
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Tools for foiling malicious links and files
In this issue
- LOUNGE LIFE: Hardware trouble: Process of elimination
- WACKY WEB WEEK: Raccoons and other animals: Mutually wary
- TOP STORY: Tools for foiling malicious links and files
- LANGALIST PLUS: Protect your Win7/8 setup from the Win10 upgrade
- BEST UTILITIES: Apps for finding potentially unwanted files
Hardware trouble: Process of elimination
Lounge member Slorm’s PC is suddenly shutting down intermittently.
He wasn’t seeing definitive clues in his Events reports, but a message from his motherboard mentioned something about power surges.
So he turned to the Hardware forum to discuss his hunches. He and his fellow Loungers talked about uninterruptible power supplies, power-supply units, and testers thereof — and also about what the problem could be if not in the PSU. You could benefit now or in the future by following their conversation.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right into today’s discussions in the Lounge.
Raccoons and other animals: Mutually wary
 |
Whether raccoons are entirely wild intruders or have been invited in to eat grapes at the dining room table, their presence can — and usually does — provoke a certain anxiety in their hosts. As you see in this collection of videotaped encounters, they’re dangerously cute. In comparison, some humans are dangerously crazy: who lights birthday candles for a pet raccoon to blow out? Click below or go to the original YouTube video. |
| Post your thoughts about this story in the WS Columns forum. |
Tools for foiling malicious links and files
Every day, malicious websites and attachments try to trick you into downloading their dangerous payload.
Fortunately, there are websites and tools to help you determine what’s safe and what might be a trap designed to steal personal information and money.
Hackers are cleverer than ever, which means it’s only getting harder to spot a malicious site or file. How many of us have received a bogus email about a product we know we never ordered?
With a bit of knowledge, some scams are easy to spot. For example, when I get a call from a “Microsoft rep” who claims my PC reports that it’s laden with malware and needs to be fixed, I know it’s a scam. Microsoft never makes support calls out of the blue; you must place the first call to its help center.
But knowing whether an email or website link will take me down the rabbit hole is much more difficult. Here are some helpful tools and tactics for revealing often well-disguised threats.
Getting help from online security sites
Before I discuss sites, let me suggest that you don’t want to check suspicious links from the browser (or browsers) you use every day. Seriously consider setting up either a virtual-PC system or a dual-boot configuration for testing suspect links and files. Virtual machines are easy to establish by using Microsoft’s Hyper-V, Oracle’s VirtualBox, or VMware. Just remember: To be legal, the second machine needs to have its own, valid license.
Next, you’ll want to bookmark several websites that let you upload malicious files or enter the URL for a suspect site. Sometimes, these security sites will tell you that the malicious link is known by antivirus companies; but sometimes, they also highlight that antivirus software doesn’t always flag malicious items.
Let’s start with the well-known VirusTotal site. An email arrived in my inbox stating I had an unpaid parking fee. I confirmed it was bogus by uploading the attached ZIP file to VirusTotal. It goes without saying that an unexpected email with a ZIP file attachment should make you suspicious. Never, ever open a ZIP attachment unless someone has told you that a file will be delivered that way.
If your anti-malware app won’t let you download the file (so you can then upload it to VirusTotal), consider that an endorsement for your security product. In the case of my suspicious attachment, only 13 of 57 antivirus products flagged it as malicious (see Figure 1), according to a VirusTotal report.

Figure 1. The results of a VirusTotal test showed that 13 of 57 AV products flagged a suspect ZIP file as malicious.
There are numerous other security sites that can help spot something malicious; they include:
- fortiguard.com/antivirus/virus_scanner.html – This site scans malicious files and also reports on potential security issues.
- hybrid-analysis.com – You can upload files to this site, but it might not handle ZIP files.
- malwr.com/submission/ – It lets you upload files and examine what processes might occur. It also notes whether a file is listed on VirusTotal.
- metascan-online.com – This is another site for checking files that might have malicious content.
- phishtank.com – Check whether a website is a known phishing site.
- urlquery.net – (Note that the site is .net and not .com. Someone has parked the .com domain.) This site scans website links for malicious files or activity.

Figure 2. urlQuery checking a website controlled by the author
- virusscan.jotti.org – Upload files for analysis.
- vms.drweb.com/online/?lng=en – It scans files but does not appear to work with ZIP files.
- websense.com – Anonymously upload as many as five URLs a day for analysis. If you register for an account, you can upload more files per day. Only Web-based URLs are allowed for free; you must be a paying customer to upload files received via email.
