-
mcbsys
AskWoody PlusMay 11, 2018 at 11:09 am in reply to: Problems with CredSSP updates CVE-2018-0886 breaking RDP connections #191759Do you know if unpatched client/workstions will be able to connect patched RDS servers?
I think yes. See the Interoperability Matrix in KB4093942, Unpatched client to Mitigated server shows “Allowed.”
-
mcbsys
AskWoody PlusMay 9, 2018 at 5:01 pm in reply to: Problems with CredSSP updates CVE-2018-0886 breaking RDP connections #191312anonymous, like Susan says, patch your server. Any cumulative server udpate from March onward should get you back in business.
-
mcbsys
AskWoody PlusMay 9, 2018 at 3:47 pm in reply to: Problems with CredSSP updates CVE-2018-0886 breaking RDP connections #191287…but with how messy patches have been this first quarter of the year it does add to issues.”
Fair enough. What used to be a few minutes a month (checking for Patch Tuesday issues before installing on Friday) has this year become a non-trivial part of my work most weeks.
@GeekDiver, did patching your server(s) fix your issue?1 user thanked author for this post.
-
mcbsys
AskWoody PlusMay 9, 2018 at 1:07 pm in reply to: Problems with CredSSP updates CVE-2018-0886 breaking RDP connections #191220Short answer is that consumers can probably ignore it unless you need to connect to unpatched servers. The patch was included in a slew of updates in March: see the CVE article to locate your OS and the corresponding patch number:
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2018-0886
-
mcbsys
AskWoody PlusMay 9, 2018 at 12:34 pm in reply to: Problems with CredSSP updates CVE-2018-0886 breaking RDP connections #191212I don’t know where the original @GeekDiver post is so don’t know the context. I suspect unpatched servers and/or clients.
This is a planned tightening of security over three months. As promised, the May update changed the default to Mitigated. You can use group policy or registry to change it back to Vulnerable until you get your systems patched. Susan gave a heads-up on this in March: https://www.askwoody.com/2018/patch-lady-tracking-some-post-release-issues/:
“Initially in March, they are rolling out the new protocol. Later in April they will make it so that an error message will occur when you attempt to remote from a patched machine to an unpatched machine, and then later in May (tentative at this time) the default will be to enforce that remoting from a patched machine to an unpatched machine will not work.”
I hate it when Microsoft releases bugs that affect millions. In this case, I think Microsoft deserves credit for FIXING a security bug with a careful, documented, multi-month rollout of a mitigation.
7 users thanked author for this post.
-
mcbsys
AskWoody PlusSusan et. al. – with 1803, once you have the group policy settings or the registry equivalents, do you see “Some settings are managed by your organization” and the link to “View configured update policies”?
I blogged in February about using group policy to manage Win10 updates, and posted the equivalent registry changes for a sample setup. Sure like being able to confirm the changes in the GUI, though.
https://www.mcbsys.com/blog/2018/02/managing-windows-10-updates-using-group-policy/
-
mcbsys
AskWoody PlusOn Windows 7 machines, are you using any software, such as GWX Control Panel, to prevent Windows 10 installation?
I’d forgotten about that, but yes, all Win7 machines, including those that WSUS is offering to upgrade, include two registry values, created as follows:
REG ADD HKLM\SOFTWARE\Policies\Microsoft\Windows\Gwx /v DisableGwx /t REG_DWORD /d 1 /f
REG ADD HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate /v DisableOSUpgrade /t REG_DWORD /d 1 /f1 user thanked author for this post.
-
mcbsys
AskWoody PlusWhoa! Any indication that it’s free? In other words, that you’ll end up with a”genuine” copy?
No; in fact, there is a popup that requires me to agree to a license. See the screen shots in this post: https://www.askwoody.com/forums/topic/how-to-really-truly-block-the-pushed-upgrade-to-the-next-version-of-windows-10-version-1803/#post-183036. Still confusing–how can an upgrade to a genuine license, offered by Microsoft-supplied WSUS software, not be genuine?
1 user thanked author for this post.
-
mcbsys
AskWoody PlusIn a small Windows 7-only environment, the upgrade to Win10 1803 was just offered through WSUS for four Win7 machines. Three are Win7 Enterprise with expired Software Assurance (I’ve seen this before). One is Win7 Pro. Another Win7 Pro machine shows that the upgrade is “not applicable.” I wonder how WSUS determines that a machine is eligible for the (free?) Win10 upgrade.
1 user thanked author for this post.
-
mcbsys
AskWoody PlusI think I managed to hide this on Win10 Home:
1. Run the Show or Hide Troubleshooter (https://support.microsoft.com/en-us/help/3183922). Choose to hide updates. The feature update does not appear.
2. Go to Settings > Update and Security > Windows Update. Click Check for updates. The feature update will appear and start preparation.
