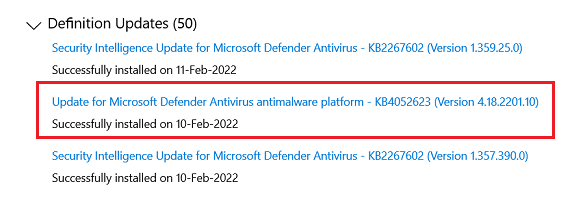
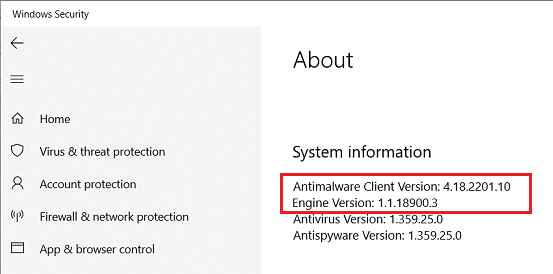
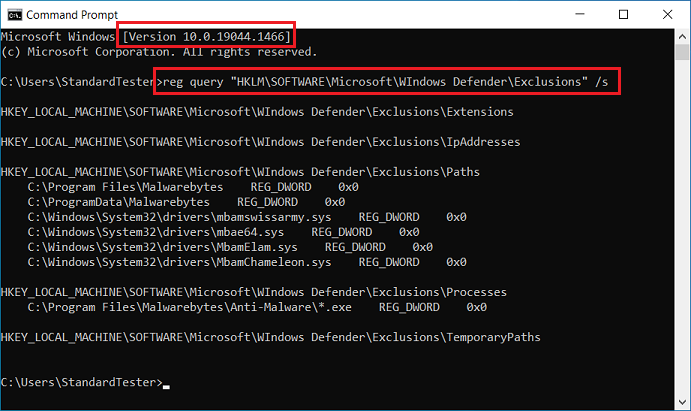
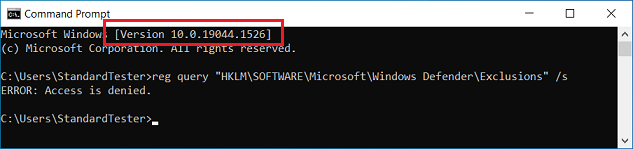
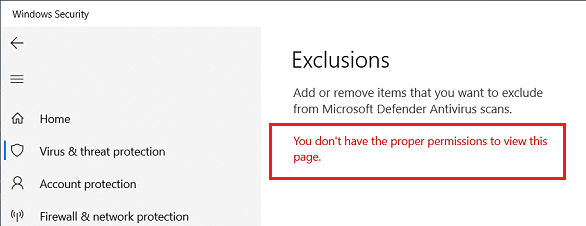
It’s that time of the month again that we wait on news of update side effects. It’s my philosophy that you shouldn’t rush into anything and patching (
[See the full post at: February 2022 Patch Tuesday early reports]
Susan Bradley Patch Lady/Prudent patcher