adjacent to the unallocated space and select Extend Volume. (In this case, “volume” is simply another name for partition.) Follow the on-screen prompts to enlarge/extend the selected partition to encompass the unallocated space. For detailed, how-to instructions, see the TechNet article, “Extend a basic volume.”
There are also many excellent, third-party, free/paid partitioning applications that offer options other than Disk Management. Some free products include MiniTool Partition Wizard Home Edition (site), EaseUS Partition Master Free (site), and Paragon’s Partition Manager 2013 Free (site). A Web search will turn up many other partitioning tools.
Any of those options should let you add the unallocated space to an existing partition in minutes!
Recover files from a password-protected PC
Reader HB was trying to give help in a difficult circumstance:
- “The family of a recently deceased friend has asked me to recover music, photos, emails, and so on from her password-protected Windows 7 Toshiba laptop.
“I thought I’d use a Linux (e.g., Ubuntu) Live CD to copy the files to an external drive.
“Does that approach make sense to you? Or am I missing something?”
It really depends on which password you mean.
If it’s a BIOS-level/power-on password — in other words, a password stored on the laptop’s hardware, outside of Windows — you might be able to reset it by any one of several fairly simple means (though you’ll probably have to open the laptop’s case). On some systems, there’s a small switch or set of electrical contacts that lets you reset the BIOS password. On other systems, you remove the coin-type battery on the mainboard and wait a few minutes; the system will then “forget” the stored password. You can find general how-tos on this method by searching the Web with the phrase reset bios password. Add the laptop brand and model to your search terms to find more specific help.
Sometimes, the hard drive itself is password-protected. If the hard-drive password is stored in the BIOS, the technique mentioned above should remove the password. However, if the password is stored within the drive’s firmware, you might be out of luck! By design, passwords stored in the drive’s electronics (not on the platters) are difficult or impossible to bypass.
But again, a Web search is the place to start. Try the phrase bypass hard drive password, and then add the laptop and hard-drive brand/model for more specific information.
If the disk has been password-protected with an encryption tool such as Windows BitLocker (info) or TrueCrypt (site), the data will almost certainly be completely out of reach. You can try searching the Web for “hard-drive data-recovery service,” but it’s unlikely any of those specialized services will break the encryption — and the cost will be high.
Let’s hope it’s just an ordinary Windows 7 password, with nothing else in the way.
As with XP and Vista, Win7’s password is mainly intended to thwart casual snoops. If you have physical access to the system (as you do in this instance), it’s easy to get around those passwords.
(Win8’s password is harder to bypass, due to the operating system’s Secure Boot feature. See the Oct. 3 LangaList Plus column, “The pitfalls of Windows 8’s Secure Boot.”)
Bypassing Win7’s password should be easy. As you thought, you can boot the laptop with just about any free Linux “live” DVD (a self-contained Linux that runs entirely from the DVD — it doesn’t require installation on the hard drive). To my knowledge, all major, current Linux versions can read NTFS drives without difficulty. So once the laptop is running Linux, you’ll be able to look inside the hard drive and locate whatever files you wish. You can then export the files via Wi-Fi or Ethernet, or save them on an external drive.
An alternate approach is to physically remove the laptop’s drive (usually just a matter of loosening a few screws) and then to attach the drive to your PC as a secondary, non-booting disk. If your system doesn’t have an empty drive bay, you can use an inexpensive USB drive connector, such as those discussed in the Feb. 13 Top Story, “House Call 2013 — Part 1: Sanitizing a drive.”
With the laptop’s drive connected to your PC, you’ll be able to access its files just as you do any other attached drive. Simply copy/paste any desired user files to your system — or to any other location you wish.
With luck, one of these simple methods will let you access the files with a minimum of time and fuss.
Running MS Works and Money on Windows 8
Susan Puente would like to use two venerable Microsoft packages on a new PC.
- “I had a Vista system with Works and Money installed. Where can I find these programs again? Does Windows 8 have them somewhere?”
Those programs weren’t part of Windows itself. Instead, your old PC probably had a “bundle” of additional programs installed by the vendor.
Unfortunately, I’m assuming you do not have the original Works and Money setup disks. If you had them, you probably could have just reinstalled the two apps in Win8. (See the Nov. 28 LangaList Plus item, “Running Windows XP–era software in Win8.” Skip down to the section that discusses Windows Compatibility Mode.)
Again, assuming you don’t have the setup disks, you’ll probably need to find replacement products; both Works and Microsoft Money have been discontinued. Luckily, there are many excellent replacement products available!
Works was a stripped-down version of Microsoft Office. If you’re looking for a 100 percent free replacement, see the March 14 Top Story, “Two free, full-blown alternatives to MS Office.”
If you’d rather stick with true Microsoft software, you can either buy the standalone Office 2013 or get a subscription for Office 365. You can read about them in the Feb. 14 Woody’s Windows, “Software SmackDown: Office 2013 vs. Office 365,” and last week’s (Dec. 4) Top Story, “MS adds more options to Office 365 Home Premium.”
Money (a basic financial tracking and management tool) is long gone, but Intuit, the 800-pound gorilla of that software category, offers free, basic financial tracking and management via its cloud-based Mint service (site). The company’s immensely popular, standalone Quicken software (site) starts at under U.S. $30.
A Web search for Microsoft Money replacement alternative will turn up other options, too.
After Win upgrade, trouble with email attachments
Ronnie Haig has lost the ability to attach files to his emails.
- “I am a professional songwriter/musician, and I frequently need to send my songs to prospective customers.
“I had no trouble at all on my XP system. Then came Win7 and Win8, and things got really confusing.
“When sending a message through AOL, clicking the lower-left ‘Attach file’ button would take me directly to my Windows Media Player, where a couple of clicks would send songs on their way. With Win7 or 8, it would be easier to win on Jeopardy.”
