
|
There are isolated problems with current patches, but they are well-known and documented on this site. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Windows 7 Starter Edition limits netbook designs
In this issue
- BONUS: It's our 200th issue! Get our bonus to celebrate
- INTRODUCTION: I can't believe we've put out 200 newsletters
- TOP STORY: Windows 7 Starter Edition limits netbook designs
- KNOWN ISSUES: Problems confirmed with Vista Service Pack 2
- WACKY WEB WEEK: Here's looking at you, Steven Seagal
- LANGALIST PLUS: Yes or no to firewall request to act as server?
- BEST SOFTWARE: Why you need to validate your downloads
- INSIDER TRICKS: Stop your ISP from tracking your Net usage
It's our 200th issue! Get our bonus to celebrate
We’ve published 200 e-mail newsletters, and we’re not slowing down. To celebrate, we’re giving away a revised edition of Spam-Proof Your E-Mail Address, 3rd Edition. My 32-page PDF e-book explains tricks anyone can use to reduce 97% of the spam that an e-mail address would otherwise attract. The e-book sells for $9.95, but all subscribers can download it completely free, now through July 1, as part of our festivities. To get yours, simply use the link below, update your preferences page with current information, and a download page will appear. Enjoy! —Brian Livingston, editorial director
All subscribers: Set your preferences and download your bonus
I can't believe we've put out 200 newsletters
 By Brian Livingston
By Brian Livingston
Numerous Windows geeks and I have brought you a lot of secrets since I first started publishing an e-mail newsletter called “Brian’s Buzz on Windows” back in February 2003.
After switching to, ahem, a better name (Windows Secrets) — and merging the old newsletter with Woody Leonhard’s in 2004, Fred Langa’s in 2006, and Gizmo Richards’s in 2008 — we’ve put out 200 newsletters, and now we’re celebrating by giving away for free my $9.95 antispam e-book, newly revised.
 Actually, “revised” is stretching it. Spam-Proof Your E-Mail Address, 3rd Edition (photo, left) has been tweaked to bring some references up-to-date and add a new color cover. But there’s just a single important change to the book’s recommendations: one very useful free service bounced around among Web sites, and the service’s new name and URL needed to be edited in throughout.
Actually, “revised” is stretching it. Spam-Proof Your E-Mail Address, 3rd Edition (photo, left) has been tweaked to bring some references up-to-date and add a new color cover. But there’s just a single important change to the book’s recommendations: one very useful free service bounced around among Web sites, and the service’s new name and URL needed to be edited in throughout.
As most Windows Secrets readers know by now, spammers use “harvester bots” to scrape e-mail addresses from Web sites. My e-book, based on studies by nonprofit research organizations, shows you how easy it is to protect your e-mail address inside images and encoded scripts whenever you really need to post your contact information.
The most useful free service I know of for encoding e-mail addresses into Web-friendly (but not harvester-friendly) scripts is Hivelogic’s Enkoder Form. I want all readers to have Enkoder’s new URL:
http://hivelogic.com/enkoder/form
From now through July 1, every Windows Secrets subscriber can download my revised e-book for free. To get yours, simply use the following link to visit your preferences page, make sure the information there is up-to-date, and a download link will subsequently appear:
All subscribers: Set your preferences and download your bonus
Thanks for your support — we promise to keep digging up more secrets for you in the years to come.
MS uses patch channel to install Firefox add-on
It’s been widely blogged that Microsoft can silently add an extension to Firefox when users install .NET Framework 3.5 Service Pack 1 and certain other updates. Readers asked us about this last week because of a May 29 article by Brian Krebs of the Washington Post.
I enjoy Krebs’s writing, but in this case he was apologizing for telling his readers earlier this year to install the .NET service pack. He didn’t realize until later that Microsoft’s Assistant 1.0 extension exposes Firefox to any .NET security holes that may be discovered. Even worse, Microsoft wrote the add-in in such a way that its Uninstall button was grayed out and unusable in Firefox.
WS contributing editor Susan Bradley warned our paying subscribers on Feb. 5 and Feb. 12 not to install .NET 3.5 SP1 (and explained, if need be, how to uninstall it). I tip my hat to her excellent advice.
No holes currently affect the latest .NET software, according to Secunia.com’s .NET Framework 3.x advisory and Assistant 1.x advisory. But the security firm published in 2006, 2007, and 2008 four security warnings about flaws in the earlier .NET Framework 2.x. The most severe hole was rated “highly critical.” A weakness that’s currently undiscovered in .NET Framework 3.x might be exploited in the future.
The extension that MS adds to Firefox implements a technology called ClickOnce. It allows .NET apps to be downloaded and executed within browsers other than Internet Explorer. Unfortunately, this technology can also allow hacked Web sites to infect PCs.
Many Windows Secrets readers use Firefox because it suffers from fewer security holes than IE — and most people don’t need .NET features — so I’m publishing in my free column today the following steps to remove Assistant 1.0 from Firefox:
Step 1. Check whether the .NET Framework Assistant is installed. You may or may not have Assistant 1.0, even if you installed .NET Framework 3.5 SP1, so check this first. In Firefox, pull down the Tools menu and select Add-ons. In the Add-ons dialog box that appears (as shown in Figure 1), if you don’t see .NET Framework Assistant, the add-on is not installed. In that case, you don’t need to do anything further (except close the dialog box).
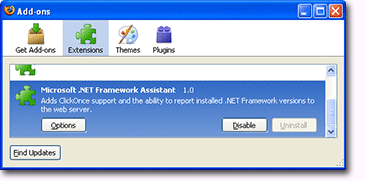
Figure 1. The Uninstall button is grayed out and unusable due to the way Microsoft implemented the original version of Assistant 1.0.
Step 2. Remove or disable the add-on. If you do find the extension, I recommend that you remove it to reduce your vulnerability to possible security flaws. Choose one of the options shown below.
