-
Microsoft snooping through Office
Just saw this post in the comments from JIY:
Upon reading ox’s post, I thought to check my installs of Office 2010 Pro Plus, as well as the Win 7 installs, on all machines for CEIP being in the “off” position. I always install MS (and most other) software that way. Because of this from Office 2013:
“When you participate, we collect basic information about how you use your programs, your computer or device, and connected devices. We also collect information about how each is set up and performing. These reports are sent to Microsoft to help improve the features our customers use most often and to create solutions to common problems.”
Okay, we’ve all read that one before. However, in light of the recent “burrowing”, I’m reading that language a bit differently today.
The Win 7 installs all were CEIP off. All three Office installs were CEIP “on” (i.e., box checked when looking at that setting). There is NO CHANCE I installed Office that way. I know right where that installation checkbox is and that you check it off before “Next”. Same thing Oracle does with Java installer and the ASK Toolbar and switch home page “offer”. I have installed Office at least 100 times.
Office updates, security and otherwise, are always allowed. Never thought to check that setting. Wonder if that switch (now unchecked) will get flipped again next month? So thanks!
-
News from Josh Mayfield, the GWX Control Panel developer
Just saw this on Josh’s site:
Hi folks, I’ve had virtually no personal time in the past week due to work, so haven’t been able to respond to emails or blog comments much.
I am aware of the new Microsoft updates (KB3139929 and KB3146449) that infect Internet Explorer with Windows 10 ads and I am actually putting several other GWX Control Panel features on hold in order to study and hopefully fix and/or prevent those patches. Keep an eye on the “News and Hot Tips” section of this post over the next few days; I will update once I know more and have a fix.
If you have questions about other Windows Update patches, please read the first topic of theGWX Control Panel FAQ.
If you’re looking for other assistance with the program, please read about the “Save Diagnostic Info” feature at this post and contact me with details, with the understanding that I might be rather slow to respond, due to having very little personal time outside of work in recent weeks.
-
Windows 10 upgrade starting automatically – and it happened to me
I’ve seen more and more reports in the past 24 hours of the Windows 10 upgrade kicking off spontaneously: People using Windows 7 suddenly find that their machines are upgrading to Windows 10, without any input or interference from them.
I can now report that it’s true. I watched it first-hand, on my own machine, overnight.
As couple of weeks ago, I built a test Windows 7 Pro virtual machine using Hyper-V in Win10. Brought it from SP1 through all of the updates (a long process), not checking or unchecking any options. It’s a clean machine, used for testing all sorts of things.
Last night, I cranked the machine up and saw the GWX icon in the system tray.Oh boy.
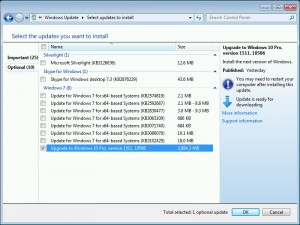
Looking at Windows Update, I saw that the “Upgrade to Windows 10 Pro, version 1511, 10586” box was checked (see screenshot). Of course, this is a Win7 Pro test machine. The last thing I want to do is change it to Windows 10.1.
I unchecked the box, and left the machine running overnight.
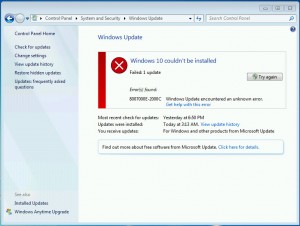
This morning, I woke up to a notice that Windows 10 couldn’t bee installed (see screenshot), failing with an error 80007000E-2000C.
Usually error 80007000E means one of the installation files is scrambled. Sure enough, the C:\Windows\SoftwareDistribution folder has 1.7 GB in it.
When I run “Check for updates,” the old “Upgrade to Windows 10 Pro, version 1511, 10586” is listed, and its box is checked. Windows Update now tells me “Upgrade to Windows 10 / Start installing the newest version of Windows now.” The only button on the dialog says “Get Started.”
