Newsletter Archives
-
Microsoft issues KB4493132 Windows 7 SP1 support notification
For those of you wondering how you will get the nag for Windows 7 EOL, Microsoft has released KB4493132 on March 19, 2019.
@Cybertooth asks
Windows Update is offering my Windows 7 box a patch released yesterday, KB4493132:
Does anybody know anything about this update? A search here at Woody’s showed no results. Even a Web search via DuckDuckGo turned up nothing.KB4493132 is available through Windows Update if you want notifications during the next year that Windows 7 will reach end of support on January 14, 2020.
After 10 years of servicing, January 14, 2020, is the last day Microsoft will offer security updates for computers running Windows 7 SP1. This update enables reminders about Windows 7 end of support. More information about Windows 7 end of support can be found here.
This update is available through Windows Update. If automatic updates are enabled, this update will be downloaded and installed automatically. For more information about how to turn on automatic updating, see Windows Update: FAQ.
Hiding this patch is suggested for those of you who don’t want multiple reminders during the next year.
Details (which are few) in Computerworld. Seven Semper Fi!
-
Patch Lady – downloading the 1809 iso
So given that the tea leaves look like that 1903 is coming soon, I’m making sure that I’m downloading 1809 from the media download site and parking it on a location so that when I’m ready to install 1809, I have it ready to go.
Today the previews of next month updates came out for everything but 1809.
https://www.microsoft.com/en-us/software-download/windows10
So if you decide WHEN you want the feature releases, make sure you’ve deferred to the semi annual channel and have 1809 downloaded and parked for the future.
-
KB 4487017 Feb Cumulative update for Win10 v1803 causing BSODs
@weedacres reports that the Feb 2019 Cumulative Update KB KB4487017 for Win10 v1803 is causing BSODs.
One of my customers called yesterday reporting BSOD’s on their two HP AIO’s. This KB is the 2019-02 Cumulative update for 1803. This apparently started on or about 3/8 when the update was installed.
I found that they’re getting 001a BSOD’s and after some research saw that many others are having the same problem. I saw several failures while working on both PC’s and finally uninstalled the update last evening. I hid it with wushowhide and so far all seems well.
My question is how long with wushowhide keep it hidden? Am I going to have to hand tend this thing until the March updates install?
Is anyone else seeing this problem?
This is a correction to an earlier report. It was not KB 4023057 causing the problems.
-
Patch Lady – Domain admins and issues with KB4489878
Sandeep pointed out that after he installed KB4489878 on a Server 2008 R2 he can no longer use the netdom query commands. I can attest that commands on a Server 2012 R2 machine work fine, but on a Server 2008 R2 it comes back with an error.

That’s what it looks like on a Server 2008 R2 after the March updates when I went to check.

This is what it looks like on a Server 2012 R2 after the March updates on a patched server.
Anyone else seeing this?
netdom /query is a command used by Admins to determine what server is the domain controller, what holds what is called the FSMO roles.
In on premises deployments it’s a command not used that often, but it’s like the c prompt or command line. It normally just works and you take it for granted.
It’s not a deal breaker bug, but needs to be addressed nonetheless.
I’ll keep you posted on the status.Now documented in the KB as a known issue. Microsoft is working on the fix.
-
Microsoft acknowledges yet another bug in this month’s Win10 1809 cumulative update, this one with Windows Deployment Services server and PXE
An anonymous poster raised the red flag a few hours ago.
After installing this update, there may be issues using the Preboot Execution Environment (PXE) to start a device from a Windows Deployment Services (WDS) server configured to use Variable Window Extension. This may cause the connection to the WDS server to terminate prematurely while downloading the image. This issue does not affect clients or devices that are not using Variable Window Extension.
There are three manual solutions offered.
Microsoft is working on a resolution and will provide an update in an upcoming release.
You really gotta wonder who’s testing this stuff – and, in this case, why it took almost a week to acknowledge the problem, which appears to happen on every Windows Deployment Service server with VWE.
-
Windows Defender Security definition problems
We’re hearing reports of problems with Definitions Update 1.289.1521.0, preventing scanning in Windows 7 and 8.0 virtual machines. Other OS versions are still being tested by @alqamar.
Has your machine been affected by this definition update?
UPDATE: Win 8.1 also affected, but newer OS are ok.
@alqamar has posted his results
(This is a real-world problem, not just limited to virtual machines, where early reports were first tested)RESOLVED: Microsoft has now issued an update that fixes the issue. In her article on the problem (which was noted as first being seen here), Mary Jo Foley wrote on zdnet.com that update 1.289.1588.0 was issued on March 19th. @alqamar posted his tests were fixed by update 1.289.1587.0.
-
Just don’t use WinRAR, OK?
I’ve been trying to avoid this topic, but it now appears to be engulfing the blogosphere.
