
|
There are isolated problems with current patches, but they are well-known and documented on this site. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Sun, Apple, Microsoft install chaff with patches
In this issue
- TOP STORY: Sun, Apple, Microsoft install chaff with patches
- KNOWN ISSUES: Gmail activity log helps you detect hijacking
- WACKY WEB WEEK: Water fights that will make you cry uncle
- LANGALIST PLUS: Free utilities make Windows smaller, faster
- IN THE WILD: Laptop rootkit is widespread but likely harmless
- PATCH WATCH: Heavy patch week to block Web-based attacks
Sun, Apple, Microsoft install chaff with patches
 By Susan Bradley
By Susan Bradley
When you apply a security update for one of the programs on your PC, beware of uninvited software that wants to come along for the ride.
Vendors are more and more often going over the line, piggy-backing unsolicited commercial products and services onto crucial security patches.
If you’re like many people, you were tricked into installing Apple’s Safari browser as part of an iTunes or QuickTime update — a marketing tactic the company has been employing for more than a year. (I reported in my March 27, 2008, Patch Watch column that Apple had quietly started installing its browser using a little-noticed check box.)
You may also have succumbed to Microsoft’s incessant offer of Silverlight and Office Live as part of the Microsoft Update service. And you may have tired of saying “no!” to downloading Internet Explorer 8. (I don’t feel IE 8 is a necessary upgrade, due to IE 7’s relative security and IE 8’s incompatibility with some sites, as I describe below.)
Now, the latest Sun Java update shows how cavalier some vendors have become in taking advantage of software updates, including vital security patches.
The latest Sun Java SE Update 16 (6u16), released on Aug. 11, includes seven security updates and fixes a few bugs. What the release notes don’t document, however, is that this update comes with a surprise.
The download process starts out normally enough, with the usual coffee-cup update icon in the notification area of Windows’ taskbar. (See Figure 1.)
![]()
Figure 1. Sun’s Java icon — the coffee cup at the far left — indicates the availability of an update.
However, after you begin the update, a confusing offer to download and install a 30-day trial of Carbonite Inc.’s commercial backup software appears. A small check box is preselected for download and installation. (See Figure 2.)
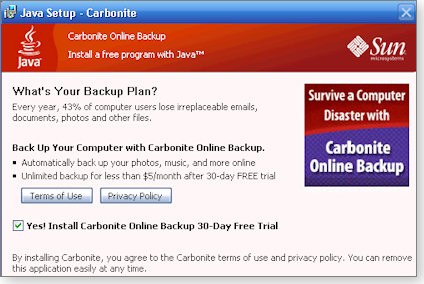
Figure 2. The option to install a trial version of Sun’s Carbonite backup software is prechecked in the Java updater.
Some Java patchers are not offered Carbonite but instead get Microsoft’s Bing search toolbar, which is preselected on many systems. (See Figure 2.)
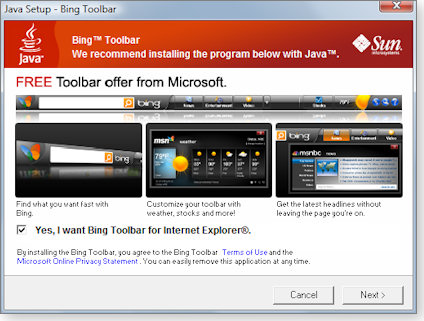
Figure 3. Sun’s Java updater preselects the option to install Microsoft’s Bing search toolbar for IE along with the Java update.
That’s right, ladies and gentlemen. Not only may we have to uninstall random toolbars if we’re not careful with our Java updates, now we have to remove trial versions of commercial software that vendors quietly attached to a security update.
| UPDATE 2009-08-20: In the Aug. 20, 2009, Known Issues column, reader Pete Poorman notes that Adobe’s updates for Flash Player and Adobe Reader attempt to install the Google Toolbar by default. |
Microsoft pushes IE 8 as ‘critical’ to your PC
Microsoft is one of the biggest offenders in promoting nonsecurity updates via its security mechanism.
First in 2006, and again in 2007, the Redmond company installed its intrusive Windows Genuine Advantage app as though it were a “critical security upgrade,” as I described in a June 14, 2007, column.
In the latest such case, you’ll find that Microsoft has prechecked Internet Explorer 8 when you use Automatic Updates and choose the option to view available updates.
The company argues that IE 8 is a critical update to your operating system. In reality, the program may conflict with other software on your PC.
I’m postponing deployment of IE 8 on my computers, because I continue to encounter compatibility problems in my testing. The glitches are slowly being resolved, but I’m still not ready to give a blanket recommendation to upgrade to IE 8, nor am I comfortable applying it to the production systems I manage. (I described the problems and some solutions in a column on May 28.)
As the person in charge of managing PCs in my company, I need to test the program before it’s installed on production systems. By preselecting the IE 8 installation, Microsoft eliminates my ability to conduct responsible testing.
