
|
There are isolated problems with current patches, but they are well-known and documented on this site. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Putting Registry-/system-cleanup apps to the test
In this issue
- INTRODUCTION: Windows Secrets reader survey posted
- TOP STORY: Putting Registry-/system-cleanup apps to the test
- WINDOWS SECRETS: The ultimate guide to fixing Windows 7 problems
- LOUNGE LIFE: Fortunate exchange between Scotland and Earth
- WACKY WEB WEEK: Wily dog takes over the beautiful game
- LANGALIST PLUS: Can Windows 7's XP Mode be uninstalled?
- INSIDER TRICKS: Find out where that e-mail really came from
- PATCH WATCH: UDP networking ports threatened by TCP/IP flaw
Windows Secrets reader survey posted
 By Tracey Capen
By Tracey Capen
Windows Secrets’ most important mission is providing our many subscribers with useful information about Windows and Windows-related topics.
Once or twice a year, we post a Windows Secrets reader survey to ensure we’re delivering the content you need.
We all know that PC technology is constantly evolving — sometimes faster than we’d like. Just within this year, Windows 7 has established itself as the Windows of choice. We’ve also seen the rapid rise of online services, such as Cloud computing, and new platforms, such as tablet computers. New and more sophisticated security threats appear regularly. So keeping up with the latest changes in PC technology is a constant, continuing task.
As always, we aim to help you make personal computing fun, productive, and safe. We (the Windows Secrets editors and all the newsletter’s outstanding contributors) hope we have accomplished that task through 2011 and will continue to do so in 2012.
To help make Windows Secrets a valued news source throughout the next year, I invite all Windows Secrets subscribers to fill out the survey. It’s an important resource for planning our future newsletters.
Reader participation is key to the survey’s usefulness. So please fill it out when you have a few spare minutes. It will take you less than five minutes. Click this link to go to the survey.
Thanks to all our subscribers for your continuing support. Without you, there is no Windows Secrets Newsletter.
Tracey Capen
Editor in chief
Putting Registry-/system-cleanup apps to the test
 By Fred Langa
By Fred Langa
The most contentious software category has to be PC-system/Registry cleaners. Some users find them invaluable; other users consider them worse than useless.
A series of controlled experiments puts these apps to the test — and turns up some surprises.
Many Windows programs are still sloppy about their uninstall process, leaving behind digital debris. In older versions of Windows, this situation was a known cause of trouble.
Leftover, “orphaned” files waste space on your hard drive and create extra work for Windows when it performs indexing, searching, defragging, backups, or other file-related operations.
Leftover Registry entries similarly inflate the Registry — to no useful purpose. Erroneous Registry entries can create system instabilities and crashes, and a bloated Registry might needlessly slow down system startup and shutdown.
Registry- and system-cleaning software is designed to correct these problems by finding and removing orphaned files, useless Registry entries, and other junk. The end result is supposed to be a leaner, cleaner, more stable system.
There’s plenty of anecdotal evidence to suggest that cleanup software can do what it claims. But most of this information derives from older versions of Windows, which were notorious for not cleaning up after and policing third-party software.
Windows 7, on the other hand, has more self-protective features than any previous version of Windows. So, are Registry- and system-cleaning tools still worthwhile in a Windows 7 world? I decided to find out.
Designing the tests and the baseline system
First, let me be perfectly clear about this report: my tests were not designed to find the best Registry cleaner — or even a comparative analysis of one cleanup tool versus another.
My sole point was to see whether the general principles of system and Registry cleaning deliver quantifiable, measurable improvements to Windows 7. Do specialized cleanup tools really let you remove more junk than Windows 7’s own built-in tools? Do system and Registry cleanups provide any real-life, practical benefits, such as faster boot times?
To find out, I started with a known-good, plain-vanilla, up-to-date, fully normal Windows 7 setup in an Oracle VirtualBox (site) PC. (See Figure 1.) VirtualBox systems can be cloned easily, which meant I’d be able to use exactly the same system as a starting point for different cleaning tests.
Figure 1. The test system was a plain-vanilla, minimalist Windows 7 VirtualBox setup with very little extra software installed, as shown.
Because this system was to be the starting point for all that followed, I documented several key variables.
First, I timed how long the unmodified system took to boot. I used a stopwatch to measure the time from the moment I switched on the system to the initial appearance of the Windows sign-on password dialog box. I then paused the stopwatch and entered my password. On hitting Enter, I restarted the stopwatch and continued timing to the point of full boot; — when the full, normal Windows desktop appeared and the system was stable and ready for use.
I also timed how long the system took to turn off — from the moment I clicked Shut down on a stable, idle system to all lights out.
I ran the tests several times in succession, with a full power-off shutdown in between, and then I averaged the results to help smooth out any human timing errors or other random variables.
These initial timing numbers would let me see whether my cleaning experiments would have any effect on startup and shutdown.
I measured the size of the test system’s Registry by exporting its full contents (via Windows’ Registry editor, Regedit) to a text file and noting the size of the file. I also used Windows Explorer to record the aggregate size of all the files on the hard drive.
These Registry-size and file-size numbers would let me see the effects, if any, of various cleanup techniques and tools, regardless of what the tools themselves might report. (Many cleanup tools tend to overstate their own effectiveness.)
Looking for trouble: adding 20 popular downloads
With the baseline measurements established, my next step was to create a system with lots of orphaned files. That meant installing and uninstalling applications that might leave digital detritus. To choose software commonly used by real-world users, I consulted CNET’s list of the “20 most popular Windows downloads.”
I installed all 20 apps on the test system as inexperienced Windows users might over time — layering on the software without regard to consequence and accepting all default settings, including the offers of extra toolbars, download managers, and so on.