If you use WinRAR, you were suckered. I’ve never recommended it. But if for some reason you’ve installed it — or even paid for it — uninstall it and get something worthwhile (and free!) like 7-Zip or one of a dozen alternatives.
@mn- posted about WinRAR’s security problems back in February, when they were discovered and disclosed. Martin Brinkmann had thorough coverage on ghacks. It all has to do with an ancient archiving format called ACE, and the “19-year-old” security hole is being exploited right now. McAfee says they’ve found “over 100 unique exploits and counting,” but I think they’re double-dipping. Catalin Cimpanu on ZDNet has a recent accounting.
Tempest, meet teapot. But if you have WinRAR for some bizarre reason, get rid of it.
-
When will MS start pushing the update to Win10 1809 on machines set for the SAC “branch”?
It’s a simple question.
I have my Win1803 machine set up with my recommended Windows Update advanced options:
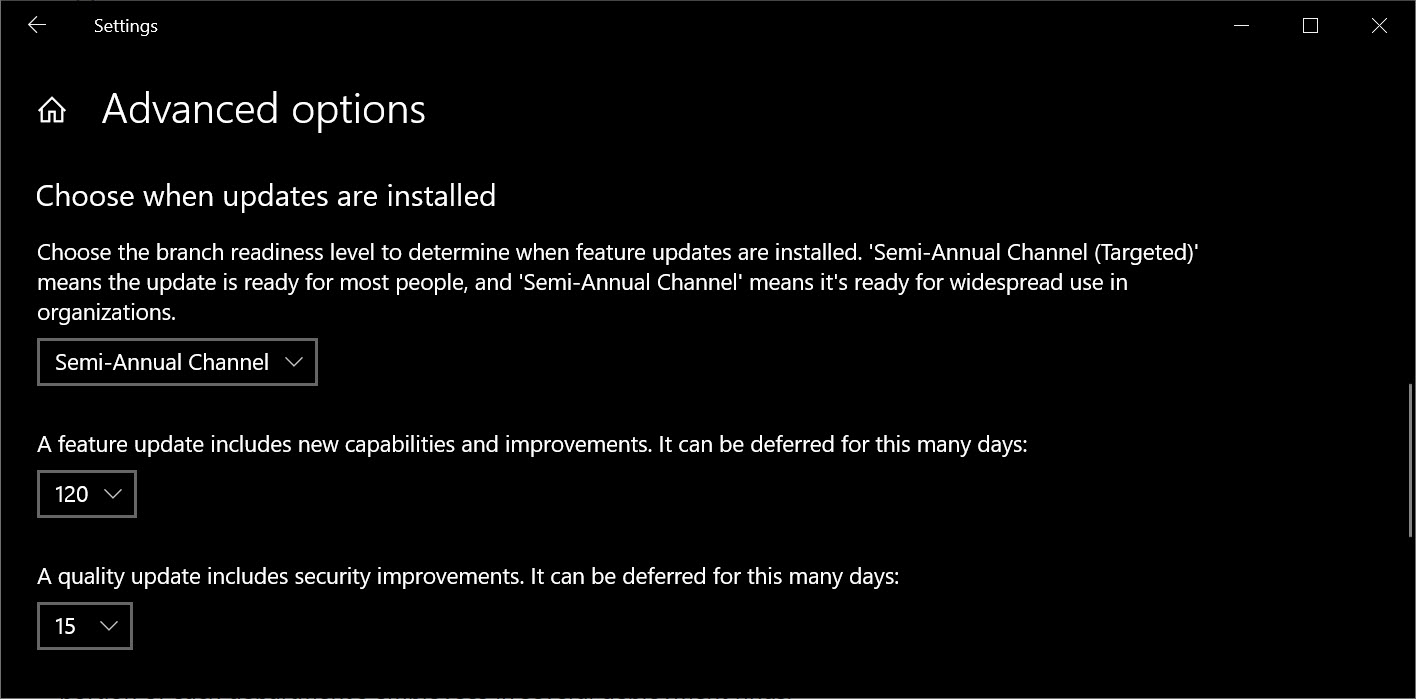
Microsoft says it’s getting rid of “Semi-Annual Channel.”
So when does Windows start pushing 1809 onto my 1803 machine? I’ve been wondering about that for some time now — figured that MS would have to declare Win10 1809 “Semi-Annual Channel” at some point, if only to honor the settings in earlier versions of Win10.
@PKCano had a fascinating observation:
If they declare 1809 “ready for business” at the same time they release 1903:
+ The deferral period for 1809 begins, (for a maximum of 365 days) from that point.
+ If they release 1903, with the changes they have made to SAC doing away with SACT, the deferral period for 1903 begins, (for a maximum of 365 days) from that point.Now they have two versions of Win10 reaching the end of the deferral time simultaneously.