Even while claiming that IE 8 is a critical update, Microsoft continues to support the hopeless old version 6 of IE, as stated on the company’s IEBlog. IE 6 long ago stopped being a defensible browser and cannot now be considered secure by any stretch of the imagination.
If you’re still running IE 6, you should upgrade to IE 7 immediately. If your company uses a line-of-business app that requires IE 6, isolate that machine from the Internet and use it only until that app is upgraded.
Installing IE 8, however, should be considered optional and should not be associated with security patches.
(In an unrelated move, IE 8 will no longer silently make itself a PC’s default browser when users select the Express installation option. The change was revealed in a U.S. Department of Justice antitrust compliance report, as reporter Grant Gross explains in an IDG News Service article.)
Let’s put a halt to any marketing in updates
I understand that the publishers of “free” software sometimes need to push other programs that generate revenue. Whenever a vendor is offering useful software at no cost, I’m willing to consider some software bundles at the time of original download.
To avoid tricky bundles, you should consult sites offering advice about specific problems. One of the best is the Calendar of Updates’ Installers Hall of Shame, which lists uninvited programs that ride along with various apps.
It’s a completely different matter to use security updates to sneak software onto our PCs — there’s simply no other term for it. Corrupting a vendor’s security channel to promote a marketing opportunity violates our fundamental right to control the programs installed on our systems.
When it comes to bug fixes and security patches, I need to be able to trust that the changes vendors are making to my system are intended only to protect me. I strongly object to attempts to install any nonessential software as part of the update process.
To me, the marketing tie-ins described above step way over the line. I hope you’ll join me in urging software vendors to limit security updates to nothing but security updates.
Susan Bradley recently received an MVP (Most Valuable Professional) award from Microsoft for her knowledge in the areas of Small Business Server and network security. She’s also a partner in a California CPA firm.
Gmail activity log helps you detect hijacking
 By Dennis O’Reilly
By Dennis O’Reilly
A line at the bottom of the Gmail window indicates when your account was last used and also links to more-complete usage info.
You can use this activity log to determine whether someone has guessed your password and taken over your account.
In the Aug. 6 Top Story, “Gmail flaw shows value of strong passwords,” WS contributing editor Becky Waring explained how to create strong passwords that are easy to remember. Her story was inspired by the disclosure of a Gmail weakness that allows hackers to test thousands of passwords per day and take over poorly defended accounts.
A reader named James points out that the Gmail activity log can alert you to unauthorized use of your account:
- “As a result of [reading] Becky Waring’s article — which I have rated as superb, by the way — I went back to Scott Spanbauer’s articles about the earlier Gmail flaws. [See Scott’s April 23 story, “Gmail accounts hacked via unpatched hole,” and his May 7 follow-up, “Google silently corrects Gmail CSRF hole.”]
“I help run a bulletin board that uses the commercial Invision Power IP.Board software. In recent months, we have been bombarded with spammers, mostly coming from Gmail accounts. So I can confirm that these exploits — both patched and unpatched — have been and are being used by the bad guys.
“If you’re a Gmail user and are concerned as to whether your account password has been compromised, there’s a link at the bottom of the screen that shows when your account was used and from where.
“At the bottom is a message Last account activity: xx minutes ago at IP xxx.xxx.xxx.xxx [or on this computer] and a link: Details. Click the Details link, and a pop-up window shows all sign-ins over the last couple of days, together with other useful info and a button to Sign out all other sessions.“
Figure 1 shows the information presented in the Gmail account activity log when you click the Details link.
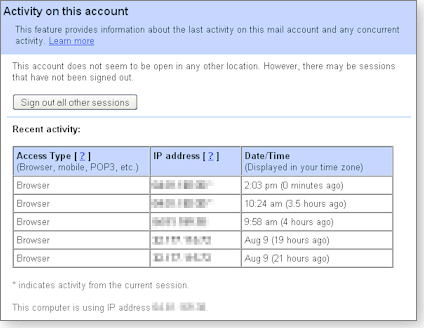
Figure 1. View recent activity on your Gmail account to determine whether someone other than you has signed in. (All IP addresses are obscured in this image.)
If you find unfamiliar IP addresses or activity recorded when you weren’t using the account, reset your password immediately and notify Google of the breach.
| UPDATE 2009-08-20: In the Aug. 20, 2009, Known Issues column, reader Dan Juroff describes how he used Gmail’s activity log to detect an attack on his company’s network. |
Microsoft’s ambiguous advice on strong passwords
When it comes to crafting strong passwords, it can be difficult to know whom to believe, especially when the same source offers conflicting advice. A reader who goes by the name of RockDoc was befuddled by contradictory information on Microsoft’s site:
- “Waring discussed the usual caveats and solutions to designing better passwords and provided a link to [Microsoft’s] Windows password checker, which also links to a document in which Microsoft discusses password design.
