Newsletter Archives
-
A March security patch, for CVE-2020-0796, gets a publicly available proof of concept
If you haven’t yet installed the March or April or May security patches, time to get cookin’.
Ionut Ilascu at Bleeping Computer just reported on a publicly available exploit for the SMB security hole.
Working exploit code that achieves remote code execution on Windows 10 machines is now publicly available for CVE-2020-0796, a critical vulnerability in Microsoft Server Message Block (SMB 3.1.1)… Known by various names (SMBGhost, CoronaBlue, NexternalBlue, BluesDay), the security flaw can be leveraged by an unauthenticated attacker to spread malware from one vulnerable system to another without user interaction.
I don’t see anything out in the wild yet, but it’s only a matter of time.
Yes, you do need to patch sooner or later.
-
MS-DEFCON 3: Get the March 2020 patches installed
It’s been a strange patching month, with a Patch Tuesday, a Patch Thursday, the usual buggy “optional, non-security C/D Week” patch, a bonus fix for a bug introduced in late February’s patch, and a warning (with no patch) about yet another bad-font fallibility.
There are several known bugs, but they all have reasonably well-known workarounds.
Anyway, now’s a good time to make sure you have the March patches installed. Full instructions in Computerworld Woody on Windows.
-
Microsoft posts a fix for the VPN-related dropped internet connection bug
That was quick.
Four days ago, Microsoft posted an acknowledgment of an unusual bug that’s contained in every Windows patch since the “optional, non-security, C/D Week” patch for February.
AskWoody poster @jayinalaska describes it thusly:
Yesterday, I installed the Pulse Secure application on my work PC so I could VPN into a sensitive work network. As soon as I make a connection in the Pulse Secure application, I get the “Limited network” (no internet) warning. I can verify the warning is accurate. During one VPN session, I had Google Drive open in a browser at the same time and was warned I didn’t have a connection any more. As soon as I disconnect from the VPN, the network comes back to normal.
Here’s the announcement:
Out-of-band optional update is available for internet connectivity issues on devices with manual or auto-configured proxies including VPNs
An out-of-band optional update is now available on the Microsoft Update Catalog to address a known issue whereby devices using a proxy, especially those using a virtual private network (VPN), might show limited or no internet connection status.
We recommend you only install this optional update if you are affected by this issue. For more information, see the known issues section for your version of Windows 10 or see the links below.
You can find all 20 of the patches in the Microsoft Update Catalog.
-
Win10 optional updates placed on hold
PATCH WATCH
By Susan Bradley
As the world hunkers down in response to the COVID crisis, so does Microsoft.
On March 24, the company announced it would pause optional non-security patches (C/D-week updates), starting in May. I assume the April releases are already mostly baked.
The primary purpose of C/D-week updates — aka “previews” — is to let enterprises test non-security fixes before the formal releases go out — typically, two or three weeks later.
Microsoft will reportedly continue to ship the official monthly cumulative updates, but with this announcement, the company is clearly putting its focus on critical security patching. In effect, Microsoft is acknowledging that both it and its customers already have a lot on their plates.
Read the full story in AskWoody Plus Newsletter 17.12.0 (2020-03-30).
-
Yet another bug in this month’s Windows patches: Proxy bug knocks out some internet connections
There’s a reason why I wait before recommending that you install patches, yes?
News came yesterday afternoon that every.single.Windows.patch released since the “optional, non-security, C/D Week” patch at the end of February introduces a newly acknowledge bug:
Devices using a proxy might show limited or no internet connection status
Devices using a manual or auto-configured proxy, especially with a virtual private network (VPN), might show limited or no internet connection status in the Network Connectivity Status Indicator (NCSI) in the notification area. This might happen when connected or disconnected to a VPN or after changing state between the two. Devices with this issue, might also have issues reaching the internet using applications that use WinHTTP or WinInet. Examples of apps that might be affected on devices in this state are as follows but not limited to Microsoft Teams, Microsoft Office, Office365, Outlook, Internet Explorer 11, and some version of Microsoft Edge.
