
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Protecting yourself from POODLE attacks
In this issue
- LOUNGE LIFE: Applying a program to different circumstances
- TOP STORY: Protecting yourself from POODLE attacks
- WACKY WEB WEEK: At work with your feline colleagues
- LANGALIST PLUS: Solving problems with VirtualBox virtual PCs
- BEST HARDWARE: Handy add-ons for enhancing mobile devices
- ON SECURITY: Privacy Badger helps block Web-activity tracking
- WINDOWS 10: Windows 10 Tech Preview now at build 9860
Applying a program to different circumstances
Lounge member saleve volunteers for an NGO that has a really old computer system running XP and Access 2003.
He has Access 2010 and wonders how to adapt the database he’d created for the organization so it works with Access 2003.
The practical Loungers in the Databases forum explain why saleve should do his NGO-database building on the older version of Access.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right into today’s discussions in the Lounge.
Protecting yourself from POODLE attacks
No, this isn’t about Fluffy gone rogue. To keep our online browsing safe, we rely heavily security protocols — the “S” in HTTPS.
But a new exploit — POODLE — shows that commonly used security protocols aren’t as secure as we thought; websites and browsers will both need an upgrade.
Pulling a new trick on a very old dog
By now, it might seem that an exploit is serious only if it has a catchy name attached to it. (I won’t go down the list of clever names; doing so might get Windows Secrets blocked by overly cautious ISPs.) The latest threat is Padding Oracle On Downgraded Legacy Encryption — POODLE, for short. That’s not a name that immediately brings viciousness to mind. As a poodle owner over the years, my greatest worry was being licked to death. But the recently revealed weakness in the Secure Sockets Layer (SSL) protocol that allows the POODLE exploit has the digital-security world worrying about a new round of nasty malware bites.
Perhaps most problematic, there’s no quick patch or easy fix; the flaw is hard-coded within SSL 3.0. As Scott Helme explains on his blog, the “attack, specifically against the SSLv3 protocol, allows an attacker to obtain the plaintext of certain parts of an SSL connection, such as the cookie.”
A note on terminology here: SSL and TLS (Transport Layer Security) are often referred to simply as SSL. However, TLS officially replaced the SSL 3.0 protocol over a decade ago. But like most things on the Web, the SSL 3.0 protocol lives on and is still in widespread use. (See the Wikipedia “Transport Layer Security” page for more details.) In short, the SSL protocols are all vulnerable; the TLS protocols, as far as we know, aren’t.
The POODLE exploit compromises the SSL protocol by forcing the server/browser connection to downgrade its TLS connection to SSL 3.0. That change allows leaks of cookie information, which could then lead to the disclosure of sensitive, personal information.
Fortunately, POODLE is not an easy exploit. It might take an attacker several hundred HTTPS requests before successfully forcing the Web server and a client browser to downgrade to a vulnerable SSL connection. On the other hand, the Web’s patchwork nature gives POODLE exploits an extremely large kennel to work in.
Protecting browsers from POODLE attacks
Most of us have two or more browsers installed on our systems. Unlike a Windows fix, there’s no one patch that will protect our browsers from POODLE. Instead, we must make adjustments within each browser; with Firefox, we must also download and use a Mozilla add-on until a new version of Firefox arrives in a month or so.
Be aware: After making these adjustments, you might find that business websites don’t work properly. So I recommend making the following adjustments to one browser and leaving another browser for those sites that are still waiting for the changes needed to protect themselves from POODLE. (Again, the fix for this exploit has to happen on both ends of Internet connections — the client and the server.)
The following changes force your browser to not use SSL 3.0. Here’s what to adjust in the top three browsers.
Chrome: In Google’s browser, edit the shortcut that launches the browser, adding a flag to the end of the Shortcut path. Start by selecting the icon normally used to launch Chrome. Right-click the icon and select Properties. Under the Shortcut tab, find the box labeled “Target” and insert –ssl-version-min=tls1 immediately after chrome.exe” (see Figure 1). It should look something like this (note the space between .exe” and –ssl-):
“C:\Program Files (x86)\Google\Chrome\Application\chrome.exe” –ssl-version-min=tls1
(Note: If your original Chrome path doesn’t start and end with quotes, don’t add one after chrome.exe.)
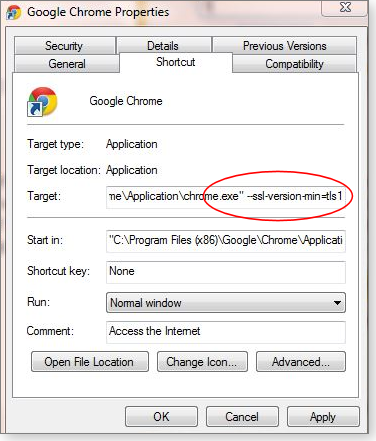
Figure 1. Disable SSL 3.0 support in Chrome by adding a flag at the end of the Properties/Target path.
From now on, launch Chrome only with this edited shortcut. Launching the browser from any unedited launch icons won’t provide protection from POODLE. Consider clicking on the General tab in the Chrome Properties dialog box and giving the edited shortcut a unique name — such as “Chrome – no SSLv3” or something similar. Then you’ll always know you’re using the right shortcut.
Firefox: As noted in the Oct. 14 Mozilla blog post, Firefox 34, due to be released on Nov. 25, will disable SSL 3.0 support. In the meantime, Mozilla recommends installing the add-on (download site), “SSL Version Control 0.2” (see Figure 2), which will let you control SSL support within the browser. (Some websites have recommended adjusting Firefox settings in the configuration file, but Mozilla recommends using the add-on instead.)