3. Run the Show or Hide Troubleshooter again. This time the feature update is listed. Hide it.
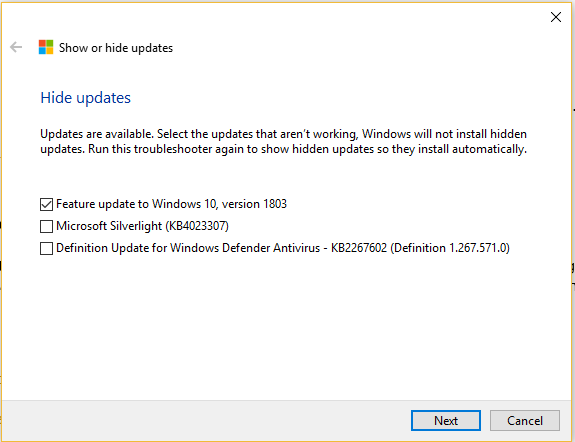
4. Turn off the network (I turned on Airplane Mode). The feature update continues “Preparing to install.” (I tried rebooting at this point but after the reboot, it just continued “Preparing to install”.) Eventually it changes to “Awaiting download.”
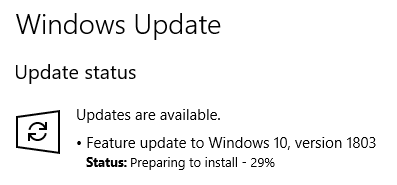
5. Turn on the network. Windows starts Checking for updates again. The feature update is no longer listed and does not download.
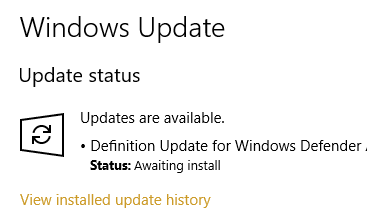
Bottom line: you can’t hide it until it detects that it should install, but after that, hiding it does seem to work. The feature update does not have a KB number but it does have an Update ID: {bd352700-9e34-4bed-9827-280d92737ef9}. It’s currently at Revision 1. If that is updated, you may have to re-hide it.
-
mcbsys
AskWoody PlusApril 20, 2018 at 10:12 am in reply to: How to change your Win10 Network Profile from Public to Private #186098Extensive documentation on multiple methods here:
https://www.tenforums.com/tutorials/6815-set-network-location-private-public-windows-10-a.html
Seems like I used the “Make this PC Discoverable” option recently.
2 users thanked author for this post.
-
mcbsys
AskWoody PlusFound this:
https://blogs.technet.microsoft.com/wsus/2017/08/04/improving-dual-scan-on-1607/
It confirms that the policy has no effect without WSUS.
It also says: While the new policy (dubbed “Disable Dual Scan”) is enabled, any deferral policies configured for that client will apply only to ad hoc scans against Windows Update, which are triggered by clicking “Check online for updates from Microsoft Update.”
I take that to mean if you are using WSUS and you enable this policy, if you release the a feature upgrade through WSUS, it’s happening now, not after any deferral defined in group policy. Deferrals don’t apply to WSUS-ordered upgrades. However, when this policy is enabled, users will not be able to bypass WSUS and bypass deferral policies to get an upgrade directly from Windows Update.
-
mcbsys
AskWoody PlusApril 9, 2018 at 7:32 pm in reply to: How to really, truly block the pushed upgrade to the next version of Windows 10, version 1803 #183122I can offer a workaround for the second question: go to
https://www.microsoft.com/en-us/software-download/windows10
and click Download tool now. Use the tool to create an offline USB installer for 1709. I always choose the option to create it for another PC, then create a combined 32-bit and 64-bit USB stick.
Can someone confirm that this works for Home? I’ve only tried with Pro.
-
mcbsys
AskWoody PlusI don’t quite understand “Do not allow update deferral policies to cause scans against Windows Update.” It sounds like it’s a policy that says, “No really, I mean it, obey the other policy.”
How does that behave in a non-WSUS environment where everything is coming from Windows Update?