- wepawet.iseclab.org – It lets you upload suspicious files or enter URLs for review. Note that it handles only Flash, JavaScript, and PDF files — it can’t check ZIP files.
(Note: All these sites support https://.)
There are more advanced tools used for investigating malicious Web servers and their locations — or for tracing mail-exchanger records (more info) for received email.
Again, many of these tools are available on the Web; here are a few. (Note: You might need to check your ISP’s terms of service and your country’s cyber laws to ensure that you have the legal right to use these tools against a site you do not control. For these examples, I tested a site that I own.)
- abuseipdb.com – It’s another site that checks a website’s malicious activity. (Note: Link does not appear to support https.)
- ipvoid.com – This site lets you enter an IP address and check whether it’s been involved in malicious activity. (Note: Link does not appear to support https.)
- mxtoolbox.com/Public/Tools/EmailHeaders.aspx – Upload email headers to this site to determine where a message came from.

Figure 3. MxToolbox decodes email headers for diagnostic information.
- quttera.com/website-malware-scanner – It checks websites for malicious activity.
- rexswain.com/httpview.html – It lets you see what a website is doing in your browser. (Note: Link does not appear to support https.)

Figure 4. Rex Swain's HTTP Viewer reveals browser activity.
- robtex.com – It gives information about DNS resolution and peering.
- sitecheck.sucuri.net/ – Use this site to check for both malicious activity and website errors.
- virustracker.net – It checks whether an IP address has had malicious activity.
The always-excellent Internet Storm Center has a tools page that can be helpful when investigating possible malware sources. The page also links to several other websites, including anubis.iseclab.org/, which can analyze malicious Android files, and http://threatstop.com/checkip, which checks whether a site has a reputation for malicious activity.
Keep your system malware-free; stay informed
Of course, after handling potentially malicious files and sites, you’ll want to thoroughly check your system with a robust malware scanner — you might have accidentally infected your virtual machine or second system.
For a deep scan of Windows, it’s best to use self-booting antivirus media such as Kaspersky’s Rescue Disk (download site). Scanning with an alternative operating system can reveal malware that successfully hides from Windows-based anti-malware products. Note: If you have a newer system that uses UEFI, you might need to take additional steps to run self-booting media. See the related Kaspersky support page or the Dec. 11, 2014, Top Story, “How to solve UEFI boot and startup problems.”
Keeping current on the latest malware trends can also help with Internet safety and security. Malware attacks seem to come in waves, so it’s good to know what types of attacks are on the rise.
Along with Windows Secrets, two very useful sources for new malware information are the OUCH! Security Awareness Newsletter and the widely read Krebs on Security site. (Brian Krebs is a former Washington Post reporter who now writes mostly about online criminal activities.)
As always, when in doubt, err on the side of tinfoil-hat paranoia. If you receive an email that just doesn’t feel right, but the sender is listed as someone you know, call them to find out whether the message is for real. Most regular Internet users now know that some messages have spoofed sender addresses — some malicious site stole a Gmail, Hotmail, or Yahoo contact list that had both our name and the names of our acquaintances.
Computing security will always be an ongoing battle between new and innovative hacking techniques and our evolving defenses. These days, simply keeping your anti-malware software up to date isn’t enough. As I’ve said many times before, the best security is to stop and think before clicking a link.
For those who want to take their security a step further, the resources listed above will help confirm that, yes, they really are out to get you.
Protect your Win7/8 setup from the Win10 upgrade
Like all operating-system upgrades, the migration to Win10 will overwrite and replace your current OS. Here’s what to do to preserve your current Win7/8 setup.
Plus: Why you should not use a Win7 image to set up a new Win8 PC, understanding Windows Easy Transfer, and solving a problem with a Win7 “nondestructive reinstall.”
Win10 upgrade will wipe out a Win7/8 setup
Reader Ronald Lenci is wondering what will happen to his Win7 setup if he upgrades it to Win10. The answer applies to Win8, too.
- After July 29, can the Win10 download be used to make a dual-boot setup on a separate drive, so that Win7 is still left on the system as a backup?”
The initial Win10 release — the free version many users have opted for in the “Get Win10” program (MS info) — is an upgrade. By design, almost all operating-system upgrades replace your current setup.
The details are still fuzzy, but Microsoft says that after installing and activating the Win10 upgrade, you’ll be able to download a Win10 .iso file, which you can use for repairs or to perform a clean install of Win10.