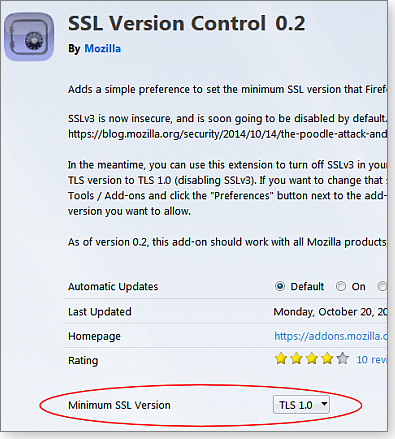
Figure 2. To disable SSL 3.0 support in Firefox, Mozilla offers a browser add-on.
Internet Explorer: In IE, click the gear (settings) icon, open Internet options, and then select the Advanced tab. Scroll down the Settings list to the Security category, and then look for Use SSL 3.0. Uncheck the box (see Figure 3), click OK, and then relaunch IE.
Network admins can make this change to all PCs on the local network via Windows’ Group policy. Go to the Internet Explorer settings and modify the Turn off encryption support object (Windows Components\Internet Explorer\Internet Control Panel\Advanced Page).
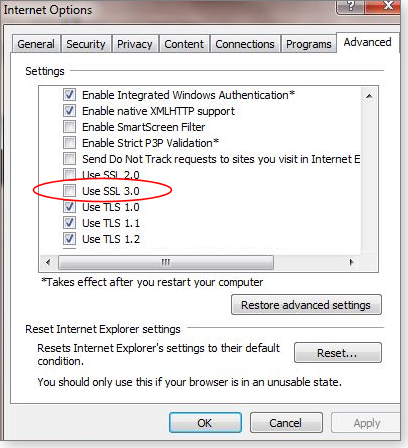
Figure 3. In IE, uncheck "Use SSL 3.0" in the advanced settings dialog box.
Microsoft released an initial security advisory on this topic; expect to see additional guidance in the near future.
How to test your browser’s TLS/SSL protection
Several websites test whether your currently open browser supports SSL 3.0. For a simple test, Poodletest.com displays a poodle dog if your browser still supports SSL 3.0, and a Springfield terrier if it doesn’t. On the other hand, Qualys SSL Labs (site) provides a more detailed analysis of the SSL protocols your browser supports.
As noted above, some business sites such as online banking might still need SSL 3.0. Again, I recommend leaving SSL 3.0 support on one browser; it’ll be faster and safer than repeatedly adjusting browser settings. If you’re running a Web server or small-business server, you should disable SSL 3.0 support to better protect connected workstations and Internet-based phones.
An InfoSec Community Forums Incidents.org page lists how to block SSL 3.0 on various Web-based platforms.
For example, in Windows Server, create (or modify) a Registry DWORD value as follows:
- In your Registry editor, go to:
HKey_Local_Machine\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
- Under the Protocols, create a key called “SSL 3.0.” Then, under that key, create another key called “Server.”
- Create a DWORD called “Enabled” and give it a value of 0.
- Reboot the server; you and any connected clients will now be protected from POODLE exploits.
Compromised cert highlights a system in doubt
POODLE is a clear indication that the TLS/SSL system we rely on needs work. In fact, the entire system of security protocols and certificates could well be a house of cards. For example, HP recently announced that one of its certificates has been used to sign malware. As noted in a Krebs on Security post, HP will revoke on Oct. 21 the certificate it has used for some of the software that shipped with older products. Unfortunately, HP isn’t completely sure what impact that change will have on the ability to restore some HP computers. Look for my future updates on that topic.
Another round in the dogfight over Internet security. As has been widely noted, POODLE effectively kills the SSL 3.0 protocol. Following the aforementioned steps, let’s make sure POODLE’s bark is worse than its bite (sorry, I couldn’t help myself). However, there’s a silver lining to this latest security mess — it should now force everyone on the Internet to finally abandon a dated, insecure protocol.
At work with your feline colleagues
 |
Nothing makes a greater flurry in a home office than a cat — unless you happen to have two cat companions. In this video, Cole and Marmalade show you best practices with regard to pens, printers, keyboards, mice (naturally), file folders, waste baskets, shredders, and all other office furniture — most especially the ergonomic chair. Good thing you have that old folding chair on the side. Click below or go to the original YouTube video. |
| Post your thoughts about this story in the WS Columns forum. |
Solving problems with VirtualBox virtual PCs
Virtual PCs are a complex blend of real and simulated hardware; problems can often be fixed with a step-by-step, refresh-and-simplify approach.
Plus: What to do when Win7 won’t install the useful “Clean up system files” update, and a fix for a near-fatal Win8 Registry problem.
VirtualBox networking (and other) problems
Long-time reader Elaine Marmel encountered a frustrating problem with her VirtualBox setups.
- “I use VirtualBox — or at least I try to use it — so that I can have a separate ‘test PC.’
“My host is a standard PC: a Win7 x64 desktop machine with 8GB of RAM and a wired network adapter connected to a router and cable modem. My guest virtual machine (VM) is a Win7 x32 machine using bridged networking.
“I have no problems with my host machine making network connections. My laptop connects just fine, too. So I don’t think I have any physical equipment problems.
“Recently, the guest VM takes forever to connect to the host. The swirly round thing just keeps on trying, like the Energizer Bunny. I’ve actually seen it take 20 minutes (yes, minutes) to connect. I haven’t made any hardware or software changes to my configuration; this problem just seemed to start over the summer.
“I have hunted in the Internet and VirtualBox forums, and I’ve found a few references to a similar problem. But most of the solutions are over my head — they talk about adding code. I wouldn’t know where to begin with something like that.
“The solutions I understood, I tried. One said to downgrade from Version 4.3.16 to Version 4.3.12. That hasn’t helped. Another site suggested trying a different virtual network adapter, so I tried two others. Neither helped.
“I’m going crazy over this, and my VM is becoming useless. Any guidance on solving this problem would be most appreciated.”