According to Microsoft, this bug was introduced in the “optional, non-security, C/D Week” patch for February. If you’re running Win10 1903 or 1909, that’s KB 4535996.
English translation: If you’ve installed any of the Windows updates since last February’s switch to MS-DEFCON 3, you’ve been bitten.
There have been three bad patches: The usual Patch Tuesday cumulative update, KB 4540673 for Win10 1903 and 1909; the emergency, notoriously buggy cumulative update KB 4551762 that was supposed to fix the SMBv3 bug; and KB 4541335, which is the next-to- penultimate “optional, non-security C/D Week” patch for Win10 1903 and 1909. [Correction: We’ll have optional, non-security, C/D Week patches in both April and May. Oh boy.]
If you’re using some other version of Windows, the KB numbers will be different.
Microsoft says “We are working on a resolution and are targeting a Microsoft Catalog only release of an out-of-band update to resolve this issue by early April.” English translation: If you were trusting enough to install any Windows patches since Feb’s switch to MS-DEFCON 3, and you hit a problem connecting to the internet, try rolling back the patch.Or “You might be able to mitigate the issue by restarting your device.”
The problem is odd enough that I haven’t seen it in action. But if your internet connection keeps dropping, you should definitely look at rolling back the buggy update(s). There’s nothing in those patches that needs to be installed, like, right now.
And fer heaven’s sake, don’t voluntarily put your machine in the “cannon fodder” category. Sit back, relax, wait for the problems to appear. And watch the MS-DEFCON level.
-
Reported problem with the latest Windows Defender “Unexpected error”
Oh boy. You know that unpublicized Windows Defender patch that fixed the “Items skipped during scan” bug?
There are two reports on Reddit already about bugs in the new version. Per u/K1Xaviesta:
Hi I just updated my windows 10 and I got a notification that the windows defender is off and when I go to Windows Security and Virus & threat protection to turn it on it says “Unexpected error. Sorry, we ran into a problem. Please try again.”
Are you seeing similar problems after installing KB4052623?
-
Microsoft pauses non-security patches
Microsoft says it won’t be pushing any new non-security patches (although they just pushed one about an hour ago).
We have been evaluating the public health situation, and we understand this is impacting our customers. In response to these challenges we are prioritizing our focus on security updates. Starting in May 2020, we are pausing all optional non-security releases (C and D updates) for all supported versions of Windows client and server products (Windows 10, version 1909 down through Windows Server 2008 SP2).
There is no change to the monthly security updates (B release – Update Tuesday); these will continue as planned to ensure business continuity and to keep our customers protected and productive.
Perhaps you can read the tea leaves better than I can. Is Microsoft saying that, for the foreseeable future, they’re only going to be releasing security patches to Win10? The announcement doesn’t quite say that – and today’s patch is a counterexample – but it certainly hints in that direction.
If so, bravo!
UPDATE: Mary Jo Foley has a recap. But it still doesn’t answer my fundamental question. I think. Will we stop getting non-security patches altogether?
ANOTHER UPDATE: I put together my concerns in this post for Computerworld Woody on Windows. I sure wish MS would learn to speak clearly….
P.S. Why, oh why, isn’t Microsoft using an Insider ring for non-security patches on production versions of Windows?
AN OFFICIAL UPDATE: On Twitter, a few minutes ago, the official @WindowsUpdate account said:
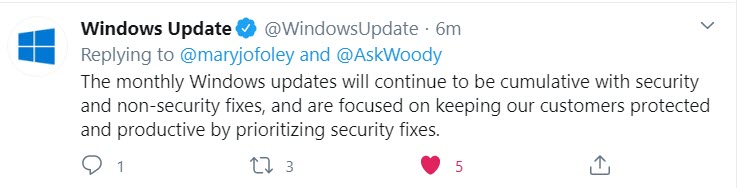
That sounds right to me.
