
|
Patch reliability is unclear, but widespread attacks make patching prudent. Go ahead and patch, but watch out for potential problems. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Test-driving ‘free scan’ tune-up suites
In this issue
- TOP STORY: Test-driving 'free scan' tune-up suites
- WOODY'S WINDOWS: Outlook.com: At last, a worthy MS mail program
- LANGALIST PLUS: Reducing shutdown delays in XP
- LETTERS: Windows Secrets readers share their findings
- WACKY WEB WEEK: World Order shows us "Machine Civilization"
- BEST PRACTICES: Clever malware masquerades as system scanner
Test-driving 'free scan' tune-up suites
Even on well-maintained systems, free system scanners might find hundreds of “problems,” as I discovered from a test of three products from well-known companies.
These suites typically offer to fix system problems — for a fee — but are these problems real or just scare tactics to drum up sales?
Long-time LangaList Plus readers know I’m a firm believer in PC maintenance. I regularly use various tune-up/cleanup tools on my PCs, and I know the good ones really do help keep systems clean, fast, and stable.
But some tune-up/cleanup tools seem to raise more questions than they answer. Consider this note from Windows Secrets paid subscriber Norman C. Freitas:
- “I recently installed Corel’s WinZip System Utilities. Its free PC scan reported:
“‘2,447 privacy traces detected, 529 registry issues found, 32 junk items detected, 6 outdated drivers found, and Registry Optimization recommended.’
“I am hesitant to pay to activate the software to ‘fix’ the reported problems without additional information. Help!”
I don’t blame Norman — I’d want more information, too.
To find out what free scanners would tell me about my PC, I ran my personal, daily-use system through a series of informal test drives. What kinds of problems (if any) would Corel’s WinZip System Utilities and some other tune-up suites report on a machine I knew was already well-maintained?
Creating a known-good starting point
No PC is perfectly clean after even minimal use, but I do use a thorough and regular maintenance regime. For example, to prevent viruses, malware, and other security problems, I continuously run Windows 7’s built-in firewall and Microsoft Security Essentials (site). As a backstop, I also regularly use the U.S. $25 version of Malwarebytes Anti-Malware (site) to catch any malware that might have slipped past MSE.
From time to time, I also use other standalone security scanners, such as ESET’s Online Scanner (site), Microsoft’s Safety Scanner (site), and Trend Micro’s House Call (site), to verify that my system is secure and uninfected.
I use Windows Update and Secunia PSI (site) to keep my most important software up to date and free of known security issues. (For more info on software updating apps, see the July 26 Top Story, “Software that updates your other software.”)
To keep my system lean and free of bogus Registry entries, junk files, useless cookies, and such, I run either Piriform’s CCleaner (free and paid; site) or Macecraft’s free PowerTools’ Lite (site) every day. I also run Macecraft’s jv16 PowerTools ($30; site) when I want a deeper, more controlled cleaning (such as when some software won’t install or uninstall properly). For general Registry cleaning, I use these tools in their safe, default modes because too-aggressive Registry cleaning can cause instabilities and other problems. All three tools are generally considered safe and effective by expert PC users.
I have Windows set to defrag my spinning-platter hard drives every night. My main PC has a solid-state drive (SSD), which should not be defragged. (Windows 7 automatically omits SSDs from its built-in defragging schedule. See the July 4 Top Story for my experiences with an SSD.)
My system also backs itself up automatically every morning before work. (See the May 12, 2011, Top Story, “Build a complete Windows 7 safety net.”)
There’s more, but the above steps and apps typically provide everything I need to reliably keep my PC clean, well optimized, stable, and secure. My machine had no known operational problems when I ran the tests.
Running Corel’s WinZip System Utilities Suite
I started with Corel’s WinZip System Utilities Suite because that was the subject of Norman Freitas’ letter.
I rebooted my PC — so that no other software would interfere with the test drive — and immediately ran CCleaner and Macecraft’s Powertools Lite, one after the other, to remove junk files and needless Registry clutter. With my system thus cleaned, I downloaded and ran the WinZip System Utilities Suite (site). The initial scan is free, but using the suite’s repair tools requires a $40 activation fee.
Figure 1 shows the report the WinZip System Utilities Suite delivered when the initial free scan completed.

Figure 1. Smart PC Care, part of the WinZip System Utilities Suite, reported a surprisingly high 398 problems on my PC.
Almost 400 problems? That definitely called for a closer look. I clicked the details links for each category, starting with the 25 issues in the “junk files and folders” section, which produced the list shown in Figure 2.

Figure 2. Most of the junk files WinZip found were normal — and harmless — items temporarily cached by my browser.
This portion of the WinZip report was accurate. These are the kinds of temporary files that normally accrue during system operation. (In fact, several of these files appeared to come from the Corel site where I downloaded the WinZip software.) There’s nothing extraordinary about these files — any cleanup tool can remove them.
I moved on to the 129 issues in the ominous-sounding “Internet and privacy traces” category. Figures 3, 4, and 5 show the detailed report results.
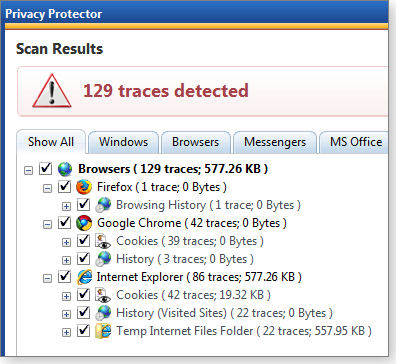
Figure 3. Although the 129 Internet and privacy traces sounded dangerous, most were ordinary browser cookies.

Figure 4. I examined several of the listed cookies to see where they'd come from and what privacy dangers they might pose.
