I’ll have a more detailed and up-to-date post on InfoWorld on Monday, but for now, here’s what you need to know if you’re concerned about the WannaCry
[See the full post at: How to make sure you won’t get hit by WannaCry/WannaCrypt]

|
Patch reliability is unclear, but widespread attacks make patching prudent. Go ahead and patch, but watch out for potential problems. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
How to make sure you won’t get hit by WannaCry/WannaCrypt
Home » Forums » Newsletter and Homepage topics » How to make sure you won’t get hit by WannaCry/WannaCrypt
- This topic has 191 replies, 30 voices, and was last updated 7 years, 10 months ago.
Tags: ports scanning WannaCry WannaCrypt
AuthorTopicViewing 55 reply threadsAuthorReplies-
GoneToPlaid
AskWoody LoungerMay 13, 2017 at 3:45 pm #114921Hi Woody,
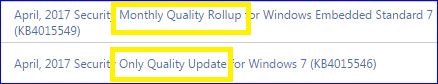
Under Windows 7, you mention “If you have any of those patches, you’re fine.” Not true if you are in Group B since April and May Security Only updates are not cumulative. For Group B, the March Security Only update must be installed. I don’t have any Windows 8x computers, yet I assume that similar would apply to Windows 8x Group B users.
Best regards,
–GTP
-
woody
ManagerMay 13, 2017 at 3:57 pm #114925Take a look at the list again.
For Win7, if you have the March, April or May Monthly Rollups you’re fine. If you have the April Preview you’re fine.
If you have the March Security-Only patch, you’re fine.
Otherwise, you’re begging for trouble.
The other Security-Only patches don’t enter into the equation.
-
GoneToPlaid
AskWoody LoungerMay 13, 2017 at 4:03 pm #114928Yes, I now see this. Yet I had initially misread it. Others might misread the list as well. Perhaps you should explicitly mention that for Group B user who avoid all updates which install telemetry, those users must have the March Security Only update installed.
1 user thanked author for this post.
-
-
GoneToPlaid
AskWoody LoungerMay 13, 2017 at 3:58 pm #114926Spain’s CERT has published a tool to prevent (at least for now) WannaCry/WannaCrypt infections. Their tool is not persistent and must be launched after every reboot. Please see this page:
Needless to say, and due to the NSA’s inept ability to prevent disclosures of their hacking tools, we most likely will see a storm of ransomware and malware which will infect unpatched Windows computers. I bet that both state actors and cyber-criminals are paying their people overtime and bonuses to develop malware and worms which use the NSA exploits which were revealed by ShadowBrokers.
-
woody
Manager -
anonymous
GuestMay 13, 2017 at 9:18 pm #114997@ woody
You are only half correct. Please refer to …
The “accidental hero” who halted the global spread of an unprecedented ransomware attack by registering a garbled domain name hidden in the malware has warned the attack could be rebooted.
-
GoneToPlaid
AskWoody LoungerMay 13, 2017 at 4:07 pm #114929But that tool only blocks WannaCrypt – which has already been blocked, for everybody, forever, thanks to Malwaretech.com. WannaCrypt is no longer the problem. The problem is with MS17-010. People have to get that baby installed. Now.
Not forever. The code can be very quickly modified to not look for this obscure domain name which has been sinkholed. Several people pointed out how quick and easily this could be done. This is why I think that Spain’s CERT tool remains relevant for the time being.
1 user thanked author for this post.
Pixie
AskWoody LoungerMay 13, 2017 at 5:00 pm #114937Woody,
I’m a bit confused. I’m in Group A, have Win 7×64. I installed March Security rollup which was replaced by cumulative April rollup KB4015549 which I have installed on my computer. Your list under Win 7 also notes May 2017 rollup (Group A) 4019264. Are we supposed to install that security monthly rollup now? Or does having IB4015549 protect for the time being?
woody
Manager-
GoneToPlaid
AskWoody LoungerMay 14, 2017 at 12:40 pm #115214100% correct. Woody has done an excellent job of updating his original post in order to make everything as clear as possible, to mention the specific Group B March patch which must be installed, and by adding information for the patches which are available for both Vista and XP. Everything is now quite clear if one takes the time to carefully read Woody’s revised post.
-
anonymous
GuestMay 14, 2017 at 7:38 pm #115291Hello and thank you for the advice about patches. After a normal format over the weekend (Windows 8.1 home/Haswell), no matter what I try, I cannot install any windows updates. Already been preparing to go to Linux, but now that’s very urgent. Wondering if others are having the same problem. Microsoft’s even worse hard sell of Win10?
-
BobbyB
AskWoody LoungerMay 14, 2017 at 9:21 pm #115304@anonymous the web site below should speed you on the way for installing Win8.1 updates, although I really think the M$ update catalogue is going to be busy/slow and for a while yet this weekend/week.
http://wu.krelay.de/en/
catalogue
https://catalog.update.microsoft.com/v7/site/Thanks.aspx?id=140I am sort of wondering here whether this is going to strengthen the case for Win10 as up to now the latest version doesent seem affected or the fully patched other versions of Win10. Bad weekend all round and sure to be much worse to come next week. So if you do update better make sure the MS070-010 is taken care of along the way. 🙁
-
anonymous
GuestMay 15, 2017 at 6:39 pm #115503Thanks for the link, BobbyB. Much appreciate. Unfortunately, have tried WSUS/offline updates/everything in safe mode, the lot, and nothing will install. Even on a totally fresh system, nothing else installed, the same issues. This has got worse and worse over the last 3-4 months. Haswell, but maybe been locked out alongside other chips. Thank goodness Linux exists. 🙂
-
anonymous
GuestMay 16, 2017 at 6:52 am #115632I can’t get the update on Windows 8.1, including using IE. Given up. Disable SMB1 (if after repeated attempts to update, you can’t), make good backups straightaway if you haven’t recently, use an external drive and get the important files, defrag, use something like Ccleaner to wipe empty space, (slow), and have nothing important on a Windows computer.
Reached the stage where its getting ridiculous, for whatever reason. Have a live USB ready and make the switch.
-
anonymous
GuestMay 17, 2017 at 1:34 am #115839Couldn’t agree more, and, even when it does eventually come up, it then breaks the machine. Oddly, it did come up, after messing with everything under the sun for 3-4 days. But it installed 6+ telemetry updates, which I had to sort through 196 to find and remove, and it’s broken my tablet driver and net, the latter so badly that nothing but yet another format would fix it.
You’re right about SMB1. Fully backed up onto externals, ccleaner is great, and the Mint USB is so ready. Looking into dual boot again briefly (proved difficult when tried before), but tbh have already bought a console to cover the games side, sorted art programs to use on Linux, only need to find out how to stream/itunes-similar, and so it’s good riddance to Windows asap. What a heap of junk. Nothing is worth this much stress, wasted time and intrusion.
-
-
-
Lori
AskWoody PlusMay 16, 2017 at 3:10 am #115618@anonymous,
I’m a home-user, Windows 8.1, 64-bit, Haswell. I’ve had trouble getting windows update to find/install updates over last 2+ months, even before “processor” problems. Windows update never broke, as it did for the “affected” processors; but it can run 24-36 hours without finding updates. I have to stop WU, come back 1-2 days later and try; or run the windows update trouble shooter. Eventually, I get the monthly security only and IE (from this site), and .NET updates (thru WU) in. I thought I was the only W 8.1 person having WU difficulties. My W 7 pc installs everything just fine and quickly.[Intel core i5 4200U, Haswell ULT 22nm] [non-tech, Group b]
-
anonymous
GuestMay 16, 2017 at 5:10 am #115623Hi Lori, very sorry to hear that, and glad you can eventually get some updates. Yes, it seems there are definite issues with problems being caused for Win8.1. I’m at the point of it just not being worth the hassle any more; all kinds of things also seem to get problems that weren’t there before [hardware’s fine], extra to the already stressful lack of security. Looking into how to do things on Linux Mint, and making some progress. Mint’s the most straightforward to use that I’ve found, and there’s a helpful forum there too. Best wishes, Cat
-
Lori
AskWoody PlusMay 16, 2017 at 11:09 am #115725Good luck with Linux. This forum is a tremendous help. Did you see Woody’s “Group B update problem” forum?
-
anonymous
GuestMay 17, 2017 at 1:35 am #115840Thank you very much for the link; will definitely read that, as am going to attempt dual boot briefly again before taking the inevitable full plunge. WinUpdate had suddenly come through, but broke tablet driver, and also broke the net too badly to fix except through re-formatting again. End of tether vanished miles back, lol, and had already been preparing to leave Windows behind; going entirely to Linux has just come round a lot sooner than I expected. Thanks for good wishes. Hope your updates come through okay, and great to meet you and others on this impressive forum.
1 user thanked author for this post.
-
Pixie
AskWoody LoungerChris M
AskWoody Lounger-
woody
Manager -
Chris M
AskWoody LoungerMay 13, 2017 at 7:22 pm #114973I see the changes you’ve made.
If you’re looking at it still and going hm, perhaps this:
“If you have any of those patches already downloaded, then you’re good to go and you can sleep well at night.”
But hey, that’s just my thought. Thanks for all your help, Woody.
1 user thanked author for this post.