There are multiple ways to access and use AOL mail. I don’t know which one you’re using, so I’m making an educated guess.
I tried the current browser-based version of AOL mail in Chrome 31 and IE 11. I had no trouble at all in attaching files to emails — up to the AOL limit of 25MB per email.
If you’re using an older, standalone AOL email client or one of the old toolbar versions, I suggest you uninstall it — it’s obsolete. Instead, use AOL email directly from within a fully up-to-date browser.
If that doesn’t work, you could try a different email system. For example, switch to a free Gmail (site) account, Outlook.com account, Windows Essentials (site), or any similar service. They all allow for normal email attachments.
Most email services also allow mail forwarding. You should be able to configure your AOL account to automatically forward all your AOL email to whatever new account you set up. That way, people who know you by your AOL address will still be able to contact you the way they’re used to — and you’ll be able to use a non-AOL email and client to reply and to attach files.
Another possibility is to use a file storage/sharing service such as Dropbox (site), SkyDrive (site), or Google Drive (site). You can post your music files there, then mail the URL for the stored files to your clients. They can download the files directly to their PCs. (You can password-protect your cloud-stored files to prevent public access. Share the password only with your clients.)
I think using a more up-to-date method to access your AOL mail — or using an alternative email or file-sharing service — will resolve your file-attachment problems!
Pre-encryption makes cloud-based storage safer
I must confess: Until recently, I deeply distrusted the security of cloud-storage services such as SkyDrive, Google Drive, and Dropbox.
But now, thanks to pre-encryption software, I’m comfortably using several cloud services — with no worries about the security and privacy of my files.
Most, if not all, cloud-storage services use some sort of server-based encryption to protect user data. But, as has been widely reported and discussed, that protection is not absolute — if your cloud-storage account is hacked or your password stolen, your files could be open to intruders.
Ensuring that the files you store online are truly safe requires encryption that you — and you alone — control. Products such as Boxcryptor, which I discuss in detail below, make it easy to pre-encrypt files before they leave your PC. Then, if a hacker manages to breach the cloud server’s own security, or if he intercepts your files while they’re being transmitted, he’ll get nothing but indecipherable gibberish.
This type of encryption works just as easily in reverse. Files and folders travel from online-storage servers to your PC under your personal encryption (on top of any encryption the service might use). Decryption takes place only when the files are back on your PC and under your local control.
Using your own encryption means that your data is always just as safe in the cloud as it is on your PC.
Below, I’ll show you — step by step — how pre-encryption software works. But first, I’ll address a couple of important points about cloud-storage services.
Why use cloud-based data storage at all?
For me, the primary benefit of cloud storage is for offsite backups. If your PC and local backups are lost or destroyed by fire, flood, theft, or whatever, you’ll still have copies of your files in the cloud.
(Keeping local copies is still important, too; some sort of disaster or outage could prevent access to your cloud-stored files.)
Moreover, cloud-based storage can act as a sort of central server. No matter where you are, a Web connection will provide quick and easy access to any file stored online.
There are dozens of cloud-storage services available; you’re probably already using one or more of the three mentioned above. But a search of the Web using the phrase cloud storage service will reveal many more.
Pre-encryption works with most cloud-storage services; but for this article, I discuss encrypting files and folders stored on Microsoft’s SkyDrive. Here’s why:
Microsoft is making SkyDrive a central part of the Windows experience. The service is built into Windows 8, and you’re “encouraged” to back up at least some of your settings and files to a SkyDrive account. Likewise, Office 2013 and Office 365 save files to SkyDrive by default.
So Microsoft’s intentions are clear: If you’re going to use Windows software, you’re going to encounter SkyDrive. With that in mind, it makes sense to start with better protection for your SkyDrive data.
To follow along with the rest of this article, you’ll need a free SkyDrive account. If you’re running Win8, it’s nearly certain you already have one. If you’re running Vista or Win7, you need a Microsoft account (which includes a free SkyDrive account) and the SkyDrive app installed locally on your system. Start by creating the Microsoft account (site); then go to the SkyDrive site and click the Get SkyDrive apps link in the lower-left corner of the window.
(Although XP users can access SkyDrive via the Web, the local SkyDrive app isn’t supported. However, XP users can use this article to encrypt their data on other, XP-compatible, cloud-storage services such as Google Drive [site].)
A free SkyDrive account currently gives you 7GB of online storage, which is plenty to start with. If you wish, you can add more storage space in increments, starting at 20GB for U.S. $10 a year.
Pre-encryption adds automatic protection
No doubt some PC users are already putting encrypted files up in the cloud. You can, for example, easily cobble together do-it-yourself encryption by using free tools such as 7-Zip (site). But that’s cumbersome, requiring several manual steps before and after every use of the encrypted files.
Pre-encryption software, on the other hand, is designed for use with cloud-storage services. It’s also transparent; as the authorized user, you save and open files just as you do with unencrypted documents. Somewhat like file compression, the encryption/decryption process is handled automatically on your local machine.
There are many kinds of pre-encryption software available. To see a list, simply search the Web using the phrase cloud encryption.
For this article, I’ve selected Boxcryptor (site). It’s free for personal use; supports Windows, Mac, Linux, iOS, and Android; and works with all the major cloud-storage providers (and numerous minor ones — see the list).
Like most pre-encryption apps, Boxcryptor creates a virtual drive on your computer. The drive acts as staging area for files going to or from whatever cloud-storage service you’re using.
Any file dropped, copied, pasted, or saved into an encrypted folder within the Boxcryptor drive is automatically encrypted (using a combination of AES-256 and RSA algorithms) and synched to the cloud. Again, the process is transparent: you access and use your cloud-based files — via the Boxcryptor drive — in the normal way. (Want the tech details? See the Boxcryptor overview page.)
