Newsletter Archives
-
Missed the September patches – now what?
Just got a message from an old friend:
Hello Woody:
You briefly went to DEFCON-3 last week for installing the September updates, but then shortly after that you dropped back to DEFCON-1 before I had a chance to install the September updates. I’m confused about what to do about the September updates, now that we’re past the Patch Tuesday for October. I’ve never seen you go past the Patch Tuesday without recommending we install the previous month’s updates. Should we be installing the September updates if we missed the narrow window of opportunity we had last week?
It’s easy. Don’t do anything.
I moved quickly to MS-DEFCON 1 when it became apparent that MS was releasing really buggy patches. Then releasing even buggier fixes to the buggy patches. Then pushing still-buggy fixes to the even buggier patches. Yep, three rounds of patches, all infested with bugs.
If you didn’t get the September updates installed, don’t worry about it. There’s absolutely nothing in the September updates that has to be installed right away.
That said, there is a significant looming problem. You need to make sure you don’t use Internet Explorer – and you have to disable IE as your default browser. Almost all of you have done that already, but if you haven’t, follow the detailed instructions in Monday’s AskWoody Plus Newsletter, or the original advice here.
Then sit back and wait for the MS-DEFCON level to change to 3, 4, or 5. If you’re a Plus Member, I’ll also send out an email Alert when the change comes.
-
October 2019 Patch Tuesday – watch out
The patches just hit. I count 132 new patches in the Update Catalog — added to the 50 that were released on Oct. 3rd (and updated on the 4th).
Dustin Childs, in his usual thorough overview for the Zero Day Initiative, pegs it at 59 separately identified security holes (CVEs). No new advisories. There are no new “Public” or “Exploited” patches. Our old friend CVE-2019-1367, the infamous IE zero-day isn’t on the list of new patches. Childs says:
– CVE-2019-1367 – Scripting Engine Memory Corruption Vulnerability
This patch was actually released on September 23 to address active attacks reported on IE. However, this initial patch was only available via manual download and wasn’t on Windows Update or Automatic Update. On October 3, they updated and re-released the patch on all platforms. They also noted the updated patch addresses some quality issues introduced by the first patch. It seems the rush to create the update to stop the attacks had a bumpy start, and some reports indicate printing issues continue. If you’re worried about the risk, restricting access to jscript.dll is a good alternative to applying the patch.Which is certainly giving Microsoft the benefit of the doubt. 🙂 I continue to recommend not using IE and setting your default browser to something – anything – else.
Martin Brinkmann has his full listing on the Ghacks.net site.
I’m happy to report that, after a five day absence, the official list of Servicing Stack Updates, ADV990001, is now up and working. Almost all of the SSUs are new this month. (Servicing Stack Updates fix Windows Update itself. Normally, Windows Update installs them automatically; you only need to worry about them if you’re manually downloading and installing updates.)
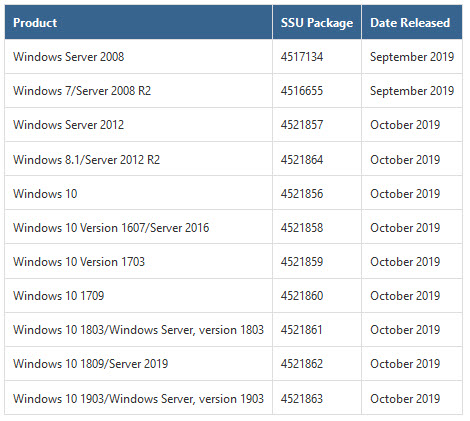
It looks like the latest cumulative updates for all Win10 versions include the changes made for the October 3 out-of-band patch. Bugs and all, I would assume.
The answer seems to be Yes https://t.co/qnVtBpeShv eg pic.twitter.com/e1ieUtKgPJ
— Tero Alhonen💙💛 (@teroalhonen) October 8, 2019
Günter Born has posted several descriptions of RDP bugs in the last cumulative update to Win10 version 1903, KB 4524147. Betcha bucks to buckaroos that we’ll see the same bugs (along with all of the printer bugs and Start menu bugs and … ) in the latest cumulative update, KB 4517389.
We’re still at MS-DEFCON 1: Don’t patch. For any reason, real or imagined.
-
MS-DEFCON 1: Don’t patch, don’t use Internet Explorer, and set up an alternate default browser
Microsoft (finally!) divulged some details about that CVE-2019-1367 patch (actually, three bumbling, successive patches, for all versions of Windows). But they stuck it behind a $690 paywall.
Details in Computerworld Woody on Windows.
