Newsletter Archives
-
February 2024 patches for Windows
 Ready or not, here comes the February updates for Windows.
Ready or not, here comes the February updates for Windows.Will we see a fix for our KB5034441 for Windows 10 22H2 and in KB5034440 for Windows 11 woes? (so far, the answer is no)
What we will see is “Highlights for Windows 11, versions 22H2 & 23H2 (cont.) •The Copilot in Windows icon will appear on the right side of the system tray on the taskbar. Also, the display of Show desktop at the rightmost corner of the taskbar will be off by default.”
Ugh. And double Ugh.
I’ll be adding more links to this post as I digest the info.
And of course it’s a “dribbled” change
- Note Windows 11 devices will get this new functionality at different times. Some of these new features roll out gradually using controlled feature rollout (CFR) to consumers.
Remember if you get Copilot and don’t want it, we’ve got your back here and here.
Grrrrrrrrrr and double grrrrrrrrrrrrrrr
Zero day blog on the updates released today.
Exchange getting patched again today. SQL client fixes released in the OS patches so check those line of business database connections. Not seeing any automated patch for the Windows RE issues. Office and specifically Outlook is getting fixed for a preview pane security issue. Defender for endpoint getting fixes for zero day that led to malware being installed.
-
Closing the year on patching
PATCH WATCH

By Susan Bradley
We need a little Copilot, now.
I have a favorite Christmas song called “We Need a Little Christmas” (now). That comes to my mind because for those of you who want to partake in the artificial intelligence experiment know as Windows Copilot, you may end up humming the slightly modified song “I Need a Little Copilot” (now).
The December updates start to bring Copilot into Windows 10. I say “start” because, like many things in Microsoftland, features and changes are no longer released en masse to everyone in the form of a service pack. Instead, the changes are dribbled out or limited to certain geographical areas.
Read the full story in our Plus Newsletter (20.51.0, 2023-12-18).
-
Wrapping up July’s updates
PATCH WATCH

By Susan Bradley
We’re at the dividing line. We are working on getting July’s updates installed and reviewing whether we have Windows 10 22H2 installed. Meanwhile, that window of opportunity for installing updates is closing soon.
But that’s just the Windows side of the patching world. On the Apple side, we’ve had to deal with zero-day patches this month. Not to be left out, Android is doing last-minute beta testing on Android 14 beta 4.1.
Read the full story in our Plus Newsletter (20.32.0, 2023-08-07).
-
Patch testing isn’t easy
PATCH WATCH

By Susan Bradley
No matter who the vendor is, bugs occur.
By the time you read this, Apple will have already re-released its rapid security patches for iOS, iPadOS (16.5.1), and MacOS Ventura (13.4.1). The patches dealt with side effects impacting Facebook, Instagram, WhatsApp, Zoom, and various other websites.
The bug release fixed a WebKit vulnerability that was being exploited in the wild. If you don’t use Safari as your default browser, or if you don’t use the impacted apps, I hope you just did the “sit tight and wait for a re-release” thing.
Read the full story in our Plus Newsletter (20.29.0, 2023-07-17).
-
Apple and Microsoft fix April zero days
PATCH WATCH

By Susan Bradley
Tomorrow is the tax-filing deadline in the US. It’s not the time to be installing updates, especially since we’re still at MS-DEFCON 2.
In other words, we’re still in deferral mode despite several newsworthy patching headlines and despite my not having noticed any significant side effects. As usual, I suggest patience until we know more.
The majority of the items of concern relate to businesses, not consumers. Here are some highlights.
Read the full story in our Plus Newsletter (20.16.0, 2023-04-17).
-
Apple emergency updates
(First off Good Friday, Happy Passover, Happy Ramadan, Happy near the end of the weekend to everyone)
Apple pushed updates for 2 new zero-days that may have been actively exploited.
🐛 CVE-2023-28206 (IOSurfaceAccelerator):
– macOS Ventura 13.3.1
– iOS and iPadOS 16.4.1🐛 CVE-2023-28205 (WebKit):
– macOS Ventura 13.3.1
– iOS and iPadOS 16.4.1Specifically:
💻 macOS Ventura 13.3.1 – 2 bugs fixed
📱 iOS and iPadOS 16.4.1 – 2 bugs fixedOn the Apple platform when you read “may have been exploited” that’s usually geek speak for “was used in a very targeted attack and has not been widely used”.
-
Ensuring you can recover
PATCH WATCH