Setting up Boxcryptor, step by step
Boxcryptor doesn’t do anything weird during installation, and the default settings should work fine for most circumstances. Generally, you can just read the dialog boxes, accept the default settings, and let the Boxcryptor installation run to completion. Setup is fast and takes only a short time to finish.)
Note: If you’re running Windows Professional, Enterprise, or Ultimate, the built-in Encrypting File System (EFS) is enabled by default — even if you’ve never used it. If Boxcryptor detects EFS on your system, you’ll see a dialog box that will offer to disable EFS, to prevent potential conflicts. Unless you’re actively using EFS (or the related BitLocker service), go ahead and let Boxcryptor disable EFS.
Boxcryptor will still run if you leave EFS enabled, but you could encounter conflicts when EFS tries to decrypt Boxcryptor files — or vice-versa.
(If you don’t see the EFS dialog box, it just means that either you don’t have EFS on your system or it’s already disabled.)
- Step 1: Download and launch Boxcryptor for Windows (site).
Figure 1. Boxcryptor for Windows is free for personal use. The app is also available for Mac, Linux, iOS, and Android.
- Step 2: When the setup wizard opens, accept the Boxcryptor terms of service and press Next.
Figure 2. The default settings in Boxcryptor's setup wizard should work for virtually all cases.
- Step 3: Click the Finish button when it appears. When you exit the installer program, you’ll see a dialog box requesting that you reboot. Close all your files and programs, and let your PC restart normally.
- Step 4: After reboot, you’ll see a new Boxcryptor icon on your desktop, and a Boxcryptor sign-in dialog box will open automatically. (If it doesn’t, click the desktop Boxcryptor icon.) Click the Sign up button to create an account and private encryption keys.
Figure 3. Click the Sign up button to create your Boxcryptor account and private encryption keys.
- Step 5: Enter your account information. As shown in Figure 4, the dialog box is straightforward; just fill it in as indicated.
Use care when selecting a password. In Boxcryptor, your password is also used to generate the encryption keys. A long, complex, hard-to-guess password will make your Boxcryptor files as secure as possible.
If you need help generating a good password, try free online tools such as Norton’s Password Generator, GRC’s Perfect Passwords, or the Secure Password Generator — or search the Web using the phrase password generator.
Figure 4. Create a unique, high-quality, hard-to-guess password.
- Step 6: Acknowledge Boxcryptor’s password warning. You’re responsible for retaining possession of the password. If you lose or forget your password, Boxcryptor can’t reset it for you! Store your password in a safe, snoop-proof place.
(For suggestions on safe, easy ways to store all your passwords, see the Oct. 17 Top Story, “Protect yourself from the next big data breach.”)
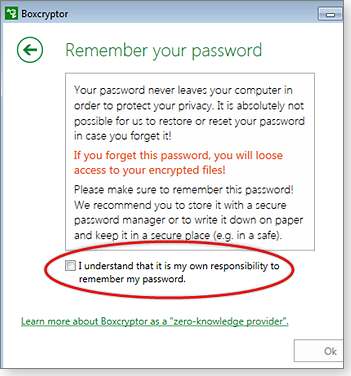
Figure 5. You must acknowledge that your password cannot be recovered or reconstructed if you lose or forget it.
- Step 7: As a last setup step, select your Boxcryptor plan. In this example, I’ve selected the free option, which is fine for most private uses. (If you wish, explore the other plans via the Plans and prices link.)

Figure 6. Boxcryptor offers plans for most personal and business needs.
After you pick a plan, the Boxcryptor software will churn for a moment as it sets up your account and generates your encryption keys. The sign-in dialog box will then reappear.
- Step 8: Sign in to Boxcryptor, using the username and password you created in Step 5. You’re ready to go!
As one of its first acts, Boxcryptor will open a selection of tutorials. The next section will show you the basics of using Boxcryptor. But it’s a good idea to keep the tutorial handy so you can also work through the indicated lessons step by step.

Figure 7. Boxcryptor starts you out with useful tutorials.
Using Boxcryptor with SkyDrive: The basics
Boxcryptor is a cinch to use with SkyDrive on Vista, Win7, and Win8.0. But there’s a small speed bump to overcome in Windows 8.1, because Microsoft changed SkyDrive’s fundamental operation in that version of Windows.
Win8.1’s SkyDrive now uses Smart Files, a default feature that does away with local copies of your SkyDrive files. This cuts down on local storage needs, which helps space-constrained portable systems such as those running Windows RT (Microsoft explanation).
Personally, I think this is a silly default setting. The vast majority of Win8.1 systems have plenty of local storage space. Plus, the Smart Files feature creates two problems: it does away with easy, offline access to your SkyDrive files, and it creates an obstacle for apps such as Boxcryptor — which are designed to encrypt files locally before they’re sent to SkyDrive.
To allow for offline access to SkyDrive files — and to allow apps such as Boxcryptor to work properly — Win8.1 users need to configure SkyDrive to operate the same way it works in Vista, Win7, and Win8.0. This make offline change is easy, as described on the Microsoft page, “Getting started with SkyDrive”; scroll down to the “Getting to files when you’re offline” section.
Once that’s done, all versions of Windows from Vista on will work with Boxcryptor in the same way.
Here’s how to Boxcryptor-encrypt your SkyDrive files:
- In File Explorer/Windows Explorer, click on the virtual Boxcryptor drive, as shown in Figure 8. You’ll see a heading for your local SkyDrive files (which Boxcryptor created automatically).