-
Microsoft quietly fixes the “Items skipped during scan” Windows Defender bug
Report out this morning from Günter Born: It appears as if Microsoft has released a new version of Windows Defender that fixes the “Items skipped during scan” bug I talked about in Computerworld yesterday.

It’s listed as KB 4052623. You should get it automatically in the next day or two (Windows Defender updates aren’t controlled by the usual Windows Update settings). It’s also available in the Microsoft Catalog.
-
Microsoft releases the “optional, non-security, C/D Week” patch for Win10 version 1903 and 1909
It’s KB 4541335 – covers lots of little fixes.
As usual, you won’t get it unless you go into Settings > Update & Security, then click the link to Download and install now.
Also as usual, you don’t want it. Let the other WFHers try it first.
-
March 2020 Windows and Office patch status
What a strange month.
Two sky-is-falling security holes with unconscionable “Microsoft warns meeeeeeelions of Windows users that they’re vulnerable” headlines. (Spoiler: The sky isn’t falling.)
A bogus warning about skipped scans.
And lots of people working from home who really don’t need another unstable round of updates or upgrades.
Details in Computerworld Woody on Windows.
We’re still on MS-DEFCON 2. There’s no pressing reason to install this month’s patches. Yet.
-
This month’s “optional, non-security, C/D Week” updates are rolling out
I see 12 new patches in the Microsoft Catalog. Notably KB 4541331 for Win10 1809. There’s nothing out for Win10 version 1903 or 1909, which is common – those usually come later.
The Win 8.1 Monthly Rollup Preview, KB 4541334, doesn’t seem to include anything except the by-now-familiar:
Addresses an issue with evaluating the compatibility status of the Windows ecosystem to help ensure application and device compatibility for all updates to Windows.
In other words, you don’t need it or want it.
No acknowledged bugs as yet.
I don’t see anything for Win7.
Of course, we’re at MS-DEFCON 2: There’s no reason to install any of the March patches yet.
P.S. If you’re running an Exchange Server and haven’t yet installed the February patches, you’re in for an unpleasant surprise. Catalin Cimpanu at ZDNet has details of an active attack.
-
Widespread reports of problems with the second March Win10 cumulative update, KB 4551762, the SMBv3 patch
I was afraid this would happen. When Microsoft releases two security patches back-to-back, it’s rare that the second patch goes in without problems.
I’m seeing lots of reports with problems with Thursday’s post-Patch-Tuesday cumulative update, KB 4551762.
Günter Born kicked off the discussion on Borncity with Windows 10: KB4551762 causes errors 0x800f0988 and 0x800f0900.
Mayank Parmar at Windows Latest has more complaint reports — and they’re extensive:
- The aforementioned errors on installation
- Random reboots
- Performance hits (which are always hard to verify)
People who already have installation issues will be lucky enough to have Windows to automatically repair the patch is manually removed. Alternatively, some will have to undergo the recovery process and reinstall their Windows 10 copy if the PC remains slow and buggy.
We’re also getting lots of reports about the new cumulative update zapping user profiles, just like the original Patch Tuesday patch and last month’s cumulative update.
There are no in-the-wild exploits of the SMBv3 security hole, although there are many Proof of Concept demos. Kevin Beaumont has tried and failed to crack it in a meaningful way. We’ve had a couple of anonymous posts that point to other potential problems, but I haven’t seen any of them in the real world.
Finally, @Alex5723 notes that MS has changed the Knowledge Base article associated with the patch, with a worthwhile inclusion:
SMB Compression is not yet used by Windows or Windows Server, and disabling SMB Compression has no negative performance impact.
Microsoft also inserted a clarification (for Dummies like me!) explaining why the Server Core versions are the ones affected.
‘Softie Nate Warfield tweeted:
Full Server is not released as part of the Windows Semi-Annual Channel releases; only Server Core.
As such, Full Server is not affected, only the listed Server Core editions.
Which is what numerous people told me here on the forum. Thanks, all!
We’re still at MS-DEFCON 2.


