
|
There are isolated problems with current patches, but they are well-known and documented on this site. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
You’re being followed! How to block Web tracking
In this issue
- TOP STORY: You're being followed! How to block Web tracking
- WACKY WEB WEEK: Reviewing cosplay at San Diego Comic-Con
- LOUNGE LIFE: Video-editing app lost after OS upgrade
- LANGALIST PLUS: Rooting out a stubborn browser hijacker
- WOODY'S WINDOWS: Going Google (apps), Part 4: Contacts/Calendar
You're being followed! How to block Web tracking
Just because you’re paranoid doesn’t mean you’re not being watched.
When you’re on the Internet, there are good reasons to have that eerie sense of being followed.
By now, most of us know that websites can gather a surprising amount of information about your computer. For example, the page request you send to a site’s server includes detailed information about your browser — not just which browser you’re using, but the exact version, its configuration, and even the screen resolution the browser is running in. Other gathered data includes the page you came from, what document you’re requesting, and — yes, your IP address.
And don’t think you have anonymity just because your service provider gives you a dynamic IP address. At a minimum, visited websites can tell what service provider you’re with and what city or region you are in.
What’s more, any communication with a Web server gives it the opportunity to deposit a cookie on your computer. Benign cookies — small text files downloaded through your browser — simply record information needed to make your Web experience better. That can include sign-in information, where you visited on the site, interface customizations, and the like. Most cookies also keep an identifier for each visitor, so that the next time you connect to a site’s server, it can match you up with its records of previous visits. That way, you won’t have to start from scratch whenever you go to the site.
Less benign cookies can let websites track your movements around the Internet, and they often collect more information than you really want to give.
Typically, the information gleaned by trackers doesn’t include your name and street address. But by putting together all the collected data from page requests and cookies, Web servers can effectively fingerprint individual computers and thus track users across the Internet.
What many users don’t know is the extent of the information now collected. If a webpage contains an advertisement, your browser will often send a request to a third-party ad server to download the advertisement. In addition to telling the ad server what site you’re visiting, the request contains yet another identifier — still not your name, but a number that corresponds to your computer.
And that ad server might deposit its own cookie on your computer.
So far, all this tracking hasn’t identified you by name and address. But online tracking companies will have a considerable amount of information — including, again, your computer’s IP address — about your online activities. On some sites, the result is targeted ads, tailored content, and possibly a Web experience that’s customized specifically for you (or, more precisely, customized for the activity on a specific computer).
For example, one day I searched for “line trimmers” on Google. The next day, I went to the Home Depot site. What was the first thing I saw? An ad for line trimmers — and it was no coincidence. Some users will be happy with that result; others will not. Let a friend or family member browse the Web with your computer, and ads for products you have absolutely no interest in might follow you around the Internet for days or weeks.
Good intelligence analysts might be able to figure out who’s behind a computer by analyzing online activities, but for most users, the real danger comes from joining social-networking sites such as Facebook or Google+. By their nature, social sites encourage you to feed them lots of personal information — including your name and address. The social site, and any organizations with which it shares data, can connect the dots back to a specific individual — as opposed to a specific computer. (And we can assume government agencies are doing the same.)
And you know all those social widgets you find on visited sites? Page requests are sent to those servers as well. If you’ve logged into Facebook in the past month, for example, and you haven’t specifically signed out, the widget can track your presence across all sites that also have the widget. If you want to see how visited websites communicate directly with each other, download the Collusion (see Figure 1) add-on for Firefox and Chrome.
Figure 1. Collusion graphically shows the connections between sites you visit.
Trackers can also use embedded bugs or beacons — typically invisible to users — to get notifications when someone has viewed a site or opened email. And any of the sites you visit might use JavaScript to examine your browsing history.
Browsers offer limited tracking controls
So what can you do to manage or reduce tracking? In this article, we’ll start by looking at the built-in controls available in the three most popular browsers. Unfortunately, though these user-configurable tools provide some protection, you can’t rely on them to fully protect your online identity.
In a following article, I’ll go into third-party add-ons and utilities that provide better protection.
The privacy tools in the major browsers focus primarily on cookie management. To understand how the tools work, it’s important to understand the various types of cookies. Here’s the short explanation:
- Session cookie: When the cookie doesn’t carry an expiration date, it’s usually a session cookie — one that will be deleted when the browser is closed.
- Persistent cookie: Also called a tracking cookie, the persistent cookie will remain on the computer until it reaches its expiration date. These cookies can be accessed by their creators whenever you connect to the creators’ Web servers.
- Secure cookie: If the cookie is set with an HTTPS attribute, it’s sent from the Web server in an encrypted form to prevent cookie theft.
- HTTPOnly cookie: Such cookies can be transmitted only through HTTP or HTTPS requests, which also helps protect them from being stolen.