Which I find to be a brilliant way to unwind the Gordian knot. Microsoft, basically, says “let ’em eat cake” and walks away.
@b offered an interesting twist:
Plus 60 days:
For devices that have been configured with a branch readiness of SAC, for the upgrade to version 1903 only, we will add an additional 60 days to the configured deferral. This will simulate the delay previously experienced when Microsoft declared the SAC milestone. For example, if your device is currently configured to defer updates 30 days from the SAC release date, for the upgrade to version 1903 (and this time only), we would append a 60-day delay to that configured 30-day deferral–meaning that the device would be upgraded 90 days (60+30) after version 1903 is released. (Note that the additional 60 days will be handled on our service side, and will not be reflected in your device configuration.)
Windows Update for Business and the retirement of SAC-TMicrosoft has already said that it’ll jump over its now-declared-redundant “SAC” setting in 1809 by adding 60 days to the 1809 Windows Update “feature update” advanced setting. Perhaps, as @b says, they’ll do the same to 1803. [Permit me to clarify: I’m saying that Win10 1809 will be upgraded to 1903 according to the 60-days-plus-deferral-days rule. We know that. But I’m betting that Microsoft will use identically obfuscated logic to upgrade 1803 users straight to 1903 using the same rule.]
What a thoroughly screwed up resolution to an incredibly convoluted series of patching re-re-re-definitions.
-
Did Microsoft just re-release KB 4480730, the “Reliability improvement to Windows 10 update components”?
I don’t see any official announcement of a re-release, but as @mn- notes, two of the files in the KB now have March 12 datestamps on them.
File name File version File size Date Time Cuassistant.dll 10.0.17134.10019 436,536 12-Mar-2019 01:23 Culauncher.exe 10.0.17134.10019 258,568 12-Mar-2019 01:22 The KB article itself is now dated March 14.
Any idea what’s going on? Is this another pre-1903-release step?
-
Proof of concept code published for one of this month’s Win7 zero-days
Catalin Cimpanu reports on ZDNet that the Chinese giant Qihoo 360 Core has published proof of concept code for the Win7 zero day identified as CVE-2019-0808. That’s the zero-day that prompted Google to patch Chrome last week, with a dire warning that you needed to get Chrome caught up on patches.
That isn’t good news for Win7 users.
I’ll be watching closely to see if the new proof of concept code makes its way into a credible threat for you Win7 customers.
Stay tuned.
-
Will Win10 1809 ever be declared “suitable for business”?
It’s been a raging question for months. Win10 version 1809, released in October, has not been declared “Semi-Annual Channel” (the previous “Current Branch for Business”) worthy as yet, although it’s been out for … count ’em … five months.
A month ago, Microsoft dismantled its whole update framework and threw away the names that we’ve known for so long — names, such as “Semi-Annual Channel (Targeted),” that are baked into the fabric of Windows Update in versions 1803 and 1809.
@1EarEngineer just pointed me to a post from ‘Softie John Wilcox which, in response to a question about the updating mess, says:
1809 has been released, there is no second, separate broad release. For self managed customers, they control and decided when they have reached their deploy decision, and our guidance is they should have started the deployment process now with 1809, following our recommend framework. This would be in the target phase, which we are in as well for WU.
For devices we manage, that are connected to WU, we are in targeted phase, which means we are only publishing the update to targeted devices, not all devices. This is our normal process, and as we get more data and confidence, we add more devise to the target list, until we reach our decision that its good for all, at which time we publish to everyone. That is when it becomes “broad”. That just signals that it is now broadly available ( same release ).
Its not a time driven thing, but a data driven thing. 1803, it took 2 months, the historical norm was 3-4 months. 1809 will not be 2 months , but more to the norm.
1809 is already on VLSC, we are now posting at the same time we start on WU, and will continue that going forward
Which, to my mind anyway, reaches a new low in obfuscation. First of all, Win10 version 1809 is five months old. Second, if MS doesn’t declare it “Semi-Annual Channel” one of these days, all of those Windows Update advanced settings in Win10 version 1803 and 1809 are just so much mealy-mouth mush.
Am I missing something here?
-
New bug reported with all of this month’s Windows patches
In the past hour or so, Microsoft has acknowledged a new bug in the latest cumulative update of every version of Windows 10, and in the Monthly Rollups for Win7 and 8.1. (Security-only patches for Win7 and 8.1 appear to be unaffected.
Symptom:
After installing this security update, Custom URI Schemes for Application Protocol handlers may not start the corresponding application for local intranet and trusted sites on Internet Explorer.
Workaround:
Right-click the URL link to open it in a new window or tab.
Microsoft is working on a resolution and will provide an update in an upcoming release.
I don’t have any details as yet, but it sounds like avoiding IE is your best bet.
Thx, Patch Lady!


