Newsletter Archives
-
What to do with the time that is given us

“I wish it need not have happened in my time,” said Frodo.
“So do I,” said Gandalf, “and so do all who live to see such times. But that is not for them to decide. All we have to decide is what to do with the time that is given us.”
-
Mingis: Tech pitches in to fight COVID-19
Some refreshing news about our industry.
As IT pros around the world go all-out to support a workforce that’s suddenly fully remote, many technology workers and companies are also joining efforts to alleviate the COVID-19 crisis in various ways, including developing products to combat the virus, tracking and predicting its spread, and protecting hospitals from cyberattacks.
Pitch in and help!
-
Our spam filter has a twitchy trigger finger

I’m not sure why, but our spam filter has been kicking out posts for reasons that leave me scratching my head.
We’re talking to the vendors about it. Hope to get it fixed soon. But in the meantime, if you post something and it disappears unexpectedly (especially if you edit a post and it disappears, or if you’re trying to post multiple links in a reply), don’t be overly alarmed. It’s happening to all of us.
Best bet is to
just post again, changing the wording a bit.I just got my knuckles rapped for making that suggestion. For a good reason: Submitting the same post over and over again really clogs up the manual vetting. Much better idea is to wait a day, and see if the post shows up. -
Yet another bug in this month’s Windows patches: Proxy bug knocks out some internet connections
There’s a reason why I wait before recommending that you install patches, yes?
News came yesterday afternoon that every.single.Windows.patch released since the “optional, non-security, C/D Week” patch at the end of February introduces a newly acknowledge bug:
Devices using a proxy might show limited or no internet connection status
Devices using a manual or auto-configured proxy, especially with a virtual private network (VPN), might show limited or no internet connection status in the Network Connectivity Status Indicator (NCSI) in the notification area. This might happen when connected or disconnected to a VPN or after changing state between the two. Devices with this issue, might also have issues reaching the internet using applications that use WinHTTP or WinInet. Examples of apps that might be affected on devices in this state are as follows but not limited to Microsoft Teams, Microsoft Office, Office365, Outlook, Internet Explorer 11, and some version of Microsoft Edge.
According to Microsoft, this bug was introduced in the “optional, non-security, C/D Week” patch for February. If you’re running Win10 1903 or 1909, that’s KB 4535996.
English translation: If you’ve installed any of the Windows updates since last February’s switch to MS-DEFCON 3, you’ve been bitten.
There have been three bad patches: The usual Patch Tuesday cumulative update, KB 4540673 for Win10 1903 and 1909; the emergency, notoriously buggy cumulative update KB 4551762 that was supposed to fix the SMBv3 bug; and KB 4541335, which is the next-to- penultimate “optional, non-security C/D Week” patch for Win10 1903 and 1909. [Correction: We’ll have optional, non-security, C/D Week patches in both April and May. Oh boy.]
If you’re using some other version of Windows, the KB numbers will be different.
Microsoft says “We are working on a resolution and are targeting a Microsoft Catalog only release of an out-of-band update to resolve this issue by early April.” English translation: If you were trusting enough to install any Windows patches since Feb’s switch to MS-DEFCON 3, and you hit a problem connecting to the internet, try rolling back the patch.Or “You might be able to mitigate the issue by restarting your device.”
The problem is odd enough that I haven’t seen it in action. But if your internet connection keeps dropping, you should definitely look at rolling back the buggy update(s). There’s nothing in those patches that needs to be installed, like, right now.
And fer heaven’s sake, don’t voluntarily put your machine in the “cannon fodder” category. Sit back, relax, wait for the problems to appear. And watch the MS-DEFCON level.
-
Reported problem with the latest Windows Defender “Unexpected error”
Oh boy. You know that unpublicized Windows Defender patch that fixed the “Items skipped during scan” bug?
There are two reports on Reddit already about bugs in the new version. Per u/K1Xaviesta:
Hi I just updated my windows 10 and I got a notification that the windows defender is off and when I go to Windows Security and Virus & threat protection to turn it on it says “Unexpected error. Sorry, we ran into a problem. Please try again.”
Are you seeing similar problems after installing KB4052623?
-
Microsoft pauses non-security patches
Microsoft says it won’t be pushing any new non-security patches (although they just pushed one about an hour ago).
We have been evaluating the public health situation, and we understand this is impacting our customers. In response to these challenges we are prioritizing our focus on security updates. Starting in May 2020, we are pausing all optional non-security releases (C and D updates) for all supported versions of Windows client and server products (Windows 10, version 1909 down through Windows Server 2008 SP2).
There is no change to the monthly security updates (B release – Update Tuesday); these will continue as planned to ensure business continuity and to keep our customers protected and productive.
Perhaps you can read the tea leaves better than I can. Is Microsoft saying that, for the foreseeable future, they’re only going to be releasing security patches to Win10? The announcement doesn’t quite say that – and today’s patch is a counterexample – but it certainly hints in that direction.
If so, bravo!
UPDATE: Mary Jo Foley has a recap. But it still doesn’t answer my fundamental question. I think. Will we stop getting non-security patches altogether?
ANOTHER UPDATE: I put together my concerns in this post for Computerworld Woody on Windows. I sure wish MS would learn to speak clearly….
P.S. Why, oh why, isn’t Microsoft using an Insider ring for non-security patches on production versions of Windows?
AN OFFICIAL UPDATE: On Twitter, a few minutes ago, the official @WindowsUpdate account said:
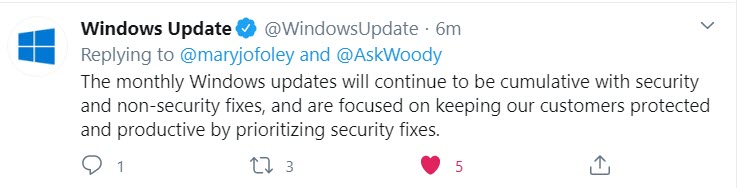
That sounds right to me.
-
Microsoft quietly fixes the “Items skipped during scan” Windows Defender bug
Report out this morning from Günter Born: It appears as if Microsoft has released a new version of Windows Defender that fixes the “Items skipped during scan” bug I talked about in Computerworld yesterday.