- Third-party cookie: These cookies come from a source other than the site you’re visiting. Webpage ads, for example, typically deliver their own, third-party cookies.
- Supercookie: Tracking technologies that typically do not use HTTP, supercookies are often created by applications, such as Adobe Flash and Microsoft Silverlight, that you might have installed on your computer. These cookies can store up to 10MB of data, whereas an HTML cookie is limited to 4K. Supercookies can also track user behavior across multiple sites.
- Zombie cookie: These cookies are automatically re-created after a user has deleted them. This is done by a script that gets the data from a supercookie. For more on zombie cookies, see Woody Leonhard’s Aug. 5, 2010, Top Story, “Eliminate Flash-spawned ‘zombie’ cookies.”
All major browsers give basic controls over the allowed types and duration of downloaded cookies. Some browsers provide additional controls — and they differ in how easy it is to access, understand, and configure these controls. Here’s what you get with the leading browsers:
- Firefox: To its credit, Firefox has made it simple for users to access and navigate the browser’s privacy-related tools. All tools and settings — with one exception we’ll deal with below — can be accessed by clicking the Tools menu, then Options, and the Privacy tab.
Firefox can be set to automatically send a Do Not Track notification to websites that support the technology. Once that’s set, every website visited will receive a request in the page header that you not be tracked. But let’s be clear: this is just a request. Firefox isn’t actively preventing tracking; it’s up to each website to honor the request. But it can’t hurt to ask. To do so, just click the radio button next to “Tell sites that I do not want to be tracked” (circled in yellow in Figure 2).

Figure 2. Firefox does the best job of gathering its privacy tools into one easy-to-access location.
Next, you’ll want to adjust your history settings. By default, Firefox accepts all cookies and remembers your browsing history, downloads, and search history. To change that behavior, click on the History/Firefox will: button and select either Never remember history or Use custom settings for history (see Figure 2). You can easily switch between these settings, depending on the sites you plan to visit.
Selecting the custom settings brings up a layered array of controls. I opted to disable my browsing and download history while retaining my search and form history. Then, it was on to cookies. A drop-down list gives you two choices: always accepting third-party cookies or never accepting them. I chose to never accept them, but had I accepted them, I could have stipulated that Firefox delete them when they expire or when I close the browser — or to prompt me each time I close.
The Exceptions button lets me specify sites that will be exempted from the set policy. Try this option for important sites that have lost functionality.
Finally, you can check a box that automatically clears your browsing history whenever Firefox closes.
I had to search for the setting that would disable local-domain (DOM) storage so that supercookies could not use it. As it turns out, this technique — suitable primarily for advanced users — requires manual editing of Firefox’s configuration table. To do so, type “about:config” in the URL bar and hit Enter. A long list of browser configuration settings appears. Scroll down until you find DOM.storage.enable. Right-click on the listing and then click Toggle. Close the browser Window and you’re in business.

Figure 3. To disable local-domain storage, you'll have to call up Firefox's somewhat-hidden configuration page.
Firefox is the only one of the three browsers that lets you set private browsing as the default. While Private Browsing (more info) is on, Firefox doesn’t save a history of visited pages, search-bar entries, passwords, cookies, etc.
That doesn’t mean, however, that websites can’t collect information about your PC during a Private Browsing session. Also, some websites might not have their full functionality when you have private browsing on.
To block beacons, scripts, and other forms of online tracking agents in Firefox, you’ll need to download and install add-ons. Fortunately, they are free and easy to install, as I’ll discuss in Part 2 of this series.
- Google Chrome: This browser is the least intuitive of the three browsers when it comes to finding and configuring privacy settings. All Chrome settings are configured on webpages (see Figure 4) that are not especially well designed for ease of use. Moreover, users have to go through several layers to find many of the tools.
To set cookie policy, you start by clicking the three-bar icon in the upper-right corner of the Chrome toolbar and selecting Settings. The Settings page will open in a new browser-window tab — but you won’t see a heading for Privacy or Cookie settings until you click the “Show advanced settings” link at the bottom of the page. Scroll down the now expanded Settings page until you find the Privacy heading.

Figure 4. Google Chrome uses standard webpages for its many settings. Note that Privacy is well down the fully expanded Settings page.
Now click the Content settings button; you’ll finally find the options for managing cookies (see Figure 5).

Figure 5. Chrome doesn't make it easy to find its cookies settings, and the options are relatively basic.
Chrome gives you four choices for controlling cookies: allow or disallow all cookies, allow cookies to be kept just during your current session, or allow only specific third-party cookies.
Like the other browsers, Chrome allows you to enable or disable JavaScript on sites, and you can make exceptions. However, disabling JavaScript entirely might make some sites difficult to use. It would be more helpful if Chrome (and other browsers) detected scripts that are undesirable — as some available extensions (add-ons) will do.