-
anonymous
GuestMay 13, 2017 at 5:33 pm #114950-
woody
Manager
Alice
AskWoody LoungerMay 13, 2017 at 6:40 pm #114970-
woody
Manager -
Alice
AskWoody LoungerMay 14, 2017 at 2:25 am #115074Woody-
A further suggestion. Perhaps you might want to change
Follow the links at the bottom of the Technet page to download and run the installer.
to
Follow the links under “Further Resources” at the bottom of the Technet page to download and run the installer.
BobbyB
AskWoody LoungerMay 13, 2017 at 7:27 pm #114976For Vista & XP M$ patches issued today use the following link at the catalogue
https://catalog.update.microsoft.com/v7/site/Search.aspx?q=4012598
for more info and again links at the bottom of the page
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
Reading about this its probable that the Virus will mutate/get messed with early next week so probably be ever vigililant and dont open “Anonymous zip files” (Sorry Anonymous who ever you may be) 😉
-
woody
ManagerMay 13, 2017 at 9:40 pm #115006 -
NetDef
AskWoody_MVPMay 14, 2017 at 1:37 am #115065It’s my understanding that the normal propagation is as a worm – it looks for exposed SMB servers and passes the bad code that way. I don’t think there’s a zip involved, except possibly as an initial infection vector.
It’s entering as an email attachment (social hacking), the runtime does not need admin rights on the workstation, and from there it scans for vulnerable SMB holes on workstations and servers that are not patched. We just finished doing a deep analysis across our clients. All of them were patched EXCEPT for several Windows Server 2003 Standard and Storage Edition servers . . . which got patched with the emergency patches that Microsoft released this weekend for them.
Direct download links for XP, Server 2003 and others are available at the bottom of this TechNet blog post from Microsoft:
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
I am happy to say none of our clients got infected, but we were definitely on high scramble mode for the last 48 hours! Now for some sleep . . .
~ Group "Weekend" ~
-
Kirsty
Manager -
NetDef
AskWoody_MVP -
Kirsty
ManagerMay 14, 2017 at 2:43 am #115078 -
GoneToPlaid
AskWoody Lounger -
NetDef
AskWoody_MVPMay 14, 2017 at 2:40 pm #115252Wave two confirmed:
http://thehackernews.com/2017/05/wannacry-ransomware-cyber-attack.html
“main-article-info” Updated: Multiple security researchers have claimed that there are more samples of WannaCry out there, with different ‘kill-switch’ domains and without any kill-switch function, continuing to infect unpatched computers worldwide
Edit to remove HTML
~ Group "Weekend" ~
1 user thanked author for this post.
-
-
-
woody
Manager -
NetDef
AskWoody_MVPMay 14, 2017 at 2:37 pm #115250I don’t believe even MS has confirmed the exact initial attack vector, we are only presuming that it’s email, but we’ve seen infections that started from machines where the end user did NOT have local admin permissions.
From Microsoft at their war page: https://blogs.technet.microsoft.com/mmpc/2017/05/12/wannacrypt-ransomware-worm-targets-out-of-date-systems/
We haven’t found evidence of the exact initial entry vector used by this threat, but there are two scenarios we believe are highly possible for this ransomware family:
- Arrival through social engineering emails designed to trick users to run the malware and activate the worm-spreading functionality with the SMB exploit
- Infection through SMB exploit when an unpatched computer can be addressed in other infected machines
I’m going to theorize that if SMB is exposed on the firewall, that could also be a vector. (I would sure hope that no admins do this!)
~ Group "Weekend" ~
-
Kirsty
ManagerMay 14, 2017 at 6:55 pm #115287From @threatintel:
Two new #wannacry variants found: One had modified killswitch. Second has killswitch disabled, but ransomware payload doesn’t execute.
-
-
John in Mtl
AskWoody LoungerMay 13, 2017 at 8:18 pm #114985Hi Woody,
I beleive there is a simple cut’n-paste error with the link mentioned in this line pertaining to windows 8.1:
If you have none of those patches, download and install the March, 2017 Security Only Quality Update for Windows 8.1 (KB4012213) for 32-bit or 64-bit.
The link goes to the windows 7 page instead of 8.1.
-
pigtail
AskWoody LoungerMay 13, 2017 at 8:40 pm #114988Yes, John in Mtl is right. I was also directed to Win7 KB # as well for the remedy of Win8.1.
-
woody
ManagerMay 13, 2017 at 9:47 pm #115010You and pigtail are both right. I’ve modified the download links (per PKCano’s suggestion) to get you directly to the download.
The Catalog has been very, very slow since this all started. The sound of billions of voices all crying out in pain, I think…
4 users thanked author for this post.
anonymous
Guest-
woody
ManagerMay 13, 2017 at 9:50 pm #115012Yes, that’s correct.
Microsoft was kind enough to release these specific patches for XP and Win8, even though they were under no obligation to do so. They had already developed the patches, but prior to yesterday they were only available to customers who are paying big bucks to get extended support.
4 users thanked author for this post.
-
John in Mtl
AskWoody LoungerMay 13, 2017 at 10:00 pm #115013 -
GoneToPlaid
AskWoody Lounger
-
ch100
AskWoody_MVPMay 13, 2017 at 10:27 pm #115027Microsoft was kind enough to release these specific patches for XP and Win8, even though they were under no obligation to do so.
I think this is debatable. Imagine half of the 25% of the computers running XP and many more still running Server 2003 in businesses being actively sources of malware on the internet. Even so, I doubt that many of those running XP/2003 would do updating or be aware of the current update.
anonymous
Guest-
ch100
AskWoody_MVP
lizzytish
AskWoody LoungerMay 14, 2017 at 1:47 am #115068Yes it was a nice gesture from MS……. you know if some companies (not naming anyone) would realise/understand that by helping others they are helping themselves as well. Service/Customer relationship……… comes to mind. When a company adheres to this……… the sky’s the limit……. they and their customers flourish. And although MS’s gesture was very generous….. it was a responsiblity that they owed to the internet.
There is a saying “Noblesse Oblige” which basically means :
“It implies that with wealth, power and prestige come social responsibilities; it is a moral obligation to act with honor, kindliness and generosity.”But after saying all that…. it was a nice gesture and I am sure they will (and would have figured out it was a good move) regain some of the respect and loyalty that has been missing for sometime now. LT
Your time is the greatest gift you can give to someone. Unknown

1 user thanked author for this post.
James Bond 007
AskWoody LoungerMay 14, 2017 at 5:11 am #115101Yes, that’s correct.
Microsoft was kind enough to release these specific patches for XP and Win8, even though they were under no obligation to do so. They had already developed the patches, but prior to yesterday they were only available to customers who are paying big bucks to get extended support.
I am quite surprised, but delighted, to see that Microsoft actually released the corresponding patches for Windows XP and Windows Server 2003. They may have their reasons for doing that (Perhaps there are still many Windows XP and Windows Server 2003 systems out there, eh?), but I still applaud them for this gesture.
Hope for the best. Prepare for the worst.
Navi
AskWoody LoungerMay 13, 2017 at 10:13 pm #115019I read Woody’s article. For the Windows 7 all those patches(?) I never had any on my computer.
You know, if MS haven’t hijacked our desktop trays with their new Windows 10 icon back in late 2015, demanding we upload it, I would have continue the security updates since then. Stupid company. They should’ve stay with selling new OS on the shelves instead. >.< I can’t stand bullies which they did back in 2015.
Oh. I do have one question though. The news kept saying Windows. They didn’t mention which one.
-
GoneToPlaid
AskWoody Lounger -
woody
Manager -
ch100
AskWoody_MVP -
woody
ManagerMay 14, 2017 at 10:02 am #115170 -
ch100
AskWoody_MVPMay 14, 2017 at 3:40 pm #115265Bottom line is that everyone should be patched up to date, regardless of Windows 10 being protected in this case by the original design of the current version of the WannaCrypt worm.
There is no guarantee though that future attacks would not take advantage of this vulnerability and other vulnerabilities already made public.1 user thanked author for this post.
-
Alice
AskWoody Lounger
-
-
-
Navi
AskWoody LoungerMay 13, 2017 at 10:16 pm #115020No. There’s no need to install any new patches unless you specifically don’t have ANY of the ones in the list.
That sounds like me. I think.
1 user thanked author for this post.
Navi
AskWoody Lounger-
lizzytish
AskWoody LoungerMay 14, 2017 at 1:19 am #115063@Navi……….. why don’t you have some sort of reminder on your calendar for example to remind you to check what the Defcon levels are. Woody’s popularity has made it very difficult for him to spread himself any further than he does. His website is stretched financially and to put out an email reminder to everyone would be stretching it even further I feel. He really does more than he needs for us and it’s for us to keep abreast with all of this for ourselves.
Also usually speaking the Defcon level rises towards the end of the month after making sure that the latest offering of patches do not cause trouble for people. So perhaps you could have a reminder for yourself to check then. Just thoughts! LT
“I worry about ridiculous things, you know, how does a guy who drives a snowplough get to work in the morning…… that can keep me awake for days” Billy Connolly

anonymous
GuestMay 13, 2017 at 10:33 pm #115014I’ve just bit the bullet and installed the update on a Windows XP SP3 machine here, installation was completed fast and peaceful…
After the reboot I just noticed that double clicking anything on the desktop would open the properties page, but after clicking ALT/CTRL a couple times things were back fine, so it could only be a stuck key rather than a minor bug…
Also, upon reboot my AV (ESET Nod32) did not search automatically for updates as usual, what could have happened due the fact that the machine was offline moments before to install the update, after a manual run, it updated just fine…
Firefox was also working fine, the internet access, one of my major concerns, was apparently unaffected…
Printing with my wireless printer was also working perfectly…
The update shows on the installed list on the Control Panel, just doesn’t know exactly what or how it changes the OS… Let’s hope it changes for better!
