
|
There are isolated problems with current patches, but they are well-known and documented on this site. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
The perils of Bitcoin; the promise of blockchain
In this issue
- TECH UPDATE: The perils of Bitcoin; the promise of blockchain
- WACKY WEB WEEK: Tech-support scripts from Down Under
- ON SECURITY: Ransomware alert: Don't be unlucky with Locky
The perils of Bitcoin; the promise of blockchain
Bitcoin has been in play since 2009, and there are still many nay-sayers heaping scorn on this much-hyped digital currency and distributed-ledger system.
The private-payment system’s underlying technology promised to be a game-changer. That hasn’t happened yet, but it probably will — eventually.
Currently, many people’s view of bitcoin is of an underground currency exchange used mostly by criminals. (It appears to be the preferred payment method for ransomware.) Its reputation took a real beating with one ignominious event: the February 2014 crash and burn of the Mt. Gox bitcoin exchange and the subsequent arrest of its founder, Mark Karpeles. An astounding U.S. $400 million of the virtual currency disappeared in what the exchange called “transaction malleability.” As the Verge’s Russell Brandom writes in an August 3, 2015, article, Karpeles’ grand theft is “a cautionary tale for anyone with dreams of unregulated digital finance.”
Bitcoin survived the scandal and attracted new adherents, despite the obvious risks of a financial system based solely on mutual trust — there’s no central authority controlling or backing the system.
The value of a bitcoin fell from more than $1,000 to less than $100 following the Mt. Gox shutdown. Eventually, it settled at its current value of around $400, according to the CoinDesk price index (site).
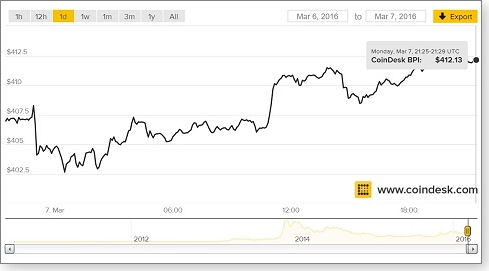
Figure 1. After a precipitous fall, bitcoin value has hovered at around $400. Source: CoinDesk
Volatility and a reputation for serving criminals are far from bitcoin’s only challenges on the road to respectability. In a March 4, 2016, International Business Times article, David Gilbert wrote that some businesses have stopped accepting bitcoins as payment because of slow transaction processing. The average time required to verify a bitcoin transaction is now 43 minutes, according to Gilbert — and some transactions are never verified.
One source of the problem is that transactions can be moved up the bitcoin queue by paying an extra fee. Anyone who doesn’t pay the added fee will see their transaction drop in the queue. To make matters worse, there’s no solution in the offing for the slow bitcoin transactions. The reason lies in bitcoin’s fundamental architecture.
Miners hard at work … though slowly
You don’t need a deep understanding of how bitcoin works to use the digital currency, but Windows Secrets readers know better than to approach any new technology on blind faith. The official bitcoin site explains the technology underlying the anonymous payment system.
It all starts with a blockchain — the shared, encrypted public ledger on which bitcoin transactions rely. All the characteristics of an asset are recorded in its blockchain: when it was created, by whom, each time it was transferred, and its value at the time of each transaction.
Each time an asset is transferred between the bitcoin wallets of the buyer and seller, the transaction is verified and recorded in its blockchain. The validation is done by “miners,” individuals or groups who collect a transaction fee for each transaction they confirm. When a consensus of miners agree that a transaction is valid, it is deemed authenticated.
To be confirmed, the transaction must follow specific cryptographic rules, and it must also fit into a single block, which can be a maximum of 1MB in size. The fastest rate at which transactions can be processed is seven per second. (Given that Visa’s payment system processes an average of 2,000 transactions per second, you have to wonder how bitcoin will ever compete with mainstream services.)
Two competing solutions have been proposed to address the block-size limit. The Bitcoin Core group, as reported in a CoinDesk article, wants to retain the size limit but change the way signatures are stored. On the other hand, the Bitcoin Classic group wants to increase the maximum block size to 2MB, as reported in another CoinDesk story. But that would make old blocks incompatible with new ones. Bitcoin’s scalability predicament was discussed at a recent Satoshi Roundtable conference, as Coinbase co-founder and CEO Brian Armstrong wrote in a March 4 post.