VirtualBox (site) virtual PC setups have three separate and complex layers, each of which is essential. They include the host PC, with its mix of hardware and software; the VirtualBox software itself; and whatever guest operating system you’ve set up inside the virtual machine’s simulated hardware environment.
There can also be a fourth layer: VirtualBox’s add-ons — the Guest Additions and Extension Packs that substantially modify the interactions between the virtual machine and its host.
Over time, each of these layers gets updated repeatedly — and separately. For example, Windows-based host and guest operating systems typically get updated at least once a month, on Microsoft’s Patch Tuesday. Oracle releases new versions of VirtualBox every couple of months or so (see Oracle’s changelog), and there’s typically a new Extension Pack and set of Guest Additions with each new release of VirtualBox.
Over a year, you could be looking at 36 or more major, internal changes to the various components of each virtual-machine setup. And that doesn’t include whatever other custom adjustments or changes you’ve made to the host, the guest OS, and to VirtualBox itself.
In short: VirtualBox setups are not static — they’re in constant, slow, flux. Eventually, they can fail from an accumulation of small problems and incompatibilities.
When things stop working correctly, the fix starts at the top — with the host system.
Make sure your host system is truly trouble-free. Run a good disk-cleanup tool and a reputable Registry cleaner. Run the system file checker (sfc.exe; Microsoft info) to ensure that all system files are intact. Manually run Windows Update to make sure you have all necessary updates. Run chkdsk (MS info for Win7; other versions are essentially identical) to make sure all parts of your hard drive and its files can be accessed correctly and without errors.
Check the health of whatever specific subsystem is causing trouble. For example, if you’re having problems with networking, visit your network adapter’s vendor (not Windows Update) to make sure you have the right drivers and they’re current. Run an antivirus scan to be sure no malware has inserted itself into your network-communications stack.
Refresh and simplify the VirtualBox setup. If your host PC checks out OK, the next step is to clean up VirtualBox. Fortunately, you usually can do this without having to reinstall the guest OSes from scratch. Here’s how:
- In VirtualBox, launch — one at a time — each Windows-based guest VM/operating system you’ve set up. In each guest system, open Windows’ Device Manager and uninstall any hardware that’s caused trouble — for example, the virtual network adapters. Shut down the OS without letting any hardware drivers reinstall.
- Back on the host system, navigate to where your VirtualBox VMs are installed (by default, it’s C:\Users\{your_name}\VirtualBox VMs\). Open each VM folder in turn and copy each guest OS’s hard-drive file (the large file, usually with a .vdi extension) to a safe place.
- Fully uninstall VirtualBox via Windows’ uninstall applet in Control Panel. When the uninstall is done, make sure the C:\Users\{your_name}\VirtualBox VMs\ folder is gone.
- Run a Registry cleaner to clear out any lingering VirtualBox remnants.
- Now reinstall VirtualBox from scratch, using a fresh download from virtualbox.org. If desired, reinstall a fresh copy of the Extension Pack, too.
- Create brand-new, virtual-machine setups, using the same VPC names and settings as before, except for these changes:
When you get to the Storage portion of the setups, don’t create new virtual hard drives. Instead, select the .vdi files you previously saved from your original setups, as shown in Figure 1. (Conceptually, this is equivalent to moving a Windows system hard drive to a new PC!) Note: You can use the .vdi files in their new location or copy them back to the newly recreated C:\Users\{your_name}\VirtualBox VMs\ folder — it’s your choice.

Figure 1. To use an existing virtual hard drive in a new virtual machine, select the third option, click the folder icon, and select the desired .vdi file.
Also, try to simplify the hardware setup in any areas that have caused trouble. For example, in Networking, using VirtualBox’s optional bridging creates a tight linkage between VirtualBox’s virtual network adapters and the host PC’s real, physical adapters. However, this adds considerable complexity to an already complex virtualized subnetwork. (That might be the source of Elaine’s problem.)
In general, I’ve found I get more reliable results by keeping the VM network settings as simple as possible. To avoid “bridging,” I use one of VirtualBox’s other options for enabling file sharing and communications between the host and guest PCs. For example, VirtualBox’s Extensions and Guest Additions add shared folders and clipboard plus two-way drag-and-drop. That makes moving files, folders, and data in and out of a VPC easy — no bridging required.
When I need to print something that’s on a virtual machine, I copy the file to the host and print from there rather than go through the hassle of trying to get a real network printer to talk to a virtualized PC via a half-real/half-virtual, bridged network connection.
Virtual PCs are complex enough without adding unnecessary complications such as network bridging. Keep things as simple as possible!
- When your setup is refreshed, lean, and clean, launch each guest OS, one by one. As a VM wakes up, it will discover and use the new, freshly installed, virtual-hardware components such as the network adapters.
These steps will usually clear things up. The most common speed bump you might encounter is having to reactivate your Windows setups because of changed “hardware.” That process usually takes just a couple of clicks, but sometimes you’ll be prompted to use an alternate method such as Microsoft’s automated, activate-by-phone system. If this happens to you, don’t worry; it’s toll-free from most locations and typically takes less than five minutes. As long as your Windows guest-OS setups were legit to begin with, reactivation won’t be a problem.
If none of the above works, your only option is to bite the bullet and start from scratch. Wipe out the original .vdi hard-drive files and set up the guest OSes anew.
Fortunately, I’ve rarely had to do that. And, with luck, you won’t have to, either!
Win7 “Clean up system files” app remains missing
After reading “Remove tons of obsolete Win Update files” (Oct. 2 LangaList Plus), Jim Haslam tried to get Win7’s optional “Clean up system files” update installed. But he ran into trouble.
- “I was following your article to clean up system files and old updates. I even went back to the Jan. 9 LangaList Plus column, “Clean out obsolete, space-consuming update files.” However, my Windows 7 dialog box didn’t look like yours. I seem to be stuck with the old version of cleanmgr.exe.
