-
Any details on the re-issued KB articles for January .NET patches?
There’s a whole bunch of re-issued KB articles for January’s security patches for multiple versions of .NET: 4076495, 4076494, 4076493, 4076492, and several more. I highlighted the once I noticed in this morning’s KBNew listing.
They seem to be associated with CVE-2018-0764 and -0786.
Anyone know if these are just housekeeping updates – or if something else is going on? The February .NET patches didn’t include any security fixes.
-
February patches bring key Outlook fixes and a rebirth of KB 2952664
Unless you use an installed version of Outlook, there’s no reason to patch just yet. Even if you have a bought-n-paid-for version of Outlook, patching is iffy.
Computerworld Woody on Windows.
-
February 2018 Security Patches Are Out
The Microsoft Software Update Services pages have finally been updated. With 34 new patches listed – first update since January 9th in spite of the patches, re-patches, and re-re patches.
Due to issues with some anti-virus software and the Meltdown/Spectre fixes last month, the ALLOW REGKEY must be set in the Registry by the AV software to enable downloads through Windows Update.
Martin Brinkman has posted his usual thorough overview on ghacks.net.
Operating System Distribution
- Windows 7: 15 vulnerabilities of which 1 is rated critical and 14 are rated important
- Windows 8.1: 12 vulnerabilities of which 1 is rated critical, 10 are important, and 1 is moderate
- Windows 10 version 1607: 17 vulnerabilities of which 1 is rated critical and 16 are rated important
- Windows 10 version 1703: 18 vulnerabilities of which 1 is rated critical and 17 are rated important
- Windows 10 version 1709: 19 vulnerabilities of which 1 is rated critical and 18 are rated important
Windows Server products
- Windows Server 2008: 11 vulnerabilities of which 1 is rated critical and 10 are rated important
- Windows Server 2008 R2: 14 vulnerabilities of which 1 is rated critical and 13 are rated important
- Windows Server 2012 and 2012 R2: 12 vulnerabilities of which 1 is rated critical 11 are rated important
- Windows Server 2016: 17 vulnerabilities of which 1 is rated critical and 16 are rated important
Other Microsoft Products
- Internet Explorer 11: 2 vulnerabilities, 1 critical, 1 important
- Microsoft Edge: 14 vulnerabilities, 11 critical, 2 important, 1 moderate
KB article 4077965 lists Office Security and non-security updates:
Office 2016 – 13
Office 2013 – 8
Office 2010 – 5
Office 2007 – 2
SharePoint and SharePoint Servers – 8
Many of these have fixes for remote code execution vulnerabilities.If last month’s updates are any example, it is a good idea to backup your system before installing these updates – after we reach DEFCON-3 or above later this month, of course.
-
I’ve re-enabled nested comments
We’re running an experiment, to see if nested (threaded) comments on AskWoody bring the server to its knees. We’ll know shortly.
In the interim, for those of you who prefer using the “flat” commenting format, to make it easier to find new replies, try searching (Ctrl+F) for the word “New.” It isn’t as easy as scrolling to the bottom (or the top) of a flat list, but nesting makes it one whole heckuvalot easier to keep conversations sorted out.
-
Thurrott: Stop the relentless release of new Windows versions
Another great post in (paywalled) Thurrott.com premium:
Apple will slow down the addition of new features to iOS in order to focus on quality. This is exactly the strategy that Microsoft needs to adopt. In fact, it’s years overdue.
Amen, bro.
One little observation. Paul says that Microsoft will soon be forced into a three-year support cycle and “at that point, we’re pretty much back to where we started.” Which is correct, but there’s a subtlety: When Windows as a Service gets out to three years of support, there will be six (or more!) versions of Win10 being supported.
We’re already on two years with 1511, 1607, 1703 and 1709.
Version Released End of service Days Home/Pro Ent/ Ed for Ent Win10 1709 17-Oct-17 9-Apr-19 8-Oct-19 721 Win10 1703 5-Apr-17 9-Oct-18 9-Apr-19 734 Win10 1607 2-Aug-16 10-Apr-18 9-Oct-18 798 Win10 1511 10-Nov-15 10-Oct-17 10-Apr-18 882 Win10 1507 9-Jul-15 9-May-17 670 Microsoft’s digging itself into a support nightmare even worse than the one we have today.
