
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Going green with Win7 is harder than it looks
In this issue
- TOP STORY: Going green with Win7 is harder than it looks
- LOUNGE LIFE: Looking to the Lounge for a cheap photo editor
- WACKY WEB WEEK: Dunkin' Donuts is whispering in your ear
- LANGALIST PLUS: Use Windows System Restore with caution
- BEST SOFTWARE: How much security software do you really need?
- PATCH WATCH: Have your Windows Mail and Windows 7, too
Going green with Win7 is harder than it looks
 By Susan Bradley
By Susan Bradley
Trying to consume less energy in a home office by putting workstations to sleep automatically seemed like the right thing to do.
But when two Windows 7 PCs developed insomnia, returning them to a greener state let me discover some interesting tricks and tips.
It started about five months ago. I looked at what we contributed annually to the local utility company and was not pleased. It was time to look at ways to cut our power consumption.
The first step was to calculate how much power we were actually using, in real numbers. To that end, I purchased a Kill a Watt device (info page), which tests and tracks the amount of energy computers and other household appliances use. Costing less than U.S. $30, this small box sits between an electrical device’s power plug and your wall outlet.
I discovered that, on average, I spent about $200 a year just to power my office PC, monitor, and printer if I leave them on all the time. Enough to make researching energy-saving techniques worthwhile.
However, simply turning those devices off was not the perfect solution. Sometimes I’m out of my office and need to access my workstation PC. Rather than leave it on, I want it to wake up when I sign in remotely.
This capability is called Wake-on-LAN (WOL) — a technology found in most of today’s network cards and a key component to my energy-saving plans.
To determine whether your PC supports WOL, click Settings, Control Panel, and then Network Connections (or the Network and Sharing Center in Win7). Click Local Area Connection, Properties, and then Configure (near the box listing the network card name). There should be a Power Management tab; if so, look for a checkbox labeled Allow this device to wake the computer or something similar. (See Figure 1.) Checking the box should ensure that a received Wake-on-LAN network packet will power up the computer.

Figure 1. Check for Wake-on-LAN capabilities in your network card’s configuration settings.
Home Server wakes up your office network
Controlling when PCs wake up and go to sleep gets complicated when you want to remotely sign into more than one system on your network. One solution is a good remote-access application such as logmein.com. My solution was to purchase an HP server with Windows Home Server (WHS) installed. An accessory app, Wake on LAN Add-in for WHS (download page), lets me remotely access the server and use it to wake up the workstations; it costs U.S. $20.
While the wake-up part was relatively easy, getting the PCs to consistently and automatically go back to sleep proved far more challenging — nearly impossible, in fact — which was surprising, given Win7’s enhanced power-management controls.
According to the advice on many Web sites, disabling the network card’s Wake-on-LAN control is the best way to ensure a PC goes to sleep automatically — good advice for a simple home PC setup. But since I needed Wake-on-LAN for remote access and so that Windows Home Server could automatically back up my workstations each night, that trick was out.
I’ve also found that using USB devices can make the computer suddenly stop dropping into sleep mode even after going to sleep for weeks. My fix is to either reboot the system or manually put it to sleep.
When any PC’s automatic-sleep mode proves unreliable, my first step is to confirm that the BIOS is up-to-date. (Surprisingly, I’ve had to flash the BIOS on Vista and Win7 systems more often than on any preceding OS.) I next check that the network adapter drivers are current.
In the case of my Windows 7 machines, the last stop was the PCs’ power-management settings, where I selected the Power Saver option.
I also applied the hotfix described in Microsoft Support article 981112, which may fix a known sleep-mode problem — sleep mode and hibernation fail when you have Windows Media Player is installed and media-sharing is not turned on. (There’s a hotfix I didn’t need, but you might if you’re running Win7 and have a biometric device attached. According to MS Support article 975599, you could receive a system Stop error when you try to put the machine into sleep or hibernation.)
Discover what sleep modes your PC uses
To test what sleep modes are enabled on your system, do the following:
In Win7, click Start, All Programs, and Accessories. Right-click Command Prompt and select Run as administrator. In the Command Prompt window, type powercfg -a and press the Return key.
