
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Run Windows on iPad using remote-computing apps
In this issue
- TOP STORY: Run Windows on iPad using remote-computing apps
- LOUNGE LIFE: At some point, you just have to move on
- WACKY WEB WEEK: Where to send your annoying Apple friends
- LANGALIST PLUS: Troubleshooting broken apps and shortcuts
- IN THE WILD: How to pick and optimize your home router
- PATCH WATCH: Support ends for Windows 2000 and Windows XP SP2
Run Windows on iPad using remote-computing apps
 By Michael Lasky
By Michael Lasky
Windows users might dismiss Apple’s new ultra-light, ultra-sleek iPad as just another frivolous toy for Mac heads.
But add remote-computing software and services, and the iPad’s combination of light weight and nicely sized screen makes Apple’s pad a dandy Windows terminal.
I’m writing this story on my iPad, using Microsoft Word for Windows 2007 that’s actually running on my home-office desktop PC. I’ve pulled off this stunt thanks to the handful of remote computing apps designed to work with iPad (and iPhone). Yes, I can have my Apple cake and Windows, too.
Even Adobe Flash, which Steve Jobs declared persona non grata on iPads and iPhones, now has a place on the iPad screen. Flash videos don’t run well (due to the slow screen refresh rates typical of remote-control software), but they do run. Even with a strong Wi-Fi signal, Flash videos were choppy at best.
The ingredients for this Windows/iPad trick are a PC that’s left on, remote-control software on the iPad and PC, and a good Wi-Fi or 3G connection.
To see just how effectively Windows runs on an iPad, I put a trio of iPad-compatible, remote-computing applications — LogMeIn, Wyse Technology’s Pocket Cloud, and iTeleport for iPad — through their paces. All of these products are a bit more expensive (U.S. $15 to $30) than your usual 99-cent iPad app — but for business use, that’s still cheap.
Remote computing has been around for decades, of course, but its move to mobile devices is a recent phenomenon enabled by the relatively large screens and the Internet connections of smartphones. Possible, yes — but not necessarily practical.
The iPad, with its 9.7-inch (diagonal) LED-backlit display, 1024-by-768-pixel resolution, and high-performance processor, meets the requirements for practical remote computing. And this story, mostly written from the iPad, is proof that it works. (See Figure 1.)

Figure 1. Remote-computing apps and an excellent screen let the iPad work as your mobile business workstation — in this case, writing this story in Word for Windows.
Ignite simple and cheap remote computing
The U.S. $30 LogMeIn Ignition for iPhone/iPad (info page) will connect to any number of PCs or Macs on which you’ve installed a small, and free, enabling application. (Ignition also works on the iTouch.)
Installing Ignition was brain-dead simple — I was banging out the notes for this story, using Word for Windows, in about five minutes. There are no firewall or router settings to work through, and my remote-control sessions were protected with 256-bit SSL encryption.
Using the iPad and my digital writing tablet took a bit of adaptation. I started out with the device’s internal software keyboard but later attached Apple’s external Bluetooth keyboard. (At this time, the iPad does not have native support for Apple’s Bluetooth mouse, but a Google search lists a bunch of iPad–mouse hacks.)
Navigating the Windows screen on the iPad took more adjustment. To move the Windows cursor, you drag your finger across the iPad display. Once the cursor is positioned, a tap or double-tap anywhere on the iPad display works in lieu of the usual Windows click/double-click. (See Figure 2.)
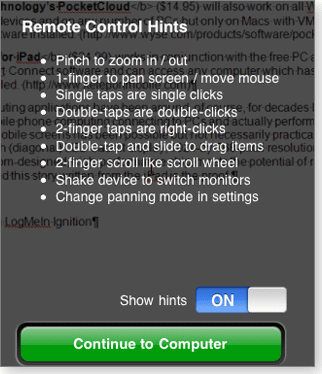
Figure 2. LogMeIn Ignition includes a handy “hints” list for navigating around Windows with the iPad touch screen.
Ignition adjusts the PC display to fit on the iPad (which can make Windows apps and documents look uncomfortably small), but the simple iPad two-finger pinch zooms objects larger or smaller, as needed. Other finger movements handle mouse right-clicks and scrolling. Alas, there seems to be no way to highlight a body of text to delete it, move it, or reformat it — which puts a crimp in your document editing.
LogMeIn handshakes your connection through its servers. The basic LogMeIn account is free, but for business applications, the $70 Pro account adds more PC-to-remote PC tasks such as remote-to-local printing and drag-and-drop file transfers. Since the iPad software does not support file transfers, the free account suffices quite well.
