
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Better data and boot security for Windows PCs
In this issue
- LOUNGE LIFE: The 'try something else' solution for Hotmail
- TOP STORY: Better data and boot security for Windows PCs
- WACKY WEB WEEK: Acrobat over real-life, rush-hour bridge traffic
- LANGALIST PLUS: How to downgrade from Windows 8 to Windows 7
- BEST PRACTICES: Tips for setting up a new Windows PC
- PATCH WATCH: The rapid-fire updates for Office 2013 continue
The 'try something else' solution for Hotmail
When Lounge member oldn advised his wife to sort her Hotmail messages into folders to make them easier to find, she did. But after she made her messages easier to see, she couldn’t move them on her own laptop.
Both oldn and his wife could move her mail on his computer — but not on hers. Members of the Non-Outlook Email forum explore the issues.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right into today’s discussions in the Lounge.
Better data and boot security for Windows PCs
Fundamental changes in PCs, including UEFI and Secure Boot, can interfere with classic security techniques such as whole-disk encryption.
But a simple, free, two-step process provides extremely reliable data and system-boot security for all Windows versions, on virtually all PC hardware.
The gold standard for local PC data and system security for years, whole-disk encryption offers two main benefits. First, it can provide robust, virtually uncrackable security for all the files on your hard drive. Without the correct password, anyone snooping through your files sees only gibberish.
Second, some whole-disk encryption tools can password-protect the entire system. Without the correct password, an unauthorized user can’t boot the PC from its hard disk.
There are, however, limitations and drawbacks to encrypting an entire hard drive.
Many Vista, Win7, and Win8 PCs sold within the past decade — and virtually all sold within the past few years — include some form of Unified Extensible Firmware Interface. UEFI is essentially an enhanced replacement of the venerable BIOS. (For more on this topic, see the Jan. 19, 2012, Top Story, “Say goodbye to BIOS — and hello to UEFI!”)
On newer systems, UEFI can provide boot-time security to prevent malware (rootkits, bootkits, and so forth) and other unauthorized software from meddling with the way a PC starts up. In fact, UEFI is the foundation for Win8’s Secure Boot feature, which is enabled by default when Win8 is installed on a UEFI-equipped PC.
Some whole-disk encryption tools require low-level access to the PC early in the boot process. These tools can fail on PCs that make use of UEFI’s advanced security features.
TrueCrypt, for example — which might well be the world’s most popular open-source, whole-disk encryption tool — currently doesn’t work on Win8 systems using Secure Boot. This situation will most likely change in the future; but today, some TrueCrypt users who upgraded from Win7 to Win8 have run into severe trouble, such as losing access to the entire contents of their hard drives.
Another popular encryption tool, DiskCryptor, doesn’t officially support Win8. But some users have made it work — in a limited fashion on individual partitions. They installed the application as a service on the desktop side of Win8. On the other hand, other DiskCryptor users have lost access to all their encrypted files.
Even if these tools are eventually patched to work with UEFI and Secure Boot, they’re still working at some level against UEFI’s low-level security features. Today’s systems simply aren’t meant to allow third-party tools to insert themselves deeply into the boot process.
Fortunately, you can choose better and safer ways to provide reliable data protection and boot security on just about any PC. The tools and methods are free, and they work without interfering with UEFI, Secure Boot, or any other existing security features or functions.
Safer alternatives to whole-disk encryption
No matter how old or new your PC is, and regardless of what Windows version you’re running, you can have extremely reliable data and boot security using two free alternatives to whole-disk encryption.
Data security: Although whole-disc encryption can be problematic, file-and-folder encryption is rock-solid. There are many tools available, but perhaps the most popular is the open-source 7-Zip (site) application. It’s free for personal and business use, and it can scramble any file, folder, or group of folders with essentially uncrackable 256-AES encryption (more info). Even if a hacker gains access to your hard drive, your encrypted files should remain completely safe, secure, and unreadable.
Note: Although this article focuses on encryption, 7-Zip also compresses files, so they occupy less disk space. The amount of compression varies with file type, but it’s not uncommon for file size to shrink by around 50 percent. Compression can be an important added benefit if you have a small, traditional hard drive or a solid-state drive (SSD). So 7-Zip can simultaneously encrypt your data and shrink the size of your folders and files.
Below, I’ll show you the basics of using 7-Zip to encrypt and compress files and folders you select. (Selective file/folder encryption and compression gives you more control than does whole-disk encryption. For example, there’s little reason to encrypt or compress music, video, and image files. More on that below.)
Boot security: Virtually every PC in use today lets you set one or more low-level, pre-boot passwords. One type of password protects the system as a whole; the password must be entered before the system will boot. Many PCs also offer a separate supervisor password to prevent unauthorized changes to the basic system settings. And some PCs let you set a password to protect the hard disk or SSD from unauthorized access.
The passwords can be used singly or in combination, depending on how much security you want or need. Later in this article, you’ll see how to access and set whatever passwords your system offers.
Combine data and boot security, and your data is protected from almost all malicious threats. A pre-boot password will keep hackers from accessing your system with separate bootable media. And if a hacker gets past that barrier, encryption will prevent access to sensitive files and folders. Whether you combine file/folder data security and boot security or use one of the two alone, you won’t run into problems with UEFI, Secure Boot, or any other of your PC’s security features.
Getting started with file and folder encryption
The first step in implementing file and folder encryption is to figure out what really needs to be encrypted.
There are many, many files on our hard drives that simply aren’t all that special, unique, or sensitive. They just don’t need to be encrypted!
For example, it’s sort of silly to encrypt your copy of Notepad, Paint, Calculator, Solitaire, or any of the other system files (.exe, .msc, .dll, and so forth) that came with your original Windows setup. Most of Windows’ core operating system files are similar from system to system, varying only by Windows version and local hardware. They typically don’t contain any sensitive information. So it’s wasted effort to encrypt them (as they would be with whole-disk encryption).
Most add-on software doesn’t need encryption, either. Your copy of Word, Excel, Skype, Photoshop, or whatever is, for the most part, like any other.
That also holds true for files you acquire through public sources. Your “Dead Skunk” MP3 and that downloaded “National Lampoon’s Vacation” video are likely identical to everyone else’s. What’s to be gained by encryption? Even your digital photographs probably don’t contain anything truly sensitive.
On the other hand, many of the files you create — within Word, Excel, or other applications — could contain sensitive information. Those are the files that need protection and should be encrypted!
In most cases, securing potentially sensitive information means selecting specific files and folders. For example, you probably don’t need to encrypt your Music folder, but you almost surely want to protect Documents and its subfolders — plus any other locations that might have information you want to keep private. Consider reorganizing your documents into sensitive and nonsensitive folders. You most likely don’t need to encrypt your collection of old family recipes.
Once you’ve decided what you need to encrypt, make a full system image or backup. Or at least make separate backup copies of the files you intend to encrypt. Although file-and-folder encryption tools are usually extremely reliable, accidents and user errors can happen. So it’s best to play it safe — make backups!
Next, download and install the file/folder encryption tool of your choice. A quick Web search will produce numerous options. I use 7-Zip for this article because — again — it’s reliable, well regarded, open-source, and free for both personal and business use.
Step by step: Encrypting data with 7-Zip
If you don’t have 7-Zip already installed, head over to 7-zip.org and download the version with the correct bittedness for your PC — the 64-bit 7-Zip for 64-bit systems, and the 32-bit 7-Zip for 32-bit systems.
- Select the files/folders you want to include, such as those in your Documents folder. Right-click on the group of selected files/folders; you’ll see 7-Zip on the context menu, as shown in Figure 1.