If this were a real, working machine, I would’ve run GWX Control Panel long ago. But it’s a test machine, and I don’t want to flip those bits.
I tried deleting the \SoftwareDistribution folder and couldn’t — “The action can’t be completed because the folder or a file in it is open in another program.” Meh. A little trial and error revealed that I could delete everything except the subfolder \DataStore and the ReportingEvents.log file – a total of 1 GB.
I’ve unchecked the “Upgrade to Windows 10 / Start installing the newest version of Windows now” box again, and will use the VM for more testing today. Let’s see what happens.
UPDATE: Dang if it didn’t happen again. Really. I was away from the computer for a couple of hours, came back, and the “Upgrade to Windows 10 / Start installing the newest version of Windows now” box is checked again. I unchecked it, clicked OK, “X”d out of Windows Update. Let’s see what happens next.
IMPORTANT: As AW notes in the comments, if this happens to you — if Windows 7 or 8.1 suddenly decides to install Win10, all on its own — you still have one fallback point. The very last step in the new installation sequence involves clicking “Accept” on the EULA, the End User License Agreement. If you click “Decline,” the whole update unwinds and your system should be restored to its original Windows 7 or 8.1 state. (Note the operative term “should.”)
If you or someone you know made a mistake and clicked “Accept” on the EULA, they’re running Windows 10 now. I strongly recommend that you immediately go back to Windows 7 or 8.1 using the built-in tools. Detailed instructions in my InfoWorld feature “How to roll back your Windows 10 upgrade.”
t/h Bogdan Poppa Softpedia
-
Is the metered connection trick to block Win10 updates working for you?
I’m seeing very sporadic reports, where Win10 users swear they have set their internet connection to metered, but Win10 is delivering cumulative updates (and possibly other updates) anyway.
I’ve never seen that on any of my machines, so I’m very interested in hearing from anyone who has.
Please post here! Tell me which update(s) ignored the “metered connection” setting. (I expect that Windows Defender and the MSRT go through.)
-
Bad patch lists
 Speaking of elevating comments to the front page, I just got this comment from CAB:
Speaking of elevating comments to the front page, I just got this comment from CAB:I’d like to know if this list of MS ‘patches’ to not install(or hacks, whatever you want to call them) is complete, or too many:
2952664, 2976978 2977759, 3021917, 3022345, 3035583, 3068708, 3075249,3080149, 3083324, 3090045, 3112343, 3136449, 3123862, 3146449
My response:
I’ve tried hard to avoid recommending any specific list. Why? Most people don’t have the time or the interest to go back and fix what’s been broken – and there are varying perspectives as to what is “broken” anyway.
My approach is to go forward with just a few simple rules:
1. Wait. Don’t install any patches until there’s been a sufficient time to see if they’re causing any problems. That’s what this site is all about – and has been for many years.
2. In the future, only install security patches for Win7 and 8.1. Don’t install optional patches. Every time I change the “MS-DEFCON” level, I include detailed instructions.
3. Run GWX Control Panel frequently.
That’s pretty simple, and it’s a formula just about anybody can follow – along with a few nudges when the MS-DEFCON level changes.
That said, other folks with “bad patch” lists should feel most welcome to post them here. I’d be happy to pass them on.
(Reader PO also points to an alternative set of patches on the AddictiveTips forum. I don’t know the principals there, so take the list with much salt.)
A NEW UPDATE: Here’s the updated list from wdburt1, incorporating observations from Vesselin Bontchev.
For emphasis: I do NOT recommend that you go into your computer and uninstall these patches. Just be aware of the fact that Microsoft’s snooping routines are changing, and that MS has pushed a whole lotta stuff onto Win7 machines to grease the skids for Win10.
Here’s the new list. I hope it comes through with the proper formatting. I have shamelessly cribbed some descriptions from Bontchev’s list, most of which were taken from Microsoft’s KB article descriptions.