“In that latter document, Microsoft properly notes that passwords with obvious substitutions are less safe than otherwise:
Avoid using only look-alike substitutions of numbers or symbols. Criminals and other malicious users who know enough to try and crack your password will not be fooled by common look-alike replacements, such as to replace an ‘i’ with a ‘1’ or an ‘a’ with ‘@’ as in ‘M1cr0$0ft’ or ‘P@ssw0rd.’ But these substitutions can be effective when combined with other measures, such as length, misspellings, or variations in case, to improve the strength of your password.
“In a deliciously ironic (and most certainly inadvertent) piece of engineering, however, Microsoft’s own password checker rates the poorly designed password M1cr0$0ft as strong! Gotta love ’em!”
Some readers questioned the security of entering passwords for strength testing on Microsoft’s unencrypted Web page. This shouldn’t pose a risk, though, because Microsoft states on the page itself that no information is transmitted to Microsoft’s servers or across the Internet in any way:
- “Password Checker does not collect, store, or transmit information beyond the computer that you use to access Password Checker. The image works on your computer desktop until you navigate away from the page.”
The page operates by downloading a small JavaScript application to your browser. This app computes each password’s weak/moderate/strong rating locally. You can demonstrate this by temporarily disabling JavaScript in your browser, in which case the password checker no longer functions.
If anyone has evidence that Microsoft transmits across the Internet the passwords entered into this browser app, let us know immediately using the Windows Secrets contact page.
Bill McGarry reports that Microsoft’s app rates an entered password as “strong” if it is merely eight or more characters in length and has two out of three of the following: both uppercase and lowercase letters, one or more numerals, and some punctuation mark. To be sure, those are good rules of thumb, but Password1 (one of the first strings an attacker would try) would receive a “strong” rating.
Several people told us about other password-strength checkers. One that goes to greater lengths than Microsoft in explaining what constitutes a weak or strong password is Password Meter. It’s available as an online password checker and also as a downloadable freeware program. You can find both at the Password Meter site.
No matter how strong a password you select, it won’t remain secret if you enter it on a machine that’s infected with a keylogger. For this reason, you shouldn’t sign in to online banking sites at random Internet cafés or any place without good antivirus protection.
Ensure passwords remain useful to your heirs
Becky’s article recommends that you avoid writing your passwords on sticky notes or saving them in an unencrypted text file on your PC. However, there’s one instance when this otherwise-sound advice doesn’t apply, as Allan Treadwell explains:
- “Although I agree with the article on strong passwords, there’s one small-but-important thing left out. I had a friend who died recently of a brain tumour (he was 59) and, of course, he had many passwords that were not stored on the computer, only in his head.
“As his memory went very rapidly, he forgot them, so his wife could not access some sites/programs easily, and others not at all.
“So I would add to the article: Do write down your passwords and tell your next of kin where they are or how to access them.”
MarketWatch columnist Andrea Coombes offers free advice on this subject in a July 20 article, “Don’t take your passwords to the grave.”
For the ultimate — and I do mean ultimate — in online security, check out a service such as Legacy Locker, which promises to “grant access to online assets for friends and loved ones in the event of loss, death, or disability.” A free trial account lets you protect three assets, assign one beneficiary, and create one “legacy letter.”
For U.S. $30 a year or a one-time fee of $300, you can protect an unlimited number of assets, assign any number of beneficiaries, create as many legacy letters as you wish, back up important documents, and even upload a “good-bye” video.
Can I leave my folder full of corrupted Office files to Steve Ballmer?
| Readers James, RockDoc, Bill, and Allan will each receive a gift certificate for a book, CD, or DVD of their choice for sending comments we printed. Send us your tips via the Windows Secrets contact page. |
The Known Issues column brings you readers’ comments on our recent articles. Dennis O’Reilly is technical editor of WindowsSecrets.com.
Water fights that will make you cry uncle
 |
By Stephanie Small
Remember when playing with squirt guns was the most fun a kid could have? The little streams of water kept you cool while also providing endless hours of fun. Then Super Soakers reinvented the water fight, blasting water at your foes in torrents! Now the water fight has been taken to a whole new level with the arrival of super-duper waterboards. Sustained, powerful jets of water pulverize your opponents and make them obey your every command, all while keeping you safe and protected behind a plastic shield. Give it a try this summer at the park, in the yard, or on the beach. Your friends won’t know what hit them! Play the video |
Free utilities make Windows smaller, faster
 |
By Fred Langa
Microsoft keeps building more and more into Windows, but sometimes all you want or need is a bare-bones, minimal OS. If small and fast is what you want, several free programs let you remove unnecessary Windows components to improve your system’s performance and reliability. |
Put your Windows installation on a diet
John Casey is looking for a way to streamline his Windows installation by uninstalling the components he doesn’t need:
- “Have you written articles about which components of Windows are safe to uninstall? I’m already a Firefox/Thunderbird user and I want to migrate to OpenOffice. Can I safely remove IE 8, the .NET Framework, etc.? I’m not a developer, I just use SAAS business applications.”
Many components and tools bundled with Windows can indeed be removed. There are two basic approaches. One technique involves removing Windows components by hand. The second and better of the two techniques takes a little doing but results in a fresh, stable, known-good minimal installation.