As you’d expect, the system ended up a mess. (See Figure 2.) After loading the programs, Windows was much less responsive; several subsystems (Internet and sound, for example) stopped working entirely.

Figure 2. Installing 20 popular apps brought Windows to its knees.
I measured the boot/shut-down times and file sizes on the bloated system. Incredibly, the time for a full boot went from under a minute (39 seconds) on the clean system to almost 10.5 minutes (629 seconds) for the bloated configuration. The Registry ballooned 170 percent — from 99MB to 169MB. Table 1 shows the results.
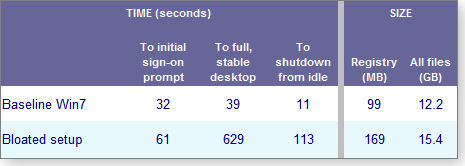
Table 1: Adding 20 popular downloads to the test system created a bloated setup whose full boot time went from 39 to 629 seconds — over 10 minutes!
Removing the bloat: Uninstalling the 20 apps
As planned, the test system was now desperately in need of cleanup.
The first step to clean any bloated system is to simply uninstall unneeded software. I uninstalled each of the 20 programs in the normal way — using the control panel’s Uninstall a program applet. This removed much of the bloat — as it should — and also resolved whatever conflicts had caused the sound and networking failures.
My next round of timing and size measurements showed that, as happens all too often in the Windows world, uninstalling programs left behind various files and Registry settings — it did not fully restore the test system to its initial condition.
Table 2 shows the results. After standard uninstallation of the popular software, the test system did not regain all its initial startup and shutdown speed. Also, 1.4GB of orphaned files and 6MB of Registry entries were left behind.
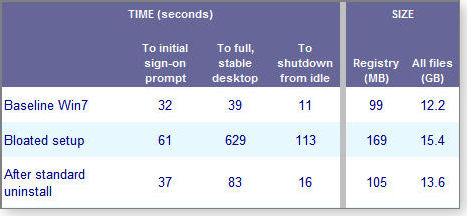
Table 2: After I uninstalled the sample apps, the test system still contained leftover files and suffered from reduced performance.
I was now ready to see what the cleanup tools could do.
Windows Disk Cleanup versus third-party cleaners
I had planned to run three different cleaning tests (I’ll explain them in a moment), so I cloned three, identical copies of my test system. These cloned systems would give each of my clean-up tests precisely the same starting point.
On the first cloned setup, I downloaded and ran the standard edition of Piriform’s free CCleaner (site), an immensely popular and easy-to-use system- and Registry-cleaning tool. (See Figure 3.)

Figure 3. Piriform’s CCleaner is designed for quick, easy, and routine removal of junk files and useless or broken Registry entries.
I chose CCleaner because I’d recommended it many times in the past and wanted to see whether my recommendations still held. CCleaner also represents a class of tools primarily intended for frequent, routine cleanups rather than a deep, targeted spelunking of the system’s internals.
I ran CCleaner’s file and Registry cleanup routines in their default settings, letting the software decide what to clean on the test system. I then rebooted the system and made new timing and file-size measurements. I’ll discuss the results in a moment.
On the second cloned setup, I downloaded and ran Macecraft’s jv16 PowerTools 2011 (site; free, fully functional trial for 50 days, $30 thereafter). This software represents a heavier-duty class of tools that can do routine cleaning but also offers much more power and configurability for expert users.

Figure 4. Macecraft’s jv16 PowerTools 2011 includes features and functions aimed at advanced users.
Using jv16 PowerTools’ default settings, I ran its Registry Cleaner, Registry Compactor (a type of tool unavailable in CCleaner), and File Cleaner. I then rebooted the system and recorded times and file size.
On the third, identical clone setup, I used Windows’ built-in Disk Cleanup app, a system-cleanup tool that’s been included in every version of Windows from Win98 onward. (You can enter cleanmgr into the Search programs and files box to access the tool in its most basic configuration.) Win7’s Disk Cleanup is actually surprisingly powerful and complete; it’s one of those unheralded tools that have been quietly improved with each iteration of Windows.
I’ve always found Disk Cleanup to be safe and reliable, but Microsoft — in an abundance of caution, perhaps — has always made Disk Cleanup’s most potent cleaning functions a little hard to get at. In fact, to use the tool to its best effect, you have to enter cleanmgr in a Command Prompt window or from a command line, and that’s what I did. When run that way, Win7’s Disk Cleanup is actually surprisingly powerful and complete; it’s one of those unheralded tools that have been quietly improved with each iteration of Windows.
Disk Cleanup’s basic commands haven’t changed in almost a decade, and long-time readers may recall the April 4, 2002, article, “Sageset unlocks CleanMgr’s power.” The how-to instructions in that story still work perfectly in Windows 7.
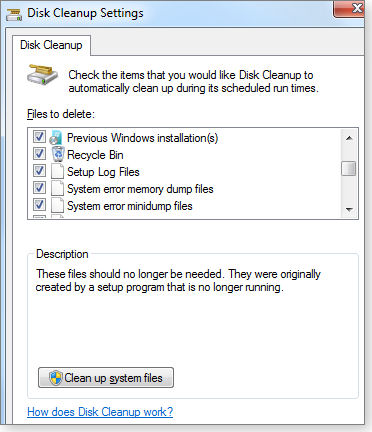
Figure 5. Windows 7’s built-in Disk Cleanup can delete about 20 different kinds of junk files.
I ran cleanmgr exactly as described in that article. When it was done, I rebooted the system and again noted the startup and shutdown times, the Registry size, and the overall disk space used — just as I’d done with CCleaner and jv16 PowerTools.