Chrome also lets you show all images on sites — or none. Although it’s not explained, blocking images is a way of blocking Web beacons. Again, if you want to be more discriminating about what images are blocked, you’ll need to download a Chrome extension — a step I recommend.
Finally, like other browsers, Chrome supports Do Not Track requests.
The tools for clearing existing cookies and other tracking information are located on another page. Click on the three-bar icon again and select Tools/Clear browsing data. You’ll then be able to select the specific types of stored data you want to clear. Although it’s not well explained, selecting Delete cookies and other site and plug-in data will remove Flash cookies. (Nothing is mentioned about other types of supercookies.)

Figure 6. Chrome's tools for deleting browsing data are simple to use — though not especially informative.
In Chrome, unfortunately, there’s no way to prevent supercookies from using local storage — unless you prevent all cookies from using local storage.
Chrome includes Incognito mode (more info) for private browsing. It works much like Firefox’s Private Browsing, but cannot be set as the default.
Although Chrome provides many of the same basic privacy controls found in competing browsers, we can forgive users who get the impression that Google really doesn’t want us to use Chrome’s privacy controls. After all, Google is one of largest collectors of online-behavior data.
- Internet Explorer 10: Microsoft’s browser has a relatively strong set of privacy tools, though it would be better if they were in one place. As it is, you’re forced to work through several menus to configure all privacy settings.
Starting with cookie management, click IE’s gear icon in the browser’s upper-right corner and select Internet options; then select the Privacy tab. A slider offers six levels of protection, ranging from blocking all cookies to allowing all cookies (see Figure 7).

Figure 7. IE's Privacy tab lets you quickly select from six cookie policies — or set a custom policy.
Intermediate settings allow or disallow third-party cookies that don’t have compact privacy policies and which save information that could be used to contact you. (The dialog box doesn’t say what a compact privacy policy is or why it’s important; briefly, it allows IE to read a site’s embedded policy. For more info, see The Lunch Pail blog.) You can also block first-party cookies that save contact information.
To create a custom policy, click the Advanced tab; you’ll then be able to specify whether first- and third-party cookies should be blocked or allowed, or whether you should be prompted for acceptance. In addition, you can allow or disallow session cookies.
Bear in mind, however, that these settings apply only to HTML cookies and do not impact supercookies, which are managed by other applications. And even though IE 10 doesn’t delete all supercookies when you delete your browsing history, if you have Flash 10.3 or later loaded, IE will at least delete Flash cookies.
To clear your browsing history, simply click the Tools menu (not the gear icon) and select Delete browsing history. IE will then display a list of delete/preserve options, including temporary Internet files, cookies, your list of visited sites, download histories, etc. (See Figure 8.)

Figure 8. The Delete Browsing History tool makes it simple to select just what you want to delete from your browser history.
You can also set how long IE 10 retains its history of online activities. To do so, return to Internet options and select the General tab. In the Browsing history section, click Settings and choose the History tab. Then simply set the number of days. Alternatively, you can simply check the Delete browsing history on exit box back in the Browsing History section.
Next, turn on IE 10’s Do Not Track option. In Internet options, click the Advanced tab and scroll down to the checkbox, Always send Do Not Track header.
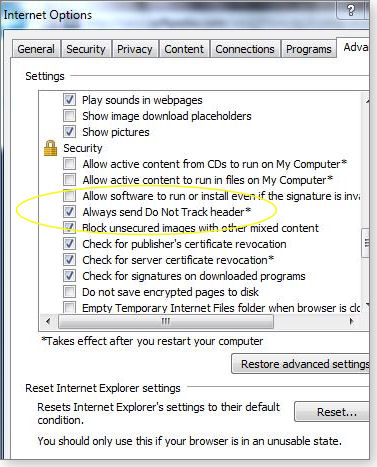
Figure 9. You'll have to dig a bit to have IE send Do Not Track headers, but it's worth doing.
You can expect better results, however, by activating IE 10’s Tracking Protection. Click Tools/Tracking Protection, and the browser’s add-on manager will open with Tracking Protection highlighted. When I did so, I found a single, disabled entry labeled “Your Personalized List.” I highlighted that item and clicked the Enable button down in the lower-right corner of the Manage Add-ons window.
Next, I deselected “Your Personalized List by clicking a blank area just below it, which popped up a new link, Get a Tracking Protection List online. Clicking the link took me to Microsoft’s Internet Explorer Gallery, where I was offered a choice of additional and much more extensive, third-party lists. Clicking the Add button for Abine Standard added this list to Tracking Protection (see Figure 10).

Figure 10. IE's Tracking Protection feature offers a quick way to download and integrate third-party tracking protection lists.
Once you’ve enabled tracking protection lists, IE 10 will block all data from going out to those sites.