In fact, the second of the two approaches uses the same basic technology that OEMs use to produce their customized installations of Windows. (Of course, OEMs are more apt to put extra stuff in rather than take anything out!) This is also the same technology used to produce a “live CD” — a self-contained, bootable CD and repair-disk version of Windows.
1. Perfectly good technique
The first approach is to start with a normal Windows installation and then uninstall unneeded components manually. Some items you remove entirely, while others you replace with slimmer alternatives. This approach is less “clean” than producing a fresh, from-scratch, minimal installation using one of the tools described below in the second technique. Still, it can be done.
The IEXBeta discussion forum offers instructions in its “Ultra-minimal tweak guide for Windows.” Also, NeoWin.net provides a similar discussion called “[Guide] Minimal Windows.”
2. Better technique
• BartPE. Perhaps the best-known tool for streamlining Windows is Bart’s Preinstalled Environment (BartPE), a bootable live Windows CD/DVD. The program is available from the vendor’s site. BartPE is the great-granddaddy of free tools of this sort, but the program is somewhat geeky to use.
• NLite. Another program, nLite, is also free and is a little easier to use than BartPE. The program has its own devoted following; you can download a copy from the company’s product page. NLite is less generic than BartPE and has a specific focus on what the company calls “component removal,” which produces a lean, compact Windows installation.
• Winbuilder. Winbuilder sports a slicker interface, and I consider it the easiest of the three programs to use. An added feature of Winbuilder is its VistaPE option. The other two tools focus mostly on XP. You’ll find a Winbuilder link on the company’s download page.
With these three tools or similar utilities, you can produce a new, legit, stripped-down copy of Windows. You end up with a fresh, fast, small, efficient, and minimal OS.
So yes, John, it’ll take a little work, but you can indeed produce a minimal build that contains only the components you need and no more!
Disk compression yields twice the space
Jeff Baker’s old hard drive is out of space, but he doesn’t think the drive is worth replacing with a new one:
- “I’m running XP on an old PC from 2002 and the C: partition is only 20GB. Therefore, I’m looking for ways to free up space on the partition. Half the drive is filled with files in C:Windows with names like $NtUninstallKB835409$ and $NtServicePackUninstall$.
“My question is, what are these files used for? Are they important, and can I just delete them in order to free up some space?”
Although a new drive can be very inexpensive and would give you the extra storage space you seek, I can understand your reluctance to invest in upgrading a very old PC. That leaves you with two options for gaining space.
First, the answer to your specific question is yes, you usually can delete the $NtUninstallKB… files and $NtServicePackUninstall$ folders and files. These are uninstall files from Windows updates and service packs. Once you’ve decided to keep a given update or service pack, the uninstall files serve no further purpose and may be deleted.
For more information, see “Is it OK to delete old install files?” in my Dec. 11, 2008, column.
Your second option is to use disk compression, which is a feature built into all current versions of Windows, although it’s turned off by default. Disk compression is a proven way to get more storage out of a hard drive — sometimes almost doubling the amount of available space.
For all the particulars, see Microsoft Knowledge Base article 307987, “How to use file compression in Windows XP.” Although the title specifies XP, the process is essentially the same in all recent Windows versions.
One caveat: Disk compression can make your PC a bit slower. It’s most noticeable on older, less-powerful systems, but if you try disk compression and don’t like it, just reverse the process and uncompress your drive.
Why won’t Media Player minimize properly?
Sam Stamport upgraded to Vista and lost a favorite function of Windows Media Player:
- “Whenever I minimized Media Player on XP, a nice, compact control panel was placed on the taskbar with a pause/play button, volume control, etc. I recently bought a new computer with Vista, but now the compact control panel doesn’t appear when I minimize Media Player. How can I get the XP functionality back?”
Just right-click any open area on the Windows taskbar, select Toolbars, and then choose Windows Media Player. You’ll see a check mark appear next to the Windows Media Player entry. This indicates that the program’s taskbar control panel option is now turned on.
That’s it. You’re done: a one-time, one-click fix!
Floppy-based upgrades on floppyless PCs
Jim Mather ran into a problem with an older copy of Microsoft Office. But the problem — and solution — actually applies to all floppy-based installations, not just MS Office:
- “I first bought MS Office when it came on floppy disks. I’ve upgraded many times since. To load a new upgrade version of MS Office requires that I prove I’ve bought a full version somewhere along the way.
“In the past, I’ve had to first load my original version from floppy. Is there any way I can put a new upgrade version of MS Office on a new computer without having to load my original, full version from floppy as proof?”
Yes, Jim, most likely there is a way to do so. In addition, you can probably migrate the old installation files off floppies permanently so that any future reinstallation takes a fraction of the time a floppy install requires.
The simplest forms of floppy-based software validation look for certain specific files. This type of software is very easy to migrate to a CD, DVD, or other medium.