“So I used your link to download and install Windows update KB 2852386. However, the installation process stated that KB 2852386 was already installed. Huh?
“I am wondering how I can set up the right [cleanmgr.exe] version, so I can clean up my system files and old updates and regain space, as described in your article. Thanks.”
Sure, Jim. I suggest you start by uninstalling the malfunctioning KB 2852386 update. Then reboot your system, run a good Registry cleaner, and reinstall a fresh copy of KB 2852386 from its info/download page. Note that there are both 32-bit and 64-bit versions of the update — be sure to select the correct bittedness for your system.
For more information on removing an installed update, see:
- “How to correct failed updates and hotfixes” – Jan. 30 LangaList Plus
- “Remove an update” – Microsoft how-to
If even that fails — and I don’t know why it would — then I suggest you try the old-school Deployment Image Servicing and Management method described in two LangaList Plus articles:
- “Shrink that gigantic WinSxS folder down to size” – April 4, 2012
- “More on shrinking Windows’ huge WinSxS folder” – May 2, 2012
Hotfix available for extreme Win8 Registry bloat
Robert Burget seeks to avoid a rare but near-fatal Registry bloat that can affect 64-bit versions of Win8.0 (but not 8.1) and Server 2012.
- “I am told that Windows 8 x64 will not restart if your Registry Hives are larger than 2GB. I understand that Microsoft has confirmed this problem.
“Microsoft states: ‘If you are experiencing this particular issue, then you can download Hotfix 496812 via KB 2978366.’
“My question: Why must we wait for the problem before fixing it?
“I appreciate any insight.”
As you note, when a group of related Registry keys, subkeys, and values — a hive — exceeds 2GB in Win8.0, the PC crashes and can’t be restarted normally.
The simplest way to solve this problem is to upgrade to Win8.1, which doesn’t share that weakness.
You’ll have to upgrade within the next year or so, anyway; Microsoft says Win8.0 users must move to Win8.1 by Jan. 12, 2016, in order to remain fully supported (see Microsoft FAQ).
By the way, fellow contributor Susan Bradley tells me that the Registry bloat problem apparently extends to MS SQL Server 2012. As described in a Rusanu Consulting article, the installer runs essentially forever, generating huge logfiles and Registry entries.
If you’re stuck on Win8.0 for the time being, and especially if you need to use SQL Server 2012, then yes: proactively install the Hotfix patch before you experience trouble.
With or without SQL in play, solving a problem is usually better than patching it. So, if at all possible, upgrade to 8.1 soon (it’s free for Win8.0 users). When you upgrade, this Registry bug — and many of the other problems associated with 8.0 — will be a non-issue.
Handy add-ons for enhancing mobile devices
Downsizing from a full desktop PC to a portable has its charms, but it can also impose some unexpected productivity compromises.
Here are three clever devices that fill the gaps in mobile hardware, plus a device for recording your life on the go.
Wireless keypad makes small keyboards complete
We all know that laptop PCs have their limitations. But when I gave up on a desktop PC in favor of a 13-inch portable, one compromise became obvious almost immediately: I really missed a dedicated numeric keypad. I soon discovered I use that keypad for quick data entry far more often than I’d thought. A laptop’s smaller keyboard just isn’t productive when doing heavy numeric entry into spreadsheets or databases.
Add-on keypads are common, but most are either wired or use a wireless USB connection. Unfortunately, like most laptops, my PC has only three USB ports — all of which are in use. (For adding more USB ports, see the review following this one.) NewerTech’s Wireless Aluminum Keypad (U.S. $49; info) solves that port problem by using Bluetooth to connect to personal computers.
The NewerTech keypad’s aluminum housing and white keys are obviously designed to match Apple’s wireless keyboard. But it works well with any brand of Bluetooth-equipped laptop, tablet, or phone. To add to your productivity, the keypad includes dedicated keys for page-up, page-down, home, end, tab/clear, delete-back, and delete-forward — plus three extra function keys.

Figure 1. NewerTech's Wireless Aluminum Keypad is a handy addition to notebook PCs.
The keypad design makes data input quick and accurate. The keys are well spaced and responsive, a slight tilt makes using the pad more comfortable, and grippy feet keep it from sliding on the desktop. I found Bluetooth pairing always quick. (Pairing was a significant problem with early Bluetooth devices but is much less so today.) The keypad is powered by two AA batteries that should last for ages.
Why not just attach a full-sized keyboard to the laptop? That’s certainly an option, but I like having the flexibility of placing the keypad where it’s more comfortable to use — something that left-handed PC users might appreciate.
A seven-port hub for all USB applications
It seems you can never have enough USB ports — or those you have are in an inconvenient place, as is often the case with desktops. Like many laptops, my Dell portable has just three USB ports. With an external keyboard and mouse, a printer, and a backup hard drive attached, all three ports are occupied. That leaves no convenient way to sync and/or charge my digital camera, smartphone, or tablet.
There are, of course, boatloads of USB hubs to choose from. However, most of those are restricted to USB 2.0 transfer speeds. The selection of USB 3.0 hubs is still somewhat limited.
VisionTek’s Charge & Sync USB 3.0 Seven Port Hub ($55; info) is one of the few hubs I’ve seen that are designed with today’s varied USB applications in mind. It includes four USB 3.0 data ports plus three more that are dedicated charging ports. The two one-amp ports are ideal for recharging low-power devices such as phones; portable speakers; and small, mobile hard drives. The lone two-amp port is for high-power devices such as tablets and some larger, external, battery-powered hard drives. The ports are nicely labeled, so you can quickly attach each device to the correct port.

Figure 2. VisionTek's Charge and Sync Seven Port Hub includes dedicated ports for data transfers and device charging.