Figure 1. Once installed, 7-Zip is easily accessed by right-clicking selected files and folders.
- Click 7-Zip in the menu, and then select Add to archive as shown in Figure 2.

Figure 2. Clicking Add to archive opens 7-Zip's archive settings.
- When the Add to Archive dialog box opens (see Figure 3), enter a secure — long, complex, and hard-to-guess — password where indicated.
The rest of the Add to Archive default choices are usually fine. 7-Zip will automatically generate an archive name based on the selected folder(s), a file’s name, or the selected files’ containing folder. The default archive format will be .7z, which typically offers 2–10 percent better compression than the classic .zip format. I recommend leaving the defaults alone — at least until you’re familiar with 7-Zip.
Click OK when you’re ready.

Figure 3. At least to start, use the default archive settings for encrypting your data.
Note: I recommend using a good password manager to help generate and remember your passwords. For more information, see the Jan. 9 Best Software story, “Why and how to use an open-source password manager,” and “Stepping up to a standalone password manager” in the Oct. 17, 2013, Top Story, “Protect yourself from the next big data breach.”
- Enter your password and click OK; 7-Zip will then compress and encrypt the selected files. As a safety feature, 7-Zip creates archived copies of your files, leaving the originals intact. In Figure 4, the files are placed in an archive called Documents.7z.

Figure 4. A new 7-Zip archive (in this example, Documents.7z) contains compressed, encrypted copies of the selected files and folders.
Your archive is now complete!
Your next step is to test the archive to make sure that encryption and compression worked properly. If it did — and that’s almost always the case — you can then delete the original files, so that only the encrypted archive remains.
- To open an archive, simply double-click it (Documents.7z, in this example). When the password dialog box opens (Figure 5), enter the password you gave that particular archive. You might use different passwords for different archives. (Keep those passwords safe! Obviously, if you lose a password, you’ve effectively lost the encrypted files and/or folders.)
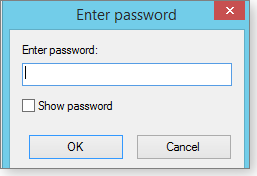
Figure 5. Entering the correct password opens archived files and folders.
- With the proper password entered, 7-Zip File Manager opens and displays the contents of the archive (Figure 6). Click on any listed file or folder; it should open normally and work just like any nonencrypted file. When you save and close an archived file, it’s automatically compressed and encrypted with the archive’s original password.

Figure 6. 7-Zip's file manager lets you view, open, edit, and save files.
- Check that the archived files are accessible and saved correctly, then delete the originals so that only the encrypted archive remains, as shown in Figure 7. (For complete security, be sure to empty the Windows trash.)

Figure 7. With the originals deleted, your files and folders are securely encrypted.
The 7-Zip File Manager is the key to easily using your archives. Leave it open as you typically might the standard Windows/File Explorer — then view, access, or edit any files in the archives just as you do nonarchived files. 7-Zip’s File Manager also lets you quickly add files to an archive.
That covers the bare-bones basics of using 7-Zip, but there’s a lot more to the software, including ways to extract files and folders from the archive and to add files and folders without using the 7-Zip File Manager. For complete information on using 7-Zip, check out its built-in Help file or see these online resources:
- 7-Zip support site
- Video tutorials at ShowMeDo
- Video tutorial at Top Windows Tutorials.com
- Tutorial by expert user Gürdal Ertek (autoloading video)
Enabling pre-boot security passwords
As mentioned above, using a pre-boot password can be an excellent security precaution. Most current PCs have some kind of BIOS/UEFI-password option built in. There can be multiple types of passwords, and they typically appear immediately after a system powers on and before the operating system loads.
The number and password options and their capabilities vary from vendor to vendor. In a moment, you’ll see how to determine what password options your PC offers.
Some passwords lock down the entire system; without the proper password, the system won’t boot at all — either from the internal hard drive or from any bootable media! Other passwords help to protect the hard drive from unauthorized access. And still other passwords let you set an administrator/supervisor password to prevent unauthorized changes to the BIOS/UEFI settings.
As Figure 8 shows, the BIOS/UEFI might offer more than one type of password.