First, copy everything from all the setup floppies to the root folder of the CD or DVD. Next, copy each separate floppy to its own subfolder on the same disc. If each floppy has its own volume label, such as BOOTDISK, DISK1, or DISK2, use the same names for the new folders. If the original floppies have no volume label, make up a clear, sequential name for each folder — DISK1, DISK2, etc.
When you’re done, all the files from all the floppies will be in the new disc’s root folder. In addition, the contents of each separate floppy will be in a separate subfolder as well.
Test your new installation disc by clicking setup.exe, install.exe, or whatever the root directory’s initial launch file is called. If that doesn’t work, try clicking the same file from inside the first subfolder. Most older floppy-based setup software will work with one or the other location.
If the setup process begins normally, you’re probably home free. To test it without interfering with your current setup, consider using a virtual PC. See my July 2 column for more info.
When upgrade software asks to see the setup floppy or some other specific floppy, use the Browse function to point the upgrade program at the correct location on the CD or DVD to which you transferred the floppy data. In most cases, the software will accept the relocated files as genuine.
If the above steps don’t work, use special software that makes a byte-for-byte image of each floppy disk and then employs “virtual floppy” software to mount that image and run the programs. The software runs from your hard drive, but the program will think it’s still on its original, physical floppy disk.
It’s not difficult to do this, but there are several steps involved. A Freeware Review how-to article includes links to the associated free software you’ll need.
One or both of the above techniques will usually let you migrate floppy-based software to a new medium. You can then use your new non–floppy-based copy to validate future updates or reinstall the original software in its entirety, if it comes to that. Because it’ll run at modern CD/DVD or hard-drive speeds instead of at the pokier floppy rate, such reinstalls will go much, much faster!
Fred Langa is editor-at-large of the Windows Secrets Newsletter. He was formerly editor of Byte Magazine (1987–91), editorial director of CMP Media (1991–97), and editor of the LangaList e-mail newsletter from its origin in 1997 until its merger with Windows Secrets in November 2006.
Laptop rootkit is widespread but likely harmless
 |
By Robert Vamosi
A presentation by two researchers at a recent security conference suggests that one particular rootkit-like program may be present in 60% of all laptops. The absence of strong authentication in this well-intentioned, widely distributed program has the potential to compromise systems, according to the researchers, but I believe you actually face little risk. |
Black Hat bark may be worse than its bite
There was considerable buzz around SMS and SSL vulnerabilities at this year’s Black Hat Briefings July 25–30 in Las Vegas. But the lion’s share of attention went to a 20-minute presentation given by Core Security researchers Alfredo A. Ortega and Anibal Sacco.
In a PDF paper titled “Deactivate the rootkit,” Ortega and Sacco said they were initially interested in showing how rootkits can infiltrate a PC’s BIOS. In the course of their research, however, they said they found that something with the potential to become a rootkit — Absolute Software’s Computrace LoJack for Laptops — was already embedded within their test laptop.
The concept is this: If a laptop with Lojack installed is stolen, the company can recover the device by pinpointing its IP address when the laptop connects to the Internet. Ortega and Sacco said the product may be embedded in as many as 60% of the laptops sold since 2005. Those notebook PCs use a BIOS from Phoenix Technologies that includes the LoJack detection system.
The researchers noted that “the antitheft agent must be stealthy, must have complete control of the system, and most importantly, must be highly persistent.” Specifically, the agent must be buried deep within the BIOS to survive a hard-drive wipe by thieves.
Ortega and Sacco pointed out that this degree of stealth is consistent with that of rootkits. The big difference is that rootkits are malicious, while antitheft agents are intended to be helpful.
The problem highlighted by the researchers in their presentation is the lack of strong authentication within the Computrace agent. Sacco and Ortega argue that this weakness could lead to a complete and persistent compromise of an affected system. The researchers suggest that someone could alter the agent so that the LoJack component becomes a malicious rootkit.
Absolute Software refuted the claim in a press release issued July 30. The company’s response includes this statement:
- “Any alteration to the BIOS module will cause any popular antivirus software to alert the customer. More importantly, if the BIOS of a computer has been compromised by an attacker, that machine is exposed to innumerable other vulnerabilities far beyond the scope of the Computrace BIOS module.”
Frankly, I was surprised that this talk received so much media attention. I don’t see any problem, and I don’t recommend removal of the Computrace agent from a laptop’s BIOS — in part because doing so is difficult. The agent lives in the NVRAM (nonvolatile RAM) and not in the CMOS chip, where BIOS settings are normally edited and stored.
Messing around with your system’s BIOS could leave you with an expensive brick, if you’re not careful. Until there’s a legitimate threat, I’d let well enough alone.
For more on rootkits and their removal, see WS contributing editor Ryan Russell’s Jan. 22 Perimeter Scan column, in which Ryan describes how he expelled a rootkit from one of his PCs.
New threat to XP, Windows Server 2003 systems
For the past several months, there have been reports of a local privilege escalation vulnerability affecting the NtUserConsoleControl function in the win32k.sys file on Windows XP and Server 2003 machines. Microsoft disputes the potential for danger posed by this security hole, however.
