We’re seeing numerous reports of problems with the March Internet Explorer Security-only patches. These are the patches that you have to download and
[See the full post at: More problems with the March IE Security-only patches]

|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
More problems with the March IE Security-only patches
Home » Forums » Newsletter and Homepage topics » More problems with the March IE Security-only patches
- This topic has 71 replies, 23 voices, and was last updated 8 years, 1 month ago by
anonymous.
Tags: KB 4012204 KB 4016446 Logjam
AuthorTopicViewing 29 reply threadsAuthorRepliesanonymous
Guestdgreen
AskWoody LoungerApril 1, 2017 at 9:16 am #105861bringing over my latest find from my original post on another thread….
“Ok, I did more research. Kb3061518 was superceded many times over, so I’m ok with that.
I did download the IE11 Cumulative Kb4012204 update first.
Rebooted then downloaded and applied the Hot fix patch Kb401664.Did the Logjam test and passed.
Seriously, after spending hours of this……
Group A is looking better to me”.just to add that I downloaded the updates to my download folder (from woody’s link) then installed them.
BTW, I’m a “her”. (:
1 user thanked author for this post.
-
walker
AskWoody LoungerApril 1, 2017 at 11:14 am #105890I do not ever use the IE11 which I have, however have always kept it updated. Is it still necessary to install these TWO updates for the IE? Also I have no clue as to what the “logjam” test is. It is becoming more and more difficult to try to stay in Group B at this point in time.
It would be great if it is NOT necessary to install the IE updates since I never use it. Your guidance will be most sincerely appreciated. Thank you. 🙂
-
PKCano
Manager -
walker
AskWoody LoungerApril 1, 2017 at 3:50 pm #106010PKCano: Thank you very much for the information. I know that in the past I was aware that the IE11 had to be updated because of other components which affected my Win 7 OS. I appreciate the guidance with this and now know that it is impossible to ever be free of those updates. Your help is most appreciated 🙂
-
-
-
anonymous
GuestApril 1, 2017 at 10:42 pm #106071@ walker
According to https://en.wikipedia.org/wiki/Logjam_(computer_security), you need millions of US$ in financial resources to exploit the Logjam vulnerability to intercept nearly any Internet communications of a target/suspect. The NSA have been doing it.
Maybe, with these problematic Security-Only updates for IE11, M$ wanna deprecate the security of Win 7/8.1 computer users who have chosen Group B against their wishes, in order to push them onto Group A.
1 user thanked author for this post.
-
Charlie
AskWoody PlusApril 2, 2017 at 2:00 pm #106209Yes indeed. Also making group B’ers spend hours, if not days gathering info., trying to understand it, making sure they have the exact proper order to install each one, and then have to test to see if you were successful. What a mess. It does make one feel like giving up and playing M$’s game, but I’m an ornery cuss, and thanks to Woody and all who contribute so much to this site, I can resist!
Being 20 something in the 70's was so much better than being 70 something in the insane 20's
-
rc primak
AskWoody_MVPlizzytish
AskWoody LoungerApril 1, 2017 at 9:53 am #105872Well Woody, on my Win7 pro B group machine I downloaded and installed the security only IE patches as per your guidelines. I usually use Iron/chrome and on reading the above I used the link for the test……. I failed with Iron/chrome………. realised I should have used IE which I then did and found that I passed!
Your user agent has good protocol support.