Some cookies have obtuse names, making their sources not immediately obvious. I randomly picked cookie 644u3a3w and used Windows Explorer and Notepad to view its contents. Ironically, that particular cookie turned out to be one that WinZip had placed on my system when I visited the Corel site.
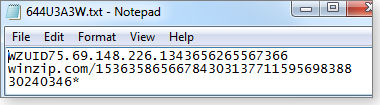
Figure 5. The contents of cookie 644u3a3w showed that it had come from WinZip.
Here, too, the WinZip Suite wasn’t technically wrong. However, the listed “privacy traces” were mostly plain, old cookies — completely normal and harmless. Heck, Corel’s own site uses them! Calling ordinary cookies “privacy traces” could inflate their perceived threat in the minds of unwary users, inaccurately suggesting serious security problems that do not exist.
I moved on to check out the 13 out-of-date or missing drivers WinZip reported (as shown in Figure 6).
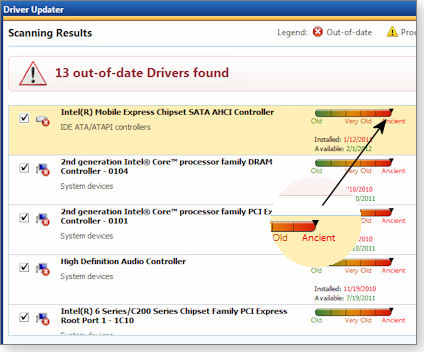
Figure 6. WinZip listed 13 drivers as 'ancient' and in need of updating.
To see whether my drivers really were out-of-date, I ran my PC manufacturer’s official driver update tool. It reported that all my drivers were fully current.
My PC has an Intel system board and CPU, so I also ran Intel’s official Driver Update Utility (site). It, too, found that none of my drivers needed updating.
Needless driver updating can destabilize a PC or even cause working hardware to fail, so this portion of the WinZip report I consider to be utterly wrong — and potentially dangerous to the health of the PC.
(For more information on driver-update false alarms, see the July 26 Top Story, “Software that updates your other software.”)
Next, I looked at the 231 Registry-related issues WinZip said it found. See Figure 7.

Figure 7. I was surprised that the Registry-cleaning tool found 231 issues on a freshly cleaned system.
This turned out to be a mixed bag when I manually examined many of the listed Registry issues. Some of the items were real but trivial. For example, the four Help file issues turned out to be associated with Adobe Acrobat. I had uninstalled Acrobat some time ago, and references to the Acrobat Help files must have been left behind in the Registry. This is indeed a kind of Registry error — but one that has no operational significance because the software involved is no longer on the system and the wasted space used by the entries is minuscule.
Other reported problems were simply wrong. For example, WinZip reported that several programs “do not have an uninstall program.” As a test, I used Control Panel’s Uninstall a program applet to try to uninstall two programs that WinZip said didn’t have an uninstall program — they both uninstalled normally. I have no idea what WinZip was detecting here.
Other issues were too vague to call. For example, it’s hard to tell what was going on with most of the 138 “orphaned” ActiveX and COM objects. My normal Registry cleaning tools, in their safe default cleaning modes, detected no problems here.
Perhaps WinZip wants to clean the Registry very aggressively — a mode available in other cleaning tools, but one I have learned not to use because of the likelihood of causing trouble.
Would removing all 138 references save a lot of space? No. I exported some of the suspect keys and found they averaged around 1.5KB of data each. Deleting them all would recover only about 207KB — that’s KB, not MB or GB — of space. That’s a truly trivial amount. These supposed ActiveX and COM “problems,” like others mentioned earlier, appear to have absolutely no effect on the operation of my system.
After working through all the test reports, I see one positive: WinZip System Utilities Suite can and does find some legitimate issues, such as junk files. However, you don’t need a $40 tool to remove junk files when there are numerous free tools available, including the free versions of CCleaner and PowerTools Lite mentioned earlier.
More troubling, WinZip System Utilities Suite (and the other scanners discussed below) seems to deliberately inflate the seriousness of some items — for example, calling its own website’s harmless cookies “privacy traces.”
Those, however, are relatively minor transgressions compared to reporting serious problems where none exist, such as flagging fully up-to-date drivers as “ancient.”
All of this seems designed to make your PC appear to be in dire need of paid-for repairs, when in fact there appear to be no real operational problems.
Similar results with Free Norton PC Checkup
I uninstalled WinZip, cleaned my system again, rebooted, and verified that everything was back to its pre-WinZip state. I then downloaded and ran Free Norton PC Checkup (site).
Its report was less detailed than WinZip System Utilities Suite’s, but it produced almost identical results, claiming to find 399 “problems” on my system. See Figure 8.

Figure 8. Free Norton PC Checkup claimed that my test system — known to be clean and stable — contained almost 400 issues.
There’s no point in going into detail because, on examination, almost all of the Norton-reported issues closely paralleled those reported by WinZip: harmless cookies (some created by the Norton site itself) reported as security “vulnerabilities,” fully up-to-date drivers being reported as obsolete, and so on.
But Norton had some major missteps all its own. It reported that my Windows firewall was disabled (it was not), and it reported that my PC’s startup had “speed issues.” This was curious because the Norton software did not actually time my system startup. If it had, it would have seen my system boot to the Windows desktop in about 12 seconds, which most would agree isn’t slow at all.
Norton PC Checkup is free, but it makes no repairs until you pay $70. The repairs are then effected by a live tech using Remote Assistance to take over your PC and make adjustments for you.
Although Norton PC Checkup can find some legitimate problems on your system (e.g., junk files), it blends these useful repairs with what I consider to be exaggerated and even outright erroneous items. And the $70 service probably does nothing you can’t do on your own with free software.
AVG’s PC Tuneup
After cleaning and rebooting once again, I ran AVG’s PC Tuneup [free scan; $35 to activate the software to allow repairs; site).
