(I rarely, if ever, write about Defender updates so – if I’ve posted in the wrong area then please move.)
Fighting against Defender querying my own activities – like scripting, exploring registry settings, etc. quickly gets tiring. As a result, quite some time ago now, I started switching Defender‘s Block At First Sight feature off by using Brink’s Disable_BlockAtFirstSight.reg file.
This morning I clean-installed my test laptop with Windows 10 Pro 22H2, ran Windows 10 Decrapifier then rolled my usual tweaks in, mostly via .REG files. Finally I connected to the internet and let Windows Update do its thing until it told me several times that it was up-to-date.
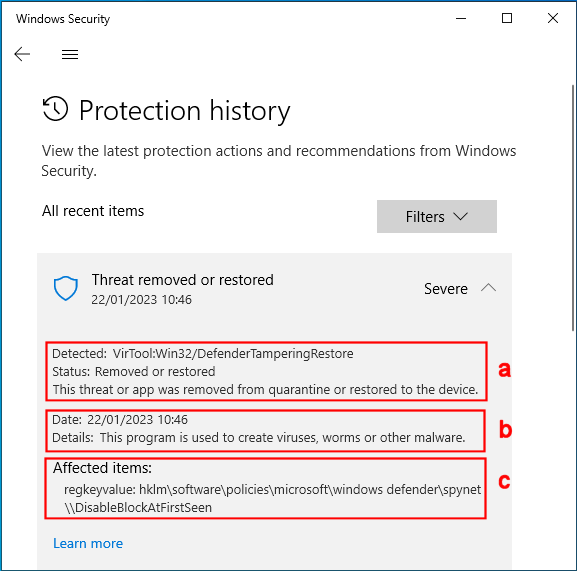
I had a few hours sleep then carried on tweaking. I also ran Windows Update again. As I was tweaking stuff, Defender popped up a Threats found notification, much to my surprise. I checked Defender’s Protection history:
To see whether there was any other information I opened an elevated PowerShell console and ran (Get-MpThreat | Measure-Object).Count which confirmed 1 threat. I also ran Get-MpThreat and was suprised to find even less information than the screenshot above.
I also checked Windows Update‘s Update history and found that two versions of a definitions update, both labelled KB2267602 – one with version 1.381.2529.0; the other with version 1.381.2535.0 had been installed.
I don’t know which definitions update is to blame but the Block At First Sight setting is now deemed a *Severe* threat.
To check, I merged the Disable_BlockAtFirstSight.reg file again then used PowerShell to force an update to Defender‘s definitions. Within seconds another Threats found notification appeared… and the registry entry was deleted again. I waited a bit then did exactly the same again. The registry entry was deleted for the third time.
PS – Perhaps of little interest to most but (Get-MpThreat | Measure-Object).Count still shows a count of 1. So, if Defender gets visited by more than one plague of locusts, Defender still counts it as only one plague?