But that’s after the free upgrade.
If you want to be certain to preserve your current setup, you need to take some protective steps.
The best approach is to make a full-image backup of your Win7/8 setup. Do this now, prior to the upgrade. First and foremost, that full-image backup will let you undo a failed upgrade or some other significant problem. (Win10 will likely offer some kind of emergency roll-back mechanism, but I think it’s nuts to totally rely on black-box automated tools whose operation is out of your control.)
Beyond disaster recovery, having an image can also let you access and resurrect files from your old setup, if and when needed (more on this in a moment).
You might also be able to use the Win7/8 image to create a dual-boot setup. First, upgrade to Win10; then restore your previous Win7/8 setup to a new partition, disk, or drive. Then let Win10 manage the dual-booting process.
There are, however, two wild cards here. Until Win10 ships, we won’t know how it’ll handle dual-booting; we also don’t know whether Microsoft will allow the re-use of original Win7/8 product keys for reactivation.
We should have answers to both questions soon after Win10 ships.
But again, the task you should tackle right now is to make a complete system image of your current setup. It’s an invaluable safety precaution and will let you keep all your options open — no matter how the Win10 upgrade goes.
If you need a refresher on creating image backups, see:
- “Step two: Create a full-system image” in the May 12, 2011, Top Story, “Build a complete Windows 7 safety net”
- “How File History creates reliable local backups” in the Jan. 15 Top Story, “Mastering Windows 8’s backup/restore system”
There also are many third-party imaging tools available, both free and paid. See, for example, EaseUS Todo Backup, Macrium Reflect, AOMEI Backupper, and many, many others.
Also, for information on how to verify the integrity of native Windows or third-party images and backups, see the April 16 Top Story, “How to safely test file and image backups.”
That article also shows how you might be able to access — and even selectively extract — files from an image/backup without a complete restore to a real or virtual hard drive.
With a current, complete, tested, known-good image of your current setup safely tucked away, you can approach the Win10 upgrade with confidence.
Can a Win7 image be used for a new Win8 PC?
Paul Kevin is pondering a nonstandard use of his Win7 image backups.
- “Quick question for Fred Langa. He has pointed out the usefulness of creating a disk image to restore everything the way it was, such as if your hard drive dies. So I’ve religiously created one each month. I actually used it once when my drive went down, and it was great to have everything back without having to reinstall programs, updates, and so forth.
“Soon, I’m going to buy a new computer that will have Windows 8 installed.
“Can I restore my saved Win7 image to the new computer? Or do I have to reinstall all my programs, because it’s Windows 8?”
No, don’t restore a Win7 image to a Win8 PC.
First, I’ll tell you why that won’t correctly move your user files and software to Win8. Then, I’ll tell you several ways that will work.
Here’s the problem with using a disk image between dissimilar systems. A classic (Win7-style) system image contains everything that was in the original setup — user files, installed programs, the operating system itself, the system-specific drivers, etc.
Obviously, restoring a Win7 image to the new PC will completely overwrite the Win8 installation. (Your new, bought-and-paid-for Win8 setup will be gone.) Your old Win7 setup will be force-fitted onto the new PC.
That’s not what you want! The restored Win7 likely won’t work well; the restored image will contain only the drivers from the previous PC — and none of the drivers that came with the new hardware.
Here’s a better approach: When you get your new PC, use Microsoft’s free Windows Easy Transfer, or an external disk, or a network to move your files from the old PC to the new. (See the next item for details.)
If you want an automated way to move installed software to the new PC, see the discussion — and caveats — on third-party migration tools, also mentioned in the next item.
But I think the best method to set up software on a new PC — especially when you’re moving between different systems and different Windows versions — is to bite the bullet and manually reinstall the software.
A clean, from-the-ground-up install of your software ensures that everything gets set up properly. You’ll have none of the baggage from the old operating system and setup that might come along for the ride and needlessly complicate — or otherwise mess up — the new system.
In any case, when you’re done setting up your new PC, make new, Win8-specific backups and images. The information you need is in the Jan. 15 Top Story, “Mastering Windows 8’s backup/restore system.”
Understanding “Windows Easy Transfer”
Henk Hanemaayer has two Win8.1 setups and wants to move programs, files, and settings from one to the other.
- “I have an issue [with] how to transfer files and settings from one Windows 8.1 PC to another.
“In the past, you were able to use Windows Easy Transfer, but this capability isn’t in Win8.1 — you can transfer files only from previous versions of Windows.