It set the record for the day, reporting almost 600 problems (see Figure 9) on a clean and stable PC.

Talk about a hard sell: AVG PC Tuneup reported 579 problems on my clean and stable system.
Just as with the previously-discussed tools, when I drilled down to examine these problems, some (such as junk files) were real, with most of the rest either exaggerated or simply wrong.
Here’s one example of an outright error: AVG flagged my C: drive as a problem because it was fragmented. But my C: drive is a solid-state drive which doesn’t need defragmentation and, in fact, can be damaged by defragging. Allowing AVG to perform this one “fix” could have started my SSD down the road to premature failure.
When I uninstalled AVG, it took one parting shot at convincing me to pay for repairs, as shown in Figure 10.
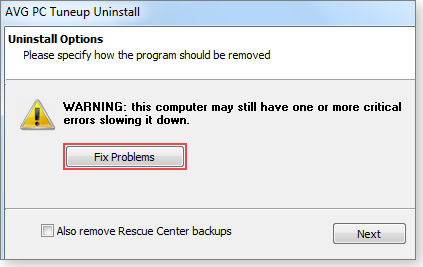
Figure 10. As if apparently exaggerating the number and severity of problems weren't enough, AVG displayed this dubious warning when I uninstalled the app.
Like the other products in this article, AVG’s PC Tuneup can find some legitimate problems on your system. But like its competitors discussed above, it has, I believe, inflammatory language, exaggerated problem counts, and at least one potentially dangerous recommended fix. And as with the others, any useful cleanup PC Tuneup might do, you can accomplish on your own with free software.
Scare tactics and hard sells should be a red flag
With only three products in this test-drive, nothing here should be taken as a blanket condemnation of this class of software.
But the software I test-drove for this article clearly seems aimed at inexperienced users who are more likely to purchase “repairs” when confronted with frightening reports of critical and numerous system problems. Unfortunately, these PC users often lack the skills to do basic troubleshooting themselves.
Windows Secrets readers tend to be more hands-on, involved, and knowledgeable about their systems. For this level of user, my original cleanup/tune-up recommendations remain unchanged:
To keep your PC clean, well-optimized, stable, and secure, all you need are the kinds of safe, proven, known-good, security and maintenance tools and techniques described at the top of this article — and in almost every issue of this newsletter!
Outlook.com: At last, a worthy MS mail program
Last week, Microsoft unveiled Outlook.com, a replacement for the venerable Hotmail that doesn’t look or act anything like the Hotmail you know.
Like Hotmail, Outlook.com is a free Web-based mail service — but with a hint of Metro-things to come.
Where Outlook.com fits in the Microsoft pantheon
R.I.P. Hotmail, 1996–2012.
It’s true. Microsoft is putting an end to Hotmail — not this week, not this month — maybe not even this year. But Outlook.com is the future for anyone who has a Hotmail account (which is, oh, about 99 percent of all the people I know).
Sabeer Bhatia and Jack Smith launched HoTMaiL on July 4, 1996. Microsoft saw it, liked it, and bought it in 1997 for $400 million. The exact number of current Hotmail subscribers is hard to come by, but it tops comScore’s (site) list of most-used, free, online e-mail services, with about 320 million active users in June — or about 36 percent of the worldwide market. Gmail has about a 31 percent share, but it’s growing fast at Hotmail’s expense.
You can see regional preferences. Although Gmail leads Hotmail in the U.S., Hotmail has twice as many users as Gmail in the U.K. But that’s changing, too. Yahoo has a 32 percent worldwide share, but it flatlined long ago. Overall e-mail use has nearly flattened as social-networking sites, instant messaging, texting, and VoIP/Skype pick up a growing portion of online, one-to-one communications.
Nevertheless, Microsoft now has a mind-numbing array of e-mail programs. You might use Outlook 2007 or 2010, included with current versions of Office; their successor, Outlook 2013, is now in preview. Microsoft still supports — in a manner of speaking — XP’s Outlook Express (which is nothing like Outlook) and OE’s look-alike, Vista Windows Mail. Then there’s the free, downloadable Windows Live Mail, which should soon have a name change as Microsoft kills off the “Windows Live” moniker. Windows 8 has a new Metro-style app called Mail.
Online, in addition to Hotmail, there’s Outlook Web App, which sorta has a Metro look and ties into MS Exchange and Office 365. (It also has offline capabilities via Internet Explorer.) And now there’s Outlook.com.
That’s 10 mail programs, each with a different user interface and each with its own quirks, problems, and bugs. You can be forgiven if you’re confused.
Once upon a time, more than a decade ago, Hotmail was cool. It was the only really big kid on the webmail block, and it had a certain appeal to the technorati of that time — at least those who weren’t still hopelessly tied to services such as the The WELL.
That changed around 2007, when Google rolled out Gmail. By 2008 or 2009, the trickle of Hotmail users moving to Gmail had turned into a flood. At the time, Gmail offered more mail storage, the ability to send larger attachments, and a more sophisticated interface.
Microsoft responded with a series of well-intentioned but horrendously implemented rebrandings — along with a few minor upgrades — that included MSN Hotmail, Windows Hotmail, Windows Live Hotmail, and Microsoft Hotmail. Hotmail’s latest facelift came just earlier this year. Few users were pleased with the update.
Now, Microsoft has not only killed off one of the most recognized brands in the world — it’s replaced the familiar Hotmail interface with something so utterly different (see Figure 1), it’ll shock most Hotmail subscribers.
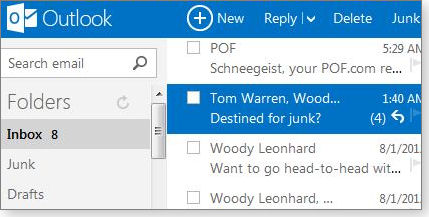
Figure 1. Outlook.com's interface has the boxiness of Metro and the spareness of Gmail.