Armstrong states that the Core group believes a larger block size — and the subsequent bitcoin fork — is inevitable but still far into the future. However, Armstrong sees a bigger problem facing the current bitcoin system: It’ll soon be uneconomical for miners to work on transactions because the cost of mining will exceed the compensation they receive (a combination of a fee per transaction and a bounty for creating new blocks). That could lead to a shortage of miners that will slow transactions even further and could ultimately cause the system to collapse. (For more on the process behind bitcoin mining, see a Business Insider article.)
Armstrong’s proposed solution is to adopt the Bitcoin Classic changes in the short term, work more closely with the Chinese miners who comprise the bulk of the transaction verifiers, and open the bitcoin protocol to allow more developers to participate.
Losing bitcoins but keeping the blockchain tech
There are few things the financial industry hates more than uncertainty. And right now bitcoin’s future is as uncertain as it gets. But the blockchain technology has piqued the interest of the financial community. Visa and Goldman Sachs are among the top services companies planning to offer customers products based on blockchain ledgers, as noted in a recent JDSupra Business Advisor article.
Any secure transaction requiring authentication of the parties and property involved is a candidate for a distributed ledger such as blockchain. Each transaction becomes a “block” that is “chained” in chronological order to other related blocks. The cryptography applied to the blocks makes it impossible (using current technology) to alter a block.
In theory, blockchain technology (see Figure 2) promises to reduce the cost of processing transactions without sacrificing security or performance. The technology’s potential to engage industries of all types has attracted much attention. In a Sept. 9, 2015, Forbes article, Laura Shin reports that blockchaining could affect industries representing a fifth of the U.S. GDP — or $3.6 trillion.

Figure 2. A diagram of distributed-ledger types; bitcoin relies on an untrusted consensus. Source: Dave Birch, Consult Hyperion
The experts don’t expect super-cheap, super-fast, super-secure transactions to arrive anytime soon. In fact, they might not start trickling into your digital wallet until the mid-2020s. It’s believed that blockchain and other distributed ledgers will take hold first in poorer parts of the world, where fees represent a higher percentage of total transaction values.
A primary reason for the slow rollout of blockchain technology is the new infrastructure needed to run the blockchain applications. The apps might not be developed until the underlying infrastructure is in place. Two early blockchain-based services are the Ethereum project (site), intended as a platform for running “smart contracts,” and the Ripple distributed system (site) for international financial transactions.
Ethereum claims to offer much faster transaction processing than bitcoin: an average of 17 seconds, according to a March 3 ZDNet article. Critics point out that no current blockchain system can scale to handle the transaction workload of, say, the SWIFT international payment clearinghouse (more info).
Ripple takes it on the chin for being under the control of its creator, Ripple Labs, although it claims to have a “path to decentralization,” as noted in a July 23, 2015, American Banker article.
Growing pains or an evolutionary dead end?
Given its volatility and reputation, the future of bitcoin is cloudy at best. Despite years of hype, it’s still far from mainstream. It’s still a “user beware” proposition. On the other hand, the long-term potential of distributed-ledger technology, or some hybrid evolutionary branch, is undeniable — though its implementation will be hidden deep inside the background systems that support our future transactions.
|
Feedback welcome: Have a question or comment about this story? Post your thoughts, praise, or constructive criticisms in the WS Columns forum. To rate this or other stories, click over to our polls page. |
Tech-support scripts from Down Under
 |
Maybe in your recent lifetime you’ve accumulated a few hours on the phone having conversations with tech-support people. The Sexy Detectives, an Australian sketch comedy group, have clearly felt your pain, as you can tell from the video they made on the topic. In real life, unfortunately, tech-support outcomes are hardly ever amusing. Click below or go to the original YouTube video. |
Ransomware alert: Don't be unlucky with Locky
Ransomware is a rapidly growing plague on computer users, and the latest variant of Locky adds malicious Word macros to its weaponry.
If you must open Word documents created by others, here are some ways to ensure you don’t become a ransomware victim.