“Do you have a solution?”
Yes, there are several good alternatives to Windows Easy Transfer.
The problem with Windows Easy Transfer (WET) is that it’s designed only for helping with upgrades — it’s not for lateral moves.
That’s why, as you discovered, the WET version built into most versions of Win8.1 is intended only for moving files and settings from Win8.0, Win7, or WinRT (see Figure 1).
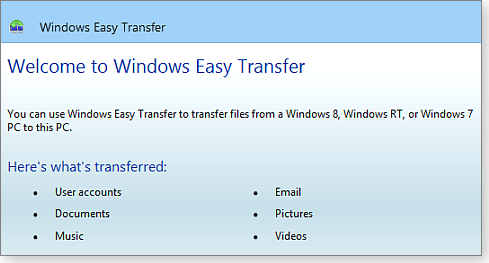
Figure 1. The Win8.1 version of Windows Easy Transfer is limited to moving files from Win8, Win7, or WinRT — it won't work between two copies of Win8.1.
Similarly, the Win7 version of WET (free download; site) is intended only for moving files and settings to Win7 from Vista or XP, period.
Also, the WET for Win8.1 and Win7 can move files between like-bitted systems (i.e., 32-bit to 32-bit; 64-bit to 64-bit) or from 32-bit systems to 64-bit systems. But neither lets you downgrade from 64-bit to 32-bit setups.
With all that said, here are two ways to move files between Win8.1 setups (or from 64-bit to 32-bit setups).
The easiest way is via an external drive. Win8’s File History requires a separate drive or network location, so you probably already have a backup drive. If not, USB-attached external drives are now inexpensive.
Just plug the drive into the source PC (the machine the files are coming from) and copy all the files/folders you want to transfer. Then connect the drive to the destination PC and copy the files/folders to their new locations.
You can also use a local network for basic file/folder transfers.
Transferring user settings and installed software takes a bit more effort.
Signing in to a Microsoft account on your Win8.1 system automatically gives you a free, basic OneDrive account. The OS uses OneDrive to store and sync user settings and native (Metro/Modern) Win8 apps you bought at the Windows store. But this won’t help to move third-party (aka desktop) apps, nor will it work on setups that don’t use a Microsoft-account sign-in or OneDrive.
If the preceding options won’t meet your needs, you can use any of several third-party tools designed specifically to migrate user files, installed software, and user settings — in theory, everything — between different systems.
Popular examples include EaseUS Todo PCTrans (free/paid; site), LapLink PCmover ($60; site), and Zinstall ($119; site). There are many others, both free and paid.
You might wonder at the wide variance in pricing. The paid apps do offer significant enhancements over the free versions. But no tool can realistically guarantee to perfectly migrate all files, settings, and software on all systems. Read the product descriptions carefully before making your selection, and then expect at least some residual cleanup and reinstallation with any tool you choose.
Problems with a Win7 nondestructive reinstall
Erik Kroese encountered error messages when attempting a Win7 no-reformat, nondestructive reinstall as described in the July 14, 2011, Top Story.
- “I tried to do a nondestructive reinstall of Windows 7 Home Premium on my HP/Compaq PC.
“But I got this: ‘The upgrade cannot be performed because of the following problems. These devices, Keyboard Filter and Anti-Malware Core, may not work properly after the upgrade.’
“Looking around on the Internet, I discovered that Keyboard Filter has something to do with the keyboard of the laptop itself and Anti-Malware Core probably with the installed McAfee Total Protection.
“What to do now?”
It sounds like you’ve correctly identified the problems: the “keyboard filter” is indeed most likely an OEM-installed file; the “anti-malware core” is likely part of your McAfee setup.
The latter is easy to work around: temporarily uninstall the anti-malware app after making note of any related product keys or unlock codes.
OEM “keyboard filters” are usually provided as ancillary software that adds nonessential keyboard functions or special key mappings. For example, many HP/Compaq systems ship with “Quick Launch” keyboard-filter software that provides shortcuts for switching between built-in and external displays, bringing up the “HP Support Assistant,” and so on.
Here’s what I recommend: Visit the HP/Compaq support site, look up your exact model PC, grab a copy of the “HP Quick Launch” software, and store the downloaded file in a safe place.
Next, open Control Panel/Programs and Features and uninstall the Quick Launch software that’s currently on your PC.
You should now be able to perform the no-reformat reinstall.
When it’s done, reinstall your anti-malware tool and — if you wish — the Quick Launch software.