The not-so-easy business remote-access solution
Wyse Technology’s $15 PocketCloud for iPad (info page) connects with both PCs and Macs. To run PocketCloud on Macs, you need to have VMware virtualization software installed. To connect to PCs loaded with any current version of Windows (except the Home Editions), you need to download the free PocketCloud Windows Companion.
Setting up PocketCloud was far harder than setting up either of the other iPad remote-control systems I tested. Requiring IT-level knowledge of Windows PCs, set-up included a 30-minute phone call with Wyse tech support to get me up and running. It also included configuration changes to both Windows and my Wi-Fi router settings.
That came as no surprise to Wyse spokesperson Tim Smith, who replied to my e-mail query on this process.
- “The app was specifically designed for IT users and was priced a bit on the high side to discourage everyday consumers from using it. It does require a level of technical sophistication that most consumers don’t expect from an iPhone app.
“That being said, the IT users I’ve chatted with absolutely love the app. Because they are all on call 24/7, if nothing else, it frees them up from carrying a laptop with them at all times.”
Once launched, PocketCloud acts much like LogMeIn, with Windows navigation handled by the native-iPad finger movements. Applications such as Microsoft Office worked well on the iPad, but video playback — flash or otherwise — was spotty, even when using PocketCloud’s optional Windows client-side Thin-Browser app, which allows full access to Web sites with Flash content.
The real kicker came when I signed off and returned to the PC. PocketCloud had reset and resized my Windows desktop, placing all the usual desktop icons out of order and in the center of the display. Another minor peeve: for security, the app will function only if the Windows user has a sign-on password. Since I work alone from my home office, I did not use one; now I have to sign on each time I boot Windows.
A word to the wise: if you are not IT, skip this app.
iTeleport offers audio and a better keyboard
iTeleport for iPad (info page) costs $25 and works in conjunction with the free PC- and Mac-based iTeleport Connect software. According to iTeleport, the company will release an updated version of the software the same day this story appears.
Once you’ve installed and run two small apps on the PC you want to access, iTeleport uses a Gmail account to make the iPad-PC connection. I was able to immediately open my Word document and continue writing what you’re reading here.
Screen refresh rates were close to instantaneous when using Word but flagged terribly when viewing Web-based Flash videos. Unlike the other apps, iTeleport does support audio playback.
As with the other two products, navigating Windows screens and documents requires a little learning time and some patience. iTeleport’s tech support consists of skimpy information on the iTeleport Web site and e-mail queries.
iTeleport has one useful feature not found on the other remote computing apps: an on-call virtual keyboard that includes the 12 function keys as well as the Windows key and some exceptionally handy shortcuts not found on the native iPad keyboard. (See Figure 3.) Unfortunately, press-and-hold key combinations such as ALT-F3 didn’t work. That makes using keyboard shortcuts in applications such as Office and Adobe PhotoShop a little harder.
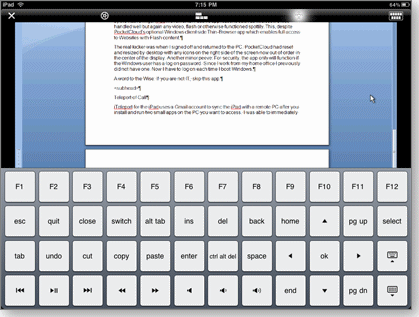
Figure 3. iTeleport’s virtual keyboard sports function keys and a number of handy shortcut keys.
As with LogMeIn and PocketCloud, iTeleport remote access is possible only when you leave your PC on, although all three products can wake up a PC that’s in sleep mode. Of course, the PC half of the remote-connection software must also be kept active.
In addition to the 256-bit SSL encryption, each of these programs typically uses two layers of passwords for the iPad-PC connections. iTeleport adds a third level: a password for its VPN-like link.
Convenient and relatively easy remote computing is now possible, thanks to these apps. They don’t duplicate every PC function, but what you can do today may be enough to ditch that heavy laptop — or maybe even that lighter netbook.
| Have more info on this subject? Post your tip in the WS Columns forum. |
WS contributing editor Michael Lasky is a freelance writer based in Oakland, California, who has 20 years of computer-magazine experience, most recently as senior editor at PC World.
At some point, you just have to move on
By Tracey Capen
When I say it’s time to move on, I’m not talking to the millions of PC users who continue to use Windows XP and refuse, for now, to upgrade to Windows 7.