Weighing in at less than three ounces, the silver-anodized aluminum hub works well on the desktop and on the road. It can be plugged into AC for high-speed data transfers and high-power charging, or it can be connected to just a PC by its USB cable — in which case you still get high-speed data transfers, but device charging is limited to the four USB 3.0 ports. No drivers are needed for the hub; it’s completely plug-and-play.
All four data ports are backward-compatible with USB 2.0, and LED indicator lights show which data ports are in use. At $55, the Charge & Sync isn’t the cheapest seven-port USB hub you can find, but it’s uniquely convenient. The package includes a 39-inch USB 3.0 cable.
Wireless speaker — all sound, no fury
If the underside of your desk is anything like mine, you have a Gordian knot of wires; trying to match the right cable with the right device is infuriating. In this case, the solution is to simply eliminate cables wherever you can — sometimes in surprising ways. For example, add stereo computer speakers that need neither audio cable nor AC adapter.
There are now a zillion Bluetooth speakers on the market (and I’ve probably looked at half of them), all designed to stream music from portable devices such as cell phones and tablets. But with Bluetooth connectivity increasingly on both laptops and desktop PCs, why not apply the advantages of mobile technology to the desktop?
Boombotix’s whimsically shaped, hexangular Boombot REX ($60; info) is only 3.3 inches wide by 2.1 inches deep, so it takes up almost no space on my desk. But packed within that small box are two full-range speakers and a passive bass woofer that deliver surprising power (loudness). Playing music, the REX had clear, crisp treble and bass, and subdued midranges.
Designed primarily for connection to mobile devices, the REX includes a noise-canceling microphone for hands-free phone calls. On my PC, it worked equally well as a speakerphone for Skype calls.

Figure 3. The 3.3-inch Boombot REX delivers surprisingly powerful sound and doubles as a speakerphone (without the phone).
Four buttons on top of the speaker let you adjust volume, play or pause audio, change music tracks, and turn the speaker’s power on or off. In my tests, Bluetooth pairing was nearly automatic. For those times you want music on the road, the REX has a soft-touch, ruggedized case and is water-resistant.
The REX comes in a variety of colors, and the kit includes a USB charging cable. (Now they need to perfect wireless recharging.) Recharge time is about an hour, and you get around eight hours of audio. Although I don’t want yet another cable on or under my desk, an included three-foot auxiliary audio cable lets you connect REX directly to a PC or other device — or to a second REX for better stereo separation.
Boombotix has generously supplied me with an extra speaker to give away to the first reader who claims it by emailing his or her name and shipping address. Send your entry to windowssecretsgiveaway@gmail.com.
Dash camera records more than your drives
When I tested Cobra’s CDR 900 Drive HD Dash Cam with Wi-Fi ($250; info) and later viewed its video to my PC, I immediately recalled Mae West’s legendary line, “Keep a diary, dearie, and someday it will keep you.” That’s quite true of the Dash Cam. As was made abundantly clear from the last big meteor strike over Russia, you have evidence of every event that occurs in front of your car — interesting or bad. Or you can just have a nice video diary of that epic road trip.
Cobra’s two-inch-square Dash Cam is similar to those seemingly ubiquitous GoPro HD action cameras (site), but it’s designed mostly for the car. It comes with a self-mounting pedestal, a USB cable, and a power adapter that plugs into a vehicle’s 12-volt port (aka cigarette lighter). The camera’s battery can also be recharged via a PC’s USB port.
The Dash Cam’s lens covers 160 degrees without obvious edge distortion. You can record in a continuous loop or have recording triggered by motion detection. The camera supports up to Super HD (2304 by 1296 pixels) and 30 frames per second. There is, of course, a built-in microphone; mine was set to mute by default. Video is stored on a MicroSD card, with a maximum capacity of 64GB. (An 8GB card is included to get you started.)

Figure 4. Cobra's Dash Cam records your automotive journeys.
The camera can be used as a simple camcorder, but its built-in Wi-Fi lets you stream live or recorded footage directly to an iOS or Android device. An app also lets you remotely command the camera or even change its advanced settings. The camera has a USB 2.0 port (USB 3.0 would have been better) and a mini-HDMI connector for transferring videos and video playback. You can also insert the MicroSD card into your computer.
Fortunately, my road trips were uneventful. But the Dash Cam let me keep my eyes on the road and enjoy the scenery later. And if I had been involved in an accident, I might’ve had useful evidence for my insurance claim.
Privacy Badger helps block Web-activity tracking
Tired of being deluged with advertisements for chainsaws wherever you go on the Web, just because you searched for one on Home Depot’s site?
Or ads for shoes, dishware, pet food, or whatever? You can’t totally eliminate Web tracking, but you can reduce it.
One webpage leads to many third-party domains
By now, only the most naive PC users don’t know that online marketers track where we go, using that information to inundate us with targeted advertising.
But the extent of that tracking isn’t as well known. For example, simply viewing a particular website — not clicking any links — can give marketers and others a surprising amount of your detailed and possibly deeply personal information. When you load a new webpage, the online server for that page will know, at a minimum, your IP address, the date and time the page was requested, and the webpage you were on when you made the request for the new page. But those who run Web servers can gather — and share — much more.
Visit Home Depot, Facebook, Google, or any other site, and your personal information isn’t retained just by that specific organization. Data points collected about you and your browsing habits are often shared with numerous third parties (i.e., other domains) — typically for targeted advertising.
Much of this information can come from your own PC. When you download a webpage, you often get numerous cookies. Some of them are tracking cookies or other types of cookies that contain activity-tracking code. Keep in mind that not all Web cookies are bad. General cookies typically store information that will make it faster and easier to visit a site you like. (That information could, however, include passwords and credit-card numbers.)