-
anonymous
GuestMay 14, 2017 at 6:00 am #115036Forgot to add, the update has the same 671kb size as the POSReady version published two months ago, which makes me think it is actually the same update… Only an analysis of both files could clear this up I guess…
Also, I was wondering myself, regarding the DoublePulsar implant discussion last month, this malware makes use of basically the same exploit, only this time it carries a specific payload…
By the time the conclusion was that it was not possible to get DoublePulsar if the ports it crawled in wasn’t listening, due to either blocking or stealthing… So I guess that still remains the same today, so what has changed? Basically nothing…
It is apparently unlikely to get hit straight from the web, just like DoublePulsar, but this time it relies on the good oldfashioned social engineering to climb onboard, and deliver its payload… The attack vector is now different, and the propagation method has also evolved, it now packs worm like capabilities, since it can not directly (most of the times) hit the ports from the web, it can now spread laterally, from other computers on the same network, where traffic on ports 139 and 445 is A LOT less likely to find any barriers, since by default most systems would flag it as trusted… And so it spreads…
So what can we conclude here… There is a new threat out there, but yet still its mechanics heavily rely on OLD, very known and familiar factors such as poor network management, bad user habits and of course the everyone’s favorite social engineering…
-
woody
ManagerMay 14, 2017 at 6:51 am #115120The attack vector is now different, and the propagation method has also evolved, it now packs worm like capabilities, since it can not directly (most of the times) hit the ports from the web
That’s what I’m looking into, as soon as my eyes open.
Do you have any links? What is the infection vector?
-
anonymous
GuestMay 14, 2017 at 8:40 am #115141I was reading so much yesterday I wasn’t bookmarking anything specific, but a lot of sources, including Malwarebites blog, claimed a rigged email started it, which I find very likely due the nature of the exploit and where it did spread to, that is basically big corporate networks, the only enviroment where we know a single machine could compromise the entire operation…
I was eager to find a sample of email or file that triggered it, but I couldn’t, and although it is very likely looking at its code, untbil the real thing comes up it all comes down to speculation…
Another factor which I believe corroborates with this hypothesis is the other ransomware campaing which are relying on rigged random generated files sent by email to hi targets, sort of piggybacking in this situation, as discussed in Talos blog…
But once again, no matter how bad it appoints to this conclusion, until the hard evidence, the email, pops up we have nothing…
-
anonymous
GuestMay 14, 2017 at 8:57 am #115152Oh, almost forgot, and ofcourse it could have started if any of those machines had any TCP/IP ports open to the web… Which could happen to a machine used by a layman, but is somewhere around unacceptable for a huge corporate server or network enviroment…
1 user thanked author for this post.
-
JohnW
AskWoody LoungerMay 14, 2017 at 12:39 pm #115213I ran across this: https://blog.fox-it.com/2017/05/12/massive-outbreak-of-ransomware-variant-infects-large-amounts-of-computers-around-the-world/
Infection vector
One of the confirmed infection vectors is the usage of the ETERNALBLUE exploit directly on machines which have SMB directly exposed to the internet.
This chapter previously stated that we were in the process of verifying if phishing e-mails were also an infection vector for the WanaCry ransomware. Thus far Fox-IT has found no evidence that any phishing e-mails were related to this specific ransomware outbreak, and we have therefor removed the related indicators from this blog.

Windows 10 Pro 22H2
1 user thanked author for this post.
-
-
anonymous
Guest-
Volume Z
AskWoody Lounger
GoneToPlaid
AskWoody LoungerMay 13, 2017 at 10:51 pm #115033There has been a second wave of WannaCry/WannaCrypt. The first wave, detected on Friday, was blocked by registering and sinkholing a hard coded domain name which was found in the code. This created a kill switch to stop further infection. The second wave is a modified version of WannaCry/WannaCrypt which has no hard coded kill switch. This second wave was detected earlier today (Saturday).
The WannaCry/WannaCrypt infection also installs DOUBLEPULSAR which will also have to be removed from an infected computer.
1 user thanked author for this post.
-
anonymous
GuestMay 14, 2017 at 8:47 am #115145This one has to be claryified yet… We had reports of DoublePulsar being non persistant and fileless, as such the implant would disappear upon reboot, since it is only RAM based…
It’s more likely WCry is using EternalBlue exploit to spread and leaving a DoublePulsar implant for communication to the host for addition payload, or basically pushing into the machine anything in particular of the creator fancy…
anonymous
GuestMay 13, 2017 at 11:22 pm #115040Hey Woody,
Thanks so much for everything you are doing and thanks as well to your great helper experts. I couldn’t download for 8.1 64bit because I got a message that the site wasn’t working and the administrator of said site should be contacted. It seemed a bit weird because it was the link you posted (adjusted to the correct KB number for 8.1 instead of for win 7 as posted).
It was odd though that a MS download site was not encrypted, ie not https. Well, it’s not the first time MS has been odd and dubious and other adjectives.
Thanks to you and your team,
Mike
P.S. Have you ever thought of writing a Dummies book for Linux? – because the way things are going with MS that’s my next OS and your previous books were good and helpful.
1 user thanked author for this post.
-
Kirsty
Manager -
anonymous
Guest
-
Navi
AskWoody LoungerMay 13, 2017 at 11:34 pm #115047Uh, all of them I think.
Oh, all Windows, then? Thank you.
-
GoneToPlaid
AskWoody Lounger -
anonymous
GuestMay 14, 2017 at 12:54 am #115056@ Navi
For more info, please refer to …
https://blog.varonis.com/massive-ransomware-outbreak-what-you-need-to-know/
https://en.wikipedia.org/wiki/Server_Message_BlockSMBv1 first came with Win 2000 and Win XP, which is vulnerable to the Eternalblue exploit.
SMBv2 came with Win Vista.
SMBv2.1 came with Win 7.
SMBv3.0 came with Win 8/8.1.
SMBv3.1 came with Win 10.
. . A company or home network over LAN/WAN may be running a gamut of interconnected Windows computers to facilitate file and printer sharing and other shared operations, eg from Win XP to Win 10 computers. So, for backwards-compatibility in networking, M$ included SMBv1 in all their later Windows OS versions that came after Win 2000/XP.
anonymous
GuestMay 14, 2017 at 12:55 am #115058Fyi;
Personally, as a Win 7 home-user with no important data stored on my system, I am not too bothered about this WannaCry ransomware or other malware because if infected, I can swiftly recover my system by just doing a clean reinstall or system reimage.
But for those with important data stored on their computers, eg corporations like the NHS, they should be doing regular data or system image backups, in order to be able to recover from a ransomware infection asap and without having to pay the ransom.
. . Of course, regular patching and running an AV program go without saying.Kirsty
ManagerMay 14, 2017 at 2:54 am #115080From Heimdal Security:
Security Alert: WannaCry Leaves Exploited Computers Vulnerable to Round Two
Preventing another ransomware outbreak becomes essentialLast Updated on May 13, 2017
Andra Zaharia
Security Evangelist
“Given that 97% of phishing emails are ransomware and that 31% of the people who receive them open these emails (and often click on links/attachments), their chances for success are still quite high.Also, their international intent was already clear when they translated the ransom note and payment instructions in 28 languages, including Spanish, Swedish, Turkish, Vietnamese, Portuguese and many others.”
The article includes a link to MS’s Baseline Analyzer 2.3, to discover which updates are missing. The tool also lists the missing updates by severity and potential impact.
Another link has been added, for the CCN-CERT NoMoreCry Tool
Check out the full article here
1 user thanked author for this post.
Kirsty
ManagerMay 14, 2017 at 3:25 am #115084Guidance:
Ransomware: Latest NCSC Guidance
Created: 13 May 2017
Updated: 13 May 2017
Computer locked by ransomware
The latest NCSC guidance on RansomwareThe NCSC are aware of a ransomware campaign relating to version 2 of the “WannaCry” malware affecting a wide range of organisations globally. NCSC are working with affected organisations and partners to investigate and coordinate the response in the UK.
From investigations and analysis performed to date, we know that the malware encrypts files, provides the user with a prompt which includes; a ransom demand, a countdown timer and bitcoin wallet to pay the ransom into.
The malware uses the vulnerability MS17-010 to propagate through a network using the SMBv1 protocol. This enables the malware to infect additional devices connected to the same network.
The NCSC advise the following steps be performed in order to contain the propagation of this malware:
Deploy patch MS17-010:
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
A new patch has been made available for legacy platforms, and is available here:
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks
If it is not possible to apply this patch, disable SMBv1. There is guidance here:
https://support.microsoft.com/en-us/help/2696547
and/or block SMBv1 ports on network devices [UDP 137, 138 and TCP 139, 445]
If these steps are not possible, propagation can be prevented by shutting down vulnerable systems.
Work done in the security research community has prevented a number of potential compromises. To benefit from this, a system must be able to resolve and connect to the domain below at the point of compromise.
www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
Unlike most malware infections, your IT department should not block this domain.
Anti-virus vendors are increasingly becoming able to detect and remediate this malware, therefore updating antivirus products will provide additional protection (though this will not recover any data that has already been encrypted).
The NCSC have previously published broader guidance on protecting your organisation from ransomware.