-
Microsoft sends cease and desist warnings to Store software publishers with “Windows” in their names
I saw this over the weekend from Günter Born. He lists two specific apps that received “infringing app” notices, and many others apparently have been hit.
One in particular stands out: Martin Geuß, who has been selling his Dr. Windows app for as long as Windows has had a store, got a notice. In case you don’t know, Martin Geuß is a Microsoft MVP of long standing, and one of the most helpful people on the internet.
Even more stupid (that’s one of BillG’s favorite terms): The notice was received on Saturday, with the recipients expected to comply by Sunday.
There’s one piece of wiggle room. Apparently the notification came from AppDetex, which “is authorized by Microsoft Corporation to facilitate the submission of and correspondence regarding complaints.” The complaint says the Dr. Windows app:
uses the trademarks of Microsoft Corporation without authorization. In this instance, the app uses “Windows” in the title.
I’ve long wondered at the way Microsoft has been granted a trademark for a common industry term. but I’m aghast at how it’s strong-arming even its most ardent supporters.
I got bit by this same bit of stupidity almost three decades ago, when a Microsoft developer warned me that the MS legal folks were casting a malicious eye at the name “Word POWER Pack.” But that’s another story, for a different time.
-
MS-DEFCON 2 for Feb 2018: Make sure Automatic Update is turned off
 Last month’s Patch Tuesday (and Monday, Wednesday, Thursday, Friday, Saturday and Sunday) should prove, once again, that knowledgeable Windows users need to turn off Automatic Update.
Last month’s Patch Tuesday (and Monday, Wednesday, Thursday, Friday, Saturday and Sunday) should prove, once again, that knowledgeable Windows users need to turn off Automatic Update.Computerworld Woody on Windows.
Do me a favor, wouldja? If you bump into any of the self-proclaimed security “experts” who tell everyone to turn on Automatic Update, would you post a link to their drivel? I took a lot of guff for my posts a year ago, advising folks to turn off Automatic Update. If there’s anybody in the industry who’s still spreading that kind of hooey, I want to know who and why.
-
Were the January Office security updates just re-released?
Anybody have info on a recent re-release of Office security patches?
On my main production machine (Win10 1703, Office 2013) I just got a Windows Update notification for all sorts of January Office (and Flash) security patches:
- Security Update for Microsoft Office 2013 (KB4011580) 64-Bit Edition
- Security Update for Microsoft Excel 2013 (KB4011639) 64-Bit Edition
- 2018-01 Security Update for Adobe Flash Player for Windows 10 Version 1703 for x64-based Systems (KB4056887)
- Security Update for Microsoft Outlook 2013 (KB4011637) 64-Bit Edition
- Security Update for Microsoft Office 2013 (KB4011636) 64-Bit Edition
- Security Update for Microsoft Word 2013 (KB4011651) 64-Bit Edition
I last installed updates on Feb 5 — when we went to MS-DEFCON 3.
I just re-ran and re-checked the KBNew list. Nothing there from Office 2013.
Did I miss something?
-
Getting out of a no-boot situation after installing Windows updates
@MrBrian has posted a very important addition to the AskWoody Knowledge Base
AKB 2000009: Getting out of a no-boot situation after installing Windows updates
It’s a step-by-step, real world guide to using the Windows Recovery Environment. Might just save your tail one day.