-
Bears repeating: Don’t use Internet Explorer, and make some other browser your default
Lots of angst floating around because of the latest, buggy patches, but the bottom line is clear:
- Don’t use Internet Explorer
- Make some other browser the default
Several of you have asked how to make a different browser the default, and it’s easy.
First, install the browser you want. I use Google Chrome most of the time, but if snooping makes your skin crawl, try Firefox or one of the zillions of alternatives. As part of the setup process, you’ll be able to make your new browser the default. Follow the instructions.
If you already have the browser that you want to use as the default….
In Windows 10:
Click Start > Settings, pick Apps (on older versions of Win10, you need to choose System). On the left, click Default Apps. On the right, under Web browser, click on whatever Microsoft has chosen for you (for many of you it’ll be Microsoft Edge). In the Choose an App list, pick anything except Internet Explorer.
You don’t need to click Save. Just “X” out of the dialog.
In Windows 7:
Click Start > Control Panel. Under Programs, click the link that says Default Programs. On the left, choose the browser you want to use. On the right, choose Set this program as default.
In Windows 8.1:
Click Start > Settings, pick Search and Apps. Click Default Programs. Click Set your default programs, choose your browser from the list, and click Set this program as default.
There are many variations on the theme — most browsers have handy shortcuts, inside the browser, that let you change the default as a browser setting. But at its most rudimentary, those paths should get you there.
-
All of the out-of-band patches were re-issued in the past few hours
Every. Single. One.
I just woke up to discover that all 50 of the 2019-10 patches in the Microsoft Update Catalog have been re-issued. They used to be dated Oct. 2. Now they’re dated Oct. 4. That kind of wholesale change is common when Microsoft changes “metadata” — the part of the patches that control how the patch gets installed. But it appears as if some of the patches (all of them?) have been yanked from Windows Update.
@PKCano reports that the Win7 out-of-band patch, KB 4524157, has disappeared from Windows Update.
The KB 4524157 Knowledge Base article says that it’s still available via Windows Update. But, apparently, the KB article lies. No surprise there.
I just ran a wushowhide check on my Win10 1809 product machine, and it doesn’t show KB 4524148 — the 1809 out-of-band patch — as pending.
Ztrucker on Tenforums reports, for Win10 version 1903:
I had to get the Servicing Stack Update and Cumulative Update from the MS Catalog since Check for updates did not give it to me.
Let me do a quick run through my virtual machines and the blogosphere and check back.
The official Windows Update Status page doesn’t say anything about the new turn of events.
@PKCano theorizes that MS isn’t even going to change the KB numbers, when the “for real” Patch Tuesday patches arrive on Tuesday. Kinda sweep everything under the rug.
Oh. And the bugs are pouring in. Mayank Parmar at Windows Latest just published an article about the Sept. 26 patch for Windo 1903 — the third September cumulative update, KB 4517211 – breaking VMWare Workstation. Yesterday, Abhay Venkatesh at Neowin talked about the broken Start menu after installing the latest (fourth September cumulative update, KB 4524147) patch for Win10 1903. Venkat at Techdows has a smorgasbord report of bugs in KB 4524147 as well. Sergiu Gatlan has a report in BleepingComputer about the broken Start menu in KB 4524147. He, too, talks about the ongoing print problems.
I just spot-checked the update downloads in the Catalog, and they contain files dated Sept 30 and Oct 1.
We’re still at MS-DEFCON 1, folks. There’s absolutely no good reason to install ANY September patches.
… and if you still think that the monthly patches are getting better, I know a fine opthamologist…
-
The latest Master Patch List is up
Susan Bradley has full details on the Master Patch List page (yes, Plus Membership required – but becoming a Plus Member is easy, and you get to decide how much to donate).
Short version: Enterprises need to test like crazy, especially for printing problems, before installing yesterday’s patches — but Susan hasn’t hit any bugs. I say individuals should wait for now.
Stay tuned.
P.S. Just saw this:
I’d like to thank @Microsoft for pushing out Windows 10 v1903 w/KB4524147 included, breaking the Print Spooler service, bypassing our WSUS, and wasting hours of my time. Seriously, thanks for the job security. @AskWoody
— Kobold Curry Chef (@KoboldCurryChef) October 4, 2019
-
We have a real out-of-band update now, but very little information – and what appear to be a LOT of bugs.
I’m still sitting on a fence. I’m moving to MS-DEFCON 1 temporarily, until we have a better understanding of what’s going on. But be prepared to get yesterday’s patches installed quickly, should the need arise.
