
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Say goodbye to BIOS — and hello to UEFI!
In this issue
- TOP STORY: Say goodbye to BIOS — and hello to UEFI!
- LOUNGE LIFE: Tablet users curious about smartphone apps
- WACKY WEB WEEK: Imagining the secret life of books, after hours
- LANGALIST PLUS: Are tracking-prevention tools worthwhile?
- KNOWN ISSUES: Welcome to the 64-bit era of Windows
- IN THE WILD: Lessons learned from the Stratfor files
Say goodbye to BIOS — and hello to UEFI!
 By Woody Leonhard
By Woody Leonhard
If you’ve ever struggled with your PC’s BIOS — or been knee-capped by a rootkit that assailed the BIOS — you undoubtedly wondered why this archaic part of every PC wasn’t scrapped long ago.
Well, be of good cheer: Windows 8 will finally pull the PC industry out of the BIOS generation and into a far more capable — and controversial — alternative, the Unified Extensible Firmware Interface.
To best understand where we’re headed, it’s helpful to look at where we’ve been. An integral part of every PC, the Basic Input/Output System spans the entire history of the personal computer — more than 30 years. The very first IBM PC had a BIOS. And despite extraordinary advances in hardware and software, the BIOS we still puzzle over today is not much different from the one in that original PC.
Essentially a miniature OS, the BIOS has a simple but critical function — when a PC powers up, the BIOS checks that all hardware is in order (the POST or “power-on self-test” sequence); fires up the full operating system on the machine, such as Windows (using OS loader code); and then hands all control of the computer over to the OS.
Although older operating systems (such as DOS) relied on the BIOS to perform input and output functions, modern OSes (including Windows) have their own device drivers and completely bypass the BIOS after they’re up and running.
These days, it’s rare that a PC user is forced to invoke the BIOS’s cryptic and somewhat enigmatic user interface. Usually, it’s in response to some near-catastrophic system failure.
The Unified Extensible Firmware Interface (UEFI) is essentially the next generation of BIOS. It’s a system that potentially offers new and more advanced control of the boot-up process. If your PC is less than two or three years old, chances are good that it already has UEFI (more info) capabilities. Chances are very good that you didn’t know that, because the hardware manufacturers have been carefully keeping the old BIOS interface as your default boot system. But that will change with Windows 8.
How UEFI is different from/better than BIOS
The standard BIOS has all sorts of problems, not least of which is its susceptibility to malware. For example, there are rootkits that hook themselves into the BIOS OS-loader code, permitting them to run underneath Windows. They’re difficult to remove and will reinfect Windows over and over.
And because the BIOS sits on a chip on the motherboard, it’s more difficult to update than an operating system or an application. So most PC users never update their BIOS, leaving the PC possibly incompatible with newer operating systems. (The early PC BIOS was hard-coded on a chip, so upgrading required replacing the entire chip or PROM.)
The UEFI is a more sophisticated system that runs before your primary OS kicks in. Unlike the BIOS, UEFI can access all PC hardware, including the mouse and network connections. It can take advantage of modern video cards and monitors. It can even access the Internet.
And as you can see in Figure 1, UEFI offers a modern, easy-to-decipher user interface. It could make dual-booting simpler, more visual, and controllable by mouse or touch. If you’ve ever played your BIOS, you discover that UEFI is in a whole new dimension.

Figure 1. The Asus.com website offers this view of a UEFI-interface screen — clearly, an improvement over the typical BIOS UI we’re faced with today.
Unlike the BIOS, the UEFI can exist on a disk, just like any other program — or in nonvolatile memory on the motherboard or even on a network share.
At this point, it’s important to note that systems can run either the BIOS or the UEFI — or both. When they’re both used, the BIOS goes first to run POST, then the UEFI takes over and hooks into any calls that may be made to the BIOS. (Windows typically doesn’t make calls directly to the BIOS, but other operating systems might — and the UEFI will handle them, not the BIOS.)
The UEFI can also run without the BIOS — it can take care of all OS loading/interface functions previously handled by the BIOS. The only thing the UEFI can’t do is perform the POST or run the initial setup (configuring the CPU, memory, and other hardware). PCs that have the UEFI but no BIOS have separate programs for POST and setup that run automatically when the PC is powered on.
As we all know, the BIOS initialization process — including POST — seems to take a long time. The UEFI, on the other hand, can run quickly.
Moreover, a BIOS is easily reverse-engineered and typically has no internal security protection, making it a sitting duck for malware. A UEFI can run malware-dodging techniques such as policing operating systems prior to loading them — which might make rootkit writers’ lives considerably more difficult. For example, the UEFI could refuse to run OSes that lack proper digital security signatures.