Jonathan Ness, a Microsoft software engineer, said in a June 11 post on the company’s Security Research & Defense blog that unchecked pointers in such privileged services as NtUserConsoleControl are reliability issues, not security vulnerabilities:
- “The Administrator to SYSTEM ‘escalation’ is not a security boundary we defend — it is impossible to defend Windows from an administrator armed with a malicious EXE. In the end, you’ve got to trust your administrators.”
That didn’t stop the U.S. National Institute of Standards and Technology from adding this security hole on Aug. 4 to its National Vulnerability Database as CVE-2009-2653. NIST says the flaw “allows local administrators to bypass unspecified ‘security software’ and gain privileges via a crafted call that triggers an overwrite of an arbitrary memory location.”
The vulnerability affects Windows XP Home Edition (SP1, SP2, and SP3), Windows XP Professional Edition (SP1, SP2, and SP3), and Windows Server 2003 (SP1 and SP2).
The reason for concern is that there is now proof-of-concept code available on the Internet. More about the code can be found on the NT Internals site.
The presence of a proof-of-concept is not the same as the delivery of full-blown malware targeting this hole. Still, the threat should be taken seriously. The workaround is solid security advice:
- Administrators should allow only trusted users to access local systems.
- Users should avoid following unsolicited links and verify the authenticity of unexpected links before following them.
- Users should also avoid opening e-mail messages from spam sources.
Comcast redirects URL typos to ad pages
The drill is familiar: When you type into your browser’s address bar a URL that doesn’t exist, you see a “404” error or a page of search results based on your query. The “oops” page could be generated by your browser’s default search engine, but most often it’s from your ISP.
Many Comcast customers aren’t happy with the so-called Domain Helper service the company launched on July 9.
What’s obnoxious about Comcast’s bad-URL redirect is the amount of advertising on the resulting page. Comcast isn’t the only ISP to pull such a stunt; Earthlink and others have tried presenting their customers with such ad-laden “oops” pages as well.
My recommendation is to assert some control over the matter by choosing your own default page-not-found setting. I use the OpenDNS service for this purpose. You’ll find more information about OpenDNS’s redirect service on the company’s site.
In her June 11 Top Story, contributing editor Susan Bradley described how to set up OpenDNS as a way to avoid common malware. Basically, you replace the DNS servers in your computer’s network settings with two OpenDNS-controlled IP addresses: 208.67.222.222 and 208.67.220.220.
Also, the July 9 Top Story by contributing editor Becky Waring presented techniques that optimize OpenDNS. She also responded to some readers’ concerns about the reliability of the service.
I agree with Becky: The handful of glitches a few people have experienced when using OpenDNS are a small price to pay for the security provided by this valuable free service.
WS contributing editor Robert Vamosi was senior editor of CNET.com from 1999 to 2008, writing Security Watch, the winner of the 2005 MAGGIE Award for best regularly featured Web column for consumers. He is currently a security, risk, and fraud analyst for a Bay Area financial services research firm.
Heavy patch week to block Web-based attacks
 |
By Susan Bradley
The Active Template Library (ATL) glitch in Microsoft’s Visual Studio, which was the subject of last month’s out-of-cycle update, requires yet more application patching this week. Outlook Express, Windows Media Player, and various ActiveX controls are all vulnerable to the ATL security hole. |
MS09-037 (973908)
A single weakness leads to multiple patches
My July 30 news update described Microsoft’s out-of-cycle patches for a problem caused by a single typo in the company’s Visual Studio Active Template Library. Unfortunately, we’re not done patching this glitch.
Released this week on Patch Tuesday were updates for Outlook Express, Windows Media Player, the Windows ATL Component, the DHTML Editing Component ActiveX control, and the MSWebDVD ActiveX control. The patches affect Windows 2000, XP, Vista, Server 2003, and Server 2008. Windows 7 and Windows Server 2008 R2 are reportedly not affected.
There are so many individual patches for this vulnerability that you need to review the list presented in Microsoft security bulletin MS09-037 to find the ones that apply to your system.
In my testing, none of these updates caused any problems.
Even if you previously installed the Internet Explorer patches described in MS09-034 (972260), you still need to install the updates for Outlook Express, Windows Media Player, the ATL components, and the DHTML ActiveX control offered to your systems by the Windows Update service. On 64-bit workstations, you may also be presented with a patch for the MSWebDVD ActiveX control.
Just be sure to uncheck the entry for Internet Explorer 8 prior to downloading this month’s security updates, if you prefer to postpone upgrading the browser — as I suggest you do. (See Figure 1.) My reasons for preferring IE 7 to IE 8 are discussed in today’s Top Story.

Figure 1. Uncheck the option to install Internet Explorer 8 prior to downloading this month’s security updates.
This week’s updates block exploits that target the ATL security hole in Windows apps and Internet Explorer. But you can expect more patches for this vulnerability from third-party software vendors once they’ve recompiled their code and are ready to distribute new versions of their applications. If you have programs that use the file atl.dll, contact the vendors about receiving an update.