• Best option: Install the Microsoft fix. On May 6, with little publicity, Microsoft posted an update for .NET Framework 3.5 SP1. Installing this update enables Firefox’s Uninstall button for the add-on. To install the official update, visit Microsoft’s download page.
• Another option: Temporarily disable the extension. Using the Add-ons dialog box to disable the extension prevents it from running and protects Firefox from potential security flaws. You might disable the extension instead of uninstalling it if your company insists that you use Firefox to run a .NET app, but you don’t wish to be vulnerable when visiting random Web sites. To disable Assistant 1.0 (or any Firefox extension), pull down Firefox’s Tools menu and select Add-ons. In the Add-ons dialog box that appears, select the unwanted extension and click the Disable button. Close the dialog box.
• Not recommended: Edit the Registry. Before Microsoft’s official patch was released, several sites published a procedure to manually delete entries from the Windows Registry to disable the Firefox extension. I don’t recommend this, because it’s easier and safer to use the options shown above. But if you need the full details, .NET Framework product unit manager Brad Abrams posted the Registry procedure in an MSDN blog entry.
Step 3. Install the third-party extension FFClickOnce, but only if necessary. If you really need ClickOnce functionality in Firefox, consider installing FFClickOnce, a Mozilla-approved extension developed by James Dobson. This third-party extension poses some of the same risks as Microsoft’s add-on. But at least Dobson’s extension prevents downloaded apps from running without first making the user click OK twice. For more info, see Dobson’s SoftwarePunk site and the extension’s Mozilla Add-ons page.
That’s it. More information on .NET problems — and what to install and not install — will appear in future columns by Susan and our other contributors.
Write 50 words and enter to win 1,000 pages
From April 16 to May 6, Windows Secrets offered subscribers an exclusive bonus: a free download of “The Final Chapter,” the thrilling conclusion to Stealing the Network, a book that hadn’t yet shipped. The new hardcover volume is a collection of four previous books describing fictional high-tech security capers.
 Now its publisher, Syngress (an imprint of Elsevier), is promising to send copies of the 1,000-page book — complete with a DVD of author interviews — free to 10 lucky Windows Secrets readers.
Now its publisher, Syngress (an imprint of Elsevier), is promising to send copies of the 1,000-page book — complete with a DVD of author interviews — free to 10 lucky Windows Secrets readers.
If you were one of the thousands who downloaded “The Final Chapter” and you’d like the whole book for free, e-mail a 50-word review of the chapter to info (at) syngress.com. The publisher will display some of the reviews on its site and select 10 winners at random to receive the hardcover collector’s edition. (By entering the contest, you agree to allow Syngress to e-mail you.)
If you’d simply like to buy the collection, Syngress is also offering Windows Secrets readers a 20% discount — a U.S. $18 savings off the $90 list price. Enter the promotional code secrets at ElsevierDirect.com. (At the site, you may select one of nine fulfillment centers around the world.) Or use the company’s special Stealing the Network link, and the promotional code will be entered for you. Offer expires July 15, 2009.
Here’s an even-better price break: anyone can get approximately 37% off the list price — a $33 savings — at Amazon.com. More info: United States / Canada / Elsewhere.
Brian Livingston is editorial director of WindowsSecrets.com and co-author of Windows Vista Secrets and 10 other books.
Windows 7 Starter Edition limits netbook designs
 By Woody Leonhard
By Woody Leonhard
Last week, Microsoft dropped its plan to enforce a three-concurrent-app limit on Windows 7 Starter Edition — the version of the new OS that will be preinstalled only on small PCs, such as netbooks.
Microsoft is still expected, however, to restrict netbook hardware configurations that are eligible for Starter Edition pricing, which means your choices for cheap netbooks may be hobbled — at least in the near term.
When Microsoft first unveiled the various versions of Windows 7 in February, the Windows Team blog explained the editions as follows:
- “Windows 7 Starter: Something that our OEM partners asked for is to have an offering for folks that will do very limited things with their PCs and for PCs with limited hardware capabilities. Windows 7 Starter allows only up to three applications to run at once. This is something that will be offered only through OEM partners.”
Windows 7 Release Candidate spelunkers soon discovered that Starter Edition differs from Home Premium in a number of key ways: there’s no Aero Glass, no Media Center, no DVD burning or playback, no Snipping Tool or Sticky Notes, and no Fast User Switching, among other restrictions.
Heaven knows why, but Starter Edition users can’t even change the desktop background (wallpaper).
| UPDATE 2009-11-19: In the Nov. 19 Top Story, Woody Leonhard explains how to change the desktop wallpaper in Windows 7 Starter Edition for netbooks. |
In addition — as promised on the Windows Team blog — the Release Candidate Starter Edition was going to limit you to a maximum of three applications running simultaneously.
That three-app restriction went over like a lead-filled balloon in a microburst.
Windows 7 Starter Edition’s planned three-concurrent-app limit drew brickbats from many corners. In practice, the three-app restriction didn’t really mean much. Many programs didn’t count toward the limit of three. Some apps — such as installers — counted against the limit but really shouldn’t have.
Microsoft never did articulate in simple, declarative sentences precisely which programs were included in the three-application limit. Ed Bott has a thorough accounting of the vagaries of the three-app rule on his ZDNet blog.
In the end, common sense ruled, and Microsoft dropped the three-simultaneous-app limit, as the Windows Team blog described on May 29. Hooray for this ounce of sanity!
SE is ultra-cheap, but netbooks don’t need it
Windows 7 embodies Microsoft’s Great Hope to lock up the netbook software market. With Linux nipping at its heels, Microsoft desperately needs a cheap, hobbled version of Windows 7 to nail down the lowest-end PC models.
From a marketing point of view, Microsoft is caught between a rock and a hard place. The ‘Softies have to endow Starter Edition with enough glitz to get you to buy it preinstalled on netbooks, but at the same time the company wants to leave a bunch of feature carrots dangling on a software stick to get you to pay more for Windows 7 Home Premium, Business, or Ultimate.