When you’re unlucky enough to get Locky
Locky ransomware show up in many formats, but in most cases it’s disguised as an invoice, shipping document, or similar-seeming legitimate attachment. Typically, those attachments are Word or Excel documents, but the malware might also be hiding inside a ZIP or RAR file.
No matter how Locky arrives, the end effect is the same — and frighteningly obvious. You’ll discover that all your documents are encrypted: not just those on the infected computer, but also files on mapped external drives and network locations. Even cloud-based documents are at risk. It can also disable Windows’ volume shadow copies.
It gets worse: Locky will look for bitcoin wallets and try to encrypt them as well.
Locky can even store information in the Windows Registry. It might show up in the following locations:
- HKCU\Software\Locky\id – Provides the unique ID assigned to the victim.
- HKCU\Software\Locky\pubkey – The RSA public key.
- HKCU\Software\Locky\paytext – Stores the text included in the ransom notes.
- HKCU\Software\Locky\completed – Indicates whether the ransomware has finished encrypting the computer.
- HKCU\Control Panel\Desktop\Wallpaper – “%UserProfile%\Desktop\_Locky_recover_instructions.bmp” – Saves the ransomware instructions.
Locky is also known to use these files:
- %UserpProfile%\Desktop\_Locky_recover_instructions.bmp
- %UserpProfile%\Desktop\_Locky_recover_instructions.txt
- %Temp%\[random].exe
Here are some reminders of ways to protect yourself from this latest variant.
The first line of defense remains unchanged
Regular Windows Secrets readers should already know the first rule of blocking ransomware and similar forms of malware: Don’t open email attachments that did not come from truly trusted sources. I’d even avoid attachments forwarded by those you know well — you can’t know the original source of the document.
Note that the ransomware payload typically isn’t triggered by simply viewing the email message; you have to open the malicious attachment to become infected.
The next best defense is using an email service that filters your email. If you never see the attachment, you won’t be tempted to open it. Many major Interest service providers will filter and clean email — it’s in their interests to protect their subscriber traffic.
If your ISP doesn’t provide effective mail filtering and cleaning, you should sign up for one of the free providers that do. You can, for example, forward your mail through Gmail or Outlook.com. I also recommend creating a separate account on one of the free, online mail services; then use that address for the sites that might lead to more spam in your inbox.
Many of the malicious emails and attachments look as if they came from legitimate businesses. It can be hard to tell a bogus FedEx notification from a real one. If you’re suspicious of an email, open it on a platform that’s less likely to be hit by ransomware. For example, I often use my iPhone to open up suspect mail. If it proves safe, I will then open it on one of my Windows machines. But even that’s not foolproof. As noted in a recent Reuters story, some OS X machines saw their first successful ransomware attack. The “KeRanger” exploit was piggy-backing on torrent sites. (That’s what you get for illegally downloading media — I jest: there are legitimate reasons for using BitTorrent.) Experts reportedly expect to see new forms of attachments on Macs.
Preventing infection by blocking macros
Locky’s use of Office-based macros is somewhat unique. If you’re unlucky enough to launch the malware, and if you’ve not taken precautions to block certain macros, the encryption process will begin. Microsoft’s Malware Center has posted tips for protecting yourself from bogus macros.
It starts with checking whether you have any Word docs or Excel worksheets that contain macros. If you don’t have or use macros, take the following steps to better protect yourself from malicious documents that might slip onto your machine.
- Open a Microsoft Word document.
- Click the File tab and then Options.
- In the Trust Center, click Trust Center Settings.
- In the Macro Settings section, check that the default Disable all macros with notification is enabled.
- Click OK.
If you do use macros, the better option is: Disable all macros except digitally signed macros. This will ensure that unsigned macros don’t launch when you open a document.
Looking for the yellow banner when opening files
If you have a newer Office platform — 2010 through 2016, it knows where opened documents have come from. Opening Word or Excel email attachments will trigger the yellow warning shown in Figure 1. (The wording will vary slightly with different Office versions.) Earlier platforms might also display the warning — if you’ve installed specific updates. But as I’ve pointed out in a Patch Watch column, the updated Office versions weren’t perfectly successful when dealing with file opening on older platforms.