Tracking code — whether in a separate cookie or embedded in other cookies, Flash code, or JavaScript — is typically loaded along with the ads displayed on a webpage. “Displayed” is the operative word here; tracking cookies are downloaded, even though you haven’t clicked an ad. Moreover, most cookie activity is hidden from website visitors.
You might assume that tracking cookies can gather only information about your recent Web activity — where, when, and what you clicked. It’s not as if they could send your name, address, and phone number off to some anonymous third party! Sorry, but that’s a faulty assumption. Sophisticated Web trackers can match your computer’s identity (your IP address) with your browsing history and other activities online and send it to various online services that deliver ads to webpages. (Today’s online ads rarely come from the same Web domain that’s providing the content you actually wanted to see.) That sharing of user identity and activity lets ads follow you around the Internet.
Your information can also be matched with other data collected about you, such as personal information you provided on social-networking sites. For example, if you sign in to Facebook and then move on to browse a few other websites, you’ve probably left a trail of information accessible to a variety of parties — advertisers, security agencies, or even unscrupulous individuals who want to steal your identity.
And it can get worse if you’ve allowed software or websites to use your location information. Get directions on Google Maps, and the service knows where you are and where you’re going. It can even track how you got there.
Controlling the glut of website cookies
Modern Web browsers typically give you some control over cookies — whether they’re loaded, how long they can stay on your PC, and so forth. But many websites require a cookie to be active while you’re on the site, so it’s impractical to simply block them all. More problematic: browsers don’t offer tools for specifically blocking tracking cookies. That task has been left to a few add-on programs. In the Aug. 8, 2013, Top Story, “Add-ons that help browsers block Web trackers,” I took a look at three such products: Disconnect, DoNotTrackMe, and Ghostery.
Recently, the Electronic Frontier Foundation released Privacy Badger (download site), a mostly hands-off option for blocking trackers. Officially, Privacy Badger is still in beta, though it’s readily available and seems stable.
EFF’s new tool differs from other tracking blockers in three fundamental ways. First, it doesn’t simply look for signs of personal data going to a specific list of tracking domains and then block the exchange. Instead, when you load a webpage, Privacy Badger keeps track of all content downloaded for a specific page. It then checks whether cookies, beacons, scripts, ads, or some other sources continue tracking you as you move to other sites. If it detects that activity, it then blocks the tracking source. (See the FAQ notes at the above Privacy Badger link.)
Second, Privacy Badger is more hands-off than any other blocking program I’ve tried. In fact, it requires no configuration at all.
Third, Privacy Badger has a “feel-good” quality because it’s offered by the EFF — a highly respected nonprofit dedicated to defending civil liberties in the digital world. The EFF has a high level of trust.
After you add Privacy Badger to a Firefox or Chrome browser, you’ll see a red octagon with a badger’s head inside, located on the far-right side of the browser’s toolbar. With Chrome, the icon will also display the number of trackers found on the current page. Unfortunately, that feature has yet to find its way into the Firefox version. (Internet Explorer and Apple’s Safari are currently incompatible with Privacy Badger’s technology.)
When you click the icon, Privacy Badger displays a list of detected trackers. Next to each tracker is a slider bar (see Figure 1) that changes from green to orange to red as you move it from right to left.
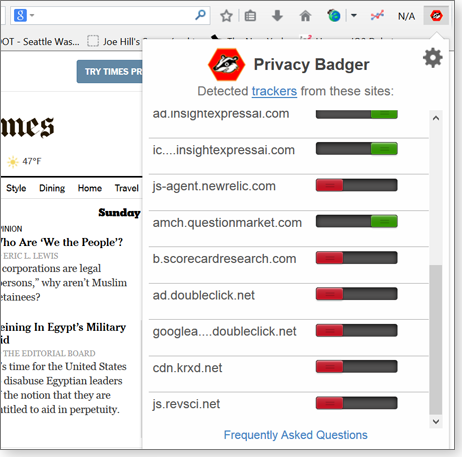
Figure 1. Privacy Badger makes it easy to see which trackers are running and what their status is. You can change that status by dragging the slider to the left or right.
A green slider means that a third-party domain was detected on the current webpage but it doesn’t appear to be tracking you. So it isn’t blocked.
A yellow slider means that Privacy Badger has detected tracking activity, but the domain is whitelisted by Privacy Badger — the domain is delivering content needed for the page to display properly. For example, images on the page might be delivered by a third-party image server. In such cases, Privacy Badger will still screen out cookies from that domain.
A red marker means that all content from the tracker has been blocked.
One potential problem with Privacy Badger: Its interface doesn’t make clear that all trackers are not initially blocked. If you click on the Privacy Badger icon, all detected tracking domains will have green sliders. Privacy Badger changes their status only when it sees them tracking you across websites. If you don’t know that, you might suspect Privacy Badger isn’t working.
As the Chrome version makes clear — but the Firefox version doesn’t — users can change the status of each tracker by moving its slider. Moreover, you can also disable Privacy Badger for a specific site or for all sites. To do so in Firefox, you must click on the gear icon in the Privacy Badger dropdown display. You’ll then see the simple dialog box shown in Figure 2. Chrome puts those two options front and center.
(In Firefox, if you want to report a Privacy Badger bug or see what others have reported, click the “Report a bug” box. However, that option doesn’t appear in the Chrome version.)
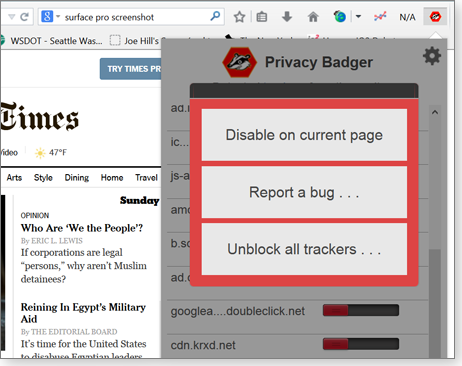
Figure 2. Privacy Badger's options for disabling the tool in Firefox
Another possibly questionable feature of Privacy Badger is that it automatically checks the Do Not Track policies of all blocked sites every 24 hours. If the site’s policy has been changed to match EFF’s privacy policy, the site will be unblocked. However, having Privacy Badger connect to tracker sites could deliver header information about the user. But equally important, unblocking a tracking site just because a site claims to have changed its privacy policy is not a reassuring practice.