Don’t be fooled: Windows 7 Home Premium works very well on most netbooks — the machines don’t need Starter Edition. I’ve been running Windows 7 Ultimate on an Asus Eee PC 1000H since the earliest days of the beta, and Win7 works great.
Despite what you may have read, Microsoft didn’t devise Starter Edition to run on smaller, less-well-endowed computers. Rather, the company needed something cheaper than Home Premium to sell to the ultra-low-cost crowd. Keep that fact in mind while you sift through the marketing hype.
Win7 Starter Edition’s hardware restrictions
Microsoft offers PC manufacturers a price break on copies of Windows XP that are preinstalled on netbooks. The company doesn’t offer any breaks at all on copies of Windows XP that are sold on more-powerful laptops — in fact, those larger notebook PCs always include a license for Windows Vista, even if they ship with Windows XP.
Although the details are highly confidential, it appears that Microsoft will enforce a similar restriction on sales of Windows 7 Starter Edition. According to the TechARP site, Microsoft will sell copies of Starter Edition to PC manufacturers only for installation on netbooks with limited processing ability. That’s defined as those using a single-core processor, running slower than 2GHz, consuming fewer than 15 watts, having less than 1GB of system memory, and using screens 10.2 inches or smaller.
If you work for a hardware manufacturer that’s gearing up to produce large numbers of netbooks with 11-inch screens for sale during the 2009 holiday season, your summer vacation plans may have just gone out the window.
An April 20 Wall Street Journal article (paid sub required) states: “People familiar with the matter say Microsoft takes in less than $15 per netbook for Windows XP once marketing rebates are taken into account — far less than the estimated $50 to $60 the company receives for PCs running Windows Vista.”
If that same differential of $35 to $45 holds true for Windows 7 Starter and Home Premium, you can bet netbook manufacturers are going to keep their low-cost offerings within Microsoft’s limits.
Microsoft’s Win7 Starter Edition requirements may change at any point. But as long as they’re in effect, Microsoft has forced hardware manufacturers to tone down their products running the low-cost version of the OS.
That doesn’t prevent netbook manufacturers from making bigger screens, using faster chips, or offering more system memory. However, those who offer better netbook configurations won’t be able to include Starter Edition as part of the package. Instead, they’ll have to ship their netbooks with Linux or a different — considerably more-expensive — edition of Windows 7.
Controversies swirl around Win7 Starter Edition
Some people see conspiracies behind every Microsoft move, and the Starter Edition hardware throttling is no exception. Certainly, by restricting Starter Edition to netbooks with screens smaller than 10.2 inches, companies planning to build netbooks with larger screens will face higher prices and, probably, lower margins.
As explained in a DigiTimes article (paid sub required), some people see the netbook hardware upgrades as a competitive advantage for Intel over up-and-coming chip makers such as Via. You can insert your favorite Intel-Microsoft conspiracy theory here.
In his InformationWeek blog, Dave Methvin — who’s been covering Windows as long as I have, meaning since the last Ice Age — has this to say about Microsoft’s Starter Edition hardware limitations:
- “Microsoft crosses the line by attempting to contractually limit OEMs on the hardware that Starter can use. That shouldn’t be Microsoft’s decision. If Starter is good enough for netbooks, then it should be available to OEMs for whatever hardware that can run Windows 7.”
Good business? Stiffed customers? Predatory monopolistic practices?
One thing’s for sure: we’re in for an interesting ride with Starter Edition. Stay tuned!
Woody Leonhard‘s latest books — Windows Vista All-In-One Desk Reference For Dummies and Windows Vista Timesaving Techniques For Dummies — explore what you need to know about Vista in a way that won’t put you to sleep. He and Ed Bott also wrote the encyclopedic Special Edition Using Office 2007.
Problems confirmed with Vista Service Pack 2
 By Dennis O’Reilly
By Dennis O’Reilly
Some early adopters have encountered installation glitches and software conflicts when attempting to apply Service Pack 2 for Windows Vista.
As with nearly all service packs, there’s no rush to install Vista SP2 — and when you do apply it, be ready with a full system backup, just in case.
In the May 28 Patch Watch column (paid content), Susan Bradley recommended that you hold off on installing Vista SP2. Microsoft hasn’t yet begun to push out the service pack via its Automatic Updates service, but some people who chose to apply SP2 now wish they’d waited. Among them is Ted Myers:
- “I have a 64-bit Sony Vaio with Vista Home Premium. I have it up-to-date with all patches. (I do have the Genuine tool installed, which has not caused problems to date.) Vista Service Pack 2 was downloaded and installed.
“Perhaps the problem was due to an AV program still running — or something else — but after the PC rebooted and began loading replacement files in DOS, it got hung up on 5367 of 81,000+ files. This happened repeatedly. My PC would no longer boot. It attempted the update several times, hanging up on the same file. This was a file involved with AMD security, which is strange since I have an Intel-based system.
“I was finally able to run a low-level System Restore, and System Restore did indeed do what it was supposed to do. A PC novice would be totally lost going through the hoops I went through to restore my system. Today I will make an up-to-date ghost copy of my hard drive — my backup is a few months old. I run a part-time business on this PC. My backup of my business record was a month old — what a mistake that was! It’s now up-to-date as well.
“Please inform your subscribers to beware of Vista Service Pack 2. Both of my PCs have Vista — the second is the Ultimate version (desktop). I am holding off on installing Service Pack 2 on both until you folks tell me it’s safe to try again.”
As Susan reminds us repeatedly, you rarely need to hurry to install a service pack, which is usually nothing more than a collection of previous updates. Most importantly, always back up your system before applying a service pack and be ready to roll back your PC if you encounter any post-update problems.