And that’s where the UEFI controversy begins.
Windows 8 will implement UEFI in new ways
Back in September, Microsoft wrote voluminously about the UEFI in Windows 8. The first post, “Reengineering the Windows boot experience,” talks about the basic ways Windows 8 will use the UEFI. (If your PC doesn’t support a UEFI, Win8 should still work fine.)
The article shows how current text-based, boot-time options, such as system repair store and image recovery, can be made more usable with a new graphical interface. The story goes on to describe how system startup could go, in seconds, from power-on to Windows Desktop without so much as flickering the screen. It also shows how dual-boot will work with a graphical face-lift.
The changes appear to be largely cosmetic, but they’re long overdue and a welcome improvement to the constrained, DOS-era recovery environments under which Windows operates.
The second article, “Protecting the pre-OS environment with UEFI,” shows how the UEFI secure boot — using Public Key Infrastructure (PKI) digital certificates — validates programs, peripherals, and OS loaders before they can run. The system can go out to the Internet and check whether the UEFI is about to run an OS that has had its certificate yanked.
If it sounds a lot like Secure Sockets Layer protection — no stranger to controversy, as I detailed in my Sept. 15, 2011, Top Story — there certainly are similarities.
Microsoft states it will let the hardware manufacturers struggle with the difficult question of who controls the digital-signature keys. “Microsoft supports OEMs having the flexibility to decide who manages security certificates and how to allow customers to import and manage those certificates, and manage secure boot. We believe it is important to support this flexibility to the OEMs and to allow our customers to decide how they want to manage their systems.”
Still, Microsoft is ensuring that anyone buying a certified Windows 8 PC can rely on a certain level of protection from rogue OS loaders. “For Windows customers, Microsoft is using the Windows Certification program to ensure that systems shipping with Windows 8 have secure boot enabled by default, that firmware not allow programmatic control of secure boot (to prevent malware from disabling security policies in firmware), and that OEMs prevent unauthorized attempts at updating firmware that could compromise system integrity.”
The controversial side of dual boot
When those details first hit, the Linux community flew up in arms. Dual booting between Windows 8 and Linux might require a digital signature from a recognized certificate authority. That authority might be Microsoft, through its Windows Certification program, and Linux folks would have to pay the piper.
That controversy went on for a while but eventually died down (though it never disappeared) when it became clear that putting together the signature is relatively easy and not very expensive.
Then another conflagration started last week. To understand why, you have to understand that UEFI secure boot has two bail-out options. First, most PCs let you turn off UEFI secure boot entirely. You have to be sitting at the computer and do it manually, but it’s easy enough. In one of the Microsoft postings mentioned previously, the company acknowledged that hardware manufacturers could “allow customers to … manage secure boot.”
Second, there’s a provision for something called “custom secure boot mode” in which you, as a customer, can sit at your computer and type in a signature for any OS loader you darned well like. This manually created whitelist overrides the Windows 8 or third-party check, letting the UEFI run OS loaders unhindered.
You must also understand that Windows 8 will run on two entirely different hardware platforms — Intel/AMD platforms spanning the range from (ponderous!) tablets to full-size desktops, and the svelte, tablet-friendly ARM platforms. If you use Win8, one of your first decisions will be which platform you choose.
The Linux world was taken aback when researcher Glyn Moody and the Software Freedom Law Center announced last week in a blog that Microsoft is making specific demands from hardware manufacturers who intend to sell Windows 8 bundled with their ARM machines — that is, those lightweight Windows 8 tablets. The Microsoft restrictions prevent hardware manufacturers from disabling secure boot and also prevent hardware manufacturers from implementing “custom secure boot” whitelists — but again, only on ARM hardware.
In other words, if at some point in the future you buy an ARM-based tablet with Windows 8 preinstalled, you won’t be able to dual-boot with Linux or any operating system other than the ones that pass the security check. Presumably that could mean Windows 8 or some later version of Windows that Microsoft might ordain in the future.
Aside from the fact that the restrictions fly in the face of what Microsoft specifically said in September, it’s hard for me to get too worked up about them. If you buy a Win8 (ARM) tablet, you won’t be able to root it (Wikipedia definition), and you may not be able to upgrade it. You’ll just have to take that into account when you think about buying one — assuming Microsoft is up-front about the limitation and mentions it to consumers.