Your user agent supports TLS 1.2, which is recommended protocol version at the moment.The reason for the Iron/chrome failure was suspected firewall restrictions. Hope this helps. LT

JNP
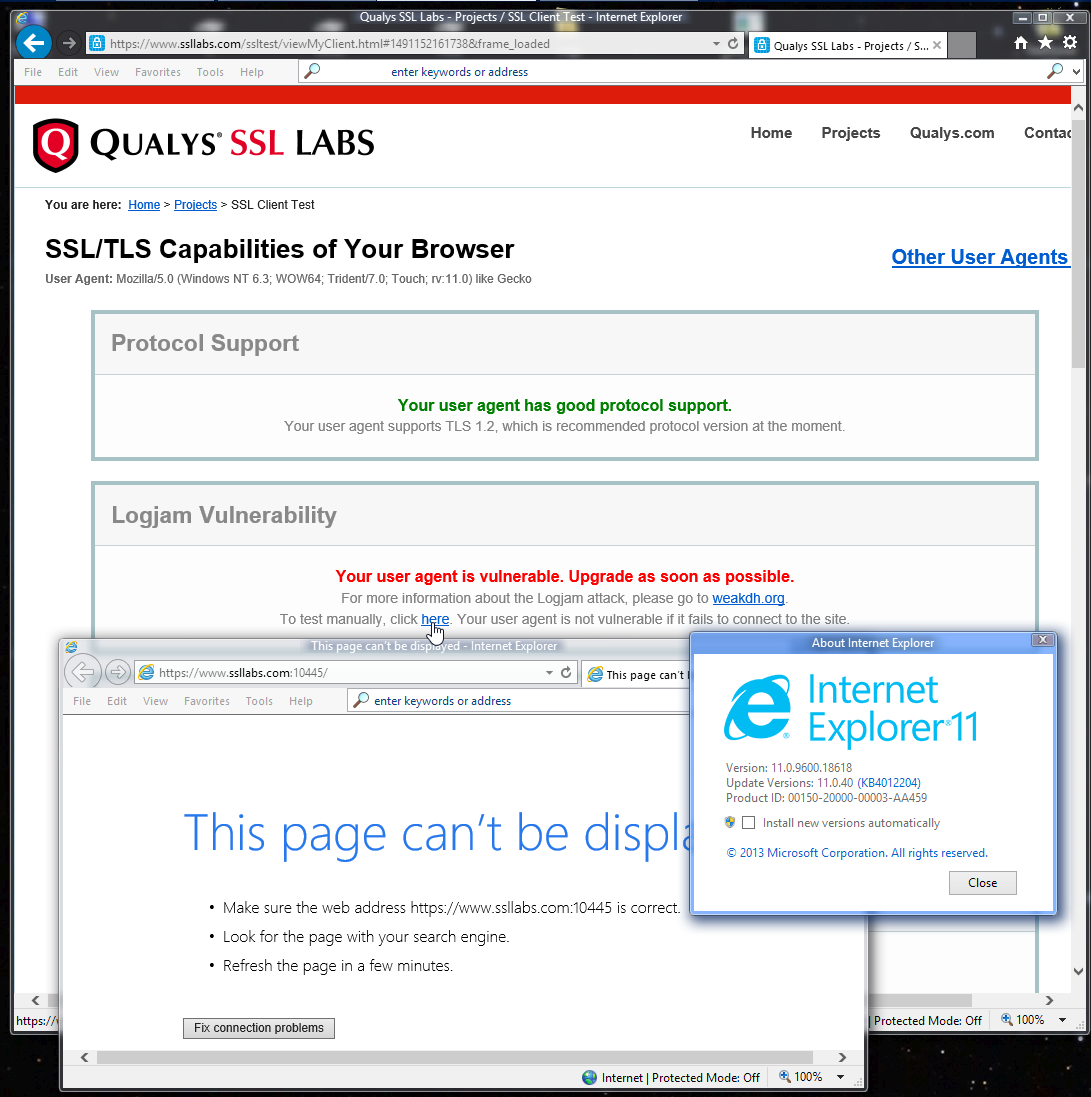
AskWoody LoungerApril 1, 2017 at 10:29 am #105879Woody,
Win7 SP1-64 bits, Group B. Both kb4016446 and kb4012204 installed. Ran SSL Qualys. Full results:
SSL/TLS Capabilities of Your BrowserUser Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; MDDCJS; rv:11.0) like Gecko
Other User Agents »
Protocol Support
Your user agent has good protocol support.
Your user agent supports TLS 1.2, which is recommended protocol version at the moment.
Logjam Vulnerability
Your user agent is not vulnerable.For more information about the Logjam attack, please go to weakdh.org.
To test manually, click here. Your user agent is not vulnerable if it fails to connect to the site.FREAK Vulnerability
Your user agent is not vulnerable.For more information about the FREAK attack, please go to http://www.freakattack.com.
To test manually, click here. Your user agent is not vulnerable if it fails to connect to the site.POODLE Vulnerability
Your user agent is not vulnerable.For more information about the POODLE attack, please read this blog post.