-
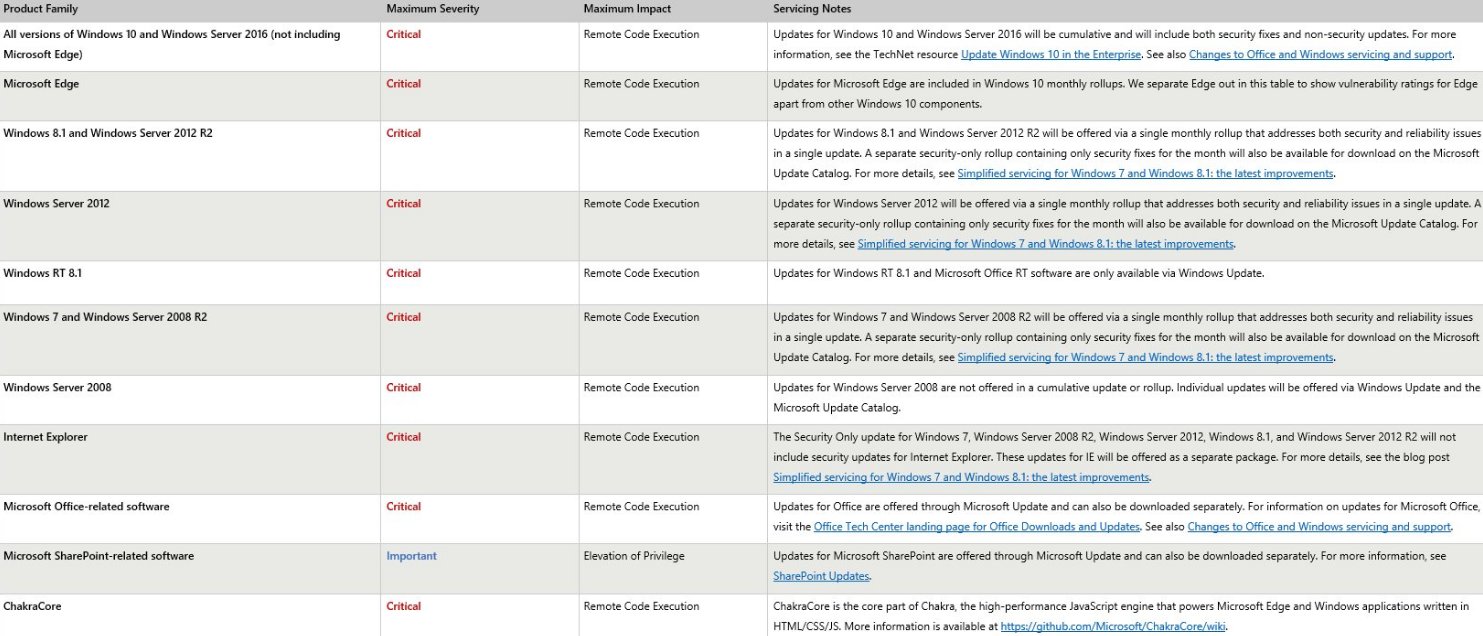
Lots of Critical, Remote Code Execution patches coming on Tuesday
Brian Krebs tweeted an early look at next Tuesday’s patches. Wowza.
-
New version 3.0 of plays-anything-anywhere app VLC
VLC 3.0 launched today.
If you’ve read my books or Computerworld top free apps articles, you know that I strongly recommend VLC. It simply runs rings around anything else.
This new version uses hardware decoding by default, streams to Chromecast (even from video formats that aren’t normally supported), and sports a dozen new features. It’s the first major update in three years.
You might want to wait a few weeks before installing it — just in case. But it’s a dynamite free utility that you’ll want sooner or later.
-
January “security” patches KB 4011657 (Word 2007), KB 4011659 (Word 2010), KB 4011643 (Word 2016), get KB article updates
Thx to @abbodi86 for picking up my earlier mistake.
Here’s another one I found while perusing the KB New list.
It looks like Microsoft just released KB article updates for the January 9 Word security patches, Word 2007, 2010 and 2016.
They’re odd. For example, the Word 2010: January 9, 2018 patch, KB 4011659, lists five CVE numbers — usually an indication that a security problem is being addressed, but the description says:
This security update contains improvements for the following nonsecurity issue:
This update improves Office application startup performance by skipping unnecessary scanning of Microsoft Word documents that are local and not encrypted.
If I read that correctly, this is a “security” update for a “nonsecurity” problem.
Go figger.
I have no idea why the KB articles were re-issued yesterday. Anybody out there have more info?