Put Outlook.com on your digital test bench
Officially, Outlook.com is currently a preview — which is like beta, but also something of a trial balloon. (In other words, if user reaction is roundly negative, Microsoft could make significant changes.) After using it for a short while, I thought Outlook.com performed well. I recommend giving it a try — though with caution: you can revert an Outlook.com account back to Hotmail, but you can’t flip between the two.
Rather than convert an existing @hotmail.com or @live.com e-mail account to Outlook.com, I suggest starting with a completely new @outlook.com e-mail address. To do so, head over to Outlook.com and click (or tap) the sign-up link in the big blue box. You’ll be taken to the usual form, asking you to enter your name, desired e-mail address, and so on. Creativity counts, though the name Frumious Bandersnatch is already taken. And you don’t need to provide a phone number if you choose a security question. With that done, you jump straight into a flat, boxy, Outlook.com/Metro-style, webpage.
If you’re a regular Hotmail user, the first thing you’ll notice is that ads aren’t scattered all over the page. Most webmail services have ads, but Hotmail’s have long been among the most intrusive. (You can eliminate ads by upgrading to Hotmail Plus (more info) for U.S. $20 a year.) Outlook.com — at least for now — has less obtrusive ads placed in Metro-like tiles in a single, right-hand column.
When you first sign in, Outlook.com offers to import mail from another account. (I love the way it says, “Have another email account like Gmail?” It’s obvious whom Microsoft is gunning for.)
An introductory message provides links to instructions for bringing over contacts from other services and hooking into Facebook. (The transition to Outlook is far from complete. One message is signed the “Outlook Team,” and the other is from the “Hotmail Team.”) With a Facebook connection established, Outlook.com automatically imports FB-timeline posts onto the right side of your inbox. Facebook friends also get synched with your Outlook.com contacts list. (The sign-up window also states that you can connect to Twitter, but I couldn’t find a Twitter connection tool.)
Outlook.com’s People tile (accessed via a somewhat hidden drop-down button to the right of the Outlook title) steps you through importing contacts from Facebook, LinkedIn, Twitter, and (you guessed it) Google. There’s also a very kludged-up way to import contacts from Outlook (remember Outlook?) — as long as you don’t mind going into Outlook; exporting a comma-separated, flat file; and then importing the file into Outlook.com. It’s like the 1970s all over again.
Outlook.com’s main page has four columns. On the left (see Figure 1) there’s a list of folders (Inbox, Junk, Drafts, Sent, and Deleted) and a Quick views section. You add mail folders by clicking New folder. As a long-time Gmail user, I immediately felt the need to create an Archive folder, to which I can drag messages I want to keep until hell freezes over.
The second column shows you a list of all e-mails in the currently selected folder. The third column — enabled by choosing the gear-shaped Settings icon and selecting Reading pane and either Right or Bottom — displays the full message. As mentioned earlier, the fourth column contains ads, ads, and more ads — just like Gmail. Unlike Gmail, however, a small tool icon below the Outlook.com ads takes you to your (old-style) personal preferences page, where you’ll find links to disable targeted ads, based on your personal information, as noted in an MSN Money article.
As with any decent e-mail program, there are loads of tweaks that you can make — for example, by using the Sweep function to remove large numbers of messages at once — that come with some poking and prodding.
How close is Outlook.com to Gmail? Really close!
After looking at the features of both products, you have to conclude that there’s surprisingly (or maybe not) little difference between Outlook.com and Gmail — not just in overall appearance, but also feature-for-eature.
If you’re going to use either mail service on a phone or a tablet, it’s marginally easier to hit the Outlook.com buttons with large or clumsy fingers. And if integration with Facebook, Twitter, LinkedIn, and/or Flickr rings your chimes, then you’re better off with Microsoft’s service.
Outlook.com’s Sweep tool (introduced about two years ago in Hotmail) makes it easy to remove gray mail — messages that are not precisely spam but are of little or no interest to you. You can perform a similar function in Gmail by using its “Filter messages like these” option, but it’s not as easy to use as Sweep.
Microsoft makes much of Outlook.com’s ability to pull large files, such as pictures, from outbound messages and deliver them to recipients via SkyDrive — bypassing e-mail entirely. That’s a novel and useful application, but there are instances when keeping a file attached to a message is more desirable. For instance, SkyDrive might automatically delete attached photos after 90 days, or you might run out of room in your SkyDrive folder.
But even with Outlook.com’s new look and features, I’m sticking with Gmail for now. As close as the two mail services are, I still prefer Gmail’s interface. Outlook.com’s Metro-ness doesn’t provide any real enhancements to my mouse-and-keyboard proclivities. (Given the large volume of e-mail I receive, I can’t imagine tackling it with a touch device.)
Moreover, I rely heavily on Gmail’s ability to sort messages into “Important” and “Everything else” categories, which speeds up the onerous task of sifting through hundreds of daily messages. Outlook.com currently can’t do that, but if Microsoft is truly gunning for Gmail, it’ll probably add the capability soon.
With the addition of Outlook.com to its mail services, one wonders what Microsoft will do with its nine other e-mail apps and services. Some will naturally die off as XP and Vista fall out of support. (Outlook Express and Windows Mail haven’t been supported in years, much to the chagrin of paying customers.) Unfortunately, the other e-mail apps tackle overlapping markets — and often do so in incompatible and inscrutable ways.
Ultimately, this latest Microsoft e-mail offering makes sense only if MS adds Outlook.com’s capabilities to Metro Mail, or combines Outlook Web Access with Outlook.com, or if Outlook.com is integrated in some other way with the other mail products so that it’s not just another offering in Microsoft’s confusing e-mail product line. Anything that reduces the company’s mail apps/services from 10 to two or three at the most would be a welcome development. Gmail and Yahoo each have just one mail program; depending on how you count, Apple has two. Ten seems absurd.
