
|
There are isolated problems with current patches, but they are well-known and documented on this site. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Update: Tools to remove almost any malware
In this issue
- ON SECURITY: Update: Tools to remove almost any malware
- PATCH WATCH: April's shower of updates for Windows and Office
- LOUNGE LIFE: Can older PCs happily run Windows 10?
Update: Tools to remove almost any malware
Special-purpose anti-malware scanners not only clean up some of the worst forms of malware, they can also be used for routine deep scans.
Here are 12 tools you can use to verify that your full-time anti-malware tool is truly keeping your PC malware-free
This article starts where a pair of earlier articles leaves off. To get the most out of the information below, please take a moment to skim through those earlier, foundational stories.
Start with the April 4, 2013, Top Story, “Microsoft’s six free desktop security tools,” which explains how Microsoft defines two main categories of malware: malicious software and potentially unwanted software. The article then discusses the built-in and free-download Windows tools that combat each type of malware.
The article also clarifies some confusing Microsoft nomenclature. For example, Windows Defender, built into Win8 and Win10, is completely different from the identically-named “Windows Defender” in Vista and Win7. The former is a relatively good front-line anti-malware application; the latter is a much simpler tool that should never be relied on as your primary defense against malware. The aforementioned Top Story has more details.
New versions of two other Microsoft tools discussed in that article — Microsoft Safety Scanner (aka “System Sweeper”) and Windows Defender Offline — are covered in this update.
Next, see “A dozen tools for removing almost any malware” (April 11, 2013, Top Story), which provides an introduction to the topic of using standalone, self-contained anti-malware scanners either to clean up difficult infections or for periodic deep scans to verify that your primary anti-malware defenses have left your PC truly malware free. I won’t repeat those introductory details here; please review the article.
This update article discusses current anti-malware–scanning tools, replacing some of the previously-recommended tools with new ones and, in all cases, noting how these special-purpose scanners now work with Win8.1 and Win10 (neither of which was released when the original articles ran).
Anti-malware for routine cleanup/verification
Trend Micro’s HouseCall (free; site) has been around for years and has an excellent reputation. It’s available in 32-bit and 64-bit versions for all current versions of Windows — Vista, Win7, Win8, and Win10.
HouseCall, shown in Figure 1, is known for its speed, making it an excellent choice for routine use to verify that a PC is malware-free.

Figure 1. Trend Micro's HouseCall scanner is small, simple, and quick.
HouseCall has the three standard levels of scans offered by most anti-malware tools — “Quick,” “Full,” and “Custom” — but, unique among the products I looked at, it also offers the optional HomeDevice Guard feature that scans your local network, checking whether your attached devices are vulnerable to common types of network-based attack.
ESET’s Online Scanner (free; site) is another tool with a long pedigree and a well-deserved reputation for excellence.
There are two flavors of Online Scanner: browser-based and standalone. If you download the application via Internet Explorer, and you have ActiveX enabled, you’ll get the in-browser version. On the other hand, if you download the Scanner through Chrome, Firefox, Opera, and so forth, you get the standalone edition that runs outside the browser. Once launched, both versions operate identically.
ESET’s Online Scanner is available in 32- and 64-bit versions. Although the ESET site only promises compatibility for Windows XP, Vista, and Win7, I’ve run it on Win8 and Win10 systems without trouble.
You can select scan type (“Quick,” “Full,” or “Custom”), and target which drives to scan (local and/or remote/networked). You can also have Online Scanner look inside archives such as ZIP files — something only a few other scanners can do. Moreover, the scanner will look for potentially unwanted programs (aka PUPs).

Figure 2. ESET's highly configurable Online Scanner comes in both standalone (shown) and browser-based versions.
For very deep malware scans, I typically run Online Scanner overnight, with all options enabled; it thoroughly examines all files on a PC’s local and network-attached drives.
Microsoft Safety Scanner (Figure 3) is fast, free, and easy to use, and it can find/remove both malicious software and PUPs. Microsoft states it’s compatible with XP, Vista, and Win7, but I’ve had no trouble running it on Win8 and Win10 PCs. You’ll find 32- and 64-bit versions on its info/download page.