No, I’m talking to those procrastinators who cling to Windows XP SP2 in spite of Microsoft’s July 13 support cutoff date.
For those who’ve seen the light — such as Lounge member MichaelA — the question is not when but how best to make the move to Windows XP SP3. Michael received some excellent advice from fellow Loungers, but the most-useful information comes near the end of the thread, where Michael summarizes the highs and lows of the upgrade process. More»
The following links are this week’s most-interesting Lounge threads, including several new questions that you may be able to provide responses to:
☼ starred posts — particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right in to today’s discussions in the Lounge.
The Lounge Life column is a digest of the best of the WS Lounge discussion board. Tracey Capen is technical editor of WindowsSecrets.com.
Where to send your annoying Apple friends
 |
By Stephanie Small
Apple fans can be really annoying. They’re always crowing about some sleek new laptop, phone, or music player. And don’t even get them started on the iPad — they just won’t stop. But the best Apple idea to come out recently doesn’t even come from Apple. A spinoff of the Genius Bar, this Onion News short introduces the Friend Bar, a place to send all your annoying Mac-obsessed friends when you grow tired of listening to them ramble. It’s possibly the only Apple product devout PC users will definitely use! Play the video |
Troubleshooting broken apps and shortcuts
 |
By Fred Langa
If you click on an icon to run a program and nothing happens, the program could be hosed — and that’s bad news. But it might only be the iconized shortcut that’s messed up, and that’s a cinch to fix. This week’s first item illustrates both these possibilities. |
Windows 7’s Control Panel will not load
Windows Secrets readers are an amazingly skillful bunch. Take, for example, this e-mail from Rick, in which he thoroughly analyzes the problem and works through possible solutions.
- “My friend has a new Windows 7 PC that has been fine. She asked me to do something which involved the Control Panel. I clicked the Control Panel icon on the task bar and nothing happened. I could hover the mouse over the Control Panel icon, and I got the small pop-up window showing me the Control Panel, but when I clicked on that window to expand the Control Panel, nothing happened. I tried other icons like Windows Explorer and Internet Explorer, and they all opened fine.
“I booted into safe mode and Control Panel opened fine. My friend said she hadn’t done anything to the PC lately.
“I ran fixwin, had it fix anything that seemed related to Aero or the Control Panel problem. I tried to disable Aero Peek, but I’m not sure I was ever able to do so because other programs were able to be peeked. I turned off her antivirus and firewall, tried using Run and typing in control.exe, but still could not find a way to open Control Panel. I right-clicked on the Control Panel icon on the task bar and chose Maximize, Restore, move, and size — but no luck.
“If I hovered the mouse over the Control Panel pop-up window, I could see a blank frame on the desktop screen, like the Control Panel had opened but was transparent. I again tried to disable Aero and couldn’t find a way to actually turn it off because any settings were related to Control Panel and I couldn’t get into Control Panel.
“Again, other icons on the task bar work fine; it’s just Control Panel. I’ve Googled and searched the Lounge at Windows Secrets but haven’t found this issue. Can you please help?”
Impressive troubleshooting, Rick. I would do many of the same things, were I in your shoes.
It’s a little worrisome that you couldn’t manually launch Control Panel. I also don’t see how this could be an Aero/graphics display problem per se. But before we go there, let’s try a simpler fix.
The Windows 7 Taskbar items are nothing more than iconized shortcuts to a file, program, or folder. If a Taskbar shortcut (or any shortcut, for that matter) stops acting the way it should, you often can get things right simply by deleting and recreating the mangled shortcut. It takes only seconds.
In your case, Rick, right-click on the Control Panel icon that appears on the Taskbar and select the Unpin option, as shown in Figure 1.

Figure 1. In Win7, you can “unpin” any Taskbar shortcut icon via the right-click menu. (The reverse, “pinning,” works the same way to let you add new icons to the Taskbar.)
To recreate a new Control Panel icon on the Taskbar, launch Control Panel by any means you can. As usual with Windows, there are many different ways to accomplish the same task. Here are a few:
- Type control.exe in the Start/Search programs and files box, and press Enter.
- Click the Start orb and then click Control Panel in the right-hand pane of the Start menu.
- Navigate to C:WindowsSystem32 and double-click on the control.exe file there.
- If you’ve previously added Control Panel to your Desktop via the Change Desktop icons settings (click Control Panel, Appearance and Personalization, Personalization), just double-click the desktop icon.