That said, I’m unaware of any exploits that specifically attack vendor applications. Still, I fully expect to see more vendors patching this glitch in their programs. Stay tuned; I don’t think we’re done with this one yet.
Heavy patch load means forced updates possible
Windows PCs will receive as many as 15 patches from Microsoft this month. That means we may experience a recurrence of unexpected updates on systems that are configured not to install updates until the user permits it. The problem with unexpected updates was reported in WS contributing editor Scott Spanbauer’s June 25 Top Story.
In months with a high number of updates, MS throttles its servers, which prevents some patches from being downloaded fully. When Automatic Updates is set to merely notify you of patches — or download but not install them — the “updates are available” icon (yellow in XP, blue in Vista) may not display as expected. When you shut down or restart a PC, you may not realize that some patches that have downloaded completely will be installed automatically.
If your PC uses a “don’t install” Automatic Updates setting, look for the telltale exclamation mark on the shutdown icon, indicating that updates are queued up for installation. In fact, it may be best to browse to the Microsoft Update site and install the desired patches manually this month. This ensures that you don’t install any updates before you have a chance to approve them.
You may need to install Windows Genuine Advantage to run Microsoft Update, but this is a small price to pay to ensure that you install patches only when you want them.
Opt out of enhanced authentication — for now
While applying this month’s Windows updates, you’ll see an option for Extended Protection for Authentication, a new Microsoft service described in security advisory 973811 and KB article 968389. You have to opt in to receive this update, which enhances the security of credentials when handling network authentication via Integrated Windows Authentication.
This update requires that you enable Registry keys to realize the increased protection. However, I haven’t yet heard of any vendors using this service. I may recommend in the future that you install this update. But there’s currently insufficient information about it, and no evidence that vendors are utilizing it, to justify installing it at this time.
What’s most interesting about this update is that Microsoft is adding some of Windows 7’s new protection to its older operating systems via optional updates. It’s nice to see that Microsoft is providing this added security to Windows Vista and XP rather than making it available only in the new OS. But for now, I suggest that you pass on applying this update.
MS09-038 (971557)
Windows Media files in the crosshairs again
Malicious media files have long been used in attacks that attempt to gain access to our systems. The update presented in MS09-038 patches Windows Media’s .avi file format.
At present, there are no known attacks targeting this hole. However, media exploits may arise on various Web sites at any time, so I recommend that you install this update on your workstations without delay.
It’s more important to install the patch on workstations and Terminal Servers that host multiple workstations than to apply it to other types of servers.
MS09-043 (957638)
Long-awaited patch for Office Web Components
In July, Microsoft released an advisory that warned about Office Web Components being used in attacks. The company’s security advisory 973472 originally provided a Fix-it link that flagged the vulnerable ActiveX control and applied a killbit to deactivate it.
If you previously applied that fix, you don’t need to remove the killbit but you do need to install the more-recent patch described in MS09-043. The exploit has been seen in the wild, so install this update as soon as possible.
Office XP users may be presented with an end-user license agreement when they launch the program after installing this patch.
If you have FrontPage 2002 or 2003 and upgraded to Office 2007, you may be offered this update — even if your system doesn’t show FrontPage among the programs installed.
For those running Visual Studio .NET 2003 Service Pack 1, there are some unique known issues. I urge you to review KB article 969172 to determine whether any of the side effects will impact your system.
If you use Office Accounting 2006 and Internet Security and Acceleration (ISA) Server 2004 or 2006, you’ll be offered patches for these systems as well.
MS09-044 (970927, 958470, 958471, 956744, 958469)
Remote Desktop can be attacked from Web sites
The update presented in MS09-044 is near and dear to my heart. I use the ActiveX control being patched nearly every day on my own network.
The update is for Windows’ Remote Desktop, which is a technology many people use to access workstations remotely across the Internet.
I use Remote Web Workplace, which utilizes an ActiveX control and a Web-based process to remotely access my workstation. If you have this control installed on your PC, the system could be attacked via an infected Web site. Make sure you update both the workstation and the server it connects to.
To confirm that your system needs this update, search for the file mstscax.dll on your computer. Right-click the file, choose Properties, select the Version tab, and review the first two parts of the file version. Version 5.1.200.2180 means you have Remote Desktop (RDP) version 5.1 on an XP workstation. (See Figure 2.)

Figure 2. Using the file’s Properties dialog, check the version of the Remote Desktop DLL installed on your system.
Review the patch numbers listed in MS09-044 to find the updates you need for the client you have installed.
MS09-041 (971657)
Workstation Service exploit threatens networks
The Windows Workstation Service glitch described in MS09-041 can’t be used to launch an attack against your system from the outside. But you should apply this update just the same, especially if your workstations are connected in a network. The security hole could allow someone to use a Remote Procedure Call (RPC) message to take over your system.
Such an attack requires a valid sign-in. Microsoft rates the update as “Important” for XP and Windows Server 2003 and “Moderate” for Vista and Windows Server 2008.