Figure 3. Microsoft's Safety Scanner is extremely easy to use.
McAfee’s Stinger (free; site) is a far more specialized tool. Rather than scan for all known forms of malware, it looks for rootkits; it then scans running processes, loaded modules, and the Registry and folder locations most commonly used by malware.
Stinger’s narrower focus means that scans are very fast, making this tool a good choice for malware first-aid. It can find and cure many of the most common types of malware problems in short order. However, Stinger’s limited focus makes it less thorough than the other tools in this article.
Stinger is available in 32- and 64-bit versions, and McAfee says it’s compatible with XP, Vista, and Win7/8. I also ran it successfully on Win10 without trouble.
Note: There’s also a beta (experimental) 64-bit Stinger version that includes “Real Protect,” a real-time, malware-behavior detection technology that should detect for suspicious activity — even if there’s no associated malware signature.
This sounds promising, but I couldn’t get the beta software to run properly on a Win10 Pro x64 test PC. (Again, the official 64-bit standard version of Stinger without Real Protect ran flawlessly.)

Figure 4. McAfee's Stinger is exceptionally fast, and it targets both rootkits and common types of malware.
If these relatively simple, on-demand scanners/cleaners don’t work, or if an infection has crippled Windows, it’s time to roll out the big guns.
Heavy-duty, self-booting, malware-cleaning tools
Some forms of malware — rootkits, for example — are especially adept at playing hide-and-seek with anti-malware apps. Infections also have been known to actually disable anti-malware tools and scanners, and to block Windows Update and browsers.
The solution is a self-contained, self-booting system scanner that operates entirely outside of Windows.
These tools are typically offered as downloadable ISO files that you use to create bootable CD, DVD, or flash drives — commonly called rescue disks — that contain both a minimal operating system and a malware scanner.
When you start and run a PC from a rescue disc, your Windows setup — and any infections it might harbor — remains inert and inactive. Malware can’t hide itself, and it’s considerably easier for the scanner to look everywhere it needs to.
The one drawback with rescue disks is setup and use; you have to take the time to create the bootable CD/DVD or flash drive. You also have to be able to boot your system from that disc or drive, which can be difficult on newer PCs with UEFI BIOSes and “Secure Boot” technology.
How to make a bootable DVD/CD: Assuming you have an optical drive, Windows 10/8/7 all have built-in tools for creating bootable CDs and DVDs (MS info). Or you can use a third-party CD/DVD burning app such as Free ISO Burner (site).
How to make a bootable flash drive: On Win10/8/7, use Microsoft’s free Windows USB/DVD Download Tool (site); or any of the many available third party tools.
For help booting from your rescue disc or flash drive:
- “How to solve UEFI boot and startup problems” – Dec. 11, 2014, Top Story
- “Emergency access to your PC’s UEFI settings” – Jan. 15, 2015, LangaList Plus
- “Emergency repair disks for Windows: Part 1” – April 10, 2014, Top Story
- “Emergency repair disks for Windows: Part 2” – April 17, 2014, Top Story
Here are three free, self-booting rescue disks to consider:
The Kaspersky Rescue Disk (free; info/download) is a self-booting, Linux-based cleaning tool. Note that you don’t have to know anything about Linux — the tool has a complete, ready-to-run, point-and-click, Windows-like desktop environment (see Figure 5). It’s about as easy to use as any good Windows application.

Figure 5. Linux based, the Kaspersky Rescue Disk has a familiar graphical interface.
I no longer recommend F-Secure’s Rescue CD (free; site). I couldn’t get it to run properly on Win10Pro x64 system, and I could not figure out why. If you’re still interested in it, see the previous write up in “A dozen tools for removing almost any malware” (April 11, 2013, Top Story).
In its place, I now recommend the AVG Rescue CD (free; site), a Linux-based, anti-malware tool that includes additional rescue/scan/repair options.
It boots to a minimalistic, text-based environment (see Figure 6), though it simulates a graphical environment via ASCII graphics, reminiscent of old-school DOS apps. It’s easy to use; you navigate with the keyboard’s arrow keys and make selections with the Enter key.