Protocol Features
Protocols
TLS 1.3 No
TLS 1.2 Yes
TLS 1.1 Yes
TLS 1.0 Yes
SSL 3 No
SSL 2 NoCipher Suites (in order of preference)
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) Forward Secrecy 256
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (0xc027) Forward Secrecy 128
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014) Forward Secrecy 256
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (0xc013) Forward Secrecy 128
TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 (0x9f) Forward Secrecy 256
TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 (0x9e) Forward Secrecy 128
TLS_DHE_RSA_WITH_AES_256_CBC_SHA (0x39) Forward Secrecy 256
TLS_DHE_RSA_WITH_AES_128_CBC_SHA (0x33) Forward Secrecy 128
TLS_RSA_WITH_AES_256_GCM_SHA384 (0x9d) 256
TLS_RSA_WITH_AES_128_GCM_SHA256 (0x9c) 128
TLS_RSA_WITH_AES_256_CBC_SHA256 (0x3d) 256
TLS_RSA_WITH_AES_128_CBC_SHA256 (0x3c) 128
TLS_RSA_WITH_AES_256_CBC_SHA (0x35) 256
TLS_RSA_WITH_AES_128_CBC_SHA (0x2f) 128
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 (0xc02c) Forward Secrecy 256
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 (0xc02b) Forward Secrecy 128
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 (0xc024) Forward Secrecy 256
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 (0xc023) Forward Secrecy 128
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (0xc00a) Forward Secrecy 256
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (0xc009) Forward Secrecy 128
TLS_DHE_DSS_WITH_AES_256_CBC_SHA256 (0x6a) Forward Secrecy2 256
TLS_DHE_DSS_WITH_AES_128_CBC_SHA256 (0x40) Forward Secrecy2 128
TLS_DHE_DSS_WITH_AES_256_CBC_SHA (0x38) Forward Secrecy2 256
TLS_DHE_DSS_WITH_AES_128_CBC_SHA (0x32) Forward Secrecy2 128
TLS_RSA_WITH_3DES_EDE_CBC_SHA (0xa) 112
TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA (0x13) Forward Secrecy2 112
(1) When a browser supports SSL 2, its SSL 2-only suites are shown only on the very first connection to this site. To see the suites, close all browser windows, then open this exact page directly. Don’t refresh.
(2) Cannot be used for Forward Secrecy because they require DSA keys, which are effectively limited to 1024 bits.Protocol Details
Server Name Indication (SNI) Yes
Secure Renegotiation Yes
TLS compression No
Session tickets No
OCSP stapling Yes
Signature algorithms SHA512/RSA, SHA512/ECDSA, SHA256/RSA, SHA384/RSA, SHA1/RSA, SHA256/ECDSA, SHA384/ECDSA, SHA1/ECDSA, SHA1/DSA
Elliptic curves secp256r1, secp384r1
Next Protocol Negotiation No
Application Layer Protocol Negotiation No
SSL 2 handshake compatibility NoMixed Content Handling
Mixed Content Tests
Images Passive Yes
CSS Active No
Scripts Active No
XMLHttpRequest Active No
WebSockets Active No
Frames Active No
(1) These tests might cause a mixed content warning in your browser. That’s expected.
(2) If you see a failed test, try to reload the page. If the error persists, please get in touch.Related Functionality
Upgrade Insecure Requests request header (more info) No
edit to remove HTMLanonymous
Guest-
lizzytish
AskWoody LoungerApril 1, 2017 at 8:25 pm #106031Well…….. I rebooted after each installation. Mind you I tried to install the ‘fix’ after installing the main IE patch, and my machine wouldn’t let me……….. I had to reboot before being able to proceed with the other. So that and also the client browser configuration that has been also mentioned could possible be the reason for some not working. But I must say so far touch wood and whistle…… Group B has been working for me very well……. and I really don’t see any cause to regret my being in Group B. Thanks to Woody and those who have given their input! LT

1 user thanked author for this post.
Charlie
AskWoody PlusApril 1, 2017 at 12:01 pm #105901When things get this bad I always think of what the average John or Jane Q. Public computer user is going to do. But then, they’re probably already on Win 10 and maybe even happy. I’m gonna let it go there, any more and I’d have to put this in the rant section.