IE 8 causes Microsoft Money print failure
Susan’s column also described some of the glitches occurring with Internet Explorer 8, including conflicts with third-party firewalls and an inability to print information from Web pages. Brad Clarkson discovered a different IE 8 glitch when he attempted to use another Microsoft application:
- “In addition to breaking Web sites, IE 8 also breaks other Microsoft products. The Home and Business editions of Microsoft Money will no longer print business invoices. There are no error messages. It doesn’t matter what printer is used. The printing process will appear to complete normally. However, the page the printer spits out will be blank.
“I can confirm the problem exists in the 2007 version [of Microsoft Money]. I understand versions from 2003 to 2007 are affected. After Googling the problem, {I find] the only current fix seems to be to roll back to IE 7.”
If you run into problems with IE 8, Microsoft describes in Knowledge Base article 957700 how to uninstall the new version and reinstall IE 7.
Reader sends kudos for informative newsletter
When the PC industry was young, dozens of print magazines sprang up to help us make sense of these convoluted machines. The medium may have changed, but the goal remains the same, as a reader named Bud points out:
- “Folks, you’ve outdone yourself again! An excellent and very informative newsletter. Having a snail-mail subscription to a PC magazine that has as part of its marque ‘In Plain English,’ today’s commentaries — as always — have done the same.
“The [May 28] article about Microsoft’s WGA and the recommendations of downloading and using autoruns.exe helped me to understand the functions and use of that utility, especially since I already had it in my utilities toolbox but didn’t fully understand its use. Today, after reading that article, I ran the software and voilà, it all made sense and was much easier to comprehend and use.
“The article on the various third-party update software is another great example of teaching all of us ‘non-geek’ PC users. Since I’ve been using and learning about PCs and their good, bad, and ugly qualities, you folks have gone a long way in helping me out of a long-time period of being a novice. Many, many thanks!”
Thank you for reading, Bud. That’s why we’re here.
| Readers Ted, Brad, and Bud will each receive a gift certificate for a book, CD, or DVD of their choice for sending tips we printed. Send us your tips via the Windows Secrets contact page. |
The Known Issues column brings you readers’ comments on our recent articles. Dennis O’Reilly is technical editor of WindowsSecrets.com.
Here's looking at you, Steven Seagal
 |
By Katy Abby
Over a few short years, Andy Samberg has risen to fame as Saturday Night Live’s veritable King of Digital Shorts. Songs such as “Lazy Sunday,” “I’m on a Boat,” and “Like a Boss” — as well as some more-crassly-named shorts that I’ll refrain from repeating here — have become instant classics, dominating YouTube and breathing new life into the SNL franchise. Before you trek off to the theater to ogle the latest summer action flick, take a look at the newest addition to Andy’s repertoire. This explosive short, which originally aired on Sunday’s MTV Movie Awards, features Samberg in cahoots with Will Ferrell and television prodigy J.J. Abrams. Play the video |
Yes or no to firewall request to act as server?
 |
By Fred Langa
It’s not always easy to tell whether a program really needs the rights and privileges of a server. When your firewall alerts you that an application wants to act as a server, you have two simple ways to determine the correct response. |
Find out why a program wants server status
Maurice Carson ran into one of those all-too-common, half-explained firewall queries:
- “What about programs wanting to ‘act as a server’? I have ZoneAlarm as a firewall, and many programs want to act as a server. Why?”
First, let’s define the jargon. A “server” is a program that responds to a request from another program to open a connection, send or receive a file or data, launch a program, or perform some other task. A “client” is a program that makes such a request.
Technically, client and server programs can reside on the same machine. Security risks come into play when the client and server are on separate networked machines. Some programs are both clients and servers, while others — known as “standalone applications” — are neither.
ZoneAlarm and other security tools are especially suspicious of any program that wants to act as a server, because letting other PCs request data or services from your system is obviously risky. The firewall has no way of knowing whether the request to act as a server is legitimate, so it punts the decision to a human — you.
The simple, empirical way to respond to a program’s request to act as a server is to choose the “No” or “Deny” option (or whatever verbiage your security tool uses) every time. Denying the request is always safest; you’ll never reduce your security by blocking a program’s request for server rights.
Saying no may cause some necessary features or functions of the program to stop working, however. In these cases, the application really does need to act as a server. You can then adjust your security tool’s settings accordingly.
The “default to No” method is crude but effective. I prefer to figure out why a particular program might need to respond to a client’s request for a file or other resource. For example, it’s pretty clear that the Skype voice-over-IP (VoIP) tool needs to act as a server in order to respond to incoming phone calls. Likewise, if you use a file-sharing app that makes your PC part of a network for receiving and redistributing files, acting as a server is part of the deal.
In cases like these, you’d let the software in question act as a server. But keep in mind that it’s always more dangerous to allow server requests. Doing so opens a path into your PC for outside service requests. Of course, this may be necessary for the software to work as intended.
If you don’t recognize the would-be server program or don’t understand why it’s making a request to act as a server, do a little research. If possible, query a search engine with the exact wording of the relevant part of your security tool’s message, and include the name of the program making the server request. Odds are many other people have asked about the same program and the answer is just a few clicks away.
If you can’t find an answer online, fall back to the empirical method. Or, as I’d put it more simply: “When in doubt, lock it out, but if it breaks, raise the gates!”
Halting an infinite software-install loop
Sam Miller’s PC is suffering from a software installation that just won’t quit:
- “I updated my display driver in Vista a week ago, and every time I boot, it installs again. How do I get it to stop? I know I’ve seen the answer to this in your newsletter, but I can’t find it now.”
A broken install can trap you in a loop that never runs to completion. What a frustrating way to start your workday! And, as you discovered, this is especially prone to happen with third-party software — most especially with driver software.
Microsoft Knowledge Base article 555175 aggregates 12 very thorough strategies for solving broken-installation woes. The solutions are rank-ordered, so the first fix listed is the most likely to succeed in the largest number of cases. If it doesn’t work, try fix #2, and so on down the list.