Figure 6. The AVG Rescue CD has an extremely simple, DOS-like interface.
With minimal graphics and no mouse support required, AVG’s Rescue CD should operate on just about any hardware — including very old, damaged, or otherwise hardware-constrained PCs.
Windows Defender Offline (WDO) is a stripped-down, locked-down, bootable version of Windows that has one function: running a self-contained version of Win10/8’s Windows Defender. It looks and operates much like the built-in versions of Windows Defender — and, for that matter, much like the Win7/Vista versions of Microsoft Security Essentials.
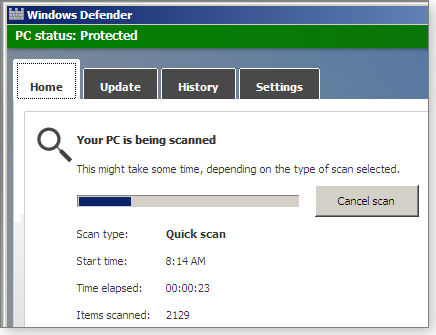
Figure 7. Windows Defender Offline is effectively a bootable, standalone version of Win8/10's built-in Windows Defender.
You’ll find free 32- and 64-bit versions of WDO that work on all current Windows versions (through Win10) on an MS info/download page.
Other Linux-based tools worth a look
If the above tools don’t meet your needs or won’t work on your PC (no software works on all systems), consider using any of the following free, well-regarded, self-booting, Linux-based anti-malware scanners. I’ve tried them all on various Windows versions up to and including Win10 Pro x64. They all offer something worthwhile.
- Bitdefender Rescue CD (site) offers a beautiful and fully graphical interface.
- Vba32 Rescue (site) uses a simple, text-based (ASCII graphics) interface that you navigate via the arrow keys. This tool can also help you to recover/copy files from a system that will no longer boot Windows.
- Comodo Rescue Disk (site) offers a choice of graphical or text-mode operation.
- Panda SafeCD (site) is the oldest tool in this lineup, but it still downloads and uses the very latest malware signatures. It has a simple, graphical interface that’s extremely easy to use.
- Sophos Bootable Anti-Virus (site) uses a slightly unusual, multi-step download process. You first download a small executable program that then downloads and builds the ISO for you.
All cleaned? Now keep your PC that way!
If an anti-malware scan finds an infection on your system, it’s an indication that your current, full-time anti-malware defenses might not be up to the job. Consider installing and using a different tool — ASAP!
Whether your system is infected or clean, use one or more of the special-purpose scanners discussed above to verify that your regular anti-malware tool is keeping your PC safe.
With a good, full-time anti-malware tool, buttressed by a periodic deep scan with a separate anti-malware scanner, you can help ensure that your PC is truly clean — and stays that way!
| Feedback welcome: Have a question or comment about this story? Post your thoughts, praise, or constructive criticisms in the WS Columns forum. To rate this or other stories, click over to our polls page. |
April's shower of updates for Windows and Office
An Adobe Flash Player update is critical — a Samba exploit: not so much.
April’s security updating includes keeping our browsers current, fixing Windows components, and protecting ourselves from ransomware.
Note: If you keep track of Security Bulletin numbers, you’ll notice that MS16-043 is missing. We can assume there’s a good reason. When Microsoft skips a bulletin number, it usually means that the company discovered issues with an update and pulled it at the last minute. We’ll probably see the missing update later this month or next month. Stay tuned: I’ll let you know when it appears.
Also, I’m tracking issues with slow Win7 updates, as noted by my colleague Woody Leonhard in a InfoWorld article.
MS16-050 (3154132)
A missing out-of-cycle Flash Player update?
With reports of a surprise Adobe Flash Player patch, some Windows 8.1 and 10 users might be wondering when they’ll see it. As noted in Tuesday’s newsletter, Adobe released a critical update on Thursday to block possible ransomware attacks. But Flash is embedded into Windows 8.1 and 10, and there’s usually a delay between when Adobe releases a Flash update and when Microsoft sends the fix out through Windows Update. In the case of Windows 10, the patch was included in the cumulative update sent out this past Tuesday.