Figure 1. Office's warning that a document that arrived in email could be malicious
If you’re using .docx and .xlsx formats, newer Office versions tend to be more effective at spotting and blocking macros. But the key is still to always watch for the yellow banner at the top of opened files. If the document came via the Web, you can enable macros — but, again, only if you truly trust the source.
What do you have access to?
An often overlooked step for limiting damage from ransomware is checking what you have access to from your PC. If you can browse to a location on an internal drive, on an external USB drive, in the cloud, and so forth, the ransomware payload has access to that location, too.
With that in mind, review how your backup software is set up. It’s one of the reasons I don’t completely trust Windows 10’s File History system; it saves a copy to an external USB hard drive that you — and ransomware — have full access to. File History makes no attempt to hide the location of archived files; hiding them would help protect them from ransomware encryption.
I wouldn’t turn File History off, but I would add the old-school method of rotating backup media (to multiple, external USB drives). Combine that strategy with cloud backup that includes versioning. In short, never rely on one backup system.
Ransomware is getting only cleverer at tricking computer users into downloading and launching malicious code. As it adapts, so too must we. Open only those attachments you expected to receive — and don’t worry if your friends think you are a tad paranoid when you call them to check that they really sent an email with any form of attached file.
A little paranoia helps keep us all safe.
| Feedback welcome: Have a question or comment about this story? Post your thoughts, praise, or constructive criticisms in the WS Columns forum. To rate this or other stories, click over to our polls page. |
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
KB5058379 / KB 5061768 Failures
by
crown
47 minutes ago -
Windows 10 23H2 Good to Update to ?
by
jkitc
51 minutes ago -
At last – installation of 24H2
by
Botswana12
28 minutes ago -
MS-DEFCON 4: As good as it gets
by
Susan Bradley
8 minutes ago -
RyTuneX optimize Windows 10/11 tool
by
Alex5723
12 hours, 40 minutes ago -
Can I just update from Win11 22H2 to 23H2?
by
Dave Easley
6 hours ago -
Limited account permission error related to Windows Update
by
gtd12345
1 day, 2 hours ago -
Another test post
by
gtd12345
1 day, 2 hours ago -
Connect to someone else computer
by
wadeer
20 hours, 39 minutes ago -
Limit on User names?
by
CWBillow
23 hours, 58 minutes ago -
Choose the right apps for traveling
by
Peter Deegan
13 hours, 40 minutes ago -
BitLocker rears its head
by
Susan Bradley
22 hours, 15 minutes ago -
Who are you? (2025 edition)
by
Will Fastie
1 hour, 24 minutes ago -
AskWoody at the computer museum, round two
by
Will Fastie
16 hours, 2 minutes ago -
A smarter, simpler Firefox address bar
by
Alex5723
1 day, 12 hours ago -
Woody
by
Scott
1 day, 21 hours ago -
24H2 has suppressed my favoured spider
by
Davidhs
21 hours, 20 minutes ago -
GeForce RTX 5060 in certain motherboards could experience blank screens
by
Alex5723
2 days, 12 hours ago -
MS Office 365 Home on MAC
by
MickIver
2 days, 6 hours ago -
Google’s Veo3 video generator. Before you ask: yes, everything is AI here
by
Alex5723
3 days, 2 hours ago -
Flash Drive Eject Error for Still In Use
by
J9438
1 hour, 4 minutes ago -
Windows 11 Insider Preview build 27863 released to Canary
by
joep517
3 days, 21 hours ago -
Windows 11 Insider Preview build 26120.4161 (24H2) released to BETA
by
joep517
3 days, 21 hours ago -
AI model turns to blackmail when engineers try to take it offline
by
Cybertooth
3 days ago -
Migrate off MS365 to Apple Products
by
dmt_3904
3 days, 1 hour ago -
Login screen icon
by
CWBillow
2 days, 15 hours ago -
AI coming to everything
by
Susan Bradley
6 hours, 30 minutes ago -
Mozilla : Pocket shuts down July 8, 2025, Fakespot shuts down on July 1, 2025
by
Alex5723
4 days, 12 hours ago -
No Screen TurnOff???
by
CWBillow
4 days, 13 hours ago -
Identify a dynamic range to then be used in another formula
by
BigDaddy07
4 days, 13 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