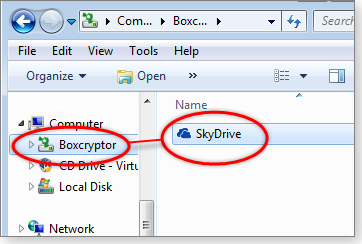
Figure 8. Here, Boxcryptor's virtual drive automatically included a SkyDrive heading
- Click on the SkyDrive heading inside Boxcryptor, and you’ll see your local SkyDrive files. (For this how-to, I created a simple test file — plaintexttestfile.txt.)
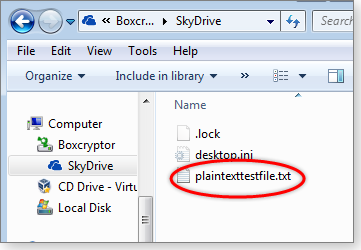
Figure 9. Sample file (circled) in a Boxcryptor-encrypted SkyDrive folder.
- To encrypt any file or folder, right-click its icon and select Boxcryptor/Encrypt from the popup menu; Boxcryptor immediately encrypts the file or folder — and keeps it encrypted any time you don’t have it open. (Any new files dropped into an encrypted folder are automatically encrypted. File-by-file encryption isn’t needed.)
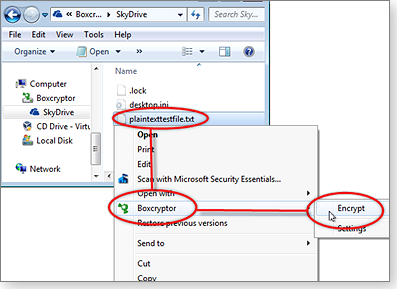
Figure 10. Three quick clicks encrypt any file or folder.
That’s all it takes!
Note: The first time you use Boxcryptor to encrypt files, you could encounter a small Windows bug. On some systems, Windows might incorrectly assume that locally encrypted files are managed by Windows’ Encrypted File System — even when they’re not! If this happens, a dialog box will ask you to export the local-authentication certificates used by EFS. However, Boxcryptor doesn’t use EFS and doesn’t require local-certificate export (Boxcryptor explanation).
To silence Windows’ needless nagging, just export the certificates anyway — it should take only a minute. On the Certificate Export Wizard, click Next and follow the prompts. Once that’s done, Windows shouldn’t nag you again about exporting certificates.
The encryption process is very fast. Once it’s done, you can access and use (open, edit, copy, paste, save, etc.) the encrypted files and folders within Boxcryptor just as you do unencrypted files on your system. Encryption/decryption is totally transparent.
For example, if I click my encrypted plaintexttestfile.txt file, it opens normally in Notepad, as shown in Figure 11.

Figure 11. My decrypted test file in Notepad
But Figure 12 shows what hackers would see if they hacked directly into my SkyDrive account and opened the same file in Notepad — either without Boxcryptor entirely or with Boxcryptor minus the correct password.
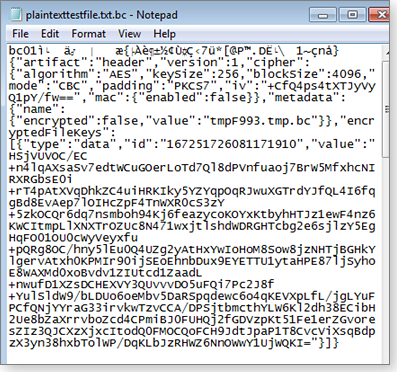
Figure 12. Access the file outside Boxcryptor, and it's gibberish — useless to hackers.
If this brief overview isn’t sufficient to get you going, refer to Boxcryptor’s local and online manuals, or work through the previously mentioned tutorials.
Encryption makes cloud storage much safer. Using Boxcryptor (or one of its competitors) is another important tool for keeping your data safe and secure — from all prying eyes. Cloud encryption software lets you gain the benefits of cloud storage — without risking your privacy!
'Local' important concept in formatting
When Lounge member moon1130 tried to apply a theme to his Word 2010 document, nothing happened.
He asked for help in the Word Processing forum — and soon enlarged his understanding of local font and paragraph formatting. In page design, as in other territorial matters, local rules tend to trump global choices.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right in to today’s discussions in the Lounge.
Closing a long year of Windows patching
Congratulations! We’ve come to the end of 2013 with 103 security bulletins, numerous nonsecurity updates, several security advisories, and a few zero-day threats.
Facing the end of official support, XP users end the year battling a resurgence of the svchost bug.
Note: Because Windows Secrets will be taking a break at the end of December, there will be no second Patch Watch column this month. But around Christmas time, I’ll be posting Patch Watch updates in the Windows Secrets Lounge/Windows Secrets Columns. So join me there for a bit of holiday fun!
MS13-097 (2898785)
The last Internet Explorer and Flash updates?
If only that were true. December brings the usual monthly security patches for Microsoft’s browser and Adobe’s Flash Player. For IE, KB 2898785 fixes seven vulnerabilities. The update is rated critical for all versions of IE, including IE 11. As always, you should apply IE updates even if it’s not your default browser.
The patched vulnerabilities are the usual suspects: remote-code execution and elevation of privileges. In other words, a user who clicks on a malicious website or link might let hackers remotely run malware on the user’s system — and then take control of the machine.
If you have Adobe Flash Player installed, make sure you’re on Version 11.9.900.170, as noted in the Dec. 10 Adobe Security Bulletin. Adobe’s Shockwave Player goes to Version 12.0.7.148, as noted in another security bulletin.
Firefox users should upgrade to Version 26, which allows non–admin level updating and the new Mozilla Maintenance Service (more info), noted in the Dec. 10 release notes.
 What to do: Install KB 2898785 (MS13-097) when offered and check that all browsers, media players, Java, and other apps are fully up to date.
What to do: Install KB 2898785 (MS13-097) when offered and check that all browsers, media players, Java, and other apps are fully up to date.