I like Win10’s cumulative update model when setting up a new machine; getting the PC fully updated is much faster and easier. But cumulative updating does have drawbacks, and the timing of critical patching is one of them. Win7 machines received the Flash update this past Friday; Win10 machines received it four days later.
Reportedly, the July “Anniversary” Win10 update will give Edge better Flash controls. But until then, you can block Flash in Edge by clicking the browser’s three-dot tools icon/Settings. At the bottom of the Settings menu, click View Advanced Settings. Look for the Use Adobe Flash Player toggle. (A handy How-To Geek post tells how to turn off Flash in most browsers.)
For even better security, you might use a spare machine to watch Flash content. That might sound draconian — but only if you’re confident you’ll never run across malicious Flash content on websites or you have firewall that has built-in, unified-threat management.
(If you dabble in technology, consider setting up the free Sophos UTM Home Edition firewall [more info] on an old PC or a virtual machine. This option isn’t for the faint of heart, but it might let you sleep better at night, knowing your home network is well protected.
 What to do: This fix is rated critical. Win8.1 users should install KB 3154132 (MS16-050) as soon as possible. Win10 users should not delay the installation of cumulative update KB 3147458 or KB 3147461.
What to do: This fix is rated critical. Win8.1 users should install KB 3154132 (MS16-050) as soon as possible. Win10 users should not delay the installation of cumulative update KB 3147458 or KB 3147461.
MS16-037 (3148198)
Malware defense via regular browser maintenance
As usual, Patch Tuesday week is a good time to ensure that all browsers are up to date. A reminder that Internet Explorer must be kept up to date, even if you never use it. Also, check that all your other browsers are current.
Note that merely opening a website with malicious content could lead to a Windows infection — which is why I also recommend doing casual browsing on a non-Windows device. For example, now that my sister does her random Web searches on an iPad, I no longer have to clean up her browser for any number of weird oddities. So you may wish to use a tablet for your more adventuresome Internet surfing.
 What to do: Install critical cumulative update KB 3148198 (MS16-037) when offered.
What to do: Install critical cumulative update KB 3148198 (MS16-037) when offered.
MS16-047 (3149090)
Badlock bug is not so bad after all
It seems that security researchers have been trying new tactics to gain headlines and our attention. Last month the buzz started about a threat surrounding Samba (more info) and Microsoft file shares. The noise was so loud, you’d have thought we were about to see massive attacks and any number of horrible computer vulnerabilities.
As it turns out, this Windows vulnerability isn’t as bad as its hype. It’s of concern mostly if you have an active-directory network with a Samba server as a domain member. Most home networks don’t use active directory.
Still the patch, rated important, is needed for preventing possible man-in-the-middle attacks. There’s no immediate threat for most Windows users, but I’ll be looking more for Samba side effects.
 What to do: Install KB 3148527 (MS16-047) when offered.
What to do: Install KB 3148527 (MS16-047) when offered.
MS16-038 (3147458, 3147461)
What’s in Win10’s April cumulative update
The cumulative Win10 updates include both security and nonsecurity fixes. April’s includes the following:
- Improved reliability for IE 11, .NET Framework, wireless LAN, Microsoft Edge, Windows Update, sign-ins, Bluetooth pairing, network connectivity, map apps, video playback, Cortana, USB, File Explorer, and Narrator
- Fixes USB connectivity issue
- On resume from sleep, improved printer discovery
- Fixes lock screen issue
- Supports visual voicemail on dual SIM phones
- Fixes audio playback problem with music apps on a phone
- Fixes revised daylight-savings time issue
- Other patches for shutdown delays, buying apps in the Store, facial recognition, Microsoft Installer, and more
The cumulative update includes a reissued security patch MS16-033. It addresses additional threats from malicious USB devices.
The update also has two security fixes that only Win10 needs. MS16-046 prevents attacks using a secondary-sign-in vulnerability. MS16-049 blocks denial-of-service attacks that use malicious packets directed towards Windows’ https.sys (a kernel driver used to handle HTTP requests).