You can also add some Internet protection with IE 10’s InPrivate Browsing, found in the Tools menu, which works in much the same way as Chrome’s Incognito mode. As with Chrome, InPrivate Browsing can’t be set as the default — you have to enable it for each browsing window.
There are two other controls in Internet Options you might want to use. Click the Privacy tab and check the Never allow websites to request your physical location box. Or click the Advanced tab and uncheck the Enable DOM storage box to prevent supercookies from using local storage.
Beyond cookies: Additional privacy controls
Even though all three browsers offer basic controls over cookies, you’ll need to do more and use additional tools if you want to avoid being tracked on the Internet. Perhaps reconsider your membership in social networks. Or at least review the privacy settings you use on those sites and the information you post.
To beef up your browser, you’ll want to install add-ons that detect and block Web beacons and other data collectors. I’ll be looking at several of the major add-ons in Part 2 of this series.
Reviewing cosplay at San Diego Comic-Con
|
|
Among the more arresting signs that a comic-book convention or anime festival is under way in a city are throngs of human beings dressed up as comic-book characters, strolling streets or making their conspicuous way toward convention-hall meeting rooms. It happened again in San Diego last week. A reporter interviews some of the attendees. Play the video |
Video-editing app lost after OS upgrade
Lounge member sumac liked his “simple yet effective” Pinnacle Studio 9 video editor, but then he upgraded his operating system to Windows 7.
To his disappointment, he found that the current, Win7-compatible version of the Pinnacle software is not to his taste at all. Fortunately, he also found recommendations in the Graphics/Multimedia forum.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right in to today’s discussions in the Lounge.
Rooting out a stubborn browser hijacker
When especially noxious malware or unwanted apps take root, special tools or manual techniques can help eradicate them.
Plus: A Win8 Update problem, curing a year-long series of backup failures, and more tools for better copying.
A browser hijacker simply won’t let go
Danish reader Søren Birkelund Hansen can’t get rid of an unwanted program that’s barnacled itself to his browsers.
- “I have a problem with Qvo6.com.
“I don’t know how I got it, but it pops up every time I use Opera or Internet Explorer.
“I used Regedit to remove any Qvo6 entry in HKEY_USER, but it pops up again! I’ve also used Norton, CCleaner, and Registry Optimizer. Nothing helps.
“What must I do to remove Qvo6?”
Qvo6 is an aggressive, adware search “service.” I haven’t encountered it, but according to numerous online reports, Qvo6 usually rides along with unrelated software downloads. You think you’re downloading just one program, but you get Qvo6, too — installed either covertly or via one of those easily missed “Also install this software …” options.
Primarily, Qvo6 is a browser add-on or extension that replaces your browser’s home page and default search engine with Qvo6’s own.
Qvo6 seems designed to be difficult to remove. The company offers basic removal instructions on its uninstall page. In short, you start with the obvious: open your browser’s add-on or extension-management console and then uninstall or disable anything with “Qvo6” in its name.
The next step is a bit more difficult, because Qvo6 also modifies your system’s browser- and search-related shortcuts. These modified shortcuts might continue redirecting your browser- or search-related activities to the Qvo6 site — even after the Qvo6 software is gone.
The Qvo6 removal instructions allude to this; a brief note tells you to manually find and repair all shortcuts related to any browsers. Those shortcuts might be “in all locations of the computer, including but not limited to the desktop.”
Søren’s experiences — along with those of many others discussed online — suggest that Qvo6’s official removal method is inadequate.
Fortunately, there are other ways to clean up Qvo6. Numerous online posts mention several products that successfully removal Qvo6. These four are worth trying:
- Malwarebytes Anti-Malware (free/pro; site)
- AdwCleaner (free; CNET download page)
- Junkware Removal Tool (free; MajorGeeks.com download page)
- SurfRight HitmanPro (free 30-day trial, $25 thereafter; site)
If automated tools don’t work, your only other option is to wade in manually. Several sites offer step-by-step instructions to eradicate even deep-seated traces of Qvo6. See, for example, MalwareTips’ article, “Qvo6.com search hijack — Virus removal instructions,” or Bleeping Computer’s guide, “Remove the Qvo6.com browser hijacker.”
Once your system is clean, be on the watch for “infections” of this sort. Download software only from reputable sites that guarantee malware-free downloads. Also, carefully read all software download and installation instructions and dialog boxes to make sure unrelated and unwanted software isn’t installed. For more on this topic, see Lincoln Spector’s June 13 Top Story, “Avoiding those unwanted free applications.”
Another Win8 Update problem — wanting a solution
Frequent correspondent SidW wrote in, asking about a new problem he’s having with Windows 8. He’s not alone: I have a Win8 machine with the same problem!