With that, you should be good to go with a lean, clean, nondestructively reinstalled setup!
Apps for finding potentially unwanted files
Finding and deleting obsolete files on a hard drive is a time-honored method of getting back storage space.
There is a plethora of utilities designed to help with that task, but they can take very different approaches; here are five examples.
In the April 9 Best Utilities column, I wrote about WinDirStat, a utility that takes an unusual approach to drive analysis and cleaning. An open-source program, it has a graphical “Treemap” view that represents similar types of data on a drive as colored boxes. You can click on individual boxes to drill down into more detailed information.
But this app is designed primarily for IT professionals. It has, for example, the ability to analyze multiple systems, run from custom command-line scripts, and automatically email reports.
As a follow-up to that story, here are alternatives that are a better fit for most PC users. But even these utilities have different strengths and goals. The first two are best for analyzing the size, type, and age of files on a drive. The other three are designed for the task of finding and removing duplicate files.
JDiskReport: Quick, simple, minimally capable
JDiskReport (site) is a quick and easy install, but you must first have full Java installed (free; site). Although JDiskReport is free, I didn’t run into any tagalong software offers during the setup process. The utility first opens as a simple screen with two options: “Scan file tree” and “Open scan.” The latter lets you open a saved session and later will also show previous scans; when clicked, it starts the scan process immediately.
Clicking Scan file tree pops up a directory list. I started by selecting my C: drive and clicking OK; the scan completed in a few minutes. When that was done, JDiskReport brought up the summary window with a pie chart, as shown in Figure 1.

Figure 1. JDiskReport offers a variety of ways to investigate what's consuming drive space. Images 410 pixels wide, max. Move, delete, or duplicate image HTML code as needed.
At the top of the pie chart, you’ll find several tabs: Size Dist, Top 50, Size, Modified, and Types. Each tab gives you information about the types of files on your hard drive. Here’s a quick summary of how they work.
- Size: This produces a pie chart of the files and folders on your hard drive, based on size. This option is most useful because you can click on pie slices and drill down through subfolders. Other view options include ring chart, bar chart, and table view.
- Top 50 lists: It lists the 50 largest files on a drive or in a partition or folder. The list can be sorted by largest, oldest, and newest. For each entry, the app lists size, modified date, and path.
- Size distribution: You’ll see a color-coded bar chart of file sizes on your hard drive. But it doesn’t list any files, so it’s not very useful. It will give you some idea of whether you have many small files (such as images) or a few very large files consuming space.
- Modified distribution: This option creates a table showing the overall size of files by their modified date. It will, for example, show that you have a large number of files that haven’t been edited in a long time. Again, it doesn’t list any files, so it doesn’t seem all that useful, either.
- Type distribution: Here, you’ll get some real data. In pie-chart, bar-chart, and table views, JDiskReport breaks out space consumption by file type. Unfortunately, it doesn’t tell you where to find them.
At the bottom of the default window are several icons: Show Pie Chart, Show Ring Chart, Show Bar Chart, Show Details Table, and the Show Files checkbox, which is not enabled.
Using JDiskReport. JDiskReport seems more like eye candy than a truly useful file/folder analyzer and cleaner. The documentation is minimal, and some features work only under specific circumstances. Finding out what those circumstances are can be frustrating.
Worse, the app offers no duplicate-file detection. But if you want something relatively simple, JDiskReport is free and offers a quick view of space consumption.
SpaceSniffer: Find folders and files by filter
SpaceSniffer (donationware; site) looks like the counterpart to JDiskReport. In fact, its complex graphical display is somewhat like that of WinDirStat.
Because it’s a portable app, you don’t install SpaceSniffer — you simply run the EXE file. Documentation consists of two PDFs: a quick-start guide and a longer user manual.
When you start the program, a dialog box pops up to let you choose which drives to scan. You can also enter a patch to limit what’s examined. When I choose the C: drive, SpaceSniffer immediately starts drawing out a detailed graphical representation of the drive’s contents as a sea of brown and blue boxes, each with a file or folder name (see Figure 2). The bigger the box, the larger the file/folder. Along with the box-based map, the app also displays a Log Console window with ongoing warnings about files it can’t examine.

Figure 2. SpaceSniffer represents the size of folders and files as boxes; clicking a box expands it to show the various sizes of folders and files within.
A complete scan of my 500GB drive took only a few minutes. As the program runs, you’ll see a small, green progress bar at the top right of the main window. When the scan is complete, the progress bar will be replaced with Ready. As the app looks at files and folders, the box display changes in real time.