MS13-096
Office patch for zero-day threat via TIFF images
As I noted in the Nov. 14 Patch Watch column, an active zero-day threat exploited a vulnerability in the Office TIFF codec. Attackers used malicious TIFF images attached to email or Word documents.
If you applied the fixit offered in Security Advisory 2896666, you now need to undo it. Otherwise, you might have problems seeing some images on your computer. You’ll find the “Disble this Fix it” button near the bottom of MS Support page 2908005.
If you did not apply the fixit, it’s safe to install KB 2908005. Because the code for TIFF-file parsing is used in both Windows and Office, you might see multiple updates for this one vulnerability.
Because of the shared code used across Office applications, you might also see updates for apps you don’t have installed. Install the updates anyway.
You might be offered any of the following critical patches:
- KB 2817641 for Office 2007 SP3, Office Compatibility Pack, and Excel Viewer
- KB 2817670 for Office 2010 SP1/SP2 and PowerPoint 2010 Viewer
- KB 2850047 for Office 2003 SP3 and MS Word Viewer
- KB 2901674 for Vista, Server 2008
You might also see one or more of the following important updates for Lync, Microsoft’s chat program:
- KB 2850057 for Lync 2013
- KB 2899393 for Lync 2010 Attendee
- KB 2899395 for Lync 2010 Attendee (admin-level install)
- KB 2899397 for Lync 2010
 What to do: Install any of the updates listed above (and in MS13-096) when offered.
What to do: Install any of the updates listed above (and in MS13-096) when offered.
MS13-099 (2892074, 2892075, 2892076)
Taking remote control via Windows Script
Visual Basic Scripting (VBScript) has been included with every desktop release of Windows since Windows 98, according to a Wikipedia post. But Windows Script 5.6–5.8 had vulnerabilities that attackers could use to take complete control of a system. Merely browsing to an infected website might let in the malicious code used for this Windows Script exploit.
Rated critical, the fixes in MS13-099 apply to all current versions of Windows, including Win8.1 and Windows RT. You should see only one of the following patches offered (based on the Windows Script version installed).
- KB2892076 patches Windows Script 5.6
- KB2892075 patches Windows Script 5.7
- KB2892074 patches Windows Script 5.8
 What to do: Install KB 2892074, KB 2892075, or KB 2892076 when offered. See MS13-099 for more information.
What to do: Install KB 2892074, KB 2892075, or KB 2892076 when offered. See MS13-099 for more information.
MS13-098 (2893294)
Proactively patching code-signing process
KB 2893294 is a bit unusual. Although we’re applying the patch now, it doesn’t take full effect until June 10, 2014, when — according to an MS Security Research & Defense blog — “binaries will be considered unsigned if they do not conform to the new [Authenticode] verification process.” In other words, the new Windows Authenticode signature-verification system that will be used by default after June 10 already has a needed fix. An attacker could build a malicious Windows Portable Executable (more info) that’s signed as authentic.
Microsoft was informed that a small number of third-party installer programs, signed with a valid Authenticode signature, had been modified to download a different — and potentially malicious — executable. This was accomplished without invalidating the installer’s Authenticode signature. Obviously, this could be a very bad thing. To give vendors time to ensure they’re code-signing correctly, Microsoft set the June deadline for fully implementing the hardened Authenticode. After that date, code that hasn’t been updated will be considered unsigned.
KB 2893294 is rated critical for all current versions of Windows.
 What to do: This update might not be needed immediately, but install KB 2893294 (MS13-098) now to get it out of the way.
What to do: This update might not be needed immediately, but install KB 2893294 (MS13-098) now to get it out of the way.
MS13-101 (2887069, 2893984)
Put another Windows kernel update on hold
KBs 2887069 and 2893984 are new kernel patches for five newly reported vulnerabilities in Windows. The first patch, rated important, defends against elevation-of-privilege attacks; the second, rated moderate, is for potential denial-of-service threats.
Too many times this year, kernel updates have had unforeseen side effects. So I’m giving my usual recommendation to put these updates aside for a few weeks. Because these fixes have low severity ratings, that’s a relatively safe bet.
At the end of this month, I’ll revisit both patches in the Windows Secrets Lounge. Reports of probems with KB 2887069 are already posted in a MS Community forum.
 What to do: Keep KBs 2887069 and 2893984 (MS13-101) on ice for now.
What to do: Keep KBs 2887069 and 2893984 (MS13-101) on ice for now.
MS13-102 (2898715)
Windows XP and Server 2003 LRPC vulnerability
It’s rare these days to see an update applicable only to Windows XP and Server 2003, but our 102nd security bulletin does just that. KB 2898715 fixes a vulnerability that lets attackers spoof a Microsoft Local Remote Procedure Call, gaining more access to a system. Windows workstations have been at risk from RPC vulnerabilities for a long time.
I had to dig into the way-way-back Patch Watch memory banks to remind myself of how the RPC is exploited. I came up with a Blaster example from the Sept. 18, 2003, Patch Watch column. The good news: This latest RPC vulnerability can’t be exploited remotely; an attacker must have local access to your system. For that reason, the update is rated important. That said, with today’s blended attacks, it’s not unthinkable that a remote hacker might find a way to use the flaw.
 What to do: Windows XP users and Server 2003 admins should install KB 2898715 (MS13-102) when it’s offered.
What to do: Windows XP users and Server 2003 admins should install KB 2898715 (MS13-102) when it’s offered.
MS13-106 (2850016, 2850022)
Long-overdue fix for a zero-day threat
A vulnerability in Office has been exploited for months, and Microsoft has known about it since September, according to a ZDNET report. Hackers discovered that a component in Office 2007 and Office 2010 was not built to implement Windows’ Address Space Layout Randomization (ASLR; more info) security feature. By targeting the hxds.dll file, attackers can more reliably predict memory offsets for specific instructions in a call stack..