Table 3 shows the results of these tests.

Table 3: All three tested cleanup methods reduced bloat and helped improve system performance.
These results make it clear that Windows 7 can indeed benefit from use of cleanup tools!
Bottom-line conclusions and caveats
The primary takeaway from these tests is that use of any cleanup tool — even the free, built-in cleanmgr — can help fight bloat and improve your system performance over what you get if you simply uninstall an application.
Although I was surprised that no tool removed all the junk files and leftover Registry entries, they all — even the lowly cleanmgr, if launched from a command line with all its cleanup options enabled — reduced the startup and shutdown times to those of my original, clean system.
The real surprise? jv16 PowerTools actually made the cleaned-up system slightly faster than the original, unmodified, baseline machine! It seems that use of a more advanced tool can yield greater benefits than using simpler, less-powerful tools.
But while system cleanup clearly is worthwhile, I urge you not to get carried away, obsessing over a few seconds of speed or a bit of extra disk space. Reducing boot time from 629 seconds to 32 seconds (by uninstalling unneeded software) is truly worth pursuing; going from 32 seconds to 33 seconds (for cleanmgr) or 30 seconds (for jv16 PowerTools) is almost meaningless in real life.
And although I encountered no problems from use of the cleaners in the above tests, it must be said that the more advanced, expert-level cleaning tools can royally mess up a system if they’re used improperly or too aggressively.
So don’t risk destabilizing a solid system for a trivial gain. Stay within your own comfort and skill zone — and always, always, always make a backup before using any cleaning tool.
For me, the bottom line is this: I’ll continue using — and recommending — lightweight tools (such as command-line cleanmgr and CCleaner) for routine cleanups and expert-level tools (such as jv16 PowerTools) when simpler software isn’t enough.
And now, if you’ll excuse me, I’m off to clean up my personal-use PCs. I suggest you do likewise!
| Feedback welcome: Have a question or comment about this story? Post your thoughts, praise, or constructive criticisms in the WS Columns forum. |
The ultimate guide to fixing Windows 7 problems
 |
Windows 7 is the best Windows ever, but no one calls it perfect. As with all operating systems, stuff happens.
Troubleshooting Windows 7 Inside Out by Mike Halsey is a soup-to-nuts reference for keeping Windows 7 running smoothly. Its 25 chapters cover such essential topics as security and maintenance basics, malware threats, Win7 fixes (both simple and advanced), disaster recovery, and advanced diagnostics utilities. This month, all Windows Secrets subscribers can download Chapter 16, Windows Problems Demystified. It explains Win7’s core system files, techniques for checking and restoring those files, how to create a slipstreamed installation DVD, and more. If you want to download this free excerpt, simply visit your preferences page and save any changes; a download link will appear. All subscribers: Set your preferences and download your bonus |
Fortunate exchange between Scotland and Earth
By Kathleen Atkins
Lounge member Tinto Tech of Scotland, puzzled by the behavior of a telnet client, posted details of his perplexing problem in the Networking forum.
Paul T, who lists his residence as Earth, solved Tinto Tech’s problem — illustrating almost by the way that geographical location is no impediment to clearing up digital difficulties and human errors.
Head to the Lounge to read about the problem and its solution. More»
The following links are this week’s most interesting Lounge threads, including several new questions to which you might be able to provide responses:
☼ starred posts — particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right into today’s discussions in the Lounge.
The Lounge Life column is a digest of the best of the WS Lounge discussion board. Kathleen Atkins is associate editor of Windows Secrets.
Wily dog takes over the beautiful game
 |
By Kathleen Atkins
Nowhere is speed and cunning play valued more greatly than in soccer. So when a dog took to the field in the middle of a game and cheerfully eluded all potential capturers, the fans were not annoyed. In fact, the crowd cheered him — a kindred spirit. Enjoy! Play the video |
Can Windows 7's XP Mode be uninstalled?
 |
By Fred Langa
Based on the feedback we’ve received, many Windows Secrets readers have switched to Windows 7 but retain a keen interest in Windows XP. Now that I’ve thoroughly covered how to set up and use Windows 7’s XP Mode, it’s time for the final chapter — removing it. |
Uninstalling XP Mode — step by step
Wow! The Sept. 22 Top Story, “Using Windows 7’s XP Mode — step by step,” is still generating lots of mail, including this one from reader Campbell Milton:
- “In working with some people in my area of work, the question has come up, ‘Can you safely uninstall XP Mode, whether in Virtual PC or if installed on its own?’
“I hope there is a link or some info on this topic. The colleagues who wish to use [XP Mode] are programmers who use GIS applications — some of which operate only in XP Pro.”
Yes, XP Mode can be uninstalled.
You may recall from that Sept. 22 story that what we casually call “XP Mode” actually comprises two separate pieces of software. One is the XP Mode software — a complete XP Pro SP3 setup. It’s preconfigured and ready to run inside the other essential part: the Windows Virtual PC application.
For XP Mode to work, both components have to be installed.
The XP Mode software is easily uninstalled:
- If Windows XP Mode is running, shut it down.
- Open Control Panel.
- Under Programs, click Uninstall a program.
- Double-click Windows XP Mode. (See Figure 1.)
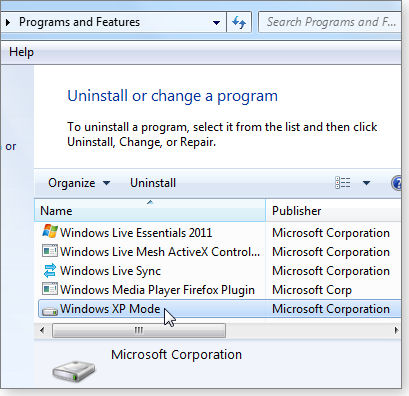
Figure 1. XP Mode shows up in the control panel’s normal Uninstall or change a program applet.