For now, let’s assume you can get Control Panel up and running. Once it’s up, a new Control Panel icon will appear on the Taskbar. By default, this icon is temporary (like all such Taskbar icons) until you tell Windows to leave the icon “pinned” to the Taskbar.
Pinning is the reverse of the removal process described earlier: right-click on the Control Panel icon and select Pin this program to Taskbar. When you later close the Control Panel, the new icon will remain in place and should work perfectly when you click it.
Odds are, you’ll be OK at this point. But if not, or if you can’t get Control Panel to run at all, then you may have encountered a rare case where Control Panel itself has become damaged. That almost never happens in normal operation, so before doing anything else, I suggest you immediately run multiple scans on your friend’s system using several different antivirus tools. Make sure it’s totally malware-free!
When you know the system is clean, you can replace the damaged control.exe with a good one via a repair install that restores the original Windows system files without disturbing the system’s data, user accounts, programs, or drivers. The best how-to I’ve found on the Win7 repair install process is a Sevenforums.com tutorial.
But with luck, you won’t need that, and your friend’s Control Panel problem can be fixed simply by deleting and then recreating the Taskbar shortcut icon!
How to replace a pirated copy of Win7
Glen’s trying to do the right thing: upgrade a pirated copy of Windows to a normal retail copy.
- “Can you please tell me if I can reinstall a regular copy of Win7 Ultimate without deleting all my programs? I just want to redo it, since someone sold me a pirated copy. I may even go back to my Windows XP.”
I don’t have an illegal installation to try this on, but as far as I know, you should be able to just pop in the retail DVD and install the new, legit version.
First, I’d suggest trying the repair install option discussed in the previous item. When prompted by the installation process, enter the new, valid license key and select the option to activate Windows once you’re online.
If that repair doesn’t work, try the Upgrade option if it’s offered. This should also keep your other files and settings intact.
As a last-ditch maneuver, you can install the new, legit Windows copy alongside the current nonlegit one, as a separate installation on the same disk. In most cases, you’ll now be able to boot the new copy of Windows. Once it’s loaded, you should be able to navigate to the nonlegit partition or folder to access your files there.
(And good on ya, Glen, for ditching the pirated copy!)
Demystifying PAL, NTSC, and DVD codes
Lyle Fettig wants to watch foreign-format DVDs.
- “I sometimes play prerecorded DVDs (movies and so forth) on my computer. I recently got one from Europe recorded in PAL format. Sometimes it plays, more often not. I’ve been told I need to download the proper decoders. It seems there is little written online about decoders. I’ve not seen much info about troubleshooting DVD players, and I have not found anything about downloading decoders. Any suggestions?”
The codecs may be the easy part! There may also be issues with either the hardware or the DVDs’ country codes (software switches designed to prevent wide distribution of pirated discs).
Fortunately, today’s mobile society means that large numbers of expats and travelers have already encountered this problem, and much of their collected wisdom is online and supported by free downloads. See, for example:
- Club.MYCE.com’s article, “Watching PAL DVDs in the USA”
- DVDdemystified’s article, “What are regional codes, country codes, or zone locks?”
- MVPs.org’s info on “DVD Region Codes”
- Fileguru.com’s download page, Neo Media Player Converter 2.1
- Free-Codec.com’s download page for the open-source (free) Cedocida DV Codec
It may take a little digging to match your exact needs, but the info’s almost surely just a few clicks away!
Microsoft’s free PowerShell task language
Roger Neate likes Microsoft’s PowerShell, an interactive command-line and task-based scripting tool. I like it, too.
- “Although PowerShell has a bit of a learning curve, the main advantages of PowerShell are:
a) It’s free.
b) PowerShell scripts are much easier to read, write, and maintain than batch files.
c) It is fully secure, unlike other scripting languages such as JavaScript.
d) A single add-on, it’s extraordinarily powerful because it provides direct access to the entire .NET Framework.”
Thanks, Roger!
PowerShell falls somewhere between a batch language and a full-blown programming language. It runs on XP and all newer editions of Windows. Here are some good information resources:
- Microsoft’s PowerShell information and download page
- TechNet’s tutorial page, “Scripting with Windows PowerShell”
- PowerShell.com’s home page provides extensive information and links to more
When you occasionally need to cobble together a little quick-and-dirty tool to accomplish a very specific task, PowerShell is a great, free tool.
| Have more info on this subject? Post your tip in the WS Columns forum. |
| Reader Roger Neate will receive a gift certificate for a book, CD, or DVD of his choice for sending the tip we printed above. Send us your tips via the Windows Secrets contact page. |
Fred Langa is a senior editor of the Windows Secrets Newsletter. He was formerly editor of Byte Magazine (1987–91), editorial director of CMP Media (1991–97), and editor of the LangaList e-mail newsletter from its origin in 1997 until its merger with Windows Secrets in November 2006.