You’re right that Windows Secrets has covered the topic of broken software installers before. Because there are many different factors that can lead to broken installs, the information has previously appeared associated with each specific problem.
Here are some of the articles from the Windows Secrets archive that you may find helpful:
- Feb. 26, 2009, LangaList Plus: “A fix for Windows’ broken installer utility”
- Nov. 13, 2008, LangaList Plus: “Incomplete install leaves ghost in the machine”
- April 26, 2007, Perimeter Scan: “iTunes installer fails to clean up”
- “I have a new notebook with a 60GB solid-state disk (SSD). I traditionally have used a number of PC performance tools (PC Pitstop, Diskeeper 2008, etc.) to keep my PCs healthy, and with good success. But with an SSD, does it make sense to use a disk-defragmentation tool that you would normally use on a standard magnetic hard disk?”
- “If you have a system that’s a couple of years old, Windows Search 4 will cost you extensive wear on your drives! I tried it and my drives were running constantly. Do I need this extra wear and tear? I personally found Search 4 more complicated than the search that came with XP.”
Do solid-state disks need to be defragged?
Allan Hamilton has a new kind of solid-state hard drive — all memory chips, no moving parts — and wonders whether the old rule of thumb about defragging still applies:
Great question, Allan, although the answer may surprise you!
First, let’s review how disk drives become fragmented. When you save a file, pieces of the file may be scattered among various sectors of the drive. File fragmentation is bad for a standard, mechanical drive because the drive heads require more frequent repositioning to read or write the disjointed file fragments contained on the spinning platter.
Each extra mechanical motion consumes a little time, so the more the heads have to jump around, the more time it takes the drive to retrieve the file. The extra motion also adds wear and generates more noise and heat.
Defragging reassembles the file fragments into contiguous wholes, which speeds the disk’s throughput and reduces wear and tear on the drive’s mechanical parts. Defragging is generally a good thing, which is why all versions of Windows for the last decade or so have shipped with a defragger.
However, an SSD is totally electronic and has no heads to mechanically reposition. File fragments still take a measurable amount of time to reassemble, but solid-state memory can operate internally at nanosecond (billionths of a second) speeds, which is six orders of magnitude faster than the millisecond (thousandths of a second) speeds of mechanical drives. Even when you add in controller delays and other factors, SSDs generally operate at sub-millisecond speeds overall.
Because of this, most of the benefits of defragging shrink to insignificance on a solid-state device. Yes, retrieving a fragmented file from solid-state memory is still slower than opening a contiguous file, but you’ll probably never notice the difference.
Some kinds of solid-state memory “cells” have finite lives and eventually wear out after some number of read/write cycles. Frequently defragging a solid-state device might reduce its useful life without delivering any perceptible benefit.
If you run Windows on a system with solid-state drives, I suggest you skip defragging, apart from a full defrag done as part of your quarterly or semiannual system housekeeping.
Why is Windows Search 4 so sl-o-o-o-o-w?
A reader with the nom de Web of Bravehart wonders why Windows Search 4 is abusing his hard drive:
Search 4 can be problematic when retrofitted to a machine with many files. The initial setup and maintenance of the index is extremely drive-intensive because Search will initially look at just about everything on your hard drive. If the drive’s also a bottleneck due to heavy fragmentation (see the item above), things can get very slow.
You can speed up indexing by keeping your hard drive defragged. This allows the drive to deliver data to the indexing engine as swiftly as possible. You can help the initial index-building and subsequent indexing by preventing other disk activity while the indexing is going on.
One trick I’ve used is to exit or disable all other software and then disable or unplug the Internet connection so that nothing will try to go online — say, for updates — while the index is building. In other words, to speed indexing, make your PC a single-tasking device working solely to build and stabilize the index. Let the task complete overnight with nothing else running.
Also, many of Search 4’s functions are configurable. For example, you can limit the indexing to only certain types of files, which speeds indexing and reduces the size of the final index file. The Windows Search 4.0 Troubleshooting Guide on Microsoft’s TechNet site walks you through many of Search 4’s options.
Keep in mind that on XP, Search 4 isn’t mandatory. If the original XP search works better on your PC, then by all means, stick with it!
Fred Langa is editor-at-large of the Windows Secrets Newsletter. He was formerly editor of Byte Magazine (1987–91), editorial director of CMP Media (1991–97), and editor of the LangaList e-mail newsletter from its origin in 1997 until its merger with Windows Secrets in November 2006.
Why you need to validate your downloads
 |
By Ian “Gizmo” Richards
One of the most common ways of getting a malware infection is by downloading and installing a seemingly legitimate program that has actually been tampered with. You can seriously reduce the risk of this kind of infection by using a free checksum program that makes it easy to validate files before you open them. |
Using checksums to validate downloadable files
The idea of using a checksum calculated from a set of data to validate the accuracy of that data is not restricted to file downloading; it is commonplace. Take, for example, your credit card.
Whenever you give someone your credit card number, it’s important that they get it exactly right. However, there’s always a chance that you or the person recording your card number will make a mistake. To guard against these transcription errors, credit card companies have built in a simple checking mechanism to ensure the validity of the card number.
The last number on your credit card is not part of your account number but is a check digit. If you apply a standard formula to all the other numbers on the card, you should end up with a number corresponding to the check digit. If you don’t, something is wrong.
An example of such a formula would be to add up all the numbers on the card and then compare the last digit of the result to the check digit. So if your numbers added up to 72, the check digit should be 2.
In practice, the formula used for credit cards — called the Luhn algorithm — is a little more complex, but the idea is the same.
The Luhn algorithm is just one example of a checksum algorithm. However, it shares a weakness with other simple checksum methods: it can certainly detect incorrect digits but can’t detect a lot of other common errors, such as the simple transposition of two digits. To do that, a more complex method is needed.
The Cyclic Redundancy Code (CRC) technique is the next step up in error detection. CRC can detect not only incorrect digits but also digits out of sequence. There are many CRC algorithms, but the most common is CRC32.