Reproduced in full from ncsc.gov.uk
1 user thanked author for this post.
anonymous
GuestMay 14, 2017 at 4:02 am #115089The following 12-hours-old news about the arrival of the unkillable WannaCry 2.0 ransomware is to be confirmed, …
criminals are now launching attacks using WannaCry 2.0 that do not have ‘kill-switch’ domain connect function.
http://thehackernews.com/2017/05/wannacry-ransomware-cyber-attack.html
-
Kirsty
Manager -
woody
Manager -
James Bond 007
AskWoody LoungerMay 14, 2017 at 8:49 am #115155The following 12-hours-old news about the arrival of the unkillable WannaCry 2.0 ransomware is to be confirmed, …
criminals are now launching attacks using WannaCry 2.0 that do not have ‘kill-switch’ domain connect function.
http://thehackernews.com/2017/05/wannacry-ransomware-cyber-attack.htmlI saw this inside that article :
As we notified today, Microsoft took an unusual step to protect its customers with an unsupported version of Windows — including Windows XP, Vista, Windows 8, Server 2003 and 2008 — by releasing security patches that fix SMB flaw currently being exploited by the WannaCry ransomware.
Are they saying Windows Server 2008 is unsupported? Windows Server 2008 is still supported until 2020, isn’t it?
And although Windows Vista is now out of support, the update concerned, KB4015298, was released in March, when Vista was still supported.
Hope for the best. Prepare for the worst.
-
woody
Manager -
James Bond 007
AskWoody LoungerMay 14, 2017 at 10:42 pm #115314I believe Server 2008 R2 reaches end of support on Jan. 14, 2020. It can be patched with the Win7 patches.
Server 2008 died long ago, if memory serves. That’s the one being patched in this TechNet article.
Woody, I am talking about Windows Server 2008 specifically, not R2.
Look at the Microsoft Lifecycle Policy page :
https://support.microsoft.com/en-us/lifecycle/search?alpha=Windows%20Server%202008It clearly shows that Windows Server 2008 SP2 has extended support until January 14, 2020. So it is definitely not dead yet, and not out of support.
A Windows Server 2008 virtual machine that I have also can obtain patches up to this month.
I have also downloaded a copy of KB4018271 (May IE9 Cumulative Security Update) for Windows Server 2008 x64 and attempted to install it on Windows Vista x64 before, and the installation was successful.
By the way, the Vista patch I was talking about should be KB4012598. Sorry for the mistake.
Hope for the best. Prepare for the worst.
1 user thanked author for this post.
-
-
Noel Carboni
AskWoody_MVPMay 14, 2017 at 7:13 am #115124My hat’s off to you, Woody.
I know how much effort it takes to create solid, accurate summary information such as what you have published here, and it’s right on point for those who really want to know whether they’re protected from these threats. The web needs more “this is how it really is” sites like this one.
Thank you.
-Noel
anonymous
GuestMay 14, 2017 at 7:14 am #115122Hello! I have few question for you if that is fine with you. Today i need to go to patch my older win xp machines, they are mostly patched with SP3 but not fully patched with SP3 later updates. Would it be enough for the first fix just to install this new patch that Microsoft provided? This is also problem with w7 machines they are patched to some point, will it also be enough to install march update provided by microsoft for w7 machines?
Thank you!-
PKCano
Manager -
anonymous
Guest -
PKCano
ManagerMay 14, 2017 at 7:45 am #115136You can TRY Windows Update. There MAY be patches up until the time MS stopped supporting XP (well passed the original EOL date).
If you look elsewhere, you need to be REALLY SURE of the source you download from. I’m sure there are a LOT of bad sites offering updates filled with malware. -
PKCano
Manager -
anonymous
Guest -
anonymous
Guest -
woody
Manager -
anonymous
GuestMay 14, 2017 at 11:09 am #115188Kevin Beaumont twitted, … WannaCry as distributed doesn’t impact XP.
This does not mean that WannaCry does not infect Win XP or that Win XP is invulnerable to the WannaCry ransomware.
. . It may be that the ransomware-makers chose to not target Win XP computers because of its dwindling market share, similar to them seldom targeting Linux desktop computers. Instead, they targeted Win 7 computers first, because it still has a nearly 50% market share for Windows computers.
. . Maybe, they will target Win 10, Win 8.1, Win XP, Win 8 and Win Vista computers later, ie down the line according to their market share. -
woody
Manager
-
-
-
JNP
AskWoody LoungerMay 14, 2017 at 9:56 am #115168You may be able to bring XP “up to date”, this meaning XPLTSB (long term service branch) which MS made available to commercial customers, by following the recommendations here: http://www.pcworld.com/article/2310301/windows-xp-registry-hack-keeps-the-security-updates-rolling.html . It worked for me in January of this year and WU, in XP, still presents me with monthly updates for my XP contained in a virtual machine that I need for legacy programs. There will be a lot of updates, should this work, so be ready for that.
Edit: If you choose to do this, and WU presents you with a list of updates, at least for the time being, hide the May .NET Framework updates, I encountered problems with these. You can always circle back, after everything else is updated, to see if you can get these to install.
-
woody
ManagerMay 14, 2017 at 7:35 am #115131If you haven’t yet seen the Sunday updates at the top of the original blog post, please check them out and tell me if you’ve seen more up-to-date, reliable info.
1 user thanked author for this post.
ch100
AskWoody_MVPMay 14, 2017 at 8:50 am #115156People at Microsoft claim that “nobody running Windows 10 was infected.” I can’t confirm that. Clearly, those who have installed MS07-010 through Win10 cumulative updates are OK (see the list below). But if all Win10 machines are immune, I’d sure like to see an explanation.
Here it is from
https://blogs.technet.microsoft.com/mmpc/2017/05/12/wannacrypt-ransomware-worm-targets-out-of-date-systems/The exploit code used by WannaCrypt was designed to work only against unpatched Windows 7 and Windows Server 2008 (or earlier OS) systems, so Windows 10 PCs are not affected by this attack.
-
anonymous
GuestMay 14, 2017 at 9:57 am #115165For the reference of ch100, …
How to gracefully remove SMB v1 in Windows 8.1, Windows 10, Windows 2012 R2, and Windows Server 2016
Eternalblue is an SMB v1 exploit and it can be used by Win 10 for networking with other older Windows computers via LAN/WAN.
M$’s Technet statement may only be referring to Win 10 not being vulnerable to email phishing attempts by the WannaCry ransomware since Win 10’s Windows Defender likely receives mandatory and immediate virus-definition updates.
anonymous
GuestMay 14, 2017 at 10:17 am #115171-
MrBrian
AskWoody_MVPMay 15, 2017 at 6:59 am #115404Both parts (disabling SMB server and SMB client) should be done. If in doubt, you can ask at https://blogs.technet.microsoft.com/filecab/2016/09/16/stop-using-smb1/.
Volume Z
AskWoody Lounger-
woody
Manager
anonymous
GuestMay 14, 2017 at 11:57 am #115194But I haven’t yet seen a definitive description of how the payload first gets into a network. Many believe that the first point of infection is via a rigged email — but I haven’t yet seen a copy of a bad email.
From this news report about an affected 3rd-party vendor:-
Further investigations by MediaOnline on Sunday revealed that the 12 systems were not installed with the latest patch to dispel the ransomware. Hence, it was being attacked by the WannaCry virus through the internet as the network was registered under a public IP address […]
“We have fixed all the affected systems by replacing the HDD with a new master image with all latest MS patches, disabled SMB access and hardened the system by using a higher security mode of operation.”
A layperson query: Is the vendor saying that systems with exposed IP addresses (& lacking firewall protection ?) are vulnerable to WannaCry & similar attacks simply by being connected to the internet ?
How does the payload enter the system ? Is it possible for an attacker to mass-scan IP addresses, check which IP addresses & ports are responsive, & then simply deploy the ransomware’s executable through an open port (eg. RDP port) ?
Or is it possible to use steganography to hide a malicious executable within an image, & code it such that the payload would automatically extract itself from the image when the latter is viewed ? This can be a tiny 1 by 1 pixel white image embedded within an innocuous-looking webpage or email with a white background.
-
woody
Manager -
PJ
AskWoody LoungerMay 15, 2017 at 6:11 pm #115472So the “index patient” with a vulnerable OS on any network got infected via drive-by “shooting” through his or her open ports ?
Here’s another case example …
What Every Employee Should Know about the WannaCrypt Ransomware (15 May 2017)
So far, HKCERT received two [WannaCrypt] incident reports. Both users were connected directly to the internet without using a router or firewall, and they had not installed the latest security update for their operating system.
The mass-scanning for vulnerable ports is very reminiscent of an incident in the 1990s where the government at my location instructed the national ISP to mass-scan users’ ports without their knowledge or consent. This was when home user firewall software was in its infancy. Hardly any home user had access to firewall protection, or had the knowledge to close & stealth vulnerable ports. (I suspect the latter still applies to the majority of users today.)
The govt was eventually caught red-handed by a university student who had a primitive firewall (or its precursor) on her home system. The govt’s excuse was that it was being “helpful” by scanning users’ systems to find out if they had malware or not. Who knows what else went on, besides the probing of vulnerable ports ? Deploying surveillance spyware perhaps ? Based on the excuse given, it sounds like the govt already managed to worm itself into home users’ systems.
-
fp
AskWoody LoungerMay 14, 2017 at 1:08 pm #115223As I predicted, MS pushes Win10 as a solution to such attacks, but this is highly suspicious.