How to pick and optimize your home router
 |
By Robert Vamosi
Staying safe on the Internet requires the combined forces of a router-based firewall, security software, regular updates, and a secure browser. In this column, I provide recommendations and tips on how to pick the right router and how to set it up for maximum protection from malicious Web sites. |
Your Internet path gives an opening to hackers
Put most simply, a router is the gateway between your PC and the Internet. It may be attached to a cable or DSL modem, or it may have those functions built in. In its most-common form, it’s a small box that distributes your Internet connection to the various PCs on your network using Network Address Translation (NAT).
Most small-business and home routers attach to your networked PCs though Ethernet cable connections (typically four to six ports) on the back, or wirelessly using the 802.11 standard. Wireless is more convenient and flexible than cabling, but it does offer openings for digital attacks and eavesdropping that a hardwired cable doesn’t.
In a recent example of eavesdropping, a Washington Post article describes how Google collected Wi-Fi data — possibly including personal information — from unsecured wireless networks as its Street View mapping vehicles drove through various cities.
But the practice of collecting data about public and private wireless networks goes far beyond Google. According to a March 2 article in the Washington Post, Microsoft, Yahoo, and others routinely collect Wi-Fi information for their location-based Internet services (such as providing, online, the locations of restaurants, gas stations, and so forth).
From a security aspect, the most-important feature found in nearly all routers is a firewall — your first line of defense against cyber attacks from the Internet. For the average PC user, most router-based firewalls provide adequate protection. They vary mostly in the user-adjustable features offered and in what advanced security options they include.
Look for routers that meet the latest standard
The standard used for virtually all wireless networking through routers is 802.11, and each update to this standard is designated with a letter — b, a, or g, for example. In October 2009, the 802.11n specification was ratified, so almost every router sold today should conform to 802.11n.
Unfortunately, not all n routers are the same. There are products on the market labeled pre- or draft 802.11n — essentially n routers that started shipping before the standard was finalized. Don’t be fooled. These early versions may not have all the features found in routers that do meet the ratified specification. Expect to pay up to $100 for a pre-802.11n router, such as the Belkin N+ Wireless router (product page) described as “Draft 802.11n.”
On the other hand, there are some early 801.11 routers with upgradable firmware (especially Linux-based routers such as models from Buffalo) that can be easily updated to all current specs.
True 802.11n-compliant routers have multiple-input–multiple-output (MIMO), the ability to use multiple antennas to improve reception. Some 802.11n routers also include multistreaming capabilities, such as the ability to use both the 2.4 GHz and 5 GHz bands — you can check e-mail on the low band while streaming a video on the high band. These advanced routers are pricey, however; D-link’s DGL-4500 Xtreme N Gaming Router (info page), for example, costs $300.
No matter which router you purchase, make sure it has a Stateful Packet Inspection (SPI) firewall. That means the firewall keeps track of the TCP and UDP data streams coming and going through your network. SPI passes along only those data packets that match known connections (by being stateful). Rogue or unknown packets are automatically blocked.
Before SPI, stateless packet inspection looked at each and every packet in isolation, a process that’s unreliable, given the Web applications we now run on our PCs. An SPI firewall is capable of sorting through multiple streams of packets.
Recommended routers for home and small biz
Finding up-to-date reviews of small routers is not easy. There are few independent testing labs that review these products on a regular basis. Based on an extensive search of router reviews, I suggest the following:
If easy installation is key, consider the Cisco Valet Plus (info page); it’s a basic wireless router, priced at around $130. It received high marks from CNET and earned an Editor’s Choice from PCMag.com. Reviewers pointed to its good performance and fast, user-friendly setup that includes the innovative USB Easy Setup key.
For a dual-band router, check out the Linksys E3000 Simultaneous Dual-Band Wireless-N Router, priced around $180. It’s an update of the Linksys WRT610N, which earned very good scores from CNET and ZDNet. The E3000 has a sleek, low-profile design similar to that of the Valet Plus, and it shares that router’s ease of setup. The E3000 supports gigabit Ethernet speeds and has a USB port for external network-attached storage.