Reducing shutdown delays in XP
Instructions for system tweaks in Vista and Windows 7 don’t always translate well to Windows XP — for example, reducing shutdown delays.
Fortunately, making an XP system power down more quickly isn’t hard, if you follow this illustrated step-by-step guide.
Two Registry changes shorten XP shutdowns
Dr. Harold Fenton hit a pothole when trying to reduce his PC’s long shutdown times. He was unable to transfer my Windows 7 instructions (July 11 Top Story) to his Windows XP system.
- “I have Windows XP and went to the sites mentioned in the article. But I couldn’t find, or rather became bewildered by, all the foreign (to me) terms. Is it possible we could see a step-by-step schedule for Windows XP like the one shown for Windows 7?”
You bet, Harold!
Here’s how to reduce shutdown delays in XP:
- Click the Start button, type regedit in the Run box, and press Enter.
- When Regedit opens, find and select Hkey_Current_UserControl PanelDesktop in the left-hand pane.
- In the right pane, double-click AutoEndTasks and change its default value from 0 (shown in Figure 1) to 1. Press OK.
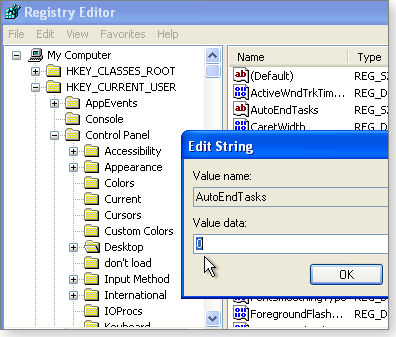
Figure 1. The AutoEndTasks setting is unique to XP. Change its value from 0 to 1 if you're experiencing long delays at shutdown.
- In the same right-hand pane, find and double-click WaitToKillAppTimeout, as shown in Figure 2. Change its default value from a sluggish 20,000 milliseconds (20 seconds) to a lower value, such as 10,000 milliseconds (10 seconds). You can adjust this timeout value up or down, as experience dictates.
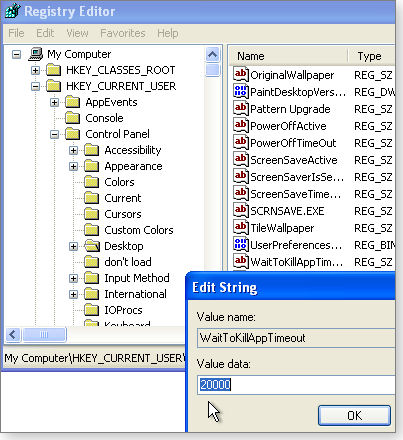
Figure 2. Reducing XP's default WaitToKillAppTimeout value can also help a PC power down faster.
- Close Regedit and reboot Windows.
Your XP shutdowns should now proceed faster!
Restoring missing Windows 7 desktop icons
Rick Bradley’s desktop icons have disappeared — all of them.
- “For some time now, I’ve had a ‘situation’ with my Windows 7 PC. I have no desktop icons. They are in the appropriate user file, and I can access them in the desktop toolbar. They used to be on the screen, but one day they just went away.
“When this first happened, I was busy doing something and set the problem aside. However, I’d really like to know why and how this happened.”
This may seem out of the blue, but did you recently install or use InfraRecorder (site)? It’s a very popular open-source DVD/CD burning tool that seems to be associated with more “missing icon” complaints than any other single cause.
InfraRecorder works well in almost all respects except one: it has a silly bug that turns off Windows 7’s Show Desktop Icons option!
Fortunately, it’s just a botched setting that’s easily set right:
- Right click on any empty spot on the Desktop.
- Select View.
- Select Show Desktop Icons.
Odds are, that’s all it’ll take to return your desktop to normal.
But if InfraRecorder isn’t the cause, there are plenty of additional diagnostic and troubleshooting tips available in the Microsoft Windows forum, “Windows 7 disappearing icons.”
Antivirus for ancient software in virtual PCs
Campbell Milton needs protection for some old, old software.
- “I run several older Windows versions, mainly to support programs and (ahem) some games, such as Meaning of Life, which runs only on NT 4 Workstation.
“The issue of installing NT4 on VMWare aside, what current AV runs on earlier Windows versions?
“I also service clients who run OSes going as far back as Windows 95, most of which are not on a VMWare PC. Some clients are gamers who are still running Windows 98 SE. So what’s the AV and anti-malware that I can use in these cases?”
Wow. That’s some ancient software you’re talking about!
As you might expect, there’s not a lot of current antivirus software that still supports 15-year-old operating systems. SRN Micro Systems claims its Solo Antivirus (site) is compatible with OSes as far back as Win95 and NT4. SRN charges U.S. $30 for a single-user license but also offers a 30-day trial. I have no practical way of testing this software first-hand, but CNET gives it a middling 3.5 out of 5 stars, based on a handful of user reviews.
Some users report successfully running ESET’s highly regarded NOD32 antivirus (site) on NT4 boxes; it’s $40 per year, with a 30-day free trial. Some third-party sites sell NOD32 at a modest discount, so shop around.
ClamWin (site) is an open-source AV product that claims support for Windows NT and Win98 (and so might work on the closely related Win95). ClamWin lacks a real-time scanner, so you have to set up frequent whole-disk scans. It’s currently still in beta, but it’s free.
I can’t help you with your VMWare-specific issues. The virtualizing tool I use and recommend is Oracle’s free VirtualBox (site), which lists Windows NT4 and Win98 among the 51 operating systems known to work inside a VirtualBox PC. (A VirtualBox webpage has the full list.)
I mention this because the risk of a virus infection spreading from a properly configured virtual machine (VM) to the host system is small. Usually (and by default) virtual machines run in sandboxed isolation (more info).