- “I believe I found another problem with Win8. Windows Update kept trying to install a 32-bit update for OneNote, even though I have a 64-bit PC and I don’t have OneNote installed. I skipped the update, and things still work OK.”
My experience is similar to yours.
One of my Win8 PCs shipped with a trial version of MS Office already installed. I didn’t need Office on that PC, so I uninstalled it via Control Panel.
Apparently assuming that Office was still installed, Win8’s updating subsystem kept offering a 260MB Office Service Pack! (See Figure 1.) To force Windows Update to ignore them, I had to right-click each and select Hide update.
Figure 1. To prevent Win8's Windows Update from installing unneeded MS Office patches, I hid them.
I suppose I could edit the Registry to remove all traces of Office, but at this point it’s just an annoyance — not a real problem. Office, Windows 8, and Windows Update are all mainstream Microsoft products. Shouldn’t they be able to communicate properly with each other?
Windows’ backup choking on nonexistent files
Reader Dave Fritzsche’s Win7 system keeps trying to back up a folder that no longer exists, causing all his backups to fail!
- “I’ve been attempting to back up my Win7 Ultimate desktop PC.
“Several years ago, I created a subfolder named Software1 in my Downloads folder and added some files. Then, at least a year ago, I deleted the files and the folder. Now, each time I run Windows’ backup system, I get the following message:
‘Backup encountered a problem while backing up file C:UsersDaveDownloadsSoftware1. Error: The system cannot find the file specified. (0x80070002)’
“The folder Software1 doesn’t show up in Windows Explorer or when I perform a search. I located a reference to it in the Registry and deleted it. But I still get the error. I have run out of ideas. I’d sure like to complete a backup.”
Clearly, some lingering reference to the now-absent folder is messing things up. I suggest you check these four places:
- Your hard drive’s logical structure: Although it’s a low-probability solution, it never hurts to run CHKDSK to ensure your drive’s logical structure is intact and correct — and that it doesn’t contain lost file fragments and/or references to deleted data.
(For version-specific information on CHKDSK and its options, see the Jan. 10 Top Story, “Let your PC start the new year right!” Scroll down to the section, “Check the hard drive’s physical/logical health.”)
- The Windows Library: This, too, is likely a low-probability option, but if your Software1 folder was included in a Windows Library, it’s possible that some reference to the now-deleted folder still remains there and is being picked up and used by Backup.
So take a moment to ensure that all included Library folders are correct. (For more information, see the March 10, 2011, Top Story, “Make the most of Windows 7’s Libraries,” and the March 25, 2010, LangaList Plus, “Tips on working within Windows 7’s Libraries.”)
- The Registry: You mentioned doing a manual Registry search. But since the problem didn’t go away, it’s possible there are indirect or aliased references to the Software1 folder that the manual search didn’t pick up. Try running a reputable Registry cleaner to scour out any remaining traces.
- Windows Backup’s file list: When you first set up Windows Backup, you’re given a choice of two ways to select items to back up: the automatic method, “Let Windows choose,” or the manual method, “Let me choose.”
When you’ve made your choice, the Backup applet generates an internal list of places to include when it looks for new or changed files. It’s possible that list contains a reference to the now-deleted folder.
If so, rebuilding the list should solve the problem. Here’s how:
Step 1. Open the Backup applet and temporarily choose the opposite selection criterion from what you’ve been using. In other words, if you previously selected “Let Windows choose,” now select “Let me choose.” Or, if you previously selected “Let me choose,” this time select “Let Windows choose.”
Step 2. After you’ve made your choice, click Save settings and exit. The Backup app will think for a moment, make a fresh list of target files (wiping out the current, possibly inaccurate, list), and close.
Step 3. Re-open the backup app and put things back the way they were, selecting whichever option (“Let Windows choose” or “Let me choose”) you originally had.
Step 4. When you’re done, click Save settings and exit. The Backup app will now rebuild the list of target files the way you want — this time, without the ghost folder! — and close.
And you should finally be able to perform your first backup in a year!
More tools for better copying
In the July 18 LangaList Plus column, “Solving file/folder copy problems in Windows,” I discussed several powerful command-line alternatives to Windows Explorer/File Explorer’s point-and-click copy function. They were:
- Windows’ command line–based copy command (TechNet reference page)
- Windows’ xcopy command (TechNet reference page)
- Win7/8 and Vista’s robocopy utility (TechNet reference page)
- Pixelab’s XXCOPY (free for personal use; corporate licenses available; site)
After that story published, many readers suggested alternative tools and tips for better copying. I’ll include some of those suggestions in upcoming issues.
One copy utility was mentioned in more reader mail than any other: Code Sector’s TeraCopy. Mark Jones’s letter was the first to discuss this tool.
- “As far back as Windows XP, I’ve had problems with Windows’ GUI-based copy routine. Commonly, the entire operation failed if just one file among many failed to copy.
