Newsletter Archives
-
Running SharePoint Server? Better get this security hole plugged soon.
Very few of you are running SharePoint Servers, but for those of you who do, this is an important heads-up. From AttackerKB:
On Tuesday, October 13, as part of the October 2020 Patch Tuesday release, Microsoft published a security advisory for CVE-2020-16952, a server-side include (SSI) vulnerability in Microsoft SharePoint. The bug is exploitable by an authenticated user with page creation privileges, which is a standard permission in SharePoint, and allows the leaking of an arbitrary file, notably the application’s
web.configfile, which can be used to trigger remote code execution (RCE) via .NET deserialization. CVE-2020-16952 carries a CVSSv3 base score of 8.6…An easily available proof-of-concept makes CVE-2020-16952 an impending threat. There are no reports of exploitation in the wild as of October 13, 2020.
Affected products
-
-
Microsoft SharePoint Foundation 2013 Service Pack 1
-
Microsoft SharePoint Enterprise Server 2016
-
Microsoft SharePoint Server 2019
-
Full details on the Rapid7 site.
Thx, Patch Lady.
-
-
How to block Win10 version 20H2
Microsoft’s ready to push that puppy out the update chute. You don’t want it until it’s been thoroughly tested, and tested again.
Susan Bradley and I have teamed up to take you step-by-step through the process for blocking Win10 version 20H2 until you’re good ‘n ready to install it.
Details in this Computerworld How-To.
-
MS-DEFCON 2: Incoming! Pause Windows and Office patches
October Patch Tuesday is just around the corner.
Now’s a good time to make sure you have “Pause” set on your Win10 machines (or that you turn off Automatic Update on your Win7 and 8.1 machines).
Full step-by-step details in Computerworld Woody on Windows.
-
Patch Lady – End of support coming for many Windows versions
From Patch Lady:
Just a kind reminder…. there are some end of life(s) coming up for several versions:
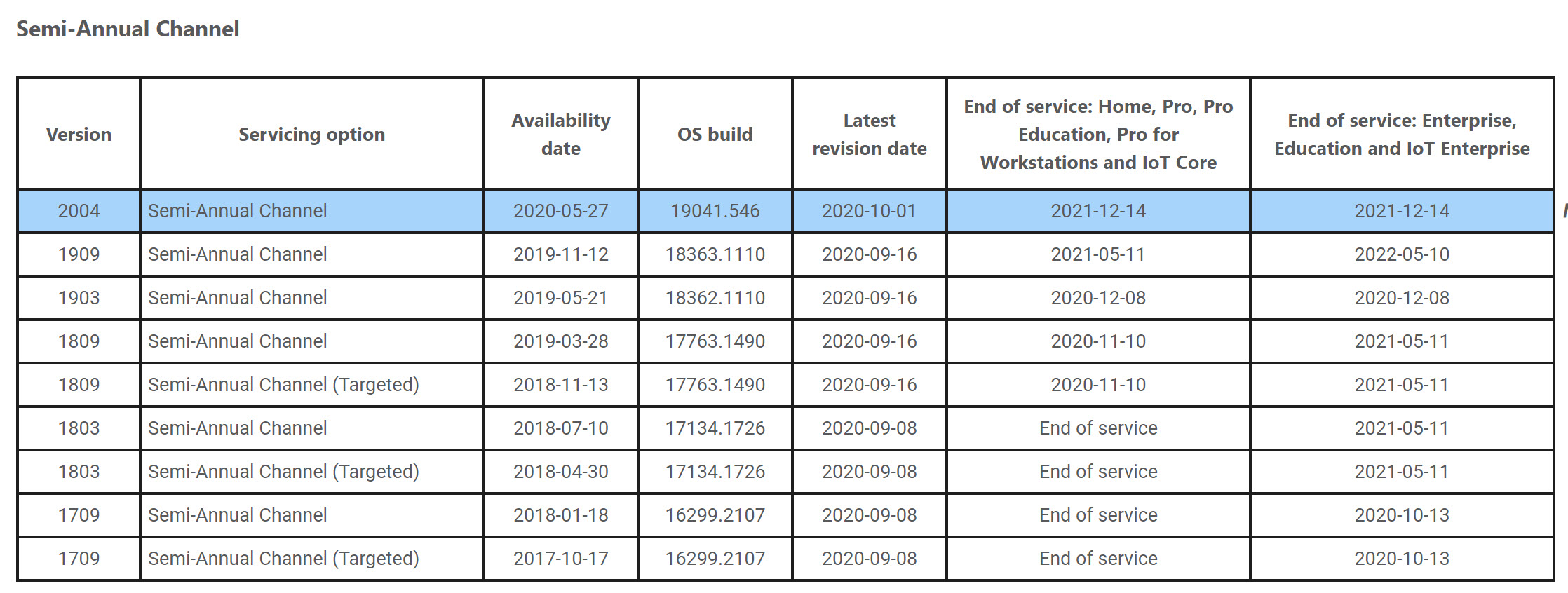 If you are running enterprise, education or IoT Enterprise, 1709 drops off support after this Tuesday.