Nevertheless, if a domain’s tracking behavior continues, it’ll get blocked — regardless of its privacy policy. (EFF hasn’t responded to my request for information on whether this process continually repeats.)
Privacy Badger’s developers have also stated that they expect to fill two other gaps in the tool’s implementation: first-party privacy protections and browser fingerprinting. For the former, that means blocking tracking by those running the site you’re visiting (as opposed to tracking by third-party domains). The latter refers to keeping sites from detecting your browser configuration. If you have an unusual configuration, trackers might use that configuration as a “fingerprint” to identify your presence on other sites.
According to EFF, it’s also working on Privacy Badger versions for Opera and Firefox Mobile. (As noted above, the techniques employed by Privacy Badger are incompatible with Safari and Internet Explorer.)
Privacy Badger might lead the field in ease of use, but it’s difficult to compare its tracker-blocking effectiveness against similar applications. To some extent, each app has its own way of reporting on tracking activity. Some list the number of requests to external domains detected on a page; others report the names of detected trackers — and those names don’t always match up, either. One program might report Google as a single tracker while another will break it down by individual Google products. You might, for example, see DoubleClick but no indication that it’s a Google product.
In addition to the difficulty in comparing results across tracking blockers, none of the products described above provides complete assurance that all trackers are being identified and blocked.
Still, I found Privacy Badger to be as effective as my previously preferred program — Disconnect (site) — in keeping my browsing experience free of targeted advertising.
A web of connections behind the connections
Here’s a tool that might just persuade you to give up on the Internet altogether. If you’re curious about just how wide the third party–tracking net is cast, install the Lightbeam add-on for Firefox and/or Chrome. As you visit websites, Lightbeam notes the places you’ve visited and graphically displays all the many third-party domains those sites are connected to (see Figure 3).

Figure 3. Lightbeam graphically displays how far and wide your online personal information might be shared.
For example, after I visited just four popular sites — the New York Times, Windows Secrets, the Seattle Times, and Google (which is difficult to avoid), Lightbeam reported that I’d connected to 111 third-party sites. In another session, visiting the NYT connected me to go.com, a Disney interactive site. Go.com, in turn, was connected to 26 other sites.
That’s just frightening.
Windows 10 Tech Preview now at build 9860
Microsoft has released an update to its Windows 10 Technical Preview; build 9860 includes a few new goodies.
It’s been only three weeks since Microsoft released the original build 9841, but the quantity of improvements in that short time is extraordinary.
How to get the latest Windows 10 build
If you installed the original Windows 10 Technology Preview, you might already have build 9860. It’s being gradually pushed down the automatic Windows Update chute. Yes, “Install updates automatically” is turned on — that was part of the agreement when you signed up for the Windows Insider Program, a prerequisite to installing the beta bits. (For more on installing the new OS, see Fred Langa’s Oct. 16 Top Story, “How to safely test-drive Win10 — step by step.”)
As with all automatic Windows updates, not everyone gets the bits at the same time. To determine whether you have build 9860, check the watermark in the lower-right corner of the desktop, just above the notification area. If it doesn’t say “Evaluation copy. Build 9860,” you can accelerate things a bit by clicking (or tapping) Start/PC Settings/Update and Recovery/Preview Builds. Click the Download now button and work your way through the installation process.
(If you’re using VirtualBox, make sure Win10’s virtual machine has a minimum of 2GB of RAM; anything less might give you an error message. Also, make sure build 9841 is fully up to date — including a reboot to finish any Windows Update installs.)
Build 9860 is not a svelte install — the download is anywhere from 2.1GB (32-bit) to 2.74GB (64-bit). That’s followed by a long install, an extra installation step, and a reboot that takes forever. The installer then restores all your Metro/Universal apps — and heaven only knows what else.
When you eventually get to sign in for the first time, you get the “Hi” introduction all over again. Oh, boy! If you have a fast Internet connection and a robust PC, expect to spend more than an hour getting the new build running. If you’re running Win10 in a virtual machine, double or triple that estimate.
Unfortunately the official word from Microsoft is that there will be no ISOs released for a clean install. The only way to get build 9860 is by first installing the original Windows Technical Preview and then upgrading. Ouch!
A quick guided tour of what’s new in build 9860
As usual, Microsoft has its own ideas about what’s important. So you should start by reading Gabe Aul’s party-line introduction on the Oct. 21 Blogging Windows post, “We’re rolling out our first new build to the Windows Insider Program.” When discussing the new features, Gabe starts with the new notification center, which Microsoft now calls the “Action Center” — thoroughly confusing anyone who’s used the completely different Action Center in Windows 7 or 8.
He then briefly mentions the keyboard shortcut — Win + Shift + arrow — that moves apps from one monitor to another. (No, there’s still no easy way to snap apps with a mouse in a multi-monitor setup.) Gabe next notes the new animation that tells you when you’re switching among multiple desktops — a feature I find so subtle, it’s basically nonexistent.
So with the official upgrades out of the way, here’s what I’ve found interesting.
Merging phone and desktop environments: Three Windows Phone apps are apparently being ported to Windows 10.
The Action Center, mentioned earlier, appears in this build as a simple white box that appears when you click on the New Notifications icon, down in the system tray (“Notifications” in “Action Center” — it will be confusing).