Intel-based Windows 8 machines — even tablets (including tablets that run only the Metro interface) — aren’t hobbled by those ARM restrictions. At least at this point, Intel/AMD machines are, in fact, required to allow multibooting (with signed operating systems) and even to replace Windows 8 with an OS of your choice. It remains to be seen whether Microsoft’s going to change its mind about that distinction.
It’s a brave new world out there, with Win8 tablets going up against the iPad 3 later this year. Stay tuned!
| Feedback welcome: Have a question or comment about this story? Post your thoughts, praise, or constructive criticisms in the WS Columns forum. |
Tablet users curious about smartphone apps
By Kathleen Atkins
Windows Secrets reader Repainter saw last week’s Top Story on smartphone apps and wondered whether he could use those same apps on his tablet.
He took his question to the Lounge, where he was encouraged to give them a try.
The discussion includes an informative — if brief — survey of some current smartphone and tablet operating systems. More»
The following links are this week’s most interesting Lounge threads, including several new questions to which you might be able to provide responses:
☼ starred posts — particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right into today’s discussions in the Lounge.
The Lounge Life column is a digest of the best of the WS Lounge discussion board. Kathleen Atkins is associate editor of Windows Secrets.
Imagining the secret life of books, after hours
 |
By Kathleen Atkins
Books represent the ultimate distillation of the life of the mind. But what if books had a life of their own? A couple of videographers imagined the life of books at home, then pondered the larger entertainments of books at their Toronto bookstore, when all the staff had gone home. And so they sneaked into the bookstore at night — and caught a dance of a most unusual kind. Enjoy! Play the video |
Are tracking-prevention tools worthwhile?
 |
By Fred Langa
Some third-party, add-on software promises to increase your security by preventing websites from tracking you across the Web. But all the current major browsers have enhanced privacy modes available that do the same thing, for free, with just a few clicks. |
Thinking about online tracking-prevention tools
Peter Klugherz seeks greater privacy online.
- “I read an article in my local newspaper about online-tracking prevention. The software specifically mentioned was Ghostery, Adblock Plus, and Do Not Track Plus. I would be interested in reading your comments about these products.”
I think those (and similar) products are usually unnecessary, Peter. I suggest you first try the enhanced privacy mode already built into your browser. If that mode provides the anonymity you want — and I think it will — you won’t need any extra software at all.
In Internet Explorer 9, click the Settings gear, and select InPrivate Browsing from the Safety menu (see Figure 1); or select it by pressing Ctrl+Shift+P; or choose it from the New Tab page. Microsoft offers complete instructions on a Help & How-to page. IE also offers separate, always-on Tracking Protection, if you wish it, as described here.
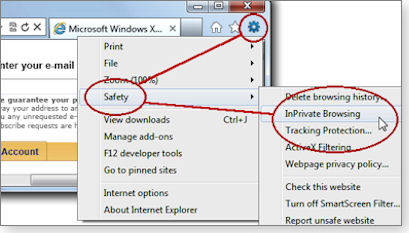
Figure 1. Internet Explorer 9’s InPrivate Browsing is always just a few clicks away, via the Safety menu.
In Firefox, the same type of privacy-protecting function is called Private Browsing. (See Figure 2.) To use it, click the Firefox menu and select Start Private Browsing. Mozilla’s full explanation is on a Firefox help page.

Figure 2. Two clicks are all it takes to access Firefox’s Private Browsing.
Chrome calls its version of this feature incognito mode. (See Figure 3.) Click Settings (the wrench icon), then New incognito window. Google’s explanation is on a “How to use Chrome” page.

Figure 3. Chrome’s Incognito is readily available and requires no additional software.
If you find those built-in privacy-boosting functions inadequate, by all means try add-on software. But odds are you’ll find you can get the privacy you want with your browser’s built-in, free tools.
Hardware nightmare foils no-reformat reinstall
Rupinder Sra ran into an incredible series of problems during and after a recent intercontinental trip.
- “Fred Langa’s methods have solved many problems for me, but this time his ‘Win7’s no-reformat, nondestructive reinstall’ [July 14, 2011, Top Story] took three days for ultimate success.
“I took my laptop from India to the USA and Europe for a month. (Four locations in the USA and six in Europe.)
“First few days in the USA, it worked fine but then started to hang. Never mind that. Went to Europe. The battery stopped charging! Never mind, I tell myself. Let’s continue working on direct power. Just don’t use it on the plane.
“Back home in India. Restart. Battery not charging. Changed the battery. Again not charging. Anyway, I continued on direct power. Windows hangs, and hangs, and hangs … sometimes takes one command/click in one to two hours. Total absolute slowdown.