Figure 8. A typical BIOS/UEFI lets you set one or more passwords to protect components such as the system, settings, and/or mass-storage drives.
Using one or more of these low-level passwords can help lock your system down tight, making it extremely secure against any unauthorized access.
Of course, make sure you remember the BIOS/UEFI passwords — or you might be unable to access your own hardware!
The various brands and models of PCs use different methods to access and change the BIOS/UEFI-password settings. The information below is a general guide, but for specific information for your brand and model of PC — or if the following instructions don’t work for you — visit your PC vendor’s online support site and search for BIOS/UEFI access. Use search terms such as access BIOS, access UEFI, enter BIOS, enter UEFI, edit BIOS, and/or edit UEFI.
► BIOS/UEFI access for Win8.1 PCs (Win8.0 is similar):
- Save any open files and exit all running programs.
- Open the Charms bar, click the gear icon (Settings), and then click Change PC settings at the bottom of the bar.
- On the PC settings page, select Update and recovery.
- Click Recovery and then, under Advanced startup, click Restart now. (Despite the terminology, your PC will not immediately restart! This is normal.)
- On the Choose an option screen, click Troubleshoot and then click Advanced options.
- If a UEFI Firmware Settings option appears, select it. (It might be called something slightly different, such as Change UEFI Settings.) If no such option exists, skip the rest of these steps.
- On the UEFI Firmware Settings screen, select Restart.
- Your PC will restart and run the built-in UEFI setup utility.
- Explore the UEFI setup utility’s tabs and dialog boxes to find the password settings. They’re often found on a tab labeled Security, or something similar. (See Figure 8, above.)
► BIOS access for non-UEFI PCs
You’ll find detailed information on accessing traditional BIOSes in the Jan. 9 Top Story, “The best of LangaList Plus from 2013.” Skip down to the subhead, “Using multiple layers of security — an update.” Then look for the subsection, “Protecting against local/physical threats.”
Bottom line: Easy data and system security for any PC, any Windows. In today’s era of UEFI PCs and Secure Boot, using low-level security tools such as whole-disk encryption is just asking for trouble. But you also don’t have to leave yourself vulnerable. Take some time to investigate your system’s boot-level password options. And if you don’t like 7-Zip, there are plenty of other file/folder-level encryption apps to choose from. They work on most versions of Windows and on any PC hardware.
Acrobat over real-life, rush-hour bridge traffic
 |
On any given day in New York City, looking up gives you plenty to see. When aerialist Seanna Sharpe climbed the Williamsburg Bridge, anchored her silk swing from upper beams, and performed her routine, onlookers paid particular attention. And so did the police. They were waiting for her when she came down from the heights, and she spent a night in jail. And yet, in a world overflowing with deadly serious consequences — kidnappings, famine, war — it might be proportionate justice that for her dangerous behavior, the acrobat was sentenced to five free performances for children. Click below or go to the original YouTube video. |
| Post your thoughts about this story in the WS Columns forum. |
How to downgrade from Windows 8 to Windows 7
Downgrading to an older Windows version is rarely ideal, but you can revert back to Win7 from Win8. Here’s how.
Plus: Free and extremely low-cost (under $10!) Win8 repair drives.
Various techniques for returning to Windows 7
Windows 8 is evolving fast. It’s gone through three iterations — Versions 8.0, 8.1, and 8.1 Update — in just 18 months. That has to be a record for any Windows.
Win8 needed those quick changes! The original 8.0 version was incredibly annoying — especially for longtime Windows users.
But the current release — Win8.1 Update — corrects or reduces many of the most egregious failings. If you install a third-party utility to add a full-fledged, useful, Win7-style Start menu — a tool such as Start Menu 8 (free; site) or Start8 (free trial, then U.S. $5; site) — Windows 8.1 Update is actually pretty good.
In fact, after months of complaining about the original Win8, I now use Win8.1 Update full-time, every day — now that I can virtually ignore the still-clumsy Modern/Metro interface. I’m a little surprised to find myself saying this, but I hardly ever miss Win7!
Despite the improvements to Win8, some users just can’t stand the OS in any form. Windows Secrets gets a small but steady stream of letters from readers looking for ways to downgrade a Win8 setup to Win7. For example, here’s a note from reader Art Tompkins:
- “I’ve had it with Win8. Is there a way to revert to Win7 without having to reinstall a zillion programs and apps? Win 7 seems to be more stable; I’m running it on two other systems and have had no problems.”
Art, there’s no automated roll-back system that downgrades Win8 setups to Win7, but you can do it manually.
The process can be quite easy if you made a full backup of your Win7 setup before you upgraded to Win8. Your old OS, apps, and data all will be restored in one smooth, highly automated step.
On the other hand, downgrading without a full Win7 backup is significantly harder but typically can be done. It usually entails a fair amount of work, including manually reinstalling applications and data.
I’ll cover both options in a moment. But first, before you do anything else, take these three preliminary steps:
- Start by preserving any new user files (documents, photos, MP3s, etc.) that you created on your Win8 setup. Copy or move all such user files to a safe location, such as to an external drive or to DVDs or CDs.
- Next, if your PC is equipped with Secure Boot, disable this Win8 security feature. For instructions, see the April 17 Top Story, “Emergency repair disks for Windows: Part 2”; skip down to the section labeled “Working around Windows 8’s Secure Boot.” (Note: Some PCs have a related function called Legacy Boot — or something similarly named. If your PC offers this type of boot option, enable it.)
- Finally, make a full image backup of your Win8 setup — just in case you want to restore it later or something goes wrong with your switch to Win7. See the Oct. 10, 2013, Top Story, “Creating customized recovery images for Win8.”
The next steps depend on whether you have a full backup of your previous Win7 setup.
► Working with a complete system backup:
- Restore your previous Win7 setup from its most recent full-backup files, using whatever tool created them. You want to remove all traces of Win8 from your boot drive (typically, C:). So reformat the drive if that option is offered; otherwise, use the backup to completely overwrite the Win8 setup.
When this initial restoration is done, there should be nothing but your original Win7 setup on your boot drive. In other words, your PC should be exactly as it was when you made a final backup of Win7 and your data: all apps installed and fully operable, and all then-current user files right where you left them.