My understanding was that the only way to be infected is by clicking on some email attachment. And indeed there are references in the media that the attack spread via human gullibility.
Edited for content.
Please follow the –Lounge Rules– no personal attacks, no swearing, and politics/religion are relegated to the Rants forum.-
GoneToPlaid
AskWoody LoungerMay 14, 2017 at 1:22 pm #115230Not entirely true. A computer on a local network can be infected within 2 minutes after another computer on the same network has been infected. Needless to say, the second computer did not open any email attachment. The worm tries to infect up to 100 computers at the same time via the SMB vulnerability.
anonymous
GuestMay 14, 2017 at 3:22 pm #115258Pretty much it… If a vulnerable system is found, via either a mass scan or a targeted attack, people can inject code for virtually anything using the EternalBlue exploit…
So, that is why even on a fully patched system it is important to keep all service ports closed or stealthed… If people can’t find you, the chances of getting hit are reduced…
With stealth someone will still be able to reach you, but it is a lot more likely to happen in a focused attack, maybe if you are the target… In an impersonal, more automatic wide scan, hence less focused, chances tend to drop a lot…
anonymous
GuestMay 14, 2017 at 12:15 pm #115202I’m the same “anonymous” from the above reply #115194. Just realized that there’s no way to submit a name & email address with the comment. The “Your Information” container is totally blank in my Firefox browser.
A question regarding Server Message Block (SMB) … Seems that this WannaCry ransomware took advantage of an SMB v1.0 vulnerability. Despite seeing instructions from Microsoft on how to disable SMB on Win 7, this SMB feature doesn’t seem to exist on my Win 7 Home Premium system.
I’d checked the ‘Turn Windows features on or off’ panel, as well as the following registry key: HKLM\SYSTEM\CurrentControlSet\services\LanmanServer\Parameters
There is no “SMB1” or any SMB-related values to disable (ie. set to “0”). Is SMB only present in Pro & Enterprise builds of Windows OS ?
Thanks,
PJ (also from reply #115194)Edit ti remove HTML
-
woody
Manager -
anonymous
GuestMay 15, 2017 at 6:13 pm #115485Thanks, I’d created an account. I had posted comments (with name & email submission) at this website a a couple of times before, but I didn’t have to register first. And my comments at that time didn’t have to undergo moderation.
1) Interestingly, despite now newly posting from an account, all my comments so far went into moderation, before subsequently disappearing from the moderation queue without being published. I’d logged out & in, but my comments that were previously under moderation queue remaining missing.
I guess this comment would be similarly affected as well. So I’m posting this using “anonymous” again to see if there’s a difference.
Comments (2 out of 2 submitted) disappeared from moderation, but not published:-
- #115463 (timestamp obtained: May 15, 2017 at 3:04 pm) — My reply to GoneToPlaid (#115232) regarding disabling SMBv1;
- #115472 (timestamp obtained: May 15, 2017 at 4:19 pm) — My reply to you Woody (#115205) regarding scanning of open ports
2) Not sure what’s up with the HTML removal issue as per my “anonymous” comment #115202. I always type out my comments on notepad, & then paste the text from notepad into the comment box. Even the registry key mentioned was obtained by right-clicking & copying my registry key, pasted into notepad before being transferred to the comment box here. So where might the (presumably-embedded) HTML codes have come from ?
Thanks !
PJ (the same “anonymous”) -
PKCano
Manager
-
-
anonymous
Guest-
PKCano
ManagerMay 14, 2017 at 12:57 pm #115220You only need one of the March patches. Either one has the fix for the vulnerability.
We have no idea what the effect on a pirated copy will be.1 user thanked author for this post.
-
GoneToPlaid
AskWoody Lounger -
anonymous
Guest -
PKCano
ManagerMay 15, 2017 at 5:33 am #115394You are not safe unless the OS is patched. MS has issued a patch for XP, but be cautious as there may be problems with it. See https://www.askwoody.com/forums/topic/how-to-make-sure-you-wont-get-hit-by-wannacrywannacrypt/#post-115342
-
-
-
GoneToPlaid
AskWoody LoungerMay 14, 2017 at 1:06 pm #115221Like it or not, Windows 10 IS NOT AFFECTED by this bug, patched or not.
Then why did Microsoft release Windows 10 patches for this? Reports of Windows 10 not being affected are simply based on not seeing any Windows 10 infections. This should not be misconstrued to mean that the underlying vulnerability was fixed in all versions of Windows 10, since clearly it wasn’t. It merely means exactly what was stated — that no Windows 10 infections have been seen — and nothing more than that. One possibility is that the WannaCry authors might have deliberately avoided infecting Windows 10 due to its deep telemetry which could possibly be used to help to identify the malware authors.
I am simply saying, don’t jump to conclusions in which 2 +2 do not actually add up to 10. That is delusional thinking which should be avoided.
-
woody
ManagerMay 14, 2017 at 8:18 pm #115296Then why did Microsoft release Windows 10 patches for this? Reports of Windows 10 not being affected are simply based on not seeing any Windows 10 infections.
Not true, on both counts. Reports of Win10 not being affected are direct from Microsoft. What isn’t clear to me is if MS is talking about versions of Win10 that have not been updated since March.
GoneToPlaid
AskWoody LoungerMay 14, 2017 at 1:25 pm #115232I’m the same “anonymous” from the above reply #115194. Just realized that there’s no way to submit a name & email address with the comment. The “Your Information” container is totally blank in my Firefox browser. A question regarding Server Message Block (SMB) … Seems that this WannaCry ransomware took advantage of an SMB v1.0 vulnerability. Despite seeing instructions from Microsoft on how to disable SMB on Win 7, this SMB feature doesn’t seem to exist on my Win 7 Home Premium system. I’d checked the ‘Turn Windows features on or off’ panel, as well as the following registry key: HKLM\SYSTEM\CurrentControlSet\services\LanmanServer\Parameters There is no “SMB1” or any SMB-related values to disable (ie. set to “0”). Is SMB only present in Pro & Enterprise builds of Windows OS ? Thanks, PJ (also from reply #115194) Edit ti remove HTML
You are correct. Instead, you must follow the procedure to disable SMB v1.0 as shown in the following MS document:
-
PJ
AskWoody LoungerMay 15, 2017 at 6:11 pm #115463@ GoneToPlaid
Thanks, that was the same Microsoft article I checked before posting my initial query.The instructions there for Win 7 (whether using Powershell, or editing the registry directly) all point to setting “SMB1” as 0 for the below key:
HKLM\SYSTEM\CurrentControlSet\Services\LanmanServer\ParametersAs mentioned, the issue is: There are no SMB1 or any other SMB-related DWORD values under that registry key on my Win 7 Home Premium system.
I also compared my ‘Turn Windows Features On or Off’ pane against sample standard screenshots, such as this one or this one.
The ‘Windows Features’ pane on my Win 7 does not have “SMB 1.0/ CIFS File Sharing Support” (shown highlighted in the aforementioned standard screenshots). As such, there is no SMB-related function I can untick there.
Am I supposed to manually create the SMB1 DWORD value in the registry, & set this to 0 ? It seems counter-intuitive. It’s like … My door has no hole (or none that I can I find) — but I deliberately create a hole, & then patch that hole ?
Thanks !
-
GoneToPlaid
AskWoody LoungerMay 16, 2017 at 7:48 am #115662Hi PJ,
Under:
HKLM\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
create a DWORD called SMB1 and set its value to zero.
This will not create a hole. Instead, all it will do is make sure that your Windows 7 computer will not be able to use the SMB1 protocol.
Best regards,
–GTP
-
fp
AskWoody LoungerMay 14, 2017 at 1:29 pm #115234I posted a question about patches to Win10 1511 that is relevent to this discussion here:
https://www.askwoody.com/forums/topic/latest-cumulative-update-for-1511/
to which I received no reply. There may be others 1511 users who may be interested, so if anybody is knowledgeable, pls respond. Thanks.
anonymous
Guestanonymous
GuestMay 14, 2017 at 2:42 pm #115248I have found an article that is warning about both SMB v.1 and SMB v.2? Is it not only SMB v. 1 that needs to be disabled if the system can´t get the patches installed now? And as far as I understand disabling SMB v.1 effectively protects against this threat?
https://heimdalsecurity.com/blog/security-alert-wannacry-computers-vulnerable/
-
woody
ManagerMay 14, 2017 at 8:25 pm #115298Is it not only SMB v. 1 that needs to be disabled if the system can´t get the patches installed now?
My understanding is that disabling SMBv1 blocks WannaCrypt … but that’s just one of the possible problems. Best bet is to install MS17-010.
-
Kirsty
ManagerMay 15, 2017 at 2:23 pm #115461From SecureList.com | May 15th:
I’ve seen conflicting reports about the exploit. Is it targeting SMBv1 or SMBv2?
The vulnerability exploited by the EternalBlue tool lies in the SMBv1 implementation. However, to exploit it, the tool also uses SMBv2. This means that it uses both SMBv1 and SMBv2 packets during the attack. Disabling SMBv1 or SMBv2 prevents the infection; however, while disabling SMBv1 (an old protocol) has no significant impact on modern systems, disabling SMBv2 can cause problems. This is why it is highly recommended to disable SMBv1 for the current attack and for the future.