MS09-039 (969883), MS09-036 (970957), MS09-039 (971032), MS09-039 (960859)
Important WINS security updates for servers
The Windows Internet Name Service (WINS) updates in MS09-039 shouldn’t be overlooked by server administrators. The remote code execution vulnerabilities have the potential to wreak havoc and are rightfully labeled as “Critical.”
The problem affects domain controllers, Exchange Servers, and Small Business Server 2003. While you should be blocking remote code-execution attacks at the firewall, something wicked could make it through the firewall and into your network, so this update should be a priority for servers.
If you run Web servers based on Internet Information Services 7.0 under Vista Service Pack 1 or Windows Server 2008, MS09-036 ensures that you won’t be affected by a denial-of-service attack due to a security hole in .NET 2.0 and 3.5.
Likewise, MS09-040 patches a service used by my office’s internal messaging software. The Windows Message Queuing Service is not installed by default on most servers. But if Microsoft Update detects it on your systems, apply this patch to prevent someone from sending code that attacks your server.
The venerable Telnet server-admin utility is patched via MS09-042. To be attacked via this vulnerability, you would need to connect the Telnet client to a malicious server.
Apply XP patches for Windows 7’s XP Mode
TechNet and Microsoft Developer Network subscribers who have access to the newly released Windows 7 aren’t affected by most of the patches released this week — if they have installed only Windows 7, that is. If you run the Windows 7 RTM or release candidate in XP Mode, however, your installation includes a full copy of Windows XP — so you need to patch that virtual machine just as you would the real XP.
The Patch Watch column reveals problems with patches for Windows and major Windows applications. Susan Bradley recently received an MVP (Most Valuable Professional) award from Microsoft for her knowledge in the areas of Small Business Server and network security. She’s also a partner in a California CPA firm.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
CD/DVD drive is no longer recognized
by
WSCape Sand
6 hours, 52 minutes ago -
Windows 11 24H2 Default Apps stuck on Edge and Adobe Photoshop
by
MikeBravo
9 hours, 42 minutes ago -
North Face and Cartier customer data stolen in cyber attacks
by
Alex5723
7 hours, 47 minutes ago -
What is wrong with simple approach?
by
WSSpoke36
19 minutes ago -
Microsoft-Backed Builder.ai Set for Bankruptcy After Cash Seized
by
Alex5723
19 hours, 12 minutes ago -
Location, location, location
by
Susan Bradley
6 hours, 14 minutes ago -
Cannot get a task to run a restore point
by
CWBillow
20 hours, 38 minutes ago -
Frustrating search behavior with Outlook
by
MrJimPhelps
11 hours, 21 minutes ago -
June 2025 Office non-Security Updates
by
PKCano
1 day, 7 hours ago -
Secure Boot Update Fails after KB5058405 Installed
by
SteveIT
3 hours, 47 minutes ago -
Firefox Red Panda Fun Stuff
by
Lars220
1 day, 7 hours ago -
How start headers and page numbers on page 3?
by
Davidhs
1 day, 17 hours ago -
Attack on LexisNexis Risk Solutions exposes data on 300k +
by
Nibbled To Death By Ducks
20 hours, 25 minutes ago -
Windows 11 Insider Preview build 26200.5622 released to DEV
by
joep517
2 days, 2 hours ago -
Windows 11 Insider Preview build 26120.4230 (24H2) released to BETA
by
joep517
2 days, 2 hours ago -
MS Excel 2019 Now Prompts to Back Up With OneDrive
by
lmacri
1 day, 16 hours ago -
Firefox 139
by
Charlie
1 day, 8 hours ago -
Who knows what?
by
Will Fastie
11 hours, 5 minutes ago -
My top ten underappreciated features in Office
by
Peter Deegan
2 days, 3 hours ago -
WAU Manager — It’s your computer, you are in charge!
by
Deanna McElveen
6 hours, 1 minute ago -
Misbehaving devices
by
Susan Bradley
22 hours, 52 minutes ago -
.NET 8.0 Desktop Runtime (v8.0.16) – Windows x86 Installer
by
WSmeyerbos
3 days, 9 hours ago -
Neowin poll : What do you plan to do on Windows 10 EOS
by
Alex5723
7 hours, 57 minutes ago -
May 31, 2025—KB5062170 (OS Builds 22621.5415 and 22631.5415 Out-of-band
by
Alex5723
3 days, 7 hours ago -
Discover the Best AI Tools for Everything
by
Alex5723
2 days, 6 hours ago -
Edge Seems To Be Gaining Weight
by
bbearren
2 days, 21 hours ago -
Rufus is available from the MSFT Store
by
PL1
3 days, 5 hours ago -
Microsoft : Ending USB-C® Port Confusion
by
Alex5723
4 days, 8 hours ago -
KB5061768 update for Intel vPro processor
by
drmark
2 days, 8 hours ago -
Outlook 365 classic has exhausted all shared resources
by
drmark
2 days, 7 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