My list of Microsoft malware Updated March 14, 2016:
KB971033–Update for Windows activation technologies*
KB2876229–Updates Skype, sets MSN/Bing as defaults
KB2902907–Description not available, update was pulled by Microsoft*
KB2922324–Description not available, update was pulled by Microsoft*
KB2952664–Installed itself on RH computer 12/1/15 even though not selected. Installed itself on RH computer in 3/3/16 update even though not checked.
KB2966583–Improvements for the System Update Readiness Tool in Windows 7
KB2976978–Performs and collect compatibility appraiser logs in order to ease the upgrade experience to Windows 10
KB2977759–Compatibility update for Windows 7 RTM (for Windows Customer Experience Improvement Program)
KB2990214–Update to upgrade from Windows 7 to a later version of Windows
KB2999226–The Windows 10 Universal C Runtime (CRT) is a Windows operating system component that enables CRT functionality on the Windows operating system. This update allows Windows desktop applications (Windows Store, other apps) that depend on the Windows 10 Universal CRT release to run on earlier Windows operating systems.
KB3012973–Upgrade to Windows 10
KB3014460–Update for Windows insider preview /upgrade to Windows 10*
KB3015249-Update that adds telemetry points to consent.exe in Windows 8.1 and Windows 7*
KB3021917–Update to Windows 7 SP1 for performance improvements
KB3022345–Update for customer experience and diagnostic telemetry
KB3035583 (THE BAD BOY)–Installs ‘Get Windows 10’ app in Win 8.1 and Win 7 SP1 (GWX)
KB3044374–Update that enables you to upgrade from Windows 8.1 to Windows 10
KB3046480–Update enables the system to determine whether to migrate the Microsoft.NET Framework 1.1 to a later version of Windows when you upgrade from Windows 8.1 or Windows 7 to a later version of Windows.
KB3050265–Updates Windows Update Client for Windows 7 (changes system files to support upgrade)
KB3050267–Updates Windows Update Client for Windows 8.1 (changes system files to support upgrade*
KB3065987–Updates Windows Update Client for Windows 7 and Windows Server 2008 R2 (changes system files to support upgrade)
KB3068708–Telemetry (replaces KB3022345)
KB3072318–Update for Windows 8.1 OOBE to upgrade to Windows 10*
KB3075249–Adds telemetry points to consent.exe in Windows 8.1 and Windows 7
KB3075851–Updates Windows Update Client for Windows 7 and Windows Server 2008 R2 (changes system files to support upgrade)
KB3075853–Updates Windows Update Client for Windows 8.1 and Windows Server 2012 r2 August 2015*
KB3080149–Telemetry
KB3083324–Windows Update Client for Windows 7 and Windows Server 2008 R2 September 2015
KB3083710–Windows Update Client for Windows 7 and Windows Server 2008 R2 October 2015
KB3090045–Update applies to some reserved devices upgrading to Windows 10 from Windows 8.1 or Windows 7 Service Pack 1 (SP1).
KB3102810–Update contains improvements for Windows Update Client in Windows 7 Service Pack 1 (SP1) or Windows Server 2008 R2 SP1. [Second issue addressed is that] svchost.exe process occupies 100 percent of CPU usage when you upgrade a Windows Update client to Windows 10.
KB3102812–Update contains improvements for the Windows Update client in Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2.[Second issue addressed is that] svchost.exe process takes 100 percent of the CPU usage when you try to upgrade to Windows 10.
KB3112336–Windows Update Client for Windows 8.1 and Windows Server 2012 R2 December 2015
KB3112343–Windows Update Client for Windows 7 and Windows Server 2008 R2 December 2015
KB3123862–Updated capabilities to upgrade Windows 8.1 and Windows 7
KB3135445–Windows Update Client for Windows 7 and Windows Server 2008 R2 February 2016
KB3138612–Windows Update Client for Windows 7 and Windows Server 2008 R2 March 2016
KB3139929–Cumulative security update for IE, carries KB3146449, Woody says avoid
KB3141092?–Installed itself on LH computer 3/3/16 even though not selected, reportedly piggybacks on Security Update KB3134814 if IE11 is installed
KB3146449–Updated Internet Explorer 11 capabilities to upgrade Windows 8.1 and Windows 7 (piggybacks on KB3139929)
* Update added per Vesselin Bontchev 3/13/16 post to Ask Woody
-
The double-edged fix to “Your system administrator has blocked upgrades on this PC”
I wanted to bring this comment from Mark Berry up to the front, because he nails the problem and its solution quite precisely.