The overall effect can seem cluttered and overwhelming. To reduce/increase the number of boxes on screen, you can use CTRL – or CTRL + respectively. (Clicking the blue buttons on the toolbar will do the same thing.) If you find the appearance of the boxes seems a little flat, you can change that by clicking on the Use File Classes Style button to the immediate right of the blue buttons (or press Ctrl + T).
Clicking Edit/Configure gives more options for controlling the overall display of information. For example, under Geometry, I increased the size of the font; under Look, I changed the style to a midpoint between Flat and Deep, and I set the Border Contrast to Hard. The result is shown in Figure 3.

Figure 3. SpaceSniffer becomes somewhat easier to view after changing some display options.
Using the SpaceSniffer interface. By default, folders are shown in brown and files in blue. As you move the cursor over the various boxes or headings, each will briefly be illuminated in white, and a tool-tip box will display basic information. If it’s a folder, you’ll see how many files are within that folder plus a prompt: (Double click to zoom). If it’s a file, you’ll see the creation date, the time when it was last modified, and how long ago it was last accessed.
Double-clicking a folder expands it to fill the entire results window. Use this method to go deeper into folders — eventually down to individual files. Again, the bigger the box, the bigger the file.
For individual files, right-clicking pops up a menu of common options such as Open with, Copy, Delete, and Properties.
To step back up the directory tree, simply click the back button on the toolbar. (As with a browser, click the forward button to return to the previously viewed subdirectory.) Clicking the Home button takes you immediately back to the top-level display.
SpaceSniffer’s filters provide a great deal of search power. For example, let’s say you want to search only for JPEG files on your hard drive. To do so, type *.jpg into the Filter parameters box and click the Use File Classes style button. SpaceSniffer will quickly run a search and show JPEG files in green. If, on the other hand, you wanted to exclude JPEG files, you’d type: |*.jpg (where “|” is the vertical line or pipe key) into the search box.
To look for files larger than a specific size, enter something similar to 1000KB into the search box. To search by year, use a similar rule. For example, to find files you haven’t accessed in a year, you’d type: a>1year into the box.
SpaceSniffer’s filter can be much more complex. You’ll want to read the user instructions carefully to fully understand how they work.
The app doesn’t offer any form of click-and-go duplicate-file detection. As with JDiskReport, it’s best used to find and highlight big files, old and unused files, or enormous numbers of similar small files that might be cluttering your system.
SpaceSniffer will appeal to advanced users who want to delve deeply into data filtering. In that sense, it’s much more powerful than JDiskReport.
DupeRAZOR: A fast and easy duplicates finder
DupeRAZOR (site) sells for $25, but you can try a free, fully functional trial version for 30 days. It starts with a standard Windows install process and an option to accept the trial period or buy it. When you first run the app, it pops up a window for selecting drives and paths to search.
Note: Although DupeRAZOR seems to run fine on Win8, the publisher’s site claims compatibility only through Win7; use this app with caution until you’re sure it’s compatible with your system.
When a search starts, another window shows a running score of elapsed time, number of duplicate files found, search progress, and number/size of files checked. At the completion of a search, you’ll see Process Finished — click either the View Results button or the Next button (they appear to do the same thing).
The next window displays a list of duplicate files. DupeRAZOR groups suspected-duplicate files in a long list, initially sorted by name. But it will find duplicate files that have different names. The information on suspected-duplicate files includes size, type, modified date, and location. If you’re working though the list quickly, simply click checkboxes and then delete them en masse with the Delete Checked button.

Figure 4. DupeRAZOR gives you various ways to select and remove duplicate files it finds.
A second choice for removing duplicate files is the Auto Select button, with its drop-down list of options. The basic selections are:
- Keep Newest or Keep Oldest
- Keep with shortest path or Keep with longest path
- Keep with shortest filename or Keep with longest filename
- Keep First in group or Keep Last in group
At the bottom of the list is Switch to Priority Menu, which lets you set layers of arguments and add more options.
Other list options include opening the file in the app of your choice and viewing image files in a preview window.
Files you want to delete can be moved to the recycle bin, deleted permanently, or backed up to a specified folder. You can also Prevent deletion of last file in group or Auto-hide groups with one file left.
Clicking the setting button opens a pane for general settings and file behavior. Clicking More Options lets you protect Windows directories and select a custom-color scheme.