There are six power modes, S0 (fully on) through S5 (fully off). Labels such as standby and sleep are used interchangeably by different vendors, so are not a precise guide to identifying the mode you’re using. To save power, you might use any of the following:
- S1 is closest to fully up and running — the PC simply powers down the hard drive and monitor. Hit a key, and the system is instantly ready for work.
- S2 is power standby mode — the PC is on and maintaining full power to the RAM, thus preserving your open applications and data, but the CPU is essentially inactive.
- S3 maintains just enough power to keep the information in RAM from being lost. Standby takes a bit longer to restart than does Sleep.
- S4 (Hibernate) saves the state of the computer system (running programs and applications to a file on your hard drive and then powers off. Because the PC’s state is saved on the hard drive, shutdown and restart take longer. But you’re using almost no power. (Modern PCs are almost never completely off.)
When my system fails to go to sleep, I run an energy report to let me know exactly what device is keeping the system awake. You can create the report with the following steps:
Launch the Command Prompt window as described above. Type in powercfg /energy and let the system run the test for 60 seconds. (See Figure 2.)

Figure 2. You can generate a report of your Win7’s energy use with a Command Prompt control.
Look for the test results in a file called energy-report.html, located in the c:Windowssystem32 folder, and open it in a browser.
In that report, scroll down to the error section and you can see the sort of devices that are keeping your system from going to sleep. In my case it tends to be after I’ve connected USB devices (such as an iPhone or Zune) to my workstation. I have yet to figure out why it happens.

Figure 3. Windows 7’s “energy-report.htmlText report” can tell you why your PC will not go into sleep mode.
I have two techniques for forcing my errant PCs to sleep: I reboot the workstation (which is a pain), or I manually make the workstation go into sleep mode. There are three ways to do this in Win7, but the easiest is to hit the Windows key, click the right-arrow next to the Log off button, and select sleep mode. After that, automatic-sleep mode works as it should when I end my remote-access sessions.
I also fine-tuned my power requirements on the various Vista and Win7 computers, following these steps:
Click Start, Control Panel, and then Power Options. Choose Power Saver and customize the settings for the length of time you want the system to stay on after you’ve finished using the computer. Then go to the advanced power settings and select Hybrid Sleep. This mode of sleep ensures that I will not lose any documents I forgot to save.
You can see other custom settings as documented on the Windows 7 power-plan settings forum at Windows SevenForums.
For now, automatic-sleep mode is still so unreliable that I take the extra steps of forcing my computer into sleep — even at the end of remote access. I’m hoping that the upcoming Windows 7 Service Pack 1 will help to solve my issues. Until then, the bother of sleeping is worth the power and cost savings I get.
| Have more info on this subject? Post your tip in the WS Columns forum. |
Susan Bradley recently received an MVP (Most Valuable Professional) award from Microsoft for her knowledge in the areas of Small Business Server and network security. She’s also a partner in a California CPA firm and writes the Windows Secrets Patch Watch column.
Looking to the Lounge for a cheap photo editor
By Tracey Capen
Serious digital photographers spend an inordinate amount of time working with their photo-editing application — usually Photoshop, if they can afford it.
For those who can’t (or for whom Photoshop is just too complicated), there is endless debate about what’s second-best.
That was the question posed by Lounge member rfe777. Is it Photoshop Elements, or PaintShop Photo Express, or one of the many small-but-useful and free image-editing apps? The answers show that there is no consensus on this question, though many think GIMP is worth a try. More»
The following links are this week’s most-interesting Lounge threads, including several new questions that you may be able to provide responses to:
☼ starred posts — particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right in to today’s discussions in the Lounge.
The Lounge Life column is a digest of the best of the WS Lounge discussion board. Tracey Capen is technical editor of WindowsSecrets.com.