- When the restoration completes, run Windows Update to bring the Win7 setup fully up to date. Then make sure your anti-malware tools and any other important software are also fully updated.
- Last step: Import or move the user files you saved from the Win8 setup into whatever location you want on the now-Win7 system.
► When there’s no full-system backup to start with:
There’s no shortcut: you’re looking at a full, from-scratch Win7 installation. But these tips might make it a little less painful:
- Before you start, make sure you have the correct Win7 drivers on hand. If you don’t have Win7 OEM driver discs, visit your system vendor’s site and download copies of the available Win7 drivers for your model. Save these drivers in a safe place — off the C: drive of your system.
- Next, using whatever Windows 7 setup disc you have available, do a complete Win7 setup, reformatting or overwriting the Win8 setup on your C: drive. If prompted for them, install the Win7 drivers from wherever you saved them.
- When Win7 is fully installed and working, let it fully update via Windows Update.
- Install your other software, starting with a known-good and fully up-to-date anti-malware tool.
- Last, when everything is in place and working correctly, import/move the user files you saved from your Win8 setup onto your new Win7 setup.
► In all cases:
When your Win7 restoration or setup is 100 percent complete and up to date, make a new system image so you’ll be able to get back to this fresh, just-installed state in the future, should you ever need or want to. For complete details, see the May 12, 2011, Top Story, “Build a complete Windows 7 safety net.”
Free — and almost-free — Win8 repair drives
Pat Santucci was stymied in creating a Win8 repair/recovery drive, as described in the Top Stories, “Emergency repair disks for Windows,” Part 1 (April 10) and Part 2 (April 17).
After researching the problem, he thought he’d have to spend big bucks for a remedy. Happily, he was mistaken!
- “Fred, the following is my unsuccessful experience trying to make a CD or DVD repair disk for Windows 8.1. Perhaps there is a solution?
“I have a PC that came with Windows 8.0 installed. I upgraded to Windows 8.1 for free via the Microsoft store.
“I wanted to make an emergency repair disk as described in your two-part article. Unfortunately, I do not have a USB drive (can’t afford one). However, I do have a lot of CDs and DVDs.
“Fred’s article clearly stated that the Windows 8 version of the Recovery Media Creator would create a bootable CD or DVD. Hence, I did a bit of research, hoping I could find a way to make a CD or DVD with Windows 8.1. I found a Microsoft site with instructions.
“Since I don’t know the required Win8 product key, I researched ways to find it. I Installed and ran Belarc Assistant [free; site]. The program identified a key for my Windows 8.1, but it didn’t work with the Windows 8.1 Setup program referred to in the aforementioned Microsoft instructions.
“My conclusion thus far is that I must either purchase a USB drive or not make a repair disk.”
I’m happy to tell you that you can indeed make a Win8 repair disk or drive, and it doesn’t have to cost you a cent!
But first, let me explain the problem you encountered. You upgraded a Win8.0 setup to Win8.1. The upgrade doesn’t change your original product key. That’s why the “Create installation media for Windows 8.1” instructions you found wouldn’t work: they require a Win8.1 key — but your setup still has a Win8.0 key.
Fortunately, that doesn’t matter. You have other, better options!
Your note states that you already have a supply of DVDs on hand. Part 2 of my series tells you how to download a completely free evaluation copy of Win8 and burn it to a blank DVD. The repair/recovery tools on the evaluation copy work exactly the same as those you create locally from the Win8 Recovery Media Creator. Thus, you can use this method to create a legitimate and fully usable repair/recovery disc with absolutely no additional out-of-pocket expense.
Here’s another option that’s free — or nearly so. The Win8.1 Recovery Media Creator is intended to work with inexpensive, basic flash drives. You don’t need a full-blown, spinning-platter drive because the repair/recovery tools occupy only a few hundred megabytes. Very small and cheap flash drives are perfectly fine.
If you have an old, small flash drive rattling around in a drawer someplace, you probably can use that as a Win8 Recovery Drive.
But if you do need a new flash drive, low-capacity models are really cheap. For example, Amazon currently lists a 1GB flash drive for $4.40. And any local electronics retailer (Staples, Best Buy, Target, and so forth) should be able to sell you a basic flash drive, with ample capacity, for under $10.
In short: You’re not stuck at all! You can create a Win8 repair/recovery disc or drive for very little cost — and quite likely for free!
Tips for setting up a new Windows PC
In the first installment of this two-part series, I discussed what to consider when it comes time to replace your old PC.
For Part 2, I review what to do now that you have a new machine — the initial steps for getting the system ready for work.
Starting a new Windows 8.1 system from scratch
The May 8 Best Hardware story, “What to look for when buying a new PC,” covered the relatively easy part of replacing a PC that’s ready for retirement: purchasing the new hardware.
Now that you’ve unboxed the new system and made the physical connections it might need, you’re ready for the hard part: making the right decisions during Windows setup, updating the OS, cleaning out the bundled junk, installing programs, creating separate operating-system and data partitions, and setting up user accounts for maximum safety.
I’m assuming that your new machine has Windows 8.1 — nearly all new PCs do. If you managed to find a new Windows 7 system, much of the following advice — and some of the specific directions — still applies. If you bought a Mac or Chromebook, you’re reading the wrong newsletter.
One initial suggestion: If your old PC still works, keep it handy and connected to the network. You’ll still need it for a bit.
Note: The only PC I own that came bundled with Windows 8.1 is an ASUS Transformer Book T100, a convertible laptop/tablet machine. For this article, I returned it to its fresh-from-the-assembly line condition. The ASUS runs a full version of Win8.1, so its setup process is typical of most new systems. That said, setting up other Windows 8.1 PCs might be slightly different.
Running through the Windows 8 setup wizard
Again, I assume you’ve taken the PC out of the box and made all necessary cable connections (power, plus for desktops the keyboard, monitor, mouse, and Ethernet). The first time you switch on the new machine, Windows will walk you through an initial setup process.
Since you’re probably already familiar with older versions of Windows, I trust you can figure out most of that process yourself. But here are a few suggestions.
Near the beginning of the initial setup, the wizard will offer you the option Use express settings (see Figure 1). You don’t want that! The Customize option takes a bit longer, but it will let you make some important choices.