Another patch, KB 3125217, is a cumulative-update clean-up tool. When Win10 is installed on smaller devices, future updates might not install because there isn’t enough room on the device.
Finally, Microsoft announced that build 1511 is officially the “Current branch for business”. Those running the original version of Win10 Pro will still get security updates. But now businesses are urged to move off of the original release and onto build 1511.
Note: When the “Anniversary” build is released in July, the original RTM Win10 will no longer get security updates — but build 1511 will.
 What to do: Don’t delay the installation of KB 3147458 (build 1511) or KB 3147461 (Win10 RTM). See MS Security Bulletin MS16-038 for more information.
What to do: Don’t delay the installation of KB 3147458 (build 1511) or KB 3147461 (Win10 RTM). See MS Security Bulletin MS16-038 for more information.
MS16-039
Multiple patches for the MS Graphics Component
Four vulnerabilities in the Microsoft Graphics Component could allow elevation-of-privilege and/or remote-code-execution attacks via malicious fonts. The update — actually a collection of updates affecting various applications — changes how the Windows font library handles embedded fonts.
Note: There are early reports of problems with KB 3114566 for Office 2010, as noted in its description page. The rest of the patches include:
- 3114542 – Office 2007
- 3114944 – Skype for Business 2013
- 3114960 – Skype for Business 2016
- 3114985 – Word Viewer
- 3142041 – .NET 3.0 SP2
- 3142042 – .NET 3.5.1
- 3142043 – .NET 3.5
- 3142045 – .NET 3.5
- 3144427 – Lync 2010
- 3144428 – Lync attendee 2010
- 3144429 – Lync admin install 2010
- 3144432 – Live Meeting console 2007
- 3145739 – Windows
Note: According to the update’s description, the fix of Office 2010 doesn’t apply on Vista and later Windows versions, which don’t have the vulnerability. So you might not see KB 3114566.
 What to do: Put KB 3114566 on hold for now. Install any of the rest of these critical updates, if and when offered. See MS Security Bulletin MS16-039 for more information.
What to do: Put KB 3114566 on hold for now. Install any of the rest of these critical updates, if and when offered. See MS Security Bulletin MS16-039 for more information.
MS16-040 (3146963)
XML flaw used in browser attacks
Extensible Markup Language (XML; more info) is used to design and code the websites we use every day. But a vulnerability in Windows’ XML Core Services could let an attacker take control of systems remotely, by using bogus website links.
The fix, KB 3114566, changes how MSXML parses links. Rated critical, this patch applies to all current versions of Windows.
 What to do: Install KB 3146963 (MS16-040) when offered.
What to do: Install KB 3146963 (MS16-040) when offered.
MS16-041 (3143693)
.NET 4.6 vulnerability leads to sideloading
As noted in a Full Disclosure post, .NET 4.6 could allow malicious Windows DLL side-loading. This isn’t the first time (and, unfortunately, probably not the last time) we’ve had to patch Windows and Office for hijacked DLLs. In this instance, an attacker can take control of a system simply by luring you into opening a malicious document.
Rated important, this update is only for Vista, Win7, and editions of Windows Server 2008.
 What to do: Install KB 3143693 (MS16-041) when offered.
What to do: Install KB 3143693 (MS16-041) when offered.
MS16-042 (3148775)
Various Office apps used in attacks
Four flaws in how Office handles objects in memory could lead to ransomware and remote-code-execution attacks. Users running PCs in an admin-level account are the most vulnerable. The patches in this update include:
Note: You might get “Windows installer service” error after installing KB 3114888 for Excel 2010 or KB 3114993 for Word 2010. The update’s description page provides two workarounds.
Office 2007
Office 2010
Office 2013
Office 2016
- 3114964 – Excel (important)
Other Office software
- 3114982 – Office Compatibility Pack SP3 (critical)
- 3114895 – Office Compatibility Pack SP3 (important)
- 3114898 – Excel Viewer (important)
- 3114987 – Word Viewer (critical)
- 3142577 – Word for Mac 2016 (important)
- 3154208 – Word for Mac 2011 (important)
Note: You might receive patches for multiple Office versions, if you’ve upgraded to newer Office releases and the vulnerable code is on your system.