Dunkin' Donuts is whispering in your ear
 |
By Stephanie Small
Advertisements are everywhere in today’s world. With billboards, televisions, the radio, and even our reading material bombarded with ads pushing product, it’s only a matter of time before they find their way into our cell phone conversations. Or has it already? In this amusing Onion News short, we observe the Google phone and its abundance of product-pushing adverts. Key words become the catalyst for what may be the most-annoying form of promotions ever … Play the video |
Use Windows System Restore with caution
 |
By Fred Langa
Window’s System Restore is a good, basic safety net for solving system problems, but what it doesn’t do will surprise you. To use Windows’ system backup tool most effectively, you need to know its limitations — and have other recovery tools readily at hand. |
System Restore is only a Band-Aid backup method
System Restore — in Windows XP, Vista, and Win7 — has always been a good news–bad news recovery tool. Fortunately, reader Mel Rocklin’s recent experience was positive:
- “I recently had strange stuff happen on my PCs. My normal approach is to Google the problem and read articles until one suggests a solution.
“But after several days of searching and not finding a solution that worked on my computers, I was ready to give up, format the drive, and reinstall Windows from scratch.
“As a last resort, I used Windows Restore and chose a restore point dated prior to the problems’ surfacing. Lo and behold, after completing the restore, both computers were back to normal. For further information on Restore, see this Microsoft article.
“I would highly recommend to all Windows Secrets readers to try System Restore before resorting to a reformat. In the future, I’ll restore even before I try any other problem-solving approach!”
Glad it worked, Mel!
System Restore (SR) is mainly a way to back up and restore a limited set of essential Windows system files. When all that’s wrong is a glitch in a system file, SR can often set things right. But it’s also important to know what SR cannot do, because its limitations are severe.
If you want detailed information on SR from its launch in XP through its current form in Windows 7, the MSDN tutorial, “System Restore,” is a good place to start.
Most of us don’t need that level of detail, so I’ll give you the essential, need-to-know stuff. System Restore varies somewhat from one edition of Windows to another, but all SR versions monitor and back up the following items (the links go to Microsoft pages that provide additional details):
- The Windows Registry (MS Support article 256986)
- Windows File Protection files in the Dllcache folder (MS Support article 222193)
- COM+ (MSDN library page) and WMI Databases (MSDN page)
- The IIS Metabase, which holds Internet Information Services settings (MS TechNet page)
- System files with extensions such as .exe, .dat, and many more listed on an MSDN library page
- The local user profile settings
Compared to the pre-XP versions of Windows (which automatically backed up exactly nothing), SR’s list of protections is impressive.
What it doesn’t restore: System Restore does not back up and restore non-system files or third-party software (nor any changes made by these apps). It doesn’t touch your data files or any other files that are not essential to getting Windows running.
It also won’t clean up files left over by a failed software install (a common cause of mangled system files), and you can’t use SR to selectively restore accidentally erased files that you now want back.
Make no mistake: SR is not, repeat not, a substitute for a full backup.
With an up-to-date, complete system backup, you can restore everything that System Restore covers plus all your data files, all your settings, all third-party software — everything.
Full-backup systems also let you selectively restore just the files you need. Or, with a complete restore, they can eliminate all munged files or leftover bits caused by crashes or failed installs. Unlike SR, a true backup system can roll back your entire system — not just selected system files — to a pre-trouble state.
So yes, SR is a good tool for a limited set of emergency recoveries. But if you’re relying on SR as your main recovery tool, you’re not well protected.
Other recovery tools: You may already have all the tools you need for total protection. Here’s a rundown of Windows’ backup options:
XP has earlier versions of two tools: System Restore and the simple, file-oriented Backup utility. Not all versions of XP have Backup installed by default; if you can’t find it on your system, look for a free third-party product. I’ve listed a couple of sources at the bottom of this item.
For more on the MS Backup utility, see the Kelly’s Korner article, “System Backup for Windows XP,” or the Microsoft tutorial, “Windows XP Backup Made Easy.”