In the discussion about the new name-and-shame messages appearing on domain-joined PCs, Mark says:
The Technet link you posted links to the solution to this problem:
https://support.microsoft.com/en-us/kb/3080351
Two “blocks” are required, one blocking Windows Update from installing the upgrade, and the second blocking the little notification icon in the system tray.
If a system administrator implements the first block, but not the second, the upgrade is blocked but not the system tray icon. When the user clicks on the system tray icon, the user sees the message “Your system administrator has blocked upgrades on this PC.”
So the message means exactly what it says: the system admin is not allowing you to upgrade.
If the system admin implements the second block (which must be done by updating the registry), the notification icon will not appear in the system tray, the user will not be able to click on it, and no message appears.
Additional references:
-
March 2016 Adobe Flash Player security updates
This just in from ER:
New Adobe Flash Player security updates just released March 10 on Adobe security bulletin APSB16-08:
https://helpx.adobe.com/
security/products/flash- player/apsb16-08.html and on Microsoft security bulletin MS16-036 for Windows 8.1 & 10:
https://technet.microsoft.com/
library/security/MS16-036 These new updates install Flash Player 21.
-
How to block forced updates to Windows 10 without borking your machine – Part 1
Now up on InfoWorld, Woody on Windows.
-
Confirming the Wushowhide technique for blocking forced Win10 updates
I have a comment from ch100 that I wanted to elevate to its own post. He says:
Woody is right! I did the test in a ‘controlled’ environment using the WSUS approval mechanism and before Windows 10 had a chance to search for updates, I ran wushowhide. When launching the utility, in the background it launches svchost.exe which I am certain is the same svchost.exe process under which Windows Update runs. So this means that Windows Update is launched by wushowhide to scan for potential updates without installing them. This looks more and more like the old (Windows 7) Windows Update in which you could hide or select updates to be installed, although it is likely that it uses a different mechanism in the background.
Now I am questioning the practicality of this finding. It appears that if the Windows 10 OS is shut down, at short time after boot will run Windows Update. There is a built in Scheduled Task for this purpose. If any updates are available at that time, they get automatically installed without any chance to intercept them.
The only working scenario for our purpose is to block the updates during the likely period in which they are released which is the Patch Tuesday and sometimes another round of patches 2 weeks after, run wushowhide and wait for few days until there is enough proof that they are reliable and only after that unhide them and allow Windows Update to complete. The only way this would work is to set the Group Policy or Registry to Never Check for Updates or maybe Notify Only while hiding the updates which are not yet desired to be installed. Disabling the Windows Update service would not work as this would not allow wushowhide to run the update process.
Fascinating finding for understanding how this works, however it is a bit complicated to be put in practice as a regular routine.
I am waiting for other posters here to confirm the same findings maybe using a different method, not via WSUS but Windows Update online site and allow Woody to correlate the findings from all of us to draw the conclusions.
Yep, I’m working on an article for InfoWorld – and welcome any input. (Let me know if I can quote you and, if so, whether I can use your name.)
It looks like Wushowhide does block updates, as long as it is applied before Windows Update gets its jaws on the patch. That’s a revelation to me, but everything I’ve seen points to a resounding success.
The next step in the approach — I’m going to call it the Carboni Technique — involves blocking Windows Update. I’m very, very concerned about stopping Windows Update for a host of reasons, but blocking Windows Update (and running it manually when you need new patches) seems to be doable, and non-destructive.