Note for server admins: You’ll need to patch Excel Services on SharePoint 2007 (KB 3114897), Excel Services on SharePoint 2010 (KB 3114871), Word Automation on SharePoint 2013 (KB 3114927), and Office Web apps 2010 (KB 3114991) and 2013 (KB 3114934)
 What to do: Install any of the above Office patches in MS16-042 if offered.
What to do: Install any of the above Office patches in MS16-042 if offered.
MS16-044 (3146706)
Linking Windows to cyber attackers
Windows Linking and Embedding (OLE; more info) allows communications between objects. However, hackers discovered a vulnerability in Windows’ OLE component that could allow remote attacks. The update is rated important because the attacker must trick the victim into opening a malicious file or program. Windows 10 isn’t affected.
 What to do: Install KB 3146706 (MS16-044) when offered.
What to do: Install KB 3146706 (MS16-044) when offered.
MS16-048 (3146723)
Windows subsystem flaw leads to full PC control
The Windows Client Server Runtime Subsystem (CSRSS; more info) is a critical component of the operating system. A vulnerability in the subsystem could give an attacker more control over a system, if he signs in to the machine and runs custom code. The fix is rated important for Win8.1 and Win10.
CSRSS was essential in older versions of Windows. But more of Window’s key components now in the protected kernel. Still, CSRSS is still an important element for starting up and shutting down a PC.
 What to do: Install KB 3146723 (MS16-048) if and when offered.
What to do: Install KB 3146723 (MS16-048) if and when offered.
MS16-045 (3135456)
When a guest takes control of the host
Our final official security update is for the Hyper-V system included with Win8.1, Win10, and editions of Server 2012. A vulnerability could let an attacker who is signed in as a Hyper-V guest run malicious code and take remote control of systems.
As a proactive measure, Microsoft is releasing the update, rated important, to any platform that might contain the Hyper-V code — even if you aren’t running a virtual machine.
 What to do: Whether or not you run Hyper-V virtual machines, install KB 3135456 (MS16-045) when offered.
What to do: Whether or not you run Hyper-V virtual machines, install KB 3135456 (MS16-045) when offered.
3152550
Microsoft Mouse get a special update
A few months back, a CNET report described “mousejacking” — the hijacking of wireless mice with a USB dongle. Several mouse vendors released updates to fix the issue.
KB 3152550 is Microsoft’s fix for its wireless devices. Look for this update if you have a Microsoft device; for other vendors, check online for updated software. Of course, you can always get an old-fashioned wired mouse and sleep a bit easier.
 What to do: Install KB 3152550 if you have a Microsoft wireless mouse.
What to do: Install KB 3152550 if you have a Microsoft wireless mouse.
Last week’s release of April nonsecurity updates
As you probably know, Microsoft now releases nonsecurity Office updates on the first Tuesday of the month. That means we’ve had a week to watch any issues. However, that doesn’t mean I now recommend installing nonsecurity fixes and enhancements along with security patches. Keeping them separate helps with tracking down any unexpected side effects.
Bottom line: I recommend waiting another week or two before installing any new nonsecurity updates — for either Windows or Office.
For the full list of nonsecurity Office updates, including SharePoint fixes, see MS Support article 3150264.
Windows 7
- 3147071 – Connection to Oracle database fails with MS ODBC or OLE DB Driver.