“OK, I think now Fred Langa should move in. But I can’t read his mail on my laptop. So let’s use my smartphone. Good. I found the mail with his instructions on ‘no-reformat reinstall ….’ But before I do that, I want to try to do a system restore.
“Plugged in my HDD with the system image taken before leaving. Started the computer. It limped back up in 30 minutes. Hit start button. Had a coffee. Hit Accessories. Had another coffee. Hit system. Too much coffee — moved to tea. Hit system restore and had lunch. Late afternoon, it showed the HDD image! Wow! So let’s recover. Started the process. But by dinnertime, it showed ‘disc errors, cannot restore.’ That was frustrating.
“Anyway, never mind, next day let’s move to Fred’s instructions to uninstall SP1. By nighttime, it said it would not uninstall. Frustrating now! Switched off by hard press of power button.
“Next day, all day: Retry, same thing. No success.
“Late night. Third try — success! I was thrilled. (What was happening all these days?)
“Shoved in original W7 CD. Started the rebuild process and went to sleep. Next morning (today) it’s working.
“Battery still not charging.
“Why, and what happened while traveling?”
I applaud your persistence. Congratulations!
However, because an original symptom — the battery not charging — remained after a total software rebuild, I think your efforts have shown that your root problem is a hardware malfunction.
I’d look first at your external power supply — the wall wart or in-line transformer you use when you plug your laptop into a wall socket. Most laptops these days use switching transformers that can handle the varying electrical voltages and frequencies used around the world. But these transformers don’t last forever.
You’re a world traveler who hops between 110-240v, 50-60Hz electrical grids, so your power supply has had an unusually heavy workout.
A malfunctioning power supply would account for many of the issues you saw. If the delivered power were marginally low, you might well not be able to charge the battery. Your hard drive could be spinning or seeking at the low end of tolerances, causing re-reads and leading to the extremely slow response. Slow fans could lead to overheating. And so on. In fact, the list of direct and consequential issues caused by a bad power supply is very long.
I suggest you try another power supply designed for your brand and model laptop. If you don’t want to purchase one from your original vendor, make sure that a replacement delivers exactly the same output voltage (and no less output amperage) and uses the same plug and polarization. (See Figure 4.)

Figure 4. This example transformer’s input accepts anything from 100 to 240 volts, at either 50 or 60 Hz. It delivers (outputs) 2.15 amps at 19 volts. Ideally, a replacement power supply should exactly match the specs of the original.
If yours is a common-model laptop, you might be able to borrow a power supply from a friend with the same system, to test whether your battery charging problems go away.
EBay and similar sites often list used power supplies for sale for small sums. These are usually offered after some other part of a portable system has died — a user has suffered a cracked screen, a failed hard drive, or some other trouble. These used power supplies can still have lots of life in them.
With luck, your next trip won’t be half so exciting!
DOCSIS 3.0 cable modem upgrade conundrum
Rick Tomaro’s cable company says he needs a new cable modem.
- “My cable company sent me e-mails suggesting I upgrade my current cable modem (I bought it several years ago) to get the full advantage of their new service. I called the company and a rep said it would be faster with a DOCSIS 3.0 modem. I’m still not sure what they’re changing, and it brought up a related question.
“I have a separate cable modem and a Linksys WRT546 router. If I decide to upgrade, would I be better off buying a new cable modem or a cable modem/router combo? I haven’t had any problems with my current cable modem and router and would be concerned about a cable modem/router combo. What if one part failed? Would I have to replace both?
“And I’m hoping, whatever your answer, that you have a recommendation as to what brand cable modem and/or router I should consider?”
DOCSIS, the Data Over Cable Service Interface Specification, rolled out in 1997. Version 2 came out in 2001; it mostly improved upload speeds. Version 3 was introduced in 2006, mostly to add support for IPv6, the new format for numeric Web addresses. (For background information on IPv6, see my Oct. 21, 2010, article, “Preparing for the switch to the IPv6 standard;” and Woody Leonhard’s March 17, 2011, Top Story, “Caution: Bumps in the road to IPv6.”)
The cable company rep was probably incorrect — or at least, oversimplifying — in saying that an upgrade to DOCSIS 3 will give you faster service, but it is possible that you’ll need a DOCSIS 3 setup to fully utilize IPv6, depending on how your cable company plans to implement it.
In any case, IPv6 is definitely here to stay, so all new networking gear we buy from here on out should be IPv6-compliant.