Typically, with a duplicate file–detection app, you’re interested only in your user files. I don’t recommend simply clicking the C: drive for scans. In fact, you’ll probably want to scan files by type, so do your audio files in one session and image files in another.
Overall, DupeRAZOR is quick and easy to use, but its search capabilities are relatively limited.
Duplicate Cleaner Pro 3: Powerful and flexible
Duplicate Cleaner Pro 3 (site) costs $30 for a single user and also comes as a 30-day, crippled trial. For $5 above the price of DupeRAZOR, you get a lot more power and flexibility. For example, Duplicate Cleaner lets you search for files with similar content. It also lets you quickly search only for image or audio files.
When launched, Duplicate Cleaner opens a full interface of search options. Many of them are self-evident; others will take a read through the help files. You’ll also want to take a quick look through the default settings. For example, by default it skips most system files — generally, a very good tactic.
The basic interface has four tabs, shown in Figure 5. The first two — Search Criteria and Scan Location — let you define and limit searches. The second two — Duplicate Files and Duplicate Folders — show results.

Figure 5. Duplicate Cleaner has a comprehensive set of controls for finding both duplicate and similar files.
The Search Criteria tab has three subtabs: Regular Mode, Image Mode, and Audio Mode. To begin a simple search, select the appropriate mode and then specify the criteria. For more complicated searches, Duplicate Cleaner Pro includes a selection of filters.
Regular Mode is useful for comparing all file types, based on content, file name, and/or file date. Unlike DupeRazor, Duplicate Cleaner makes it easy to search for files that are similar — not bit-for-bit duplicates. But, obviously, you have to be far more careful to check the files before deleting a “duplicate.”
Image Mode offers search options such as aspect ratio, rotated, flipped, and resolution. You can even set the ratio of file similarity. Supported file formats include BMP, GIF, JPG, ICO, PNG, EMF, DIG, and Tiff. (Other file types are ignored.) Sadly, it does not support RAW.
Audio Mode is obviously designed for music files. Search options include metatag information such as artist, title, and album — or you can match by audio data. The mode searches only for MP3, OOG, WAV, WMA, APE, FLAC, M4A, and M4P files.
All three search types — Regular, Image, and Audio — include advanced options such as excluding zero-side files, system files, and others.
Before you start a search, click the Scan Location tab. This window lets you quickly select folders from multiple locations, including devices on the local network.
Deleting duplicate files. Scan time will depend on number of files searched, types of files, and your search settings. Unfortunately, the app does not give you a real indication of its progress. It simply shows a moving green “activity” bar and the number of files and folders found. Generally, the process is noticeably slower than with the other apps in this article.
Once a scan is complete, Duplicate Cleaner displays a list of candidates, separated by color bars. File information includes name, path, size, date created, date modified, file type, and image dimensions. Right-clicking a listed file opens a long list of options such as mark, unmark, various filters, rename file, and properties.
The list doesn’t include delete option; files are removed by clicking a checkbox, which puts a strikethrough line through the file name and its stats (see Figure 6). Other options for checked files include move, rename, and create “hardlinks” via the File Removal button.

Figure 6. Duplicate Cleaner clearly highlights files marked for removal with a strikethrough
Duplicate Cleaner Pro 3 offers many more options, such as the ability to select the type of content comparison and an option to search within ZIP files. This utility should be useful to PC users of intermediate-to-advanced skills.
Auslogics Duplicate File Finder
Duplicate File Finder is touted as completely free — and free of adware — but if you use the default Express Install option, you’ll also get Auslogics BoostSpeed, a utility designed to “clean up” your system and make it run faster. (Windows Secrets generally doesn’t recommend most “fix-it” suites.) Aside from that, the installation process is fairly standard.
The running DFF starts with a file-selection wizard. The first window lets you select the type of file to search: all types, images, audio, video, archives, and applications. The next windows let you set the file-size range, set file types to ignore, and set a text string within file names to search for. In a final window, you can set whether files are trashed, sent to the Rescue Center, or permanently removed.
The Rescue Center option archives deleted files — in case you change your mind later.
You can also select a search path from a directory tree displayed in the left pane.
The search process has a progress bar and stats for files found out of total files to be searched. In my informal tests, DFF seems faster than Duplicate Cleaner Pro.
It also returned a large number of suspected duplicates in a long results list (Figure 7). DFF’s user interface makes it somewhat hard to sort through the results. I had to enlarge the default window and resize columns before comparing files. A right-hand column gives you quick access to file previews, basic details, and HEX-based file-header information. And while the app considers PDFs as an image type, they’re not displayed in the preview window.