However, removing the XP Mode application doesn’t affect the Windows Virtual PC (VPC) installation, which you installed separately when you first set up the XP Mode system.
You can leave the VPC software installed, if you wish, and use it to set up generic virtual PCs running the operating system of your choice.
Removing a Windows Virtual PC installation is also relatively easy:
- Open Control Panel.
- Under Programs, click Uninstall a program.
- In the left pane, click View installed updates.
- Under Microsoft Windows, double-click Windows Virtual PC (KB958559).
- Reboot your PC.
Depending on how you used XP Mode and Windows VPC, some additional virtual machine files may be left on your system. You can delete these, too, if you wish.
To do so, open Windows Explorer and browse to the location where the virtual machine files are stored. The default location is
C:Users{username}AppDataLocalMicrosoftWindows Virtual PCVirtual Machines
where username is the name of your Windows 7 user account.
If you want to be selective, open the folder and delete only those files and subfolders that you want gone. (You might want to keep some VPC configuration files for future use.) To delete all traces of VPC files, delete the entire Virtual Machine folder, including all subfolders.
After you’ve removed XP Mode, Windows VPC, and any extra virtual machine files you may have created, your PC should be back the way it was prior to your XP Mode setup.
Suddenly, Intuit’s Quicken will not launch
John Hood is among the numerous Quicken users who’ve been mired in various glitches of late.
- “Supposedly because of .NET 4, Quicken 2011 and other versions will no longer launch. I spent a whole day in a run-around with Quicken Tech support: uninstall .NET 4 — didn’t work; reinstall .NET 4; yada, yada. Something is really screwed up. If you Google Quicken Launcher has stopped working, you’ll find pages and pages of frustrated users with insane fixes that don’t fix anything.
“It appears that there is ‘suddenly’ a compatibility issue, and neither I nor many others can resolve it. I’m seething about incredibly inept tech-support personnel using me as a testing guinea pig because they don’t have a clue how to fix it. When I saw them heading toward an uninstall of Windows, I ran like a rabbit.
“Do you have any clues? Please help!”
I feel your pain, John. First, let me list three sites that seem to offer the best workarounds — if the users’ responses on those sites are an accurate indication. (You may already have tried some or all of these, but I’ll include them for completeness.)
- Quicken official help item, “Message when opening Quicken: Quicken launcher has stopped working”
- Quicken Live Community discussion, “Quicken launcher has stopped working”
- Intuit Community discussion, “Quicken launcher has stopped working”
On other sites, some Quicken users report success after modifying the properties of the Quicken launcher:
- Right-click the Quicken icon and select Properties.
- On the General tab, make sure that Run as Administrator is checked.
- On the Compatibility tab, select Run this program in compatibility mode for and then select Windows XP.
Still other users report that a key Quicken .dll, qwutilnet.dll, is getting quarantined, deactivated, or removed by some antivirus utilities. Check your AV tool logs to see whether this is the case. If necessary, restore the .dll.
Good luck, John.
Using newer drivers on older hardware
Eric Kisch’s letter asks specifically about getting an older printer to work with Win7. But the answer can apply to other hardware types as well.
- “My concern is finding printer drivers for HP printers the company has abandoned. The moment we switched to Win7 — or, more correctly, all our new computers came with Win7 — our HP 3500 color laser and HP880C inkjet stopped working. HP in its wisdom had decided not to support them with drivers that work in Win7.
“The 3500 is a substantial chunk of printer hardware, and I have hundreds of dollars invested in the four-color cartridges. Surely, there must be a way to get this to work with Win7. The damn thing is only five years old — too new to cast on the technology scrapheap.”
Normally, I don’t recommend fiddling with drivers. But it might become necessary when a hardware maker stops supporting its older equipment. At that point, you really have little to lose by experimenting with nonstandard drivers.
First, back up your system. That should always be a given.
Then look for drivers that might not be an exact match but are close enough to work.
For example, if you check the Windows 7 Compatibility Center site, you’ll see that there are approved Win7 drivers available for the HP Deskjet 882, which is a close cousin to your 880.
If I were you, I’d try the drivers for the 882 and see what happens.
If that driver fails, try another closely related driver, along the lines suggested in the HP support forum discussion, “Deskjet 880C Windows 7 driver workaround?”
If a near-match driver doesn’t work, you might as well try something further afield. For instance, Windows 7 includes generic drivers for a number of widely used printer types, including three kinds of Epson legacy printers. See Microsoft Support article 895612.
If your printers accept any of the legacy drivers, or any other close-enough drivers, you may be able to squeeze a little more life out of them — perhaps until you’ve used up your ink or toner supply.
And if not, consider selling (e.g., craigslist), donating, or recycling (info) your printers.
I agree with you, Eric: it’s too soon for the scrap heap!
A less-expensive alternative for creating PDFs
In response to Michael Lasky’s Oct. 6 story, “Three exceptional apps for every Windows version,” Garth Ponsonby writes:
- “I just posted something in the Windows Secrets Lounge about Tracker PDF software.
“They have an offer of PDF-XChange Lite 4, which is free for home and academic use.
“I’ve used it for years. I’m extremely satisfied with it — both for its quality and its ease of use. The price can’t be beat, either!”