Vista’s Business, Ultimate, and Enterprise editions have a Backup and Restore Center that offers three options:
- System Restore
- The file-oriented Automatic Backup, which includes scheduled backups
- System Image backup
The little-used versions of Vista offer less: Vista Home Premium has a file-oriented backup and System Restore; Vista Home Basic has only System Restore.
For more information on Vista’s tools, see Microsoft’s article, “Explore the features: Windows Backup and Restore Center,” and BleepingComputer.com’s how-to page.
Windows 7 has the most-complete recovery options ever built into Windows. It has all of Vista’s tools plus a new Previous Version feature, which you can use to restore files and folders you changed or deleted. It’s like an always-on, short-term mini-backup!
For more information on all these, see Microsoft’s Win7 general backup FAQ; a tutorial on Win7’s backup and restore tool; and an MS article on how to restore from a system image.
Although Win7 has finally built in all the basic backup tools most users are likely to need, there are numerous third-party alternatives available for all versions of Windows. Check out CNET’s compilation of backup software or MakeUseOf’s list.
So, Mel, it’s great that you discovered System Restore, but don’t stop there! Supplement it with other backup tools, and you’ll be able to recover from just about any kind of software or data-loss problem.
Now, that’s peace of mind!
Essentials story generates lots of feedback
My May 6 Top Story on Microsoft Security Essentials (the new, free antivirus/anti-malware tool for Windows) brought a lot of mail, including this item and the next one.
First, Anita L. writes:
- “I am intrigued by the information in Fred’s article, but I am still running XP. Will I be able to use MSE on XP?
“If I get a new Windows 7 machine, will it already have MSE loaded on it, or will I still need to download it?
“Thanks for keeping us safe and up-to-date!”
Yes, Anita, Microsoft Security Essentials works on XP, Vista, and Win7. Microsoft publishes the full system requirements on the MSE download page. MSE isn’t yet bundled with any version of Windows, but you can use that same link to download it.
How do you put 1.5TB of storage on your laptop?
Bill was surprised by part of the test setup in my Microsoft Security Essentials article.
- “Fred Langa’s test of MSE stated that he used a 1.5TB laptop. I would like to know how he was able to buy a 1.5TB drive in a laptop!”
The laptop has 500GB (.5TB) of internal storage, and a 1TB external USB drive.
All my essential stuff is on the internal hard drive, so the laptop is self-contained and portable — as it should be. But the 1TB external drive simplifies backups and drive imaging; gives me access to a large, static library of software (e.g., ISO copies of my setup and installation CDs and DVDs); and so on.
If you’re hungry for disk space, note that external drives are almost unbelievably inexpensive now. Many drive vendors repackage their new-but-no-longer-top-of-the-line internal drives into external housings. There’s nothing wrong with these brand-new, never-used drives at all, except that they’re no longer cutting-edge technology.
A hard drive’s speed isn’t critical in USB applications because the USB connection itself is usually the limiting factor. (Almost any current hard drive can exceed the throughput speed of USB.)
A quick search turned up 80 vendors selling 1TB external USB drives for under $100. The current best price I can find right now is $75, or less than eight cents per gigabyte — a spectacular bargain!
Laptop, desktop, whatever: You’ll be hard-pressed to find more-affordable storage than that!
3G Wireless security has same rules as Wi-Fi
Mark Mailloux wonders whether he needs additional security software when he’s online via 3G/GSM (Global System for Mobile communications).
- “I currently use an AT&T USB wireless (GSM or Wi-Fi) card to connect to the Internet. When I’m using this connectivity, can other wireless users connect to my PC? If so, I assume I’d have to enable whatever firewall software I have, right? Having trouble getting a straight answer elsewhere.”
GSM is a set of cellular telephony and data communications standards — it’s the method by which your mobile device communicates with your carrier’s antenna. Aside from encrypting your transmitted data, GSM has nothing to do with securing your files and operating system once you’re online. (See GSMWorld’s GSM info page.)
Here’s a good rule of thumb to remember: It doesn’t matter how you connect to the Internet — dial-up, DSL, cable, fiber, corporate line, Wi-Fi, packet radio, GSM, or tin cans and string — you still need a firewall and malware protection.