Even CRC32 has a weakness: while it’s excellent at detecting accidental errors, it’s not robust against deliberate falsification. In other words, it’s possible for a knowledgeable attacker to modify the data yet ensure that it generates the correct checksum.
To guard against this, we need even more sophisticated methods. These more advanced techniques are usually called cryptographic hashes rather than checksums.
The most common of these cryptographic hashes is Message Digest number 5 (MD5), which is capable of producing a 128-bit fingerprint. MD5 is more difficult to falsify by reverse engineering than CRC32.
However, even MD5 is no longer considered fully secure. A smart hacker can tamper with the file in such a way that it still gives a valid checksum. MD5 is good enough for casual file verification purposes, but there’s a strong move to more-secure hashes, such as the Secure Hash Algorithm (SHA-1) and RACE Integrity Primitives Evaluation Message Digest (RIPEMD, which has evolved into RIPEMD-160 and other, more-recent variants). RACE stands for “R&D in Advanced Communications Technologies in Europe.” Ah, we techies do love our embedded acronyms!
Whatever the technique, the idea is still much the same as the check digit on a credit card. You run a program that calculates a number — the hash — from the data and compare this to the correct hash quoted for that data by the publisher or download site. If the two don’t agree, you have a problem.
Why hashes matter when you download a file
Just as it’s important to get your credit card number right when making a transaction, you need to validate the programs you download before opening them. And believe me, downloads can get corrupted.
By far the most common cause is an error in transmission, usually as a result of a download that didn’t fully complete. However, even files that appear to download completely can still be corrupted accidentally.
But corruption can also be deliberate. A hacker may have modified the original file and secretly inserted a Trojan or other malware program. This is not uncommon for files distributed via BitTorrent or other file-sharing services. (I wrote in my Jan. 15 column that 39 out of 61 illegal programs I tested after downloading them using BitTorrent were infected.)
The use of an MD5, SHA-1, or other hash will detect corruption, whether accidental or deliberate. That’s why you should validate all downloads against the checksums or hashes provided by the program distributor. Unfortunately, not all download sites provide these hashes, but if they do, be sure to use them.
Thankfully, there are some excellent free programs that simplify the task of calculating hashes for your downloaded files. I looked at seven different free checksum and hashing utilities and describe in today’s column the three I consider the best for typical PC users. If you want to calculate only the common hashes, such as MD5 or SHA-1, any of these programs will do the job — though they differ in usage and the types of hashes they calculate.
#1: WINHASHER 1.03
File checker runs from .exe without installer
If you download files only occasionally, you may be attracted to WinHasher 1.03, mainly because the program runs directly from the .exe file without installing. However, WinHasher does require the Microsoft .NET Framework 2.0.
To use WinHasher, you must first select the hash method you want from a list of eight different hashing algorithms, several of which have iterations of their own. (See Figure 1.) Then you select the file you want to analyze. WinHasher calculates the hash and can also compare it to the hash published by the download site. WinHasher also generates or validates hash files, if required.
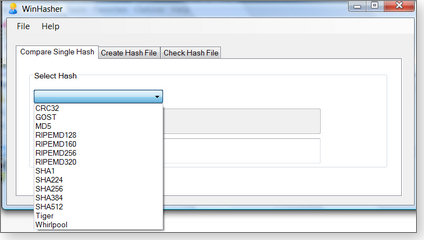
Figure 1. The WinHasher file validator supports eight different hashing algorithms.
The most-recent version, WinHasher 1.4, includes more features, such as the ability to create hashes from the right-click (context) menu and to generate hashes from text. However, this version requires installation.
Personally, I prefer the earlier version because it’s portable. If you’re fine with a program that needs to be installed, however, I suggest you look at either FileTweak or HashCalc, both of which are described below.
Download version 1.03 (334KB) from Download.com or version 1.4 (374KB) from the vendor’s site.
#2: FEBOOTI FILETWEAK HASH & CRC 2.0
Check downloaded files via Properties dialog
The name “Febooti FileTweak Hash & CRC” might be a mouthful, but this product is delightfully simple to use. Once installed, the program adds a Hash & CRC tab to the file’s Properties dialog — the one that opens when you right-click the file and choose Properties.
FileTweak handles all the formats shown in Figure 2, plus RIPEMD-128, -256, and -320. However, the program can’t compare calculated hashes with published values; you’ll need to do that manually.
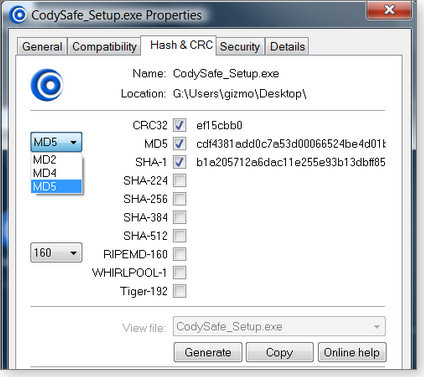
Figure 2. FileTweak adds a file-checker option to the file’s Properties dialog in Windows.
Download FileTweak from the vendor’s site (264KB).
#3: SLAVASOFT HASHCALC 2.02
The drag-and-drop way to check your downloads
SlavaSoft’s HashCalc runs as a standalone application, so once it’s running, you simply select the file you want to check and the hashing method to use, and then click Calculate. Alternatively, you can drag and drop the file into the program window. HashCalc handles 13 different checksum and hashing algorithms, including the special method used by the eDonkey/eMule file-sharing services.

Figure 3. HashCalc supports keyed-Hash Message Authentication Code hashes for an added level of security.
This program processes not only files but also text or hex strings. It’s also the only program of the three described here that can process keyed-Hash Message Authentication Code (HMAC) hashes. HMAC combines a hash with a key and is typically used in high-security environments.
HashCalc is available from the SlavaSoft site (468KB).