Being 20 something in the 70's was so much better than being 70 something in the insane 20's1 user thanked author for this post.
anonymous
GuestApril 1, 2017 at 12:09 pm #105898Well, I had installed the first update when it came out and saw no problems. I saw this, and I checked and found I was vulnerable. I installed the hotfix, and after a restart, checked again. I was still vulnerable, although everything else was OK. I just uninstalled both updates, and on checking again, I came up as not vulnerable. I alternate between IE and Firefox, depending on website; and am uncertain what to do at this point. I’m group B, using a Dell XPS7100 (64 bit).
grayslady
AskWoody Lounger-
PKCano
Manager -
grayslady
AskWoody LoungerApril 1, 2017 at 1:06 pm #105925Yep. Rebooted everything individually, just to be sure, even if the pop-up window didn’t say a restart was required. I’m more concerned that even with the new patches uninstalled IE is failing the logjam test. My hard drive crashed in December so I re-installed Windows 7 plus IE11 with all patches through October, 2016 and security only thereafter. I didn’t even know about logjam, or the test for logjam, until reading these last couple of articles here on Ask Woody.
1 user thanked author for this post.
-
anonymous
GuestApril 1, 2017 at 1:57 pm #105955Okay, I solved the problem! In Windows 7, SSL 2.0 must, repeat must, be disabled. There is a known conflict between SSL 2.0 and TLS 1.2 on Windows 7. If SSL 2.0 is enabled, Windows 7 will not pass the logjam test. Period. As soon as I changed the security settings in Internet Options, Advanced, in Internet Explorer, my computer passed the logjam test–first, without the updates installed, then with the IE 11 update installed, and, finally, with both the update and the hotfix installed. Hurray!
-
Canadian Tech
AskWoody_MVP -
PKCano
Manager -
anonymous
GuestApril 1, 2017 at 3:23 pm #105993Well, I am post 105898 (justaned-not yet registered). I just checked my settings and no ssl is checked; neither ssl2.0 nor ssl3.0, and I failed logjam with both installed. I passed with both removed. I’m attempting to reply to PKCano’s post 105966; not sure it will show in the proper place. #105967 says only tls12 is checked, whereas I have all 3 checked;1.0, 1.1 and 1.2. No idea if this helps or not, but…
BTW, I tried to reply using IE, and was unable to get the blinking curser. I had to switch to Firefox.
justaned
-
-
-
anonymous
GuestApril 1, 2017 at 1:02 pm #105921-
PKCano
Manager -
anonymous
Guest
-
The Surfing Pensioner
AskWoody PlusCanadian Tech
AskWoody_MVPApril 1, 2017 at 1:18 pm #105932-
anonymous
GuestApril 2, 2017 at 12:29 am #106096Agree. Might be time to lock down Windows 7 and 8.1 like XP for those who are comfortable doing this. Suspect they are having problems with providing updates for what we call Group B, ie, they can’t seem to do it now they have separated into two updating methods. Also, aren’t their update catalog pages insecure anyway? Wonder if this has something to do with this problem.
-
212louis
AskWoody Lounger -
RCPete
AskWoody LoungerApril 2, 2017 at 11:11 am #106153I’ve been planning for Group W (or “L”). One laptop is Win 7, currently up to date (Group B). I’m keeping the financial data on it as well as the Windows-only applications. Haven’t decided if it will go on line or not. The main reason it’s going on line is for updates and virus definitions. If it were isolated from the ‘net, we’d still be fine.
The other Win 7 machine is my main web-surfer. I’ve found Linux equivalents for everything it needs to do, and I’ve prepared a Linux laptop with the packages I’ll need. I’m already using Pale Moon for Linux on that laptop; it’s easy to copy the profile from one machine to the other.
1 user thanked author for this post.
anonymous
Guestanonymous
GuestApril 1, 2017 at 1:33 pm #105943The problem is at the server end. My understanding is that the patches are OK.
“it is important to note that this is a flaw in the TLS protocol and not a vulnerability due to the implementation itself”. The browser is able to detect the insecure connection.
-
anonymous
Guest -
rc primak
AskWoody_MVPApril 2, 2017 at 8:54 am #106139If the server tries to connect with insecure protocols, the browser must defend itself by refusing the connection. Otherwise, there will be a vulnerability. But if the browser refuses the connection, the site may fail to load. Which from a security point of view is good, and makes the user not vulnerable to the exploit.
It does not just depend on the server end. But a secure server will not show the vulnerability even if the browser is not secure. It is the combination of an insecure server and an insecure browser which allows the vulnerability to be exploited. Hence the need to patch the browser.