If you are running enterprise, education or IoT Enterprise, 1709 drops off support after this Tuesday.If you are running Home, Pro, Pro education you need to be moving off 1809 after 11-10-2020 and if you are 1903 you need to be right behind them and will be dropping out of support on December 8, 2020
Enterprise, Education and IoT Enterprise also drops out of support 12-8-2020.
-
Welcome to Google Workspace
I’ve almost completely switched over to Google G-Suite.
Except, as of today, it’s known as Google Workspace.
Google just announced the name change, gussied it up with a bunch of marketing gobbledygook, and a “new user experience.”
Except, well, it mostly looks like the old user experience. Which I like just fine, thankyouverymuch. If you want to “dynamically create and collaborate on a document with guests in a Chat room,” I wish you well. But if you just want to knock out a doc or sheet, or even a slide deck, Google’s just fine, the same as it’s always been.
Remember, Google doesn’t snoop on your G-Suite stuff:
The data that G Suite organizations and users put into our systems is theirs, and we do not scan it for advertisements nor sell it to third parties.
They scan emails and files for viruses and the like, but “Google does not collect, scan or use data in G Suite Core Services for advertising purposes.” It’s all in black and white, although the official policy pages haven’t been updated with the new “Google Workspace” name.
-
Ed Bott’s poll results: Here’s why people are sticking with Windows 7
Ed got more than 3,200 replies to his survey. Here’s a summary of what people are saying about moving away from Win7:
DO YOU PLAN TO UPGRADE TO WINDOWS 10 IN THE NEXT 12 MONTHS?
The answer to this question was pretty emphatic. Just under 58% replied No, with another 27% answering Not Sure. Only 16% said Yes.Lots of interesting info in that ZDNet article.
Patch Lady Susan Bradley posted a question last week, referencing Ed’s survey. We got dozens of interesting, and well-considered, replies.
-
If you have an avatar (a picture) here on AskWoody, make sure Gravatar doesn’t have any personal data
Ax Sharma at BleepingComputer published an article that shows how a sufficiently motivated cracker can scan all of the entries at Gravatar.com and pick up personal information there.
If you have an avatar here on AskWoody (or on any other WordPress-based site), you have an entry in the Gravatar database. That’s where WordPress (and other sites) pick up your picture. Your picture is indexed by email address – your username on AskWoody doesn’t make any difference. The picture gets picked up by matching the email address you have associated with your AskWoody account, with an email address in the Gravatar database.
Gravatar is owned by WordPress.
Since this new scraping technique can pull data from Gravatar, you might want to double-check and make sure you don’t have any sensitive info stored over there. It’s easy.
Step 1. Go to Gravatar.com
Step 2. In the upper right, click Sign In. Enter your email address and your Gravatar password (not your AskWoody password). Click Continue and Sign In.
Step 3. Click My Profile. You see the settings in the screenshot.
Step 4. Work through the entries on the right side and make sure there’s absolutely nothing there that you want to have snooped.
Step 5. If you changed anything, click Save Profile.
To be clear, this hack has nothing to do with WordPress itself, nor with AskWoody. But if you’ve set up an avatar for use on AskWoody or any other WordPress site, you should make the effort now to ensure that there’s nothing in the Gravatar database that you don’t want scarfed up for posterity.
A reminder that AskWoody maintains the absolute minimum amount of information necessary to keep the site going — your username, the email address you used to create the account, your Plus membership status, and any additional info you may have stored, including your signature if you created one. Your password is stored in a one-way salted hash, which means that anyone reading the AskWoody database wouldn’t be able to figure out your password.
Of course, we don’t store any payment information on AskWoody.com, or anything else worthy of tracking.
-
Warning: If you pay ransomware, the US Dept of Treasury may fine you
Dan Goodin at Ars Technica has a great review of the latest US Treasury Department advisory:
Businesses, governments, and organizations that are hit by crippling ransomware attacks now have a new worry to contend with—big fines from the US Department of Treasury in the event that they pay to recover their data… payments made to specific entities or to any entity in certain countries—specifically, those with a designated “sanctions nexus”—could subject the payer to financial penalties levied by the Office of Foreign Assets Control, or OFAC.
The prohibition applies not only to the group that is infected but also to any companies or contractors the hacked group’s security or insurance engages with, including those who provide insurance, digital forensics, and incident response, as well as all financial services that help facilitate or process ransom payments
It’s an important new angle on an increasingly difficult subject.
UPDATE: Brian Krebs has a more-detailed look on Krebs on Security.
-
MS-DEFCON 4: Get the September 2020 patches installed
If you’re running SQL Server 2019, surprise!, Microsoft yanked the old cumulative update and replaced it with a working one last night.