Although KB 2850016 is for Office 2007 and KB 2850022 applies to Office 2010, you might see both updates in Windows Update. Both are rated important.
 What to do: Install KBs 2850016 and 2850022 (MS13-106) if offered.
What to do: Install KBs 2850016 and 2850022 (MS13-106) if offered.
MS13-104 (2850064)
Office 2013 users get another security patch
New products often produce new attacks. In this case, the vulnerability is in Office 2013 for both Windows and Windows RT. If an Office user clicks a malicious link, an attacker can grab the user’s access tokens used for communicating with an online SharePoint or Office server. The attacker could then use the stolen tokens to sign in to the servers as the user.
This exploit is already in play. Although this update, rated important, applies to all Office 2013 users, it’s most important to Office 365 subscribers.
 What to do: Install KB 2909976 (MS13-104) immediately if offered.
What to do: Install KB 2909976 (MS13-104) immediately if offered.
Svchost running amok on Windows XP PCs
If your Windows XP system seems especially slow lately, Task Manager might show Windows’ svchost.exe taking 100 percent of your CPU cycles. (The executable is a system process that hosts other services, according to an MS Support document.) Numerous XP users have reported the problem in an MS Community Windows forum.
For now, those who are hit hard by excess svchost activity can only disable Microsoft Update and wait for a fix from Redmond — hopefully sooner rather than later. (Keep in mind that support for XP ends on April 8, 2014.) You can run manual scans for new updates, but on my system this takes a long time. Some users have reported fixing the problem by manually installing IE updates (such as KB 2870699) and letting all other patches install via Microsoft Update.
 What to do: Microsoft is aware of the issue and is reportedly working on a fix. But when it’ll be released is unknown.
What to do: Microsoft is aware of the issue and is reportedly working on a fix. But when it’ll be released is unknown.
MS13-100, MS13-013, MS13-105
A few updates for various Microsoft servers
Admins running local MS Exchange 2010 and 2013 servers could see KBs 2903903, 2903911, and/or 2905616 (MS13-105). The patches are rated critical and fix four vulnerabilities by updating Oracle Outside In libraries. Those admins running Exchange 2013 need to be on Cumulative Update 2 to deploy this update, as noted in an Exchange Team blog.
The five patches in MS13-100 (KBs 2850058, 2553298, 2837629, 2837631, and 2910228) impact only SharePoint Server 2010, SharePoint 2013, and Microsoft Office Web Apps 2013.
Application developers will be interested in KBs 2903566 and 2903919 (MS13-103). They fix a privately reported vulnerability in ASP.NET SignalR that could allow cross-site scripting.
 What to do: Deploy these server updates only after testing.
What to do: Deploy these server updates only after testing.
Various nonsecurity updates for December
Once again, Microsoft has released numerous nonsecurity updates on Patch Tuesday, mixing them in with critical security patches. Microsoft lists these nonsecurity updates in the lower half of an MS Support page, and a slew of Office fixes are listed on the Office Updates page. I’ll give my ruling on them at the end of the month in the Windows Secrets Lounge.
 What to do: Please join me for our special end-of-the year Patch Watch cleanup column in the Windows Secrets Lounge. Look in the Windows Secrets Columns section. If there are other security updates I’ve failed to mention, list them in the Lounge and I’ll give my thumbs-up or thumbs-down.
What to do: Please join me for our special end-of-the year Patch Watch cleanup column in the Windows Secrets Lounge. Look in the Windows Secrets Columns section. If there are other security updates I’ve failed to mention, list them in the Lounge and I’ll give my thumbs-up or thumbs-down.
Regularly updated problem-patch chart
This table provides the status of recent Windows and Microsoft application security updates. Patches listed below as safe to install will typically be removed from the table about a month after they appear. For Microsoft’s list of recently released patches, go to the MS Security TechCenter page.
See our “Windows Secrets master Patch Watch chart” post for a more extensive list of recent updates.
| Patch | Released | Description | Status |
|---|---|---|---|
| 2817630 | 09-10 | Outlook 2013 | Skip |
| 2858725 | 11-26 | .NET Framework 4.5.1 | Skip |
| 2813430 | 12-10 | SSL-certification hardening; optional for admins | Skip |
| 2887069 | 12-10 | Windows kernel-mode driver; also KB 2893984 | Wait |
| 2687455 | 07-23 | Office 2010 SP2 | Optional |
| 951847 | 10-08 | .NET Framework 3.5 SP1 | Install |
| 2885089 | 10-08 | MS SharePoint Server; see MS13-084 for complete list | Install |
| 2862152 | 11-12 | DirectAccess | Install |
| 2868626 | 11-12 | Denial of service using X.509 certs | Install |
| 2868725 | 11-12 | Disabling RC4 | Install |
| 2875783 | 11-12 | 64-bit Windows editions | Install |
| 2876331 | 11-12 | Windows Graphics Device in WordPad | Install |
| 2885093 | 11-12 | WordPerfect files; see MS13-091 for complete list | Install |
| 2888505 | 11-12 | Internet Explorer cumulative update | Install |
| 2893986 | 11-12 | Hyper-V installations | Install |
| 2894514 | 11-12 | Outlook; see MS13-094 for full list; issues with KB 2837618 | Install |
| 2900986 | 11-12 | ActiveX killbits | Install |
| 2850016 | 12-10 | Office 2007; also KB 2850022 (Office 2010) | Install |
| 2850064 | 12-10 | Office 2013 — especially Office 365 subscribers | Install |
| 2893294 | 12-10 | Windows Authenticode signature verification | Install |
| 2898715 | 12-10 | Local Remote Procedure Call; XP and Server 2003 only | Install |
| 2898785 | 12-10 | IE cumulative update | Install |
| 2908005 | 12-10 | Office; see MS13-096 for complete list | Install |
| 2909158 | 12-10 | Windows Scripting; see MS13-099 for complete list | Install |
Status recommendations: Skip — patch not needed; Hold — do not install until its problems are resolved; Wait — hold off temporarily while the patch is tested; Optional — not critical, use if wanted; Install — OK to apply.