-- rc primak
anonymous
Guestzero2dash
AskWoody Loungeranonymous
GuestApril 1, 2017 at 3:33 pm #106002Yesterday I installed the March security-only updates on three Windows 7 Pro 64bit SP1 computers: KB4012212, KB4012204, KB4016446 in that order and rebooting after each one. I barely use IE but after reading this I fired it up to do the Logjam test. It passes on all three computers. Sorry to be boring!
anonymous
GuestApril 1, 2017 at 3:42 pm #106006Two machines here- long term very basic user – HP Win 8.1 64-bit i-5 desktop circa 2012 and HP Win 8.1 64-bit i-3 Hybrid notebook. Both have Office 2010.
Group B – have updated both, Security Only, Office, Silverlight & Adobe (though I do not use), MSRT. Plus let through INTEL – System 8/9/2016 on both and NVIDEA drivers (foolishly I now realise?). I wasn’t offered IE 11 updates on either machine which I was expecting.
All seems OK so far EXCEPT for Windows Update settings…the main screen which was showing the Crossed Red Shield Never Check setting was changed to the Yellow Check Now setting.
In the Change Settings screen, the Red Shield Never Check is showing, with my tick still there in Update Microsoft products when I Update Windows.
I have reticked the Never Check, OKed it and in Settings this is what it says, but still the Yellow Check For Updates is displayed and this is what happens…..what is going on?
-
anonymous
GuestApril 1, 2017 at 4:08 pm #106013Same poster – just to add, now realise you manually download the IE updates separately, which I have not done, especially after reading the other messages again.
I use Firefox and did the check described and it is fine. Don’t use IE these days, but understand it should be updated. Will leave until clear or should I risk it?
Very nervous now.
Deep Lurker
AskWoody LoungerApril 1, 2017 at 3:46 pm #106008Could the installation method be part of the problem? Like if you installed both IE patches before rebooting?
Could well be. I was the “anonymous” who reported trouble with Notepad++ and I installed the security-only patch plus both IE patches before rebooting. Things went back to normal after uninstalling both IE patches and then rebooting.
I just tried reinstalling both IE patches, rebooting after the first one. The second one didn’t request a reboot. Things look OK now – I don’t see the problems I had before with Notepad++ or the SFC:OP game.
1 user thanked author for this post.
-
Deep Lurker
AskWoody LoungerApril 2, 2017 at 3:13 pm #106224I may have spoken too soon; I’ve noticed other, more subtle problems such as my custom power-management profile being switched out on restarting and various slow downs in my system. I’ve uninstalled the IE updates again and plan to keep them uninstalled. In fact, I’m at the point of being ready to jump from Group B to Group W.
1 user thanked author for this post.
davinci953
AskWoody PlusApril 1, 2017 at 5:06 pm #106018Could the installation method be part of the problem? Like if you installed both IE patches before rebooting?
Could well be. I was the “anonymous” who reported trouble with Notepad++ and I installed the security-only patch plus both IE patches before rebooting. Things went back to normal after uninstalling both IE patches and then rebooting. I just tried reinstalling both IE patches, rebooting after the first one. The second one didn’t request a reboot. Things look OK now – I don’t see the problems I had before with Notepad++ or the SFC:OP game.
It was an installation problem for me. After installing KB 4012204, I didn’t reboot and installed KB 4016446. I then rebooted. IE failed the Logjam test.
I uninstalled both IE patches, installed KB 4012204 and rebooted when prompted. I then installed KB 4016446. This patched also prompted a reboot. After installing KB 4012204, I ran the Logjam test, and IE passed. After installing KB 4016446, I ran the Logjam test again, and IE passed.
Noel Carboni
AskWoody_MVPApril 1, 2017 at 9:08 pm #106048It occurs to me to wonder…
What good does it do Microsoft to release bug-free patches to older software?
Yeah, I really do think TODAY’s Microsoft really would stoop so low as to make their “support” of older systems a pain to make people crave better. They still apparently don’t realize Windows 10 is widely known as “not better”.
Perhaps you subscribe to the philosophy of “never attribute to malice that which can be explained by incompetence“… Fair enough. Unfortunately, it’s not all that much better than the first theory.
I don’t think I’m going to install the March updates myself on any of my Win 8.1 and older systems. Not yet anyway. Tweaking Win 10 Creator’s Update into becoming a desktop-only system in a test VM has me distracted for now.

-Noel
-
AlexEiffel
AskWoody_MVPApril 1, 2017 at 10:01 pm #106065 -
anonymous
GuestApril 2, 2017 at 12:30 am #106097If M$ makes it enough of a pain to maintain Windows 7/8, then Windows 10 will look “better” if only by comparison to the trouble that holdouts need to go through.
