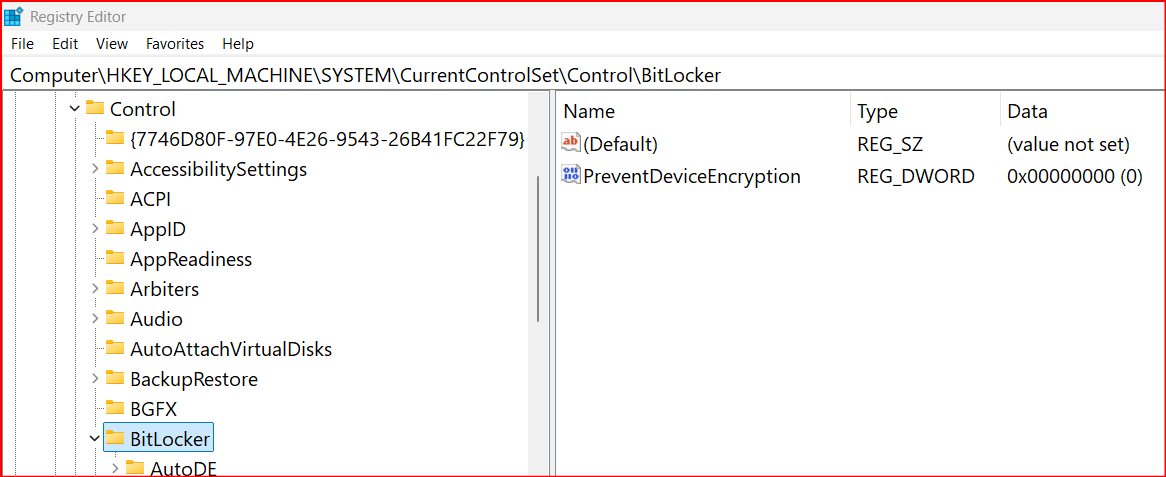
..For those who are on Windows 11 24H2 or are planning to upgrade soon, keep in mind that Microsoft encrypts your Windows drive with BitLocker or Device Encryption by default…
BitLocker has been found to impact drive speed and performance in the past, but there is a far scarier aspect of it, and that is the possibility of data loss…
“After seeing multiple users lose all their data because of BitLocker after Windows 11 system changes, I wanted to discuss this:
Microsoft now automatically enables BitLocker during onboarding when signing into a Microsoft Account.
Lose access to your MS account = lose your data forever. No warnings, no second chances. Many people learn about BitLocker the first time it locks them out…
Without mandatory, redundant key backups, BitLocker isn’t securing anything — it’s just silently setting users up for catastrophic failure. I’ve seen this happen too often now…
Microsoft posts official BitLocker key recovery and back up guide for Windows 11/10 PCs
* The problem with Device Encryption is more for Home users or users that create only local account.
I think that Microsoft shouldn’t encrypt PCs with only local accounts.