In short, once you’re online by any means, you’re potentially vulnerable.
| Have more info on this subject? Post your tip in the WS Columns forum. |
Fred Langa is a senior editor of the Windows Secrets Newsletter. He was formerly editor of Byte Magazine (1987–91), editorial director of CMP Media (1991–97), and editor of the LangaList e-mail newsletter from its origin in 1997 until its merger with Windows Secrets in November 2006.
How much security software do you really need?
 |
By Ian “Gizmo” Richards
Yes, the Internet can be a dangerous place. But use smart computing practices and the right security products, and you can reduce your risk to very low levels. What may surprise you is that safe Web browsing needn’t require very many computer security products, and you can put together an effective defense without spending a cent. |
Break the security-industry-centric mentality
Security product vendors want you to believe that the only sure way to ward off malicious Web attacks is to load your PC to the gunnels with security products — theirs, of course.
I believe the vendors are abetted by some security experts and members of the computer press who have a vested interest in encouraging a climate of fear and promoting a blind belief in technological overkill.
They have been very effective in this mission. It’s now common for a typical PC to have four or more security products installed — not just antivirus scanners, but complex firewalls, anti-spyware programs, anti-Trojan programs, rootkit detectors, behavioral detectors, and the like. Ultimately, it’s a road to nowhere; it’s complex and expensive and can slow your computer to a crawl.
What’s worse, all that protection is not as effective as vendors would have you believe. They’re fond of quoting test results that show detection rates approaching 100%. For example, AV-Comparatives’ most-recent on-demand tests rating signature-file detection (listed on the company’s Main-Tests page), gave scores of 96.6% for Microsoft Security Essentials, 98.9% for McAfee, and 98.6% for Norton.
However, these figures most often apply to malware that’s already known. The detection rates for brand-new malware are much lower. In AV-Comparatives’ November 2009 proactive/retrospective tests, the heuristic detection rates for the major AV programs ranged from 32% to 74%. The popular Norton AV managed only 36%, while McAfee AV achieved 47%.
For specially crafted malware such as that used to steal financial information, the figures are worse. The Malware Research Group recently tested how well security applications stopped malware that targets online banking transactions. The results, published in a PDF-based report, noted that “… having an up-to-date antivirus only reduces the chance of infection [from financial malware] by about 25%.”
This is not to say security software is useless — it’s useful and necessary. But twice as much security software doesn’t make you twice as secure. In fact, no amount of piled-on security software will, by itself, ever make your PC 100% secure.
There’s no such thing as total security
The idea of perfect computer security is a myth. It’s no different from your home security. No matter how many locks, alarms, and other security aids you install in your home, a skilled thief can still break in. It is fantasy to believe otherwise.
We’ve learned to live with less than 100% physical security for our homes, and now we need to do the same with computers. The first step is to set aside the claims and promises made by those who sell security products, as well the often self-serving advice of security experts.
You need to start thinking about defending your computers in the same way you protect your house. You don’t leave home with the front door wide open, and you balance the level of security — burglar alarms, for example — against cost and inconvenience.
Think of your computer security the same way. Act responsibly and consider whether the benefits of AV products outweigh their cost and maintenance.
The biggest security risk isn’t the Web, but us
No security product can protect you from the greatest security risk of all — you, the PC user.
In a Computerworld report, a Trend Micro researcher stated that around 63% of all computer infections stem from downloading and installing infected files. Some of the malware embedded in these files is so potent that it can overcome just about any computer security software.
Downloading software (games, shareware, screen savers, and such) whose integrity cannot be verified is like giving your front-door key to a stranger. Once you allow unknown software to install, there is no guarantee that your security system can protect you against any malware that may be embedded in those files.
One corporate security manager, complaining about how often senior executives’ PCs get infected, commented, “You try and stop a guy watching a juicy porn movie he’s just downloaded. It doesn’t matter what warnings his security software gives, he’s going to watch it anyway.”