That should be enough to convince some percentage of Win 7 users who dislike Win 10 but lack the time or inclination or skills to keep messing with the ever-more convoluted ways to keep 7 up to date.
-
zero2dash
AskWoody LoungerApril 2, 2017 at 1:20 am #106107Unfortunately it doesn’t do them any good, and it doesn’t seem like they care anyway. Some people have no recourse regardless, and those who do have moved on or are in the process of moving on.
2-5 years from now, I think MS will be asking “what went wrong” because I think they’ve gone further than burning bridges; they’re napalming the forests too. They still think they’re the only game in town, and yet they’re too oblivious to realize that no, they’re not.
Geo
AskWoody Plus-
Charlie
AskWoody Plus
anonymous
Guest-
anonymous
GuestApril 1, 2017 at 11:24 pm #106087Perhaps that Logjam test is unreliable. I suggest trying the other two Logjam tests listed at https://www.askwoody.com/forums/topic/ie-security-update-kb-4012204-trips-a-logjam-security-test-warning/#post-106085.
anonymous
Guestcmar6
AskWoody PlusApril 2, 2017 at 9:26 am #106140This may be related to 3/17 IE Security patch if that was included in the bundled Windows 10 update. But after my “successful” Windows 10 patch when it went t MS-Defcon3, I find that Windows 10 does not fully shut down. I have to hold down the start button on the system to fully shut it down.
Noel Carboni
AskWoody_MVPApril 2, 2017 at 12:00 pm #106164davinci953
AskWoody PlusApril 2, 2017 at 2:18 pm #106213I think this screen grab says it all: The results from the ssllabs.com page are inconsistent at best. Some folks up above have noticed this as well. I suggest not basing any decisions on such results. -Noel
I think you might be right. After I updated a Windows 8.1 system yesterday, the sslabs.com page indicated the user agent was vulnerable for Logjam. It also showed IE as vulnerable before I installed the patches. I checked the ssllabs.com page today, and it’s now indicating the user agent is not vulnerable. I used the manual check as well, and the page did not display.
anonymous
Guestanonymous
GuestApril 2, 2017 at 5:25 pm #106251I think Noel may be on to something. Both win 7 computers on Group B done manually from MS catalog with 4012212 and 4012204 ONLY (no hotfix installed since it is needed if you had installed KB 4013073, “Forms in Dynamics CRM 2011 are broken after KB 4013073 for Internet Explorer 11 is installed”) seem to be OK with the SSL Labs test.
-
walker
AskWoody LoungerApril 3, 2017 at 1:42 pm #106369 -
PKCano
ManagerApril 3, 2017 at 1:50 pm #106372See the reply here https://www.askwoody.com/forums/topic/ie-security-update-kb-4012204-trips-a-logjam-security-test-warning/#post-106364
1 user thanked author for this post.
-
-
anonymous
GuestApril 3, 2017 at 2:52 pm #106383Walker, I think I saw your question about KB 4016446 and it wasn’t answered. As far as I can tell, based on the MS site, you don’t need the “hotfix” if you did not install KB 4013073.
https://support.microsoft.com/en-us/help/4016446/forms-in-dynamics-crm-2011-are-not-displayed-correctly-after-kb-401307 (yes the last 3 is missing).
“Forms in Microsoft Dynamics CRM 2011 are not displayed correctly after KB 4013073 is installed on a Windows system that is running Internet Explorer 11.”
Also if you are not using MS Dynamics 2011 does it really matter?
Hope this helps.
1 user thanked author for this post.
-
walker
AskWoody LoungerApril 3, 2017 at 4:31 pm #106407@anonymous: I think PKCano answered the question, however I appreciate you taking the time to reply to my question as well. I appreciate all of the help I can get (being “totally computer illiterate). Thank you for the information, and for taking the time to reply. 🙂
-
anonymous
Guest
-
anonymous
GuestApril 5, 2017 at 1:23 pm #106698ARE THE MARCH IE SECURITY-ONLY PATCHES KB4012204 & KB4016446 SAFE?
Many Thanks as usual to you Woody and especially PK Cano for the March Windows Update Group B navigation!
Have done all you have advised and used PK’s excellent AKB article 2000003 to sort it.
Except the March IE Security-Only Patches.
Still not sure they’re safe.
As you advise I don’t use IE as a browser – Firefox is fine!