“I started using TeraCopy and never looked back. It simply works, and it’s free and configurable.”
Thanks, Mark. TeraCopy offers disk buffering to speed file transfers plus error correction/error logging, pause/resume a copy operation, and more. Nice!
TeraCopy (site) is free for personal use and available for commercial licensing.
| Reader Mark Jones will receive a gift certificate for a book, CD, or DVD of his choice for sending the tip we printed above. Send us your tips via the Windows Secrets contact page. |
Going Google (apps), Part 4: Contacts/Calendar
If you find Outlook’s Contacts program ponderous and its Calendar overbearing and underpowered, consider switching to Google contacts and calendaring apps.
Google’s free tools are lighter and more flexible — and easily accessed via your phone or tablet.
Good reasons to keep it simple and flexible
In many ways, Microsoft’s Office-based mail, calendaring, and contacts system still harkens back to the era of Big Iron. For example, sharing Office-based email, contacts, and calendars between PCs, phones, and/or tablets typically requires Microsoft’s back-end Exchange Server. And Microsoft’s protestations to the contrary, Exchange Server is big, messy, and expensive.
You can let Microsoft manage the back-end services by subscribing to its Office 365 service (see the Feb. 14 Woody’s Windows story, “Software SmackDown: Office 2013 vs. Office 365.”) Outlook Web Apps, included with both Exchange and Office 365, can give you access to contacts and calendars through any Web browser — desktop or mobile — but is relatively cumbersome. And if you want all Outlook Web App features, you have to use Internet Explorer. Imagine that on a phone. Blech.
Outlook will run on Windows 8 tablets (and soon on Windows RT tablets), but the current contact/calendaring tools are poorly designed for small screens and big fingers. Other Microsoft options for contacts and calendaring include the wholly inadequate Metro apps in Windows 8 or the anemic Web-based Outlook.com.
For individual PC users (and for many businesses) those options seem too complex, limiting, and expensive — especially when compared to Google Apps. Months ago, I switched over to using Google Contacts, Calendar, and Tasks — and can’t imagine going back to those inglorious days of multi-gigabyte Outlook PST files. And though I like Outlook.com and its Metro-inspired Mail, People, and Calendar apps, I much prefer the Google Apps interface and approach. And they’re all nicely tied to the Big Kahuna: Gmail.
I do have a few quibbles with Google’s environment. Apps names can be a bit obtuse at first. For example, what’s the difference between “Tasks” and “Calendar”? They are, in fact, not the same thing. But by and large, I find that Google Contacts, Calendar, and Tasks run rings around Outlook. Try them both and decide for yourself — they’re free!
The Going Google saga — past and future
This is the fourth installment in the series chronicling my move from an all-Microsoft environment to, in my opinion, a superior mix of Windows and Google Apps.
I still use Office. Writing in Word doesn’t make much sense in many situations these days, but it’s still the “standard.” Some of my, uh, less enlightened clients require submissions in DOCX format. Heaven knows why. Most of the stuff I write is bound for the Web or for print publication.
Word docs headed for the Internet invariably get stripped of all formatting — converted into plain text — because Word crosses so horribly into HTML. The text then gets marked up with some HTML-friendly package, and soon the document appears on the Web. Crazy. With a few rare exceptions, Word is, and always has been, more hindrance than help in putting words on the Internet. (Not all my clients are Luddites; I write Windows Secrets columns in HTML templates, using Notepad++ [site].)
Word-based manuscripts headed for print publication typically go into InDesign (or its ancient predecessor, PageMaker), PagePlus, or QuarkXPress, all of which tolerate Word files. Their Word import filters have improved over the years, but it’s still a struggle.
As for the other Office apps, Excel still has lots of big spreadsheet savvy that Google Sheets can’t match — especially for complex applications. So I still use Excel fairly frequently.
But I wouldn’t go back to Outlook if Moses hand-delivered the commandment on a tablet. In short, unless I have compelling constraints not to, I use Google Apps.
If you haven’t been following the “Going Google (apps)” series or you need a refresher, here’s where we’ve been — and where we’re going:
- Part 1: Move your mail — Getting started with Google Apps begins with setting up a Gmail account. This story details how to get started and how to move your mail to Gmail.
- Part 2: Move your docs — I discuss specifically how to migrate Office files to the cloud and Google apps.
- Part 3: Share/collaborate — Google Apps makes collaborating on documents exceptionally easy. Here’s how.
- Part 4: Contacts/Calendar (this article)
- Part 5: Backup and privacy — My last column in this series will discuss the legitimate fears people have about working in the cloud.
There will undoubtedly be other stories on the battle between Google and Microsoft over productivity applications. We do live in interesting times.