Thanks, Garth! Nice to see that good-quality, low-cost, and free PDF alternative tools are becoming more common. A welcome development!
| Feedback welcome: Have a question or comment about this story? Post your thoughts, praise, or constructive criticisms in the WS Columns forum. |
| Reader Garth Ponsonby will receive a gift certificate for a book, CD, or DVD of his choice for sending the tip we printed above. Send us your tips via the Windows Secrets contact page. |
Find out where that e-mail really came from
 |
By Susan Bradley
Potentially dangerous scam e-mails might be landing in your inbox, masquerading as legitimate mail. Fortunately, there are tools that can help you determine the source of suspect messages and possibly identify who’s sending them. |
Malicious e-mails are getting harder to detect
Recently, some PC users have received suspicious e-mails containing attached Word documents. Hidden within the Word docs was a zero-day bug that automatically installed itself when the documents were opened. A Nov. 1 Symantec blog gives a detailed explanation of how it works.
The Symantec blog notes that the Word files were cleverly designed to look like legitimate documents recipients might expect to receive. This goes well beyond the old Nigerian financial-aid ploys. Computer users have even received forged Facebook e-mails that appear completely authentic. But click the familiar yellow “See the comment thread” box, and you could be infected. The U.S. Federal Bureau of Investigation’s New E-Scams & Warnings page notes other types of e-mail scams, such as responses to online job postings and lottery notifications. And then there are those notorious PDF attachments.
I’m seeing a growing number of scam e-mails on both my business and personal accounts. My spam filters catch most of these, but I maintain one unfiltered e-mail account to keep an eye on the latest spoofs. For example, now that businesses are moving to electronic payroll and income-tax filings, I’m receiving malicious e-mail disguised as official payment messages. I’ve also seen PayPal-transaction spoofs and other online payment alerts. I’ve even come across bogus notices from the FBI and the U.S. Internal Revenue Service, two agencies that can strike the fear-of-compliance in recipients. (The IRS still does not send e-mails to taxpayers. It gives you the bad — or occasionally good — news by printed correspondence.)
Dissecting mail headers can provide useful info
So how do you pick out these impostors lurking in your inbox? As I’ve said many times, the first rule is to be suspicious of 1) any unexpected mail with attachments or 2) mail from someone (or some company) you’re unfamiliar with. Any message that asks for personal information is immediately suspect.
The second step is to pick apart the message’s header. (As you probably already know, spoofing an e-mail’s From address is easy.) But looking more deeply at the header can give you a heads-up that something is amiss.
The message-header file contains a history of how messages are handed off from one mail server to the next. Tracking e-mail headers isn’t new: numerous white papers on the Internet, such as Marwan Al-Zarouni’s “Tracing e-mail headers” (PDF document), detail how it’s done.
Outlook — especially Outlook 2010 — doesn’t make dissecting message headers easy. An e-mail’s header information is hidden under File/Info/Properties. Look for the Internet Headers box at the bottom of the properties window.
Fortunately, there’s an easy-to-use tool — PocketKnife Peek (info/download) — that lets you peek into Outlook’s header file immediately. Once Peek is installed, simply right-click a message in Outlook’s Inbox and select Peek from the options list — a message-details window immediately pops up. Select the Internet Header tab. (See Figure 1.)
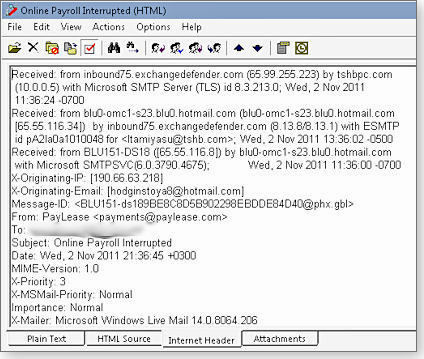
Figure 1. PocketKnife Peek lets you call up e-mail header information instantly.
What you’ll see is a raw, possibly confusing mash-up of text. But never fear, there are Web resources to help you decipher it. For example, copy everything in the Internet Header box and go to the iptrackeronline.com website (home page). Once there, click the Email Header Analysis button and paste the header information into the Paste email header here box. You get a nicely organized report of where the e-mail came from. (See Figure 2.)
s 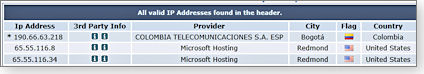
Figure 2. Use iptrackeronline.com’s Email Header Analysis tool for an easy-to-read report of header information.
For example, the header information shown in Figures 1 and 2 was taken from an e-mail purportedly warning us that our online payroll wasn’t processed properly (shown in Figure 3.) The e-mail had the client’s correct name and the company’s address. Its “transaction was not processed” warning focuses the recipient’s attention on the possible problem — not the e-mail’s source.
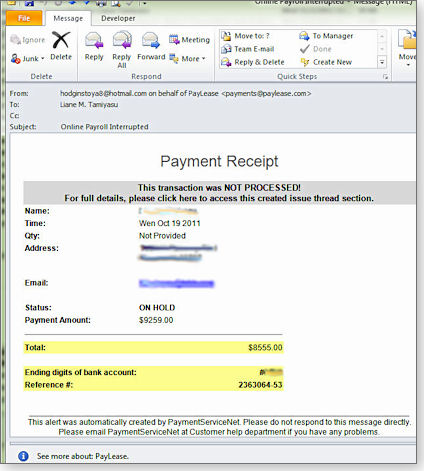
Figure 3. This bogus e-mail looks like the real thing.
However, the header information shows that the e-mail was sent from Bogotá, Colombia, and then bounced through Microsoft’s Hotmail system. It’s extremely unlikely that our payroll-processing company would send a message from Bogotá — it’s clearly a fictitious e-mail.
Other e-mail clients make it a bit easier to find key e-mail header information. In Thunderbird, you click View/Header/All to see the full header. An easier way is to use the Thunderbird extension MailHops (site), which adds the ability to view the mail servers the e-mail hopped through to get to you.