If you are willing to spend more and would like something that’s more than a nondescript box sitting on your desk, check out D-Link’s DIR-685. At around $225, this interesting device is pricey, but it includes an open bay for an optional 2.5″ internal hard drive, giving you network-attached storage. It also has a small color LCD, so that ugly box turns into a digital picture frame.
Fine-tune your new router for maximum security
Once you’ve run through your router’s basic installation (following the instructions provided in the box), it’s time to make a few security enhancements. Most routers today come with a URL that allows your browser to talk to it. When prompted, you’ll need a username and a password, which should be included the instructions.
When you’re signed in to the router’s control menus, make the following changes:
Default SSID: It’s a good idea to change the service set identifier or SSID from the default label (D-Link, for example) to something unique and more descriptive. Just don’t be too descriptive, or everyone will know which router is yours. Be creative: avoid labels such as BobSmithsBelkin or 123MainStLinksys; try something like nofreewifihere or whatchulookingat.
Some security experts recommend that you turn SSID broadcasting off, but I don’t see the value in that. I recently added TiVo to my wireless network and was able to quickly find my router among others in the neighborhood. Moreover, a good Wi-Fi sniffer can find your network even if SSID is off.
Default password: When I look for wireless connections on my laptop, I see too many 2Wires, D-Links, and Linksyses among the available SSIDs. That tells me that the owners probably haven’t bothered to change their routers’ administrative passwords or other security settings.
From the Router Passwords Web site, I know that 2Wire has a default administrator name that’s blank and a password of “Wireless”; D-Link uses a variation of blanks or “admin” in either position; and Cisco/Linksys uses “admin” for both the admin name and the password.
If you have a Yahoo DSL router, there’s a whole page that can let someone gain access to your router’s administrator controls (because the DSL installer didn’t bother to change the default settings).
The point is, default passwords are well known or easily discovered. So, change your username and password as soon as possible (and keep that information in a secure place) to prevent someone with bad intentions from taking over your router. If your router won’t let you change the username (some Linux routers are hardwired to use root as the username), then be certain to use a long, complex, and difficult-to-crack password.
WPA encryption: You need to use encryption to protect your data as it travels over a wireless network. Wi-Fi Protected Access (WPA) is the most-commonly used encryption protocol for small businesses and homes. Check that your router is not set to Wired Equivalent Privacy (WEP), an older protocol that can be hacked.
For even-better security, you can use the newer WPA2, as long as all your networking devices support it. If you have one device that supports only WPA, you can’t use WPA2 for the network.
OpenDNS (optional): Most ISPs tell you what Domain Name System (DNS) address to use. (This is the system that translates the common name of a Web site to its numerical address on the Internet.) Start by making sure you can connect to the Internet. Once you can do that, change the default DNS settings to those provided by OpenDNS: 208.67.222.222 and 208.67.220.220.
Why make this change? OpenDNS blocks addresses that are known phishing or botnet sites, and it does so more quickly than most conventional DNS servers.
MAC address filtering (optional): If you change your home networking devices infrequently, I recommend using Media Access Control (MAC) address filtering. The MAC address is unique to each networked device. Enter the MAC addresses of your PCs, printers, and other network components into the router’s MAC address table, and it will accept only traffic from those devices. If someone gets around your WEP security, MAC filtering will still keep the intruder at bay.
Some routers also allow you to store the MAC addresses of those devices you want to specifically prevent from joining your Wi-Fi (say, the neighbor you suspect is piggybacking onto your network). The router’s admin settings will usually let you see who’s connected to your network, by listing their IP and MAC addresses.
MAC addresses are made up of twelve characters arranged in sets of two, and there are two ways to find these numbers. First, the router’s admin settings should reveal the MAC address of all connected devices. You might have to lower security to let your printer connect. Once you have its particulars, reset security and adjust the settings to let the printer connect securely.
To find the MAC address of a Windows PC to which you have full access, click Start and Run, then type cmd and hit Enter. At the command prompt, type ipconfig /all, then hit Enter again. Within the resulting list of details about your machine, locate the entry for physical address.
Carefully enter those digits onto the router’s MAC address table. You will need to do this with each device you want to connect to the network.
These are basic security steps. But time and time again, I’m amazed at how few people actually take the time to perform them. Take the time to do it now, if you haven’t already.
Make router config changes with less effort
Once your router is set up and secure, there will be times when you have to make changes to its configuration — such as when you add a new network device or want to give friends or family temporary access.