That said, it’s possible to weaken VM sandboxing by setting up shared files and folders, internal peer-to-peer networking, and the like. But if you don’t do that — if you don’t deliberately open links and connections between the virtual PC’s operating system and the host system — the risks to your host system should remain low.
GNU Image Manipulation Program (GIMP) feedback
I’m still receiving feedback on the July 18 item, “GIMP: A free alternative to Photoshop.” For example, Sid Marshall had trouble installing GIMP.
- “Upon checking the GIMP website (which seems almost as obfuscated as Fred suggests the GIMP program itself might seem to the novice), it appears GIMP might not work with Windows 7.
“Please confirm. Inasmuch as GIMP downloading and installation could be a nontrivial task, I do not wish to waste a lot of time trying to install the program on a new machine if GIMP and Windows 7 are incompatible.”
GIMP comes in many flavors and for many platforms. It’s even available as raw source code that you can modify and compile yourself. If you wade into GIMP.org’s full software library, you’ll see all these myriad options — and that can indeed be confusing.
But the latest, compiled, ready-to-run Windows version is available on its main download page (www.gimp.org/downloads/).
Near the center of the page, where it says, “GIMP for Windows,” click on the link “Download GIMP 2.8.0 — Installer for Windows XP SP3 or later.”
That version runs fine on my Win7 setups, both 64- and 32-bit. And, as the link states, it will also run on any normal Windows installation back to XP SP3.
Reader Bob Lurie offered a tip and his opinion about image editors:
- “FastStone.org’s [site] Resizer, Editor, and Capture image utilities are all extremely useful and easy to use.
“I also think you underestimate Adobe Photoshop Elements [$70; site]. It has everything a photographer could want. (OK, it lacks LAB, which many of us don’t use, anyway!) I recommend Elements to all of my ‘students’ (Harvard Institute for Learning in Retirement).
GIMP would turn them off immediately.”
Good tip on FastStone’s tools. Although they’re new to me, they look like a nice mix of freeware and shareware.
Thanks, Bob!
| Reader Bob Lurie will receive a gift certificate for a book, CD, or DVD of his choice for sending the tip we printed above. Send us your tips via the Windows Secrets contact page. |
Windows Secrets readers share their findings
Many Windows Secrets readers are seasoned systems builders, sophisticated tool users, metaphor makers, and generous souls.
We often receive thoughtful letters from these readers. Here’s some of the more interesting mail that’s recently arrived in our inbox.
Reader compares Linux and Windows servers
- In her Aug. 2 article, “The end for Home Server and Small Business Server,” Susan Bradley states, “The rise of simpler solutions, such as Linux-based, network-attached storage, also made Home Server less appealing.” Little does she know.
I recently purchased a Home Server license but have not yet installed it because nothing could be worse than the sloppy software workmanship in my Linux-based NASes that have cost me literally man-months of inexcusable aggravation.
For a starter, my Buffalo LinkStation and D-Link NASes do not accurately or adequately represent NTFS file attributes or file dates. This flaw is insidious because you normally don’t trip on it (and because I was unwilling to believe, when I did trip on it, that Linux implementers could be as sloppy and out of it as they have proven to be.) One would think they would understand the relevance of a server maintaining the file date and attribute integrity that the client system uses and expects.
The situation is insidious partly because of the way Windows and Linux, working in combination, handle file dates. When Windows copies a file to the NAS, [the Linux version of the file is given the same] creation date, last-access date, and last-write date of the Windows file. Under this condition, the files match up adequately.
[There are, however,] date-representation discrepancies that result in two problems. First, Linux represents file dates in a different form than Windows does. Second, when an application edits or saves a file directly to the NAS, the NAS uses its own internal clock to set the file’s dates. If the NAS’s clock is accurate, this is a non-issue. Unfortunately, one of my NAS clocks was found to be over nine years slow!
[I can] hear the Linux-lovers howl over this one. They’ll say to just program the NASes to interrogate a time server each day. My NASes are so programmed, but they don’t update their time even though they have access to an open Internet connection. Moreover, they correctly handle the GMT and DST offsets only sometimes. Windows interrogates time servers without difficulty and handles the GMT/DST offsets correctly.
The consequence of all this is that, on many occasions, newer files have been overwritten, causing considerable lost time and professional embarrassment to my significant other.
Details, details, a Linux loyalist will quickly rejoin. But then, “For want of a nail … .”
I find it easy to understand these Linux server problems, but only in retrospect. In my experience, Linux people like to abstract the real world into mathematical simplicity, whereas Windows people usually take the abstract and complexify it with the zillions of exceptions that apply in the real world. In short, the difference in approach is between wanting a Turing machine or wanting an accounting machine. The difficulty, skill, and practical value needed to give the world a good accounting machine vs. a good Turing machine is shown by good accountants being collectively worth so much more in the marketplace than good mathematicians are. Elegant brainpower can be applied to either world. —Charles E. Dial
Search Registry with Regedit? Oh, no!
Fred Langa’s Aug. 2 Langalist Plus piece, “Keeping secure connections in an XP/Win7 net,” elicited this comment from a reader.
- In the section titled “Leftover software setting causes trouble,” Fred Langa suggests that the reader use Regedit’s Find function to root out references to some old software.
Talk about tedious! Look for one string … locate one reference … fix it … look for the next reference … — over and over and over.
Please, the next time this comes up, do your readers a favor and suggest RegScanner (site), one of NirSoft’s incredibly useful tools. Tell it what to look for and it will scan your whole Registry (or whatever parts you want) and show you all the matches at once, so you can take whatever action you need. There are options to export the selected items as a backup [file]. [You can also] create a delete .reg file, which you can merge [with the main Registry file] to get rid of what you select.