So which is my favorite download verifier? I like WinHasher 1.03 because it’s portable and is the only product in this group that checks the generated hash against the published hash. However, the choice is ultimately a matter of personal preference. I suggest you try all three, as they’re tiny programs that can be downloaded in a few seconds.
But please do get yourself a hash-checking program. There are simply too many dodgy downloads floating around the Internet to risk accidentally downloading a file that has been tampered with. Make sure, though, to get your published hashes or checksums from the original source of the program rather than get some untrustworthy value obtained from a file-sharing service.
Ian “Gizmo” Richards is senior editor of the Windows Secrets Newsletter. He was formerly editor of the Support Alert Newsletter, which merged with Windows Secrets in July 2008.
Stop your ISP from tracking your Net usage
 By Becky Waring
By Becky Waring
Alarmingly, ISPs now have the tools to log, analyze, and respond to every bit of data you send and receive.
Proxy services can’t prevent ISPs from snooping, but encryption can — although you need to know about some significant limitations.
Confidential business data may need protection
Last year, Charter Communications, a major U.S.-based Internet service provider, started using the data it was collecting regarding its clients’ online behavior in order to target specific ads to users. Rumblings from Congress helped kill that plan, and NebuAd — the company Charter was working with on the project — recently closed its doors.
While both Congress and the FCC — as described by the Cable360.net site — are considering Internet privacy regulations, no laws yet exist in the U.S. to adequately protect against similar schemes.
Meanwhile, another targeted-advertising firm named Phorm is doing good business in the U.K. and claims to have been assured by the British government that its service is legal.
According to a recent Associated Press story, Phorm has “struck partnerships with three access providers reaching 70% of Britain’s broadband market — BT Group PLC, Virgin Media Inc., and Carphone Warehouse Group PLC’s TalkTalk … BT has completed its trial of Phorm’s ad-targeting service and expects to deploy it this year.” Phorm claims to ask for the consumer’s explicit approval to receive targeted ads.
While U.S. service providers don’t (yet) seem to be actively selling information about your Internet usage, there are no guarantees that clones of NebuAd won’t surface. The profit potential for ISPs in this entirely new revenue stream is just too huge for them to ignore.
According to a NoDPI.org report, other firms seeking to use ISP data for marketing purposes include KindSight, Experian Hitwise, FrontPorch, and Adzilla.
Even if Congress ends up banning deals with such targeted-advertising firms for privacy reasons, many providers are now using the same deep-packet inspection (DPI) tools for other purposes that may infringe on your Internet usage — such as bandwidth throttling and capping.
For example, an Ars Technica article states that in Canada “just about every major ISP in the country has admitted to regulators that it uses DPI gear to throttle traffic, often singling out P2P protocols.”
There are also no guarantees that governments themselves will not seek to use DPI in surveillance or censorship efforts. At worst, this can lead to human-rights abuses — already a reality in many countries, as reported by the OpenNet Initiative and NoDPI.org. At best, there’s yet another database floating around with your information in it, waiting to be compromised.
Many people have perfectly legal needs for confidentiality, including those who’ve signed nondisclosure pacts or are working on undisclosed mergers and acquisitions. The only way to truly ensure your online privacy in these and other such situations is to take matters into your own hands.
Proxy servers provide a false sense of security
Given the very real use of deep-packet inspection by ISPs, what can law-abiding Internet users do to protect themselves against possible snooping of their e-mail and Web-surfing habits?
Many people believe that using a proxy server is enough to keep their activities private. Corporations, schools, and libraries often use proxy servers to filter content and provide security. In reality, proxy servers alone do nothing to prevent ISPs from monitoring your data transmissions.
Proxy servers work by putting an intermediate IP address — a “proxy” — between you and the sites you visit. If you do all your surfing through a proxy, your URL requests go through the proxy server before being passed to the sites you visit.
This hides your IP address from the target Web site, which sees only the proxy’s address. This means sites that record IP addresses won’t be able to identify you or pass on your address to others, including government agencies or the Recording Industry Association of America (RIAA), which is always on the prowl for what it considers copyright infringement.
Conversely, proxy servers hide the URL of the target site from a governmental, corporate, or school firewall. This lets you surf to sites that the organization may be blocking, such as Facebook. (It’s been widely reported that China blocked access to YouTube, Flickr, Twitter, Hotmail, and numerous other sites beginning June 2, two days before the 20th anniversary of the Tiananmen Square massacre, as described by the Huffington Post.)
When you use a proxy server, all the organization’s firewall sees is the URL of the proxy. This is why proxy servers are frequently used by file sharers. However, eluding the RIAA is not the same thing as protecting your legitimate need for privacy and unfettered Net access.
Even with a proxy server, all your surfing still has to go through your ISP, which can use packet filtering to log that data. For true privacy, the entire data path needs to be protected, not just the upstream portion.
Most proxies are operated by fleeting and anonymous entities: only 25% of the nearly 32,000 proxy servers listed on the Proxy.org site are actually working, and a mere handful are labeled as “recommended.”
Not one of the proxy sites Proxy.org lists is run by a big-name company that the average person would have heard of or would have reason to trust.
The fleeting nature of proxy sites is partly due to necessity, since proxy servers quickly get put on block lists. But the here-today-gone-tomorrow nature of proxies can make them unreliable and somewhat dangerous to use. (You can check out the ever-changing roster of proxy servers at Proxy.org, but note that your security software may flag this site as unsafe.)
Encrypted proxy servers like Proxify.com and the Tor Project can shield your traffic from your ISP. But they don’t encrypt traffic between their servers and your final destination.
Even worse, public proxy servers are attractive fronts for cybercrime. Operators can easily read all traffic passing through their servers, redirect your URL requests to phishing sites, or inject malware into downloads.
The Tor Project itself, which depends on volunteer proxy hosts, warns that “malicious or misconfigured Tor exit nodes can send you the wrong page or even send you embedded Java applets disguised as domains you trust.”