In general, it looks like a pretty healthy bunch of patches, with the usual (undocumented) problems: the “temporary profile” bug; stealthy installation of KB 4023057; odd miscellaneous blue screens and interface bleeps.
I still won’t install version 2004 on my production machines, even though about one-third of all Win10 users have swallowed that pill. There’s nothing in version 2004 that warrants even the slightest bit of sweat off your brow.
So I’m moving us to MS-DEFCON 4: There are isolated problems with current patches, but they are well-known and documented here. Check this site to see if you’re affected and if things look OK, go ahead and patch.
Full story in Computerworld Woody on Windows.
-
Microsoft drops KB 4577063, the “optional, non-security, E Week” patch for Win10 version 2004
At least they made it before F Week.
Microsoft just pushed 48 separately identified bug fixes in KB 4577063, the E Week optional, non-security patch for Win10 version 2004.
Looks like the Linux-under-Windows bug has been fixed, as has an uncommon bug that makes Windows appear as if your internet connection dropped. Details at BleepingComputer.
No, you don’t want it. Wait for Patch Tuesday.
There’s also a .NET preview for version 2004, KB 4576945.
Looks like they fixed the Linux bug. I don’t see anything else that’s particularly interesting. Do you?
-
If your organization uses HP Device Manager to control thin clients, you need to plug this hole now
News early this morning from Thomas Claburn at The Register
HP Device Manager, software that allows IT administrators to manage HP Thin Client devices, comes with a backdoor database user account… the account can be exploited to achieve privilege escalation and, in conjunction with other flaws, gain unauthorized remote command execution as SYSTEM.
This is bad: if you can reach a vulnerable installation of this device manager on a network, you can gain admin-level control over its machine and the thin clients it controls. HPDM typically runs on a Windows-powered server, and directs multiple Windows clients.
HP just updated its security bulletin HPSBHF03689.
There’s an updated HP Device Manager coming. In the interim, make sure you follow the HP remediation steps — and close up the hole manually following @nickstadb ‘s steps in The Reg.
-
Office (er, Microsoft) 365 authentication heads for the hills
If you’re trying to log in to Microsoft 365, and can’t get past the authentication step, you aren’t alone.
Per Brad Sams:
Microsoft is aware of the issue but at this time there is not an ETA for a fix. Amusingly, the support account for Microsoft 365 on Twitter recommends that you check your account dashboard for MO222965 but when you try to authenticate, it fails… If you are already logged into an app or dashboard, you should be safe to utilize that feature but do not log out.
I expect it’ll be fixed in short order.
Here’s the official notification:
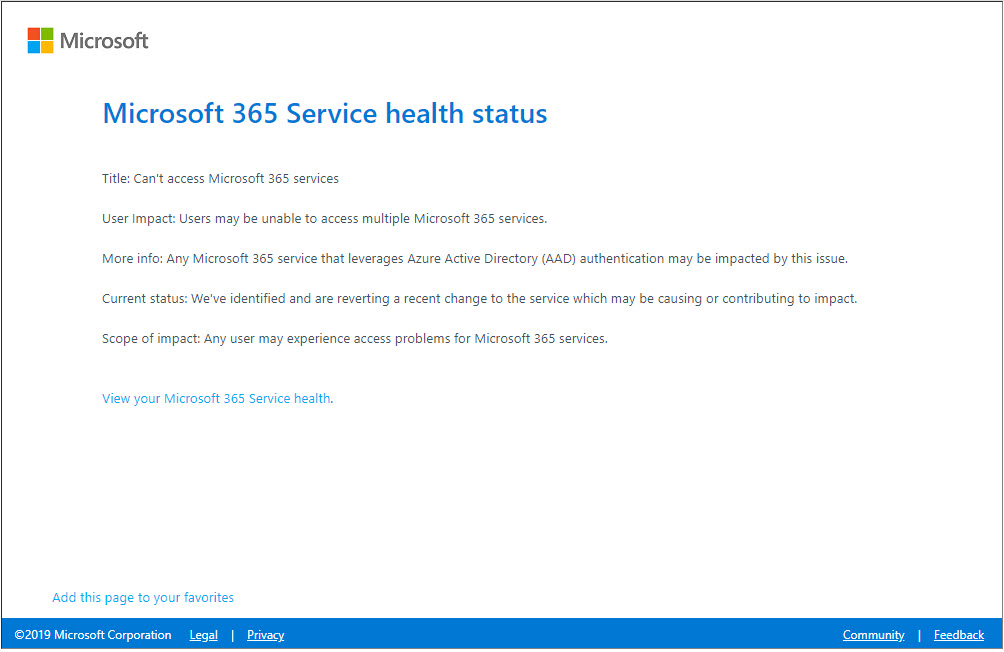
Man, if Microsoft itself can’t install patches to its key service without blowing things up….