In fact, I did exactly that on my system. I had installed PerfectDisk Free on my PC a year ago and later uninstalled it. Regscanner found more than a dozen references that were still on my system.
Anything that makes a tedious cleanup job both easier and safer — at no cost — is worth passing along! —Bill Aycock
How to get portable PhotoFiltre and why
In an Aug. 1 LangaList Plus item, reader Ray Marshall recommended PhotoFiltre as an alternative to the complex image editor, GIMP. Peter Townsend sent in a note suggesting that the portable version of PhotoFiltre was a better way to go and included a download link to PortableApps.
- When they’re available, I always use portable versions of software because it’s one less program to install when anything goes wrong. Also, it can be used from a USB stick, so I can turn anyone else’s computer into “mine.” Further, there are no issues with older DLLs overwriting newer ones or resetting common registry keys or any other side effects. —Peter Townsend
Widening your laptop’s printing options
A reader suggests a useful tool for mobile users:
- I recently noticed a Win7 item that I should be familiar with but somehow overlooked.
In Control Panel, go to Devices and Printers and then to the toolbar item Manage default printers.
I wonder how many WIN7 users know that they have the ability to do laptop location-aware printer settings? —Bob D
This option might not appear initially at the top of Devices and Printers. As a Windows Help & How-to site explains, it requires Windows 7 Professional, Ultimate, or Enterprise and a portable PC that uses a battery.
To make the option appear, you might have to temporarily set another printer as the default or reinstall a printer. Other printer options such as Print server properties and See what’s printing should also appear.
World Order shows us "Machine Civilization"
 |
World Order is a band and dance troupe formed by the retired Japanese mixed-martial artist, Genki Sudo. In this video, World Order comes to streets and monuments of Mexico, which induces a number of passersby to pause and photograph the event. Play the video |
Clever malware masquerades as system scanner
When an unexpected alert appears on screen, warning that your system needs repair and that paying a small fee will fix it, chances are high it’s malware.
Here’s a true story of how one such infection hit an experienced PC user (and the steps needed to remove it) — and how we all can stay vigilant in preventing such attacks.
Putting a new face on a common malware ploy
My dad lives just down the street from me, so we see each other often. Because I write about PC security, he keeps me up to date on the most recent computer scams and attacks he’s encountered. His age group, unfortunately, is a favorite target for scams of all sorts.
Dad is no computing neophyte. To date, he’s had four unexpected callers who informed him that his computer needed fixing, had a virus, or was slow and could be made to run better. Rather than ask how they could possibly know the status of his PC, he simply informed them that he “has a girl that helps me with my computer.”
(Many unsolicited “repair” calls suggest that the warnings come from Microsoft. The problem is so widespread, the company built a website specifically to warn PC users about tech-support scams.)
Dad has been sent any number of bogus e-mails urging him to download tools to make his computer run faster. He’s also received those chain-letter e-mails from friends with the usual: “If you don’t forward this e-mail to 10 of your closest friends, you’ll miss out on the prize!” He ignored them all.
Dad has also dodged the “THIS IS THE WORST VIRUS EVER” alerts sent by friends. In these cases, he either checked with me or consulted the postings on Snopes.com. (Although I’m a fan of Snopes, the massive numbers of pop-unders on the site are nearly as annoying as receiving bogus scam alerts.)
But despite that skilled, defensive computing, Dad got a virus that nearly tricked him. It was a fake system-scan alert, warning that his hard drive needed repair. He stopped just short of whipping out his credit card and paying a $39.95 “repair fee.” (Most likely, his credit-card information would have been sold to a thief.)
Thankfully, Dad called me and said that he had a problem with his hard drive. His PC is one of my hand-me-downs, but since it’s only a few years old, it’s unlikely to have a failing drive. He said with all certainty, “I got an alert on the system.” When I asked for more details on the alert, he stated that an application had started on its own, scanned all his drives, and indicated a hard-drive problem. (My PC security spidey sense immediately began to tingle.)
Windows Secrets has published several stories about rogue antivirus apps — malware that pretends to scan for viruses and remove them, typically for a fee. “Exactly what did the alert say?” I asked him. He replied, “It said that I had a SMART-HDD problem, and it indicated I could fix the problem by paying $39.95. That didn’t seem right to me, so I left it.”
Dad had almost been tripped up by one of the more malicious and deceptive scams — one that pretends to rescue your system but in truth tries to steal your money or financial information, or tries to take over your PC. Usually this type of scam puts up fake virus warnings. But as shown in sample images on the Trojan Killer site, cyber criminals are trying new tricks — in this case colorful — but fake — SMART HDD warnings. The more you click the warning, the more warnings you get that you cannot write to the hard drive.
More than just stealing credit-card info
That these rogue alerts try to steal personal information is bad enough, but they can also make unwanted changes to your PC. For example, they might change the attributes on a currently open user account so that your personal files are hidden from you. Try looking for files and folders under the c:users{the signed-in user} — and nothing’s there. The malware can also hide menu items from the Start menu — the Control Panel, Windows Update, and Administrative Tools, for instance, are gone.
Using products such as Combofix (site) and Malwarebytes (site) can remove an infection. But when malware starts to change permissions and settings, you need to take an added step: either a system restore to a time before the infection or a system recovery using a backup run before the event.
How do you know the actual time when the infection occurred? In this case, Malwarebytes gave me the location of the malware (shown in Figure 1), which had not hidden itself well — it created a folder underneath ProgramData, and the folder has a creation date of July 31. This tracked with when Dad started seeing alerts.

Figure 1. A Malwarebytes report shows where the viruses are located on the PC.
Sometimes it’s also wise to know the history of a computer. Because this workstation had been mine before I gave it to Dad, and I did not reinstall the operating system before I gave it to him, Malwarebytes found leftover network tools and flagged them as backdoors and Trojans. Although the items that Malwarebytes found were a concern, the application can, and does, at times flag legitimate software such as the password auditing tools I use to run test scans as backdoors. Malwarebytes will also flag various remote-control tools as Trojans. Knowing what applications you’ve installed on a system, and ones you know you haven’t, will help you know which alerts to be concerned about and which you can safely ignore.