But because both IPv6 and DOCSIS 3 are industry standards, brand shouldn’t matter. Any major-brand DOCSIS 3/IPv6 gear should work fine and give you access to the DOCSIS 3/IPv6 services your cable company offers.
As for choosing separate or all-in-one boxes, consider that DOCSIS is a slowly changing standard. In contrast, LAN standards are evolving rapidly, with above-gigabit speeds available for wired connections and Wi-Fi subtypes a/b/g/h/j/n and y already available (depending on where you live), with faster versions constantly in the works.
Because of this, I agree with you that it can make good sense to use an inexpensive, plain-vanilla cable modem along with a separate, advanced router (and Wi-Fi access point, if you want). That way, as LAN and Wi-Fi standards evolve, you’ll be able to change your router as required without also having to needlessly churn the cable modem hardware at the same time.
Converting admin files to user files
Roger Meyer wants to convert an admin account to a standard user account without altering the account’s user files.
- “I’ve been running Windows 7 as an admin since the beta releases. How about an article on how to convert all my admin files to user (non-admin) files?”
I’m happy to say the procedure is easy, Roger!
First, create a new admin account with a new name and password. After you create the new admin account, log off or restart your PC.
When the sign-in screen appears, you’ll see the new admin account listed, along with your previous account(s). Select and sign into the newly created admin account.
After you’re in the new admin account, simply convert (the menu calls it Change the account type) the original account from admin to standard user. That’s all it takes!
If you need additional details about how to access and change account types, this Microsoft Help & How-to page covers the process, step by step.
Isn’t it great when what seems like a difficult problem turns out to be a snap to fix? I love problems like that!
| Feedback welcome: Have a question or comment about this story? Post your thoughts, praise, or constructive criticisms in the WS Columns forum. |
Welcome to the 64-bit era of Windows
 |
By Michael Lasky
In the brave new world of huge software packages and gigantic memory requirements, capacity counts. Here’s what you need to know about upgrading from 32-bit to 64-bit machines — because sooner or later, upgrades will happen to you. |
The new normal: 4GB of RAM and 500GB hard drives
The average PC sold today, desktop or notebook, has a 500GB hard drive, 4GB or more of RAM, and a blazing graphic processor — and costs less than the horse-and-buggy systems of the pre–Windows XP days. The escalating demand for hard-disk space and processing power is driven by the powerful software we now use and by ever-larger data files — especially digital images and video. Mindful of the need to let users adjust to change yet still have the option of upgrading legacy 32-bit machines, Microsoft offered both 32-bit and 64-bit versions of Windows 7 on the same installation disc, right from launch.
Although many Windows XP users still cling to their 32-bit systems as if they were life preservers on the Titanic, many more are moving to Windows 7 — and a surprisingly large number of those machines are 64-bit editions. Here’s why that change is good.
The move to 64-bit and Win7 goes hand in hand
Unlike any previous version of Windows, the use of a 64-bit operating system is tied closely with the rapid uptake of Win7. In July 2009, for example, Amazon.co.uk had more preorders for Win7 in just eight hours than it had had for Windows Vista in that OS’s first 17 weeks, according to a July 2009 BBC report. (I was unable to find Amazon U.S. preorder numbers.) Windows 7 quickly became the fastest-selling OS in Microsoft’s history.
And a lot of those sales were Win7 x64. A Microsoft blog stated that by June 2010, 46 percent of all PCs were running a 64-bit edition of the OS. It went on to report that only 11 percent of Vista PCs were using the 64-bit edition — three and a half years after that OS launched. The blog noted that, according to the NPD Group, 77 percent of April 2010, U.S. retail PC sales were Win7 x64 machines. That’s an astounding change.
Using 32-bit software: apps, yes; hardware, no
The first rule of using 32-bit code on Win7 x64 is that hardware drivers won’t run. You must use 64-bit hardware drivers for all internal and external devices.
Fortunately, the same is not true for applications. Just about any 32-bit Windows app that runs on XP will run without a snag on a 64-bit Windows system. That’s because of an integrated technology called Win32 on Win64 (WOW). This Win7 subsystem converts 32-bit API-call executables into 64-bit APIs. But the technology isn’t perfect. Although these converted executables work most of the time, they can fail if a particular application relies on proprietary, legacy 32-bit device drivers.
Another problem: On first look, it doesn’t seem that 32-bit apps have Registry entries. They do, but they’re buried in a subkey of a subkey. To maintain the integrity of the 64-bit Registry, Windows redirects 32-bit installed apps to the Wow6432Node key located below the primary Software key. You have to expand this key to see the 32-bit keys and values. For more on this, see Microsoft’s “32-bit and 64-bit application data in the Registry” page.