More details in Computerworld Woody on Windows: Microsoft releases even more patches for the CVE-2019-1367 IE zero-day, and the bugs are having a field day.
-
Reported problem with Start menu after installing today’s out-of-band IE patch
This from Reddit poster pyork211099:
Broke my Start Menu immediately… It gives me critical error when i click start menu button…
StartMenuExperienceHost.exe not running. Nor is ShellExperienceHost.exe, actually.
All users that log in, multiple computers, Domain joined.
Got a response back from poster apsolutiNN, who describes the same problem. He was running Win10 1903 with the August cumulative update, build 18362.295. He apparently installed KB4524147, skipping the three September cumulative updates, and today’s patch froze his Start button. Rolling back KB4524147 brought the Start button back to life.
The original poster says:
18362.356 working fine. [That’s the first September cumulative update. -WL]
18362.388 breaks start menu. Uninstalling KB4524147 fixes that start menu issue.
I rolled back the KB4517211 through WSUS.
Looking for more confirmation.
-
Heads up! 50 new security patches just pushed to the Update Catalog
Sometime in the past hour-or-so we got 50 new patches in the Catalog. They’re marked:
IMPORTANT This is a required security update that expands the out-of-band update dated September 23, 2019. This security update includes the Internet Explorer scripting engine security vulnerability (CVE-2019-1367) mitigation and corrects a recent printing issue some users have experienced. Customers using Windows Update or Windows Server Update Services (WSUS) will be offered this update automatically. To help secure your devices, we recommend that you install this update as soon as a possible and restart your PC to fully apply the mitigations. Like all cumulative updates, this update supersedes any preceding update.
Note This update does not replace the upcoming October 2019 monthly update, which is scheduled to release on October 8, 2019.
According to @EP, we’re being treated to:
KB4524135 IE update for IE9/IE10/IE11
KB4524147 CU for 1903 (build 18362.388)
KB4524148 CU for 1809 (build 17763.775)
KB4524149 CU for 1803 (build 17134.1040)
KB4524150 CU for 1709
KB4524151 CU for 1703
KB4524152 CU for 1607
KB4524156 Rollup for Win8.1
KB4524157 Rollup for Win7More info as we find out what the Sam Hill is going on.
UPDATE: The KB article also says that it fixes the .NET 3.5 installation problem introduced in both the second and third September cumulative updates for all Win10 versions:
This security update includes quality improvements. Key changes include:
Addresses an intermittent issue with the print spooler service that may cause print jobs to fail. Some apps may close or generate errors, such as the remote procedure call (RPC) error.
Addresses an issue that may result in an error when you install Features On Demand (FOD), such as .Net 3.5. The error is, “The changes couldn’t be complete. Please reboot your computer and try again. Error code: 0x800f0950.”
That tells me somebody’s listening – but it also tells me that MS is doing a very poor job of updating their Windows Release Information page. I think I’ll write about that in Monday’s Plus Newsletter.
By the way… depending on your definition, the September 23 cumulative update was absolutely NOT an out-of-band patch. A real out-of-band patch goes out to everybody (the Sept. 23 patch was download only), gets distributed through the update servers, and it’s reasonably well documented. This patch is an out-of-band update — except we still don’t know much about the zero day.
-
October 2019 Office non-Security updates have been released
The October 2019 non-Security Office updates have been released Tuesday, October 1, 2019. They will not included in any DEFCON approval for the September 2019 patches. Unless you have a specific need to install them, you should wait until Susan Bradley (Patch Lady) approves them and any problems have been reported.
Remember, Susan’s patching sequence and recommendations are based on a business environment that has IT support and may have time constraints on the updating process. Consumer patching should be more cautious due to limited technical and mechanical resources. The latter is the reason for the AskWoody DEFCON system.
Office 2010
Update for Microsoft Outlook 2010 (KB4475604)Office 2013
Update for Microsoft Outlook 2013 (KB4484096)Office 2016
Update for Microsoft Office 2016 (KB4475585)
Update for Microsoft Office 2016 (KB4484114)
Update for Microsoft Office 2016 Language Interface Pack (KB4475582)
Update for Microsoft Outlook 2016 (KB4484107)
Update for Microsoft PowerPoint 2016 (KB4475578)
Update for Microsoft Project 2016 (KB4484116)
Update for Microsoft Word 2016 (KB4484105)
Update for Skype for Business 2016 (KB4484102)There were no non-security listings for Office 2007 (which is out of support).
Updates are for the .msi version (persistent). Office 365 and C2R are not included.
Security updates for all supported versions of Microsoft Office are released on the second Tuesday of the month (Patch Tuesday).