Windows 8 mice: Pointing in the right direction
Windows 8’s signature feature, touchscreen navigation, is a poor choice for most traditional PC applications.
But new devices nicely blend the familiarity of the classic mouse with the speed of Win8’s new touch-and-swipe commands.
A touchscreen display makes sense on tablets, phones, and similar mobile devices, but it’s a pain — literally, for some users — to use on the desktop. Unfortunately, using a classic mouse with Windows 8’s Metro/Modern user interface is almost equally unpleasant. Win8’s tile-based interface is truly optimized for touch-and-swipe gestures.
Acknowledging that fact, Microsoft, Logitech, and most other mouse manufacturers are now offering hybrid pointing devices: essentially mice with built-in touchpads. Whatever your feelings about touch-and-swipe, these new pointing devices let you live more comfortably within Windows 8’s two computing environments.
Logitech’s stylish, portable, touchmouse
Specifically designed for Ultrabooks and other light laptops that have a traditional screen, the Logitech Ultrathin Touch Mouse T630 (more info) is both portable and adaptable. Equipped with Bluetooth communications and rechargeable battery, the T630 has a smooth top for gesture navigation. But it also retains the traditional point-and-click, drag-and-drop movements I’m accustomed to.
Using the T630 takes a bit of adjustment — especially if you’re used to a full-sized mouse. Its relatively small size — three by two inches — limits control gestures to just your fingertips. It took a couple of hours of use before I became comfortable with the T630, but eventually performing typical Metro navigation gestures felt quite natural.

Figure 1. Logitech's Ultrathin Touch Mouse T630 (source: Logitech)
Logitech equipped the T630 with two Bluetooth channels, allowing it to connect to two separate systems. To switch channels, you simply flip the toggle switch on the mouse’s underside. That’s also where you find the Bluetooth pairing button. Pairing was immediate, and in most cases the T630 automatically reconnected on system startup. When it didn’t, pushing the pairing button quickly got me up and running again.
On most portable devices, the T630’s Bluetooth connection saves precious USB ports. But charging is via an included USB cable. That’s not something you’ll have to do often; my T630 ran for weeks on a single charge. And according to Logitech, if you do run out of power, you can get an hour’s worth of work from a one-minute charge.
When I first connected the T630, I got an automatic prompt to download Logitech’s SetPoint app for mice and keyboards. Although the mouse works without SetPoint, the software adds additional functions and customization settings.
The black-and-chrome T630 lists for U.S. $70. But you can find it online for less. There’s also a white version — the T631 — for Mac users. (The two models differ only in cosmetics.) If portability isn’t important, you can find Logitech’s larger T620 Touch Mouse online for around $28.
Logitech’s touchpad bargain: In the Nov. 21, 2012, Best Hardware column, I reviewed Logitech’s Wireless Rechargeable Touchpad T650 (info), an early solution for systems lacking a touchscreen. The 5.25-inch-square touchpad is a worthy choice for working with Windows 8’s tap-and-swipe commands — all the more so now that its typical online selling price has dropped from $80 to a bargain $35. Check it out.
An inexpensive, Windows 8–centric mouse
Microsoft either had an inkling that millions of Windows users would be miffed with touchscreen computing, or it was able to rapidly design and release its Sculpt Comfort Mouse (info).
At under $40, the 4.4-by-2.7-inch pointer is both a bargain and an excellent compromise for Win8 systems with traditional displays. This is reportedly the first mouse with a Windows button integrated into the body. The blue Windows tab (see Figure 2) let me easily navigate to the Win8 Start screen with a single touch. (When you touch the tab, a slight vibration verifies that it’s ready — a feature you can turn off in Settings.)
Located on the left side of the mouse, the Windows tab is also a convenient navigation control. (Sorry, lefties; you’re out of luck here.) Swiping up or down on the tab scrolls through all open apps. Pausing at any app opens its window in much the same way as Aero works in Windows 7. (The Windows tab works the same way on Win7 machines, too.)

Figure 2. Microsoft's MS Sculpt Comfort Mouse includes a Windows touchtab. (Source: Microsoft)
Aside from the Windows tab, the Sculpt Mouse operates like a conventional mouse but with some Windows 8 optimization. In other words, it doesn’t have a touch surface like the Logitech T630’s. That said, the four-way tilt wheel offers smooth left/right and forward/backward scrolling.
The Sculpt Mouse works well on most surfaces, and (true to its name) its domed shape and right-thumb indent make it feel as if it had been carved for your hand. It’s powered by two AA batteries (alkalines included) and uses Bluetooth to communicate with PCs. If your system doesn’t support Bluetooth, I recommend the ASUS Mini Bluetooth Dongle, available at Amazon for $13.00.
Allow me to express one peeve, though. Typical of Microsoft’s tendency for software bloat, the Sculpt Comfort Mouse’s software requires 150MB of hard disk space. Really? Really!
Looks like a pen, but acts like a mouse
There will undoubtedly be many debates over whether touch-and-swipe or point-and-click causes more repetitive strain injuries (RSI). But the Swedish-based Penclic company claims its Penclic Mouse (info) is ergonomically superior to either of those alternate technologies. The Penclic is a pen-shaped device that’s anchored to a moving base. That design, along with five buttons and a scroll wheel, theoretically provides a more relaxed and natural working position.