And it’s not just visiting suspect Web sites and installing software that you should worry about. Many other high-risk activities, such as opening e-mail attachments from strangers, visiting cracked software sites, and installing software given to you by friends, pose serious threats to your security.
Any of these activities can lead to an infection, regardless of the type or amount of security software you have installed. Sooner or later, you’ll get clobbered. And the rational response is not to add even more security software, but to change your behavior.
Good security requires a different mindset
Since you cannot make your PC impregnable with security software, the first step to a safer Web experience is to adopt safe computing practices — and then look for a complementary security-software solution that balances effectiveness against cost and inconvenience.
So what are the rules for safe computing? They should be familiar to any frequent Windows Secrets reader and are well documented on the Web. They include the basic behaviors such as being extremely careful about clicking on unfamiliar sites, not downloading e-mail attachments from sources you don’t know, not clicking on odd links forwarded by friends, not installing downloads from sites using P2P (for example, BitTorrent and eMule sites), and being wary of programs friends pass along on removable media. In fact, be wary of the medium itself, as it may be infected with hidden malware.
For more, check out the following sites:
- Gizmo’s page, “Safe Hex: The Rules for Safe Computing”
- ResNet’s “Safe Computing Practices” info page
- Computer Knowledge’s “Safe Computing Practices” article
But it’s not just a matter of knowing the rules — it’s a matter of applying them in your everyday computing. Print them out and give them to every member of your family and to your co-workers. Have a security war council and get everyone on board.
Match the security suite to your computing
With the right security practices, you need less anti-malware software than you might think. In fact, I have a number of acquaintances who don’t use any security software at all — apart from the firewall that comes with Windows — and don’t get infected. However, these are not typical users; they’re highly skilled and highly disciplined IT professionals who know how and when to use limited user accounts. Most users (me included) need at least some security software.
My first software suggestion is not security software per se, but rather a security measure. I suggest you change your browser to Google Chrome. Currently, it’s the safest of the mainstream browsers, due to the way it isolates (sandboxes) browsing sessions. Most security experts agree that sandboxing makes it extremely difficult for hostile Web sites to infect your PC. I noted in my May 13 column that Chrome is not only safer but also faster than most of the leading browsers.
Once you’ve installed Chrome, go to the Google Extensions/Web of Trust (WOT) site and download the extension. WOT rates Web sites according to their level of trustworthiness. This will help keep you away from malicious sites.
An alternative to Chrome is to use your browser in a sandbox. The free version of Sandboxie (sandboxie.com) is a good choice — though using Chrome is the simpler option.
Once you have swapped your browser, install a single, broad-spectrum malware scanner with real-time protection. There are two outstanding choices, both of which are free: Microsoft Security Essentials (MSE) and Avira AntiVir Free Edition. Neither slows down your PC.
In his May 6 Top Story, Fred Langa was impressed with MSE’s anti-malware capabilities, and I fully agree.
According to a recent AV-Comparatives.org test report (listed on the company’s Main-Tests page), Avira AntiVir Free Edition offers slightly better overall protection than MSE, though this comes at the cost of a nag screen prompting you to upgrade to the paid version. However, the ad is not overly intrusive and is quite acceptable, given the overall quality of the product.
The only other piece of security software prudent users need is a firewall. Simply use the one that comes free with every version of Windows since XP. Its inbound malware protection is excellent, and that’s most important.
Windows’ firewall offers little protection against malware already installed on a PC and trying to phone home. Fortunately, this type of outbound malware action is uncommon, and many PC users do would not know how to respond to outbound firewall alerts.
What other security software do you really need? Nothing, if you assiduously follow safe computing practices.
Follow these steps, and your chances of becoming infected are minimal — certainly much lower than for those who pack their PCs to the gunnels with expensive security software but continue to engage in risky practices such as downloading illegal software.
| Have more info on this subject? Post your tip in the WS Columns forum. |
Ian “Gizmo” Richards is senior editor of the Windows Secrets Newsletter. He was formerly editor of the Support Alert Newsletter, which merged with Windows Secrets in July 2008.