By Susan Bradley
Anyone reading the title of this edition of Patch Watch may think I’m talking about a Windows update issue.
But no matter what your technology, I want to remind you that having a backup means that you will be able to recover.
A good friend of mine, totally ensconced in the Apple world, reported that her older Apple computer running Monterey was not a happy camper. She had been traveling and did not want to install updates. Once at home after her travels, she attempted to update. That’s when the “fun” started.
Read the full story in our Plus Newsletter (20.11.0, 2023-03-13).
-
Zero day in office – but don’t panic
Microsoft Releases Workaround Guidance for MSDT “Follina”; Vulnerability
05/31/2022 11:11 AM EDT
Original release date: May 31, 2022
Microsoft has released workaround guidance to address a remote code execution (RCE) vulnerability—CVE-2022-30190, known as “Follina”—affecting the Microsoft Support Diagnostic Tool (MSDT) in Windows. A remote, unauthenticated attacker could exploit this vulnerability to take control of an affected system. Microsoft has reported active exploitation of this vulnerability in the wild.
CISA urges users and administrators to review Microsoft’s Guidance for CVE-2022-30190 Microsoft Support Diagnostic Tool Vulnerability and apply the necessary workaround.
Here at Askwoody we are a bit more savvy. WE DON’T OPEN THINGS WE AREN’T EXPECTING. That said if you do want to proactively protect yourself ….
Group policy fix – Just disable “Troubleshooting wizards” by GPO see the location here:
Registry fix:
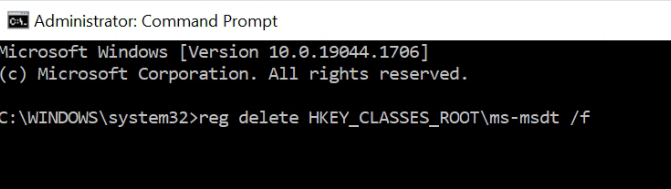
click on the search box, type in cmd
Right mouse click on cmd in the menu bar to RUN AS ADMIN
type in reg delete HKEY_CLASSES_ROOT\ms-msdt /f
Click enter
If you want to restore it back:
This registry key will restore the troubleshooting wizard – link here
Click on the downloads, double click to launch, follow the slightly scary instructions to import the registry key back in.
=================
Update 6/1/2022
Now the URI for Search is being abused.
Once again if you want to proactively protect yourself
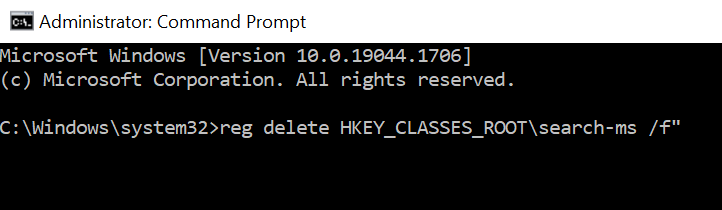
Run Command Prompt as Administrator.
Execute the command “reg delete HKEY_CLASSES_ROOT\search-ms /f”
If you want to restore it back, click here
-
Understanding the zero days
PATCH WATCH

By Susan Bradley
What do attackers go after?
If you take a look at the known, exploited vulnerability listing as put out by the Cybersecurity & Infrastructure Security Agency, you’ll find that the list is long and confusing. Even if you cut it down to just Microsoft and Apple, it’s still a bit overwhelming, to say the least.
I’m going to focus on two bugs, to showcase differences in how the attacks occur on Windows and Apple and what the attackers are going after.
Read the full story in the AskWoody Plus Newsletter 19.10.0 (2022-03-07).
-
Zero day for Windows 7
Bleeping computer reports that 0-patch is releasing a fix for a zero day in Windows 7 and server 2008 R2.
I haven’t yet seen an out of band patch released to Windows 7 ESUs but I’ll keep you posted.
One clarification on that post, Sergiu says “At the moment, only small-and-midsize businesses or organizations with volume-licensing agreements can get an ESU license until January 2023.” You actually don’t need a volume licensing agreement in order to buy Windows 7 patches. Amy Babinchak is still selling Windows 7 ESUs and for anyone who bought them last year, she’ll be contacting you to see if you want the updates again this year. Microsoft hasn’t yet set it up so that the 2021 Windows 7 ESUs are on their price list, but I’m guessing December 1st is when they will post it to the price list. It’s expected to be twice the price of last years.
-
Patch lady – targeted attacks using zero day
Per https://www.zdnet.com/article/google-discloses-windows-zero-day-exploited-in-the-wild/:
On Twitter, Hawkes said the Windows zero-day (tracked as CVE-2020-17087) was used as part of a two-punch attack, together with another a Chrome zero-day (tracked as CVE-2020-15999) that his team disclosed last week.
“We have confirmed with the Director of Google’s Threat Analysis Group, Shane Huntley, that this is targeted exploitation and this is not related to any US election-related targeting.”
It will be patched November 10th.
So the good news is that this is targeted only – not by us mere mortals. Until then keep your tinfoil on and in the ready mode
-
SandboxEscaper drops another Win10 0day on Twitter
Remember the Task Scheduler ALPC 0day dropped on Twitter at the end of August?
The same gal, @SandboxEscaper, just dropped another one. On Twitter. No forewarning. No chance for Microsoft to fix it.
Catalin Cimpanu has a good overview on ZDNet.
It’s another privilege elevation attack, which means the attacker has to be running on your machine before it kicks in, and the 0day can be used to change the running code from standard to admin.
The PoC, in particular, was coded to delete files for which a user would normally need admin privileges to do so. With the appropriate modifications, other actions can be taken, experts believe.
That makes it very mean, but not yet a potent attack.
Kevin Beaumon, @GossiTheDog, has taken a look at it:
https://twitter.com/GossiTheDog/status/1054847922452480002
I’ll update this post with the CVE number as soon as I have it.