The ease of finding 64-bit hardware drivers has improved greatly since Win7 was first released. Peripheral manufacturers have even updated many older, legacy devices with 64-bit drivers. The two best resources for 64-bit drivers are the hardware vendors’ websites and Microsoft’s Windows 7 Compatibility Center (info).
Future-proofing: 64-bit provides power to spare
As Microsoft points out on a Help & How-to page, “A computer with a 64-bit version of Windows can use more memory — 4 GB (gigabytes) or more — than a PC with a 32-bit version of Windows, which is limited to about 3.5GB or less. (Even if a PC comes with 4GB or more of memory installed, a 32-bit version of Windows can use only about 3.5GB of that memory.)”
With the relatively low price for RAM these days, it should be no surprise that 4GB is the default configuration on most new PCs. Although 2GB is the minimum RAM required for running Win7 x64, 4GB is the real minimum needed to make good use of 64-bit processors and operating systems. (Up to a point, more RAM installed translates to more apps you can have open without loss of speed.)
There are some limitations to the amount of RAM that a particular version of Win7 x64 can support. For example, Windows 7 Professional, Enterprise, and Ultimate can address up to 192GB of RAM; Home Premium, by far the most common version installed today, supports 16GB; however, Windows 7 Home basic is limited to just 8GB. That’s still an impressive — and usually excessive — amount of RAM for most personal computing use.
Better security with a 64-bit operating system
Even the most passionate Windows XP user has to admit that it was a malware nightmare; we survived years of what seemed like endless rounds of patches. Antivirus protection is better in all versions of Windows 7, but even more so in 64-bit versions. While we still get security fixes for the 64-bit operating systems, these fixes are far fewer than on 32-bit systems.
There’s a significant reason a 64-bit OS is more secure: malware written as 32-bit software will usually not run on an x64 system. For example, it would be difficult for a 32-bit virus or rootkit to modify the 64-bit Win7 kernel.
When the time comes to update to Win7 x32
If you’ve decided to move to the 64-bit version of Win7, you have essentially two options: buy a new PC with Win7 x64 already installed, or add it to your existing system. The former is obviously the easiest route. You’ll know that all installed components and drivers are 64-bit compatible.
Whether you can upgrade an existing system depends on the age and design of its components — primarily the BIOS and CPU. Start by consulting Microsoft’s Windows 7 system requirements page and then run Windows 7 Upgrade Advisor (download page). Once the advisor app finishes examining your system, its 64-bit report page will tell you whether you can safely install Win7 x64. As shown in Figure 1, you might have to install the OS and then reinstall your apps and data. It’s a bit of work, but it should give you a clean system.

Figure 1. Windows 7 Upgrade Advisor’s 64-bit report can determine whether your system is Win7 x64–ready.
On some Windows XP systems, you can also check x64 compatibility by going to My Computer and selecting Properties. Under System, you might see x64 Edition.
If you’re already running Windows 7 x32 and want to upgrade, use the Performance Information tool already included with your OS. Click Start/Control Panel/Performance Information and Tools. Under Base score, click the View and print detailed performance and system information link. In the Systems section, you’ll see a 64-bit–capable listing, as shown in Figure 2.

Figure 2. If you want to know the bittedness of your current Win7 installation and whether your system is 64-bit–ready, run Win7’s built-in Performance Information tool.
Finally, I recommend you check out Microsoft’s Windows 7 Compatibility Center for a list of compatible third-party hardware and software.
Windows 8, now available as a developer’s preview download, comes in 32-bit and 64-bit flavors. (It currently has the same system requirements as Windows 7.) Given the proliferation of 64-bit hardware and, more slowly, 64-bit apps, it will be interesting to see who’s not using the 64-bit version of Microsoft’s next OS.
| Feedback welcome: Have a question or comment about this story? Post your thoughts, praise, or constructive criticisms in the WS Columns forum. |
Lessons learned from the Stratfor files
 |
By Robert Vamosi
Creating truly secure passwords can be difficult — at least for some security professionals, it seems. A recent data breach at the private intelligence firm Stratfor revealed some all-too-common password weaknesses. Here’s how to strengthen your own. |
Stratfor fails to protect customer data
If not for the players involved, this story might have gone down as just another company losing customer credit-card information to clever hackers. As detailed in a Jan. 11 Reuters report, the perpetrators were members of the infamous hacking group Anonymous (also referred to as AntiSec) and the victim was Strategic Forecasting Inc (Stratfor), a Texas-based political and economic analysis firm with an impressive list of private and public clients and subscribers.