Cisco has come up with a helpful solution: Valet, a new line of routers that come with USB key software. With Valet, it’s easy to take your network configuration settings from one working PC to another; it works on Macs as well. The basic model, Valet M10 (info page), lists for about $100.
The Valet USB also solves the problem of friends’ wanting you to share your network by setting up a temporary network and a temporary encrypted password for them to use.
Get the full Windows Secrets Security Baseline
Windows Secrets has put together a short, easy-to-read summary of the minimum hardware, software, and services needed for safe Internet computing. It contains recommendations for a router, anti-malware suite, update management practices and services, and secure browsers.
| Have more info on this subject? Post your tip in the WS Columns forum. |
WS contributing editor Robert Vamosi was senior editor of CNET.com from 1999 to 2008, writing pieces such as Security Watch, the winner of the 2005 MAGGIE Award for best regularly featured Web column for consumers.
Support ends for Windows 2000 and Windows XP SP2
 |
By Susan Bradley
We bid farewell to Microsoft support for Windows 2000 and Windows XP SP2 this month. The complex security systems we live with today that protect us from malicious Internet attacks have their roots in these two venerable operating systems. |
Windows 2000 event taught hard security lessons
It’s no small irony that, on this lighter-than-usual month of patches, the most interesting news is about the operating system that failed. No, I’m not talking about Vista but rather Windows 2000, which is now officially no longer supported by Microsoft.
At one time, Windows 2000 was touted as the safest operating system ever. And then came that fateful July 13, 2001, when a virus called Code Red hit.
That event launched many of the security concepts we live with today: the User Account Control we hate and the services such as Internet Information that are now disabled by default. Bill Gates reportedly made Microsoft’s engineers go back to school for several months to learn how to code securely.
Windows XP, arguably Microsoft’s most popular operating system, gained many of its most important security features from the lessons learned by Microsoft as it patched Windows 2000.
► What to do: You’ll no longer receive Windows 2000 security patches from Microsoft. So if you’re running this OS, consider isolating it from the Internet. And as I’ve said many times already, Windows XP SP2 users need to move up to Service Pack 3.
I’ll be checking the Lounge for any issues or concerns you still have, if you’ve yet to upgrade.
MS10-042 (2229593)
Microsoft quickly patches controversial bug
Fewer than 60 days after the so-called Help bug was revealed by Google employee Tavis Ormandy, it’s been squashed by Microsoft in patch KB 2229593.
First publicly discussed by Microsoft June 10 in Security Advisory 2219475, this vulnerability caused some controversy between the two giant technology companies and the security industry.
According to various reports on the dispute, Tavis may have felt that Microsoft was dragging its feet in addressing the flaw and decided to force the issue. Microsoft felt that Tavis had jumped the gun, not giving MS time to analyze the flaw. Whatever the facts, poor communication between the two sides contributed to the dispute.
The only operating systems affected by this flaw are Windows XP SP2 and SP3, XP Pro x64 SP2, and three flavors of Windows Server 2003 SP2. But the patch is listed as critical only for the three versions of XP. Remember, this is the last update for Windows XP SP2.
► What to do: For more information on this patch and links to patch downloads, consult MS Security Bulletin MS10-42. Again, there have been attacks using this vulnerability, so I urge you to accept the patch if it’s offered or to download it as soon as you can.
MS10-043 (2032276)
Canonical driver fixed for Windows 7 displays
In what sounds like a bug having to do with the Pope, the Canonical Display Driver problem first listed in a May 18 security advisory is finally patched. The flaw impacted 64-bit Windows 7 and Windows Server 2008 R2 systems, and only those with Aero display enabled.
This patch is a bit unusual in that it applies only to 64-bit operating systems. Normally x64 OSes have better security features than their 32-bit counterparts.
► What to do: For those running Windows 7 x64, install this as soon as you can. For additional information and download links, check out MS Security Bulletin MS10-043 (2032276).
MS10-044 (982335)
ActiveX patch for Office could hit business apps
The patch in MS10-044 impacts an ActiveX control used in Access 2003 and 2007. Whenever I read about an ActiveX fix, I worry that it might impact a critical line-of-business application. Fortunately, to my knowledge, it hasn’t yet happened. So the best policy is to go ahead and install the patch.
The patch is listed as critical and prevents attacks launched when users open a malicious Office file or view Web pages having Access ActiveX controls.