Figure 4. The Thunderbird add-on MailHops makes tracing an e-mail’s journey easy.
In Gmail, you click the down-arrow button next to Reply (in the upper-right corner of the message box) and then click Show original. For other e-mail clients, see the appriver.com site, “How to retrieve an e-mail message header for various e-mail clients.”
Just another tool in the war against malware
I now make it a standard practice to check the origin of suspicious e-mails. This helps greatly in determining whether an e-mail is valid. An e-mail from the U.S. government? It’s highly unlikely that any government entity would ever send me an e-mail I did not expect — and certainly not one from outside the U.S.
If a company you work with sends you an e-mail via an outsourcing company, it’s probably marketing mail you don’t need. (And if your business is sending out important e-mails, preserve your reputation by using a reputable delivery service.)
Even with the ability to find out where e-mails come from, the best practice is to be extremely careful about clicking links in a message. I will always, for example, go to my online-banking site through my browser. Still, I feel a bit more empowered being able to figure out where the scammers come from and knowing they are not living next door.
| Feedback welcome: Have a question or comment about this story? Post your thoughts, praise, or constructive criticisms in the WS Columns forum. |
UDP networking ports threatened by TCP/IP flaw
 |
By Susan Bradley
For the average Windows user, the topic of networking ports is often confusing — and easily ignored. But November’s Patch Tuesday includes a critical patch for Vista and Windows 7 users — for an unusual networking-protocol vulnerability. |
MS11-083 (2588516)
TCP/IP vulnerability threatens Vista and Win7
Generally, Windows XP users face more security risks than Vista or Win7 users. But this Patch Tuesday is light for anyone running Windows XP or Windows Server 2003. Vista and Windows 7 users, however, need to apply this patch as soon as possible to fend off a potentially nasty threat.
In almost all computer operating systems, networking communications are handled though TCP/IP ports. There are 65,535 ports in a modern OS, and if you’ve poked around the common home/small-business firewall, you’ve seen references to two types of ports: TCP and UDP. TCP ports are used for such things as websites and e-mail. UDP ports are used when a transmission doesn’t need to have confirmation that a packet has arrived at its destination. In home networks, UDP (definition) ports are used mostly for online gaming. For example, the Xbox needs UDP ports 88 and 3074 to connect properly with the Xbox Live service.
Normally, a port is closed when there are no system services using it (or listening to it) — and your system is protected from outside attacks. In this vulnerability, however, a closed port can be circumvented if an attacker sends a large amount of specially crafted UDP packets.
Now, before you yank your Internet connection out of the wall, keep in mind that there is normally a firewall between you and the outside world. You are more vulnerable if you have manually opened any UDP ports on your external firewall or if there are ports closed but waiting for applications to use them.
To check this, review what firewall ports you have open. There are several ways to do this. One is to open your external firewall’s configuration utility and look in the port-forwarding section. See whether any UDP ports are open. To review open ports as seen from the outside, try the ShieldsUP test at grc.com (site) or the Firewall Test (page) at auditmypc.com. If you’re unsure of the results of either scan, post them in the Windows Lounge and I’ll try to help you decipher the results.
► What to do: Since this patch is rated critical, install KB 2588516 when offered, or go to MS11-083 for more details and links to the patch for specific versions of Windows. This threat could be nasty if someone codes up an exploit and our external firewalls are more open than we think.
MS11-085 (2620704)
The continuing process of fixing DLL threats
It wouldn’t be a Patch Tuesday without a .dll fix. We’ve been patching .dll files for over a year now; I wrote about them in my Sept. 9, 2010, Top Story.
This time around, it’s a compromised Windows Mail or Windows Meeting Space .dll file that could let an attacker gain control of your system.
This patch is rated important for Windows Vista, moderate for Windows Server 2008, and low for Windows 7 and Windows Server 2008 R2. Once again, Windows XP users are off the hook.
► What to do: Install KB 2620704 (MS11-085) on your Vista and Windows 7 systems as soon as possible.
(2639658)
TrueType font attacks lead to true headaches
Earlier this month, a Symantec blog described how Word documents were sent out with malicious code that targeted a previously unreported Windows kernel vulnerability. As it turns out, the vulnerability was in how Windows parsed True Type fonts and is the common elevation of privileges threat.
Microsoft acknowledged the problem in Security Advisory 2639658 and announced a temporary Fix it solution in MS Support article 2639658. However, if you’re running Windows XP or Server 2003 and you use the fix, you’ll be reoffered security updates KB 982132 and KB 972270.
► What to do: For now, I suggest that you skip Microsoft’s Fix it, avoid opening suspicious Word documents, and wait for the real patch that will inevitably come.
MS11-084 (2617657)
Another TrueType-fonts patch is a minor one
This time, the fix is not for elevation of privileges but merely a denial-of-service threat. Over the years, fonts have often been used in attacks, so expect more of this type of patch down the road. Only Windows 7 and Windows Server 2008 systems are affected, and the threat’s severity rating is moderate.
► What to do: Install KB 2617657 (MS11-084) as soon as possible.
MS11-037 (2544893)
A fix for Windows XP is fixed again
It’s rare when Microsoft re-releases an update (shown in Figure 1). It’s even rarer — and more interesting — when the do-over is only for Windows XP and Server 2003 and comes with a cryptic explanation that it “provides the same cumulative protection that is provided by this update for all other affected operating systems” — and then doesn’t explain exactly what those cumulative protections are.
In short, the patch fixes a flaw in the Windows security system that could let attackers using malicious websites collect information from your machine.