According to various sources, the hackers broke into Stratfor in early December 2011 and acquired company e-mails and customer account information. They returned Christmas Eve to publicize the break-in on Stratfor’s own homepage and then cripple the company’s servers. Eventually, Anonymous claimed responsibility and reportedly used some of the stolen credit-card information to make sizable donations to charitable organizations.
The irony in this story is that Stratfor, a company focused on global intelligence and forecasting, had not bothered to encrypt its subscribers’ credit-card information. Moreover, its security system required subscriber passwords that were no more elaborate than what we might use for everyday computing.
Here are some lessons to learn from the Stratfor incident.
Rebuilding passwords from encrypted hashes
As reported in a Jan. 2 story, online news site The Tech Herald analyzed 860,160 of the nearly one million Stratfor password hashes publicly revealed by the hackers. (A hash is a fixed-length bit string that represents the original password.)
The publication easily cracked 81,883 of these hashes using a conventional desktop computer and the password-recover application, Hashcat (info page). They wrote in their analysis, “Anyone can do this; it’s as simple as loading the hashes, word lists, starting the cracking process, and walking away.” To understand how The Tech Herald was able to accomplish this feat, you have to understand how passwords work. You’ll then understand why creating secure passwords is important.
Password hashes are one-way encryptions, so named because they can’t be unencrypted. The only way to crack a one-way encryption is to generate another one-way encryption that matches the original. When a PC user types in a password, the computer or Web server compares the new hash with the old hash and looks for a match. A mistyped password creates a new, unique hash that won’t match the original. Revealing the original password from the hash file requires software such as Hashcat.
Using brute-force password-cracking software
The basic method for cracking a password is to generate a matching hash — typically by trying all possible variations of numbers, letters, and special characters. This is the brute force technique. Well-known (and free) password-cracking apps such as John the Ripper, Hash Suite, and Hashcat pick through simple passwords relatively quickly, but given enough time and resources, harder passwords can also be cracked. (There are legitimate uses for these programs, such as recovering passwords lost when an employee leaves the company.)
In addition to password-cracking software, you also need hash dictionaries — lists of common passwords and their encrypted hashes. A good brute-force program and dictionary can render results in a surprisingly short time. The Tech Herald cracked roughly 10 percent of the Stratfor passwords within five hours. From its analysis, The Tech Herald came to an easy conclusion: Stratfor’s subscribers, people who should be very familiar with secure computing environments, were just as lazy about passwords as the rest of us.
Examples of easily cracked “secure” passwords
Given those rules, you might expect a password such as #John316 would be secure — right? Not so, according to The Tech Herald; that particular password was among those cracked within the first five hours.
So were many variations on the password password: i.e., PassWord123!@#, Password0032, password1234, password1981, password2009, password9191, Password999, P@$$w0rd123, Password01!, password101, Password12*, password122, Password123 — all of which were found within the Stratfor hash files.
The majority of the Stratfor passwords had six to eight characters and included proper names such as Robert, George, Daniel, John, Hannah, Thomas, Charles, Matthew, and Michael.
So once again, avoid proper names! They’re easy pickings for any good password-cracking program.
Websites often enable poor password habits
Although all websites set rules for the passwords they allow, the implementation of those rules is extremely inconsistent. A few years ago, I worked as an analyst for a financial-services firm. For one of my reports, I tested the password strengths of various online-banking sites. The list of banks with weak password requirements is proprietary, but I can say about 10 percent of the top U.S. banks examined had weak password policies in place.
These weaknesses included “secure” sites that didn’t allow special characters. (Special characters could make a site open to cross-site scripting attacks, where the special characters might trigger malicious actions within the Web server’s SQL database — something that a good SQL policy would avoid. But I digress.) Other sites allowed fewer than six characters or didn’t include space for eight or more characters. Still others didn’t allow the use of capitals or numbers. Many sites didn’t enforce password lockouts after three misses.
Microsoft’s rules for creating secure passwords
Creating a secure password is not all that difficult; it just takes a little discipline. In its “Create strong passwords” page, Microsoft breaks password creation into four components: length, complexity, variation, and variety. It recommends making up a short phrase, removing the spaces, misspelling one word, and randomly capitalizing letters. It also recommends including numbers — to which I add special characters as well.
Microsoft recommends not using any of the following: dictionary words from any language, words spelled backwards, common misspellings of dictionary words, or common abbreviations. Don’t use recognizable sequences or repeated characters (such as 12345678, 222222, abcdefg) or adjacent letters on a QWERTY keyboard. Most important, don’t use personal information such as your name, birthday, driver’s license number, passport number, or similar information.