- 3148851 – Time-zone changes for Russia
Office 2007/2010
- 3114867 – PowerPoint 2010; Broadcast Service unavailable to Windows Live ID
- 3114979 – Office 2007 junk-mail filter
- 3114989 – Office 2010; Access issues after installing KB 3085515
- 3114996 – Outlook 2010; various fixes
- 3114999 – Outlook 2010 junk-mail filter
Office 2013
- 3114815 – PowerPoint; hyperlinks and media fail in Kiosk mode
- 3114825 – Office; clipped double-byte characters
- 3114928 – Office; various fixes
- 3114932 – Visio; images won’t load on ribbon, other VBA issues
- 3114941 – Outlook fix for various Exchange issues
- 3114942 – Outlook junk-mail filter
- 3114953 – OneDrive for Business; synching SharePoint and sync restore
- 3114954 – Project; various fixes
- 3039756 – Office; SQL Server Reporting Services search indexing
- 3114974 – Outlook; Adds Autodiscover support for non-Outlook MAPI apps
- 3114977 – Outlook; HTTP 500 error and free/busy info not displayed
- 3085587 – Office; font issues on PDF creation in Word
Office 2016
- 2920720 – Office; font issues on PDF creation in Word
- 3114535 – PowerPoint; Morph-transition playback support
- 3114694 – Office; fixes not documented
- 3114712 – Office; SharePoint checkout error message
- 3114854 – Office; Unhandled-exception error when opening Office in safe mode
- 3114856 – Office; Language Interface Pack
- 3114859 – PowerPoint; Morph-transition playback support
- 3114860 – Office; clipped double-byte characters
- 3114864 – OneDrive for Business; synching issues with SharePoint
- 3114903 – Office; Dengxian font-family update
- 3114957 – Visio; various fixes
- 3114958 – Office; various improvements and fixes
- 3114959 – Outlook junk-mail filter
- 3114961 – PowerPoint; Morph-transition playback support
- 3114965 – Office; After apps insert, Office 2013 and 2016 apps shown
- 3114968 – Office; SharePoint synching failures
- 3114969 – Word; crashes with views and subheadings collapse
- 3114970 – Office; various fixes
- 3114971 – PowerPoint; Morph-transition playback support
- 3114972 – Outlook; numerous fixes
- 3114973 – Project; numerous fixes
 What to do: I’m not ready to give the green light for these nonsecurity updates. I’ll report back in the next Patch Watch column.
What to do: I’m not ready to give the green light for these nonsecurity updates. I’ll report back in the next Patch Watch column.
Regularly updated problem-patch chart
This table provides the status of recent Windows and Microsoft application security updates. Patches listed below as safe to install will typically be removed from the table about a month after they appear. Status changes are highlighted in bold.
For Microsoft’s list of recently released patches, go to the MS Security TechCenter page.
| Patch | Released | Description | Status |
|---|---|---|---|
| 3137513 | 03-08 | Win PDF Library | Install |
| 3138910 | 03-08 | Windows Media; also KB 3138962 | Install |
| 3139398 | 03-08 | Windows USB driver | Install |
| 3139852 | 03-08 | Windows kernel | Install |
| 3139914 | 03-08 | Windows Secondary Logon | Install |
| 3139929 | 03-08 | IE cumulative update | Install |
| 3139940 | 03-08 | Windows OLE | Install |
| 3140410 | 03-08 | Windows; Vista and Win7 | Install |
| 3140709 | 03-08 | Windows Library; Vista | Install |
| 3140735 | 03-08 | Windows OpenType fonts | Install |
| 3140745 | 03-08 | Win10/Edge cumulative update | Install |
| 3140768 | 03-08 | Win10 1511/Edge cumulative update | Install |
| 3141780 | 03-08 | .NET; see MS16-035 for full list | Install |
| 3141806 | 03-08 | MS Office; see MS16-029 for full list | Install |
| 3135456 | 04-12 | Windows Hyper-V | Install |
| 3143693 | 04-12 | NET Framework | Install |
| 3145739 | 04-12 | MS Graphics Component; hold on KB 3114566 | Install |
| 3146706 | 04-12 | Windows OLE | Install |
| 3146723 | 04-12 | CSRSS; Win8.1, included in Win10 cumulative update | Install |
| 3146963 | 04-12 | MS XML Core Services | Install |
| 3147458 | 04-12 | Cumulative Win10 1511 update; KB 3147461 for Win10 | Install |
| 3148198 | 04-12 | Internet Explorer cumulative update | Install |
| 3148538 | 04-12 | Secondary Logon; Win10 only | NA |
| 3148775 | 04-12 | Office; see MS16-042 for full list | Install |
| 3148795 | 04-12 | HTTP.sys; Win10 only | Install |
| 3149090 | 04-12 | SAM/LSAD Remote Protocols | Install |
| 3154132 | 04-12 | Flash; Win8.1, included Win10 cumulative update | Install |
Status recommendations: Skip — patch not needed; Hold — do not install until its problems are resolved; Wait — hold off temporarily while the patch is tested; Optional — not critical, use if wanted; Install — OK to apply.
| Feedback welcome: Have a question or comment about this story? Post your thoughts, praise, or constructive criticisms in the WS Columns forum. |
Can older PCs happily run Windows 10?