Figure 7. Duplicate File Finder has a relatively simple interface, but few file-filtering features.
You can manually select the files to delete or make use of the Select button, which gives you options such as Invert Selection, Deselect All, Select One in Each Group, and others.
Again, once you’ve made your selection, the Delete Selected Files button becomes active, allowing you to send files to the recycle bin or to the Rescue Center — or to delete them permanently.
One annoying feature about Duplicate File Finder: it seems designed to get you to install BoostSpeed and other Auslogics apps. For example, the Advanced toolbar option has “Optimize My Computer,” “Protect My PC Against Viruses,” and “Protect My Data From Accidental Loss.” Another prompt asks to “Check your system state.”
There appear to be no actual advanced options such as filters and searches for “similar” files.
Bottom line: No losers, but some clear winners
Recommendations for all these programs: You should use these utilities only if you fully understand the filing system on your computer. You should also have a recent backup before you start deleting bunches of files.
JDiskReport and SpaceSniffer are hard drive–cleaning programs, not duplicate-file finders. These two apps are truly opposites: JDiskReport is easy to use but has limited functionality; SpaceSniffer is more capable, but not nearly as user-friendly as JDiskReport. The best product depends on your skill level and UI preferences.
Of the duplicate-file finders, Duplicate Cleaner Pro is the clear winner. It has a good combination of intuitive interface and extensive filtering controls. But it will take some time to understand how to use all its features. If ease of use is your most important selection criterion, I recommend Duplicate File Finder. DupeRAZOR is also relatively easy to use and perhaps a bit more capable than DFF.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Windows 7 ISO /Windows 10 ISO
by
ECWS
2 hours, 33 minutes ago -
No HP software folders
by
fpefpe
3 hours, 18 minutes ago -
Which antivirus apps and VPNs are the most secure in 2025?
by
B. Livingston
1 hour, 18 minutes ago -
Stay connected anywhere
by
Peter Deegan
8 hours, 40 minutes ago -
Copilot, under the table
by
Will Fastie
5 hours, 55 minutes ago -
The Windows experience
by
Will Fastie
14 hours, 55 minutes ago -
A tale of two operating systems
by
Susan Bradley
5 hours, 51 minutes ago -
Microsoft : Resolving Blue Screen errors in Windows
by
Alex5723
20 hours, 14 minutes ago -
Where’s the cache today?
by
Up2you2
1 day, 11 hours ago -
Ascension says recent data breach affects over 430,000 patients
by
Nibbled To Death By Ducks
1 day, 4 hours ago -
Nintendo Switch 2 has a remote killing switch
by
Alex5723
4 hours, 40 minutes ago -
Blocking Search (on task bar) from going to web
by
HenryW
1 day, 12 hours ago -
Windows 10: Microsoft 365 Apps will be supported up to Oct. 10 2028
by
Alex5723
2 days, 4 hours ago -
Add or Remove “Ask Copilot” Context Menu in Windows 11 and 10
by
Alex5723
2 days, 4 hours ago -
regarding april update and may update
by
heybengbeng
2 days, 6 hours ago -
MS Passkey
by
pmruzicka
1 day, 8 hours ago -
Can’t make Opera my default browser
by
bmeacham
2 days, 14 hours ago -
*Some settings are managed by your organization
by
rlowe44
2 days ago -
Formatting of “Forward”ed e-mails
by
Scott Mills
2 days, 13 hours ago -
SmartSwitch PC Updates will only be supported through the MS Store Going Forward
by
PL1
3 days, 8 hours ago -
CISA warns of hackers targeting critical oil infrastructure
by
Nibbled To Death By Ducks
3 days, 17 hours ago -
AI slop
by
Susan Bradley
1 day, 11 hours ago -
Chrome : Using AI with Enhanced Protection mode
by
Alex5723
3 days, 18 hours ago -
Two blank icons
by
CR2
1 day, 3 hours ago -
Documents, Pictures, Desktop on OneDrive in Windows 11
by
ThePhoenix
1 day, 5 hours ago -
End of 10
by
Alex5723
4 days, 6 hours ago -
Single account cannot access printer’s automatic duplex functionality
by
Bruce
3 days, 4 hours ago -
test post
by
gtd12345
4 days, 12 hours ago -
Privacy and the Real ID
by
Susan Bradley
4 days, 2 hours ago -
MS-DEFCON 2: Deferring that upgrade
by
Susan Bradley
2 days, 5 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