-
mcbsys
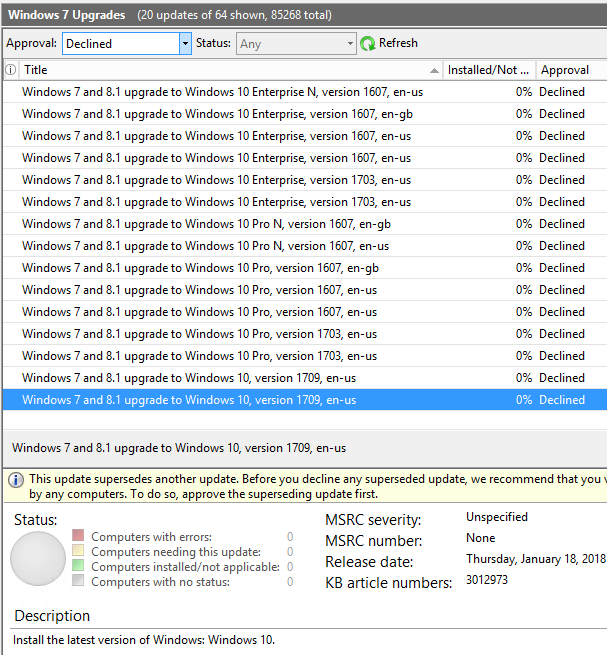
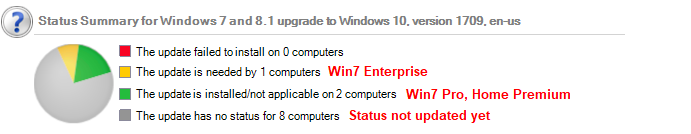
AskWoody PlusApril 9, 2018 at 3:15 pm in reply to: How to really, truly block the pushed upgrade to the next version of Windows 10, version 1803 #183036I only have one customer with Enterprise licenses, a small non-profit that gets those licenses through TechSoup. Wanted to post a screen shot but that’s confusing: when I create a WSUS view listing Windows 7 Upgrades, it actually looks like WSUS offered Windows 10 1607 and 1703 to both Pro and Enterprise, then 1709 was offered without being specific to the Windows edition.
I temporarily moved the last 3012973 upgrade from Declined to Not Approved and pushed through detection on three computers. On Windows 7 Home Premium and Windows 7 Pro, the Status is “Not Applicable,” so it wouldn’t install even if I approved it. On Windows 7 Enterprise, the status is “Not Installed,” indicating that it would install if I approved it. So it’s reproducible in this environment.
Will have to watch what happens when 1803 comes down the chute.

|
There are isolated problems with current patches, but they are well-known and documented on this site. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
June 2025 Office non-Security Updates
by
PKCano
2 hours, 40 minutes ago -
Secure Boot Update Fails after KB5058405 Installed
by
SteveIT
25 minutes ago -
Firefox Red Panda Fun Stuff
by
Lars220
2 hours, 36 minutes ago -
How start headers and page numbers on page 3?
by
Davidhs
13 hours, 1 minute ago -
Attack on LexisNexis Risk Solutions exposes data on 300k +
by
Nibbled To Death By Ducks
7 hours, 36 minutes ago -
Windows 11 Insider Preview build 26200.5622 released to DEV
by
joep517
21 hours, 41 minutes ago -
Windows 11 Insider Preview build 26120.4230 (24H2) released to BETA
by
joep517
21 hours, 43 minutes ago -
MS Excel 2019 Now Prompts to Back Up With OneDrive
by
lmacri
11 hours, 24 minutes ago -
Firefox 139
by
Charlie
3 hours, 59 minutes ago -
Who knows what?
by
Will Fastie
16 hours, 48 minutes ago -
My top ten underappreciated features in Office
by
Peter Deegan
22 hours, 27 minutes ago -
WAU Manager — It’s your computer, you are in charge!
by
Deanna McElveen
16 hours, 50 minutes ago -
Misbehaving devices
by
Susan Bradley
1 day ago -
.NET 8.0 Desktop Runtime (v8.0.16) – Windows x86 Installer
by
WSmeyerbos
2 days, 4 hours ago -
Neowin poll : What do you plan to do on Windows 10 EOS
by
Alex5723
1 hour, 43 minutes ago -
May 31, 2025—KB5062170 (OS Builds 22621.5415 and 22631.5415 Out-of-band
by
Alex5723
2 days, 2 hours ago -
Discover the Best AI Tools for Everything
by
Alex5723
1 day, 2 hours ago -
Edge Seems To Be Gaining Weight
by
bbearren
1 day, 17 hours ago -
Rufus is available from the MSFT Store
by
PL1
2 days, 1 hour ago -
Microsoft : Ending USB-C® Port Confusion
by
Alex5723
3 days, 4 hours ago -
KB5061768 update for Intel vPro processor
by
drmark
1 day, 3 hours ago -
Outlook 365 classic has exhausted all shared resources
by
drmark
1 day, 2 hours ago -
My Simple Word 2010 Macro Is Not Working
by
mbennett555
2 days, 23 hours ago -
Office gets current release
by
Susan Bradley
3 days, 2 hours ago -
FBI: Still Using One of These Old Routers? It’s Vulnerable to Hackers
by
Alex5723
4 days, 16 hours ago -
Windows AI Local Only no NPU required!
by
RetiredGeek
4 days, 1 hour ago -
Stop the OneDrive defaults
by
CWBillow
4 days, 17 hours ago -
Windows 11 Insider Preview build 27868 released to Canary
by
joep517
5 days, 3 hours ago -
X Suspends Encrypted DMs
by
Alex5723
5 days, 5 hours ago -
WSJ : My Robot and Me AI generated movie
by
Alex5723
5 days, 5 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.