This feature is supremely uninteresting at this point. It lists only the notifications that currently zoom by in Windows 8, never to be seen again. But there are well-founded rumors that Action Center/Notifications will soon grow some Windows Phone–like smarts, including the ability for programs to set actionable links in their notifications — plus your ability to stifle programs that are “notifying” excessively.
New to build 9860, Battery Saver appears as an option in the PC Settings window. As you might imagine, Battery Saver can change certain hardware settings, on the fly, to minimize battery use. But in this build, your only choices are “On” and “Off.” Apparently, similar to Windows Phone, Win10’s Battery Saver will cut off automatic synching when the battery’s feeling a bit peckish. No doubt there are more power-management tricks in store. Whether Battery Saver works better than its equivalents in Windows 7 and 8 remains to be seen.
The third Windows Phone migrant — Data Sense — tracks the amount of data going into and out of the system over both Wi-Fi and cellular connections. I imagine some people will find this useful; however, checking directly with your carrier’s website should give a more accurate view of your data bill. Some forward-looking carriers might come up with small Metro/Universal apps that sit on your desktop and let you watch your funds drip away.
If you’re interested in fast-tracking Windows 10 Technical Preview updates (really, would you be reading this if you weren’t?) in build 9860, click Start/PC Settings/Update and Recovery/Preview Builds. Then, at the top, switch the default Slow delivery of updates to Fast. I suggest you read the details about Win10 development’s “ring progression” in Gabe’s blog. Getting new builds sooner has obvious liabilities, but I bet you’ll end up doing it anyway. (Extra points if you realize that Firefox and Chrome have been doing something similar for years.)
Apparently, some Win10 reviewers are excited about the new “pop” animation when you open a window — but then some people can always be wowed by a new icon color or some other minor change. If you want to see this feature in action, check out Brad Sams’s Neowin post.
What’s (probably) broken in build 9860
In build 9860, some Win10 pieces have gone “backwards” (to use Gabe’s terminology). For example, joining a Wi-Fi network is harder in build 9860 than it was in build 9841. His blog post identifies other known problems.
There’s an entry on the All Apps list called DockingController which presumably will help manage docking stations. As best I can tell, it isn’t working. Similarly, an entry called zPC Settings seems to point to a new build of the PC Settings applet — but there’s little in it that rings any chimes.
One other glitch: I haven’t been able to set a picture password in this build. My old build 9841 picture passwords didn’t carry through in the update. On the other hand, I’ve seen screen shots that mention picture passwords — so the jury’s out on that issue.
The future’s so bright, you wanna wear shades
With apologies to Timbuk 3, Microsoft’s party line states that 7,000 improvements were made between builds 9841 and 9860. No doubt that’s true — Windows 10 is a work in progress — but the changes you can see are fairly limited. In many cases, they’re just stubs of features yet to come.
That’s OK. Microsoft’s obviously working fast and hard to bring out an improved version of Windows. I’m quite confident that Windows 10 will be a worthy successor to Windows 7 — and the final nail in Windows 8’s coffin.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Ascension says recent data breach affects over 430,000 patients
by
Nibbled To Death By Ducks
19 minutes ago -
Nintendo Switch 2 has a remote killing switch
by
Alex5723
40 minutes ago -
Blocking Search (on task bar) from going to web
by
HenryW
5 hours, 20 minutes ago -
Windows 10: Microsoft 365 Apps will be supported up to Oct. 10 2028
by
Alex5723
10 hours, 28 minutes ago -
Add or Remove “Ask Copilot” Context Menu in Windows 11 and 10
by
Alex5723
10 hours, 34 minutes ago -
regarding april update and may update
by
heybengbeng
12 hours, 4 minutes ago -
MS Passkey
by
pmruzicka
8 hours, 8 minutes ago -
Can’t make Opera my default browser
by
bmeacham
19 hours, 44 minutes ago -
*Some settings are managed by your organization
by
rlowe44
6 hours, 27 minutes ago -
Formatting of “Forward”ed e-mails
by
Scott Mills
18 hours, 38 minutes ago -
SmartSwitch PC Updates will only be supported through the MS Store Going Forward
by
PL1
1 day, 14 hours ago -
CISA warns of hackers targeting critical oil infrastructure
by
Nibbled To Death By Ducks
1 day, 23 hours ago -
AI slop
by
Susan Bradley
13 hours, 25 minutes ago -
Chrome : Using AI with Enhanced Protection mode
by
Alex5723
2 days ago -
Two blank icons
by
CR2
12 hours, 21 minutes ago -
Documents, Pictures, Desktop on OneDrive in Windows 11
by
ThePhoenix
2 days, 9 hours ago -
End of 10
by
Alex5723
2 days, 12 hours ago -
Single account cannot access printer’s automatic duplex functionality
by
Bruce
1 day, 10 hours ago -
test post
by
gtd12345
2 days, 18 hours ago -
Privacy and the Real ID
by
Susan Bradley
2 days, 8 hours ago -
MS-DEFCON 2: Deferring that upgrade
by
Susan Bradley
10 hours, 40 minutes ago -
Cant log on to oldergeeks.Com
by
WSJonharnew
2 days, 22 hours ago -
Upgrading from Win 10
by
WSjcgc50
1 day, 10 hours ago -
USB webcam / microphone missing after KB5050009 update
by
WSlloydkuhnle
1 day, 13 hours ago -
TeleMessage, a modified Signal clone used by US government has been hacked
by
Alex5723
3 days, 14 hours ago -
The story of Windows Longhorn
by
Cybertooth
3 days, 1 hour ago -
Red x next to folder on OneDrive iPadOS
by
dmt_3904
3 days, 16 hours ago -
Are manuals extinct?
by
Susan Bradley
16 hours, 33 minutes ago -
Canonical ditching Sudo for Rust Sudo -rs starting with Ubuntu
by
Alex5723
4 days, 1 hour ago -
Network Issue
by
Casey H
3 days, 12 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