The article contains plenty of good information 🙂

-
Geo
AskWoody Plus-
Geo
AskWoody Plus
ch100
AskWoody_MVP-
woody
Manager -
b
AskWoody_MVPMay 14, 2017 at 11:45 pm #115340Any attached or networked drive is liable to be affected by ransomware (even if unmapped). So there’s no practical solution for a File History drive:
Be aware new ransomware variants will also encrypt or delete the backup versions of your files. This means that even if you have enabled File History, if you have set the backup location to be a network or local drive your backups might also be encrypted. Backups on a removable drive, or a drive that wasn’t connected when you were infected with the ransomware, might still work.
Microsoft Protection Center: Security Tips to Protect Against Ransomware -
Kirsty
ManagerMay 16, 2017 at 4:22 am #115622From Symantec:
In some cases, files may be recovered without backups. Files saved on the Desktop, My Documents, or on a removable drive are encrypted and their original copies are wiped. These are not recoverable. Files stored elsewhere on a computer are encrypted and their original copies are simply deleted. This means they could be recovered using an undelete tool.

JNP
AskWoody LoungerMay 14, 2017 at 5:14 pm #115274Benjamin Disraeli said: “I am prepared for the worst, but hope for the best.” What we seem to be doing, these past few days, and it is most certainly vital, is something in between these two points: We are discussing how to avoid the worst. Obviously, this is the best first line of defense and all that have contributed to this should be thanked profusely.
But, we are not spending much time on the actual topic of “being prepared for the worst”. And whether it is WannaCry/WannaCrypt, or something else down the road, I think we should be spending some time on what to do if you get hit. So, this is going to be my topic, perhaps Woody will want to start a new thread for this topic.
Back in November Woody posed the question: “What’s the best way to do a full image backup in Win7?” This discussion can be found here: https://www.askwoody.com/forums/topic/whats-the-best-way-to-do-a-full-image-backup-in-win7/ . Not surprisingly :), no consensus was reached, but a number of imaging programs were mentioned in this thread. Those new to this site, since November, should strongly consider going back to read this thread.
After that, to whatever extent you are unfamiliar with imaging your primary hard drive, and this is probably most valuable to the home user, the pros on this site will likely have their own strategies, it is time to become familiar with imaging and then starting to do it. Because if you get hit, the best/easiest solution may be as simple as going back to a previous image (depending on how old the image is, some data will be lost unless you also are running constant backups of critical files). But even if imaging isn’t the “full” solution, and you have to do a clean re-install, after that, you can then go to your latest image and get back to pretty great point, before the infection, where all/most of your programs are present, all/most of you data is present, and most important, all of your Windows updates, to that point, are present.
I am an attorney by profession, so I am not the person to tell you how to image, what program to use (I use Paragon Backup & Recovery), etc. That said, I do want to make one thing very clear to newbies to imaging: IT WILL NOT BE ENOUGH TO LEARN HOW TO IMAGE BY RUNNING YOUR IMAGING PROGRAM INSIDE OF WINDOWS FOR THE OBVIOUS REASON THAT, IF YOU GET HIT, AND ARE FROZEN BY SOMETHING, YOU CAN’T OPERATE IN WINDOWS. So, yes, by all means, start to learn how to image within Windows but make certain you have a CD/DVD/Thumb Drive, containing the imaging program, and your bios is set to boot to this device/media before launching Windows. If you don’t know how to do this, hire somebody to do it for you. And make certain you know how to image but, more important, make certain you know how to restore an image from your CD/DVD/Thumb Drive. Again, if you don’t know how to do this, or you can’t figure it out, then hire somebody to spend one or two hours to teach you how to do this.
In summation: Now, more than ever, part of preparing for the worst must include knowing how to image and actually having images available for emergencies. Personally, I keep two available (on an external hard drive that is turned off unless I am using it), just in case one image is corrupted. Some may want more images, but two seems to be the minimum. As for scheduling, you must decide for yourself the correct frequency for your situation. But, please, if you don’t know how to create images of your primary hard drive, it’s time to learn, or be taught, a new skill.
5 users thanked author for this post.
-
anonymous
GuestMay 14, 2017 at 6:00 pm #115278 -
PKCano
ManagerMay 14, 2017 at 6:07 pm #115284More than ever, PATCH RIGHT AWAY, and IMAGE RIGHT AWAY!
You are so right about making frequent images.
But if you wait a week or two after Patch Tuesday before installing the updates, you won’t be a Guinea Pig for everyone else if the patch has a problem. Read Woody’s information on the MS-DEFCON System (button in the bar at the top of the blog)
-
Noel Carboni
AskWoody_MVPMay 14, 2017 at 10:45 pm #115316But if you wait a week or two after Patch Tuesday before installing the updates, you won’t be a Guinea Pig for everyone else if the patch has a problem.
Right on!
There isn’t just one risk here. It’s complicated, and requires a reasoned approach.
-Noel
1 user thanked author for this post.
-
-
Alice
AskWoody LoungerMay 15, 2017 at 1:55 am #115360depending on how old the image is, some data will be lost unless you also are running constant backups of critical files
This is only true if your OS and your data are in the same partition. Having separate partitions is a much better arrangement.
1 user thanked author for this post.
Tinsel
AskWoody LoungerMay 14, 2017 at 5:33 pm #115276Hi there, I have two questions:
1. I tried installing the January security-only KB3212642 on both my and my mother’s laptops and both times was told it wasn’t applicable to the computer. Should I be worried? Is there an earlier patch (ie earlier than Oct 2016) that I need to install it?
2. Once I’ve installed a patch, can I delete it from my downloads file? These are huge files…
Thanks!
-
PKCano
ManagerMay 14, 2017 at 5:57 pm #1152791. The patch you mention is for Win7 SP1 – is that correct?
2. Did you download the correct bittedness – 32-bit of 64-bit?
3. Look in Control Panel\Windows Update. On the right click “View Update history.” If you find any of these updates (KB3212664, KB4012215, KB4015549 or KB4019264) you will not be able to install that update.
4. If you find KB4012215, KB4015549, or KB4019264 in the Update history, you are safe from the WannaCry/WannaCrypt exploit.
5. If you find NONE of the updates listed in #4 in the Update history, download KB4012212 from AKB2000003 and install it. Be sure it matches 32-bit or 64-bit of the PC.You can delete the install file after the reboot if it installs OK.
-
Tinsel
AskWoody LoungerMay 14, 2017 at 9:07 pm #115303Hi there, yes, it’s for Win7 SP1, 64 bit. I used the link from that helpful German bloke’s monthly updates list. When I looked in the update history and searched my updates list, I didn’t have any of the four updates you listed. It looks like they’re all Monthly Quality Roll-Ups, and as a Group B’er, I’m trying to avoid those. Shall I bite the bullet and install the January Roll-Up (3212646) to ensure I get what was in 3212642?
I have 4012204 and 4012212, so I think I’m safe, for now, from the WannaCry exploit.
-
Alice
AskWoody LoungerMay 15, 2017 at 9:52 pm #115542Shall I bite the bullet and install the January Roll-Up (3212646) to ensure I get what was in 3212642?
I have 4012204 and 4012212, so I think I’m safe, for now, from the WannaCry exploit.
With 4012212 installed you’re safe. There’s no need to install any rollups.
-
-
Volume Z
AskWoody LoungerMay 14, 2017 at 9:34 pm #115306Hi Tinsel,
it’s perfectly regular that you cannot install the January Security-Only Rollup with any of the March, April or May Security-Only Rollups present. They all include (supersede) KB3212642 without notification by the Microsoft Catalog. I have just recently made a suggestion to modify AKB2000003 correspondingly.
Regards, VZ
-
Kirsty
ManagerMay 14, 2017 at 10:13 pm #115311@Volume-Z
Confusion is being created by referring to the security-only patches as “rollups”.Please note the “rollup” is not security only:
Microsoft delivers the “Security Monthly Quality ROLLUP for Windows” through Windows Update to the PC. It contains both Security and non-security updates and is cumulative. Cumulative means that this month’s ROLLUP contains the previous month’s ROLLUPS. It is available to all Windows Users.
For those people who do not want the non-security, Microsoft provides the “Security Only Quality UPDATE for Windows.” It contains only the security patches

1 user thanked author for this post.
-
Volume Z
AskWoody LoungerMay 14, 2017 at 10:50 pm #115318An update starts being a rollup as soon as it’s made up of several inseparable units of maintenance. The Monthly Rollup is called a rollup for being made up of several updates. The Security-Only thing, for evidently being made up of several updates, cannot be considered anything else than a rollup.
Regards, VZ
-
PKCano
ManagerMay 15, 2017 at 5:55 am #115398@Volume Z
Your information is incorrect.The “Security Only Quality UPDATES for Windows” are NOT CUMULATIVE.
To receive all security patches, you must install EVERY individual month’s security-only UPDATE. They are NOT offered through Windows Update. They have to be downloaded and manually installed.Only the “Security Monthly Quality ROLLUPS for Windows” offered through Windows Update are cumulative.
-
ch100
AskWoody_MVPMay 15, 2017 at 7:03 am #115408Can everybody please stop using legacy unsupported operating systems.
Please be grateful that you were thrown a lifeline for the next few weeks, but plan quickly for an upgrade, preferably to Windows 10 and keep updated according to the manufacturer’s instructions for your situation and not according to dubious guidelines, too easily found elsewhere. -
anonymous
Guest -
Volume Z
AskWoody LoungerMay 16, 2017 at 9:57 pm #115812My information is correct. You cannot install KB3212642 with any of KB4012212, KBKB4015546 or KB4019263 installed.
If you find any of these updates (KB3212664, KB4012215, KB4015549 or KB4019264) you will not be able to install that update.