Figure 1. When first setting up Windows 8.1, use the Customize option for better privacy (see Figure 2).
For instance, for more privacy, I recommend you turn off the following options:
- Let apps use my name and account picture
- Let apps use my advertising ID for experiences across apps

Figure 2. Using the Customize setup option gives you access to various privacy settings.
(I’ll bet you didn’t know you have an “advertising ID.” Welcome to the brave new world of silent online connections.)
When you get to the Set up your account page, you might wish to create a local account — not tied to Microsoft’s online octopus (as is any official MS account). Sorry, Microsoft does not approve of such behavior. You have to use a Microsoft account; if you don’t already have one, you can click Create a new account. You’ll be able to make a local one later.
Get Windows updates and unhide libraries
It might be a new computer, but the operating system is already out of date. You’ll want to fix that immediately.
You have two choices for adding the latest updates: let Microsoft do the update in its own good time, or do it all yourself. Why wait? You can continue to do other things while the updates download and install.
Here again, there are two choices. You can go the Modern route: type “updates” into the charms-bar search box. (New to Win8? Simply start typing “updates” from the Start screen.) Select Install. Click Check for updates and then wait while Windows consults with the MS updates servers. (This step might take some time.) Experienced users will probably want to open the classic Control Panel, select Windows Update, and then click Check for updates. (You can launch the Control Panel quickly by pressing the Windows key + X to open the power-user’s menu.)
After a bit, Windows tells you that updates will happen automatically. If you prefer not to wait, click View details. Check whether Windows 8.1 Update (KB 2919355) is listed; if so, make sure it’s checked. Finally, click or tap the Install button.
Repeat this process after every boot until Updates tells you that there are no further updates.
One more thing: Like Windows 7, Windows 8 uses libraries. But Microsoft hid them — most likely hoping that you’ll put all your files into the company’s OneDrive cloud-storage service. Open the Desktop and then File Explorer (located on the taskbar). Click the View tab, pull down the Navigation pane menu in the upper-left corner, and then select Show libraries.
Clean out the junk installed by the PC vendor
Windows PCs are notorious for coming with a lot of stuff you don’t want. Software companies pay manufacturers to include demo versions of programs, possibly hoping they’ll entice you into buying the real thing.
To be fair, my ASUS arrived pretty clean — if you don’t count the apps that Microsoft includes with every Windows 8.1 installation. But you might not be so lucky.
Keep in mind that Windows 8 runs two entirely different kinds of software: traditional Windows programs and Modern/Metro apps. Each type has its own uninstall tool.
To uninstall traditional programs, start typing “programs and features” into the charms-bar search box. When Programs and Features pops up on the search list, select it. Then right-click the programs you want to remove and select Uninstall or Uninstall/Change.
If there are a lot of programs you want to dump, consider automating that chore with an application such as PC Decrapifier (Figure 3; download page). Free for personal use, it lets you check items on a list of installed programs and then uninstall them all with one click.