Have your Windows Mail and Windows 7, too
 |
By Susan Bradley
From the e-mail received after May’s Patch Tuesday, it’s obvious that Windows Mail is still extremely popular with Windows 7 users. So I’m revisiting the patch described in Microsoft Support article MS10-031 and giving more details on exactly how to get the Mail you want on Windows 7. |
MS10-031 (978542)
Getting Vista’s Windows Mail to work on Win7
Windows Mail originally shipped with Vista as a replacement for Outlook Express. Microsoft discontinued Windows Mail in Windows 7, replacing it with Windows Live Mail, available as a free download on its info page.
This change did not sit well with some Win7 users who preferred the familiar, older, Windows Mail client — they installed Windows Mail on Win7. It worked until May, when Microsoft’s MS10-031 update stopped Windows Mail (installed on Win7) dead in its tracks.
Adding to the confusion, MS10-031 originally offered a patch for systems with Win7 and Windows Mail installed. But just last week, the instructions were changed: a Windows Mail–Win7 configuration is no longer listed.
► What to do: A workaround is posted in the Chairman Mow blog, but read the caveats before trying it. The workaround may introduce new security problems, and any future patches such as KB 978542 may stop Windows Mail all over again. The better long-term fix is to bite the bullet and upgrade to Windows Live Mail or to a third-party e-mail client.
Mozilla offers an easy way to check plug-ins
Browser plug-ins are some of the best ways to enhance your browsing experience — and also one of the routes hackers may exploit to take control of your PC or install malware. Regularly updating plug-ins is one of the best ways to ensure you’re safe while browsing the Internet.
Mozilla has developed a Web page for checking installed browser plug-ins; it will point you to the locations where they can be updated. (See Figure 1.) It works best with Firefox and Chrome, but will work with Internet Explorer as well.
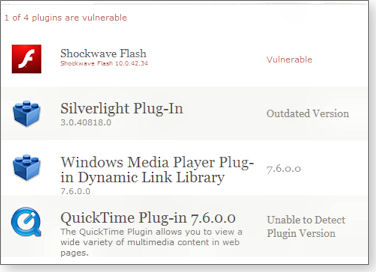
Figure 1. Mozilla offers a handy way to make sure your browser plug-ins are current.
► What to do: Check your browser plug-ins at Mozilla’s Plug-in Check page.
931125
Patching the roots — on your browser
Periodically, Microsoft updates the root certificates your browser uses to authenticate Web sites. Root certificates ensure that the security messages from secured Web sites are accurate. KB 931125 includes additional Extended Validation Certificates, which require a higher level of checking by the certificate authority before it issues a valid certificate.
This update is offered only to workstations, not to servers. Windows Server 2003 limits the total size of certificates installed, and KB 931125 may push the OS over that limit. (If the update is added to Server 2003, an SChannel event ID 36885 will show up in its event log.)
► What to do: Accept KB 931125 to ensure that you have the most-recent version of Extended Validation Certificates in your browser. Microsoft support article 931125 includes a download link, if you want to install it manually.
Should you install this update in Server 2003, you may need to launch the Certificate console and remove any out-of-date certificates from the root certificate section.
Update Java for Mac when it’s offered
Mac users should look for Java for Mac OS X 10.5 Update 7, which includes both security and stability fixes for the application. According to Apple security bulletin HT4170, a vulnerability could allow untrusted Java applets to run malicious code outside the Java sandbox.
► What to do: Look for the update in the usual software update system, or go to the Apple support downloads page as soon as possible.
MS09-061 (974417)
Looking for help with a .NET reoffering problem
I’m still trying to get to the bottom of a problem where patch KB 974417 in MS support article MS09-061 (a security update for .NET 2 Service Pack 2 and .NET 3.5 Service Pack 1) is reoffered on some systems.
If you’ve been plagued with this reoffering since the second week of May, I need your help.
► What to do: If you’ve been impacted by this problem, contact me via the contact box. With your help, I’ll hopefully have an answer in the next edition of Patch Watch.
