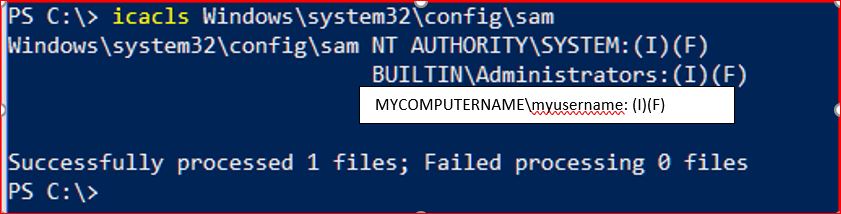
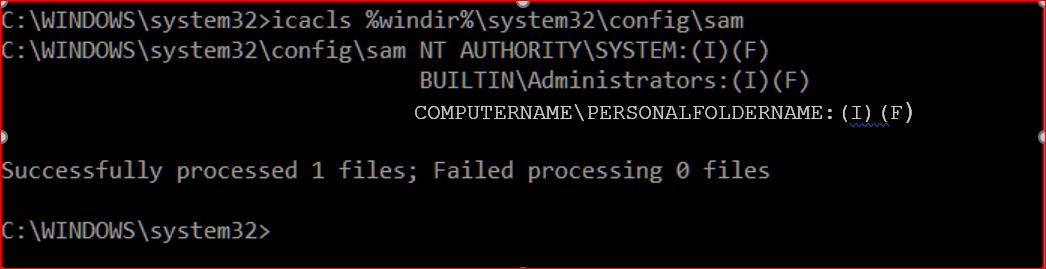
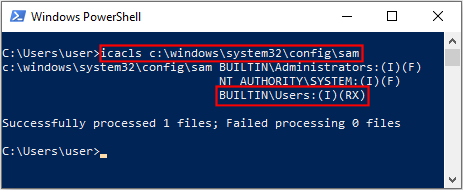
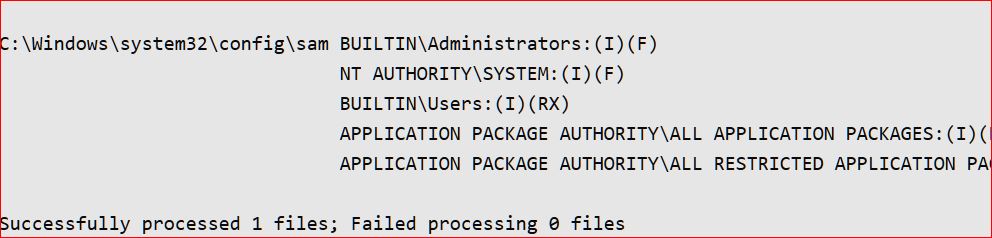
I have some questions about the update guide for CVE-2021-36934 (aka HiveNightmare/SeriousSAM) posted at <here>
1. If I understand the guidance, the first operation is to restrict access and the second operation is to delete the shadow copies. Is the order important?
2. I read the Caution statement which says
Restoring your system from a backup could restore the overly permissive ACLs and therefore revert your system to a vulnerable state. After restoring a backup, you must verify that the ACLs are correct to ensure that the restore operation did not reintroduce this vulnerability.
a) What does “restoring your system from a backup” mean – i) does this refer to restoring the system backup image? ii) Or does this refer to a complete restore of files and folders (in contrast to the system files)? iii) what about restoring a single folder or a single file (in contrast to all of the files and folders)?
b) How does one verify that the ACLs are correct?
3. If you have restricted access and have deleted shadow copies, and then you follow that with a backup that creates a system image, backups files and folders (most likely they will be files and folders since the last backup), and also creates shadow copies, is that later backup (of system image, of lately modified files/folders, and newly created shadow copies) “good” for restoring, whether it be a system image, all files and folders (including those that were backed up before the work-around), some files and folders (including those that were backed up before the work-around), or a shadow copy of a file (I presume that no shadow copy will have a date that precedes this new backup date)?