Finally, if the proxy or VPN service keeps logs — although many claim not to — a subpoena or government-agency order could force the service to disclose information about you.
Bottom line: There’s just no way to be sure such services are legitimate, or even that they work at all. File sharers likely won’t care, but anyone who has a legitimate concern about privacy and safety certainly will.
What you can do now to safeguard your online privacy
Given all these caveats, is there any real solution for protecting your Internet activities from prying eyes? For true online privacy, you need to encrypt all your Internet traffic from end to end, making deep-packet inspection tools fail. DPI tools that can crack strong encryption may become a reality in the future, but it’s not going to happen any time soon.
Fortunately, for most people who aren’t named Barack Obama, end-to-end encryption is overkill. If you’re not hiding from law-enforcement agencies or foreign intelligence services, you can get all the protection you need by combining a reliable VPN service — one that prevents ISP data collection and hotspot snooping — with an encryption-enabled e-mail client.
Paid VPN services like the well-known Witopia.net, which provides an encrypted tunnel between you and a VPN server, generally cost a few dollars a month. The services work not only for Web browsing but for all your Internet traffic, including e-mail, chat, and automatic software updates. Once turned on, VPN services work transparently, and the paid services are usually pretty fast. Such networks are especially popular with Wi-Fi hotspot users, since they also protect against wireless snooping.
Gmail and other major webmail services offer encrypted Secure Sockets Layer (SSL) access, which is indicated by the URL prefix https. But like a VPN or encrypted proxy, SSL works only between your computer and the mail server. Data leaving your provider’s servers is unencrypted.
For most people, this level of protection is sufficient. However, very sensitive e-mails and chat sessions require end-to-end protection, such as PGP (Pretty Good Privacy) and other public-key encryption software. In order to read your messages, however, your correspondent will need to use the same software, which can be a hassle.
For occasional use, an easier encryption method is to send a password-protected Word, PDF, or .zip file as an e-mail attachment, then deliver the password to the recipient by a separate channel, such as a phone call or text message.
The Skype VoIP service is encrypted by default, which makes it the best way to chat securely with no added effort. Google, for its part, is currently testing built-in support for PGP in Gmail. This would make end-to-end encryption much easier to use in that service. Look for PGP support as a Gmail Labs topic soon.
If you want or need more privacy than that — well, you probably shouldn’t be using the Internet for sensitive communications at all.
WS contributing editor Becky Waring has worked as a writer and editor for CNET, ZDNet, Technology Review, Upside Magazine, and many other news sources.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Discover the Best AI Tools for Everything
by
Alex5723
4 hours, 34 minutes ago -
Edge Seems To Be Gaining Weight
by
bbearren
6 hours, 53 minutes ago -
Rufus is available from the MSFT Store
by
PL1
15 hours, 32 minutes ago -
Microsoft : Ending USB-C® Port Confusion
by
Alex5723
17 hours, 42 minutes ago -
KB5061768 update for Intel vPro processor
by
drmark
7 minutes ago -
Outlook 365 classic has exhausted all shared resources
by
drmark
15 hours, 53 minutes ago -
My Simple Word 2010 Macro Is Not Working
by
mbennett555
13 hours, 27 minutes ago -
Office gets current release
by
Susan Bradley
16 hours, 5 minutes ago -
FBI: Still Using One of These Old Routers? It’s Vulnerable to Hackers
by
Alex5723
2 days, 6 hours ago -
Windows AI Local Only no NPU required!
by
RetiredGeek
1 day, 14 hours ago -
Stop the OneDrive defaults
by
CWBillow
2 days, 6 hours ago -
Windows 11 Insider Preview build 27868 released to Canary
by
joep517
2 days, 16 hours ago -
X Suspends Encrypted DMs
by
Alex5723
2 days, 19 hours ago -
WSJ : My Robot and Me AI generated movie
by
Alex5723
2 days, 19 hours ago -
Botnet hacks 9,000+ ASUS routers to add persistent SSH backdoor
by
Alex5723
2 days, 20 hours ago -
OpenAI model sabotages shutdown code
by
Cybertooth
2 days, 20 hours ago -
Backup and access old e-mails after company e-mail address is terminated
by
M W Leijendekker
2 days, 8 hours ago -
Enabling Secureboot
by
ITguy
2 days, 15 hours ago -
Windows hosting exposes additional bugs
by
Susan Bradley
3 days, 4 hours ago -
No more rounded corners??
by
CWBillow
3 days ago -
Android 15 and IPV6
by
Win7and10
2 days, 14 hours ago -
KB5058405 might fail to install with recovery error 0xc0000098 in ACPI.sys
by
Susan Bradley
3 days, 16 hours ago -
T-Mobile’s T-Life App has a “Screen Recording Tool” Turned on
by
Alex5723
3 days, 19 hours ago -
Windows 11 Insider Preview Build 26100.4202 (24H2) released to Release Preview
by
joep517
3 days, 14 hours ago -
Windows Update orchestration platform to update all software
by
Alex5723
4 days, 2 hours ago -
May preview updates
by
Susan Bradley
3 days, 14 hours ago -
Microsoft releases KB5061977 Windows 11 24H2, Server 2025 emergency out of band
by
Alex5723
3 days, 5 hours ago -
Just got this pop-up page while browsing
by
Alex5723
3 days, 19 hours ago -
KB5058379 / KB 5061768 Failures
by
crown
3 days, 16 hours ago -
Windows 10 23H2 Good to Update to ?
by
jkitc
2 days, 18 hours ago
Recent blog posts
Key Links
| S | M | T | W | T | F | S |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | 7 |
| 8 | 9 | 10 | 11 | 12 | 13 | 14 |
| 15 | 16 | 17 | 18 | 19 | 20 | 21 |
| 22 | 23 | 24 | 25 | 26 | 27 | 28 |
| 29 | 30 | |||||
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

