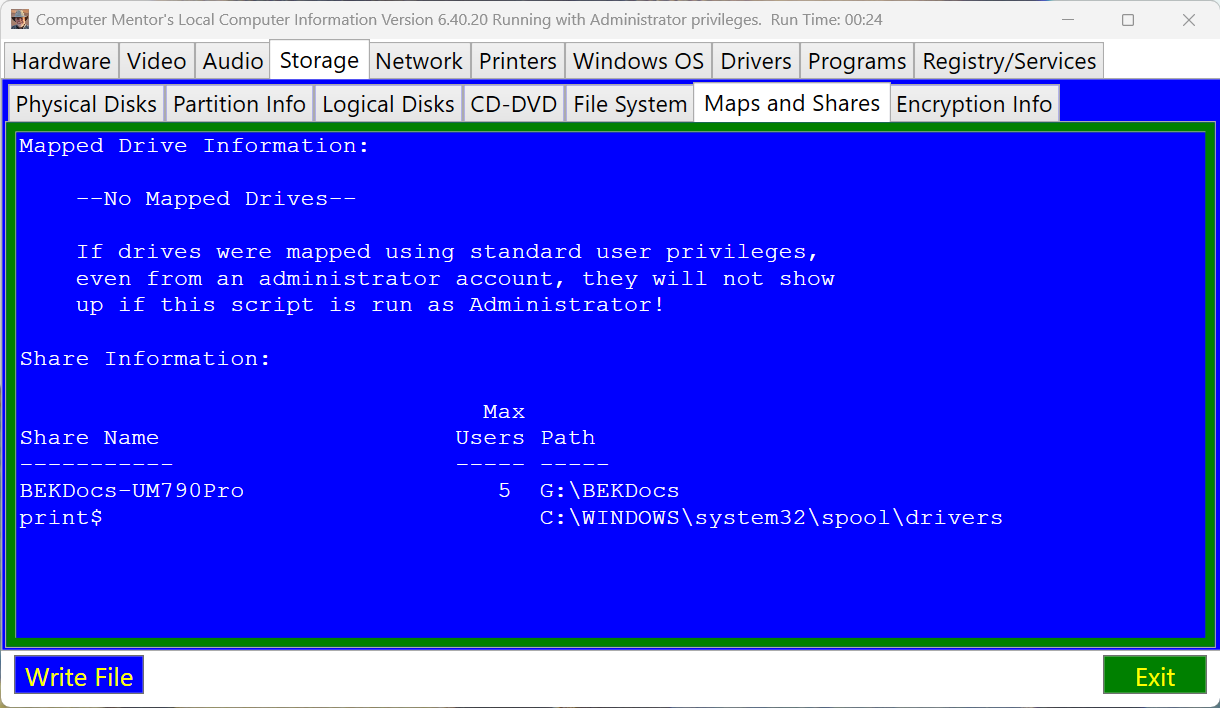
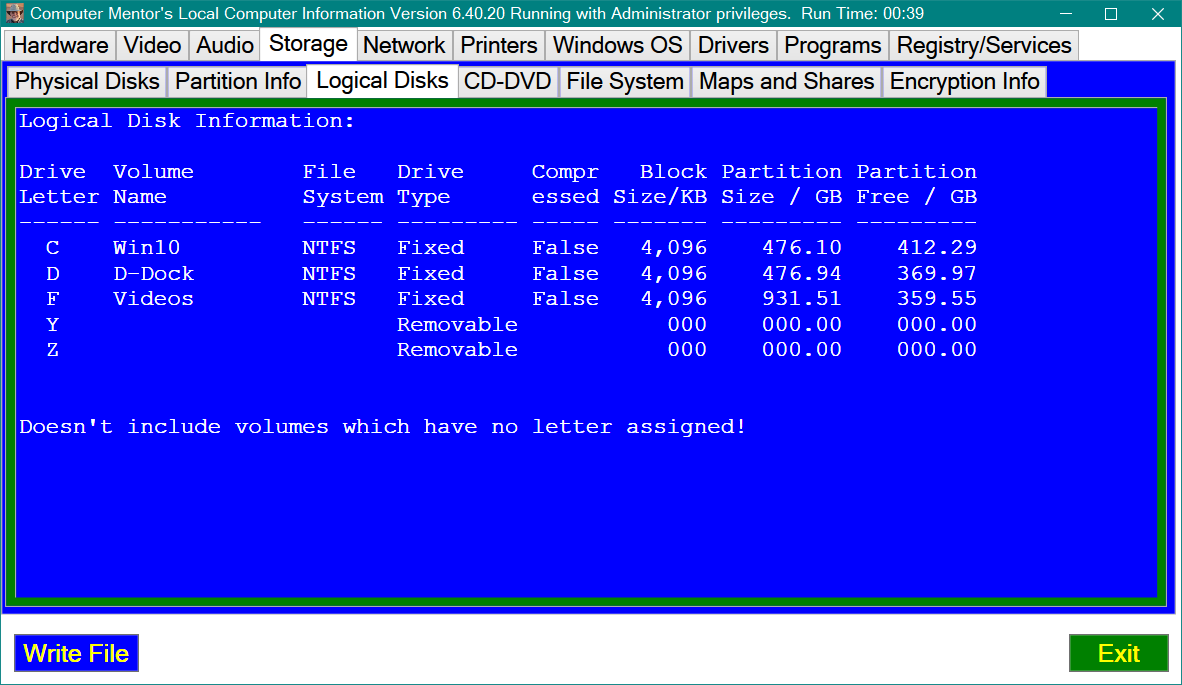
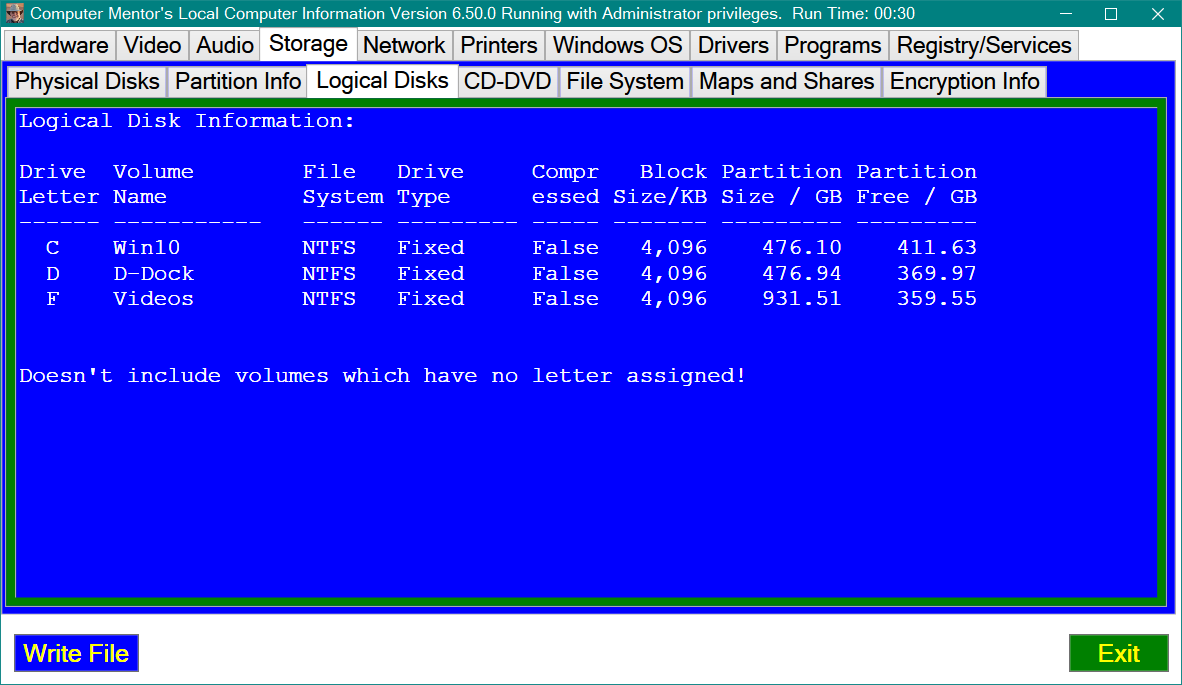
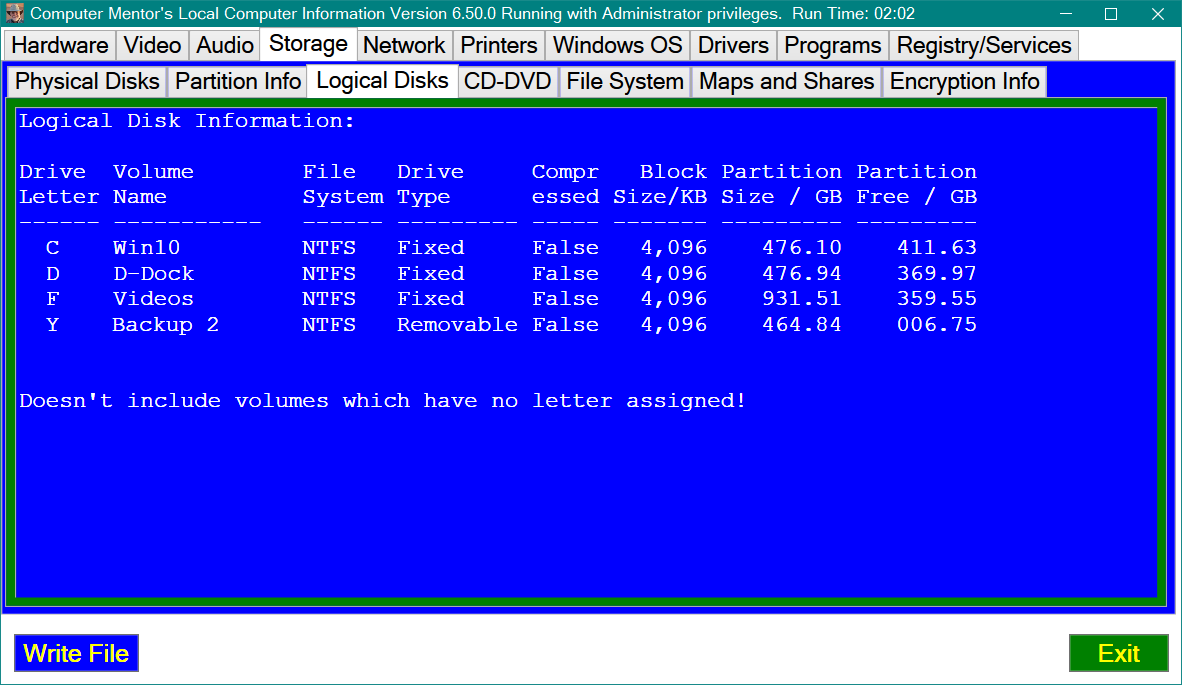
ISSUE 21.31.1 • 2024-07-31 By Susan Bradley It’s time to check whether your boot drive is encrypted. As I predicted, Microsoft’s July 2024 security up
[See the full post at: MS-DEFCON 3: Secure Boot triggers recovery keys]
Susan Bradley Patch Lady/Prudent patcher