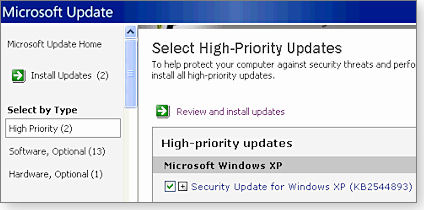
Figure 1. XP users should look for the re-release of KB 2544893.
► What to do: You’ll find the original description of the patch in MS11-037 and the new download for XP systems on the KB 2544893 download page.
MS11-086 (2616310)
Domain controllers face internal threats
This security patch won’t appear on most computer systems. It’s of interest only to IT professionals running Active Directory on their internal networks. You’ll also see it if you’re running a domain controller such as Small Business Server.
By default, Active Directory is not configured to use the Lightweight Directory Access Protocol over SSL (LDAP over SSL), so the risk of attack is relatively low and the patch is rated merely important.
► What to do: Consult MS Security Bulletin MS11-086 for specific details about the threat. Install KB 2616310 immediately only if you think there is a specific threat and only after testing the patch.
Pass on nonsecurity Office 2010 updates for now
Surprised to see a screenful of Office 2010 updates (shown in Figure 2) on one of my test boxes, I soon discovered that none is security-related.
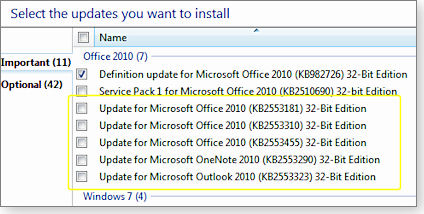
Figure 2. Skip these nonsecurity Office 2010 updates (in the yellow box) until further notice.
According to the cryptic descriptions in their respective MS Support articles, KBs 2553181, 2553310, 2553455, 2553290, and 2553323 include the latest fixes for 32-bit and 64-bit versions of Office 2010 plus the usual “stability and performance improvements.”
► What to do: Since these fixes are probably minor, and because I don’t like mixing nonsecurity and security updates, I recommend that you hold off on installing these patches until I get more information about what they fix.
Firefox and Thunderbird Versions 8 released
Nearly everyone I talk to in the tech community is not happy with Mozilla’s fast-release schedule. But if you’re a habitual early adopter, you can now upgrade to Firefox 8 and Thunderbird 8.
The problem with rapid updates is that popular browser add-ons and plug-ins can’t keep up — they sometimes break. That creates a dilemma: both Firefox 8 and Thunderbird 8 include needed security fixes.
► What to do: Check out the Mozilla Security Advisories pages for what’s fixed in Thunderbird and Firefox. And test the new browsers with your favorite add-ons before updating all your PCs.
Apple’s iOS 5 is easier to buy than to upgrade
In the past couple of weeks, I have set up three new iPhone 4S’s in my office. I also updated two older iPhones and my iPad. Based on that experience, I can report that configuring iOS 5 on new hardware is much easier than upgrading older equipment.
Moving up to iOS 5 just doesn’t feel like the normal application update. In a somewhat confusing series of steps, it does a full backup of your iPhone (obviously a good thing), installs the new OS, and then restores your backed-up data over the new OS. (Most updates simply leave the data in place through the entire process.) Part of the process requires going into the Apple user accounts and adjusting user names and profile information — and additional step that bogs down the update process.
Once that’s done, the updating process walks you through the following nine system-setup screens:
- Indicates that your iPhone was successfully restored.
- Enables location services.
- Prompts you to join a Wi-Fi network.
- Requests your Apple ID; if it’s not a full e-mail address, requires you to change it to one.
- Asks you to enter your birth date to ensure you are over 18.
- Asks you to accept the Apple end-user license agreement, including the new iCloud services.
- Asks whether you want to send diagnostic information to Apple automatically.
- States (hopefully) that the device is now set up.
- Asks whether you’d like to re-enter an auto-lock passcode (the updating process removes the one you used prior to iOS 5).
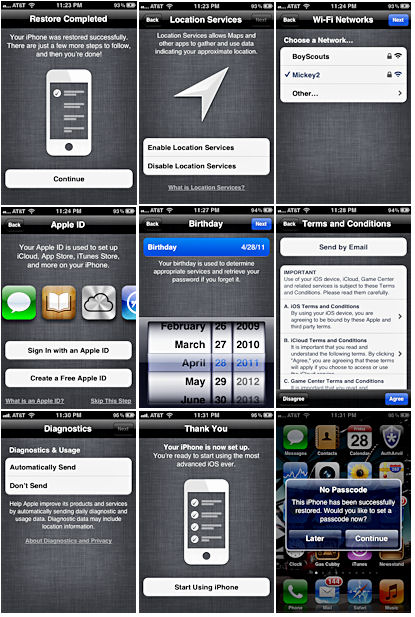
Figure 3. The final nine steps to an iOS 5 upgrade
And after all that, iOS 5 users are likely to see yet another update within the next few weeks. According to a 9to5mac.com story, a few iOS 5 users have ended up with reduced battery life after updating the OS. Apple has sent out a pre-release version of iOS 5.0.1 to selected customers for testing.
► What to do: This is no trivial upgrade. Many iOS users had problems running the update when it was first released. Set aside an hour or two. Your iOS device will have to be connected to a PC or Mac.