Why not? Even if KB3212642 has been superseded by any Monthly Rollup, then that’s an anomaly for a Security-Only something.
Kirsty
ManagerJNP
AskWoody LoungerMay 14, 2017 at 6:36 pm #115286More than ever, PATCH RIGHT AWAY, and IMAGE RIGHT AWAY!
You are so right about making frequent images. But if you wait a week or two after Patch Tuesday before installing the updates, you won’t be a Guinea Pig for everyone else if the patch has a problem. Read Woody’s information on the MS-DEFCON System (button in the bar at the top of the blog)
1. I know this version of anonymous is an attorney :).
2. I wanted to make this long for the new people and to stress the two most important things: a) Bios settings and b) the necessity to learn how to at least restore from CD/DVD/Thumb Drive.
3. One strategy, to split the baby between ann. and PK, would be to image just before running WU and then just after. If one does this, having a third image, older than a month would be advisable.
4. I know Woody has questioned the value of Group B, but I could argue this is now a new world in PC-land and if you image just before Patch Tuesday, and then manually install the two security updates (a. for your version of Windows and b. the IE update) you can then have some added security during the time the full group of patches are completely vetted. Worst case, there is something wrong with these two patches and you can immediately revert to pre-patch Tuesday status. Best case, Groups A & B have two of the three patches (not .NET Framework) already installed, and Group A can do their thing once Woody announces all clear on the full group of Patch Tuesday releases. The better question is not the viability of Group B, but the viability of Group W (BTW, seeing Arlo when he comes to town in October).
-
woody
Manager
anonymous
GuestMay 14, 2017 at 8:33 pm #115294Woody,
On my one desktop Win8 64 bit computer, I followed your link above for “Windows XP, Windows 8…under Further Resources at the bottom of the Technet page…” I choose the link to Window 8 x 64 and downloaded . I was given the default box of “open” and not “save”. And I got the message that it was installed, but I am not finding it in the Windows Update History. I tried again and got this message “Windows Update Standalone Installer Security Update for Windows (KB4012598) is already installed on this computer.” If I am not seeing it on my Windows Update History, is it really installed or must I do something else?
-
PKCano
Manager -
anonymous
GuestMay 15, 2017 at 4:13 pm #115469Boy, has it been hard to get into site today!!! Everybody freaking out.
When I finished installing, I did not get a message instructing me to restart, BUT I chose to “Restart” my computer and not “Shut Down”. Then I checked the Update History and saw there was not anything showing for updates. That is when I click the link in the article for Win 8 x 64 and got the message that the KB article was already on the computer. Not being a computer techie, I am not sure where else to look to see if it is installed or if I need to perform another step in the process. Thank you.
-
PKCano
Manager -
anonymous
Guest
-
-
-
BobbyB
AskWoody LoungerMay 14, 2017 at 9:45 pm #115307This could be a “Moot” point while the current crisis is raging but as we speak different versions of this virus are emerging and the the Monday morning “Boot storm” is likely firing up in Asia/Austalasia/middle east and soon to be Europe.
Does any one have any ideas as to what happens when you get the RSOD (Red Screen Of Death)?
I am hearing restoring from backup? (got that covered) is it going to be as drastic as re-format & reinstall? Just thinking ahead here as to possible solutuions should any of us be unfortunate enough to have “fell through the cracks”
I am currently searching right now for details but they seem scant on the ground after all “fore warned is forearmed” for worst case scenario.
PS this may be of interest https://www.theregister.co.uk/2017/05/14/microsoft_to_spooks_wannacrypt_was_inevitable_quit_hoarding/
NetDef
AskWoody_MVPMay 14, 2017 at 10:34 pm #115313Woody, on the main post/blog about one page down, this section was (I suspect) written before we knew a wave 2 was coming:
IMPORTANT details about WannaCrypt:
It clobbered lots of sites and many computers, but it’s no longer a threat. The folks at Malwaretech.com enabled a sinkhole that’s blocking WannaCrypt. No more infections.
Italics added . . . I feel fairly strongly that anyone newly arriving and seeing those italicized words will relax and not follow through on getting the March patch checked. Perhaps a revision of that section? 😀
Thanks!
~ Group "Weekend" ~
NetDef
AskWoody_MVPanonymous
GuestMay 15, 2017 at 12:43 am #115341-
PKCano
Manager
Psychee
AskWoody LoungerMay 15, 2017 at 12:47 am #115342Woody, some of us out here in XP-SP3 land have tried to install KB4012598 (the WannaCrypt patch) on our machines only to discover that the patch rendered our USB ports non-functional. USB mouses (mice?) no longer worked and USB drives were no longer recognized.
We had to use Restore to get system functionality back – or at least those of us who had another way of interacting with Windows without our USB mouses did. I am thinking that a bunch of others are now stuck not knowing how to proceed without a mouse.
We need the patch, but we also need our USBs. Can you help us?
I have left a message in the “Microsoft Community” about this. Got a dozen folks saying that they were having the same problems, but so far, no solution is being suggested.
Thanks in advance…
Information you might need to help us: I have XP-SP3 (32 bit) on an exceptionally dependable HP Pavilion notebook that I love. There is nothing special about the USB. It is 2.0 and only seems to be using universal USB drivers.The patch installed easily enough, with no errors generated. Upon first restart, it hung with a black screen, like it was in sleep mode, with no way to wake it up. I forced another restart and that’s when the mouse problem became obvious. I then checked Explorer to see if the USB drives were being recognized, and they were not, but there was USB power. Using Restore got my system back to the way it was with the exception of Firefox — that program couldn’t start and I had to re-install it to fix it.
Thanks again for your help.
-
Psychee
AskWoody LoungerMay 18, 2017 at 12:49 am #116054Never mind. I solved my own problem. Turns out that disconnecting from the internet, turning off all McAfee services (and every other program) and removing all USB accessories from their ports allows it to work properly. I disconnected the mouse right after I clicked on the agreement so that port would be empty as well.
When it completed, the USB ports were all dead, but pressing ENTER re-booted the system without need for a mouse, and when the system re-booted, the USB drives were all functional again.
So, thanks anyway!
1 user thanked author for this post.
Pim
AskWoody PlusMay 15, 2017 at 6:50 am #115401@woody: the link to the patch for a localized Windows XP version at the bottom of Microsoft’s TechNet page you refer to, results in the update for Windows XP Embedded and not regular Windows XP (click on the link and then open Details: it says “Embedded” even though the title of the page says Windows XP SP3 and not Embedded). You may want to include a link to the Update Catalog in your article for those people who need the localized KB4012598. In Windows XP it is not possible to install a different language patch so falling back on the English version (which is correctly linked on the TechNet page) does not work.
-
AJNorth
AskWoody PlusMay 15, 2017 at 4:44 pm #115480Hello Pim,
You should find all the patches for XP and Sever 2003 toward the bottom of the page Customer Guidance for WannaCrypt attacks: https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/ .
Cheers,
AJN
-
James Bond 007
AskWoody LoungerMay 15, 2017 at 10:15 pm #115548The link to the patch for a localized Windows XP version at the bottom of Microsoft’s TechNet page you refer to, results in the update for Windows XP Embedded and not regular Windows XP (click on the link and then open Details: it says “Embedded” even though the title of the page says Windows XP SP3 and not Embedded). You may want to include a link to the Update Catalog in your article for those people who need the localized KB4012598. In Windows XP it is not possible to install a different language patch so falling back on the English version (which is correctly linked on the TechNet page) does not work.
The problem you referred to apparently has been fixed by Microsoft. I had experienced the same problem before when attempting to download the Traditional Chinese version of the patch. But now that page does give the correct version instead of the Embedded version.
Hope for the best. Prepare for the worst.
anonymous
Guest-
b
AskWoody_MVP
anonymous
GuestMay 16, 2017 at 7:28 pm #115786Windows 7 KB4019264 was updated to KB4019265 new patch on 16th May 2017. On Windows 7 all important and optional Windows Updates were downloaded until it was up to date, but it could not find any of the patches listed in View installed updates which was confusing. However instead of KB4019264 it had KB4019265 and a search found it on the Microsoft site listed as..
“May 16, 2017—KB4019265 (Preview of Monthly Rollup) Improvements and fixes This non-security update includes improvements and fixes that were a part of Monthly Rollup KB4019264 (released May 9, 2017) and also includes this new quality improvement as a preview of the next Monthly Rollup update: Addressed issue by updating the d3dcompiler_47.dll file to improve application compatibility.”
1) It says KB4019265 “includes improvements and fixes that were a part of Monthly Rollup KB4019264” however the Microsoft support page is not informative about exact patches included. Assuming because it says includes fixes from KB4019264 that it is patched for MS17-010 ransomware?.
2) It is listed as a non-security update but includes a critical patch for the MS17-010 ransomware. Assuming if users already have the KB4019264 patch then KB4019265 is just optional as it’s the same thing but with addition of a .dll file. And if users don’t have KB4019264 then Windows Updates either replaces KB4019264 or just jumps straight to downloading KB4019265?.
As it’s new thought I’d add a heads up here, although I expect it will be detailed in due course. Thanks for the details Woody and hope this information helps others too.
-
PKCano
ManagerMay 16, 2017 at 7:48 pm #115789Windows 7 KB4019264 was updated to KB4019265 new patch on 16th May 2017.