► What to do: If you have a critical business application that uses Access ActiveX controls, check carefully that installing the patch didn’t break it. Remember that the patch can always be removed if it causes problems. Consult Security Bulletin MS10-044 (982335) for more info.
MS10-045 (978212)
Office 2010 skates past a vulnerability unharmed
For those early adopters of Office 2010, Outlook 2010 is not vulnerable to the security issue described in MS10-045. Anyone using older versions of Outlook, however, is not so lucky. Office XP SP3, Office 2003 SP3, and Office 2007 SP1 all need this update.
You may also see updates for versions of Office you don’t think you have, as shown in Figure 1. The offering is normal and the patch replaces older files on your system.

Figure 1. Among the Office updates you might be offered are patches for a version of Outlook you don’t have installed.
► What to do: I anticipate attacks soon, so install the patches — all of them — as soon as they’re offered. If you want to install the patches manually, you’ll find links in Security Bulletin MS10-045 (978212).
| Have more info on this subject? Post your tip in the WS Columns forum. |
The Patch Watch column reveals problems with patches for Windows and major Windows applications. Susan Bradley has been named an MVP (Most Valuable Professional) by Microsoft for her knowledge in the areas of Small Business Server and network security. She’s also a partner in a California CPA firm.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Microsoft: Troubleshoot problems updating Windows
by
Alex5723
32 minutes ago -
Woman Files for Divorce After ChatGPT “Reads” Husband’s Coffee Cup
by
Alex5723
40 minutes ago -
Moving fwd, Win 11 Pro,, which is best? Lenovo refurb
by
Deo
47 minutes ago -
DBOS Advanced Network Analysis
by
Kathy Stevens
10 hours, 30 minutes ago -
Microsoft Edge Launching Automatically?
by
healeyinpa
55 minutes ago -
Google Chrome to block admin-level browser launches for better security
by
Alex5723
13 hours, 10 minutes ago -
iPhone SE2 Stolen Device Protection
by
Rick Corbett
5 hours, 26 minutes ago -
Some advice for managing my wireless internet gateway
by
LHiggins
1 hour, 7 minutes ago -
NO POWER IN KEYBOARD OR MOUSE
by
HE48AEEXX77WEN4Edbtm
7 hours, 22 minutes ago -
A CVE-MITRE-CISA-CNA Extravaganza
by
Nibbled To Death By Ducks
22 hours, 39 minutes ago -
Sometimes I wonder about these bots
by
Susan Bradley
18 hours, 57 minutes ago -
Does windows update component store “self heal”?
by
Mike Cross
8 hours, 59 minutes ago -
Windows 11 Insider Preview build 27858 released to Canary
by
joep517
1 day, 12 hours ago -
Pwn2Own Berlin 2025: Day One Results
by
Alex5723
1 day, 12 hours ago -
Windows 10 might repeatedly display the BitLocker recovery screen at startup
by
Susan Bradley
14 minutes ago -
Windows 11 Insider Preview Build 22631.5409 (23H2) released to Release Preview
by
joep517
1 day, 15 hours ago -
Windows 10 Build 19045.5912 (22H2) to Release Preview Channel
by
joep517
1 day, 15 hours ago -
Kevin Beaumont on Microsoft Recall
by
Susan Bradley
1 day, 3 hours ago -
The Surface Laptop Studio 2 is no longer being manufactured
by
Alex5723
1 day, 23 hours ago -
0Patch, where to begin
by
cassel23
1 day, 17 hours ago -
CFPB Quietly Kills Rule to Shield Americans From Data Brokers
by
Alex5723
2 days, 13 hours ago -
89 million Steam account details just got leaked,
by
Alex5723
2 days ago -
KB5058405: Linux – Windows dual boot SBAT bug, resolved with May 2025 update
by
Alex5723
2 days, 21 hours ago -
A Validation (were one needed) of Prudent Patching
by
Nibbled To Death By Ducks
2 days, 12 hours ago -
Master Patch Listing for May 13, 2025
by
Susan Bradley
1 day, 23 hours ago -
Installer program can’t read my registry
by
Peobody
16 hours, 32 minutes ago -
How to keep Outlook (new) in off position for Windows 11
by
EspressoWillie
2 days, 10 hours ago -
Intel : CVE-2024-45332, CVE-2024-43420, CVE-2025-20623
by
Alex5723
2 days, 17 hours ago -
False error message from eMClient
by
WSSebastian42
3 days, 8 hours ago -
Awoke to a rebooted Mac (crashed?)
by
rebop2020
3 days, 17 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