Regularly updated problem-patch chart
This table provides the status of problem Windows patches reported in previous Patch Watch columns. Patches listed below as safe to install will be removed from the next updated table. For Microsoft’s list of recently released patches, go to the MS Safety & Security Center PC Security page.
| Patch | Released | Description | Status |
| 2487367 | 08-09 | August .NET updates; see MS11-066 for complete patch list | Skip |
| 2533523 | 08-09 | .NET 4 Reliability Update 1 | Skip |
| 2539631 | 08-09 | August .NET updates; see MS11-069 for complete patch list | Skip |
| 2553065 | 09-13 | Office File Validation update | Skip |
| 931125 | 10-25 | Root-certificate update for XP | Skip |
| 2639658 | 11-03 | Microsoft Fix it for zero-day Word attacks | Skip |
| 2510690 | 06-28 | Office 2010 SP1 — will revisit in December when needed hotfix is released | Wait |
| 2528583 | 07-12 | Cumulative update for SQL Server 2008 R2 | Wait |
| 2526086 | 10-25 | Office 2007 SP3 | Wait |
| 2603229 | 10-25 | Registry fix for 32-bit apps on 64-bit PCs | Wait |
| 2553181 | 11-09 | Nonsecurity Office 2010 updates — including KB2553181, KB2553310, KB2553455, KB2553290, and KB2553323 | Wait |
| 2607576 | 10-25 | Jump-list fix | Optional |
| 2564958 | 10-12 | DLL-preloading attack via WebDAV | Install |
| 2567053 | 10-12 | Windows kernel-mode driver vulnerability | install |
| 2579692 | 10-12 | DLL-preloading attack via Media Center TV Pack | Install |
| 2586448 | 10-12 | Internet Explorer cumulative security update | Install |
| 2592799 | 10-12 | Windows Ancillary Function Driver flaw | Install |
| 2604930 | 10-12 | October .NET updates; see MS11-078 for complete patch list | Install |
| 2544893 | 11-09 | Re-release of MS11-037 update for XP systems | Install |
| 2588516 | 11-09 | TCP/IP update attacking closed UDP ports — Vista/Win7 only | Install |
| 2617657 | 11-09 | TrueType fonts denial-of-service threat | Install |
| 2620704 | 11-09 | Windows Mail/Meeting Space DLL-preloading threat — Vista/Win7 only | Install |
Status recommendations: Skip — patch not needed; Hold — do not install until its problems are resolved; Wait — hold off temporarily while the patch is tested; Optional — not critical, use if wanted; Install — OK to apply.
| Feedback welcome: Have a question or comment about this story? Post your thoughts, praise, or constructive criticisms in the WS Columns forum. |
The Patch Watch column reveals problems with patches for Windows and major Windows applications.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Discover the Best AI Tools for Everything
by
Alex5723
2 hours, 28 minutes ago -
Edge Seems To Be Gaining Weight
by
bbearren
4 hours, 47 minutes ago -
Rufus is available from the MSFT Store
by
PL1
13 hours, 26 minutes ago -
Microsoft : Ending USB-C® Port Confusion
by
Alex5723
15 hours, 36 minutes ago -
KB5061768 update for Intel vPro processor
by
drmark
1 hour, 29 minutes ago -
Outlook 365 classic has exhausted all shared resources
by
drmark
13 hours, 47 minutes ago -
My Simple Word 2010 Macro Is Not Working
by
mbennett555
11 hours, 21 minutes ago -
Office gets current release
by
Susan Bradley
13 hours, 58 minutes ago -
FBI: Still Using One of These Old Routers? It’s Vulnerable to Hackers
by
Alex5723
2 days, 4 hours ago -
Windows AI Local Only no NPU required!
by
RetiredGeek
1 day, 12 hours ago -
Stop the OneDrive defaults
by
CWBillow
2 days, 4 hours ago -
Windows 11 Insider Preview build 27868 released to Canary
by
joep517
2 days, 14 hours ago -
X Suspends Encrypted DMs
by
Alex5723
2 days, 16 hours ago -
WSJ : My Robot and Me AI generated movie
by
Alex5723
2 days, 17 hours ago -
Botnet hacks 9,000+ ASUS routers to add persistent SSH backdoor
by
Alex5723
2 days, 17 hours ago -
OpenAI model sabotages shutdown code
by
Cybertooth
2 days, 18 hours ago -
Backup and access old e-mails after company e-mail address is terminated
by
M W Leijendekker
2 days, 6 hours ago -
Enabling Secureboot
by
ITguy
2 days, 13 hours ago -
Windows hosting exposes additional bugs
by
Susan Bradley
3 days, 2 hours ago -
No more rounded corners??
by
CWBillow
2 days, 22 hours ago -
Android 15 and IPV6
by
Win7and10
2 days, 11 hours ago -
KB5058405 might fail to install with recovery error 0xc0000098 in ACPI.sys
by
Susan Bradley
3 days, 14 hours ago -
T-Mobile’s T-Life App has a “Screen Recording Tool” Turned on
by
Alex5723
3 days, 17 hours ago -
Windows 11 Insider Preview Build 26100.4202 (24H2) released to Release Preview
by
joep517
3 days, 12 hours ago -
Windows Update orchestration platform to update all software
by
Alex5723
4 days ago -
May preview updates
by
Susan Bradley
3 days, 12 hours ago -
Microsoft releases KB5061977 Windows 11 24H2, Server 2025 emergency out of band
by
Alex5723
3 days, 3 hours ago -
Just got this pop-up page while browsing
by
Alex5723
3 days, 16 hours ago -
KB5058379 / KB 5061768 Failures
by
crown
3 days, 14 hours ago -
Windows 10 23H2 Good to Update to ?
by
jkitc
2 days, 16 hours ago
Recent blog posts
Key Links
| S | M | T | W | T | F | S |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | 7 |
| 8 | 9 | 10 | 11 | 12 | 13 | 14 |
| 15 | 16 | 17 | 18 | 19 | 20 | 21 |
| 22 | 23 | 24 | 25 | 26 | 27 | 28 |
| 29 | 30 | |||||
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