Out with Newsgroups, in with MS Answers forums
For many years, one of the ways Windows users obtained help with patching was to contact experts at Microsoft Newsgroups.
Beginning June 1, Microsoft will start to close all newsgroups, transitioning to Web forums for support offerings, as noted in the company’s announcement, “Microsoft Responds to the Evolution of Communities.”
► What to do: Check out the Windows Update forum, located on the Microsoft Answers Web site.
| Have more info on this subject? Post your tip in the WS Columns forum. |
The Patch Watch column reveals problems with patches for Windows and major Windows applications. Susan Bradley has been named an MVP (Most Valuable Professional) by Microsoft for her knowledge in the areas of Small Business Server and network security. She’s also a partner in a California CPA firm.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Microsoft: Troubleshoot problems updating Windows
by
Alex5723
2 hours, 25 minutes ago -
Woman Files for Divorce After ChatGPT “Reads” Husband’s Coffee Cup
by
Alex5723
2 hours, 34 minutes ago -
Moving fwd, Win 11 Pro,, which is best? Lenovo refurb
by
Deo
1 hour, 21 minutes ago -
DBOS Advanced Network Analysis
by
Kathy Stevens
12 hours, 23 minutes ago -
Microsoft Edge Launching Automatically?
by
healeyinpa
2 hours, 48 minutes ago -
Google Chrome to block admin-level browser launches for better security
by
Alex5723
15 hours, 4 minutes ago -
iPhone SE2 Stolen Device Protection
by
Rick Corbett
7 hours, 19 minutes ago -
Some advice for managing my wireless internet gateway
by
LHiggins
3 hours ago -
NO POWER IN KEYBOARD OR MOUSE
by
HE48AEEXX77WEN4Edbtm
9 hours, 16 minutes ago -
A CVE-MITRE-CISA-CNA Extravaganza
by
Nibbled To Death By Ducks
1 day ago -
Sometimes I wonder about these bots
by
Susan Bradley
20 hours, 50 minutes ago -
Does windows update component store “self heal”?
by
Mike Cross
10 hours, 53 minutes ago -
Windows 11 Insider Preview build 27858 released to Canary
by
joep517
1 day, 14 hours ago -
Pwn2Own Berlin 2025: Day One Results
by
Alex5723
1 day, 13 hours ago -
Windows 10 might repeatedly display the BitLocker recovery screen at startup
by
Susan Bradley
2 hours, 8 minutes ago -
Windows 11 Insider Preview Build 22631.5409 (23H2) released to Release Preview
by
joep517
1 day, 17 hours ago -
Windows 10 Build 19045.5912 (22H2) to Release Preview Channel
by
joep517
1 day, 17 hours ago -
Kevin Beaumont on Microsoft Recall
by
Susan Bradley
1 day, 5 hours ago -
The Surface Laptop Studio 2 is no longer being manufactured
by
Alex5723
2 days, 1 hour ago -
0Patch, where to begin
by
cassel23
1 day, 19 hours ago -
CFPB Quietly Kills Rule to Shield Americans From Data Brokers
by
Alex5723
2 days, 14 hours ago -
89 million Steam account details just got leaked,
by
Alex5723
2 days, 2 hours ago -
KB5058405: Linux – Windows dual boot SBAT bug, resolved with May 2025 update
by
Alex5723
2 days, 23 hours ago -
A Validation (were one needed) of Prudent Patching
by
Nibbled To Death By Ducks
2 days, 14 hours ago -
Master Patch Listing for May 13, 2025
by
Susan Bradley
2 days, 1 hour ago -
Installer program can’t read my registry
by
Peobody
18 hours, 26 minutes ago -
How to keep Outlook (new) in off position for Windows 11
by
EspressoWillie
2 days, 12 hours ago -
Intel : CVE-2024-45332, CVE-2024-43420, CVE-2025-20623
by
Alex5723
2 days, 19 hours ago -
False error message from eMClient
by
WSSebastian42
3 days, 10 hours ago -
Awoke to a rebooted Mac (crashed?)
by
rebop2020
3 days, 19 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