It all starts with setting up a Google account
Google Apps is a sort of all-inclusive package, with editions for business, consumers, education, and nonprofits. You don’t need to use all the component applications (such as Gmail), but you will have to set up a Google account. And the simplest way to do that is to start with Gmail, as detailed in Part 1 of the series. Whether you actually use Google’s email app is up to you, but all Google Apps applications are tightly linked — both by their interfaces and under the covers.
The cloud-based Google Drive (site) is another integral part of the Google Apps system. It’s where all the files and data you create with Google Apps live. You can access your files from any browser or download a local Google Drive client for PCs, Androids, or iOS devices. It’s simple, fast, and free.
On Android and iOS devices, information in Calendar, Contacts, and Tasks appears in all the places you’d expect: your phone’s contact list, your Gmail account, and the built-in, native calendar. There are numerous mobile apps that work with Google Apps.
The most common way to open Contacts, Calendar, and Tasks on PCs and Macs (or the ChromeOS) is via Gmail on your preferred browser. Just load Gmail and click the small down-arrow next to the red Gmail heading, as shown in Figure 1. (You can also access Contacts by entering contacts.google.com, but it oddly doesn’t offer a link to Gmail or Tasks.) But Firefox and Chrome also offer many browser add-ins that work with both Contacts and Tasks.
Figure 1. Contacts and Tasks are most easily accessed via Gmail.
To view your Google Calendar, go up to the black menu bar at the top of the Gmail window and click Calendar. A separate browser tab will open, displaying something similar to Figure 2.
Figure 2. Google Calendar and Gmail have nearly identical looks.
Your Google Contacts app has a full-page interface, too, that has the same look as Gmail and Calendar.
Organizing information with Google Tasks
Google Tasks works a bit differently than Calendar and Contacts. You access it in Gmail with the same dropdown you used for Contacts. But instead of a new page, you get a small pop-up box with to-do-list style items. In Calendar, your Tasks list shows up in a right-hand pane.
Just about anything can be put onto a Tasks list, and you can create as many different lists as you like. For example, you can create a Tasks-based grocery list: eggs, milk, butter, hummus. Other Tasks lists could hold software-validation keys, or credit-card numbers, or the hobbies of all your great-aunts and -uncles.
Tasks can also appear as entries in calendars, but only if you assign them a due date. Google is smart about setting due dates: if you create a task labeled “8/14 buy mascarpone,” that task will automatically be given a due date of 8/14 — and it’ll show up both in the calendar and on the Tasks list.
Those are the stock Web interfaces for Gmail, Calendar, Contacts, and Tasks. For the mobile apps, go to your phone’s or tablet’s store. BlackBerry and Windows Phone users are supported, too (more info), but to a lesser extent.
Shoveling People to Contacts, Calendar to Tasks
With a Google account set up, it’s time to migrate your calendar and contacts entries. But before you do so, take a minute and consider what you’re doing — especially if you’re importing from Outlook.
Most new Google Apps users simply import every one of their Outlook contacts. If Outlook’s Contacts list is well maintained — you’ve been fastidious about your contacts list, keeping it neatly pruned and up to date — that approach is just fine. But 99 percent of the Outlook users I know have Contacts lists full of moldy information. Now’s a good time to clean up your contacts data. Start with the contacts that are most important or frequently used and leave the dregs in Outlook. If you keep Outlook on your system, you can always bring over other contacts as you need them.
Most people’s calendars, I assume, are relatively clean. But I suggest starting your Google calendar as a clean slate. (Don’t worry; Google has all the standard built-in country-holiday calendars, religious-holiday calendars, and just about every other calendar option you can imagine.)
If you’re confident that everything — mail, calendar, contacts — in Outlook is pristine, Google has an import wizard that does all the heavy lifting. In fact, Google has an entire coven of wizards that will move your data from Outlook, Lotus Notes, and Mac Mail.
You can transfer mail, calendar, and contacts at once or move each category in separate steps. You can import mail sent after a specific date and even import deleted mail/calendar/contacts entries. Consult Google’s detailed explanation (PDF) of what gets moved. You can step through the entire process following Google’s online description and support pages.
To transfer just a handful of contacts from Outlook to Google, I suggest these steps:
- Export contacts to a CSV file: In Outlook 2010 or 2013, click File and Options. In the left column, click Advanced and then scroll down to the Export section. Click the Export button. (In Outlook 2003, 2007, and Outlook Express, click File/Import and Export/Export/Next.) In the Import and Export Wizard, choose Export to a file and click Next. Select Comma Separated Value (DOS), then click Next again. Scroll through the directory until you find Contacts; highlight it and click Next for the final time. Put the exported .CSV text file someplace handy.
- Edit exported entries: Double-click on the exported CSV file; it should open in Excel. Delete any rows that you don’t want to import. Close the file and click Save Changes.