One of the most common questions asked about Windows 10 is whether it’ll run on aging machines.
In the Windows 10 forum, fellow Loungers give kevmeist tips on which systems to start with and whether to do an upgrade or clean install. Read the thread.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right into today’s discussions in the Lounge. If you’d like to quickly see what’s new in the Lounge, click to the New Posts page.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Discover the Best AI Tools for Everything
by
Alex5723
5 hours, 57 minutes ago -
Edge Seems To Be Gaining Weight
by
bbearren
44 minutes ago -
Rufus is available from the MSFT Store
by
PL1
16 hours, 56 minutes ago -
Microsoft : Ending USB-C® Port Confusion
by
Alex5723
19 hours, 5 minutes ago -
KB5061768 update for Intel vPro processor
by
drmark
1 hour, 30 minutes ago -
Outlook 365 classic has exhausted all shared resources
by
drmark
17 hours, 16 minutes ago -
My Simple Word 2010 Macro Is Not Working
by
mbennett555
14 hours, 50 minutes ago -
Office gets current release
by
Susan Bradley
17 hours, 28 minutes ago -
FBI: Still Using One of These Old Routers? It’s Vulnerable to Hackers
by
Alex5723
2 days, 7 hours ago -
Windows AI Local Only no NPU required!
by
RetiredGeek
1 day, 16 hours ago -
Stop the OneDrive defaults
by
CWBillow
2 days, 8 hours ago -
Windows 11 Insider Preview build 27868 released to Canary
by
joep517
2 days, 18 hours ago -
X Suspends Encrypted DMs
by
Alex5723
2 days, 20 hours ago -
WSJ : My Robot and Me AI generated movie
by
Alex5723
2 days, 20 hours ago -
Botnet hacks 9,000+ ASUS routers to add persistent SSH backdoor
by
Alex5723
2 days, 21 hours ago -
OpenAI model sabotages shutdown code
by
Cybertooth
2 days, 22 hours ago -
Backup and access old e-mails after company e-mail address is terminated
by
M W Leijendekker
2 days, 10 hours ago -
Enabling Secureboot
by
ITguy
2 days, 17 hours ago -
Windows hosting exposes additional bugs
by
Susan Bradley
3 days, 5 hours ago -
No more rounded corners??
by
CWBillow
3 days, 1 hour ago -
Android 15 and IPV6
by
Win7and10
2 days, 15 hours ago -
KB5058405 might fail to install with recovery error 0xc0000098 in ACPI.sys
by
Susan Bradley
3 days, 18 hours ago -
T-Mobile’s T-Life App has a “Screen Recording Tool” Turned on
by
Alex5723
3 days, 20 hours ago -
Windows 11 Insider Preview Build 26100.4202 (24H2) released to Release Preview
by
joep517
3 days, 15 hours ago -
Windows Update orchestration platform to update all software
by
Alex5723
4 days, 4 hours ago -
May preview updates
by
Susan Bradley
3 days, 15 hours ago -
Microsoft releases KB5061977 Windows 11 24H2, Server 2025 emergency out of band
by
Alex5723
3 days, 7 hours ago -
Just got this pop-up page while browsing
by
Alex5723
3 days, 20 hours ago -
KB5058379 / KB 5061768 Failures
by
crown
3 days, 17 hours ago -
Windows 10 23H2 Good to Update to ?
by
jkitc
2 days, 19 hours ago
Recent blog posts
Key Links
| S | M | T | W | T | F | S |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | 7 |
| 8 | 9 | 10 | 11 | 12 | 13 | 14 |
| 15 | 16 | 17 | 18 | 19 | 20 | 21 |
| 22 | 23 | 24 | 25 | 26 | 27 | 28 |
| 29 | 30 | |||||
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