Figure 3. PC Decrapifier makes removing unwanted software quick and easy.
Neither of these methods can remove Modern/Metro apps. For those, go to the Search charm, type “uninstall” and select Uninstall apps to free up disk space. Select what you don’t want and click Uninstall.
Install the applications you do want
If your system didn’t come with Windows 8.1 Update installed, and you’re feeling confused by the Windows 8.1 user interface, I’ve got good news for you. First, with Win8.1 Update, you can mostly avoid the tile-based world of the Modern/Metro UI and its full-screen apps. And second, you can install a third-party Start menu program that will make you feel like you’re back with Windows 7.
There are plenty of Start-menu replacements — many of them free. My personal favorite is Classic Shell (site); it feels very much like Windows 7.
Also, you don’t have to install an antivirus program. Windows 8 comes with one built in. But if you feel that a third-party program would offer more protection, I’ll just tell you that in AV-Comparatives’ latest tests (page), Emsisoft, Kaspersky, and Avira all got top marks. Avira has a free product for home use.
Whatever AV app you use, you should supplement it with an on-demand malware scanner such as Malwarebytes Anti-Malware (free and paid; site). As with earlier versions of Windows, run the on-demand scanner weekly to catch malicious software that might have sneaked past your regular antivirus program.
If you use a third-party, cloud-synching service such as Dropbox, iCloud, or Google Drive, now would be a good time to install it and set it up. If you use OneDrive, it’s already installed and probably set up.
Next, install your favorite browser (assuming it’s not Internet Explorer), productivity suite, media player, photo editor, and so forth. You might also want to check out the Windows Secrets ultimate utilities list (page) for other useful apps. Boot your old PC and decide which programs you want to keep using.
Some of the programs still installed on your old PC might object to your using the same license on a different machine. But generally, publishers will let you run their programs on two computers for a few weeks. Eventually, you’ll have to uninstall the program from the older system.
Create separate Windows and data partitions
Data and code don’t belong together. If you keep your libraries and other data files on one partition, and Windows and your installed program on another, you’ll have an easier time protecting them both.
For instance, you can back up your Windows partition — including your other programs — with an image-backup program — and do so only a couple of times a year. Then you can back up your data partition daily with a file-backup program.
I’m not going to give you full instructions because I’ve already done so: see my Jan. 26, 2014, article, “Hard-drive partitioning gives better protection.” But a new computer with Windows 8.1 installed is a somewhat different situation. Keep the following in mind as you follow the article’s instructions:
- You don’t have to do a full backup beforehand. It’s a new computer; you don’t have much to lose.
- That article was written for Windows 7, but it still pretty much works. You may need to type in “disk management” in the Search charm, not the Start menu.
- Since you haven’t yet moved your files onto this PC, you don’t have to hassle with resizing the partitions over and over again.
- Don’t create an image backup just yet. Your Windows partition is still changing.
Set up separate administrator and user accounts
Once you’re signed in as an administrator, you’re more vulnerable to attacks. So it’s best to do most of your work in a standard account — and use the admin account only when you need to.
If you’ve followed my advice so far, you’ve got only one account, and it has admin rights. Now is the time to fix that.
- At the Search charm, type “add” and select Add, delete, and manage other user accounts.
- Click Add an account (Figure 4).

Figure 4. Click Add an account to add another user or account type. You can also use the tool to create a 'local' account.
- To create a local account — again, one not tied to an online MS account — click Sign in without a Microsoft account (not recommended), as shown in Figure 5.
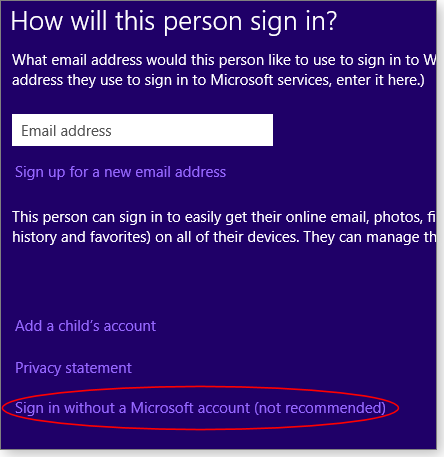
Figure 5. Microsoft discourages users from setting up local user accounts it can't track.
- On the next screen, select Local account (as you marvel at how much Microsoft really doesn’t want you to do this).
- This will bring you to the Add a user screen. Designate the user as “Admin” and give it a unique password that you’ll remember.
- Now change accounts. Return to the Start screen, select your name in the upper-right corner, and click Sign out.
- Log onto the new Admin account and wait until you’re at the Start screen.
- Using the Search charm, type “add” and select Add, delete, and manage other user accounts again.
- Go to the Other accounts tab, select your original account, and then click Edit. Change the account type to Standard User (Figure 6).

Figure 6. For protection from attacks, a PC should have an admin account — for when you need it — and a standard account, for daily computing.
- Log off and return to the original account.
Final chores: Moving your data and backing up
You now need to move your data files from your old computer to the new one. Windows comes with a migration tool, but I stopped using it years ago.
It’s simpler to copy the contents of your libraries manually, with Windows’ familiar drag-and-drop process. The contents of My Documents on your old machine go to the new computer’s My Documents, and so forth. For instance, over your network or using an external drive, drag and drop the contents of your old My Documents folder to the new PC’s My Documents folder. By going through the Documents library, your files will automatically be transferred to the D: partition.
You’ll also want to drag and drop the contents of your %appdata% folder, which is probably located in C:\Users\{yourname}\AppData\Roaming. But you can get to it easily by typing “%appdata%” into either the Desktop’s Start-menu Search field or the Search charm.
Keep the old PC around for a couple of months, along with its data, just in case you missed something.
Make a backup of your new, fully configured PC
Now that the new system is set up mostly the way you want it to be, it’s time to do an image backup of your Windows partition (most likely, C:). Windows 8’s built-in backup program can do this, but I prefer the more versatile EaseUS Todo Backup Free (site).
You’ll also want to set up a daily file backup routine for your data partition (probably D:). See the March 6 article, “Simple ways to back up your most precious files,” for suggestions.
Congratulations! You’ve now got a safe, convenient, and workable PC. Now get back to work.
The rapid-fire updates for Office 2013 continue
May updates highlight the ongoing vulnerabilities in XP and the continuing push to move Windows 8.1 users to Win8.1 Update.
I’m changing the rules on .NET updates. Windows 8 and Office 2013 users will see another heavy batch of updates; concentrate on the security updates and leave most of the nonsecurity fixes for later.
MS14-029 (2953522, 2961851)
Warm up with the monthly Internet Explorer fix
For Vista, Win7, and Win8 users, KB 2953522 and KB 2961851 are the usual monthly updates for IE. In this instance, the patches fix two new vulnerabilities in IE. Both patches are rated critical for Windows workstations.
For XP users, it’s another reminder that the use of IE is becoming only more dangerous. There are no XP updates for IE — nor will there be for the general public. XP systems are clearly becoming more vulnerable to drive-by attacks via Web browsers.
If you’re still running XP and must go online with IE, I suggest making the following settings changes. Be aware that these are noisy settings — they’ll probably drive you crazy with popup warnings.
- In Internet Explorer, click Internet Options on the Tools menu.
- Click the Security tab.
- Click Internet and then click the Custom level button.
- In the Settings list, scroll down to Scripting (it’s near the bottom of the list) and, under Active scripting, click either Disable or Prompt (see Figure 1). Then click OK.