The device comes in three versions: wireless USB, Bluetooth, and corded. I tested the Bluetooth B2 model. Bluetooth pairing was quick, and my PC found the device every time I rebooted. Unlike the aforementioned Logitech and Microsoft mice, there’s no additional software to install. The vendor claims that the included NIMH, AAA, rechargeable battery will last about two months between charges. (It can also be powered by five one-time-use watch batteries.)

Figure 3. The Penclic Mouse for tired hands?
As with most mice, the Penclic is designed primarily for right-hand use. Scrolling about with the device was remarkably smooth — no doubt due to its 1200 DPI resolution. But adjusting to its base-side scroll wheel and five buttons on the shaft took this conventional mouse user on a moderately long retraining journey. The forward and back buttons on the side and front of the pen are a good fit, as are the left- and right-click buttons. Using my middle finger to operate the scroll wheel was the most difficult part of the process. But eventually, it was worth the effort.
If you have difficulty using traditional mice, the Penclic is a worthy option. Think of it as a pen you never set down. After testing it for a week, I returned to a traditional mouse — and was quickly reminded of the Penclic’s benefits.
The Penclic Mouse B2 lists for $90 and is available at Amazon.com.
A comfortable backpack has digital power
As we travel with more mobile devices, a backpack has become de rigueur. Better yet is a pack that can also keep our smartphones, tablets, and other devices powered.
The Tylt Energi+ Backpack (info) has some dozen pockets, one of which holds a removable, 10,400 mAh lithium battery — enough juice to recharge a smartphone four times or a tablet once. (The battery constitutes 11 ounces of the pack’s three-plus pounds.) My tests of the pack’s recharging capabilities verified Tylt’s claims.
I’ve had my share of backpacks over the years, and they all had one annoying characteristic: they flopped over when I set them down. The Energi+ has been designed to stay upright when put down.
Inside the pack, there’s a special liner for routing charging cables to the three USB ports (two one-amp ports for phones and one 2.1-amp port for charging tablets). There’s also a headphone pass-through for listening to music or phone calls while walking with the backpack on.

Figure 4. The Tylt Energi+ Backpack both organizes and recharges your digital devices.
The pack is nicely designed for business travel. It has small, easy-access, padded pockets for items such as smartphones and sunglasses. A TSA checkpoint–friendly, soft-lined pocket accommodates laptops up to 15.5 inches. For the true road warrior, there’s also a separate pocket for a tablet. A front pocket provides quick access to documents such as passports and boarding passes.
All that gear gets heavy on a long trip, and it seems that all my flights leave from the farthest gate. Fortunately, the Energi+ has a well-supported strap system, as I learned on a recent excursion.
The pack lists for $200, but don’t expect to pay that when shopping online.
A dangerous proximity to curious bears
 |
Wildlife photographers love their cameras, even — or maybe especially — their robot cameras. Photographers’ subjects can also develop an interest in cameras. Polar bears, in this instance, want to get their paws on the annoying instruments — and sometimes succeed. See the video |
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Office gets current release
by
Susan Bradley
1 hour, 9 minutes ago -
FBI: Still Using One of These Old Routers? It’s Vulnerable to Hackers
by
Alex5723
16 hours, 20 minutes ago -
Windows AI Local Only no NPU required!
by
RetiredGeek
51 minutes ago -
Stop the OneDrive defaults
by
CWBillow
17 hours, 9 minutes ago -
Windows 11 Insider Preview build 27868 released to Canary
by
joep517
1 day, 3 hours ago -
X Suspends Encrypted DMs
by
Alex5723
1 day, 5 hours ago -
WSJ : My Robot and Me AI generated movie
by
Alex5723
1 day, 5 hours ago -
Botnet hacks 9,000+ ASUS routers to add persistent SSH backdoor
by
Alex5723
1 day, 6 hours ago -
OpenAI model sabotages shutdown code
by
Cybertooth
1 day, 6 hours ago -
Backup and access old e-mails after company e-mail address is terminated
by
M W Leijendekker
18 hours, 59 minutes ago -
Enabling Secureboot
by
ITguy
1 day, 1 hour ago -
Windows hosting exposes additional bugs
by
Susan Bradley
1 day, 14 hours ago -
No more rounded corners??
by
CWBillow
1 day, 10 hours ago -
Android 15 and IPV6
by
Win7and10
1 day ago -
KB5058405 might fail to install with recovery error 0xc0000098 in ACPI.sys
by
Susan Bradley
2 days, 3 hours ago -
T-Mobile’s T-Life App has a “Screen Recording Tool” Turned on
by
Alex5723
2 days, 5 hours ago -
Windows 11 Insider Preview Build 26100.4202 (24H2) released to Release Preview
by
joep517
2 days ago -
Windows Update orchestration platform to update all software
by
Alex5723
2 days, 13 hours ago -
May preview updates
by
Susan Bradley
2 days ago -
Microsoft releases KB5061977 Windows 11 24H2, Server 2025 emergency out of band
by
Alex5723
1 day, 16 hours ago -
Just got this pop-up page while browsing
by
Alex5723
2 days, 5 hours ago -
KB5058379 / KB 5061768 Failures
by
crown
2 days, 2 hours ago -
Windows 10 23H2 Good to Update to ?
by
jkitc
1 day, 4 hours ago -
At last – installation of 24H2
by
Botswana12
3 days, 4 hours ago -
MS-DEFCON 4: As good as it gets
by
Susan Bradley
2 hours, 20 minutes ago -
RyTuneX optimize Windows 10/11 tool
by
Alex5723
3 days, 16 hours ago -
Can I just update from Win11 22H2 to 23H2?
by
Dave Easley
1 day, 15 hours ago -
Limited account permission error related to Windows Update
by
gtd12345
4 days, 6 hours ago -
Another test post
by
gtd12345
4 days, 6 hours ago -
Connect to someone else computer
by
wadeer
7 hours, 40 minutes ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