KB4019264 is the 2017-05 Security Monthly Quality Rollup for Win7. It is cumulative and contains three parts: security, non-security, and IE11 updates. It contains the patches from previous months’ Rollups. It is delivered through Windows Update as a CHECKED IMPORTANT update.
KB4019265 is the 2017-05 Preview of Monthly Quality Rollup for Win7. It contains previous months’ Rollup plus the non-security patches that will become part of the June 2017 Rollup. It is delivered through Windows Update as an UNCHECKED OPTIONAL update. It is unchecked because it is not meant to be installed by the general User. It is there for IT people and other similar individuals to test before it is released as part of the following month’s Security Monthly Quality Rollup.
The fix for MS17-010 was part of the March Monthly Rollup and has been a part of the Monthly Rollups since then.
Edit to add content
1 user thanked author for this post.
-
anonymous
Guest -
PKCano
ManagerMay 16, 2017 at 8:36 pm #115800There is no problem leaving KB4019265 installed. The non-security patches for June that are included will be rolled into the June Rollup along with June’s security and IE11 patches.
Just realize, if you install the Preview patches each month, you are helping vet next month’s non-security updates.1 user thanked author for this post.
-
anonymous
GuestMay 16, 2017 at 9:58 pm #115811Hi @pkcano thanks for the advice appreciated, I might leave it then. I didn’t realise the optional update was for testing, the title was “Update for Microsoft Windows” and with concern over recent ransomware it was included with important updates. I’ll check in more detail what optional updates are in future. Might see if there are snooping patches to remove. I read about monthly rollup bundling patches into one important update and you can’t see individual patches on Windows Update history only via the Control Panel, intentional I suppose forcing updates, but for those who want finer control it’s more time consuming, I understand that’s a different topic though. At least it’s patched against the ransomware that’s good.
-
-
-
anonymous
GuestMay 26, 2017 at 9:48 pm #118288Hi,
Just wanted to pass the following info…
I used the XP patch on a genuine (XP sp3 English) install. It installed successfully and I assume I am now protected against Wannacry.
Unfortunately it also seems I am protected against accessing my Kindle Paperwhite. I admit I have unlocked the latter and am running various non-standard apps, but it is the root file access that appears blocked. It will accept power from the USB port, but the computer does not see the device.
And a question…
The latest post seems to say that XP machines are not affected. That would appear to be correct (I think, I’m no expert) since some of the underlying Wannacry functionality does not (I think, I’m no expert) work on an XP install. Any comments or confirmation.
PS I’m going to have to reinstall XP (well actually restore my XP image) anyway. But it would be good to know my risk level
-
Kirsty
ManagerMay 26, 2017 at 10:09 pm #118291From nakedsecurity.sophos.com | 25 May 2017:
During testing, SophosLabs found that XP wasn’t the effective conduit for infection via the EternalBlue SMB exploit that many thought it was, while Windows 7 was easily infected. The research showed that WannaCry ransomware can affect XP computers – but not via the SMB worm mechanism, which was the major propagation vector for WannaCry.
…
Early in the outbreak, researchers determined that both SMBv1 and SMBv2 packets were used in the attack. Since both versions of SMB were in play, it could be theorized that Windows XP proved hard to infect because it does not include SMBv2, which was introduced in Windows Vista. But so far, it’s hard to reach that conclusion with 100% confidence.
…
The bottom line: if you use older versions of Windows, you’re at greater risk for attacks like these.
Kirsty
ManagerJune 4, 2017 at 4:24 pm #119374From theverge.com: Russell Brandom | May 30, 2017
Windows XP isn’t as vulnerable to the WannaCry ransomware as many assumed, according to a new report from Kryptos research. The company’s researchers found that XP computers hit with the most common WannaCry attack tended to simply crash without successfully installing or spreading the ransomware. If true, the result would undercut much of the early reporting on Windows XP’s role in spreading the globe-spanning ransomware.
The core of WannaCry is a vulnerability in a Windows file-sharing system called SMB, which allowed WannaCry to spread quickly across vulnerable systems with no user interaction. But when Kryptos researchers targeted an XP computer with the malware in a lab setting, they found that the computers either failed to install or exhibited a “blue screen of death,” requiring a hard reset. It’s still possible to manually install WannaCry on XP machines, but the program’s particular method of breaking through security simply isn’t effective against the older operating system.
“The worst-case scenario, and likely scenario,” the Kryptos report reads, “is that WannaCry caused many unexplained blue-screen-of-death crashes.”

1 user thanked author for this post.
Kirsty
ManagerJune 10, 2017 at 6:30 pm #120151Reporting on InfoSec 2017:
Was there a silver lining in WannaCry ransomware attack?“If there was a silver lining to wannacry, it’s that it [grabs] people’s attention” in regards to ransomware. What was once an obscure threat for a private individual, though an obsession for the security industry, is now a real and present danger in the minds of many more.
Ransomware, it should be said is far from dead. In fact, it appears to be in rude health: There were 246 new families of ransomware in 2016, compared to just 29 in 2015. A recent PhishMe report revealed that 97 percent of all phishing emails contain crypto ransomware and another report from Infoblox recorded a 35-fold increase in ransomware domains in 2016.
As awareness of the problem increases, ransomware’s astounding success may turn out to be a weakness, too. “This rate of expansion and investment won’t continue,” Ferguson said. “It will plateau.”
Read the full article on scmagazine.com:
By Max Metzger | June 8, 2017
MrBrian
AskWoody_MVPJune 11, 2017 at 9:57 pm #120237From EternalPot — Lessons from building a global Nation State SMB exploit honeypot infrastructure (May 28, 2017):
“Then I placed the systems live, deploying 7 Nodes into datacenters worldwide, opening up port 445 on the firewall for the first time, and made a brew while I waited for traffic to arrive.
By the time I returned back to my desk with my brew, most of the honeypots were already owned, or blocking things.
The reality is malicious SMB using MS17–010 exploits arrives at a Node every minute or so. If you think back to the Blaster worm from ten years ago, we’re back to that.”
1 user thanked author for this post.
Viewing 55 reply threads -

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Tracking content block list GONE in Firefox 138
by
Bob99
4 hours, 55 minutes ago -
How do I migrate Password Managers
by
Rush2112
4 hours, 18 minutes ago -
Orb : how fast is my Internet connection
by
Alex5723
9 hours, 17 minutes ago -
Solid color background slows Windows 7 login
by
Alex5723
10 hours, 37 minutes ago -
Windows 11, version 24H2 might not download via Windows Server Updates Services
by
Alex5723
9 hours, 8 minutes ago -
Security fixes for Firefox
by
Susan Bradley
8 hours, 37 minutes ago -
Notice on termination of services of LG Mobile Phone Software Updates
by
Alex5723
21 hours, 21 minutes ago -
Update your Apple Devices Wormable Zero-Click Remote Code Execution in AirPlay..
by
Alex5723
1 day, 6 hours ago -
Amazon denies it had plans to be clear about consumer tariff costs
by
Alex5723
21 hours, 26 minutes ago -
Return of the brain dead FF sidebar
by
EricB
8 hours, 37 minutes ago -
Windows Settings Managed by your Organization
by
WSDavidO61
7 hours, 45 minutes ago -
Securing Laptop for Trustee Administrattor
by
PeachesP
8 hours, 46 minutes ago -
The local account tax
by
Susan Bradley
9 hours, 58 minutes ago -
Recall is back with KB5055627(OS Build 26100.3915) Preview
by
Alex5723
1 day, 19 hours ago -
Digital TV Antenna Recommendation
by
Win7and10
1 day, 11 hours ago -
Server 2019 Domain Controllers broken by updates
by
MP Support
2 days, 7 hours ago -
Google won’t remove 3rd party cookies in Chrome as promised
by
Alex5723
2 days, 8 hours ago -
Microsoft Manager Says macOS Is Better Than Windows 11
by
Alex5723
2 days, 12 hours ago -
Outlook (NEW) Getting really Pushy
by
RetiredGeek
1 day, 14 hours ago -
Steps to take before updating to 24H2
by
Susan Bradley
1 day, 5 hours ago -
Which Web browser is the most secure for 2025?
by
B. Livingston
1 day, 19 hours ago -
Replacing Skype
by
Peter Deegan
1 day, 7 hours ago -
FileOptimizer — Over 90 tools working together to squish your files
by
Deanna McElveen
2 days, 6 hours ago -
Excel Macro — ask for filename to be saved
by
nhsj
1 day, 3 hours ago -
Trying to backup Win 10 computer to iCloud
by
SheltieMom
1 day, 7 hours ago -
Windows 11 Insider Preview build 26200.5570 released to DEV
by
joep517
4 days, 12 hours ago -
Windows 11 Insider Preview build 26120.3941 (24H2) released to BETA
by
joep517
4 days, 13 hours ago -
Windows 11 Insider Preview Build 22635.5305 (23H2) released to BETA
by
joep517
4 days, 13 hours ago -
No April cumulative update for Win 11 23H2?
by
Peobody
3 days, 1 hour ago -
AugLoop.All (TEST Augmentation Loop MSIT)
by
LarryK
4 days, 14 hours ago
Recent blog posts
Key Links
| S | M | T | W | T | F | S |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | ||||
| 4 | 5 | 6 | 7 | 8 | 9 | 10 |
| 11 | 12 | 13 | 14 | 15 | 16 | 17 |
| 18 | 19 | 20 | 21 | 22 | 23 | 24 |
| 25 | 26 | 27 | 28 | 29 | 30 | 31 |
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.