Figure 1. In IE on XP, set Active scripting to Prompt or Disable for better security.
- Now click Local intranet and then click Custom level.
- In Settings, again scroll down Scripting/Active scripting and click either Disable or Prompt. Click OK.
- Click OK to return to Internet Explorer.
For supported versions of Windows, keep in mind that this is not a cumulative security update. Be sure you’ve installed the earlier updates released in MS14-018 (IE 6, 7, 8, and 10) or MS14-012 (IE 11).
 What to do: Install KB 2953522 and/or KB 2961851 (MS14-029) as soon as possible.
What to do: Install KB 2953522 and/or KB 2961851 (MS14-029) as soon as possible.
MS14-024
Common controls bugs result in Office fixes
Once again, Microsoft is patching a set of Office controls called MSCOMCTL.OCX. This binary is included with a number of Microsoft products and provides a common set of ActiveX controls.
Due to past problems with line-of-business apps, I’m going to err on the side of caution; I suggest holding back on the update that patches MSCOMCTL — specifically, KB 2817330 for Office 2007, KB 2810073 for Office 2010, and KB 2880502 for Office 2013. The other updates are fine.
Line-of-business apps seem particularly vulnerable to MSCOMCTL updates. When you test it on your systems, expect an error message that MSCOMCTL.OCX can’t be loaded, as noted in a 2010 Stack Overflow forum thread. Because this security issue is not likely to be exploited directly for code execution, I’m going to be overly cautious and wait to see that there are no issues before giving the all-clear.
The patches in MS14-024 are all rated important and include:
- KB 2589288 – Office 2010 (install)
- KB 2596804 – Office 2007 (install)
- KB 2760272 – Office 2013 (install)
- KB 2810073 – Office 2010 (wait)
- KB 2817330 – Office 2007 (wait)
- KB 2880502 – Office 2013 (wait)
- KB 2880507 – Office 2007 (install)
- KB 2880508 – Office 2007 (install)
- KB 2880971 – Office 2010 (install)
 What to do: If you have a critical line-of-business application running, install only the approved patches listed above if offered. See MS14-024 for more information. Workstation users running common applications can install any of the above updates offered.
What to do: If you have a critical line-of-business application running, install only the approved patches listed above if offered. See MS14-024 for more information. Workstation users running common applications can install any of the above updates offered.
MS14-027 (2926765, 2962123)
Windows Shell attacks used in common malware
The vulnerability in the Windows Shell is relatively minor for most versions of Windows. Attackers could use a malicious application to exploit the flaw, but they must be able to sign in locally to a system. Moreover, the exploit has already been used in common forms of malware, so it will most likely be blocked by up-to-date antivirus software. For those reasons, the update is rated just important.
That said, Windows XP is once again without a patch. If you’re planning to go online on an XP system, be sure to have a strong, paid version of AV software. Don’t rely on free products. It might also help to use a browser other than Internet Explorer.
 What to do: Install KB 2926765 or KB 2962123 (MS14-027) when offered.
What to do: Install KB 2926765 or KB 2962123 (MS14-027) when offered.
MS14-023 (2767772, 2878284, 2880463, 2878316)
The LoadLibrary gift that keeps on giving
Way back in August 2010, Security Advisory 2269637 described the growing problem of DLL-preloading attacks. The exploits were first found by a company investigating Apple iTunes on Windows security issues. But the vulnerability was soon found in some of Microsoft’s own products. If you’d like to refresh your memory on this topic, check out the Sept. 9 Top Story, “A threat to common ‘.dll’ files hits many apps.”
Four years later, we’re still receiving fixes for DLL preloading exploits. In this case, one of the fixes is for a .dll used by a Chinese grammar checker in Office. If you have this proofing tool installed, you’ll see KB 2767772 for Office 2007, KB 2878284 for Office 2010, or KB 2880463 for Office 2013. The patches are all rated important.
The Office 2013 patch, KB 2878316, also includes a fix for Microsoft online services. An attacker could trick his victim into unknowingly handing over authentication tokens.
 What to do: Install the appropriate update in MS14-023 as soon as offered.
What to do: Install the appropriate update in MS14-023 as soon as offered.
MS14-026
My updating policy on .NET Framework evolves
With official XP support ended, Microsoft no longer releases .NET patches for XP systems. That might be a blessing in disguise: .NET has always been problematic on XP. Updates too often required uninstalling and reinstalling .NET.
But on newer versions of Windows — those running .NET 3.5, 4, or 4.5 — .NET updates are much better behaved. So breaking with tradition, I’m recommending that Vista, Win7, and Win8 users install the .NET patches in MS14-026 when offered. The update is rated important and patches a new elevation-of-privilege vulnerability.
XP users should keep in mind that they’re going to be vulnerable to new .NET exploits. Unfortunately, I have no viable workarounds. However, the exploit fixed by this particular patch leverages .NET Remoting, which is rarely used.
 What to do: Install the offered .NET updates included in MS14-026.
What to do: Install the offered .NET updates included in MS14-026.
2871997
Reducing threats to corporate sign-in creds
Hackers often attack enterprises by finding credentials stored as hash values. Intruders can then use stolen hash values to access servers and resources that they normally could not access. Called “pass the hash” (more info), this form of exploit lets attackers gain toeholds into corporate networks. Cyber thieves can then steal customer credit-card information and other sensitive data.
When Microsoft designed Windows 8.1, it added code to protect from this type of network attack. KB 2871997 backports these protections to Windows 7 and 8 by making the Local Security Authority component more secure.
On peer-to-peer networks — such as a home network — the update is optional. However, in business-based domain settings, I recommend admins read more on pass-the-hash attacks — especially if you work for or with potentially targeted institutions such as defense contractors or those that keep large databases of credit-card information.
 What to do: Home-network users — or anyone who doesn’t sign into a domain — can pass on KB 2871997. Those who do sign into a corporate domain should install the update when offered.
What to do: Home-network users — or anyone who doesn’t sign into a domain — can pass on KB 2871997. Those who do sign into a corporate domain should install the update when offered.
2952664
Take a pass on upgrade compatibility updates
If you’re running Windows 7 and considering upgrading to Windows 8.1, Microsoft has pushed out KB 2952664 to make the transition smoother. But I think you’re better off installing Win8.1 as a clean installation — not as an in-place upgrade.
 What to do: I recommend that Win7 users take a pass on KB 2952664 — and any future compatibility updates for in-place upgrades to Win8.1.
What to do: I recommend that Win7 users take a pass on KB 2952664 — and any future compatibility updates for in-place upgrades to Win8.1.
2919355
A reprieve from KB 2919355 for Win8.1 users
As has been widely reported, Microsoft put an unusually abrupt deadline on Windows 8.1 users: they need to move up to Win8.1 Update by May 13, or they’ll no longer get Windows security updates.
But after receiving a flood of criticism from customers, Microsoft pushed the deadline for enterprises to August. And then early this week, it announced that consumers now have until June 10 to install KB 2919355 — the update that adds Win8.1 Update. (Could MS have given this latest tweak to Windows 8 a more confusing name?)
Microsoft repackaged KB 2919355 with a fix for an all-too-common servicing stack–corruption failure. But not all problems with the Win8.1 Update update have been fixed. Some Win8.1 users have had to reinstall the operating system — a far-from-acceptable solution.
If you’ve installed KB 2919355 and discover that your PC will no longer go into sleep mode, install update KB 2965065; it should show up under the Optional tab in Windows Update.
 What to do: If you’re still struggling with KB 2919355, take some consolation in knowing you’re far from alone. Post a description in the Windows Secrets Lounge of what’s failing when you try to install Win8.1 Update. I will try to respond.
What to do: If you’re still struggling with KB 2919355, take some consolation in knowing you’re far from alone. Post a description in the Windows Secrets Lounge of what’s failing when you try to install Win8.1 Update. I will try to respond.
MS014-022, MS014-025, MS014-028
Three updates of interest to admins
The following three patches should not show up on Windows workstations.
Rated critical, MS14-022 (2952166) fixes multiple, privately-reported vulnerabilities in SharePoint Server 2007, 2010, and 2013. If you’re running SBS 2011, don’t forget to manually run the psconfig command (more info) after installing these updates.
Rated important, MS14-025 (KB 2928120 and KB 2961899) applies to most supported versions of Windows. It fixes a potential exploit in Group Policies preferences when passwords are distributed via Active Directory Group Policies preferences, or if network Remote Server Administration Tools are installed on a Windows workstation.
Also rated important, MS14-028 (2962485) patches a Windows Server vulnerability in the iSCSI storage protocol that could lead to denial-of-service attacks. The patch is for Windows Storage Server 2008, Storage Server 2008 R2, Windows Server 2012, and Server 2012 R2.
 What to do: Network admins should install these updates after appropriate testing.
What to do: Network admins should install these updates after appropriate testing.
Nonsecurity updates to leave for later
Given the ongoing fixes for Windows and the many patches for Office 2013, I think it’s especially important to install security and nonsecurity updates separately. Once I’ve had a chance to see these various fixes for Office 2013, I’ll report my findings in the Windows Secrets Lounge around May 26.
As Figures 2 and 3 show, Windows 8 and Office 2013 users are still receiving a weighty bundle of patches. Figure 4 shows the May updates for an XP system.
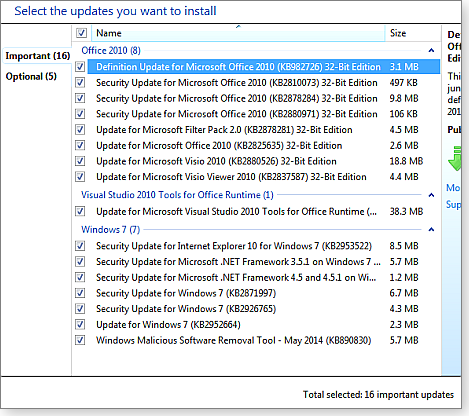
Figure 2. May's security and nonsecurity updates for a typical Windows 7 system