Use a password manager with complex passwords
I believe that the best passwords are complex. Good passwords should consist of at least eight characters — with at least one capital, one numeral, and one special character. If a site limits the length, at least use the other three requirements. Finally, don’t use the same password for multiple sites.
Given that you’ll end up with numerous complex passwords, a password-management program is a must. With a good password-management app, you need to remember only one password — the one that accesses the app. In most cases, simply click the site you want to visit on a drop-down menu, and the program will automatically fill in the site’s password.
I’m a fan of 1Password (site), which lets you access password lists from any PC. The app is a bit pricey at U.S. $50, but it supports Windows, OS X, iPads, iPhones, and Android-base smartphones.
Another good password-management system is IronKey Personal ($60 and up; info page), which uses secure USB keys. (Unfortunately, the keys sometimes get left at home or at the office.) For just one computer, many malware-protection suites also contain fairly robust password-management systems as well.
Passwords should also be written down and stored in a safe place, but with the caveat that they are coded. For example, the password to your online mortgage payment might be listed under “Shelter” instead of the actual bank account name. I don’t recommend leaving such a list close to a computer, however. At the very least, store paper-based password lists in another room of your home or office. You’ll find an interesting discussion on the pros and cons of storing written passwords in a Schneier on Security blog.
| Feedback welcome: Have a question or comment about this story? Post your thoughts, praise, or constructive criticisms in the WS Columns forum. |
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Thunderbird release notes for 128 esr have disappeared
by
EricB
2 hours, 15 minutes ago -
CISA mutes own website, shifts routine cyber alerts to X, RSS, email
by
Nibbled To Death By Ducks
2 hours, 43 minutes ago -
Apple releases 18.5
by
Susan Bradley
3 hours, 3 minutes ago -
Fedora Linux 40 will go end of life for updates and support on 2025-05-13.
by
Alex5723
4 hours, 9 minutes ago -
How a new type of AI is helping police skirt facial recognition bans
by
Alex5723
4 hours, 47 minutes ago -
Windows 7 ISO /Windows 10 ISO
by
ECWS
11 hours, 43 minutes ago -
No HP software folders
by
fpefpe
12 hours, 28 minutes ago -
Which antivirus apps and VPNs are the most secure in 2025?
by
B. Livingston
4 hours, 41 minutes ago -
Stay connected anywhere
by
Peter Deegan
17 hours, 51 minutes ago -
Copilot, under the table
by
Will Fastie
9 hours, 4 minutes ago -
The Windows experience
by
Will Fastie
1 day ago -
A tale of two operating systems
by
Susan Bradley
15 hours, 1 minute ago -
Microsoft : Resolving Blue Screen errors in Windows
by
Alex5723
1 day, 5 hours ago -
Where’s the cache today?
by
Up2you2
1 day, 20 hours ago -
Ascension says recent data breach affects over 430,000 patients
by
Nibbled To Death By Ducks
1 day, 13 hours ago -
Nintendo Switch 2 has a remote killing switch
by
Alex5723
13 hours, 51 minutes ago -
Blocking Search (on task bar) from going to web
by
HenryW
1 day, 21 hours ago -
Windows 10: Microsoft 365 Apps will be supported up to Oct. 10 2028
by
Alex5723
2 days, 14 hours ago -
Add or Remove “Ask Copilot” Context Menu in Windows 11 and 10
by
Alex5723
2 days, 14 hours ago -
regarding april update and may update
by
heybengbeng
2 days, 15 hours ago -
MS Passkey
by
pmruzicka
1 day, 17 hours ago -
Can’t make Opera my default browser
by
bmeacham
2 days, 23 hours ago -
*Some settings are managed by your organization
by
rlowe44
2 days, 9 hours ago -
Formatting of “Forward”ed e-mails
by
Scott Mills
2 days, 22 hours ago -
SmartSwitch PC Updates will only be supported through the MS Store Going Forward
by
PL1
3 days, 17 hours ago -
CISA warns of hackers targeting critical oil infrastructure
by
Nibbled To Death By Ducks
4 days, 2 hours ago -
AI slop
by
Susan Bradley
1 day, 20 hours ago -
Chrome : Using AI with Enhanced Protection mode
by
Alex5723
4 days, 4 hours ago -
Two blank icons
by
CR2
1 day, 12 hours ago -
Documents, Pictures, Desktop on OneDrive in Windows 11
by
ThePhoenix
1 day, 14 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