I’m looking at various ways to block Win10’s Update, and am trying to settle on a way that works for everybody (Win10 Home and Pro alike), without interfering with truly important updates, including Windows Defender, MSRT, and anything else that relies on WU. Noel Carboni recommends using gpedit (which is only available in Win10 Pro) to set the Configure Automatic Updates task to Disabled. There are other ways to turn off Windows Update, and I’m considering them, too.
If you have any specific experience with blocking WU in Windows 10, I’d sure like to hear about it.
-
On forced upgrades
Just got this entertaining message from Alan Arndt:
Woody,
I applaud all your efforts with regards to Microsoft’s Force update to Windows 10 and the automatic and uncontrolled updates of Windows 10 itself. I certainly expect to upgrade my home machines and work machines to Windows 10 before the free update period ends. However, even though we are using Windows 8.1 at home and work I haven’t been terribly motivated to make the switch. A big concern is the way Microsoft intends to force updates down your throat. For that an many other reasons I have only purchased Windows 10 Pro, however, several of my machines (3 laptops, came with home editions of Windows 7 & 8 and only get the Home version of Windows 10). It would be very nice if Microsoft would offer a reasonably priced upgrade from one to the next instead of basically the full price of a new copy of Windows. To experiment with things I have updated the three laptops (two son’s and mine – as I only use it for trips, not daily use), and one home computer (with Pro).
Anyhow, my main point of this letter is to address the forced updating of Windows 10. Recently I was on a business trip, with only my laptop to use. I put my computer to sleep for a few minutes while I stepped away. I came back and my Bluetooth mouse wouldn’t work. No explanation why. It seems the Bluetooth interface had been turned off. I can’t get it to turn on from the Action center. I can’t find it under settings for devices to turn it on. I notice that there is a yellow triangle exclamation point on my computer, so I run troubleshooting. It says I need to restart to apply updates but it allows me to continue troubleshooting process. Sure enough. It comes back and says I need to restart and apply updates. Are you KIDDING ME? God damn Microsoft BUSTED my computer when I stepped away for a few minutes because they applied updates.
I very EXPLICTLY do NOT WANT to install any updates when I am gone on a trip. Who knows what will happen. So now I have no bloody choice because they have broken my computer and are forcing me to abandon what I am working on, restart everything and pray the computer still works. What a bunch of jerks.
Note that the Bluetooth issue with the mouse is especially frustrating because I have my laptop set to turn off the touchpad when I am using the mouse. When the mouse disappears without properly shutting it off the touchpad is NOT re-enabled. This is quite annoying enough when the laptop goes to sleep or is put to sleep by closing the lid, because that’s what it remembers when it wakes up. So if you packed up things and put the mouse away, you are screwed next time to wake up the laptop. Very poor thinking all around.
-
Your system administrator has blocked upgrades on this PC
I still don’t know how the Get Windows 10 icon got stuck on domain-joined computers, but it’s there.
Admins I know are, rightfully, livid. Microsoft’s doing an end run.
InfoWorld Woody on Windows
UPDATE: Looks like there was a kinda-sorta advance warning, back on January 13.
http://blogs.technet.com/b/windowsitpro/archive/2016/01/13/making-it-easier-for-small-businesses-to-upgrade-to-windows-10.aspxThe TechNet article says it’s only aimed at machines “Configured to receive updates directly from the Windows Update service (i.e. updates are not managed by WSUS or System Center Configuration Manager on those devices)” which conflicts with several reports.There’s also no mention in the TechNet article about the name-and-shame message, “Your system administrator has blocked upgrades on this PC,” which is threatening to some, insulting to others. -
IE patch KB 3139929: When a security update is not a security update
This is a new low, even for Microsoft’s much-maligned “Get Windows 10” campaign.
InfoWorld Woody on Windows
Can any of you get the blue banner to trigger on “new” tabs in Internet Explorer? I’ve been trying and trying, and can’t get it to work. Shoot me email, please: woody@askwoody.com.
UPDATE: Annemarie, who’s quoted in the article, has dropped me a note to give the correct attribution. The original discovery (in Dutch) came from Bobo. Thanks, Bobo!