I do keep IE going because as PK says:
“IE is an integral part of Windows and, as such, needs to be updated even if you don’t use it. The system uses it. So yes, you need to apply the IE11 patches every month.”
<So are IE patches KB4012204 & KB4016446 really OK?
Or should I wait for another Hotfix of the Hotfix!
Cheers Mates!
sainty?⚓️⛵️??Edited to remove HTML. Please convert your replies to text.
-
PKCano
Manager -
anonymous
GuestApril 5, 2017 at 2:01 pm #106726 -
PKCano
Manager -
Kirsty
ManagerApril 5, 2017 at 2:13 pm #106734Thanks PK for your swift and clear response for this Non-Tekkie! It was all going over my head with MSIP – Microsoft Induced Paranoia! I don’t know how much Woody is paying you for your fine contributions but treble it!
What a lovely thought! 🙂
Askwoody is funded by donations, and staffed by volunteers, who really appreciate your feedback.
https://www.askwoody.com/forums/topic/betanews-microsoft-is-disgustingly-sneaky-windows-10-isnt-an-operating-system-its-an-advertising-platform/#post-100800
-
anonymous
GuestApril 5, 2017 at 4:10 pm #106762
-
-
-
Viewing 29 reply threads - This topic has 71 replies, 23 voices, and was last updated 8 years, 1 month ago by
-

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Help with WD usb driver on Windows 11
by
Tex265
36 minutes ago -
hibernate activation
by
e_belmont
1 hour, 26 minutes ago -
Red Hat Enterprise Linux 10 with AI assistant
by
Alex5723
5 hours, 14 minutes ago -
Windows 11 Insider Preview build 26200.5603 released to DEV
by
joep517
8 hours, 18 minutes ago -
Windows 11 Insider Preview build 26120.4151 (24H2) released to BETA
by
joep517
8 hours, 20 minutes ago -
Fixing Windows 24H2 failed KB5058411 install
by
Alex5723
11 hours, 30 minutes ago -
Out of band for Windows 10
by
Susan Bradley
13 hours, 3 minutes ago -
Giving UniGetUi a test run.
by
RetiredGeek
20 hours ago -
Windows 11 Insider Preview Build 26100.4188 (24H2) released to Release Preview
by
joep517
1 day, 3 hours ago -
Microsoft is now putting quantum encryption in Windows builds
by
Alex5723
1 day, 1 hour ago -
Auto Time Zone Adjustment
by
wadeer
1 day, 8 hours ago -
To download Win 11 Pro 23H2 ISO.
by
Eddieloh
1 day, 5 hours ago -
Manage your browsing experience with Edge
by
Mary Branscombe
10 hours, 22 minutes ago -
Fewer vulnerabilities, larger updates
by
Susan Bradley
21 hours, 18 minutes ago -
Hobbies — There’s free software for that!
by
Deanna McElveen
5 hours, 12 minutes ago -
Apps included with macOS
by
Will Fastie
3 hours, 4 minutes ago -
Xfinity home internet
by
MrJimPhelps
1 day, 1 hour ago -
Convert PowerPoint presentation to Impress
by
RetiredGeek
1 day, 1 hour ago -
Debian 12.11 released
by
Alex5723
2 days, 5 hours ago -
Microsoft: Troubleshoot problems updating Windows
by
Alex5723
2 days, 8 hours ago -
Woman Files for Divorce After ChatGPT “Reads” Husband’s Coffee Cup
by
Alex5723
1 day, 12 hours ago -
Moving fwd, Win 11 Pro,, which is best? Lenovo refurb
by
Deo
49 minutes ago -
DBOS Advanced Network Analysis
by
Kathy Stevens
3 days, 1 hour ago -
Microsoft Edge Launching Automatically?
by
healeyinpa
2 days, 16 hours ago -
Google Chrome to block admin-level browser launches for better security
by
Alex5723
13 hours, 59 minutes ago -
iPhone SE2 Stolen Device Protection
by
Rick Corbett
2 days, 20 hours ago -
Some advice for managing my wireless internet gateway
by
LHiggins
2 days, 4 hours ago -
NO POWER IN KEYBOARD OR MOUSE
by
HE48AEEXX77WEN4Edbtm
1 day, 6 hours ago -
A CVE-MITRE-CISA-CNA Extravaganza
by
Nibbled To Death By Ducks
3 days, 14 hours ago -
Sometimes I wonder about these bots
by
Susan Bradley
1 day, 2 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.