It’s listed as KB 4052623. You should get it automatically in the next day or two (Windows Defender updates aren’t controlled by the usual Windows Update settings). It’s also available in the Microsoft Catalog.
-
Microsoft releases the “optional, non-security, C/D Week” patch for Win10 version 1903 and 1909
It’s KB 4541335 – covers lots of little fixes.
As usual, you won’t get it unless you go into Settings > Update & Security, then click the link to Download and install now.
Also as usual, you don’t want it. Let the other WFHers try it first.
-
March 2020 Windows and Office patch status
What a strange month.
Two sky-is-falling security holes with unconscionable “Microsoft warns meeeeeeelions of Windows users that they’re vulnerable” headlines. (Spoiler: The sky isn’t falling.)
A bogus warning about skipped scans.
And lots of people working from home who really don’t need another unstable round of updates or upgrades.
Details in Computerworld Woody on Windows.
We’re still on MS-DEFCON 2. There’s no pressing reason to install this month’s patches. Yet.
-
Yet another font exploit
You’d think that MS would’ve figured out a way to block all of the bad font takeover scenarios, but apparently not. Adobe Type Manager fonts just got hit again, this time with a Type 1 PostScript font.
MS just released Security Advisory ADV200006: Type 1 Font Parsing Remote Code Execution Vulnerability
Two remote code execution vulnerabilities exist in Microsoft Windows when the Windows Adobe Type Manager Library improperly handles a specially-crafted multi-master font – Adobe Type 1 PostScript format.
There are multiple ways an attacker could exploit the vulnerability, such as convincing a user to open a specially crafted document or viewing it in the Windows Preview pane.
Doesn’t look like something you should worry about – when MS says it’s seen “limited targeted attacks” that usually means normal people aren’t in the line of fire. Expect more about this next Patch Tuesday.
There’s a manual workaround, but it’s pretty hairy.
-
Windows Defender SNAFU: “Items skipped during scan”
Günter Born is chasing an odd bug (at least, it looks like a bug).
In Win10, when you run a scan in Windows Defender, it may tell you

But there’s no indication of which items were skipped, or how or why. And many people are saying they haven’t told Defender to skip anything.
Looks like the bug’s been out for a couple of weeks. Anybody have any guesses?
-
Help us test the new AskWoody FREE Newsletter
We’ve hit more than a few snags along the way, but all now seems set for the re-appearance of the old Windows Secrets Free Newsletter, now cleverly renamed the AskWoody FREE Newsletter.
And, yep, it’s free – unlike the AskWoody Plus Newsletter, which goes out to folks who make a donation.
For you Plus Members, it won’t have any remarkable new content — the main article in the FREE Newsletter will be one of the articles in the Plus Newsletter, and “Best of the Lounge” will come across — but it’ll be arranged a little differently. Most of all it’s an absolutely free way for folks to see what we’re all about. With a little luck, FREE subscribers will decide to donate — or at the very least, sign up here on AskWoody.com and join the merry, no-bull crew.
If you’d like to help test, there’s a very simple signup form here. (Yes, we’ve brought across the signups from our last effort to get the FREE Newsletter off the ground. No need to sign up twice.)
Expect the first, beta test version, to arrive in your mailbox later today.
Your comments, criticisms, suggestions, and off-the-wall ideas are most welcome here in the comments.