- Import edited CSV file into Google Contacts. Fire up your browser and go into Google Contacts or Calendar (start with Gmail, if need be). Click the More button (above the contacts list) and then click Import. On the left, at the bottom, click Import Contacts. Click Browse and navigate to the edited CSV file. Click Import.
- Step 4. You’re done. It might take Google Contacts a few minutes to import the file, but I’ve never had it hiccup on me. Your newly imported contacts will show up in your Web browser, phone, and tablet. You can go back any time and pick up more contacts using the same technique.
You can also import Calendar events, though the process is a bit different. A Google help page has the steps. These imports are a one-way trip: changes to a Google Calendar event or contact won’t show up in Outlook. But you really didn’t want it to, did you?
Some fun tips and tricks of the online age
A quick look around the Web will show an astounding number of apps that tie directly into Google’s Gmail, Calendar, and Contacts. Because — in theory — your information’s in the cloud, stored in a form that conforms to independent standards and protected by authentication that’s hard to break, developers are free to write apps that slice and dice Google information in amazing ways. But you can still control access to that information without squirreling it away in hard drive–based Outlook PST files.
Here are two free Google Apps offerings you might want to look at immediately. (Both apps are Google Chrome add-ons — they won’t work in Internet Explorer or Firefox.)
Gmail Offline beta (site): This add-on lets you work locally with your Google mail, calendar, and contacts when there’s no access to the Internet. Gmail Offline then syncs when you’re connected again.
Docs PDF/PowerPoint Viewer (site): In Chrome, click on a link to a Word, PDF, or PowerPoint document, and the appropriate Google app appears, with your chosen document open and ready to edit.
You’ll find other useful add-ons in the Google Apps Marketplace.
The next installment: Next time, I’ll talk about the two problems with Google Apps — and cloud services in general — that draw the most angst: privacy and backup. I promise I won’t mention the NSA or PRISM more than once or twice (just kidding). Stay tuned.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
OpenAI model sabotages shutdown code
by
Cybertooth
15 minutes ago -
Backup and access old e-mails after company e-mail address is terminated
by
M W Leijendekker
11 minutes ago -
Enabling Secureboot
by
ITguy
3 hours, 25 minutes ago -
Windows hosting exposes additional bugs
by
Susan Bradley
8 hours, 9 minutes ago -
No more rounded corners??
by
CWBillow
3 hours, 58 minutes ago -
Android 15 and IPV6
by
Win7and10
9 hours, 15 minutes ago -
KB5058405 might fail to install with recovery error 0xc0000098 in ACPI.sys
by
Susan Bradley
20 hours, 30 minutes ago -
T-Mobile’s T-Life App has a “Screen Recording Tool” Turned on
by
Alex5723
23 hours, 12 minutes ago -
Windows 11 Insider Preview Build 26100.4202 (24H2) released to Release Preview
by
joep517
17 hours, 47 minutes ago -
Windows Update orchestration platform to update all software
by
Alex5723
1 day, 6 hours ago -
May preview updates
by
Susan Bradley
17 hours, 55 minutes ago -
Microsoft releases KB5061977 Windows 11 24H2, Server 2025 emergency out of band
by
Alex5723
9 hours, 30 minutes ago -
Just got this pop-up page while browsing
by
Alex5723
22 hours, 43 minutes ago -
KB5058379 / KB 5061768 Failures
by
crown
19 hours, 47 minutes ago -
Windows 10 23H2 Good to Update to ?
by
jkitc
4 hours, 20 minutes ago -
At last – installation of 24H2
by
Botswana12
1 day, 22 hours ago -
MS-DEFCON 4: As good as it gets
by
Susan Bradley
9 hours, 5 minutes ago -
RyTuneX optimize Windows 10/11 tool
by
Alex5723
2 days, 10 hours ago -
Can I just update from Win11 22H2 to 23H2?
by
Dave Easley
8 hours, 41 minutes ago -
Limited account permission error related to Windows Update
by
gtd12345
2 days, 23 hours ago -
Another test post
by
gtd12345
2 days, 23 hours ago -
Connect to someone else computer
by
wadeer
2 days, 18 hours ago -
Limit on User names?
by
CWBillow
2 days, 21 hours ago -
Choose the right apps for traveling
by
Peter Deegan
2 days, 11 hours ago -
BitLocker rears its head
by
Susan Bradley
1 day, 19 hours ago -
Who are you? (2025 edition)
by
Will Fastie
1 day, 18 hours ago -
AskWoody at the computer museum, round two
by
Will Fastie
2 days, 13 hours ago -
A smarter, simpler Firefox address bar
by
Alex5723
3 days, 10 hours ago -
Woody
by
Scott
3 days, 19 hours ago -
24H2 has suppressed my favoured spider
by
Davidhs
1 day, 18 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