A folder’s date and time isn’t always a good indicator of when an infection occurs. Even worse, the malware might have destroyed all system restore points. (Also, I might not have had a recent backup of Dad’s system). If that’s so, it might be necessary to consider starting over: reinstall Windows and all your applications from scratch. Yes, that’s time-consuming, but a vintage TechNet story from 2004 says it best: If you cannot trust the system, you have no choice but to start over.
So how did this critter get on Dad’s system? I’m fairly sure that unpatched Java was the trigger. I was remiss in not setting up Secunia’s Personal Software Inspector (site) on his machine, so older Java was still installed.
I also noted that he was still running the system as an administrative-level user, so I set up a limited-user account, as detailed in the Aug. 1 Best Practices story, “Banking on whether Windows is safe for banking.”
I just recently discovered a little-known and under-utilized tool in Microsoft’s system-protection arsenal — AppLocker (more info). Unfortunately it’s not included in the Home versions of Windows where it might do a lot of good. It’s in only Windows Professional, Ultimate, and Enterprise.
I always assumed that AppLocker could be set up only on a network using Windows’ Group Policy. But that’s not the case. Because Dad is using Windows 7 Ultimate, I can go into the local security policy and set up policies that let him update known applications yet restrict installations of unapproved software.
I’ll be testing this new capability soon and providing an evaluation to Windows Secrets readers. In the meantime, keep this in mind: if an unfamiliar alert unexpectedly pops up on your screen and requests a repair fee, it’s most likely a scam. (The key word here is “unexpected.” In this week’s Top Story, Fred Langa reviews legitimate system scanners you choose to run on your machine, and he talks about their sometimes over-zealous alerts.)
Get security help only from known sources
Dad stayed out of the rogue system-alert trap because he had help and advice (from me) he trusted more than a pop-up warning with a $39.95 web page. But what about you? If your usual remedy is to Google the alert to see what comes up, you could be in for a long search session. I’m increasingly concerned about running random Google or Bing searches for tech advice. Many of these advice sites use search engine–optimization tricks to lure you in, but then don’t offer much in the way of real help or real information. They’re mostly selling eyeballs to advertisers. You also run the risk of landing on a malicious site that will only add new infections.
Windows Secrets is, of course, one good source, but I also recommend sites such as Microsoft Answers, Bleeping Computer, and Micrsoft IT pro forums for Windows 7 and XP SP3. The Windows Secrets Lounge is a good place to post security questions.
While in the Lounge, check out other scams going around. Lounge regulars “Chowur” and “BruceR” warned about the latest scam, a fake AT&T bill alert that once clicked, puts the BlackHole exploit kit on your computer.
If your machine is truly disabled by malware, you’ll also need another way to get on the Net. It’s a good excuse to get that new UltraBook or tablet PC you’ve been thinking about.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Red x next to folder on OneDrive iPadOS
by
dmt_3904
37 minutes ago -
Are manuals extinct?
by
Susan Bradley
19 minutes ago -
Canonical ditching Sudo for Rust Sudo -rs starting with Ubuntu
by
Alex5723
9 hours, 45 minutes ago -
Network Issue
by
Casey H
1 hour, 48 minutes ago -
Fedora Linux is now an official WSL distro
by
Alex5723
21 hours, 44 minutes ago -
May 2025 Office non-Security updates
by
PKCano
22 hours, 11 minutes ago -
Windows 10 filehistory including onedrive folder
by
Steve Bondy
1 day ago -
pages print on restart (Win 11 23H2)
by
cyraxote
59 minutes ago -
Windows 11 Insider Preview build 26200.5581 released to DEV
by
joep517
1 day, 2 hours ago -
Windows 11 Insider Preview build 26120.3950 (24H2) released to BETA
by
joep517
1 day, 2 hours ago -
Proton to drop prices after ruling against “Apple tax”
by
Cybertooth
1 day, 9 hours ago -
24H2 Installer – don’t see Option for non destructive install
by
JP
2 hours, 4 minutes ago -
Asking Again here (New User and Fast change only backups)
by
thymej
1 day, 21 hours ago -
How much I spent on the Mac mini
by
Will Fastie
20 hours, 26 minutes ago -
How to get rid of Copilot in Microsoft 365
by
Lance Whitney
5 minutes ago -
Spring cleanup — 2025
by
Deanna McElveen
2 days, 2 hours ago -
Setting up Windows 11
by
Susan Bradley
21 hours, 57 minutes ago -
VLC Introduces Cutting-Edge AI Subtitling and Translation Capabilities
by
Alex5723
1 day, 22 hours ago -
Powershell version?
by
CWBillow
1 day, 23 hours ago -
SendTom Toys
by
CWBillow
10 hours, 5 minutes ago -
Add shortcut to taskbar?
by
CWBillow
2 days, 3 hours ago -
Sycophancy in GPT-4o: What happened
by
Alex5723
2 days, 19 hours ago -
How can I install Skype on Windows 7?
by
Help
2 days, 18 hours ago -
Logitech MK850 Keyboard issues
by
Rush2112
2 days, 1 hour ago -
We live in a simulation
by
Alex5723
3 days, 9 hours ago -
Netplwiz not working
by
RetiredGeek
2 days, 20 hours ago -
Windows 11 24H2 is broadly available
by
Alex5723
3 days, 22 hours ago -
Microsoft is killing Authenticator
by
Alex5723
23 hours, 57 minutes ago -
Downloads folder location
by
CWBillow
4 days, 4 hours ago -
Remove a User from Login screen
by
CWBillow
3 days ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