Figure 3. A Windows 8 system with Office 2013 has nearly a gigabyte of updates.

Figure 4. With the end of official XP support, there's just one XP update in May.
Put the following on hold for now:
- KB 2852386 – A Windows update clean-up tool for Win7 and Win Server 2008 R2 SP1
- KB 2920540 – Stop error for sysprep issue
- KB 2932074 – Win8 app launcher for Windows Embedded 8.1 devices
- KB 2932354 – Update for Embedded Lockdown Manager
- KB 2934950 – Client backup to Home Server/SBS 2011 Essentials fails after installing .NET patch
- KB 2938459 – Win8 Windows Communication Apps
- KB 2939153 – Windows Defender for Win8
- KB 2950153 – Windows Update Standalone Installer freezes when Win8.1 update installed
- KB 2954879 – .NET Native on Win8.1
- KB 2955163 – May rollup for Win8
- KB 2955164 – May rollup for Win8.1
- KB 2956037 – Update randomizes Device Setup Manager task-creation time
- KB 2956575 – Win8.1 Store and Windows Update improvements
- KB 2958262 – Win8.1 compatibility
- KB 2962824 – UEFI rollup; update troublesome on HyperV servers and some systems with noncompliant Unified Extensible Firmware Interface modules
General Office stability and performance fixes:
- KB 2825635 – Office 2010
- KB 2863819 – Outlook 2010
- KB 2817302 – Office 2013
- KB 2826040 – Office 2013
- KB 2837644 – Office 2013
- KB 2878319 – Word 2013
- KB 2880455 – Word 2013
- KB 2880461 – Office 2013
- KB 2880462 – Office 2013
- KB 2880464 – Office 2013
- KB 2880466 – Office 2013
- KB 2880470 – Outlook 2013
- KB 2880475 – Excel 2013
- KB 2880476 – Office 2013
- KB 2880478 – Office 2013
- KB 2880480 – OneDrive for Business
- KB 2880482 – Office 2013
- KB 2880980 – MS Lync 2013
Miscellaneous other fixes:
- KB 2726952 – Publisher 2013 – Stability and performance
- KB 2837587 – Visio Viewer 2010 – Stability and performance
- KB 2878281 – MS Filter Pack 2.0 – Stability and performance
- KB 2878315 – PowerPoint 2013 – Fixes various display errors
- KB 2880526 – Visio 2010 – Latvian/Euro currency fix
 What to do: Wait for my update on these nonsecurity fixes.
What to do: Wait for my update on these nonsecurity fixes.
Regularly updated problem-patch chart
This table provides the status of recent Windows and Microsoft application security updates. Patches listed below as safe to install will typically be removed from the table about a month after they appear. Status changes are highlighted in bold.
For Microsoft’s list of recently released patches, go to the MS Security TechCenter page. See our “Windows Secrets master Patch Watch chart” post for a more extensive list of recent updates.
| Patch | Released | Description | Status |
|---|---|---|---|
| 2862973 | 02-11 | MD5 deprecation; skip on workstations, optional for admins | Skip |
| 2934207 | 03-11 | XP end-of-support warning | Skip |
| 2862330 | 01-14 | Reissued kernel fix; ongoing USB issues | Hold |
| 2961033 | 05-13 | Common controls; using line-of-business apps, KBs 2810073, 2817330, 2880502; see MS14-024 | Wait |
| 2871997 | 05-13 | Enhancements to Local Security Authority | Optional |
| 2952664 | 05-13 | Migration compatibility | Optional |
| 2923392 | 03-11 | Security Account Manager on servers; also, KB 2933528 | Install |
| 2925418 | 03-11 | Internet Explorer cumulative security update | Install |
| 2929961 | 03-11 | Windows DirectShow | Install |
| 2930275 | 03-11 | Kernel-mode driver update | Install |
| 2932677 | 03-11 | Silverlight | Install |
| 2919355 | 04-08 | Windows 8.1 Update; May 13 deadline to install | Install |
| 2922229 | 04-08 | Windows file handling | Install |
| 2936068 | 04-08 | Cumulative IE patch; also KB 2929437 for IE 11 for Win7 | Install |
| 2949660 | 04-08 | Word zero-day; see MS14-017 for complete list | Install |
| 2950145 | 04-08 | Publisher; KB 2817565 (2007) and KB 2878299 (2003) | Install |
| 2926765 | 05-13 | Windows Shell; also, KB 2962123 | Install |
| 2928120 | 05-13 | Group Policies preferences; for admins, also KB 2961899 | Install |
| 2933826 | 05-13 | Windows Server; for admins; also, KB 2962073 | Install |
| 2952166 | 05-13 | SharePoint; for admins; see MS14-022 for complete list | Install |
| 2953522 | 05-13 | Internet Explorer; also, KB 2961851 | Install |
| 2958732 | 05-13 | .NET; see MS14-026 for complete list | Install |
| 2961033 | 05-13 | Common controls; basic workstations; see MS14-024 for complete list | Install |
| 2961037 | 05-13 | MS Office; KBs 2767772, 2878284, 2880463, 2878316; see MS014-023 | Install |
Status recommendations: Skip — patch not needed; Hold — do not install until its problems are resolved; Wait — hold off temporarily while the patch is tested; Optional — not critical, use if wanted; Install — OK to apply.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
DBOS Advanced Network Analysis
by
Kathy Stevens
33 minutes ago -
Microsoft Edge Launching Automatically?
by
healeyinpa
1 hour, 16 minutes ago -
Google Chrome to block admin-level browser launches for better security
by
Alex5723
3 hours, 13 minutes ago -
iPhone SE2 Stolen Device Protection
by
Rick Corbett
3 hours, 56 minutes ago -
Some advice for managing my wireless internet gateway
by
LHiggins
25 minutes ago -
NO POWER IN KEYBOARD OR MOUSE
by
HE48AEEXX77WEN4Edbtm
4 hours, 51 minutes ago -
A CVE-MITRE-CISA-CNA Extravaganza
by
Nibbled To Death By Ducks
12 hours, 43 minutes ago -
Sometimes I wonder about these bots
by
Susan Bradley
9 hours ago -
Does windows update component store “self heal”?
by
Mike Cross
1 day, 1 hour ago -
Windows 11 Insider Preview build 27858 released to Canary
by
joep517
1 day, 2 hours ago -
Pwn2Own Berlin 2025: Day One Results
by
Alex5723
1 day, 2 hours ago -
Windows 10 might repeatedly display the BitLocker recovery screen at startup
by
Susan Bradley
22 hours, 35 minutes ago -
Windows 11 Insider Preview Build 22631.5409 (23H2) released to Release Preview
by
joep517
1 day, 5 hours ago -
Windows 10 Build 19045.5912 (22H2) to Release Preview Channel
by
joep517
1 day, 5 hours ago -
Kevin Beaumont on Microsoft Recall
by
Susan Bradley
17 hours, 58 minutes ago -
The Surface Laptop Studio 2 is no longer being manufactured
by
Alex5723
1 day, 13 hours ago -
0Patch, where to begin
by
cassel23
1 day, 7 hours ago -
CFPB Quietly Kills Rule to Shield Americans From Data Brokers
by
Alex5723
2 days, 3 hours ago -
89 million Steam account details just got leaked,
by
Alex5723
1 day, 14 hours ago -
KB5058405: Linux – Windows dual boot SBAT bug, resolved with May 2025 update
by
Alex5723
2 days, 11 hours ago -
A Validation (were one needed) of Prudent Patching
by
Nibbled To Death By Ducks
2 days, 2 hours ago -
Master Patch Listing for May 13, 2025
by
Susan Bradley
1 day, 13 hours ago -
Installer program can’t read my registry
by
Peobody
6 hours, 36 minutes ago -
How to keep Outlook (new) in off position for Windows 11
by
EspressoWillie
2 days ago -
Intel : CVE-2024-45332, CVE-2024-43420, CVE-2025-20623
by
Alex5723
2 days, 7 hours ago -
False error message from eMClient
by
WSSebastian42
2 days, 22 hours ago -
Awoke to a rebooted Mac (crashed?)
by
rebop2020
3 days, 7 hours ago -
Office 2021 Perpetual for Mac
by
rebop2020
3 days, 9 hours ago -
AutoSave is for Microsoft, not for you
by
Will Fastie
6 hours, 41 minutes ago -
Difface : Reconstruction of 3D Human Facial Images from DNA Sequence
by
Alex5723
3 days, 12 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

